Access Control

Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
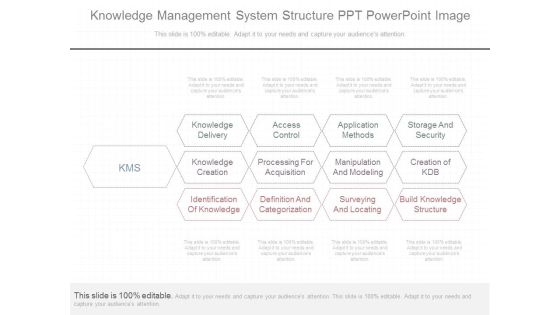
Knowledge Management System Structure Ppt Powerpoint Image
This is a knowledge management system structure ppt powerpoint image. This is a three stage process. The stages in this process are knowledge delivery, access control, application methods, storage and security, knowledge creation, processing for acquisition, manipulation and modeling, creation of kdb, identification of knowledge, definition and categorization, surveying and locating, build knowledge structure, kms.

Chart Showing Comparison Of Database Systems Ppt PowerPoint Presentation Portfolio Styles
Presenting this set of slides with name chart showing comparison of database systems ppt powerpoint presentation portfolio styles. The topics discussed in these slides are price in usd, basic, professional, premium, data functionality features, data backup and recovery, multiuser access control, minimum duplication and redundancy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
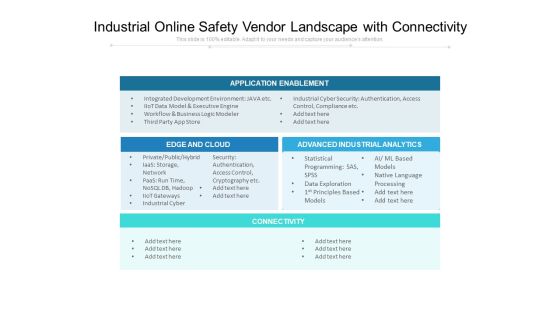
Industrial Online Safety Vendor Landscape With Connectivity Ppt PowerPoint Presentation Infographic Template Graphics Download PDF
Showcasing this set of slides titled industrial online safety vendor landscape with connectivity ppt powerpoint presentation infographic template graphics download pdf. The topics addressed in these templates are network, security,authentication, access control, cryptography, processing, business, analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Governance Building Blocks Ppt PowerPoint Presentation Gallery Inspiration PDF
Presenting this set of slides with name data governance building blocks ppt powerpoint presentation gallery inspiration pdf. This is a three stage process. The stages in this process are ownership, classification, access control. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Company Vulnerability Administration Record Discovered Vulnerabilities Ideas PDF
Presenting company vulnerability administration record discovered vulnerabilities ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like discovery date and time, categorization, affected assets, priority assure access control of the repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Complete IT Security IT Implementation Checklist Ppt Diagrams PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Deliver an awe inspiring pitch with this creative complete it security it implementation checklist ppt diagrams pdf bundle. Topics like training, antivirus software, secure communications, access control measures, device security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

RBAC Variations For Different Organizational Levels Summary PDF
This slide shows the role based access control variations organized as levels. It includes details related to name of different levels od RBAC along with their functional capabilities. Showcasing this set of slides titled RBAC Variations For Different Organizational Levels Summary PDF. The topics addressed in these templates are RBAC Variations, Different Organizational Levels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Benefits Of Report Software For Life Science Quality Management System Summary PDF
This slide highlights the advantage of document control software for life science quality management system. It includes authoring, review, approval, access controls, audit trails, alerts and notifications, reporting capabilities, secure cloud storage, version control, etc. Presenting Benefits Of Report Software For Life Science Quality Management System Summary PDF to dispense important information. This template comprises Ten stages. It also presents valuable insights into the topics including Reporting Capabilities, Secure Cloud Storage, Version Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
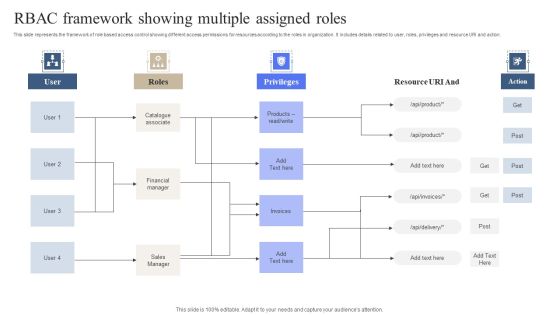
RBAC Framework Showing Multiple Assigned Roles Download PDF
This slide represents the framework of role based access control showing different access permissions for resources according to the roles in organization. It includes details related to user, roles, privileges and resource URI and action. Pitch your topic with ease and precision using this RBAC Framework Showing Multiple Assigned Roles Download PDF. This layout presents information on Catalogue Associate, Financial Manager, Sales Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Information Protection Methodologies For Organizational Facilities Demonstration PDF
This slide covers business security methodologies for organizational facilities which are security plan documentation, access control, installing surveillance system and reinforce data security.Presenting Business Information Protection Methodologies For Organizational Facilities Demonstration PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Plan Documentation, Implement Access, Surveillance System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Policy And Why You Should Embrace It Cloud Computing Security IT Ppt Infographics Gridlines PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a zero trust policy and why you should embrace it cloud computing security it ppt infographics gridlines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication, device validation, restrict access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Network Operations 5G Protocol Layers Mapped With OSI Stack Topics PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C-Plane protocol stack, and so on. There are so many reasons you need a 5G Network Operations 5G Protocol Layers Mapped With OSI Stack Topics PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

5G Network Applications And Features 5G NR Radio Protocol Stack Architecture Topics PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C-Plane protocol stack, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable 5G Network Applications And Features 5G NR Radio Protocol Stack Architecture Topics PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

5G Nr Radio Protocol Stack Architecture 5G Functional Architecture Structure PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C Plane protocol stack, and so on.Deliver and pitch your topic in the best possible manner with this 5G Nr Radio Protocol Stack Architecture 5G Functional Architecture Structure PDF. Use them to share invaluable insights on protocol stack includes, data processes, information travels and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Project Assistance Templates Bundle Application Users Ppt Inspiration Demonstration PDF
Deliver and pitch your topic in the best possible manner with this Project Assistance Templates Bundle Application Users Ppt Inspiration Demonstration PDF. Use them to share invaluable insights on Access Settings, Control Center, Activation Pending and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
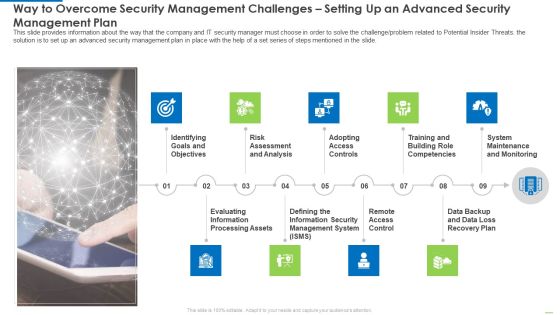
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Introduction PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment and analysis, adopting access controls, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
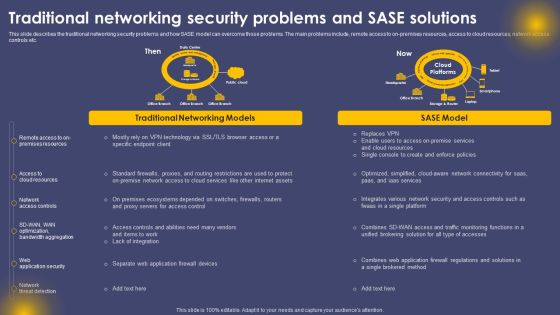
Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.
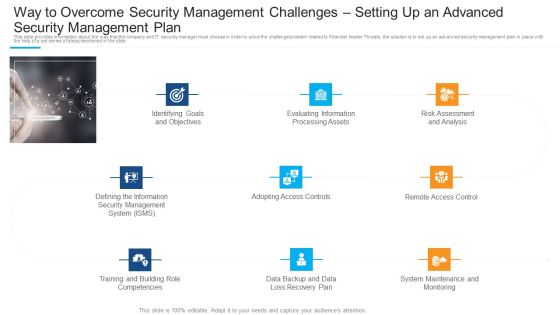
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Pictures PDF
Presenting way to overcome security management challenges setting up an advanced security management plan pictures pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Circular Process For Enterprise Resource Planning With Data Services Ppt PowerPoint Presentation Infographics Ideas PDF
Persuade your audience using this circular process for enterprise resource planning with data services ppt powerpoint presentation infographics ideas pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including finance accounting, human resources, engineering, purchasing, project management, crm, data services, access control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Techniques And Strategies To Reduce Security Management Risks Table Of Contents Structure PDF
Presenting techniques and strategies to reduce security management risks table of contents structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF
This slide shows how we can build a successful cloud security strategy. It explains about data privacy, keeping access control, responsibilities of cloud and providing training.Presenting How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Enterprise, Data Privacy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly Internet Defence Protection Evolution And Metrics Roadmap Sample PDF
This slide exhibits quarterly based cybersecurity roadmap showcasing evolution and metrics such as access control, vulnerability management, assessment and testing etc.Presenting Quarterly Internet Defence Protection Evolution And Metrics Roadmap Sample PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Auditing Documentation, Penetration Test, Administrative Privileges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Improve IT Service Desk Pre Deployment Audit Checklist For Service Desk Tool Icons PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc.Deliver and pitch your topic in the best possible manner with this Improve IT Service Desk Pre Deployment Audit Checklist For Service Desk Tool Icons PDF. Use them to share invaluable insights on Customizable Integrable, Operational Automation, Service Desk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF. Use them to share invaluable insights on Cloud Frameworks, Information Division, Cautious Scaling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Agency Business Profile Corporate And Industrial Security Services Information PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Corporate And Industrial Security Services Information PDF. Use them to share invaluable insights on Corporate Security, Industrial Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF bundle. Topics like Corporate Security, Industrial Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web App Firewall Services IT Web Application Firewall With Traditional Firewall Professional PDF
This slide represents the difference between a web application firewall and a traditional firewall based on functionality, implementation, threat prevention, OSI layers, and access control. Deliver an awe inspiring pitch with this creative web app firewall services it web application firewall with traditional firewall professional pdf bundle. Topics like organization, applications, implementation, networks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web Application Firewall With Traditional Firewall WAF Platform Summary PDF
This slide represents the difference between a web application firewall and a traditional firewall based on functionality, implementation, threat prevention, OSI layers, and access control. Deliver and pitch your topic in the best possible manner with this Web Application Firewall With Traditional Firewall WAF Platform Summary PDF. Use them to share invaluable insights on Network, Applications, Data Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
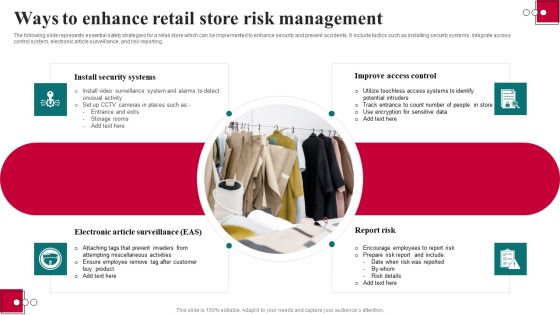
Ways To Enhance Retail Store Risk Management Introduction PDF
The following slide represents essential safety strategies for a retail store which can be implemented to enhance security and prevent accidents. It include tactics such as installing security systems, integrate access control system, electronic article surveillance, and risk reporting. Pitch your topic with ease and precision using this Ways To Enhance Retail Store Risk Management Introduction PDF. This layout presents information on Electronic Article Surveillance, Report Risk, Install Security Systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

High Level Hyperledger Architecture For Blockchain Creation Involving Cryptographic Ledger To Enhance Topics PDF
This slide depicts the high-level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Present like a pro with High Level Hyperledger Architecture For Blockchain Creation Involving Cryptographic Ledger To Enhance Topics PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Overview For Configuration Management Database With Characteristics Microsoft PDF
This slide represents meaning of CMDB Configuration Management Database with its key characteristics. It covers details regarding asset configuration, dashboards, access control etc. Present like a pro with Overview For Configuration Management Database With Characteristics Microsoft PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
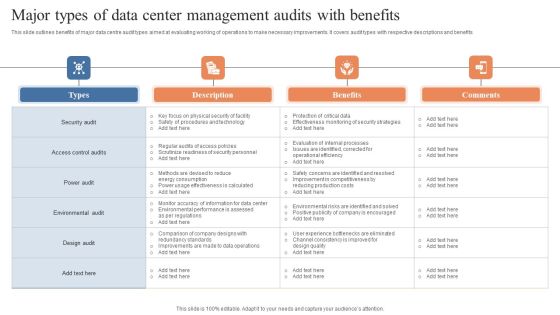
Major Types Of Data Center Management Audits With Benefits Pictures PDF
This slide outlines benefits of major data centre audit types aimed at evaluating working of operations to make necessary improvements. It covers audit types with respective descriptions and benefits. Showcasing this set of slides titled Major Types Of Data Center Management Audits With Benefits Pictures PDF. The topics addressed in these templates are Security Audit, Access Control Audits, Power Audit . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Execution Of ICT Strategic Plan Selection For Cloud Management Platform Tools Summary PDF
This slide represents selection for cloud management tools. It covers asset inventory management, workflow automation, security, access control etc. Want to ace your presentation in front of a live audience Our Execution Of ICT Strategic Plan Selection For Cloud Management Platform Tools Summary PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

IT Security Complete IT Security Implementation Checklist Ppt Layouts Graphics PDF
This slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Presenting complete information technology security implementation checklist ppt file introduction pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like secure communications, device security, access control measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. The Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Blockchain Technology Framework IT High Level Hyperledger Architecture For Blockchain Creation Rules PDF
This slide depicts the high level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Presenting blockchain technology framework it high level hyperledger architecture for blockchain creation rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like high level hyperledger architecture for blockchain creation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
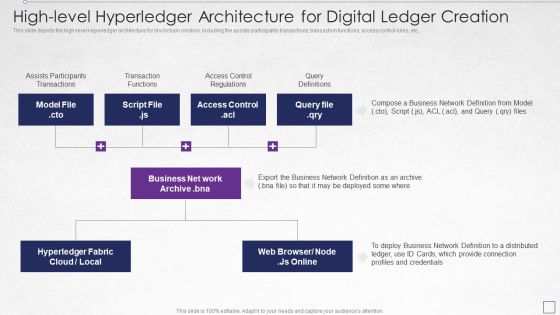
Digitized Record Book Technology High Level Hyperledger Architecture Information PDF
This slide depicts the high level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Presenting digitized record book technology high level hyperledger architecture information pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high level hyperledger architecture for digital ledger creation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF
This slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy.This is a Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Best Example, Authentication, Implement Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Benefits Of RBAC For Companies And Employees Introduction PDF
This slide represents the role based access control benefits for both the companies and the employees. It includes benefits of RBAC for company such as reduced costs, improvement in security, better compliance and reporting capabilities etc. Showcasing this set of slides titled Key Benefits Of RBAC For Companies And Employees Introduction PDF. The topics addressed in these templates are Benefits For Company, Benefits For Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. This is a Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Article Surveillance, Install Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

DLT Technology High Level Hyperledger Architecture For Blockchain Creation Topics PDF
This slide depicts the high-level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward DLT Technology High Level Hyperledger Architecture For Blockchain Creation Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal DLT Technology High Level Hyperledger Architecture For Blockchain Creation Topics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
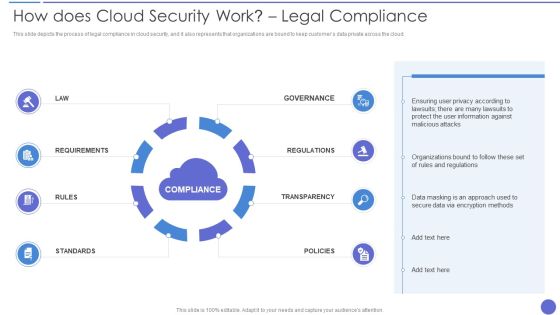
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Trending Features Of Ai In Technological Smart Homes Products Background PDF
This side showcase the features of artificial intelligence for power efficiency, time saving alerts, evolved smart appliances in smart homes. It include the features such as smart security, controlled power, energy saving, better device functioning and better user experience. Presenting Trending Features Of Ai In Technological Smart Homes Products Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Smart Security Access Control, Energy Saving Right Utilization, Better Device Functioning. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Assessment For Brand Element Management Software Slides PDF
This slide signifies the comparative assessment of different of different softwares on brand asset management. It includes features like asset creation, indexing, accessing control, collaboration and distribution. Showcasing this set of slides titled Comparative Assessment For Brand Element Management Software Slides PDF. The topics addressed in these templates are User Friendly Interface, Indexing, Storage Digital Assets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
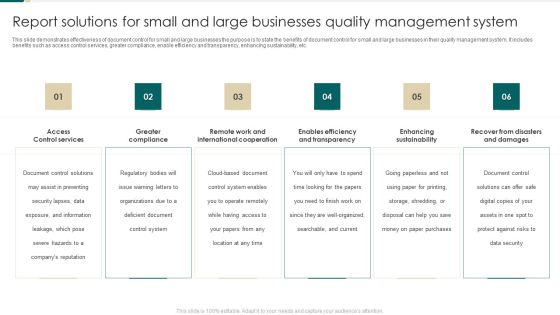
Report Solutions For Small And Large Businesses Quality Management System Guidelines PDF
This slide demonstrates effectiveness of document control for small and large businesses the purpose is to state the benefits of document control for small and large businesses in their quality management system. It includes benefits such as access control services, greater compliance, enable efficiency and transparency, enhancing sustainability, etc. Persuade your audience using this Report Solutions For Small And Large Businesses Quality Management System Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Control Services, Greater Compliance, Enables Efficiency And Transparency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
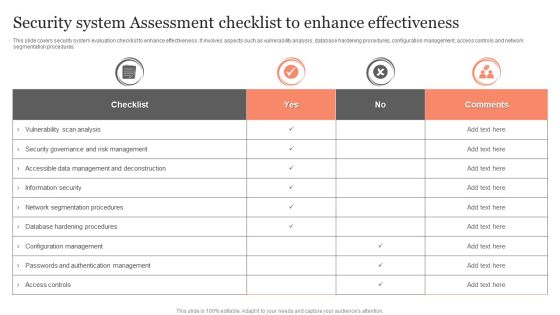
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF
This slide shows framework which can be used by organizations to develop cloud security for data protection. It includes authentication, access control, user behavior analytics, logging an reporting, etc. Persuade your audience using this Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF. This PPT design covers Eight stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Framework, To Ensure Data Safety . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF
This slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cyber Security Components To Enhance Processes Tools Used For Cyber Security Goals Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
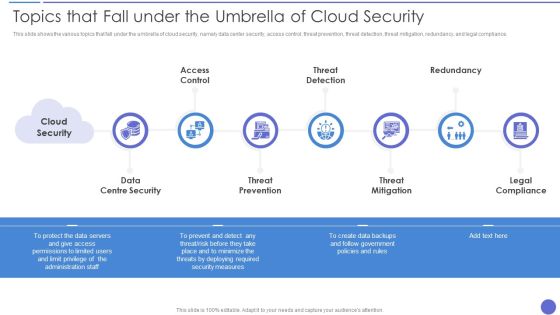
Topics That Fall Under The Umbrella Of Cloud Security Formats PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Topics That Fall Under The Umbrella Of Cloud Security Formats PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Threat Mitigation, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF
The following slide highlights the information and cyber security policy development by depicting purpose, audience, information security, access control, data segregation, data support, security awareness and responsibilities. Presenting Information And Digital Risk Assessment Policy Development Ppt Portfolio Slideshow PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Responsibilities, Security Awareness, Data Support, Data Segregation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Terrorism Assault Techniques To Protect SCADA Systems From Cyber Attacks Demonstration PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls.Presenting cyber terrorism assault techniques to protect scada systems from cyber attacks demonstration pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like access controls, strict firewalls, network security procedures In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF
This slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Presenting Info Safety And ISO 27001 Security Domains That Will Be Addressed By Isms Sample PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Security Policy, Asset Management, Physical And Environmental Security, Operational Security, Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF
This slide signifies cyber security roadmap of an organization with seven millstone achieved within 4 year timeline. Persuade your audience using this Milestone Roadmap Of A Cyber Security Company With Key Dates Ppt PowerPoint Presentation File Design Templates PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Security Assessment Team, Identify Digital Assets, Provide Access Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions.Presenting Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Categorization Of Services, Access Control, Data Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF
This slide showcases the features do digital security have for security. It includes features such as authentication, confidentiality, integrity, non-repudiation and access control. Persuade your audience using this Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Security Measures, Functions, Authentication, Confidentiality. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Essential Features Of An Application Programming Interface Governance Platform Topics PDF
This slide covers the features that are necessary for an API governance platform that will help the organisation to get the power for streamlining the adoption of APIs. It includes access management, audit trail, ingress or egress control and analyze. Persuade your audience using this Essential Features Of An Application Programming Interface Governance Platform Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Access Management, Egress Control, Analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

5G NR Radio Protocol Stack Architecture 5G Network Functional Architecture Sample PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C-Plane protocol stack, and so on.Want to ace your presentation in front of a live audience Our 5G NR Radio Protocol Stack Architecture 5G Network Functional Architecture Sample PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

5G NR Radio Protocol Stack Architecture 5G Network Structure Portrait PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C-Plane protocol stack, and so on.Want to ace your presentation in front of a live audience Our 5G NR Radio Protocol Stack Architecture 5G Network Structure Portrait PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Process Of Web Security Testing And Analysis Ppt Design
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.
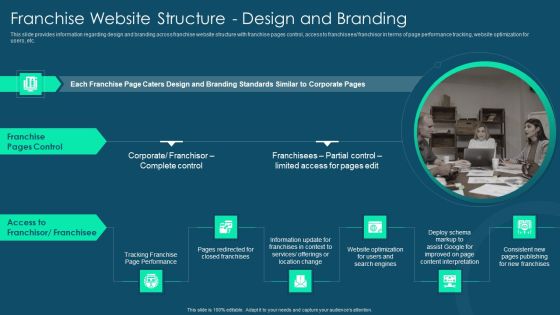
Franchise Promotion And Advertising Playbook Franchise Website Structure Design And Branding Template PDF
This slide provides information regarding design and branding across franchise website structure with franchise pages control, access to franchisees or franchisor in terms of page performance tracking, website optimization for users, etc. Deliver and pitch your topic in the best possible manner with this franchise promotion and advertising playbook franchise website structure design and branding template pdf. Use them to share invaluable insights on franchise pages control, access to franchisor or franchisee and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

5 Steps To Develop Workplace Protection Strategy Sample PDF
This slide shows multi steps process to draft protection strategy for office premises. These stages are assess vulnerabilities, adopt safety measures, control access, alert authorities and audit procedures. Presenting 5 Steps To Develop Workplace Protection Strategy Sample PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Assess Vulnerabilities, Control Access, Alert Authorities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Steps To Develop Protection And Precaution Strategy Themes PDF
This slide shows multi steps process to build safety and security strategy. These strategies are assess vulnerabilities, adopt safety measures, control access, alert authorities and audit procedures. Persuade your audience using this Major Steps To Develop Protection And Precaution Strategy Themes PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Assess Vulnerabilities, Adopt Safety Measures, Control Access. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
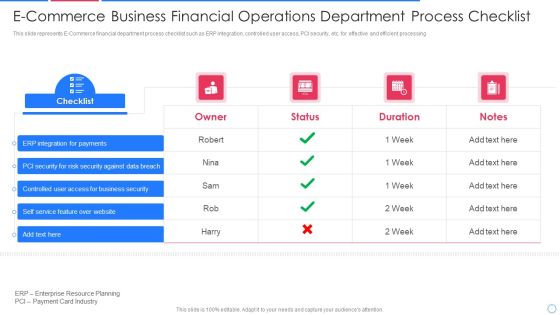
E Commerce Business Financial Operations Department Process Checklist Information PDF
This slide represents E-Commerce financial department process checklist such as ERP integration, controlled user access, PCI security, etc. for effective and efficient processing Pitch your topic with ease and precision using this e commerce business financial operations department process checklist information pdf This layout presents information on integration for payments, security for risk security against, controlled user access It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
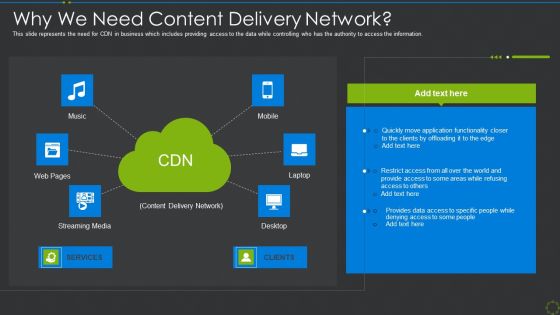
Why We Need Content Delivery Network Ppt File Slides Ppt Slides Inspiration PDF
This slide represents the need for CDN in business which includes providing access to the data while controlling who has the authority to access the information. Deliver an awe inspiring pitch with this creative why we need content delivery network ppt file slides ppt slides inspiration pdf bundle. Topics like why we need content delivery network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Server Network Design Structure Model Ppt PowerPoint Presentation Gallery Graphics PDF
Presenting this set of slides with name customer server network design structure model ppt powerpoint presentation gallery graphics pdf. This is a one stage process. The stages in this process are central data base, data and information, internet, control switch, providing connection to server, common control switch, wireless access point server, providing internet medium, security firewall acting, threat and viruses. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Presenting this PowerPoint presentation, titled Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
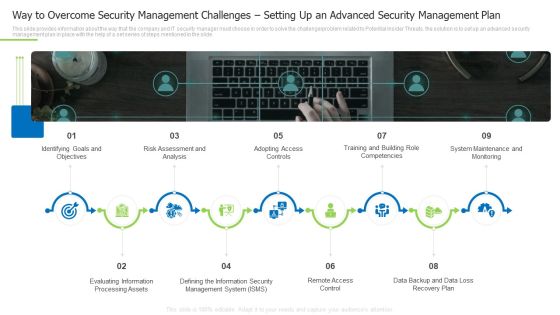
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Rules PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan rules pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

HRMS Execution Plan Employee Document Management System Ideas PDF
This slide covers the use case of document management software. It also includes the features of software such as automatic tax document generation, company policies, employee handbook, document access control, etc. This modern and well arranged HRMS Execution Plan Employee Document Management System Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Techniques And Strategies To Reduce Security Management Risks Security Management Plan Steps Portrait PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Adopting Access Controls. This is a techniques and strategies to reduce security management risks security management plan steps portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like suggested coverage, security risk management, estimated security management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
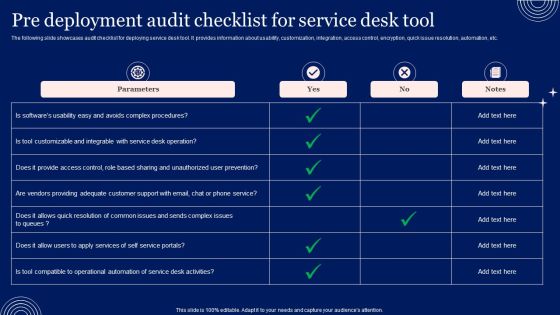
Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc.This Implementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. TheImplementing Advanced Service Help Desk Administration Program Pre Deployment Audit Checklist For Service Desk Tool Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cybersecurity Monitoring Plan Steps In Detail Setting Up A Centralized Collection And Elements PDF
This slide provides information about the sixth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Setting up a Centralized Collection and Analysis Capability. This is a cybersecurity monitoring plan steps in detail setting up a centralized collection and elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interpret information, high priority alerts, analysts, access controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
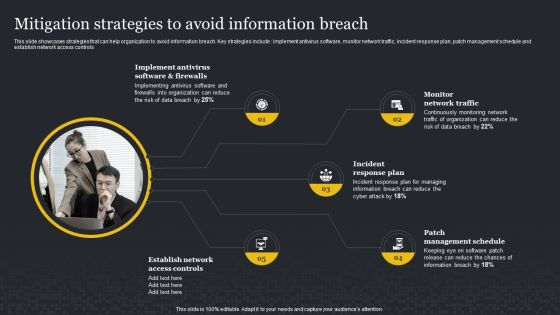
Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Present like a pro with Mitigation Strategies To Avoid Information Breach Cybersecurity Risk Assessment Professional PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security And Human Resource Services Business Profile Corporate And Industrial Security Formats PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Present like a pro with Security And Human Resource Services Business Profile Corporate And Industrial Security Formats PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Datafy Measures To Maintain Data Security In Datafication Diagrams PDF
This slide talks about the measures to keep data secure in datafication, including legal requirements, technical measures and business practices, containing marketing campaigns, sales operations and customer service. The technical measures include encryption, firewalls, and access controls. Welcome to our selection of the Datafy Measures To Maintain Data Security In Datafication Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
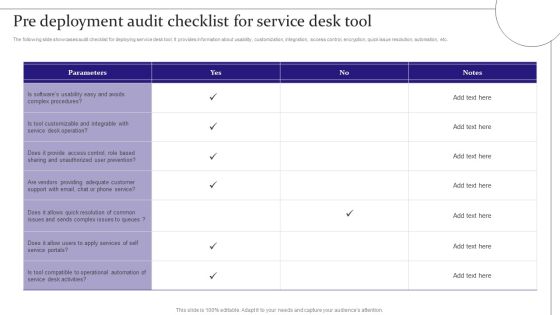
Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. This Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Digitalization Of Service Desk Pre Deployment Audit Checklist For Service Desk Tool Ppt Infographics Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Integrating ITSM To Enhance Service Pre Deployment Audit Checklist For Service Desk Tool Summary PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Ppt PowerPoint Presentation Diagram PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Pre Deployment Audit Checklist For Service Desk Tool Sample PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc. Welcome to our selection of the Pre Deployment Audit Checklist For Service Desk Tool Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Top Software Providers For Designing Framework For Effective Information Management Slides PDF
The following slide delineates top software providers that can assist businesses in designing knowledge management framework. It includes information about controlling access, content management, data security, automation, reporting, analytics, workflows, etc. Showcasing this set of slides titled Top Software Providers For Designing Framework For Effective Information Management Slides PDF. The topics addressed in these templates are Content Management, Data Security, Controlling Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Determine 5G Era Network Flexibility NFV SDN And Cloud Ran Clipart PDF
This slide provides details regarding 5G era network flexibility in terms of NFV or SDN and cloud RAN in order to cater customized services for major clients. Deliver an awe inspiring pitch with this creative Determine 5G Era Network Flexibility NFV SDN And Cloud Ran Clipart PDF bundle. Topics like Network Control Planes, Location, Access Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Report Best Practices For Quality Management System Graphics PDF
This slide highlights the excellent QMS document control best practices. The purpose is to avoid costly mistakes and better manage document control policies. It includes elements such as improving document management standards, establishing a document control procedure, establishing a document access policy, etc. Pitch your topic with ease and precision using this Report Best Practices For Quality Management System Graphics PDF. This layout presents information on Improve Document Management Standards, Educate Your Staff, Document Access Policy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Content Delivery Network Edge Server Why We Need Content Delivery Network Designs PDF
This slide represents the need for CDN in business which includes providing access to the data while controlling who has the authority to access the information. This is a Content Delivery Network Edge Server Why We Need Content Delivery Network Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Streaming Media, Desktop, Application. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Why We Need Content Delivery Network Ppt PowerPoint Presentation File Example File PDF
This slide represents the need for CDN in business which includes providing access to the data while controlling who has the authority to access the information. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Why We Need Content Delivery Network Ppt PowerPoint Presentation File Example File PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Distribution Network Why We Need Content Delivery Network Diagrams PDF
This slide represents the need for CDN in business which includes providing access to the data while controlling who has the authority to access the information. Presenting Distribution Network Why We Need Content Delivery Network Diagrams PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Application, Services, Content Delivery Network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Planning Transnational Technique To Improve International Scope Comparative Analysis For Evaluating Market Themes PDF
This slide covers and includes comparisons of various market entry modes. It includes parameters such as financial risks, quality control, resources access, brand control, flexibility, speed of entry, cultural fit, and ownership structure. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Planning Transnational Technique To Improve International Scope Comparative Analysis For Evaluating Market Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Action Plan Management Infrastructure Information Governance Approach Elements PDF
This is a action plan management infrastructure information governance approach elements pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like access understand, organize control, leverage take action, management objectives, legal compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
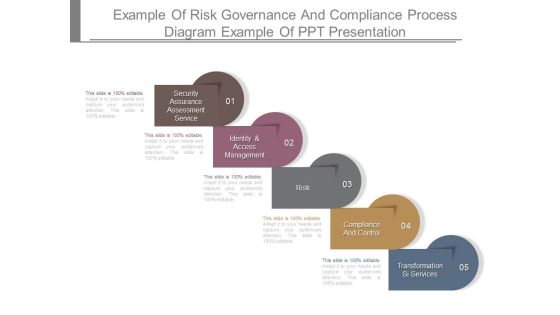
Example Of Risk Governance And Compliance Process Diagram Example Of Ppt Presentation
This is a example of risk governance and compliance process diagram example of ppt presentation. This is a five stage process. The stages in this process are security assurance assessment service, identity and access management, risk, compliance and control, transformation si services.

Canva Pro Business Profile Products Pricing With Features Template PDF
This slide highlights the Canva pro and enterprise packages prices which includes premium package, integrate and comment in real time, cloud storage, control team access and multiple brand kits. This is a Canva Pro Business Profile Products Pricing With Features Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Team Members, Designs, Social Media Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effective Franchise Marketing Strategy Franchise Website Structure Design And Branding Professional PDF
This slide provides information regarding design and branding across franchise website structure with franchise pages control, access to franchisees franchisor in terms of page performance tracking, website optimization for users, etc.This is a Effective Franchise Marketing Strategy Franchise Website Structure Design And Branding Professional PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking Franchise, Access To Franchisor, Content Interpretation You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CASB Forward Proxy Deployment Use Cases Ppt PowerPoint Presentation File Inspiration PDF
This slide highlights the main use cases of forward proxy server CASB deployment. The main purpose of this slide is to showcase the primary use cases of the forward proxy, including implementing granular access and activity controls and detecting show IT in the network. There are so many reasons you need a CASB Forward Proxy Deployment Use Cases Ppt PowerPoint Presentation File Inspiration PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Integrated Agreement Process Maturity Model Ppt PowerPoint Presentation Gallery Tips PDF
Presenting this set of slides with name integrated agreement process maturity model ppt powerpoint presentation gallery tips pdf. This is a five stage process. The stages in this process are full auto motion, perfect execution, control of language, analysis for action, accessibility and compliance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Docsend Capital Fundraising Revenue Model Ppt Infographic Template Guide PDF
This slide depicts DocSends revenue model which includes corporate branding, team control, data and API access, etc. This is a docsend capital fundraising revenue model ppt infographic template guide pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team control and features, data and api access, crm integration, advances security, corporate branding. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Docsend Capital Raising Pitch Deck Revenue Model Pictures PDF
This slide depicts DocSends revenue model which includes corporate branding, team control, data and API access, etc.Presenting Docsend Capital Raising Pitch Deck Revenue Model Pictures PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Advances Security, Corporate Branding, Team Control In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF
The following slide illustrates the seven pillars of SaaS security to protect organizations from cyber attack and data breaches. It includes elements such as access management, network control, VM management, data protection, incident management etc. Presenting Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including VM Management, Data Protection, Network Control, Perimeter Network Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Compliance Procedure Checklist Icons PDF
This slide presents information technology checklist, helpful in defining key tasks to be accomplished for successful completion of compliance process and management. It includes Access and identity control, incident response, disaster recovery, data loss prevention and protection against malware Showcasing this set of slides titled Information Technology Compliance Procedure Checklist Icons PDF. The topics addressed in these templates are Key Elements, Activities Accomplished, Status. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Franchise Website Structure Design And Branding Clipart PDF
This slide provides information regarding design and branding across franchise website structure with franchise pages control, access to franchisees franchisor in terms of page performance tracking, website optimization for users, etc. This is a Franchise Website Structure Design And Branding Clipart PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Franchise Page, Franchisor Franchisee, Information Franchises. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Franchise Marketing Plan Playbook Franchise Website Structure Design And Branding Background PDF
This slide provides information regarding design and branding across franchise website structure with franchise pages control, access to franchisees or franchisor in terms of page performance tracking, website optimization for users, etc. This is a Franchise Marketing Plan Playbook Franchise Website Structure Design And Branding Background PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Website Optimization, Information Update, Content Interpretation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Analysis Of Virtual Monitoring And Management Software Pictures PDF
This slide outlines comparative assessment of various remote monitoring and management software to assist organizations in accessing cybersecurity technical controls for any potential breaches. This slide focuses on components such as software, reviews, features, price and target audience. Showcasing this set of slides titled Comparative Analysis Of Virtual Monitoring And Management Software Pictures PDF. The topics addressed in these templates are Software, Reviews, Features, Price, Target Audience. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Administration Process To Enhance Performance Of Sales Management Project Microsoft PDF
This slide signifies the risk management plan to improve performance of sales management project. It covers information about stages like identify, assess, control, review and result. Persuade your audience using this Risk Administration Process To Enhance Performance Of Sales Management Project Microsoft PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Access, Review, Control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Map Mapping With Action Plan Ppt PowerPoint Presentation Gallery Slideshow PDF
This slide shows data inventory mapping with action plan. It provides information such as personal data, category, purpose, location, access, security controls, data duration, privacy notice, action required, etc. Persuade your audience using this Data Map Mapping With Action Plan Ppt PowerPoint Presentation Gallery Slideshow PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Security Controls, Data Storing Time, Payroll Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Process Flow Diagram Depicting Ransomware Incidents Occurrence Sample PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event. It starts with the threat actors entry and ends with the threat actor demanding ransom.Presenting Process Flow Diagram Depicting Ransomware Incidents Occurrence Sample PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Gains Access, Takes Control, Impacts Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Market Capitalisation Of Various Virtual Crypto Coinage Pictures PDF
The following slide exhibits digital fund transfer in global economy. It aims on providing access to capital and entrepreneurs getting more control of wok. It provides information related to market capitalization, international debt scenarios, etc. Presenting Market Capitalisation Of Various Virtual Crypto Coinage Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Ethereum, Ripple, Bitcoin Cash. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
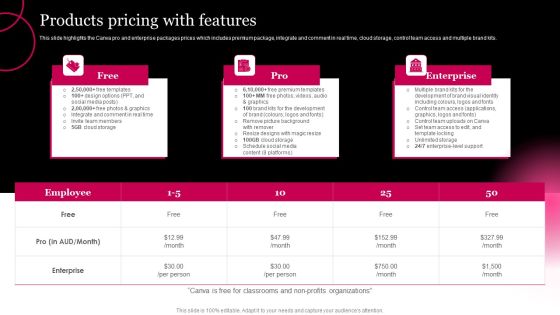
Picture Editing Company Outline Products Pricing With Features Graphics PDF
This slide highlights the Canva pro and enterprise packages prices which includes premium package, integrate and comment in real time, cloud storage, control team access and multiple brand kits. Present like a pro with Picture Editing Company Outline Products Pricing With Features Graphics PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Modern Multiple Point Of Sale System Architecture Diagram Template PDF
This Slide shows modern point of sale system architecture diagram which can be referred by backend IT team to streamline POS working. It includes information about preview, controller, hardware, tasks, data access proxy, device manager, etc. Pitch your topic with ease and precision using this Modern Multiple Point Of Sale System Architecture Diagram Template PDF. This layout presents information on Commerce Scale Unit, Data Access Proxy, Application Context Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Big Data And Analytics Framework Principles To Accelerate Strategy Professional PDF
This slide showcase principle of data and analytics architecture to gain full control over data in clear and accessible way. It includes principles such as validate data at entry point, pursue consistency, document everything and avoid duplicating Persuade your audience using this Big Data And Analytics Framework Principles To Accelerate Strategy Professional PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Entry Point, Pursue Consistency, Document Everything . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Elements Of Information Technology Security Operational Security Ppt Professional Format Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a it security elements of information technology security operational security ppt professional format ideas pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, restrict device access, implement dual control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Benefits Of An Automated Integrated Logistics Management Software Demonstration PDF
This slide shows the benefits that an automated Integrated Logistics Management Software can deliver such as increased speed and process scalability, access to real-time freight data, improved customer service, increased organizational control, provides real time updates etc. This is a benefits of an automated integrated logistics management software demonstration pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increases speed and process scalability, grants access to real time freight data, improved customer service, increased organizational control, real time updates. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

WMS Application To Increase Integrated Logistics Effectiveness Benefits Of An Automated Integrated Logistics Portrait PDF
This slide shows the benefits that an automated Integrated Logistics Management Software can deliver such as increased speed and process scalability, access to real-time freight data, improved customer service, increased organizational control, provides real time updates etc. This is a wms application to increase integrated logistics effectiveness benefits of an automated integrated logistics portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increases speed and process scalability, grants access to real time freight data, improved customer service, increased organizational control, real time updates. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Industrial Robots System Main Causes Of Industrial Robotic System Hazards Introduction PDF
This slide shows the reasons of hazards caused by industrial robots. The purpose of this slide is to explain the different types of reasons behind any accident caused due to malfunctioning of robots. These causes include human and control errors, unauthorized access, mechanical failures, improper installation, etc. Welcome to our selection of the Industrial Robots System Main Causes Of Industrial Robotic System Hazards Introduction PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Robotic Automation In Workplace Main Causes Of Industrial Robotic Hazards Designs PDF
This slide shows the reasons of hazards caused by industrial robots. The purpose of this slide is to explain the different types of reasons behind any accident caused due to malfunctioning of robots. These causes include human and control errors, unauthorized access, mechanical failures, improper installation, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Robotic Automation In Workplace Main Causes Of Industrial Robotic Hazards Designs PDF from Slidegeeks and deliver a wonderful presentation.

Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF
This slide outlines the security advantages of the platform as a service framework. It covers data governance, client endpoints, account and access management, identity and directory infrastructure, and application and network controls. Make sure to capture your audiences attention in your business displays with our gratis customizable Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Food Organization Financial Trends Voice Search Implementation Challenge Designs PDF
The slide highlights the challenges faced by food store to implement voice search for operations. It covers less product visibility, difficulty in placing large order, access to technology and lack of control. Are you searching for a Food Organization Financial Trends Voice Search Implementation Challenge Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Food Organization Financial Trends Voice Search Implementation Challenge Designs PDF from Slidegeeks today.

Strategies For Integrated Logistics Management Enhancing Order Efficiency Benefits Of An Automated Designs PDF
This slide shows the benefits that an automated Integrated Logistics Management Software can deliver such as increased speed and process scalability, access to real time freight data, improved customer service, increased organizational control, provides real time updates etc. This is a Strategies For Integrated Logistics Management Enhancing Order Efficiency Benefits Of An Automated Designs PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Scalability, Increased Organizational, Improved Customer You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Benefits Of An Automated Integrated Logistics Management Software Designs PDF
This slide shows the benefits that an automated Integrated Logistics Management Software can deliver such as increased speed and process scalability, access to real time freight data, improved customer service, increased organizational control, provides real time updates etc. Presenting benefits of an automated integrated logistics management software designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like customer service, process scalability, management, information, software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Information Security Elements Of Data Security Operational Security Ppt Icon Background Designs PDF
This slide defines the operational security element of data security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a information security elements of data security operational security ppt icon background designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like change management processes, deploy automation, plan for disaster, implement dual control, restrict device access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Sme Development Template Powerpoint Slide Deck
This is a sme development template powerpoint slide deck. This is a six stage process. The stages in this process are enhancing access to financing, building capacity and capability, to become more competitive, access to finance, access to markets, access to information.

Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Components To Enhance Processes Operational Security Element Of Cyber Security Graphics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Steps For Online Risk Management Ideas PDF
The purpose of this slide is to represent key steps in digital risk management to maintain control during a cyber attack. It includes various stages such as determining all exposed assets, drafting incident response plan, minimizing attack surface, observing all network access and continuously observing attack surface. Presenting Key Steps For Online Risk Management Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Draft Incident Response Plan, Minimize Attack Surface, Observe All Network Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Overview Of 5G Network Topology Architecture 5G Functional Architecture Background PDF
This slide represents the overview of the 5G network topology architecture and its components, such as access and mobility management, session management function, user equipment, network exposure function, network repository function, policy control function and UPF.Deliver an awe inspiring pitch with this creative Overview Of 5G Network Topology Architecture 5G Functional Architecture Background PDF bundle. Topics like Access Management, Responsible Transporting, Between Equipment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Reverse Proxy Server IT Why To Use Reverse Proxy Server Ppt Gallery Good PDF
This slide depicts why to use reverse proxy servers, including control over cyber loafing, bandwidth saving, privacy benefits, security, and access to blocked resources. Presenting reverse proxy server it why to use reverse proxy server ppt gallery good pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like employees, privacy benefits, advanced security, access to blocked, resources and websites. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer Enhanced Security System Ppt PowerPoint Presentation Show Structure
This is a computer enhanced security system ppt powerpoint presentation show structure. This is a three stage process. The stages in this process are access rights, access management, business.

User Roles And Permissions Web Admins And Editors Ppt PowerPoint Presentation Inspiration Example Topics
This is a user roles and permissions web admins and editors ppt powerpoint presentation inspiration example topics. This is a four stage process. The stages in this process are access rights, access management, business.
Sme Development Template Sample Of Ppt Presentation
This is a sme development template sample of ppt presentation. This is a four stage process. The stages in this process are investment climate, capacity building, access to markets, access to finance.

Cubeit Venture Capitalist Financing Elevator Pitch Deck Competitive Assessment Of Existing Inspiration PDF
This slide shows the competitive assessment of existing players in market on the basis of local network transfer, multiple device connectivity, file accessibility with other systems, etc.Deliver and pitch your topic in the best possible manner with this Cubeit Venture Capitalist Financing Elevator Pitch Deck Competitive Assessment Of Existing Inspiration PDF Use them to share invaluable insights on Multiple Connectivity, Accessibility Systems, Offline Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparative Assessment Of Identification Lifecycle Management Software For Identity Provisioning Rules PDF
This slide depicts identity provision and lifecycle management software with comparative analysis. It provides information about HR driven provisioning, manage access requests, regular review of access rights, streamline and automate business procedures, etc.Persuade your audience using this comparative assessment of identification lifecycle management software for identity provisioning rules pdf This PPT design covers one stage, thus making it a great tool to use. It also caters to a variety of topics including manage access requests, regular review of access rights, streamline and automate Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Mergers Acquisition Playbook Mergers Acquisition Playbook Defining The Merger Portrait PDF
Mentioned slide illustrates the primary objectives of merger and acquisition. It shows that businesses go for a merger or acquisition to eliminate competition, synergies, gain access to new markets or access to intangible assets.This is a Mergers Acquisition Playbook Mergers Acquisition Playbook Defining The Merger Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access To Intangible Assets, Eliminate Competition, Gain Access To New Markets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Techniques To Enhance Cost Efficiency Multiple Stages Of Project Cost Management Sample PDF
The slide illustrates the steps of project cost management to plan and control the business expenses. Various stages involved are project resource planning, cost estimation, cost budgeting and cost control for effective project cost management Retrieve professionally designed Key Techniques To Enhance Cost Efficiency Multiple Stages Of Project Cost Management Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Design Software Playbook Engineers Software Development Inspiration PDF
This template covers software development source control rules. It also includes source control process such as branching, committing code, pull request, merge into master and release branch.Retrieve professionally designed Design Software Playbook Engineers Software Development Inspiration PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
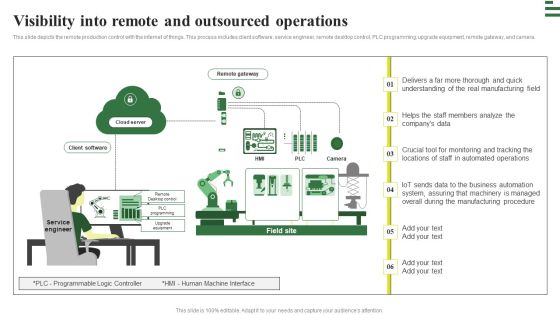
Transforming Manufacturing With Automation Visibility Into Remote And Outsourced Guidelines PDF
This slide depicts the remote production control with the internet of things. This process includes client software, service engineer, remote desktop control, PLC programming, upgrade equipment, remote gateway, and camera. Retrieve professionally designed Transforming Manufacturing With Automation Visibility Into Remote And Outsourced Guidelines PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Benefits Of Effective Inventory Planning And Management Ppt PowerPoint Presentation Show Elements PDF
Persuade your audience using this benefits of effective inventory planning and management ppt powerpoint presentation show elements pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Increase customer demand, product availability improved, Improved quality control with on time product delivery, Better collaboration with improved access of data to supply chain leaders, Helps in Identifying the most efficient shipping methods to optimize shipping experience. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Internet Security Threats Management Framework Icons PDF
This slide exhibits data breach risk management model. It includes major evaluation criteria such as- does the management has two unique credentials to perform administer activities, does the multifactor authentication is enabled for administrative access etc. Showcasing this set of slides titled internet security threats management framework icons pdf. The topics addressed in these templates are asset, control topic, evaluation questions, response, threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Areas Of Report Software Use For Quality Management System Rules PDF
This slide highlights the usage of document control software for quality management. The purpose is to save time, effort, and cost. It includes access management and security, version management, collaboration, swift search, optimization techniques, reporting, and audit trails, and archiving. Presenting Areas Of Report Software Use For Quality Management System Rules PDF to dispense important information. This template comprises Seven stages. It also presents valuable insights into the topics including Version Management, Optimization Techniques, Reporting And Audit Trails. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF
The following slide shows dashboard of CPM cyber security program management which helps to access high value assets and check threats , risks and policies on one platform. It includes current threat postures, risks, policy, service breakdown, assets by category and their control issues. Pitch your topic with ease and precision using this Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF. This layout presents information on Cyber Security, Program Management Dashboard, Kpi Metrics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

5G Network Applications And Features Overview Of 5G Network Topology Architecture Mockup PDF
This slide represents the overview of the 5G network topology architecture and its components, such as access and mobility management, session management function, user equipment, network exposure function, network repository function, policy control function and UPF. Want to ace your presentation in front of a live audience Our 5G Network Applications And Features Overview Of 5G Network Topology Architecture Mockup PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Why To Use Reverse Proxy Server Reverse Proxy For Load Balancing Clipart PDF
This slide depicts why to use reverse proxy servers, including control over cyber loafing, bandwidth saving, privacy benefits, security, and access to blocked resources.Presenting Why To Use Reverse Proxy Server Reverse Proxy For Load Balancing Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Provide Load, Application Firewalls, Delivery Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Closed Loop Supply Chain Management End To End Returns Management Automation Ppt Professional PDF
Presenting this set of slides with name closed loop supply chain management end to end returns management automation ppt professional pdf. The topics discussed in these slides are accessing real time returns data, real time access to material, smooth flow across value chain. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
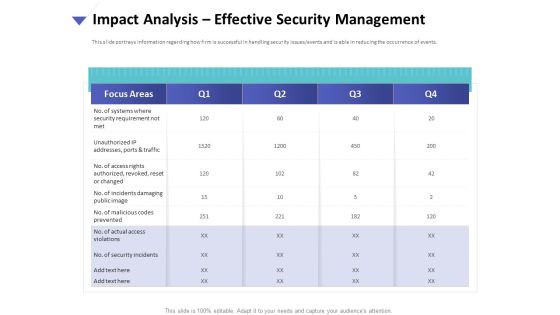
Strategies To Mitigate Cyber Security Risks Impact Analysis Effective Security Management Introduction PDF
Presenting this set of slides with name strategies to mitigate cyber security risks impact analysis effective security management introduction pdf. The topics discussed in these slides are focus areas, security requirement, access rights authorized, incidents damaging, actual access violations. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Pitch Deck For Raising Funds From Product Crowdsourcing Competitive Analysis Related To Product Features Template PDF
Presenting this set of slides with name pitch deck for raising funds from product crowdsourcing competitive analysis related to product features template pdf. The topics discussed in these slides are broader range of colors, dual remote accessibility, sound quality, access to social media, onboarding experience. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
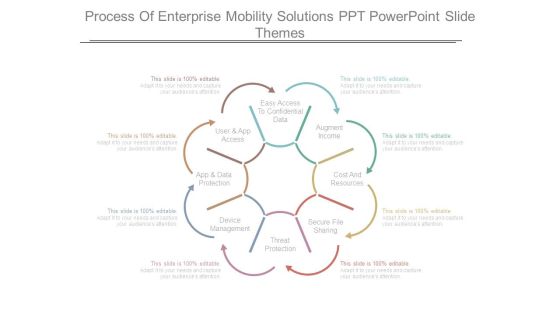
Process Of Enterprise Mobility Solutions Ppt Powerpoint Slide Themes
This is a process of enterprise mobility solutions ppt powerpoint slide themes. This is a eight stage process. The stages in this process are user and app access, app and data protection, device management, threat protection, secure file sharing, cost and resources, augment income, easy access to confidential data.

Business Capital Network Alliance Powerpoint Show
This is a business capital network alliance powerpoint show. This is a nine stage process. The stages in this process are access to capital, growth and expansion, contract award, contract performance, job creation, access to capital, contract award, contract bidding, business development.

Nurturing The Start Up Ecosystem Diagram Ppt Example
This is a nurturing the start up ecosystem diagram ppt example. This is a six stage process. The stages in this process are access to market, entrepreneurial network and mentoring, access to finance, innovation, business environment and support, culture human capital and education.
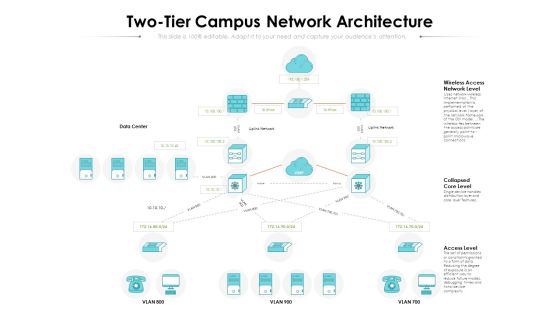
Two Tier Campus Network Architecture Ppt PowerPoint Presentation Model Inspiration PDF
Presenting this set of slides with name two tier campus network architecture ppt powerpoint presentation model inspiration pdf. This is a one stage process. The stages in this process are wireless access network level, collapsed, core level, access level, data center. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF
The following slide illustrates practices to protect sensitive data in cloud infrastructure that comply with many standards, law and regulations. It presents information related to securing access to cloud, monitoring privileged users,etc. Presenting Best Practices To Protect Data In Cloud Infra Cyber Security Designs PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Secure Access Cloud, Manage User Access Privileges, Provide Visibility Employee. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF. Use them to share invaluable insights on Formulate Network, Access Rules, Particular Applications, Bandwidth Access Limitation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

5G Architecture As Per 5G New Radio Nr Standard 5G Functional Architecture Mockup PDF
This slide depicts the 5G architecture as per the 5G NR standard. It includes the components such as access and mobility management function, user plane function, next generation radio access network, next generation base station and 5G core.Deliver and pitch your topic in the best possible manner with this 5G Architecture As Per 5G New Radio Nr Standard 5G Functional Architecture Mockup PDF. Use them to share invaluable insights on protocol terminations, management function, access mobility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Knowledge Management Challenges Template Backgrounds Template
This is a knowledge management challenges template backgrounds template. This is a six stage process. The stages in this process are access to experts, talent management, organization, people, knowledge process, knowledge strategy, basic concepts.

Knowledge Management Challenges Template Ppt Inspiration
This is a knowledge management challenges template ppt inspiration. This is a eight stage process. The stages in this process are effectiveness, performance support, access to experts, social networking and collaboration, knowledge management, relevance, structured learning, organization.

International Human Resources Management Example Of Ppt
This is an international human resources management example of ppt. This is a four stage process. The stages in this process are global competition, international mergers and acquisitions, foreign human resources, market access opportunities.

Reputation Management Example Diagram Powerpoint Layout
This is a reputation management example diagram powerpoint layout. This is a five stage process. The stages in this process are start building, create a reputation strategy, determine your best, identity changes needed, access your current reputation.
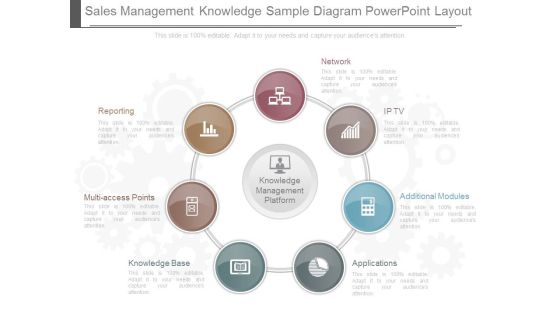
Sales Management Knowledge Sample Diagram Powerpoint Layout
This is a sales management knowledge sample diagram powerpoint layout. This is a seven stage process. The stages in this process are network, ip tv, additional modules, applications, knowledge base, multi access points, reporting.

Small Business Management Diagram Presentation Pictures
This is a small business management diagram presentation pictures. This is a seven stage process. The stages in this process are output and exports, taxes govt revenues, poverty alleviation, youth entrepreneurship, networks mentoring and coaching, supportive environment, access to capital.

Concept Of Inclusion And Ways To Ensure It In Offices Training Ppt
This slide explains the meaning of Inclusion. It is the process of ensuring that all people have equal access to opportunities and resources. It also mentions strategies to ensure inclusion in the workplace.

Financial Strategies For Business Growth Ppt Slides
This is a financial strategies for business growth ppt slides. This is a four stage process. The stages in this process are reeducation of finance cost, access to finance, increased cash flow, financial management, strategic planning and growth.

Merger And Acquisition Due Diligence Why We Need To Merge With Or Acquire Other Business Information PDF
Following slide illustrates the importance of merging with or acquiring any other business. Businesses go for a merger or acquisition on order to eliminate competition, synergies, gain access to new markets or access to intangible assets. Presenting merger and acquisition due diligence why we need to merge with or acquire other business information pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like eliminate competition, synergies, gain access to new markets, access to intangible assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Learning Solutions Layout Powerpoint Shapes
This is a learning solutions layout powerpoint shapes. This is a six stage process. The stages in this process are structured learning, management, organization, learning solutions layout, social networking and collaboration, performance support, access to experts.
Mobile With Fingerprint Scanner Vector Icon Ppt Powerpoint Presentation Outline Slide
This is a mobile with fingerprint scanner vector icon ppt powerpoint presentation outline slide. This is a four stage process. The stages in this process are password, access approval, authentication icon.
Due Diligence Process In Merger And Acquisition Agreement Why We Need To Merge Structure PDF
Following slide illustrates the importance of merging with or acquiring any other business. Businesses go for a merger or acquisition on order to eliminate competition, synergies, gain access to new markets or access to intangible assets. This is a due diligence process in merger and acquisition agreement why we need to merge structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like eliminate competition, gain access to new markets, access to intangible assets You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Revenue Lifecycle Business Template Powerpoint Templates
This is a revenue lifecycle business template powerpoint templates. This is a five stage process. The stages in this process are total costs, change capture, patient access management, variable costs, fixed costs.

Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home