Authentication

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
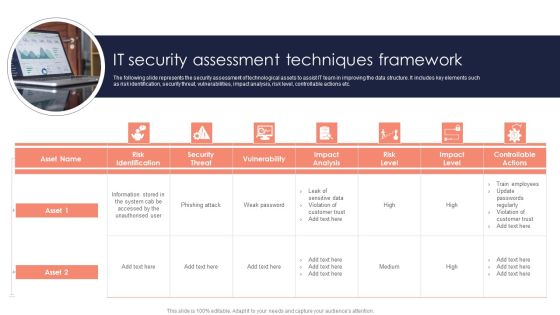
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Management Best Practices Themes PDF
This slide presents various best practices for information security governance to effectively manage and mitigate IT risks. It includes key practices such as reflect business objectives, develop and enforce security program, embrace organizations culture, etc. Presenting Information Security Management Best Practices Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Reflect Business Objectives, Spend Resources Effectively, Embrace Organizations Culture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Employee Training Record With Participant Record Ppt PowerPoint Presentation Pictures Background PDF
Presenting this set of slides with name employee training record with participant record ppt powerpoint presentation pictures background pdf. The topics discussed in these slides are department, designation, verification training effectiveness, verification criteria, satisfactory. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
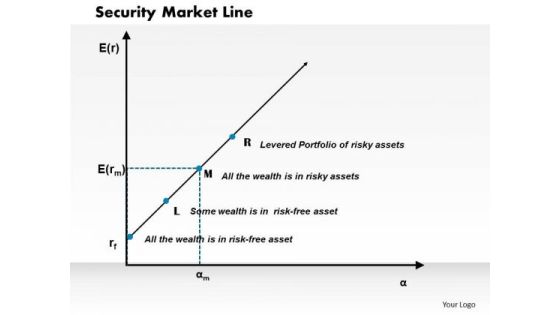
Security Market Line Business PowerPoint Presentation
Document The Process On Our Security Market Line Business Powerpoint Presentation Powerpoint Templates. Make A Record Of Every Detail. Satiate Desires With Our success Powerpoint Templates. Give Them All They Want And More.
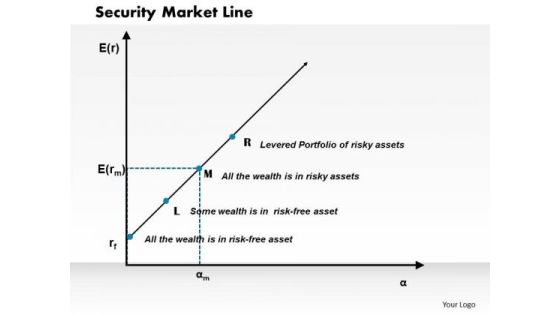
Business Framework Security Market Line PowerPoint Presentation
This diagram displays graph of security market line. You can use line graph to plot changes in data over time, such as monthly revenue and earnings changes or daily changes in stock market prices.

Security Of Supply Project Assessment Ppt Slides
This is a security of supply project assessment ppt slides. This is a four stage process. The stages in this process are project assessment, technical resilience, technical aspects, losses variation.
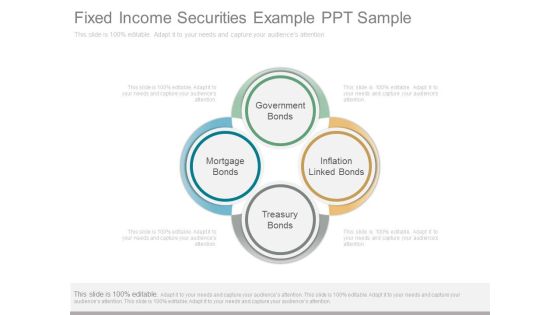
Fixed Income Securities Example Ppt Sample
This is a fixed income securities example ppt sample. This is a four stage process. The stages in this process are government bonds, inflation linked bonds, treasury bonds, mortgage bonds.\n\n\n\n\n\n
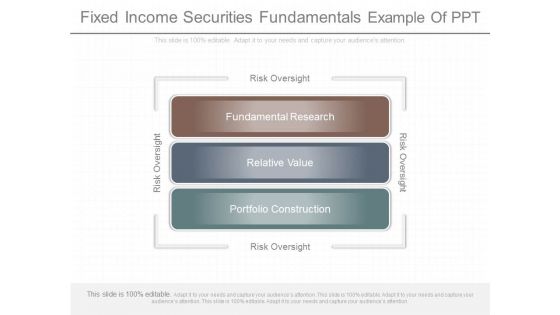
Fixed Income Securities Fundamentals Example Of Ppt
This is a fixed income securities fundamentals example of ppt. This is a three stage process. The stages in this process are risk oversight, fundamental research, relative value, portfolio construction.
Kinds Of Fixed Income Securities Presentation Backgrounds
This is a kinds of fixed income securities presentation backgrounds. This is a six stage process. The stages in this process are arts and antiques, commodities, real estate, mutual funds and etfs, stock market, debts government bands, investment options.

Stock Exchange Securities Listings Ppt Presentation
This is a stock exchange securities listings ppt presentation. This is a four stage process. The stages in this process are advertisement, minimum subscription, applying mode, public offer size.

Investment Securities Research Diagram Ppt Slides
This is a investment securities research diagram ppt slides. This is a four stage process. The stages in this process are investment objectives, economic analysis, market analysis, construct portfolio, implement review.

Securities Settlement System Diagram Ppt Slides
This is a securities settlement system diagram ppt slides. This is a five stage process. The stages in this process are market makers, stock exchange, clearing house, share seller, share purchaser.
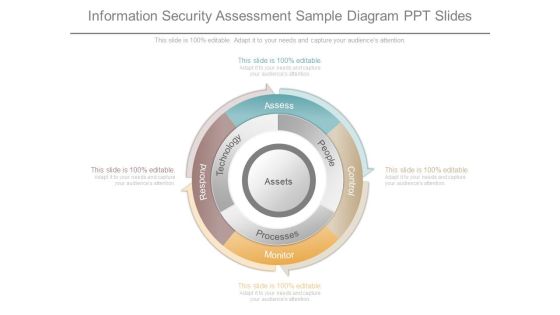
Information Security Assessment Sample Diagram Ppt Slides
This is a information security assessment sample diagram ppt slides. This is a four stage process. The stages in this process are assess, people, processes, technology, respond, monitor, control.

Security Assessment Services Sample Diagram Powerpoint Image
This is a security assessment services sample diagram powerpoint image. This is a six stage process. The stages in this process are define scope, agree start date, configuration review, vulnerability scanning, penetration testing, configuration review.

Strategy Of Proactive Security Process Ppt Presentation
This is a strategy of proactive security process ppt presentation. This is a three stage process. The stages in this process are environment scanning, pear networking, result, threat detection, incident response, cyber incident.

Secure Merchant Account Services Template Presentation Slides
This is a secure merchant account services template presentation slides. This is a four stage process. The stages in this process are point of sales, optimize, business financing, growth.

Security Policy Process Diagram Layout Ppt Gallery
This is a security policy process diagram layout ppt gallery. This is a five stage process. The stages in this process are executions, commercial bank, customer service assistance, bank office, custodian.
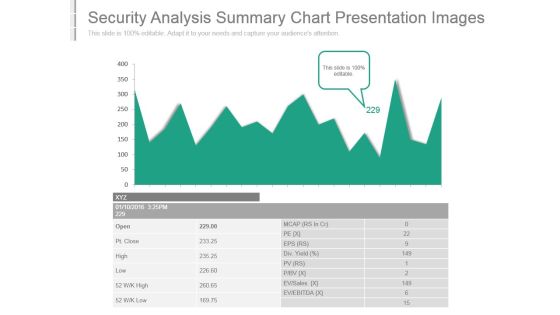
Security Analysis Summary Chart Presentation Images
This is a security analysis summary chart presentation images. This is a one stage process. The stages in this process are ev ebitda, ev sales, div yield, open, pt close, high, low, mcap, eps.
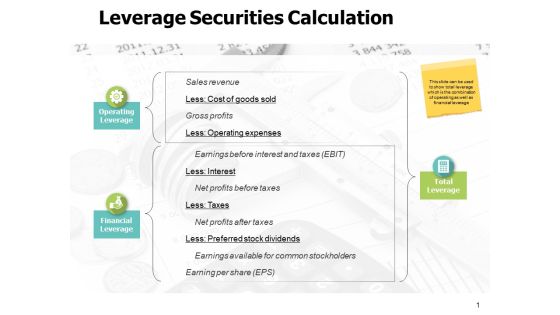
Leverage Securities Calculation Ppt PowerPoint Presentation Model
This is a leverage securities calculation ppt powerpoint presentation model. The topics discussed in this diagram are marketing, business, management, planning, strategy This is a completely editable PowerPoint presentation, and is available for immediate download.

Cyber Security Incident Response Lifecycle Information PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Presenting this PowerPoint presentation, titled Cyber Security Incident Response Lifecycle Information PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cyber Security Incident Response Lifecycle Information PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cyber Security Incident Response Lifecycle Information PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Security Encryption Ppt PowerPoint Presentation Layouts Cpb
Presenting this set of slides with name security encryption ppt powerpoint presentation layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like security encryption to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Securities Finance Ppt PowerPoint Presentation Pictures Cpb
Presenting this set of slides with name securities finance ppt powerpoint presentation pictures cpb. This is an editable Powerpoint four stages graphic that deals with topics like securities finance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
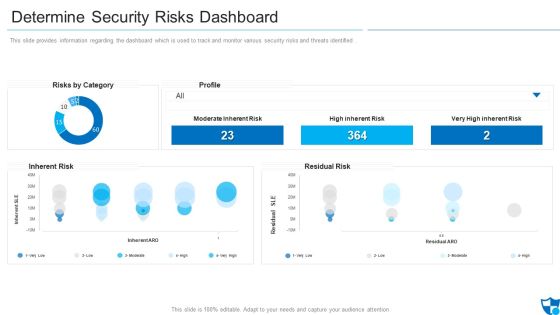
Determine Security Risks Dashboard Introduction PDF
This slide provides information regarding the dashboard which is used to track and monitor various security risks and threats identified.Deliver and pitch your topic in the best possible manner with this determine security risks dashboard introduction pdf. Use them to share invaluable insights on moderate inherent risk, high inherent risk, very high inherent risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
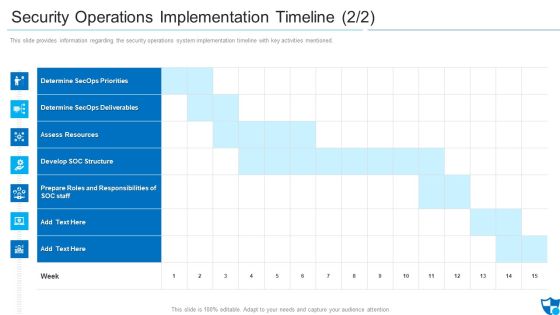
Security Operations Implementation Timeline Assess Diagrams PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned.Deliver and pitch your topic in the best possible manner with this security operations implementation timeline assess diagrams pdf. Use them to share invaluable insights on determine secops priorities, determine secops deliverables, assess resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
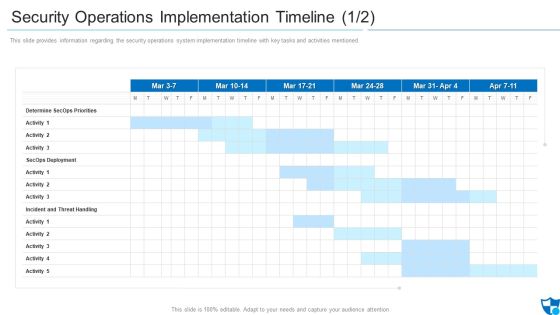
Security Operations Implementation Timeline Priorities Introduction PDF
This slide provides information regarding the security operations system implementation timeline with key tasks and activities mentioned.Deliver an awe inspiring pitch with this creative security operations implementation timeline priorities introduction pdf bundle. Topics like determine secops priorities, secops deployment, incident and threat handling can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management System Microsoft PDF
The following slide illustrates the cyber security threat management system which includes threat containment, logging and traceability management. Pitch your topic with ease and precision using this cyber security risk management system microsoft pdf. This layout presents information on mapping threats, threat containment and remediation, identify management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Technology Evaluation Process Download PDF
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda For Cloud Data Security Ideas PDF
This is a Agenda For Cloud Data Security Ideas PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Responsibilities And Service, Organizations, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Hybrid Cloud Security Solutions Rules PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy This is a Hybrid Cloud Security Solutions Rules PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Redundancy, Categorization Of Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
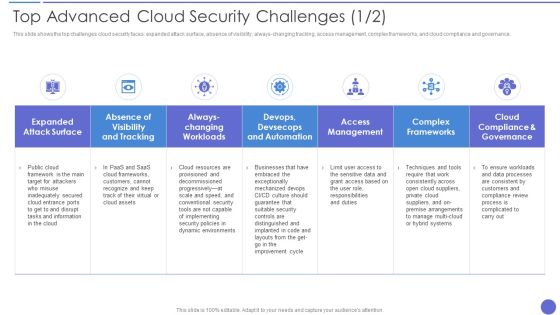
Top Advanced Cloud Security Challenges Brochure PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governance. Deliver an awe inspiring pitch with this creative Top Advanced Cloud Security Challenges Brochure PDF bundle. Topics like Complex Frameworks, Access Management, Dynamic Environments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
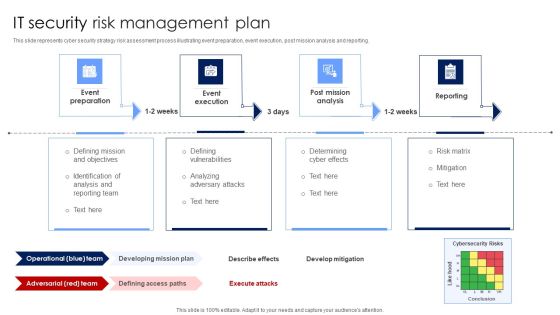
IT Security Risk Management Plan Mockup PDF
This slide represents cyber security strategy risk assessment process illustrating event preparation, event execution, post mission analysis and reporting. Presenting IT Security Risk Management Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Post Mission Analysis, Reporting, Event Execution. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
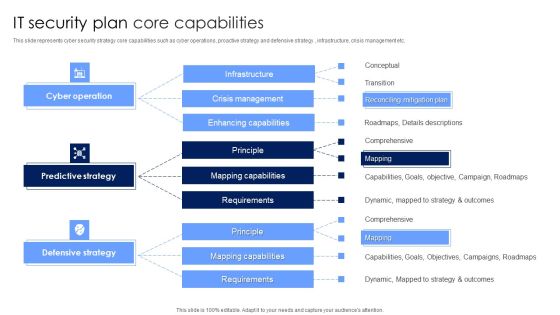
IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
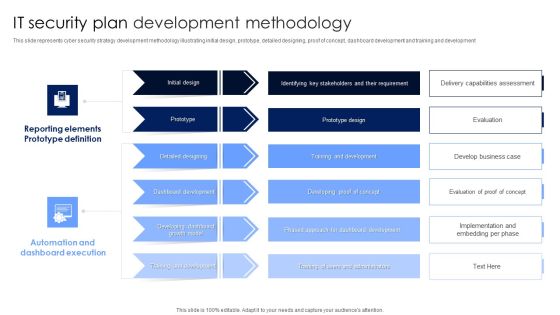
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Digital Network Security Assessment Flowchart Structure PDF
This slide showcases digital network security assessment flowchart which helps ensure reduction in information leaks. It provides information regarding network enumeration, service assessment and data collection and reporting. Showcasing this set of slides titled Digital Network Security Assessment Flowchart Structure PDF. The topics addressed in these templates are Account Holder, Information Leak, Network Service Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
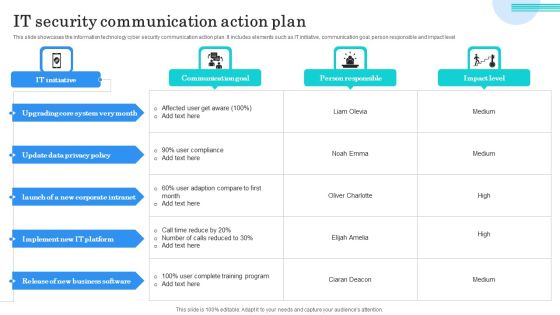
IT Security Communication Action Plan Portrait PDF
This slide showcases the information technology cyber security communication action plan. It includes elements such as IT initiative, communication goal, person responsible and impact level. Showcasing this set of slides titled IT Security Communication Action Plan Portrait PDF. The topics addressed in these templates are Upgrading Core System, Update Data Privacy, Implement IT Platform. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Incident Communication Strategy Information PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cyber Security Incident Communication Strategy Information PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cyber Security Incident Communication Strategy Information PDF.

Cyber Security Five Year Strategic Timeline Demonstration
We present our cyber security five year strategic timeline demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security five year strategic timeline demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
IT Security Five Years Strategic Timeline Icons
We present our it security five years strategic timeline icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched it security five years strategic timeline icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Strategic Five Year Functional Timeline Graphics
We present our security strategic five year functional timeline graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched security strategic five year functional timeline graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Internet Security Incident Analysis Report Template PDF
This slide exhibits security data breach incident report. It includes multiple steps such as- report the number of personal data record lost, analyze the possible effects of personal data breaches and so on. Showcasing this set of slides titled internet security incident analysis report template pdf. The topics addressed in these templates are data breach details, consequences, measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
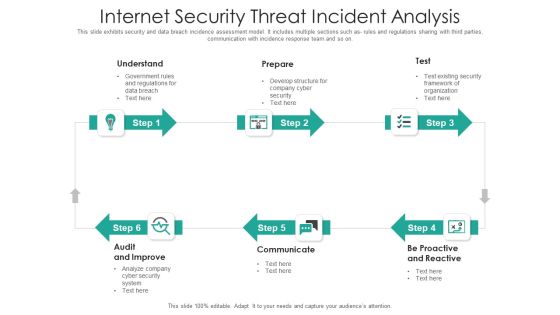
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Threats Malware Attacks Sample PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Security Threats Malware Attacks Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technology, Targets, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Threats Revenue Losses Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Security Threats Revenue Losses Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organizations, Revenue, Investing Money. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Challenges In Cloud Security Portrait PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs. Presenting Key Challenges In Cloud Security Portrait PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Daniel Of Service, Compliance Violations, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Risks Or Threats Brochure PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Security Risks Or Threats Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Malware Attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
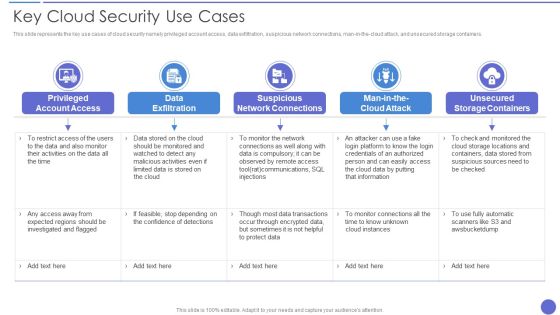
Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
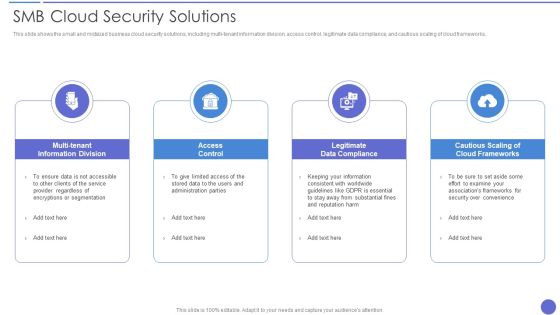
Smb Cloud Security Solutions Download PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. This is a Smb Cloud Security Solutions Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Legitimate Data Compliance, Cloud Frameworks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Incident Handling Checklist Elements PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Take your projects to the next level with our ultimate collection of Cyber Security Incident Handling Checklist Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Information Security Management Strategic Model Inspiration PDF
The following slide showcases a framework presenting strategy development and implementation phase in information security governance. It includes key components such as organizational structure, value delivery, strategic alignment, resource optimization, performance measurement, etc. Presenting Information Security Management Strategic Model Inspiration PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Value Delivery, Key Insights, Organizational Structure. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Selecting Secured Threat Management Software Introduction PDF
This slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable Selecting Secured Threat Management Software Introduction PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Key Cloud Network Security Challenges Sample PDF
The slide includes security challenges faced by users and providers in cloud computing. The elements are Ddos and denial of service attacks , data breaches , data loss , insecure access control points, metastructure and applistructure failures Persuade your audience using this Key Cloud Network Security Challenges Sample PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Insecure Access Control Points, Data Breaches, Data Loss. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
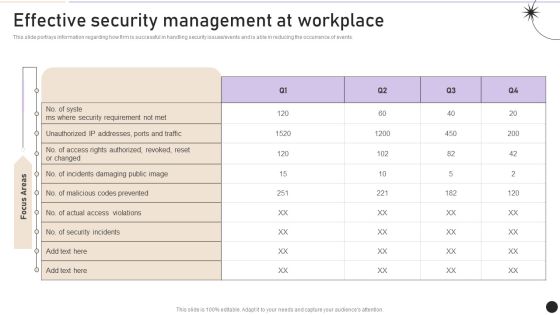
Effective Security Management At Workplace Designs PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present like a pro with Effective Security Management At Workplace Designs PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cyber Security Hazards Management Program Pictures PDF
The below slide outlines the cyber security threats along with mitigation strategy which helps an organisation to tackle and prevent potential risks. Key components are threat, risk, priority, mitigation step, person responsible and deadline.Showcasing this set of slides titled Cyber Security Hazards Management Program Pictures PDF. The topics addressed in these templates are Sensitive Customer, Data Encryption Using. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information IT Security Communication Plan Guidelines PDF
This slide showcases an information cyber security communication plan to effectively communicate cyber incident and action plan. It includes cyber incidents such as virus, spyware, firewall hacking and phishing. Showcasing this set of slides titled Information IT Security Communication Plan Guidelines PDF. The topics addressed in these templates are Run Microsoft Defender Offline, Install Antivirus, Block Traffic Default. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Page Object Model In Automated Testing Framework Ppt Professional Graphics PDF
This slide shows page object model in test automation framework which can be beneficial for web developers to streamline their routine work. It contains information about test script, driver, credentials login, page object, login page, main page, menu bar, header section and page or screen. Presenting Page Object Model In Automated Testing Framework Ppt Professional Graphics PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Test Script, Page Object, Main Page. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

New Software Training Project Rollout Roadmap Calendar Infographics PDF
This slide shows new software training plan rollout schedule for helping employees to adapt technical advancement. It include steps such as passing login instructions, getting familiar with app, building separate project team etc. Presenting New Software Training Project Rollout Roadmap Calendar Infographics PDF to dispense important information. This template comprises Nine stages. It also presents valuable insights into the topics including Pass Login Instructions, Build Separate Project Team, Develop Content Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Generic Use Cases Of Financial Banking Application Testing Ppt Summary Show PDF
This slide provide information about generic use case to properly understand the nature of mobile application testing. It includes elements such as valid login credentials, perform basic transactions, change data, account blockage. Presenting Generic Use Cases Of Financial Banking Application Testing Ppt Summary Show PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Valid Login Credentials, Perform Basic Transactions, Change Data, Account Blockage. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
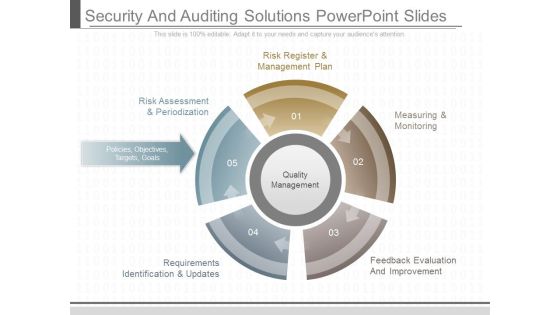
Security And Auditing Solutions Powerpoint Slides
This is a security and auditing solutions powerpoint slides. This is a five stage process. The stages in this process are risk register and management plan, risk assessment and periodization, policies objectives targets goals, requirements identification and updates, measuring and monitoring, feedback evaluation and improvement, quality management.
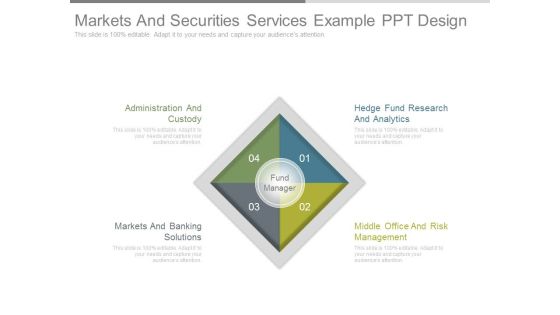
Markets And Securities Services Example Ppt Design
This is a markets and securities services example ppt design. This is a four stage process. The stages in this process are administration and custody, markets and banking solutions, hedge fund research and analytics, middle office and risk management, fund manager.
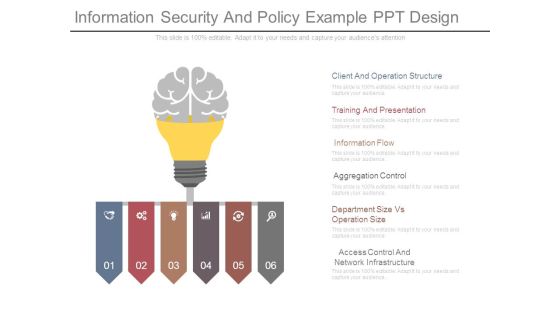
Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.

Organizational Security Solutions Quotes Ppt Model PDF
Deliver an awe inspiring pitch with this creative organizational security solutions quotes ppt model pdf bundle. Topics like quotes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Organizational Security Solutions Financial Icons PDF
Presenting organizational security solutions financial icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like euro, dollar, pound. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Growing Cyber Security Issues Portrait PDF
Deliver and pitch your topic in the best possible manner with this growing cyber security issues portrait pdf. Use them to share invaluable insights on unprecedented attacks, cyber espionage, data theft and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
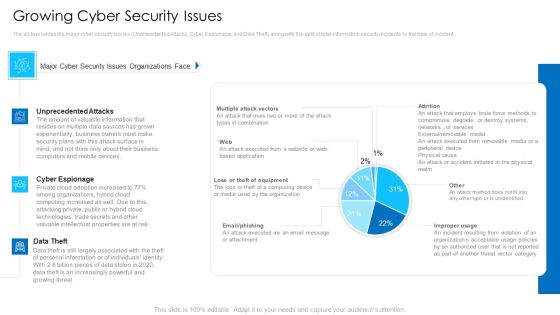
Growing Cyber Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative growing cyber security issues mockup pdf bundle. Topics like unprecedented attacks, cyber espionage, data theft can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
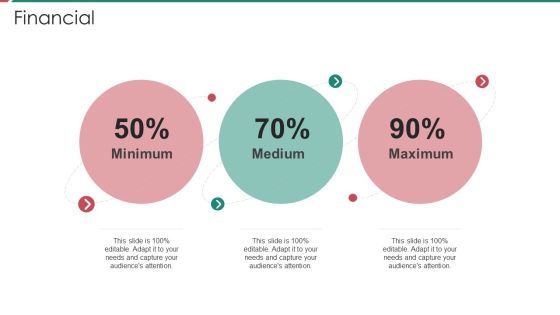
Security And Process Integration Financial Formats PDF
Presenting security and process integration financial formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like minimum, medium, maximum. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Desktop Security Management Structure PDF
This is a agenda for desktop security management structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan, strategies, information systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Icons Slide For IT Security Designs PDF
Download our innovative and attention grabbing icons slide for it security designs pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.

Agenda For Cloud Security Assessment Infographics PDF
Presenting Agenda For Cloud Security Assessment Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Incident Response Lifecycle Diagrams PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Incident Response Lifecycle Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Incident Handling Checklist Information PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Welcome to our selection of the Cyber Security Incident Handling Checklist Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
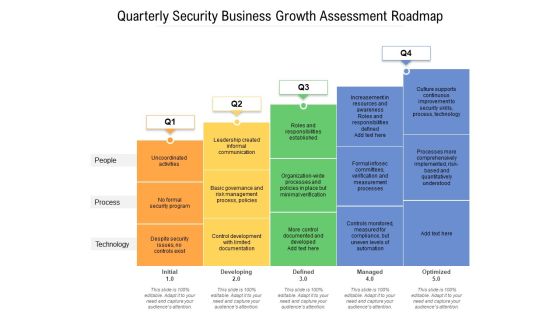
Quarterly Security Business Growth Assessment Roadmap Infographics
Presenting our jaw-dropping quarterly security business growth assessment roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Quarterly IT Security Recognition Program Roadmap Infographics
Presenting our innovatively-structured quarterly it security recognition program roadmap infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Half Yearly Strategic Timeline Icons
Presenting our innovatively structured cyber security half yearly strategic timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Three Months Strategic Timeline Sample
Presenting our jaw dropping cyber security three months strategic timeline sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
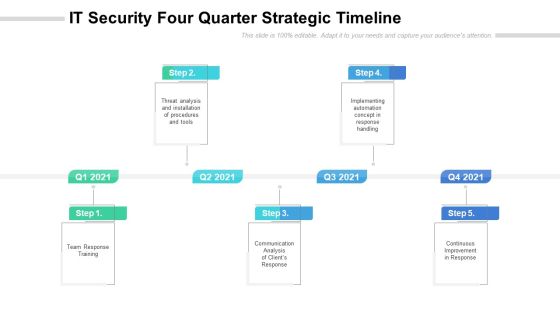
IT Security Four Quarter Strategic Timeline Slides
Presenting our innovatively structured it security four quarter strategic timeline slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

IT Security Half Yearly Strategic Timeline Diagrams
Introducing our it security half yearly strategic timeline diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

IT Security Three Months Strategic Timeline Portrait
Presenting our jaw dropping it security three months strategic timeline portrait. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Security Strategic Four Quarter Functional Timeline Icons
Presenting our innovatively structured security strategic four quarter functional timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
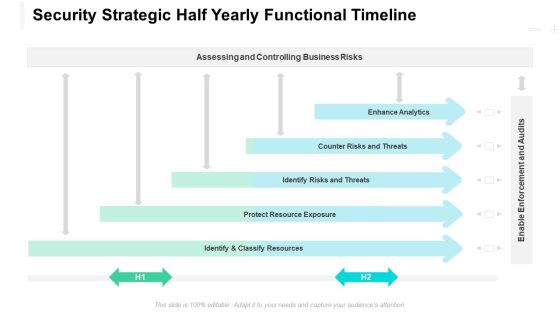
Security Strategic Half Yearly Functional Timeline Designs
Introducing our security strategic half yearly functional timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Security Strategic Three Months Functional Timeline Introduction
Presenting our jaw dropping security strategic three months functional timeline introduction. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Information Security Ppt PowerPoint Presentation Complete Deck
Incorporate this Information Security Ppt PowerPoint Presentation Complete Deck to define the objectives of business performance and how to drive results. List goals and outline a plan to achieve all your enterprise targets using this well-crafted complete deck in sixty four slides. Walk your audience through the key objectives of your business set-up, especially for customers and inspire them to work with diligence using this predesigned presentation template. Download now with the added assurance of a 100 percent customizable and editable product.

Cyber Security Network Development Timeline Download PDF
The following slide depicts a roadmap to plan an action plan to ensure data safety and prevent threats. It also includes quarter wise actions such as analyse, establish, select and practice. Presenting Cyber Security Network Development Timeline Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Establish, Analyse, Practice. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

IT Security Six Months Strategic Timeline Portrait
Presenting the it security six months strategic timeline portrait. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Security Strategic Six Months Functional Timeline Clipart
Presenting the security strategic six months functional timeline clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
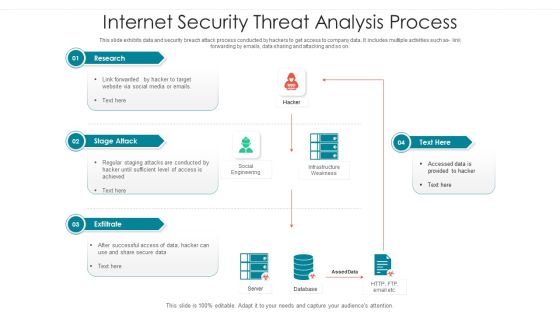
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Security And Risk Management User Spending By Segment Portrait PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Presenting this PowerPoint presentation, titled Information Security And Risk Management User Spending By Segment Portrait PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security And Risk Management User Spending By Segment Portrait PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security And Risk Management User Spending By Segment Portrait PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Stock Photo Graphics Of Padlock With Us Dollar Pwerpoint Slide
This business image has been designed with graphic of padlock with US dollar. This image contains the concept of finance and security. Make a quality presentation for financial security.

Stock Photo Textured Lock With Us Dollar Pwerpoint Slide
This business image has been designed with graphic of textured lock with US dollar. This image contains the concept of finance and security. Make a quality presentation for financial security.

Stock Photo Us Dollar Lock With Golden Keys Pwerpoint Slide
This business image has been crafted with graphic of US dollar lock and golden keys. This image contains the concept of finance and security related presentation. Build a strong presentation for wealth management and security.

Stock Photo Dollar Covered With Chain Financial Safety PowerPoint Slide
This Power Point image template has been crafted with graphic of dollar. Dollar is covered with chain which shows the concept of security. Use this image template financial security related presentations.

Computer Security Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this Computer Security Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Model Business PowerPoint Templates Security Plan Slides
We present our model business powerpoint templates security plan Slides.Download our Marketing PowerPoint Templates because you should Experience excellence with our PowerPoint Templates and Slides. They will take your breath away. Download our Circle Charts PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Download our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download and present our Business PowerPoint Templates because It will get your audience in sync. Download and present our Shapes PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown.Use these PowerPoint slides for presentations relating to arrow, blue, chart, chevron, circle, circular, diagram, graphic, green, hub, icon, illustration, isometric, pie, pieces, process, purple, red, round, set, slices, stages, vector, wheel, yellow. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
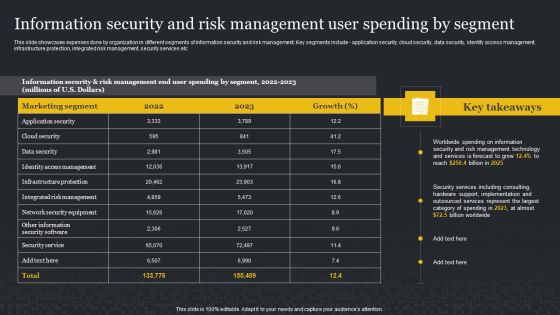
Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

White Tail Buck Animal PowerPoint Template 0810
White tail buck with antlers still in velvet touching noses with young offspring. Useful for many concepts; love security bonding parenting etc.

The Problem Challenges Tools Ppt Slides
This is a the problem challenges tools ppt slides. This is a four stage process. The stages in this process are business, industrial, security, success.

Vertical Chart For Solution Powerpoint Slide Designs
This is a vertical chart for solution powerpoint slide designs. This is a six stage process. The stages in this process are business, success, management, strategy, security.

Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Get a simple yet stunning designed Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Find highly impressive Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.
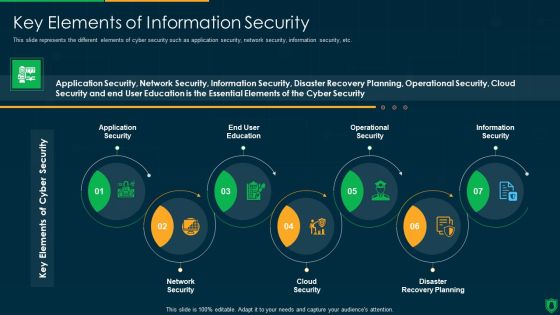
Info Security Key Elements Of Information Security Ppt PowerPoint Presentation Gallery Slide Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. Presenting info security key elements of information security ppt powerpoint presentation gallery slide download pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like application security, end user education, operational security, information security, network security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
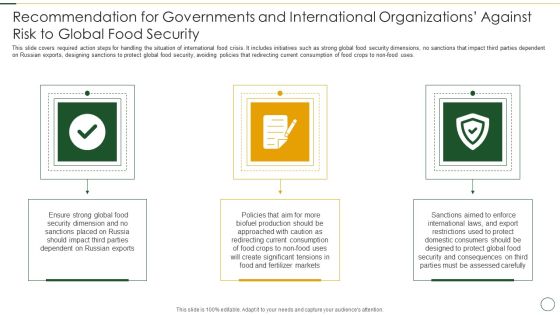
Recommendation For Governments And International Organizations Against Risk To Global Food Security Infographics PDF
This slide covers required action steps for handling the situation of international food crisis. It includes initiatives such as strong global food security dimensions, no sanctions that impact third parties dependent on Russian exports, designing sanctions to protect global food security, avoiding policies that redirecting current consumption of food crops to non food uses. Presenting recommendation for governments and international organizations against risk to global food security infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dependent on russian, ensure strong global, security dimension In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
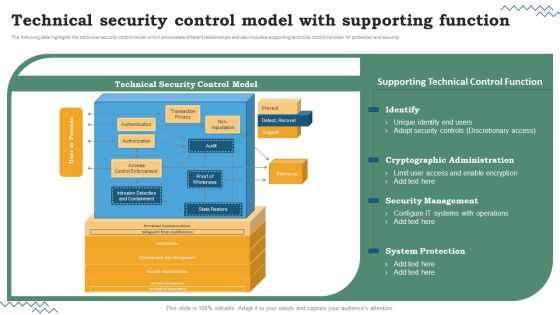
Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Are you searching for a Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF that is uncluttered, straightforward, and original. Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Software Development Life Cycle Planning Technical Security Control Model With Supporting Function Inspiration PDF from Slidegeeks today.

Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
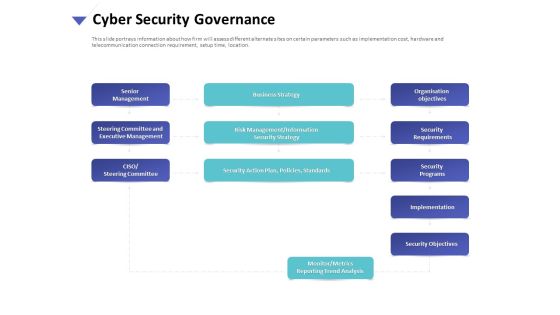
Strategies To Mitigate Cyber Security Risks Cyber Security Governance Ppt Styles Model PDF
Presenting this set of slides with name strategies to mitigate cyber security risks cyber security governance ppt styles model pdf. This is a one stage process. The stages in this process are senior management, steering committee and executive management, ciso steering committee, business strategy, risk management, information, security strategy, security action plan, policies, standards organisation, objectives security requirements, security programs, implementation, security objectives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Deliver an awe inspiring pitch with this creative IT Security Automation Tools Integration Domain Security Controls That Can Be Automated Information PDF bundle. Topics like Information Security Controls, Controls, Security Policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Bunch Of House Shaped Keys Real Estate PowerPoint Templates And PowerPoint Themes 0912
Bunch Of House Shaped Keys Real Estate PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with bunch of color house shape keys-Bunch of color house shape keys, real estate, business, security, success, symbol

Stock Photo Business Intelligence Strategy Theme Of Key To Success Pictures Images
Extract Admiration From The Audience. Create A Forceful Impact With Our stock photo business intelligence strategy theme of key to success pictures images. Force Doors Open With Our security. The Audience Will Decide To Let Your Thoughts Enter.
Stock Photo Business Model Strategy Keys For Terms Best
Actualize The Dreams Of Your Forefathers. Bring Them To The Forefront With Our stock photo business model strategy keys for terms best. Put Your Ideas In The Forefront. Our security Will Back Your Call.
Stock Photo Basic Marketing Concepts Illustration Of Key Innovation Business Pictures Images
Get The Doers Into Action. Activate Them With Our stock photo basic marketing concepts illustration of key innovation business pictures images Powerpoint Templates. Put Your Money On Our Security Powerpoint Templates. Your Ideas Will Rake In The Dollars.
Stock Photo Basic Marketing Concepts Illustration Of Key To Success Business Pictures Images
Put In A Dollop Of Our stock photo basic marketing concepts illustration of key to success business pictures images Powerpoint Templates. Give Your Thoughts A Distinctive Flavor. Create Your Domain With Our Security Powerpoint Templates. Rule Minds With Your Thoughts.
Stock Photo Business And Strategy Find The Key Of Solution Clipart Images
Connect The Dots With Our stock photo business and strategy find the key of solution clipart images Powerpoint Templates. Watch The Whole Picture Clearly Emerge. Dot Your Thoughts With Our Security Powerpoint Templates. Give Your Demeanor That Propel Look.
Stock Photo Business Development Strategy Illustration Of Key Solution Clipart Images
Land The Idea With Our stock photo business development strategy illustration of key solution clipart images Powerpoint Templates. Help It Grow With Your Thoughts. Cover The Compass With Our Security Powerpoint Templates. Your Ideas Will Be Acceptable To All.

Stock Photo Business Expansion Strategy Key Of Strategies Pictures
Draft It Out On Our stock photo business expansion strategy key of strategies pictures Powerpoint Templates. Give The Final Touches With Your Ideas. Get A Bakers Dozen With Our Security Powerpoint Templates. Receive That Little Bit More Than Expected.

Stock Photo Business Strategy Execution Keys Of Success And Growth Clipart
Delight Them With Our Stock Photo Business Strategy Execution Keys Of Success And Growth Clipart Powerpoint Templates. Your Audience Will Be Ecstatic. Our Security Powerpoint Templates Are Created Cost Effective. They Understand The Need For Economy.

Business Diagram Lock With Puzzle Strategy Concept Presentation Template
This business diagram template has been crafted with graphic of puzzle. This diagram contains the concept of strategy building and safety. Use this diagram for your business and security related presentations.

Stock Photo Pile Of Dollars Chained And Locked PowerPoint Slide
This image displays dollar bundles locked in chains. Use this image slide, in your PowerPoint presentations to express views on financial security and monetary savings. This image will enhance the quality of your presentations.

Stock Photo Red Dollar Symbol With Metallic Combination Lock PowerPoint Slide
This image slide displays red color dollar symbol with combination lock. Use this image, in your PowerPoint presentations to express views on financial security and monetary savings. This image slide will enhance the quality of your presentations.

Stock Photo Red Euro Symbol With Padlock PowerPoint Slide
This image slide displays red color Euro symbol with padlock. Use this image, in your PowerPoint presentations to express views on financial security and monetary savings. This image slide will enhance the quality of your presentations.
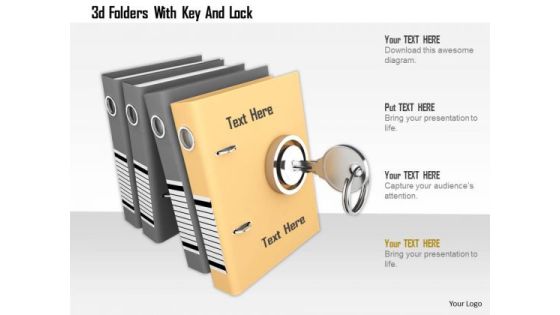
Stock Photo 3d Folders With Key And Lock PowerPoint Slide
Concept of data security has been displayed in this power point image template with suitable graphics. This image contains the graphics of 3d folders and key with lock. Use this PPT image for your data related presentations.

Business Diagram Ying Yang Style Traffic Lights Presentation Template
This power point template diagram has been designed with graphic of three ying and yong icons. This PPT diagram contains the concept of balance in energy. Use this PPT for technology and security related presentations.

Colorful House Model With Six Boxes And Icons Powerpoint Template
This PPT slide displays diagram of colorful house chart with bunch of keys. This has been designed to exhibit house safety and security. You can present your opinions using this impressive slide
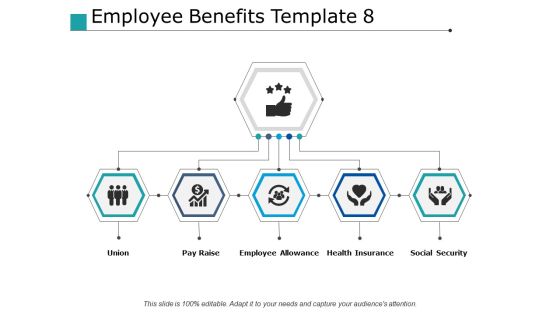
Employee Benefits Union Ppt PowerPoint Presentation Pictures Example File
This is a employee benefits union ppt powerpoint presentation pictures example file. This is a five stage process. The stages in this process are union, pay raise, employee allowance, health insurance, social security.

Table Of Contents Mitigating Cybersecurity Threats And Vulnerabilities Portrait PDF
Presenting table of contents mitigating cybersecurity threats and vulnerabilities portrait pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, secure digital assets, physical security, natural calamity threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
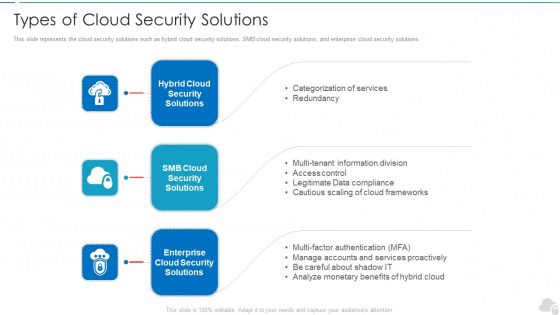
Types Of Cloud Security Solutions Cloud Computing Security IT Ppt Layouts Example PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. This is a types of cloud security solutions cloud computing security it ppt layouts example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hybrid cloud security solutions, smb cloud security solutions, enterprise cloud security solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
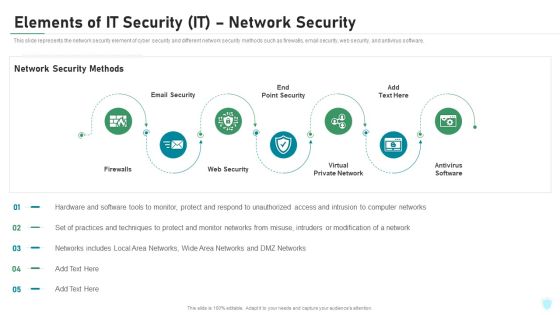
Elements Of IT Security IT Network Security Ppt Pictures Ideas PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a elements of it security it network security ppt pictures ideas pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like firewalls, email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Security Incident Handling Cyber Security Governance Ppt Gallery Summary PDF
Presenting this set of slides with name computer security incident handling cyber security governance ppt gallery summary pdf. The topics discussed in these slides are senior management, business strategy, security objectives, implementation, security requirements, risk management or information security strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF
Showcasing this set of slides titled Spending On Security Software Against Cyber Security Attack Ppt Icon Show PDF. The topics addressed in these templates are Endpoint Security, Network Security, Messaging Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Methods To Develop Current Market Trends That Are Increasing Importance Of Security Portrait PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a methods to develop current market trends that are increasing importance of security portrait pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization sensitive data, general data protection laws, outsourcing, on sourcing, and subcontracting, data breach notification laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Create an editable Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
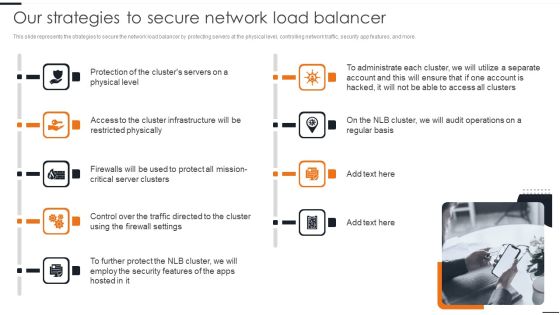
Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF
This slide represents the strategies to secure the network load balancer by protecting servers at the physical level, controlling network traffic, security app features, and more. This modern and well arranged Elastic NLB Our Strategies To Secure Network Load Balancer Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF
The following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. This Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Weakest Link Security PowerPoint Template 0510
weakest link in the chain on a white background

Sold Personal Data Security PowerPoint Template 0910
3d illustration of a red Sold sticker with curled ends stuck to a large orange fingerprint on a red surface

Weak Link Chain Security PowerPoint Template 0910
red man breaks the chain on white background

Digital Files Security PowerPoint Template 1110
3d illustration of transparent binary and html data revolving around an open file folder

Binary Internet Security PowerPoint Template 1110
Graphic depicting binary data escaping through a keyhole

Identity Theft Security PowerPoint Template 1110
Hand punching through the image grabbing documents

Data Is Secure Internet PowerPoint Template 1110
3d illustration of a lock sitting in front of a computer display showing a file folder

Laptop Security PowerPoint Backgrounds And Templates 1210
Microsoft PowerPoint Template and Background with rendered illustration of a laptop with chains and lock around screen

Flag American Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with flag american with gun creative actual for designer

Flag American Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with flag american with gun creative actual for designer

Flag American Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with flag american with gun creative actual for designer

Flag American Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with flag american with gun creative actual for designer

Flag American Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with flag american with gun creative actual for designer

IT Security Ppt PowerPoint Presentation Complete Deck
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the eighty one slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Architecture Of Cloud Security Authorization Cloud Computing Security IT Ppt Model Sample PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative architecture of cloud security authorization cloud computing security it ppt model sample pdf bundle. Topics like monitoring, security, authorization, services, data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Architecture Of Cloud Security Ppt Outline Graphics Design PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system. Deliver an awe inspiring pitch with this creative Cloud Information Security Architecture Of Cloud Security Ppt Outline Graphics Design PDF bundle. Topics like Providers Responsibility, Application Security, Data Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Officer Service Company Profile Commercial And Residential Building Security Services Clipart PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Commercial And Residential Building Security Services Clipart PDF bundle. Topics like Commercial Building Security, Residential Building Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Agency Business Profile Corporate And Industrial Security Services Information PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Corporate And Industrial Security Services Information PDF. Use them to share invaluable insights on Corporate Security, Industrial Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF bundle. Topics like Corporate Security, Industrial Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
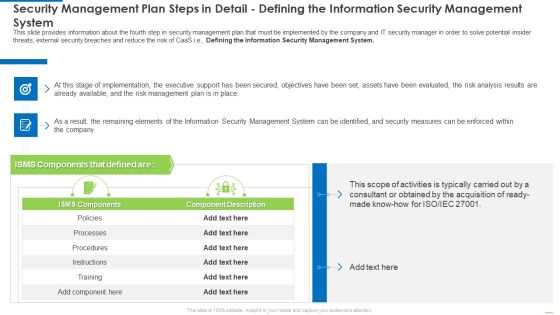
Security Management Plan Steps In Detail Defining The Information Security Management System Diagrams PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system diagrams pdf bundle. Topics like security management plan steps in detail - defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Defining The Information Security Management System Sample PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver an awe inspiring pitch with this creative security management plan steps in detail defining the information security management system sample pdf bundle. Topics like security management plan steps in detail defining the information security management system can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Growth Guidelines PDF
This slide portrays information regarding the dashboard that firm will track various security incidents detected. These incidents will be managed in order to avoid security risks. Deliver and pitch your topic in the best possible manner with this developing firm security strategy plan security incidents tracking dashboard growth guidelines pdf. Use them to share invaluable insights on number of open security incidents, open security incidents by age, average age of open security incidents, security incident backlog growth and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Defining The Information Security Management System Mockup PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Defining the Information Security Management System. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail defining the information security management system mockup pdf. Use them to share invaluable insights on implementation, management plan, security management, security measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Techniques And Strategies To Reduce Security Management Risks Estimated Security Management Plan Information PDF
This slide shows some of the estimated future IT Security Management Critical Success Factors of the company prior to the proactive measures taken by the company to mitigate security management problems and implementing an advanced Information Security Management System.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks estimated security management plan information pdf Use them to share invaluable insights on security incidents level, security implementation, overall security management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. This is a Cloud Information Security Essential Pillars Of Cloud Security Ppt File Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security, Identity Security, Visibility Consistency. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
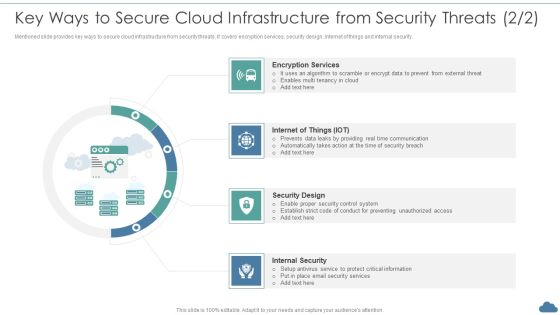
Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF
Mentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.This is a Cloud Optimization Infrastructure Model Key Ways To Secure Cloud Infrastructure From Security Threats Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Encryption Services, Security Design, Internal Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.This is a Cloud Security Assessment How Does Cloud Security Work Governance Sample PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Physical Security, Internet Security, Endpoint Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF
This slide highlights the security company services for retail outlets, mall and shopping complex and theatre security which includes the key role and responsibility of security guard. This is a Security Officer Service Company Profile Retail And Shopping Complex Security Services Summary PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Retail Security, Shopping Complex Security, Theatre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Retail And Shopping Complex Security Services Icons PDF
This slide highlights the security company services for retail outlets, mall and shopping complex and theatre security which includes the key role and responsibility of security guard. Presenting Manpower Corporate Security Business Profile Retail And Shopping Complex Security Services Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Retail Security, Shopping Complex Security, Theatre Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF
This slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. This is a IT Security Automation Tools Integration Enterprise Network IT Security Automation Download PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Orchestrating Network Security, Integrating Network, Security Policy Automation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Sample Of Sales Flow Chart Ppt Powerpoint Slide Download
This is a sample of sales flow chart ppt powerpoint slide download. This is a eight stage process. The stages in this process are select product, decide on suggested product, review and confirm shopping car, confirm address information, print license, specify inventory fulfillment method, submit payment, answer survey questions.

Lock And Us Dollar And Key Finance PowerPoint Templates And PowerPoint Themes 1012
Lock And US Dollar And Key Finance PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint Template shows the Dollar Bills along with the lock signifying its security. This PowerPoint Template signifies the concept of Finance, Profit, Loss, money, economics, business, investment, backing, sponsorship, funding etc. Colors generate instant reactions in our brains. Use them to your advantage to prioritize your ideas.-Lock And US Dollar And Key Finance PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Money, Lock And Key, Money, Finance, Security, Success, Symbol

Cyber Terrorism Assault How To Prevent Ddos Attacks In The Company Inspiration PDF
This slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc.Presenting cyber terrorism assault how to prevent ddos attacks in the company inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like service providers bandwidth capacity, network monitoring, update security components In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
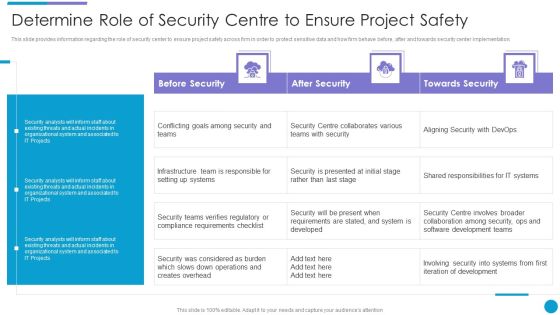
Major Techniques For Project Safety IT Determine Role Of Security Centre To Ensure Project Safety Download PDF
This slide provides information regarding the role of security center to ensure project safety across firm in order to protect sensitive data and how firm behave before, after and towards security center implementation. Deliver an awe inspiring pitch with this creative major techniques for project safety it determine role of security centre to ensure project safety download pdf bundle. Topics like before security, after security, towards security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home