Authentication
Solution Monitoring Verification Solution Assessment And Validation Task Options Graphics PDF
This slide shows the overview and some details of the fourth task in solution assessment and validation process i.e. Define Transition Requirements such as purpose of defining transition requirements, process inputs and output description, elements, stakeholder details and transition requirements model. Deliver an awe inspiring pitch with this creative solution monitoring verification solution assessment and validation task options graphics pdf bundle. Topics like techniques, requirements, process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Solution Monitoring Verification Solution Assessment And Validation Task Validate Solution Brochure PDF
This slide shows the overview and some details of the sixth and the last task in solution assessment and validation process i.e. Evaluating Solution Performance such as purpose of evaluating solution performance , process inputs and output description, elements, stakeholder details and evaluating solution performance model. Deliver and pitch your topic in the best possible manner with this solution monitoring verification solution assessment and validation task validate solution brochure pdf. Use them to share invaluable insights on performance, purpose, techniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Application Development Life Cycle Verification Phases Of V Model Inspiration PDF
This slide illustrates the verification phases of the V model, including business requirement analysis, system design, architectural design, module design, and coding phase. Presenting application development life cycle validation phases of v model introduction pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like pros of rapid application development model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
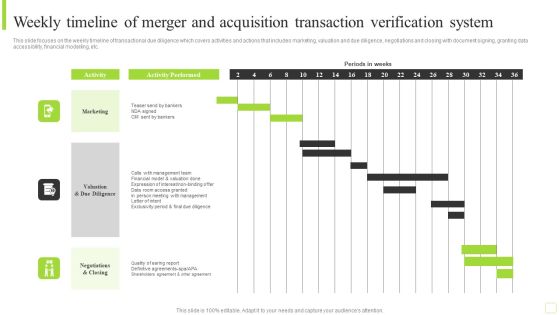
Weekly Timeline Of Merger And Acquisition Transaction Verification System Brochure PDF
This slide focuses on the weekly timeline of transactional due diligence which covers activities and actions that includes marketing, valuation and due diligence, negotiations and closing with document signing, granting data accessibility, financial modelling, etc. Pitch your topic with ease and precision using this Weekly Timeline Of Merger And Acquisition Transaction Verification System Brochure PDF. This layout presents information on Marketing, Management Team, Financial Model. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

KPI Dashboard To Track Enterprise Information Protection Topics PDF
This slide shows key performance indicator dashboard which can be used by organizations to monitor business information protection. It includes metrics such as compliance, project protection, stimulating projects, etc. Showcasing this set of slides titled KPI Dashboard To Track Enterprise Information Protection Topics PDF. The topics addressed in these templates are Security Projects, Projects Sustainability, Services. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Computer Security PowerPoint Templates And PowerPoint Themes 1012
Computer Security PowerPoint Templates And PowerPoint Themes 1012-With the move to high speed internet connection comes the greater possibility of your business being the target of an attack. One use of the term computer security refers to technology to implement a secure operating system. The Above Template will help you and your partners to understand the importance of Computer Security. Deliver amazing presentations to mesmerize your audience with our Security Template.-Computer Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Protect your computer, security, communication, computer, technology, background
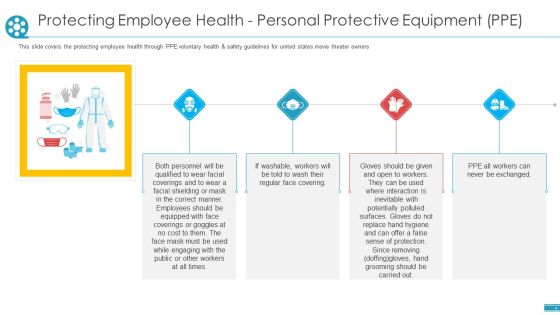
Protecting Employee Health Personal Protective Equipment PPE Ppt Summary Shapes PDF
This slide covers the protecting employee health through PPE voluntary health and safety guidelines for united states movie theater owners. This is a protecting employee health personal protective equipment ppe ppt summary shapes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting employee health personal protective equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

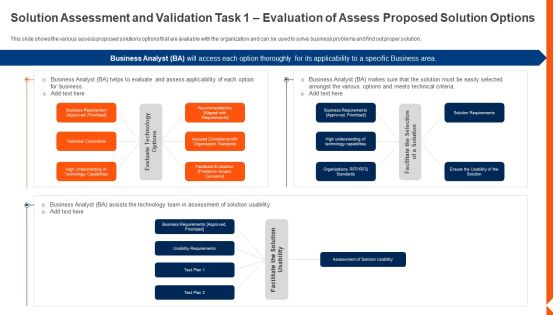
Solution Monitoring Verification Role Of Business Analyst In Solution Assessment Sample PDF
This slide show the roles and responsibilities of a Business Analyst BA in the process of Solution Assessment and Validation such as developing alternative solutions, promoting the selection of a solution, evaluating the various technology options, monitoring the QA process, communicating the solution impacts to the stakeholders etc. This is a solution monitoring verification role of business analyst in solution assessment sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like develop, technology, consideration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparison Of Various Cyber Protection Software Portrait PDF
This slide shows comparative analysis of various cyber protection tools which can be used by organizations for IT safety. It includes features, compatibility, price and ratings. Pitch your topic with ease and precision using this Comparison Of Various Cyber Protection Software Portrait PDF. This layout presents information on Compatibility, Price, Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Information Cyber Protection Program For Threat Prevention Background PDF
This slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover.Showcasing this set of slides titled Business Information Cyber Protection Program For Threat Prevention Background PDF. The topics addressed in these templates are Business Environment, Administrative Governance, Evaluating Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF
This slide represents the preventing measures for social media accounts, including setting up login notifications, updating social media login credentials, using anti-malware software, and reviewing company policies.Presenting IT Security Hacker Preventing Measures For Social Media Accounts Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Login Notifications, Malware Software, Policies Regularly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Years Medical Device Development Roadmap With FDA Regulatory Approval Inspiration
We present our five years medical device development roadmap with fda regulatory approval inspiration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five years medical device development roadmap with fda regulatory approval inspiration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Protect Healthy Food To Protect Life PowerPoint Templates Ppt Backgrounds For Slides 0813
Our Protect Healthy Food To Protect Life PowerPoint Templates PPT Backgrounds For Slides deliver at your doorstep. Let them in for a wonderful experience. Dig out the dope with our Food PowerPoint Templates. Your thoughts will expose the truth. Knock on the door to success with our Global PowerPoint Templates. Be assured of gaining entry.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Introduction PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. This is a developing firm security strategy plan information security process to manage firms sensitive data introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like privileged password management, daily tasks performed by network administrator, network security audit checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Project Security Administration IT Information Security Process To Manage Firms Sensitive Data Summary PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative project security administration it information security process to manage firms sensitive data summary pdf bundle. Topics like privileged password management, daily tasks performed by network administrator, network security audit checklist can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Internet Defence Protection Certification Roadmap For Career Advancement Information PDF
This slide represents cybersecurity certification roadmap illustrating certificates such as CompTIA ITFplus, CompTIA Aplus, CompTIA Network plus etc for professional growth.Pitch your topic with ease and precision using this Internet Defence Protection Certification Roadmap For Career Advancement Information PDF. This layout presents information on Intermediate Level, Information Security, Data Specialist. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Internet Defence Protection Expert Career Growth Roadmap Introduction PDF
This slide exhibits cybersecurity specialist career roadmap illustrating steps such as introduction, operating system, networking, understanding protocols, programming, security approach and expert.Presenting Internet Defence Protection Expert Career Growth Roadmap Introduction PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Understanding Cyber, Understanding Operating, Operate Applications. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Social Media Protection And Privacy Issues Template PDF
The following slide highlights some social media security threats to safeguard unauthorized access. It includes elements such as data mining, hacking, harassment, cyberbullying, privacy loophole etc. Presenting Major Social Media Protection And Privacy Issues Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Mining, Harassment And Cyberbullying, Privacy Loophole. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Aligning Business Information Protection Program Action Structure PDF
This slide covers aligning business security program action which includes direct product evaluation participation and impact analysis.Showcasing this set of slides titled Aligning Business Information Protection Program Action Structure PDF. The topics addressed in these templates are Setting Priorities, Assets Stakeholders, Decision Making. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Information Resource Protection With Policy Compliance Information PDF
This slide covers business resource security with policy compliance which includes user group, roles and permissions. Showcasing this set of slides titled Business Information Resource Protection With Policy Compliance Information PDF. The topics addressed in these templates are Product Designer, Organization Manage, Resource Manage. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
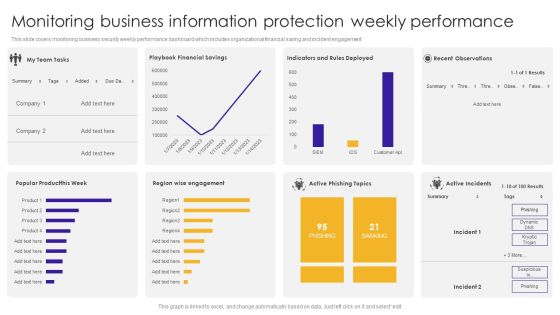
Monitoring Business Information Protection Weekly Performance Summary PDF
This slide covers monitoring business security weekly performance dashboard which includes organizational financial saving and incident engagement. Pitch your topic with ease and precision using this Monitoring Business Information Protection Weekly Performance Summary PDF. This layout presents information on Active Phishing, Active Incidents, Recent Observations. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
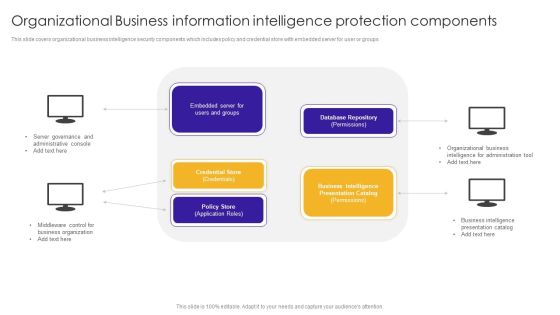
Organizational Business Information Intelligence Protection Components Background PDF
This slide covers organizational business intelligence security components which includes policy and credential store with embedded server for user or groups. Presenting Organizational Business Information Intelligence Protection Components Background PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Administrative Console, Server Governance, Middleware Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Mitigating Business Information Cyber Protection Strategies Themes PDF
This slide covers risk mitigating business cyber security strategies which are training employees, installing spyware, backup data and privileged access.Presenting Risk Mitigating Business Information Cyber Protection Strategies Themes PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Train Employees, Information Business, Related Activities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Step Process Of Protection And Precaution Formats PDF
This slide shows the five stages process of safety and security. These stages are audit, plan, execute, monitor and repeat. Persuade your audience using this Five Step Process Of Protection And Precaution Formats PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Audit, Plan, Execute. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Four Workplace Protection And Precaution Threats Template PDF
This slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting Four Workplace Protection And Precaution Threats Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Theft, It Failure, Cyber Attacks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Strategies For KPMG For Client Data Protection Pictures PDF
This slide covers techniques to secure customers confidential data through several cyber security strategies. The purpose for this template is to provide an overview on important elements of top techniques deployed by the company . It includes strategies such as people, process, data and technology and regulatory. Boost your pitch with our creative Cyber Strategies For KPMG For Client Data Protection Pictures PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Best Practices To Manage Cyber Protection Of Organization Microsoft PDF
This slide shows various practices which can be used to by organizations to manage information technology protection. These practices are monitor, risk plan, protection protocols and use technology. Persuade your audience using this Best Practices To Manage Cyber Protection Of Organization Microsoft PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Plan, Security Protocols, Technology. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Six Months Roadmap For Saas Protection Brochure PDF
This slide shows roadmap which can be used by organizations to develop SaaS protection plan. It includes requirements analysis, protection services planning, etc. Persuade your audience using this Six Months Roadmap For Saas Protection Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Determine Security, Requirements, Organization. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Solution Monitoring And Verification Process To Meet Company Requirements Ppt PowerPoint Presentation Complete Deck With Slides
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fourty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.

Strategy To Protect Iot Integrated Devices Sample PDF
This slide showcases strategy to protect internet of things IoT integrated devices. It includes information about virtual containers, user access, identification, communication, data center, virtual conditions, etc. Presenting Strategy To Protect Iot Integrated Devices Sample PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security, Network, Applications. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategy To Protect Iot Integrated Devices Designs PDF
This slide showcases strategy to protect internet of things IoT integrated devices. It includes information about virtual containers, user access, identification, communication, data center, virtual conditions, etc. This is a Strategy To Protect Iot Integrated Devices Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Segregate Networks, Connect New Iot Device, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solutions To Overcome Various It Protection Challenges Summary PDF
This slide shows solutions to various challenges faced by organizations to provide information technology protection. These challenges are data breaches, lack of expertise, insider threats and unsecured APIs. Persuade your audience using this Solutions To Overcome Various It Protection Challenges Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breaches, Cloud Security, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Protection And Privacy Roadmap Sample PDF
The following slide showcases IT security and privacy roadmap to protect digital information from severe threats. It includes elements such as assess, build, select, deploy, train and test. Persuade your audience using this Information Technology Protection And Privacy Roadmap Sample PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Deploy, Build, Select, Train. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF
This slide represent entity relationship diagram showcasing user journey for mobile app. It provides information regarding login page, password creation, home page, resources, settings etc. Presenting Entity Relationship Diagram Showcasing User Journey Of Mobile App Topics PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Password Creation, Correct Password Input, Setting Configuration, Document Creation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Components Of Data Protection And Privacy Policies Graphics PDF
The following slide depicts some elements of data security and privacy policies to communicate the relevance and purpose of collected data. It includes elements such as scan vulnerabilities, manage patches, response to incidents, monitor compliance etc. Presenting Key Components Of Data Protection And Privacy Policies Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Patches, Response To Incidents, Monitor Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Protection And Privacy Response Action Plan Graphics PDF
The following slide illustrates the series of steps to respond security incidents. It includes elements such as report, identify, declare, respond, remediate and close. Persuade your audience using this Protection And Privacy Response Action Plan Graphics PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Declare, Respond, Remediate, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technologies To Ensure Data Protection And Privacy Background PDF
The following slide showcases some technologies to administer organizational data privacy and security concerns. It includes elements such as data encryption, change management and auditing, user and behavior analytics UEBA, backup and recovery etc. Presenting Technologies To Ensure Data Protection And Privacy Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Encryption, Change Management And Auditing, Backup And Recovery. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Online Business Information Protection And Fraud Prevention Topics PDF
This slide covers online business security and fraud prevention which includes installing firewall, periodic user name change and separate financial terminal. Persuade your audience using this Online Business Information Protection And Fraud Prevention Topics PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Create Separate, Financial Terminal, Prevent Network. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Major Steps To Develop Protection And Precaution Strategy Themes PDF
This slide shows multi steps process to build safety and security strategy. These strategies are assess vulnerabilities, adopt safety measures, control access, alert authorities and audit procedures. Persuade your audience using this Major Steps To Develop Protection And Precaution Strategy Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Assess Vulnerabilities, Adopt Safety Measures, Control Access. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Workplace Protection And Precaution Inspection Checklist Clipart PDF
This slide shows comprehensive checklist which can be used to measure safety and security in organization. It includes points such as whether CCTVs are working or employees wear id card or not etc. Presenting Workplace Protection And Precaution Inspection Checklist Clipart PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Checklist, Properly Working Cctvs, Employee Wear Id Badges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
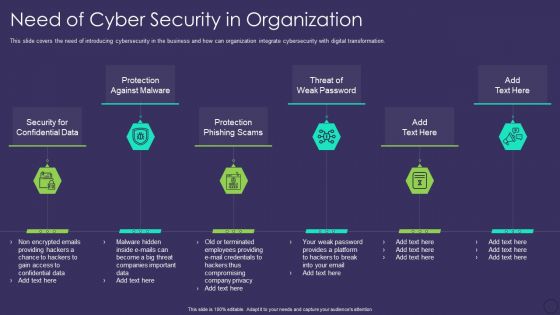
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
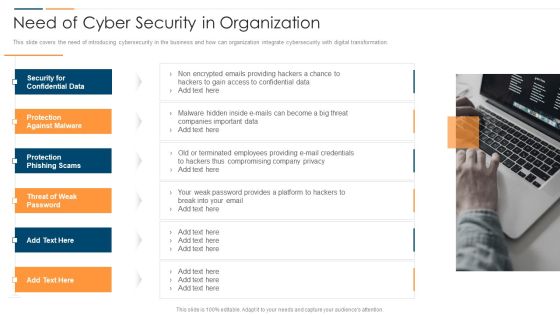
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting Organization Transition Need Of Cyber Security In Organization Ppt PowerPoint Presentation Gallery Themes PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
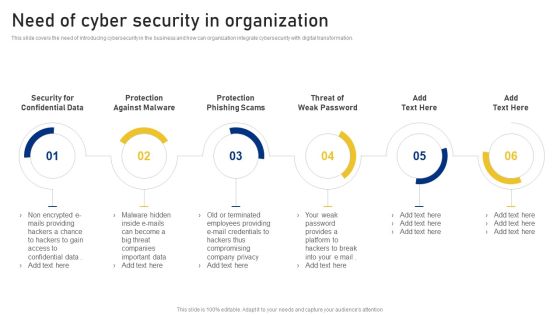
Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Reshaping Business In Digital Need Of Cyber Security In Organization Sample PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Protection Against Malware, Protection Phishing Scams, Threat Weak Password . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
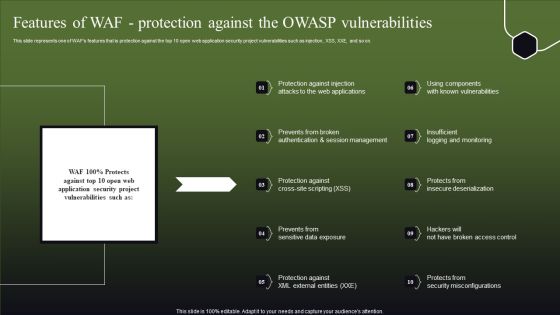
Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF
This slide represents one of WAFs features that is protection against the top 10 open web application security project vulnerabilities such as injection, XSS, XXE, and so on. This Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Features Of WAF Protection Against The OWASP Vulnerabilities Slides PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF
Mentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e-wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Retrieve professionally designed Cashless Payment Strategies To Enhance Business Performance Best Practices To Maintain Digital Wallet Security Brochure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Agile Project Management Acceptance Criteria With User Story Ideas PDF
This slide shows agile acceptance criteria with user story. It provides information about goal, benefit, scenario, navigate, login page, recovery, password, reset link, security, etc. Presenting Agile Project Management Acceptance Criteria With User Story Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Proceeds, Benefit, Goal. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Stock Photo Basic Marketing Concepts Image Of Key Innovation Business
Establish The Dominance Of Your Ideas. Our stock photo basic marketing concepts image of key innovation business Powerpoint Templates Will Put Them On Top. Put Yourself In A Dominant Position. Our Powerpoint Templates Will Confirm Your Superiority.

Cloud Security Assessment Cloud Security Checklist Networking Formats PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks.This is a Cloud Security Assessment Cloud Security Checklist Networking Formats PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gateway To Protect, Injecting Malicious, Precautions To Protect You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
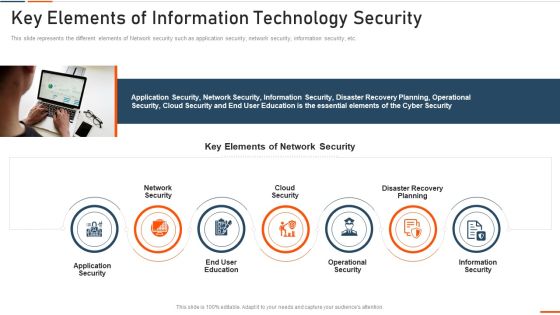
Key Elements Of Information Technology Security Ppt Styles Example PDF
This slide defines the meaning of network security and how it helps to prevent data through different methods and techniques. Presenting key elements of information technology security ppt styles example pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like approach, collective, methods, techniques, procedures, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Prepare Data Backup Ppt Layouts Slides PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information technology security prepare data backup ppt layouts slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, information, manipulation, deletion, prevent . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Organizing Security Awareness Cyber Security Awareness Checklist To Ensure IT Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF
This slide highlights the extensive devices suite for home security which includes outdoor video, doorbell video, indoor video, thermostat control, vehicle protection, flood protection and motion awareness. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Intelligent Smart Home Security Devices Portrait PDF bundle. Topics like Flood Protection, Motion Awareness, Vehicle Protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Additional Security Services Formats PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Additional Security Services Formats PDF bundle. Topics like Safety Escort Service, Executive Protection, Safety Escort Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Security Internet PowerPoint Templates And PowerPoint Backgrounds 0511
Microsoft PowerPoint Template and Background with internet data security with fiber optical background

Lock Minded Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with security minded digital collage of human profile with key

Data Security Internet PowerPoint Themes And PowerPoint Slides 0511
Microsoft PowerPoint Theme and Slide with internet data security with fiber optical Slide

Stock Photo 3d Blue Folder With Lock For Data Security PowerPoint Slide
This power point image template has been crafted with graphic of 3d blue folder and lock. This image contains the concept of data security. Use this image PPT for your technology and security related presentations.

Develop Corporate Cyber Security Risk Mitigation Plan Next Steps For Organization Cyber Protection Services Topics PDF Themes PDF
Presenting develop corporate cyber security risk mitigation plan next steps for organization cyber protection services topics pdf themes pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like desired changes, initial payment, organization, cyber protection services. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home