Authentication

Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Slidegeeks is here to make your presentations a breeze with Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
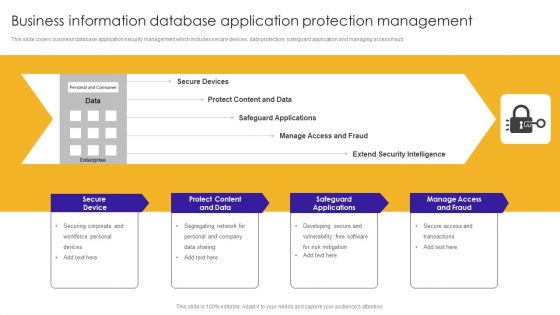
Business Information Database Application Protection Management Ideas PDF
This slide covers business database application security management which includes secure devices, data protection, safeguard application and managing access fraud.Showcasing this set of slides titled Business Information Database Application Protection Management Ideas PDF. The topics addressed in these templates are Safeguard Applications, Protect Content, Manage Access Fraud. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Develop Corporate Cyber Security Risk Mitigation Plan Timeline For Organization Protection Proposal Themes PDF
This is a develop corporate cyber security risk mitigation plan timeline for organization protection proposal themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2019 to 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
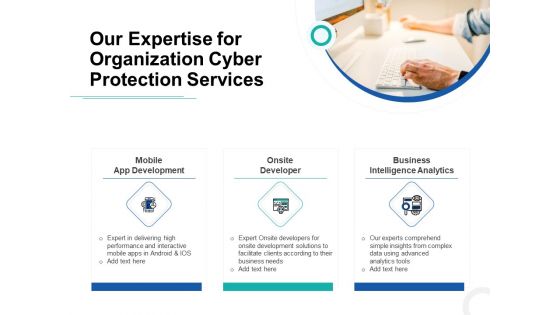
Develop Corporate Cyber Security Risk Mitigation Plan Our Expertise For Organization Cyber Protection Services Background PDF
Presenting develop corporate cyber security risk mitigation plan our expertise for organization cyber protection services background pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like mobile app development, onsite developer, business intelligence analytic. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
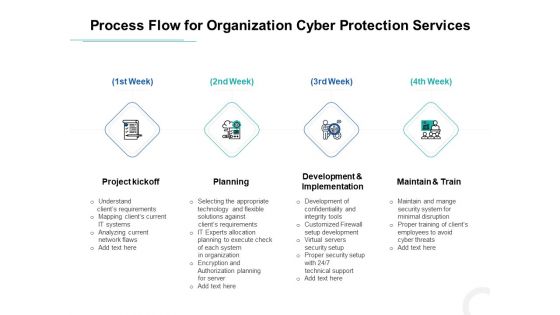
Develop Corporate Cyber Security Risk Mitigation Plan Process Flow For Organization Cyber Protection Services Background PDF
This is a develop corporate cyber security risk mitigation plan process flow for organization cyber protection services background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, maintain and train. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Develop Corporate Cyber Security Risk Mitigation Plan Timeframe For Organization Cyber Protection Services Structure PDF
This is a develop corporate cyber security risk mitigation plan timeframe for organization cyber protection services structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, results. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
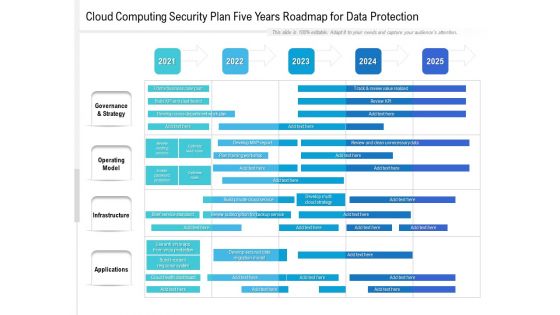
Cloud Computing Security Plan Five Years Roadmap For Data Protection Template
Introducing our cloud computing security plan five years roadmap for data protection template. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
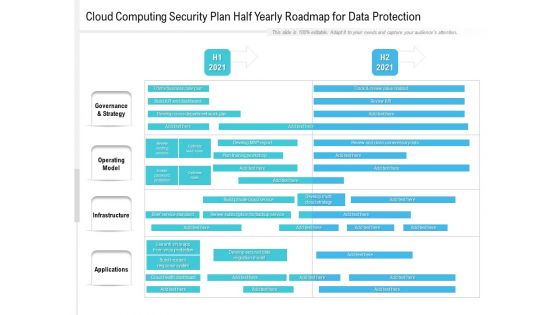
Cloud Computing Security Plan Half Yearly Roadmap For Data Protection Formats
Presenting our innovatively structured cloud computing security plan half yearly roadmap for data protection formats Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Desktop Security Management Cyber Safety Tips Protection Against Cyberattacks Download PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting desktop security management cyber safety tips protection against cyberattacks download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like systems, network, sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security IT Safety Tips Protection Against IT Attacks Ppt Layouts Outfit PDF
This slide represents various tips or procedures that can be followed to prevent an organizations network security from cyberattacks or networkcriminals. This is a information technology security it safety tips protection against it attacks ppt layouts outfit pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network, antivirus, systems, sources, unsecured. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Verification Phases Of V Model Phases Of Software Development Procedure Brochure PDF
This slide illustrates the verification phases of the V-model, including business requirement analysis, system design, architectural design, module design, and coding phase.Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Verification Phases Of V Model Phases Of Software Development Procedure Brochure PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Verification Phases Of V Model Phases Of Software Development Procedure Brochure PDF.
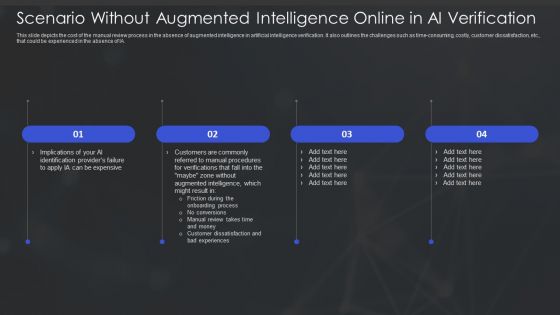
Augmented Intelligence Tools And Applications IT Scenario Without Augmented Intelligence Online In AI Verification Icons PDF
This slide depicts the cost of the manual review process in the absence of augmented intelligence in artificial intelligence verification. It also outlines the challenges such as time-consuming, costly, customer dissatisfaction, etc., that could be experienced in the absence of IA. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Augmented Intelligence Tools And Applications IT Scenario Without Augmented Intelligence Online In AI Verification Icons PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Augmented Intelligence Tools And Applications IT Scenario Without Augmented Intelligence Online In AI Verification Icons PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Data Center Relocation Process Step 9 Post Relocation Verification Inspiration PDF
This slide shows the eighth step that is involved in data center relocation process which is to be implemented for minimizing data center costs and improving scalability i.e. post-relocation verification. Find highly impressive Data Center Relocation Process Step 9 Post Relocation Verification Inspiration PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Data Center Relocation Process Step 9 Post Relocation Verification Inspiration PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
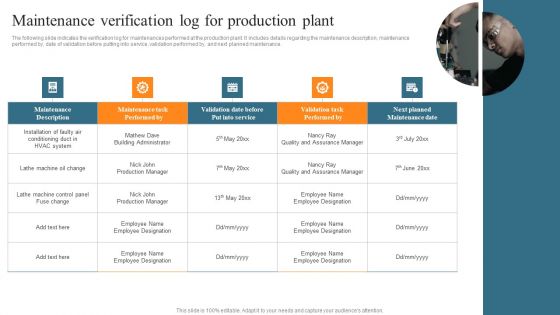
Leveraging Predictive Maintenance To Enhance Production Process Maintenance Verification Log For Production Plant Background PDF
The following slide indicates the verification log for maintenances performed at the production plant. It includes details regarding the maintenance description, maintenance performed by, date of validation before putting into service, validation performed by, and next planned maintenance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Leveraging Predictive Maintenance To Enhance Production Process Maintenance Verification Log For Production Plant Background PDF can be your best option for delivering a presentation. Represent everything in detail using Leveraging Predictive Maintenance To Enhance Production Process Maintenance Verification Log For Production Plant Background PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Intelligence Amplification IA IT Scenario Without Augmented Intelligence Online In AI Verification Mockup PDF
This slide depicts the cost of the manual review process in the absence of augmented intelligence in artificial intelligence verification. It also outlines the challenges such as time-consuming, costly, customer dissatisfaction, etc., that could be experienced in the absence of IA. Find highly impressive Intelligence Amplification IA IT Scenario Without Augmented Intelligence Online In AI Verification Mockup PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Intelligence Amplification IA IT Scenario Without Augmented Intelligence Online In AI Verification Mockup PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
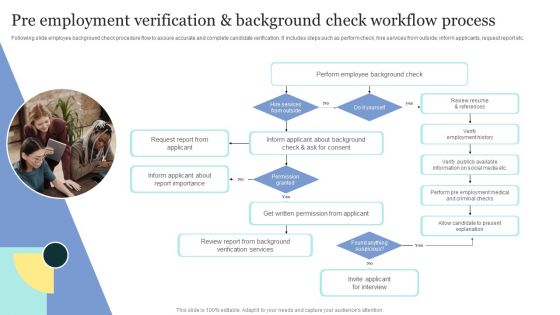
Strategic Approaches To Efficient Candidate Selection Pre Employment Verification And Background Check Slides PDF
Following slide employee background check procedure flow to assure accurate and complete candidate verification. It includes steps such as perform check, hire services from outside, inform applicants, request report etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Strategic Approaches To Efficient Candidate Selection Pre Employment Verification And Background Check Slides PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Strategic Approaches To Efficient Candidate Selection Pre Employment Verification And Background Check Slides PDF.

Data Encryption Method In Application Security Testing Ppt Powerpoint Formats
This slide discusses the introduction of encryption in application security for protection of specific fields in an application. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Data Encryption Method In Application Security Testing Ppt Powerpoint Formats to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
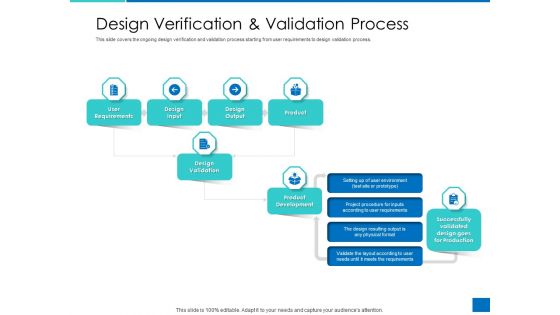
Analyzing Requirement Management Process Design Verification And Validation Process Inspiration PDF
This slide covers the ongoing design verification and validation process starting from user requirements to design validation process. This is a analyzing requirement management process design verification and validation process inspiration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, design, validation, requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Candidate Document Verification Hiring And Induction System Ppt PowerPoint Presentation Pictures File Formats PDF
Persuade your audience using this candidate document verification hiring and induction system ppt powerpoint presentation pictures file formats pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including core hr, department hr, hiring manager, identify appropriate candidate, conducts reference check, makes offer and candidate accepts, enter hired employees documents, verified documentation, verification character, provides clearance to department hr, employees onboarding in organization, requests clearance, request background check to hiring manager. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Scenario Without Augmented Intelligence Online In AI Verification Ppt PowerPoint Presentation File Infographics PDF
This slide depicts the cost of the manual review process in the absence of augmented intelligence in artificial intelligence verification. It also outlines the challenges such as time-consuming, costly, customer dissatisfaction, etc. that could be experienced in the absence of IA. Make sure to capture your audiences attention in your business displays with our gratis customizable Scenario Without Augmented Intelligence Online In AI Verification Ppt PowerPoint Presentation File Infographics PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Data Center Relocation Process Step 9 Post Relocation Verification Microsoft PDF
This slide shows the eighth step that is involved in data center relocation process which is to be implemented for minimizing data center costs and improving scalability i.e. post relocation verification. Find a pre designed and impeccable Data Center Relocation Process Step 9 Post Relocation Verification Microsoft PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
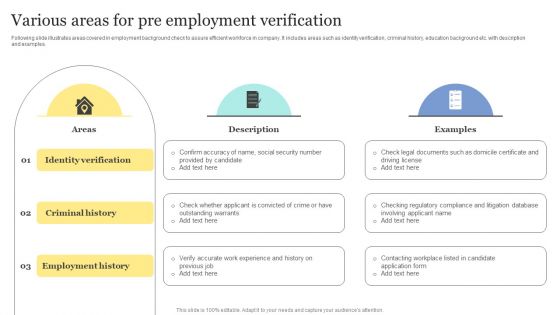
Strategic Approaches To Efficient Candidate Selection Various Areas For Pre Employment Verification Information PDF
Following slide illustrates areas covered in employment background check to assure efficient workforce in company. It includes areas such as identity verification, criminal history, education background etc. with description and examples. There are so many reasons you need a Strategic Approaches To Efficient Candidate Selection Various Areas For Pre Employment Verification Information PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Protection And Privacy Issues In Cloud Technology Rules PDF
The following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Persuade your audience using this Protection And Privacy Issues In Cloud Technology Rules PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Absence Of Control, Saas Security, Security Model. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Stock Photo Global Environmental Protection PowerPoint Template
Rake In The Dough With Your Ideas. Profits Will Rise With Our Stock Photo Global Environmental Protection PowerPoint Template Powerpoint Templates. Dowse The Flames With Our globe Powerpoint Templates. Put Out The Fire Before It Starts.
Nature Balance And Protection Powerpoint Templates
The above template contains diagram of circles Infographic. This diagram slide may be used to display nature, balance and protection concepts. Earn appreciation with our slide and your listeners will surely laud your performance.

Arrows Around Globe For Protection Powerpoint Templates
This PowerPoint template has been designed with graphic of arrow around globe. This business slide contains the concept of global protection. You may use this slide for education and business related presentations.

Protection Management Example Powerpoint Slide Background Image
This is a protection management example powerpoint slide background image. This is a eight stage process. The stages in this process are continuous optimization, policies, procedures, strategy formulation, strategy equation, performance analysis, awareness, software.

Online App Protection System Powerpoint Slide Deck
This is a online app protection system powerpoint slide deck. This is a five stage process. The stages in this process are web browser, veracode discovery, external code, uncover and retire, inventory.
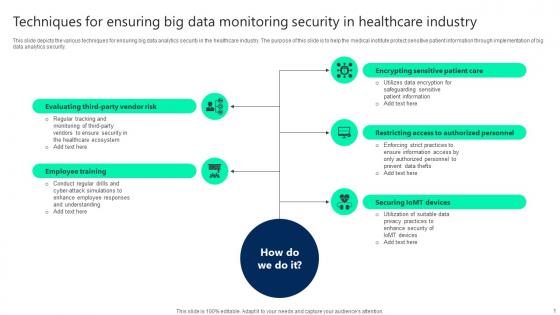
Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf
This slide depicts the various techniques for ensuring big data analytics security in the healthcare industry. The purpose of this slide is to help the medical institute protect sensitive patient information through implementation of big data analytics security. Pitch your topic with ease and precision using this Techniques For Ensuring Big Data Monitoring Security In Healthcare Industry Infographics pdf. This layout presents information on Employee Training, Securing Iomt Devices, Restricting Access. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
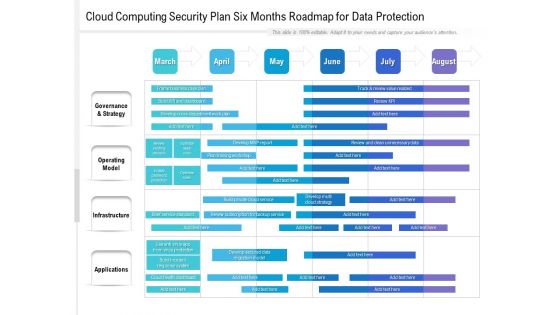
Cloud Computing Security Plan Six Months Roadmap For Data Protection Themes
Presenting our jaw dropping cloud computing security plan six months roadmap for data protection themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Cloud Computing Security Plan Three Months Roadmap For Data Protection Structure
Presenting the cloud computing security plan three months roadmap for data protection structure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
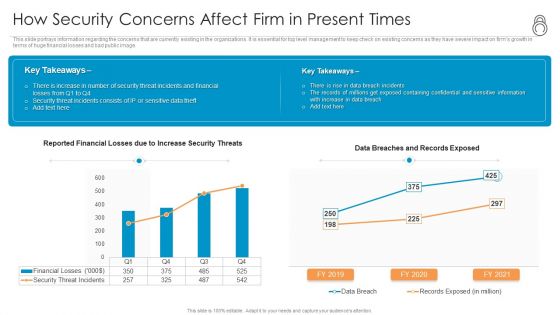
Enhanced Protection Corporate Event Administration How Security Concerns Affect Firm In Present Times Inspiration PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration how security concerns affect firm in present times inspiration pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
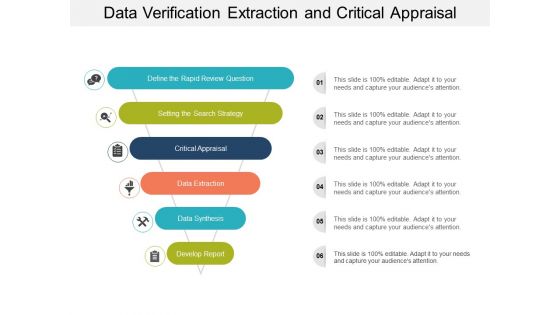
Data Verification Extraction And Critical Appraisal Ppt PowerPoint Presentation Show Inspiration
Presenting this set of slides with name data verification extraction and critical appraisal ppt powerpoint presentation show inspiration. This is a six stage process. The stages in this process are Data analysis, Data Review, Data Evaluation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

All About HRM Employee Verification Process Ppt Summary Background Images PDF
Presenting this set of slides with name all about hrm employee verification process ppt summary background images pdf. The topics discussed in these slides are technical capacity, emotional intelligent, soft skills, physical fitness, professional qualifications. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Process Verification With Plan And Design Ppt PowerPoint Presentation Gallery Inspiration PDF
Presenting this set of slides with name business process verification with plan and design ppt powerpoint presentation gallery inspiration pdf. This is a nine stage process. The stages in this process are innovate, process, execute, plan, design, validate. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Software Testing Process With Requirement And System Verification Ppt PowerPoint Presentation Icon Slides PDF
Presenting this set of slides with name software testing process with requirement and system verification ppt powerpoint presentation icon slides pdf. This is a two stage process. The stages in this process are requirements, design, development. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Software Testing With Coding And Verification Ppt PowerPoint Presentation File Shapes PDF
Presenting this set of slides with name software testing with coding and verification ppt powerpoint presentation file shapes pdf. This is a two stage process. The stages in this process are integration, acceptance, design. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Change Workflow Diagram With Implementation And Verification Ppt PowerPoint Presentation File Example PDF
Presenting this set of slides with name change workflow diagram with implementation and verification ppt powerpoint presentation file example pdf. This is a eight stage process. The stages in this process are communicate, analysis, implementation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Asset Data Verification Workflow Chart Ppt PowerPoint Presentation Icon Files PDF
Presenting asset data verification workflow chart ppt powerpoint presentation icon files pdf to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including database, inventory, data approved. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
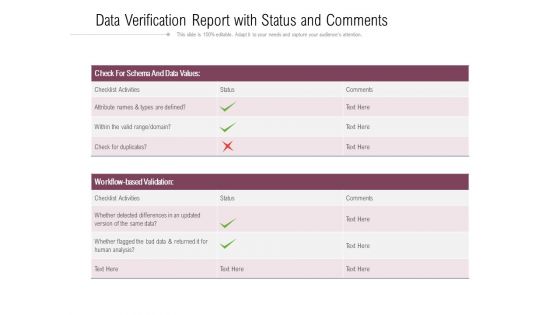
Data Verification Report With Status And Comments Ppt PowerPoint Presentation Gallery Designs Download PDF
Pitch your topic with ease and precision using this data verification report with status and comments ppt powerpoint presentation gallery designs download pdf. This layout presents information on data values, validation, analysis. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
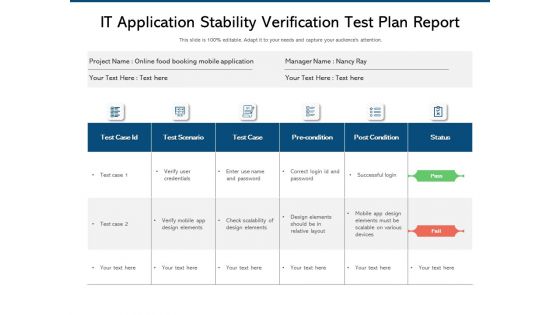
IT Application Stability Verification Test Plan Report Ppt PowerPoint Presentation File Background Image PDF
Showcasing this set of slides titled it application stability verification test plan report ppt powerpoint presentation file background image pdf. The topics addressed in these templates are scenario, design elements, scalability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

6 Stages Product Testing And Verification System Ppt PowerPoint Presentation Slides Model PDF
Presenting 6 stages product testing and verification system ppt powerpoint presentation slides model pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including concept generation, proof of concept, product design process development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
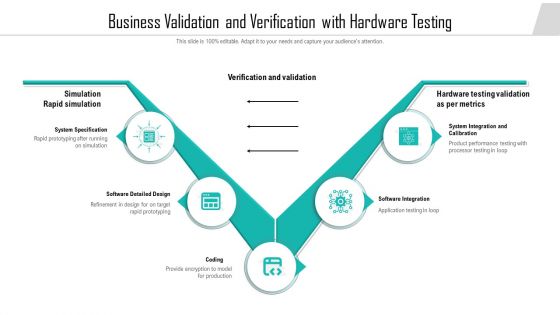
Business Validation And Verification With Hardware Testing Ppt PowerPoint Presentation File Visuals PDF
Showcasing this set of slides titled business validation and verification with hardware testing ppt powerpoint presentation file visuals pdf. The topics addressed in these templates are system integration and calibration, system specification, software detailed design. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
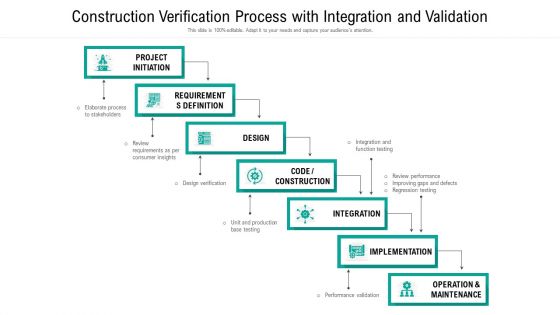
Construction Verification Process With Integration And Validation Ppt PowerPoint Presentation Gallery Templates PDF
Presenting construction verification process with integration and validation ppt powerpoint presentation gallery templates pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including project initiation, implementation, operation maintenance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Product Validation And Verification Workflow With Specifications Ppt PowerPoint Presentation Infographics Professional PDF
Presenting product validation and verification workflow with specifications ppt powerpoint presentation infographics professional pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including validation process, development, product. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Design Validation And Verification Process Ppt PowerPoint Presentation Styles Show PDF
Showcasing this set of slides titled data design validation and verification process ppt powerpoint presentation styles show pdf. The topics addressed in these templates are design process, correctness and completeness review, validation summary report. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Requirements Traceability Chart With Verification And Validation Ppt Model Graphic Images PDF
Showcasing this set of slides titled requirements traceability chart with verification and validation ppt model graphic images pdf. The topics addressed in these templates are requirement information, relationship traceability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Icons Slide For Solution Monitoring And Verification Process Meet Company Mockup PDF
Download our innovative and attention grabbing icons slide for solution monitoring and verification process meet company mockup pdf template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.
PMP Acceptability Benchmarks IT Project Experience Tracking For PMP Eligibility Verification Formats PDF
Deliver and pitch your topic in the best possible manner with this pmp acceptability benchmarks it project experience tracking for pmp eligibility verification formats pdf. Use them to share invaluable insights on requirement, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
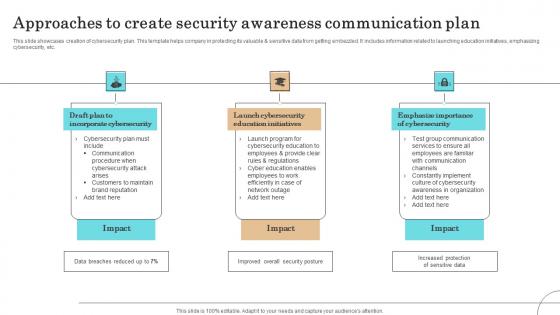
Approaches To Create Security Awareness Communication Plan Professional Pdf
This slide showcases creation of cybersecurity plan. This template helps company in protecting its valuable sensitive data from getting embezzled. It includes information related to launching education initiatives, emphasizing cybersecurity, etc.Showcasing this set of slides titled Approaches To Create Security Awareness Communication Plan Professional Pdf The topics addressed in these templates are Incorporate Cybersecurity, Launch Cybersecurity, Education Initiatives All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
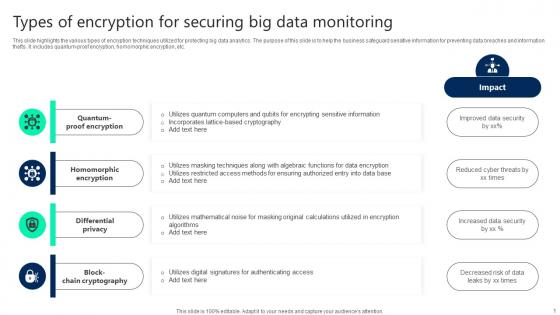
Types Of Encryption For Securing Big Data Monitoring Topics pdf
This slide highlights the various types of encryption techniques utilized for protecting big data analytics. The purpose of this slide is to help the business safeguard sensitive information for preventing data breaches and information thefts. It includes quantum-proof encryption, homomorphic encryption, etc. Showcasing this set of slides titled Types Of Encryption For Securing Big Data Monitoring Topics pdf. The topics addressed in these templates are Quantum Proof Encryption, Homomorphic Encryption, Differential Privacy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Breach Prevention Software KPI Dashboard Information Pdf
This templates shows the KPI dashboard for malware attack prevention software. The purpose of this slide to evaluate the software prevention on different parameters. It includes KPI such as device problems, daily safety check, web protection check, antiviruses installs , etc. Showcasing this set of slides titled Cyber Security Breach Prevention Software KPI Dashboard Information Pdf The topics addressed in these templates are Electronic Devices, Device Problems, Daily Safety Check All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
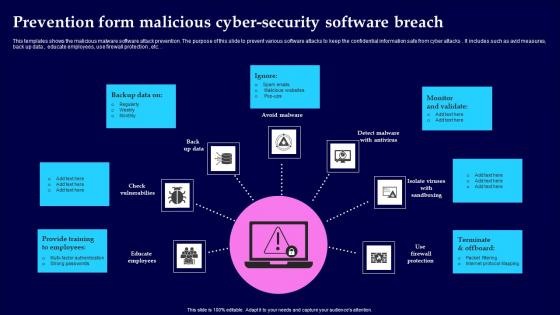
Prevention Form Malicious Cyber Security Software Breach Portrait Pdf
This templates shows the malicious malware software attack prevention. The purpose of this slide to prevent various software attacks to keep the confidential information safe from cyber attacks. It includes such as avid measures, back up data , educate employees, use firewall protection , etc. Showcasing this set of slides titled Prevention Form Malicious Cyber Security Software Breach Portrait Pdf The topics addressed in these templates are Provide Training, Monitor And Validate, Terminate And Offboard All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Security Defense Maturity Evaluation Strategy Information Pdf
This slide showcase integrated strategy to protect and defend enterprise from cybersecurity threat with multiple level of maturity model evaluation. It includes culture and organization, governance, visibility and control, focused defense and intelligence operations.Pitch your topic with ease and precision using this Internet Security Defense Maturity Evaluation Strategy Information Pdf This layout presents information on Visibility Controls, Focused Defense, Intelligence Operations It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Enhanced Protection Corporate Event Administration Determine Focus Areas To Implement Security Operations Centre Icons PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a enhanced protection corporate event administration determine focus areas to implement security operations centre icons pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Plan To Enhance Manufacturing Maintenance Verification Log For Production Plant Brochure PDF
The following slide indicates the verification log for maintenances performed at the production plant. It includes details regarding the maintenance description, maintenance performed by, date of validation before putting into service, validation performed by, and next planned maintenance. Boost your pitch with our creative Plan To Enhance Manufacturing Maintenance Verification Log For Production Plant Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Strategies For Effective Manufacturing Maintenance Verification Log For Production Plant Brochure PDF
The following slide indicates the verification log for maintenances performed at the production plant. It includes details regarding the maintenance description, maintenance performed by, date of validation before putting into service, validation performed by, and next planned maintenance. Boost your pitch with our creative Strategies For Effective Manufacturing Maintenance Verification Log For Production Plant Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.
Human Augmented Machine Learning IT Scenario Without Augmented Intelligence Online In AI Verification Summary PDF
This slide depicts the cost of the manual review process in the absence of augmented intelligence in artificial intelligence verification. It also outlines the challenges such as time-consuming, costly, customer dissatisfaction, etc., that could be experienced in the absence of IA. This modern and well-arranged Human Augmented Machine Learning IT Scenario Without Augmented Intelligence Online In AI Verification Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Machine Repairing And Servicing Maintenance Verification Log For Production Plant Designs PDF
The following slide indicates the verification log for maintenances performed at the production plant. It includes details regarding the maintenance description, maintenance performed by, date of validation before putting into service, validation performed by, and next planned maintenance. Present like a pro with Machine Repairing And Servicing Maintenance Verification Log For Production Plant Designs PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
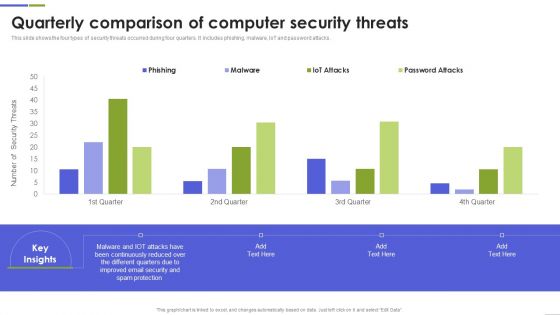
Quarterly Comparison Of Computer Security Threats Mockup PDF
This slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Pitch your topic with ease and precision using this Quarterly Comparison Of Computer Security Threats Mockup PDF This layout presents information on Continuously Reduced, Different Quarters, Spam Protection It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
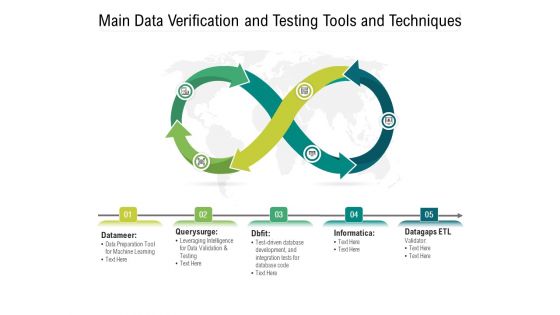
Main Data Verification And Testing Tools And Techniques Ppt PowerPoint Presentation Gallery Design Ideas PDF
Persuade your audience using this main data verification and testing tools and techniques ppt powerpoint presentation gallery design ideas pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including data validation, development, integration. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Home Loan Approval Process With Document Verification Ppt PowerPoint Presentation Icon Professional PDF
Presenting home loan approval process with document verification ppt powerpoint presentation icon professional pdf to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including bank rates, tag additional documents, final loan approval, loan disbursement and close, apply for home loan, document scanning, and loan approval, issue loan documents. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
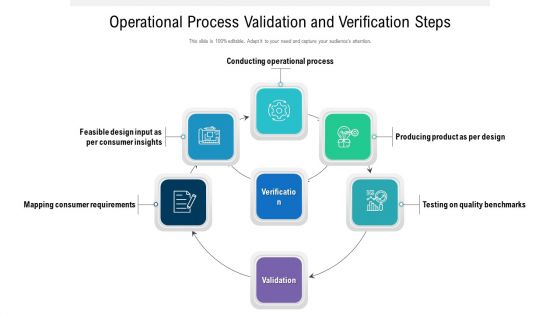
Operational Process Validation And Verification Steps Ppt PowerPoint Presentation Pictures Gridlines PDF
Persuade your audience using this operational process validation and verification steps ppt powerpoint presentation pictures gridlines pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including conducting operational process, mapping consumer requirements, producing product as per design. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

8 Essential Stages Of Purchase Order With Invoice Verification Ppt PowerPoint Presentation Professional Example Introduction PDF
Presenting 8 essential stages of purchase order with invoice verification ppt powerpoint presentation professional example introduction pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including payment processing, purchase order processing, manufacturing appropriate quantity to fulfil sales order. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda For Solution Monitoring And Verification Process To Meet Company Diagrams PDF
This is a agenda for solution monitoring and verification process to meet company diagrams pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like objectives, determine, assessment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solution Monitoring Verification Assess Organizational Readiness Force Field Analysis Slides PDF
This slide explains the various elements of force field analysis framework such as proposed change, pushing forces, forces resisting change etc.. along with the benefits of force field analysis tool Deliver and pitch your topic in the best possible manner with this solution monitoring verification assess organizational readiness force field analysis slides pdf Use them to share invaluable insights on capabilities, control, eliminates and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Solution Monitoring Verification Business Analysis Body Of Knowledge BABOK Download PDF
This slide shows the framework that illustrates the business analysis tasks that need to be performed in order to understand and evaluate that how the desired solution will deliver value to the company. Deliver an awe inspiring pitch with this creative solution monitoring verification business analysis body of knowledge babok download pdf bundle. Topics like performed, value, analysis, tasks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
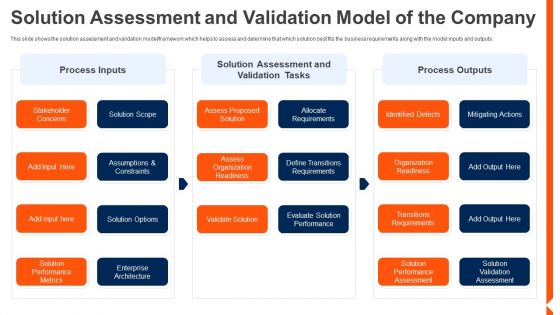
Solution Monitoring Verification Solution Assessment And Validation Model Company Elements PDF
This slide shows the solution assessment and validation model framework which helps to assess and determine that which solution best fits the business requirements along with the model inputs and outputs. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation model company elements pdf bundle. Topics like process inputs, assessment, validation tasks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Solution Monitoring Verification Solution Assessment And Validation Task Define Pictures PDF
This slide shows the various assess proposed solutions options that are available with the organization and can be used to solve business problems and find out proper solution. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation task define pictures pdf bundle. Topics like recommendations, business, requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured Hotel Protection And Security Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.
Business Framework Risk Protection Factors PowerPoint Presentation
A white tube with blue wire has been used to decorate this Power point diagram template slide. This PPT slide contains the concept of risk protection in any field. This PPT slide can be used for business risk related topics. Build an exclusive presentation for your business presentation.
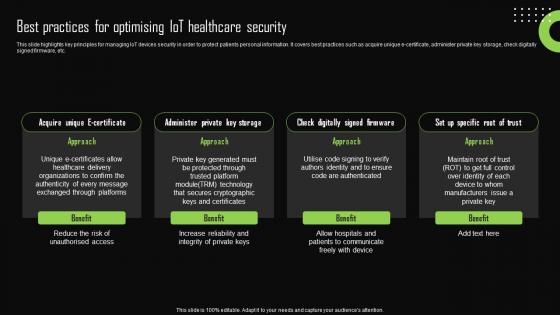
Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf
This slide highlights key principles for managing IoT devices security in order to protect patients personal information. It covers best practices such as acquire unique e-certificate, administer private key storage, check digitally signed firmware, etc. There are so many reasons you need a Best Practices For Optimising Iot Healthcare Security Iot Device Management Professional Pdf. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Visionary Guide To Blockchain Securing Voting Systems With Blockchain BCT SS V will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Reactive And Proactive Business Information Protection Evaluation Process Sample PDF
This slide covers reactive and proactive business security evaluation process which includes evaluating security based on set standards. Persuade your audience using this Reactive And Proactive Business Information Protection Evaluation Process Sample PDF. This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including Conventional Reactive, Proactive Security, Evaluation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Approaches To Improve Workplace Protection And Precaution Background PDF
This slide shows three strategies to increase safety and security of workplace. These are reduce manual security, reliance on technology and monitor. Persuade your audience using this Three Approaches To Improve Workplace Protection And Precaution Background PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Reduce Manual Security, Reliance On Technology, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Best Practices For Cyber Safety At Job Safety Infographics PDF
This slide covers the best practices for cyber safety at workplace which includes protecting the data, using strong password protection, connecting to the secure wi-fi, investing in security systems, etc. Presenting best practices for cyber safety at job safety infographics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including protecting data, connect to secure wi fi, invest in security systems, strong password protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Solution Monitoring Verification Description Of BABOK Areas Solution Assessment Brochure PDF
This slide shows the description of a BABOK Business Analysis Body of Knowledge area i.e. solution assessment and validation whose main purpose is to assess and determine that which solution best fits the business requirements along with elements and techniques at each stage. Presenting solution monitoring verification description of babok areas solution assessment brochure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like proposed, requirements, organizational. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
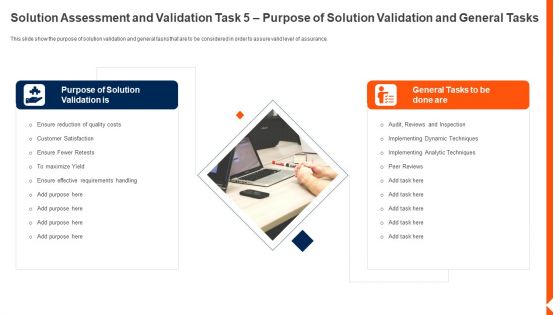
Solution Monitoring Verification Solution Assessment And Validation Validation General Background PDF
This slide show the purpose of solution validation and general tasks that are to be considered in order to assure valid level of assurance. Presenting solution monitoring verification solution assessment and validation validation general background pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like purpose, solution, requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solution Monitoring Verification Solution Assessment And Validation Task Allocate Portrait PDF
This slide shows the overview and some details of the second task in solution assessment and validation process i.e. Allocation of Requirements such as purpose of allocate requirements, process inputs and output description, elements, stakeholder details and allocation requirements model. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation task allocate portrait pdf bundle. Topics like allocate requirements, techniques, process, description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
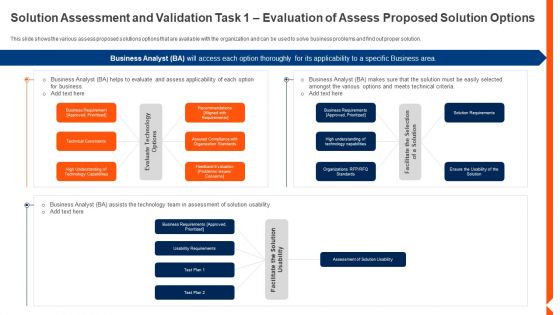
Solution Monitoring Verification Solution Assessment And Validation Task Assess Sample PDF
This slide shows the overview and some details of the first task in solution assessment and validation process i.e. Assess Proposed Solution such as purpose of assessed proposed solution, process inputs and output description, elements, stakeholder details and assess proposed solution model. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation task assess sample pdf. Use them to share invaluable insights on techniques, purpose, process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

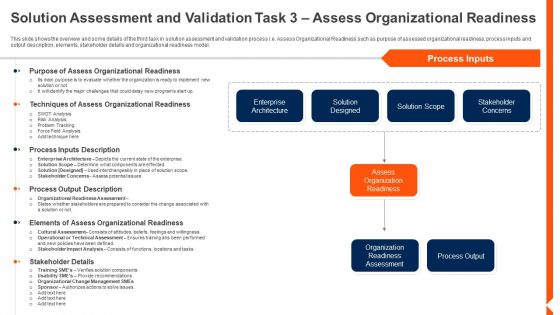
Solution Monitoring Verification Solution Assessment And Validation Task Evaluating Graphics PDF
This slide shows the overview and some details of the third task in solution assessment and validation process i.e. Assess Organizational Readiness such as purpose of assessed organizational readiness, process inputs and output description, elements, stakeholder details and organizational readiness model. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation task evaluating graphics pdf. Use them to share invaluable insights on organization, enterprise, stakeholder concerns and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Solution Monitoring Verification Solution Assessment And Validation Task Options Graphics PDF
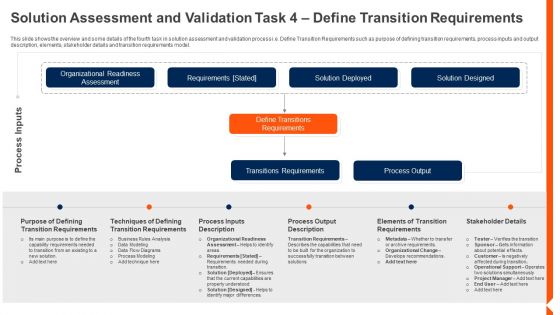
This slide shows the overview and some details of the fourth task in solution assessment and validation process i.e. Define Transition Requirements such as purpose of defining transition requirements, process inputs and output description, elements, stakeholder details and transition requirements model. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation task options graphics pdf bundle. Topics like techniques, requirements, process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Solution Monitoring Verification Solution Assessment And Validation Task Validate Solution Brochure PDF
This slide shows the overview and some details of the sixth and the last task in solution assessment and validation process i.e. Evaluating Solution Performance such as purpose of evaluating solution performance , process inputs and output description, elements, stakeholder details and evaluating solution performance model. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation task validate solution brochure pdf. Use them to share invaluable insights on performance, purpose, techniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Application Development Life Cycle Verification Phases Of V Model Inspiration PDF
This slide illustrates the verification phases of the V model, including business requirement analysis, system design, architectural design, module design, and coding phase. Presenting application development life cycle validation phases of v model introduction pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like pros of rapid application development model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
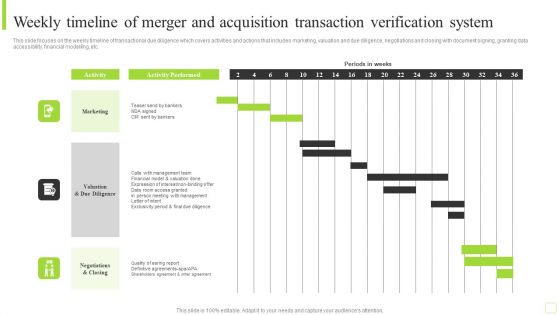
Weekly Timeline Of Merger And Acquisition Transaction Verification System Brochure PDF
This slide focuses on the weekly timeline of transactional due diligence which covers activities and actions that includes marketing, valuation and due diligence, negotiations and closing with document signing, granting data accessibility, financial modelling, etc. Pitch your topic with ease and precision using this Weekly Timeline Of Merger And Acquisition Transaction Verification System Brochure PDF. This layout presents information on Marketing, Management Team, Financial Model. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. There are so many reasons you need a Companies Paving The Path For Confidential Computing Secure Multi Party Elements Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. There are so many reasons you need a Operational And Technical Assurance Of Data Privacy Secure Multi Party Professional Pdf The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
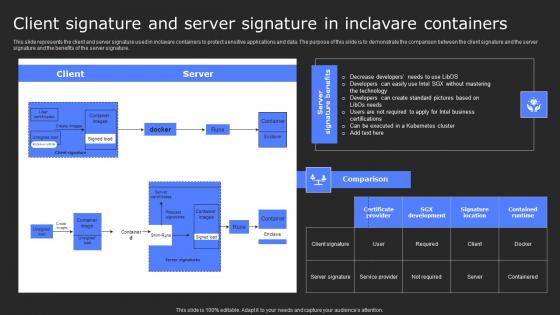
Client Signature And Server Signature In Secure Computing Framework Themes Pdf
This slide represents the client and server signature used in inclavare containers to protect sensitive applications and data. The purpose of this slide is to demonstrate the comparison between the client signature and the server signature and the benefits of the server signature. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Client Signature And Server Signature In Secure Computing Framework Themes Pdf will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Applications Of Data Masking Internet Of Things Security Technology Topics Pdf
This slide represents the various applications of data masking technology that helps to protect sensitive data by providing a functional alternative for networks. The various categories include encryption, scrambling, nulling out, substitution, shuffling, etc. Showcasing this set of slides titled Applications Of Data Masking Internet Of Things Security Technology Topics Pdf The topics addressed in these templates are Encryption, Scrambling, Substitution, Shuffling All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
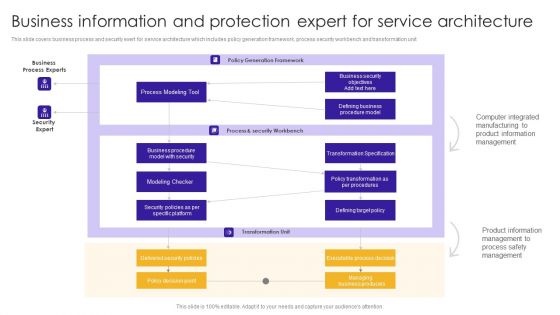
Business Information And Protection Expert For Service Architecture Demonstration PDF
This slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit.Showcasing this set of slides titled Business Information And Protection Expert For Service Architecture Demonstration PDF. The topics addressed in these templates are Business Process, Computer Integrated, Product Information. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
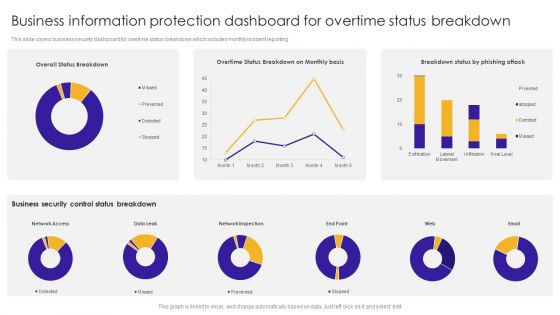
Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF
This slide covers business security dashboard for overtime status breakdown which includes monthly incident reporting.Pitch your topic with ease and precision using this Business Information Protection Dashboard For Overtime Status Breakdown Introduction PDF. This layout presents information on Business Security, Control Status Breakdown, Network Inspection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
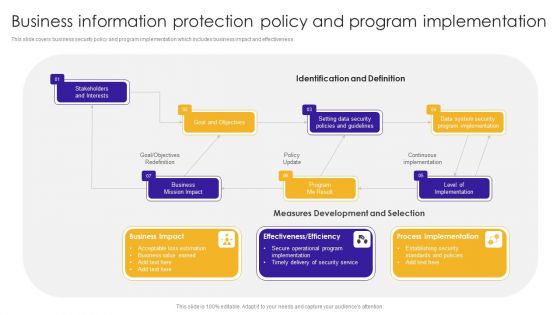
Business Information Protection Policy And Program Implementation Brochure PDF
This slide covers business security policy and program implementation which includes business impact and effectiveness.Showcasing this set of slides titled Business Information Protection Policy And Program Implementation Brochure PDF. The topics addressed in these templates are Acceptable Loss, Business Value Earned, Secure Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
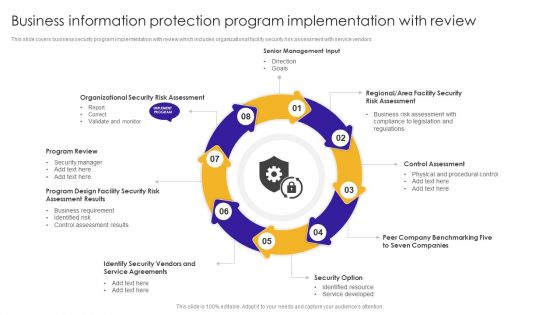
Business Information Protection Program Implementation With Review Information PDF
This slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors.Persuade your audience using this Business Information Protection Program Implementation With Review Information PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Program Review, Assessment Results, Business Requirement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
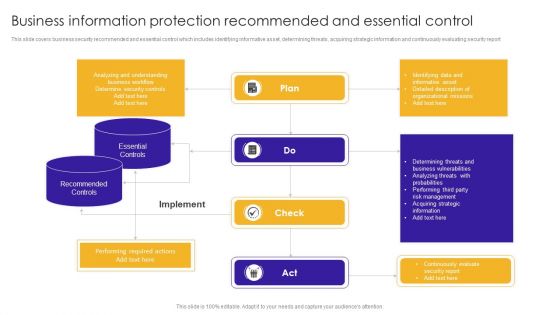
Business Information Protection Recommended And Essential Control Background PDF
This slide covers business security recommended and essential control which includes identifying informative asset, determining threats, acquiring strategic information and continuously evaluating security report. Showcasing this set of slides titled Business Information Protection Recommended And Essential Control Background PDF. The topics addressed in these templates are Determining Threats, Business Vulnerabilities, Risk Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
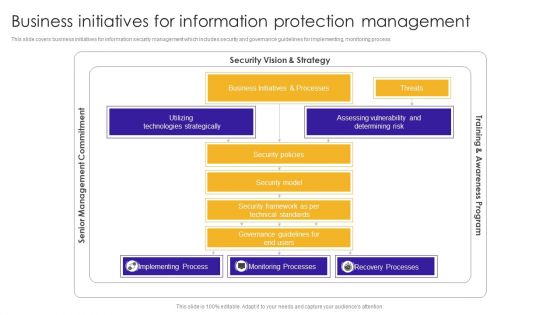
Business Initiatives For Information Protection Management Designs PDF
This slide covers business initiatives for information security management which includes security and governance guidelines for implementing, monitoring process. Pitch your topic with ease and precision using this Business Initiatives For Information Protection Management Designs PDF. This layout presents information on Technologies Strategically, Assessing Vulnerability, Implementing Process. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
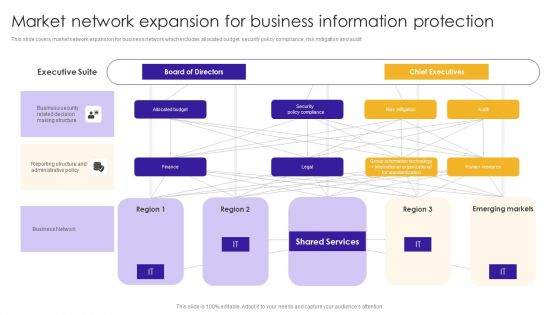
Market Network Expansion For Business Information Protection Sample PDF
This slide covers market network expansion for business network which includes allocated budget, security policy compliance, risk mitigation and audit. Showcasing this set of slides titled Market Network Expansion For Business Information Protection Sample PDF. The topics addressed in these templates are Business Security, Related Decision, Making Structure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizational Business Information Governance And Protection Structure Guidelines PDF
This slide covers organizational business governance and security structure which includes design strategy, human factor and enabled support. Showcasing this set of slides titled Organizational Business Information Governance And Protection Structure Guidelines PDF. The topics addressed in these templates are Communicate Rules, Organizational Policy, Business Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
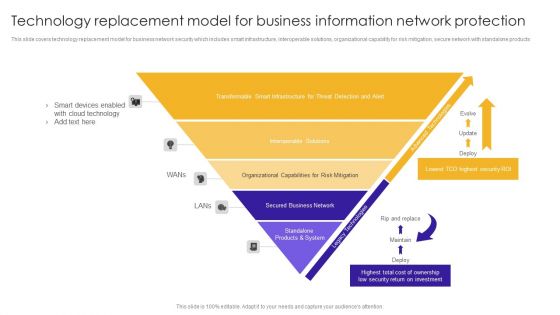
Technology Replacement Model For Business Information Network Protection Structure PDF
This slide covers technology replacement model for business network security which includes smart infrastructure, interoperable solutions, organizational capability for risk mitigation, secure network with standalone products.Showcasing this set of slides titled Technology Replacement Model For Business Information Network Protection Structure PDF. The topics addressed in these templates are Smart Devices, Cloud Technology, Transformable Smart. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Cyber Protection And Precaution Tracking Dashboard Designs PDF
This slide shows the dashboard of cyber safety and security of an organization. It includes risk level, compliance status, tracking and security budget. Showcasing this set of slides titled Cyber Protection And Precaution Tracking Dashboard Designs PDF. The topics addressed in these templates are Risk, Compliance Status, Risk Level. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Solution Monitoring Verification Role Of Business Analyst In Solution Assessment Sample PDF
This slide show the roles and responsibilities of a Business Analyst BA in the process of Solution Assessment and Validation such as developing alternative solutions, promoting the selection of a solution, evaluating the various technology options, monitoring the QA process, communicating the solution impacts to the stakeholders etc. This is a solution monitoring verification role of business analyst in solution assessment sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like develop, technology, consideration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Russian Cyber Attacks On Ukraine IT How To Protect Yourself Summary PDF
This slide talks about how to protect yourself from ongoing Russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Presenting russian cyber attacks on ukraine it how to protect yourself summary pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like resources, account, potentially. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Protection Ppt PowerPoint Presentation Complete With Slides
Improve your presentation delivery using this Protection Ppt PowerPoint Presentation Complete With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twenty three this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.
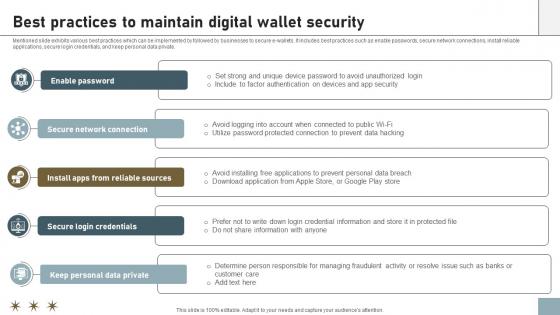
Online Payment Techniques Best Practices To Maintain Digital Wallet Security
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Online Payment Techniques Best Practices To Maintain Digital Wallet Security template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Online Payment Techniques Best Practices To Maintain Digital Wallet Security that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V
This slide presents an overview and types of encryption security threats, helpful in protecting data during transmission and storage. It includes various threats such as side channel, cryptanalysis, and man in middle attack. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Building Trust With IoT Security Overview Of Encryption Security Attacks In IoT Environment IoT SS V for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
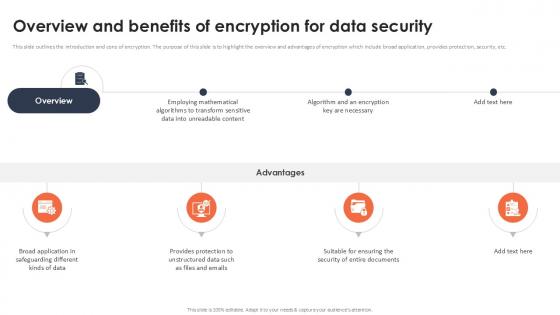
Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint
This slide outlines the introduction and cons of encryption. The purpose of this slide is to highlight the overview and advantages of encryption which include broad application, provides protection, security, etc. Retrieve professionally designed Overview And Benefits Of Encryption For Data Security Securing Your Data Ppt Powerpoint to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
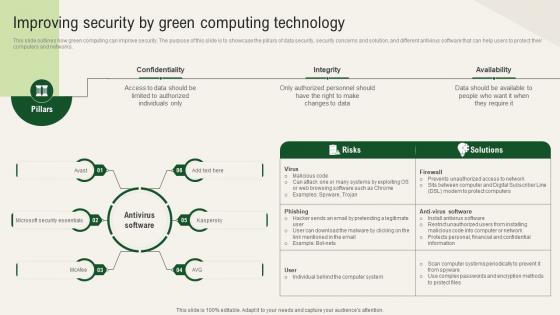
Solar Computing IT Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Are you searching for a Solar Computing IT Improving Security By Green Computing Technology that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Solar Computing IT Improving Security By Green Computing Technology from Slidegeeks today.

Information Protection Risk Management Committee Diagram Information PDF
This slide shows flow chart of cyber protection risk management team of an organization. It includes cyber protection system deployment team, data center management, network member, etc. Persuade your audience using this Information Protection Risk Management Committee Diagram Information PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security Head, Information Security Audit Scan, Network Member. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low level encryption, reliance on cloud service providers for data protection, poor key management, etc. Take your projects to the next level with our ultimate collection of Factors Responsible For Cloud Security Cloud Data Security Using Cryptography Formats Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example
The purpose of this slide is to explain the various misconceptions and mistakes of organization while integrating cryptographic solutions into cloud. These include dependence on low-level encryption, reliance on cloud service providers for data protection, poor key management, etc. The Factors Responsible For Cloud Security Data Security In Cloud Computing Ppt Example is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Organizational Design Methodologies Powerpoint Guide
This is a organizational design methodologies powerpoint guide. This is a five stage process. The stages in this process are requirements, design, implementation, verification, maintenance.
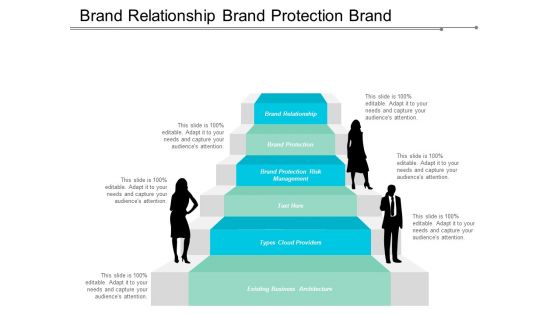
Brand Relationship Brand Protection Brand Protection Risk Management Ppt PowerPoint Presentation Ideas Layout
This is a brand relationship brand protection brand protection risk management ppt powerpoint presentation ideas layout. This is a six stage process. The stages in this process are brand relationship, brand protection, brand protection risk management.
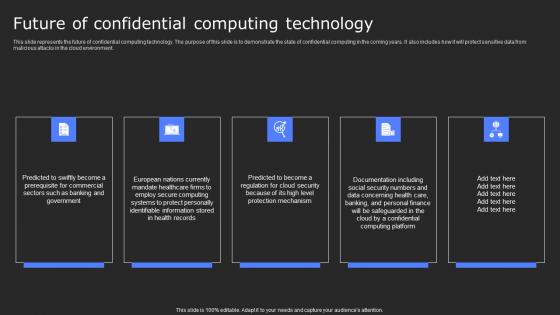
Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Presenting this PowerPoint presentation, titled Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Future Of Confidential Computing Technology Secure Computing Framework Ideas Pdf that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
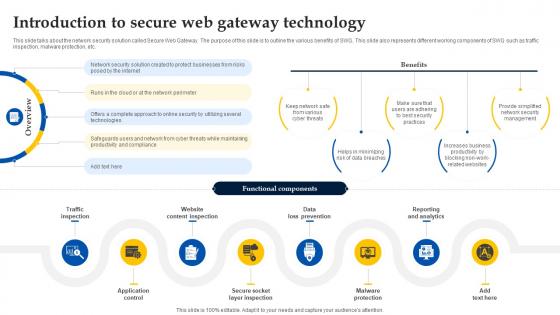
Web Access Control Solution Introduction To Secure Web Gateway Technology
This slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Retrieve professionally designed Web Access Control Solution Introduction To Secure Web Gateway Technology to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
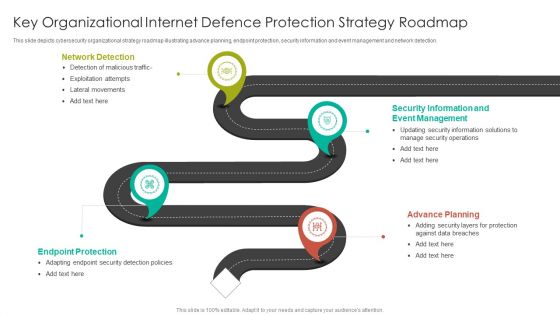
Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF
This slide depicts cybersecurity organizational strategy roadmap illustrating advance planning, endpoint protection, security information and event management and network detection.Persuade your audience using this Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Detection, Event Management, Security Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major 5G Protection And Privacy Challenges Themes PDF
The following slide highlights the top safety and protection challenges in 5G network to safeguard sensitive data from hackers. It includes elements such as architecture, security and encryption, location and data privacy etc. Presenting Major 5G Protection And Privacy Challenges Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Privacy, Location Privacy, Security And Encryption. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
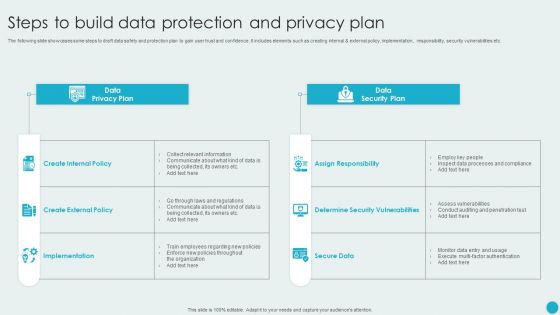
Steps To Build Data Protection And Privacy Plan Diagrams PDF
The following slide showcases some steps to draft data safety and protection plan to gain user trust and confidence. It includes elements such as creating internal and external policy, implementation, responsibility, security vulnerabilities etc. Showcasing this set of slides titled Steps To Build Data Protection And Privacy Plan Diagrams PDF. The topics addressed in these templates are Data Privacy Plan, Data Security Plan, Implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
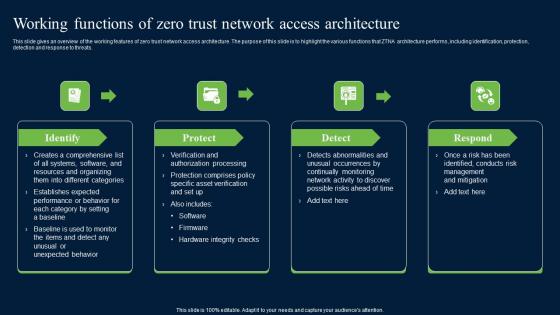
Working Functions Of Zero Trust Network Access Security Infographics Pdf
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Create an editable Working Functions Of Zero Trust Network Access Security Infographics Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Working Functions Of Zero Trust Network Access Security Infographics Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Future Of Confidential Computing Technology Secure Multi Party Rules Pdf
This slide represents the future of confidential computing technology. The purpose of this slide is to demonstrate the state of confidential computing in the coming years. It also includes how it will protect sensitive data from malicious attacks in the cloud environment. Slidegeeks has constructed Future Of Confidential Computing Technology Secure Multi Party Rules Pdf after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
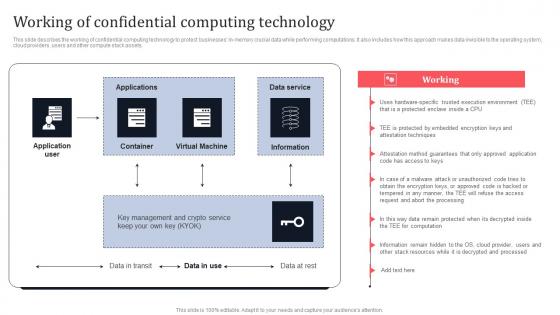
Working Of Confidential Computing Technology Secure Multi Party Information Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Working Of Confidential Computing Technology Secure Multi Party Information Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
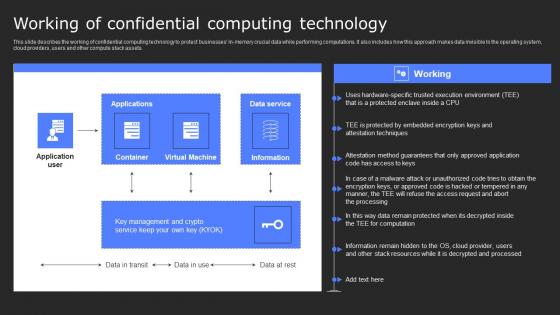
Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf
This slide describes the working of confidential computing technology to protect businesses in-memory crucial data while performing computations. It also includes how this approach makes data invisible to the operating system, cloud providers, users and other compute stack assets. Slidegeeks is here to make your presentations a breeze with Working Of Confidential Computing Technology Secure Computing Framework Diagrams Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

Concept Of Locked Money Credit PowerPoint Templates And PowerPoint Themes 0912
Concept Of Locked Money Credit PowerPoint Templates And PowerPoint Themes 0912-Microsoft Powerpoint Templates and Background with protect your investments
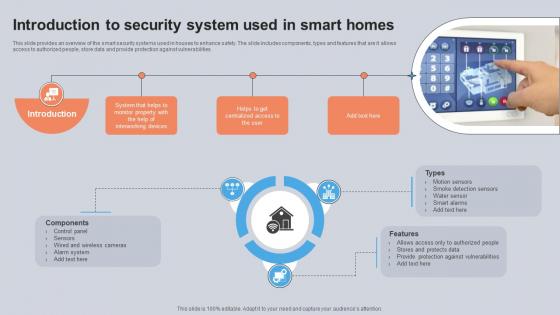
Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V
This slide provides an overview of the smart security systems used in houses to enhance safety. The slide includes components, types and features that are it allows access to authorized people, store data and provide protection against vulnerabilities. Create an editable Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Introduction To Security System Used In Smart Homes Utilizing Smart Appliances IoT SS V is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
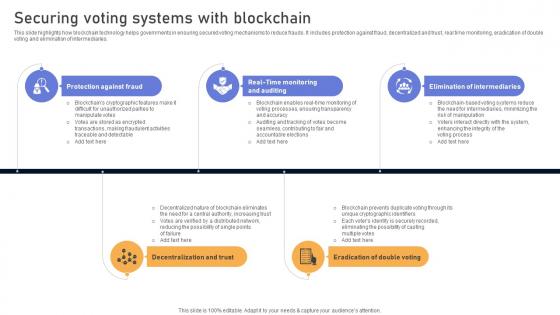
Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V
This slide highlights how blockchain technology helps governments in ensuring secured voting mechanisms to reduce frauds. It includes protection against fraud, decentralized and trust, real time monitoring, eradication of double voting and elimination of intermediaries. Get a simple yet stunning designed Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Comprehensive Look At Blockchain Securing Voting Systems With Blockchain BCT SS V can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Presenting this PowerPoint presentation, titled Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Importance Of Cryptographic Algorithms Data Security In Cloud Computing Ppt Presentation that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Solution Monitoring And Verification Process To Meet Company Requirements Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Protection And Precaution Measures For Construction Company Portrait PDF
This slide shows various measures for safety and security in a construction company. It includes measures such as training, work method assessment, site security, first aid and proper equipments. Pitch your topic with ease and precision using this Protection And Precaution Measures For Construction Company Portrait PDF. This layout presents information on Measures, Key Description, Duration. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
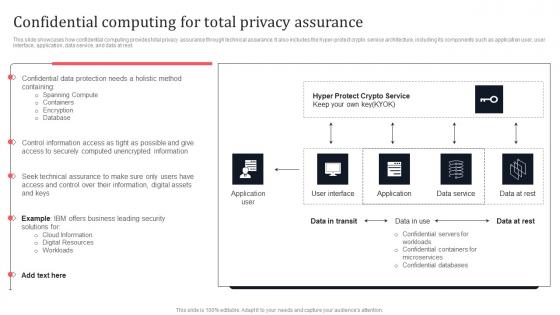
Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Confidential Computing For Total Privacy Assurance Secure Multi Party Brochure Pdf that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
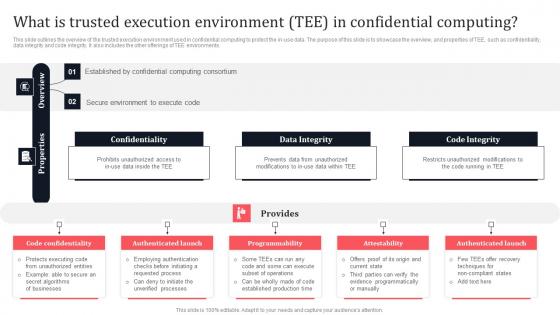
What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into What Is Trusted Execution Environment Tee In Confidential Secure Multi Party Slides Pdf

Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf
This slide outlines the overview of operational and technical assurance of data privacy by demonstrating that technical assurance offers the highest degree of data protection and privacy. In technical assurance, cloud providers cannot tamper with user data. Get a simple yet stunning designed Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Operational And Technical Assurance Of Data Privacy Secure Computing Framework Mockup Pdf can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
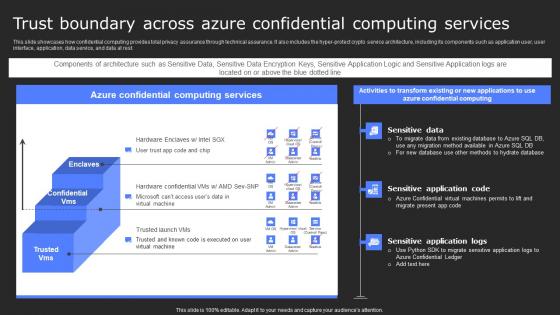
Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf a try. Our experts have put a lot of knowledge and effort into creating this impeccable Trust Boundary Across Azure Confidential Services Secure Computing Framework Sample Pdf. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf
This slide discusses the enforcement of custom rules on network. The purpose of this slide is to explain how IT departments of organizations can set custom rules to protect network from external attacks. The components include users, cloud firewall and attackers. This How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The How Fwaas Enforce Custom Rules On Network Network Security Professional Pdf features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Various Practices To Protect Functional Technology System Information PDF
Showcasing this set of slides titled various practices to protect functional technology system information pdf. The topics addressed in these templates are inventory software, awareness training, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Regulations Of Security Tokenization Strategies For Data Security PPT Template
This slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A, S regulations, etc. Find a pre-designed and impeccable Regulations Of Security Tokenization Strategies For Data Security PPT Template. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Top Web Application Security Threats Application Security Testing
This slide discusses the vulnerabilities and security threats in web application such as SQL injection, cross-site scripting, etc. Presenting this PowerPoint presentation, titled Top Web Application Security Threats Application Security Testing, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Top Web Application Security Threats Application Security Testing. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Top Web Application Security Threats Application Security Testing that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
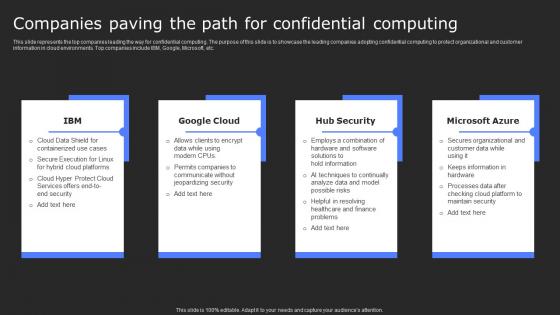
Companies Paving The Path For Confidential Secure Computing Framework Download Pdf
This slide represents the top companies leading the way for confidential computing. The purpose of this slide is to showcase the leading companies adopting confidential computing to protect organizational and customer information in cloud environments. Top companies include IBM, Google, Microsoft, etc. Present like a pro with Companies Paving The Path For Confidential Secure Computing Framework Download Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
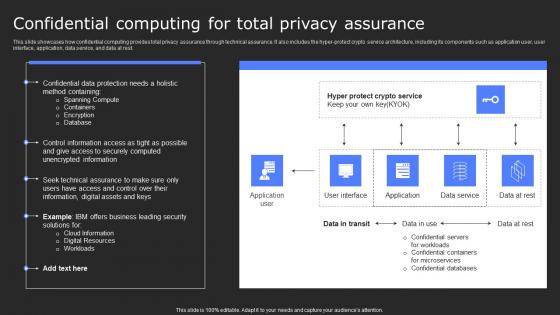
Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf
This slide showcases how confidential computing provides total privacy assurance through technical assurance. It also includes the hyper-protect crypto service architecture, including its components such as application user, user interface, application, data service, and data at rest. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing For Total Privacy Assurance Secure Computing Framework Professional Pdf to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf
This slide outlines the overview of the trusted execution environment used in confidential computing to protect the in-use data. The purpose of this slide is to showcase the overview, and properties of TEE, such as confidentiality, data integrity and code integrity. It also includes the other offerings of TEE environments. Present like a pro with What Is Trusted Execution Environment Tee In Secure Computing Framework Mockup Pdf Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf
This slide talks about the role of cryptography in cloud computing. The purpose of this slide is to elaborate the importance of cloud cryptography. The key points are protects data from unauthorized access, maintains data confidentiality, ensures data integrity, etc. Boost your pitch with our creative Importance Of Cryptographic Algorithms Cloud Data Security Using Cryptography Graphics Pdf. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
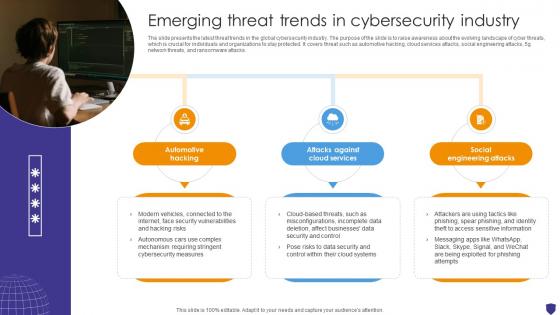
Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V
The slide presents the latest threat trends in the global cybersecurity industry. The purpose of the slide is to raise awareness about the evolving landscape of cyber threats, which is crucial for individuals and organizations to stay protected. It covers threat such as automotive hacking, cloud services attacks, social engineering attacks, 5g network threats, and ransomware attacks. Slidegeeks is here to make your presentations a breeze with Global Data Security Industry Report Emerging Threat Trends In Cybersecurity Industry IR SS V With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first
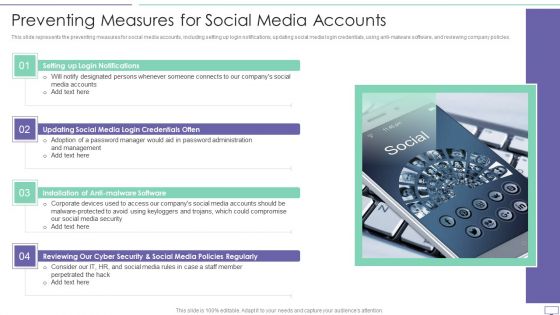
IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
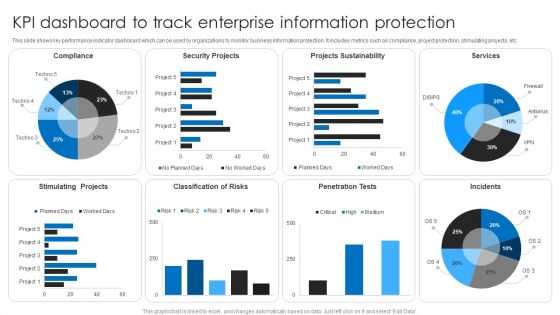
KPI Dashboard To Track Enterprise Information Protection Topics PDF
This slide shows key performance indicator dashboard which can be used by organizations to monitor business information protection. It includes metrics such as compliance, project protection, stimulating projects, etc. Showcasing this set of slides titled KPI Dashboard To Track Enterprise Information Protection Topics PDF. The topics addressed in these templates are Security Projects, Projects Sustainability, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
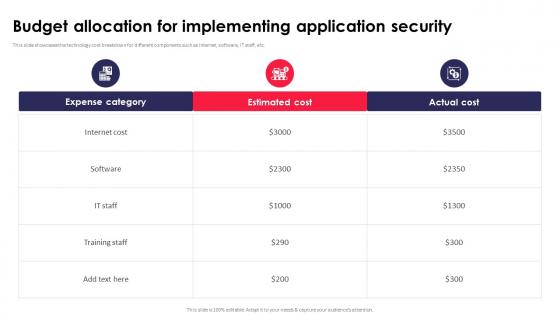
Budget Allocation For Implementing Application Security Application Security Testing
This slide showcases the technology cost breakdown for different components such as internet, software, IT staff, etc. Find highly impressive Budget Allocation For Implementing Application Security Application Security Testing on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Budget Allocation For Implementing Application Security Application Security Testing for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Checklist To Implement Effective Application Security Application Security Testing
This slide showcases the actions performed while deploying application security, person responsible, status and comments for the same. If you are looking for a format to display your unique thoughts, then the professionally designed Checklist To Implement Effective Application Security Application Security Testing is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Checklist To Implement Effective Application Security Application Security Testing and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
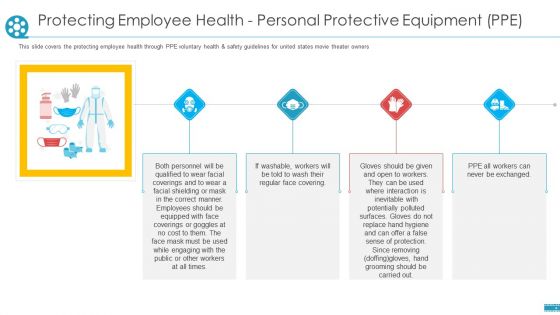
Protecting Employee Health Personal Protective Equipment PPE Ppt Summary Shapes PDF
This slide covers the protecting employee health through PPE voluntary health and safety guidelines for united states movie theater owners. This is a protecting employee health personal protective equipment ppe ppt summary shapes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting employee health personal protective equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Lock With Three Key Steps Powerpoint Templates
This PowerPoint template has been designed with lock and three key steps. This editable slide helps to display the key concepts for business success. Use this PPT slide for your business and marketing related presentations.
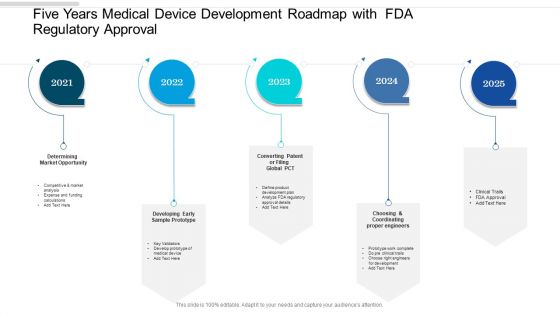
Five Years Medical Device Development Roadmap With FDA Regulatory Approval Inspiration
We present our five years medical device development roadmap with fda regulatory approval inspiration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five years medical device development roadmap with fda regulatory approval inspiration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Comparison Of Various Cyber Protection Software Portrait PDF
This slide shows comparative analysis of various cyber protection tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Comparison Of Various Cyber Protection Software Portrait PDF. This layout presents information on Compatibility, Price, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
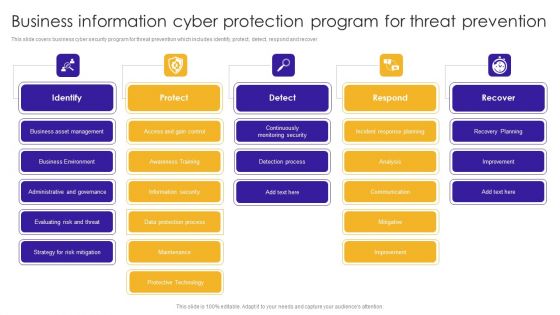
Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Protect Healthy Food To Protect Life PowerPoint Templates Ppt Backgrounds For Slides 0813
Our Protect Healthy Food To Protect Life PowerPoint Templates PPT Backgrounds For Slides deliver at your doorstep. Let them in for a wonderful experience. Dig out the dope with our Food PowerPoint Templates. Your thoughts will expose the truth. Knock on the door to success with our Global PowerPoint Templates. Be assured of gaining entry.

Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways
This slide demonstrates the concept of cloud security gateways and Secure Web Gateways. The purpose of this slide is to compare cloud security gateways and SWGs on the basis of various factors such as scope, deployment, architecture, features and cost. If you are looking for a format to display your unique thoughts, then the professionally designed Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Web Access Control Solution Comparison Between Secure Web Gateway And Cloud Security Gateways and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Big Data Monitoring Security Icon Download pdf
Pitch your topic with ease and precision using this Big Data Monitoring Security Icon Download pdf. This layout presents information on Big Data Monitoring, Security Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
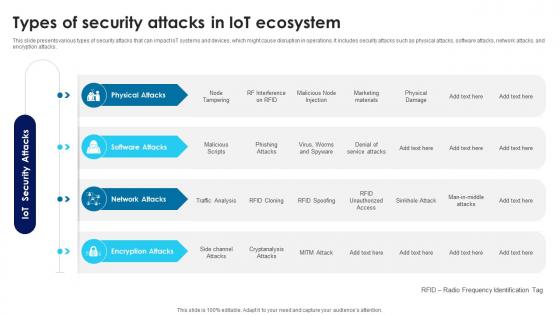
Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V
This slide presents various types of security attacks that can impact IoT systems and devices, which might cause disruption in operations. It includes security attacks such as physical attacks, software attacks, network attacks, and encryption attacks. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V can be your best option for delivering a presentation. Represent everything in detail using Building Trust With IoT Security Types Of Security Attacks In IoT Ecosystem IoT SS V and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template
This slide highlights the differences between security and utility tokens. The purpose of this slide is to compare security and utility tokens on various aspects such as purpose, expectations, scam potential, etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template can be your best option for delivering a presentation. Represent everything in detail using Comparative Analysis Of Security And Utility Token Securing Your Data Ppt Template and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Timeline For Implementing Efficient Application Security Testing
This slide outlines the different steps performed while deploying application security, including planning phase, requirement gathering, etc. Are you searching for a Timeline For Implementing Efficient Application Security Testing that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Timeline For Implementing Efficient Application Security Testing from Slidegeeks today.
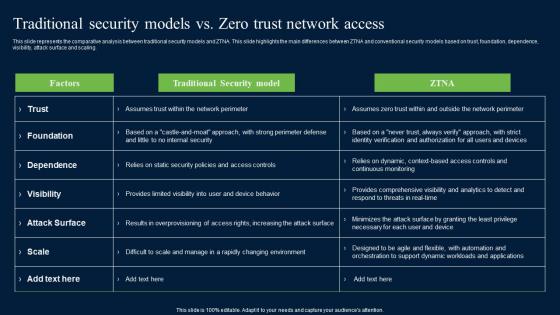
Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
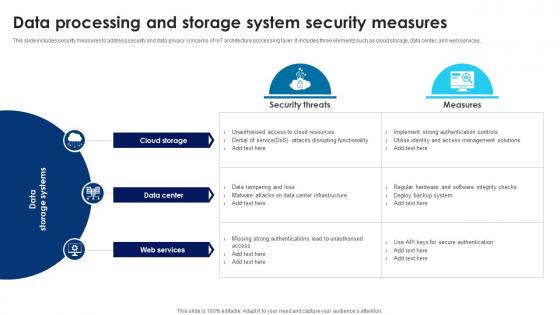
Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V
This slide includes security measures to address security and data privacy concerns of IoT architecture processing layer. It includes three elements such as cloud storage, data center, and web services. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Building Trust With IoT Security Data Processing And Storage System Security Measures IoT SS V and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Internet Protocol Security PPT Example
This Internet Protocol Security PPT Example is a primer on how to capitalize on business opportunities through planning, innovation, and market intelligence. The content-ready format of the complete deck will make your job as a decision-maker a lot easier. Use this ready-made PowerPoint Template to help you outline an extensive and legible plan to capture markets and grow your company on the right path, at an exponential pace. What is even more amazing is that this presentation is completely editable and 100 percent customizable. This eighty nine slide complete deck helps you impress a roomful of people with your expertise in business and even presentation. Craft such a professional and appealing presentation for that amazing recall value. Download now.
Agenda For Secure Computing Framework Portrait Pdf
Create an editable Agenda For Secure Computing Framework Portrait Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Agenda For Secure Computing Framework Portrait Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

4 Steps For Building Internet Security Strategy Clipart Pdf
This slide showcase developing and implementation of cyber security strategy for streamline the data security and organization vision and mission. It includes cyber threat landscape, assess cybersecurity maturity, determine security program and document cybersecurity strategy.Showcasing this set of slides titled 4 Steps For Building Internet Security Strategy Clipart Pdf The topics addressed in these templates are Cyber Security Maturity, Cyber Security Program, Document Cybersecurity Strategy All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf
The following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Are you searching for a Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Adopt Security Auditing Checklist Comprehensive Guide To Blockchain Digital Security Template Pdf from Slidegeeks today.

Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V
This slide highlights security concerns in various areas of internet of things system in order to effectively address and mitigate such risks. It includes various components Of IoT ecosystem such as web and mobile application, cloud, communications, gateways, IoT sensors, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V a try. Our experts have put a lot of knowledge and effort into creating this impeccable Building Trust With IoT Security Potential Security Vulnerabilities In IoT Ecosystem IoT SS V. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf
This slide showcases checklist which helps organisations to plan and manage their security awareness training program education planning. It includes information related to implementing security awareness, conducting periodic assessment, etc.Showcasing this set of slides titled Checklist For Effectively Communicating Security Plan Objectives Introduction Pdf The topics addressed in these templates are Implementing Security Awareness, Sustaining Security Awareness, Awareness Program All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Classification Of Big Data Security Monitoring Techniques Professional pdf
This slide showcases the classification of big data security techniques. This slide aims to help the business implement appropriate security measures for safeguarding sensitive business information. It includes infrastructure security, data privacy, data management, etc. Pitch your topic with ease and precision using this Classification Of Big Data Security Monitoring Techniques Professional pdf. This layout presents information on Infrastructure Security, Data Privacy, Data Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
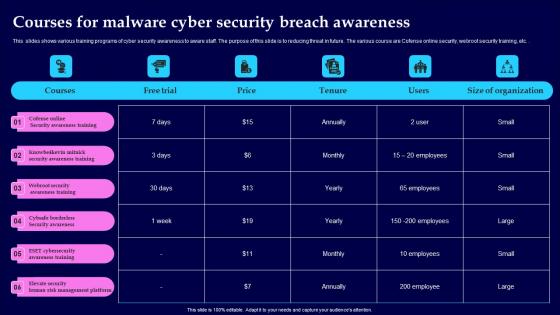
Courses For Malware Cyber Security Breach Awareness Download Pdf
This slides shows various training programs of cyber security awareness to aware staff. The purpose of this slide is to reducing threat in future. The various course are Cofense online security, webroot security training, etc. Showcasing this set of slides titled Courses For Malware Cyber Security Breach Awareness Download Pdf The topics addressed in these templates are Awareness Training, Webroot Security, Cybsafe Borderless All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Defence Protection Certification Roadmap For Career Advancement Information PDF
This slide represents cybersecurity certification roadmap illustrating certificates such as CompTIA ITFplus, CompTIA Aplus, CompTIA Network plus etc for professional growth.Pitch your topic with ease and precision using this Internet Defence Protection Certification Roadmap For Career Advancement Information PDF. This layout presents information on Intermediate Level, Information Security, Data Specialist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
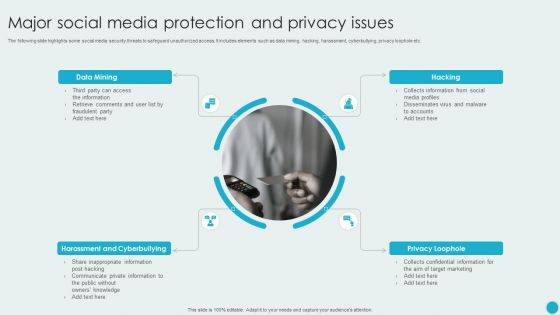
Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
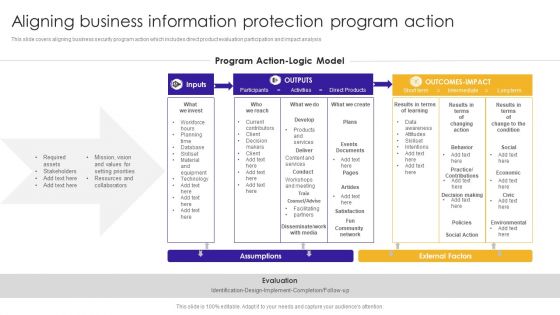
Aligning Business Information Protection Program Action Structure PDF
This slide covers aligning business security program action which includes direct product evaluation participation and impact analysis.Showcasing this set of slides titled Aligning Business Information Protection Program Action Structure PDF. The topics addressed in these templates are Setting Priorities, Assets Stakeholders, Decision Making. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
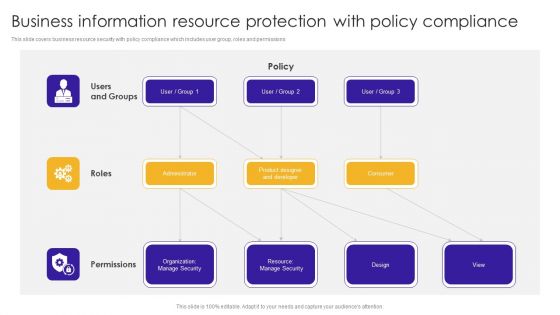
Business Information Resource Protection With Policy Compliance Information PDF
This slide covers business resource security with policy compliance which includes user group, roles and permissions. Showcasing this set of slides titled Business Information Resource Protection With Policy Compliance Information PDF. The topics addressed in these templates are Product Designer, Organization Manage, Resource Manage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Monitoring Business Information Protection Weekly Performance Summary PDF
This slide covers monitoring business security weekly performance dashboard which includes organizational financial saving and incident engagement. Pitch your topic with ease and precision using this Monitoring Business Information Protection Weekly Performance Summary PDF. This layout presents information on Active Phishing, Active Incidents, Recent Observations. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Organizational Business Information Intelligence Protection Components Background PDF
This slide covers organizational business intelligence security components which includes policy and credential store with embedded server for user or groups. Presenting Organizational Business Information Intelligence Protection Components Background PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Administrative Console, Server Governance, Middleware Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
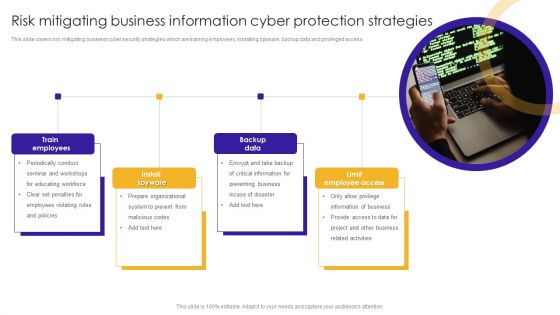
Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
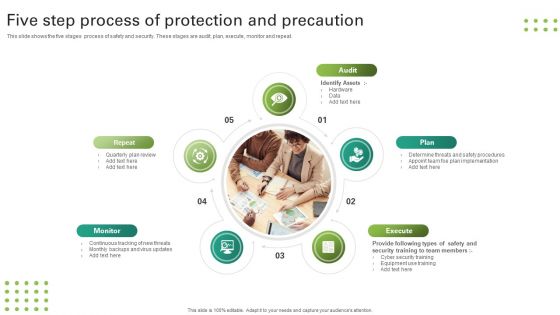
Five Step Process Of Protection And Precaution Formats PDF
This slide shows the five stages process of safety and security. These stages are audit, plan, execute, monitor and repeat. Persuade your audience using this Five Step Process Of Protection And Precaution Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Audit, Plan, Execute. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Slidegeeks is here to make your presentations a breeze with Comparison Between ZTNA And Secure Access Zero Trust Network Security Graphics Pdf With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first

CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CASB 2 0 IT Cloud Access Security Broker And Secure Web Gateway.

 Home
Home