Construction Safety Plan

Cyber Security Implementation Framework Vital Records Maintenance Register Ppt PowerPoint Presentation Layouts PDF
Presenting this set of slides with name cyber security implementation framework vital records maintenance register ppt powerpoint presentation layouts pdf. The topics discussed in these slides are settlement agreements, litigation files, department file room, primary location records. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
IT Security Program Icon For Protecting Client Data Ideas PDF
Persuade your audience using this IT Security Program Icon For Protecting Client Data Ideas PDF This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including It Security, Program Icon, Protecting Client Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Awareness Training Program For Employees Icon Mockup PDF
Persuade your audience using this IT Security Awareness Training Program For Employees Icon Mockup PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including IT Security Awareness, Training Program, Employees Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Corporate Data Management And Privacy Security Mechanism Icon Slides PDF
Persuade your audience using this Corporate Data Management And Privacy Security Mechanism Icon Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Data, Management Privacy, Security Mechanism Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
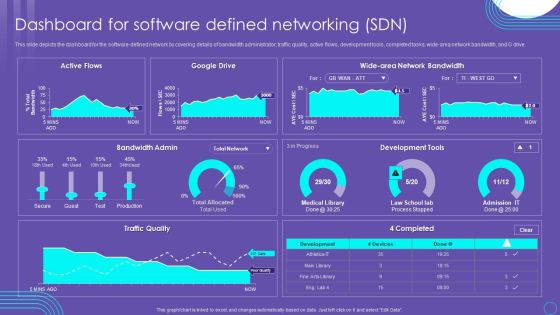
SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF
This slide depicts the dashboard for the software defined network by covering details of bandwidth administrator, traffic quality, active flows, development tools, completed tasks, wide area network bandwidth, and G drive. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created SDN Security Architecture Dashboard For Software Defined Networking SDN Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Protection Vector Showing Secured Bitcoin With Dollar Symbol Ppt PowerPoint Presentation Infographic Template Icon PDF
Showcasing this set of slides titled protection vector showing secured bitcoin with dollar symbol ppt powerpoint presentation infographic template icon pdf. The topics addressed in these templates are protection vector showing secured bitcoin with dollar symbol. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Security Of Business Website Vector Icon Ppt PowerPoint Presentation Pictures Infographics PDF
Showcasing this set of slides titled security of business website vector icon ppt powerpoint presentation pictures infographics pdf. The topics addressed in these templates are security of business website vector icon. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Measures To Prevent Accident At Workplace Ppt PowerPoint Presentation Pictures Display PDF
Showcasing this set of slides titled security measures to prevent accident at workplace ppt powerpoint presentation pictures display pdf. The topics addressed in these templates are security measures to prevent accident at workplace. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF
Pitch your topic with ease and precision using this Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF. This layout presents information on Virus Cyber Security, Attack Warning, Web Browser Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Sales Model With Value Improvement And Security Ppt PowerPoint Presentation Outline Design Inspiration PDF
Persuade your audience using this sales model with value improvement and security ppt powerpoint presentation outline design inspiration pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including global markets, medium markets, small markets. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Functioning Centre Role Of Security Operations Centre In Security Operations Sample PDF
This slide portrays information regarding the role of security operations center in SecOps and how firm behave before, after and towards SecOps implementation. Presenting security functioning centre role of security operations centre in security operations sample pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like organizational system, security, operations team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Big Data Analytics Marketing Impact Ppt PowerPoint Presentation Show
This is a big data analytics marketing impact ppt powerpoint presentation show. This is a four stage process. The stages in this process are healthcare, science, security, business.

Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF from Slidegeeks and deliver a wonderful presentation.
IT Capability Strategy With Service Delivery Ppt Icon Gridlines PDF
Persuade your audience using this it capability strategy with service delivery ppt icon gridlines pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including information security, operations, enterprise mobility. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF
This slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy.This is a Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Best Example, Authentication, Implement Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident Management before the occurrence of the incident. This modern and well arranged Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Half Yearly IT Security Recognition Program Roadmap Designs
Presenting our innovatively-structured half yearly it security recognition program roadmap designs Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Find a pre-designed and impeccable Reverse Proxy Web Server Secure Proxy Connection To Content Server Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
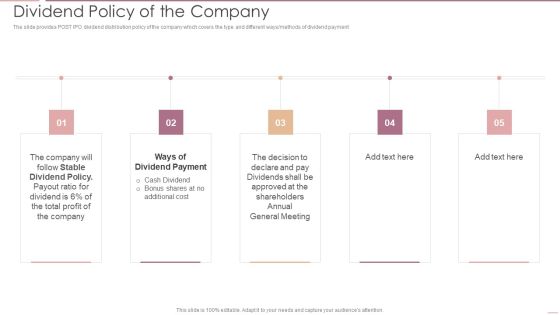
Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF
The slide provides POST IPO dividend distribution policy of the company which covers the type and different ways methods of dividend payment.Presenting Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Stable Dividend, Dividend Payment, General Meeting In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Understanding The Kubernetes Concepts And Architecture Table Of Contents Ppt Summary Inspiration PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture table of contents ppt summary inspiration pdf. This is a six stage process. The stages in this process are introduction kubernetes, kubernetes component, nodes kubernetes, kubernetes development process, networking kubernetes, security measures kubernetes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Automated Government Procedures E Governance Workstream Strategies Introduction PDF
Here we are covering the e-governance strategies which is enable everyone to use effective government services, in a secure, integrated and easy way through multiple electronic channels. Deliver an awe-inspiring pitch with this creative automated government procedures e governance workstream strategies introduction pdf bundle. Topics like infrastructure, institutional framework, change management, human capital, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slide For Cloud Based Email Security Market Report Ppt Infographics Graphic Images PDF
Introducing our well designed icons slide for cloud based email security market report ppt infographics graphic images pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Key Hurdles For Security Management Reporting Ppt PowerPoint Presentation Styles Graphic Tips PDF
Showcasing this set of slides titled key hurdles for security management reporting ppt powerpoint presentation styles graphic tips pdf. The topics addressed in these templates are employee, job responsibilities, complicated reporting documentation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Dislike Icon For Poor Data Security Ppt PowerPoint Presentation Portfolio Template PDF
Showcasing this set of slides titled dislike icon for poor data security ppt powerpoint presentation portfolio template pdf. The topics addressed in these templates are dislike icon for bad mobile app experience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Secured Video Hosting Platform Investor Capital Funding Pitch Deck Portrait PDF
Introducing our well designed icons slide for secured video hosting platform investor capital funding pitch deck portrait pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For Risk Management Model For Data Security Elements PDF
Introducing our well designed Icons Slide For Risk Management Model For Data Security Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide For IT Security Evaluation Scorecard Ppt Icon Good PDF
Introducing our well designed Icons Slide For IT Security Evaluation Scorecard Ppt Icon Good PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Icons Slide For Security Alarm And Monitoring Systems Company Profile Inspiration PDF
Introducing our well designed Icons Slide For Security Alarm And Monitoring Systems Company Profile Inspiration PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF
Pitch your topic with ease and precision using this Phishing Cyber Security Attack On Unprotected Web Icon Ppt Ideas Inspiration PDF. This layout presents information on Phishing Cyber Securit, Attack Unprotected, Web Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icons Slide For Security Automation To Analyze And Mitigate Cyberthreats Structure PDF
Introducing our well designed Icons Slide For Security Automation To Analyze And Mitigate Cyberthreats Structure PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Icons Slide For Deploying Cyber Security Incident Response Administration Elements PDF
Introducing our well designed Icons Slide For Deploying Cyber Security Incident Response Administration Elements PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
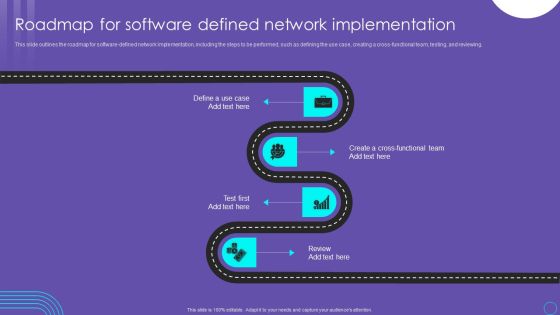
SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF
This slide outlines the roadmap for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Find a pre designed and impeccable SDN Security Architecture Roadmap For Software Defined Network Implementation Slides PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Components Of Enterprise Architecture Diagram Presentation Diagrams
This is a components of enterprise architecture diagram presentation diagrams. This is a four stage process. The stages in this process are risk and security, program management, technology driven, business driven.
PowerPoint Presentation Designs Education Chains Ppt Presentation
PowerPoint Presentation Designs Education Chains PPT Presentation-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.

E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Home Security Systems PowerPoint Templates And PowerPoint Themes 1012
Home Security Systems PowerPoint Templates And PowerPoint Themes 1012-With these pre-designed chains you can visualize almost any type of concept, chronological process or steps of your strategies. This Targets the Security of Home, Business as illustrated by image. This Template points to the Chain Security which can be showed by alarm clock, dollars and house.-Home Security Systems PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Great For Home Security, Security, Business, Shapes, Symbol, Background

Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF
This slide shows insider threat protection process with usage of defensive controls. It provides information about indicators, prevent, detect, respond, recruitment, scouting, collection, elimination, etc. Showcasing this set of slides titled Insider Threat In Cyber Security Protection Process With Defensive Controls Template PDF. The topics addressed in these templates are Recruitment, Scouting, Collection, Elimination. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
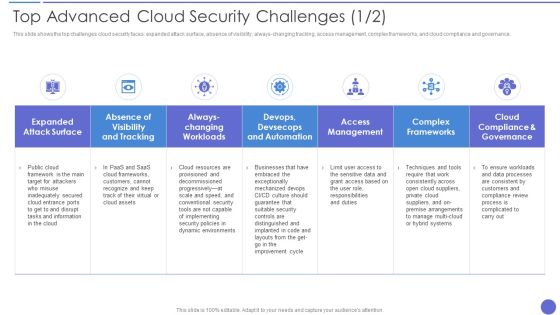
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. Slidegeeks is here to make your presentations a breeze with Overview Of Cyber Security Awareness Course Ppt Ideas Styles PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Crisis Communication Process Framework Icons PDF
This slide showcases a model of crisis communication process for cyber security. It includes identify issues, set goals, and objectives, community and constraints, stakeholder assessment, communication and engagement tools, implement strategy and evaluate and follow up. Presenting Cyber Security Crisis Communication Process Framework Icons PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Implement Strategy, Identify Community, Set Goals And Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents
Presenting you an exemplary Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Table Of Contents For One Page Yearly Report For Internet Security Company One Pager Documents brilliant piece now.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF
This slide showcases organizational framework for handling service desks. It provides information about end user interaction, incident management, request fulfilment, network management, end user computing, etc. Deliver and pitch your topic in the best possible manner with this Improve IT Service Desk Organizational Framework For Handling Service Desks Background PDF. Use them to share invaluable insights on Security Management, Network Management, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Face Scanning Smart Phone Security Technique Icon Brochure PDF
Persuade your audience using this Face Scanning Smart Phone Security Technique Icon Brochure PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Face Scanning, Smart Phone, Security Technique Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
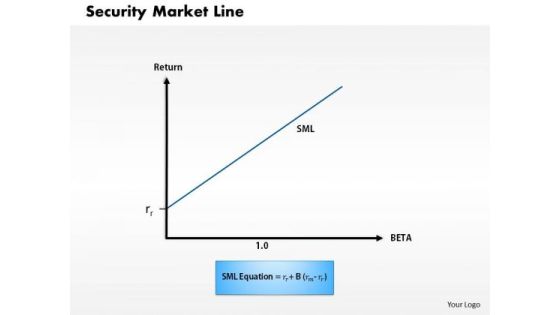
Business Framework Security Market Line 1 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

Business Framework Security Market Line 11 PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF
This slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. If you are looking for a format to display your unique thoughts, then the professionally designed CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download CYBER Security Breache Response Strategy Cyber Security Incident Management Team Roles Responsibilities Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
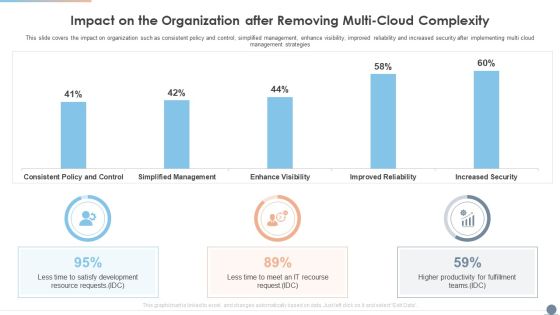
Multi Cloud Complexity Management Impact On The Organization After Removing Multi Cloud Complexity Information PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. Deliver an awe inspiring pitch with this creative Multi Cloud Complexity Management Impact On The Organization After Removing Multi Cloud Complexity Information PDF bundle. Topics like Satisfy Development, Resource Requests, Fulfillment Teams can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. This Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Bestinformation Technology Security And Data Security Practices Slides PDF
The following slide highlights the best practices to protect the business from security threats. It includes activities such as installing and upgrading protective software, adopting strong password policy, applying multi-layer authentication etc. Persuade your audience using this Bestinformation Technology Security And Data Security Practices Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Adopt Strong Password Policy, Make Regular Backups, Resource Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Retrieve professionally designed Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
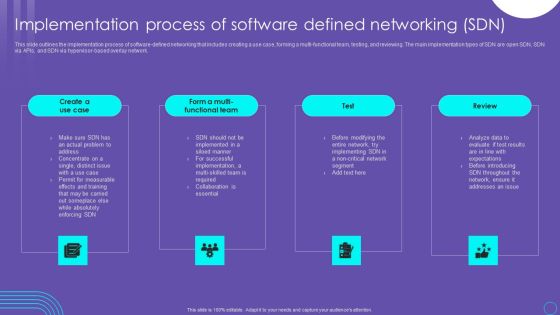
SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF
This slide outlines the implementation process of software defined networking that includes creating a use case, forming a multi functional team, testing, and reviewing. The main implementation types of SDN are open SDN, SDN via APIs, and SDN via hypervisor based overlay network. The SDN Security Architecture Implementation Process Of Software Defined Networking SDN Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. This CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The CYBER Security Breache Response Strategy Cyber Security Risk Assessment And Management Dashboard Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Explore a selection of the finest CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our CYBER Security Breache Response Strategy Cyber Security Systems Monitoring Report Formats PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

IT Risk Control Strategies Risk Management Framework Mockup PDF
This slide shows the framework for information technology risk management which includes cyber security governance, IT and security risk assessment, training and awareness, security operation centre, independent audit and gap analysis. Persuade your audience using this IT Risk Control Strategies Risk Management Framework Mockup PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Governance, IT Risk Assessment, Security Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Firm Productivity Administration BI Design And Development Access Ppt PowerPoint Presentation Show Examples PDF
Presenting this set of slides with name firm productivity administration bi design and development access ppt powerpoint presentation show examples pdf. This is a four stage process. The stages in this process are web based access, component based architecture, service oriented architecture, ssl security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012
Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012-With these pre-designed chains you can visualize almost any type of concept, chronological process or steps of your strategies. This Targets the Security in Life, Business as shown above. This Template points to the Chain Security which signifies Team Work. It shows the number of chains crossed together to secure the family ,Business etc.-Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chain cross, security, business, chains, success, leadership

 Home
Home