Access Control

Information Technology Security Threat Mitigation Strategies Formats PDF
The slide covers strategies to prevent IT security threats for reducing overall impact of risks or attacks on business. It includes four strategies such as risk assessment, network access control, incident response plan and regular network traffic monitoring. Persuade your audience using this Information Technology Security Threat Mitigation Strategies Formats PDF. This PPT design covers Four stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Assessment, Network Access Controls, Incident Response Plan. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
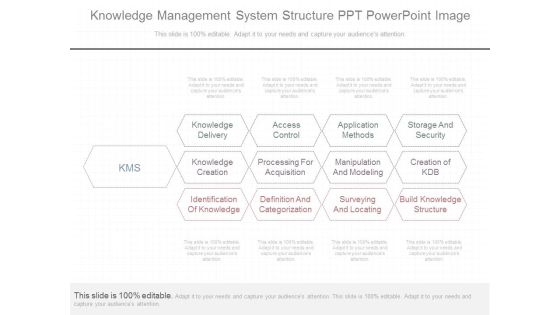
Knowledge Management System Structure Ppt Powerpoint Image
This is a knowledge management system structure ppt powerpoint image. This is a three stage process. The stages in this process are knowledge delivery, access control, application methods, storage and security, knowledge creation, processing for acquisition, manipulation and modeling, creation of kdb, identification of knowledge, definition and categorization, surveying and locating, build knowledge structure, kms.

Chart Showing Comparison Of Database Systems Ppt PowerPoint Presentation Portfolio Styles
Presenting this set of slides with name chart showing comparison of database systems ppt powerpoint presentation portfolio styles. The topics discussed in these slides are price in usd, basic, professional, premium, data functionality features, data backup and recovery, multiuser access control, minimum duplication and redundancy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
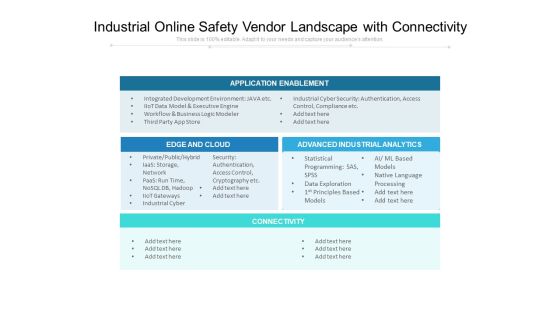
Industrial Online Safety Vendor Landscape With Connectivity Ppt PowerPoint Presentation Infographic Template Graphics Download PDF
Showcasing this set of slides titled industrial online safety vendor landscape with connectivity ppt powerpoint presentation infographic template graphics download pdf. The topics addressed in these templates are network, security,authentication, access control, cryptography, processing, business, analytics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Governance Building Blocks Ppt PowerPoint Presentation Gallery Inspiration PDF
Presenting this set of slides with name data governance building blocks ppt powerpoint presentation gallery inspiration pdf. This is a three stage process. The stages in this process are ownership, classification, access control. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Company Vulnerability Administration Record Discovered Vulnerabilities Ideas PDF
Presenting company vulnerability administration record discovered vulnerabilities ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like discovery date and time, categorization, affected assets, priority assure access control of the repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Complete IT Security IT Implementation Checklist Ppt Diagrams PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Deliver an awe inspiring pitch with this creative complete it security it implementation checklist ppt diagrams pdf bundle. Topics like training, antivirus software, secure communications, access control measures, device security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

RBAC Variations For Different Organizational Levels Summary PDF
This slide shows the role based access control variations organized as levels. It includes details related to name of different levels od RBAC along with their functional capabilities. Showcasing this set of slides titled RBAC Variations For Different Organizational Levels Summary PDF. The topics addressed in these templates are RBAC Variations, Different Organizational Levels. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Benefits Of Report Software For Life Science Quality Management System Summary PDF
This slide highlights the advantage of document control software for life science quality management system. It includes authoring, review, approval, access controls, audit trails, alerts and notifications, reporting capabilities, secure cloud storage, version control, etc. Presenting Benefits Of Report Software For Life Science Quality Management System Summary PDF to dispense important information. This template comprises Ten stages. It also presents valuable insights into the topics including Reporting Capabilities, Secure Cloud Storage, Version Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
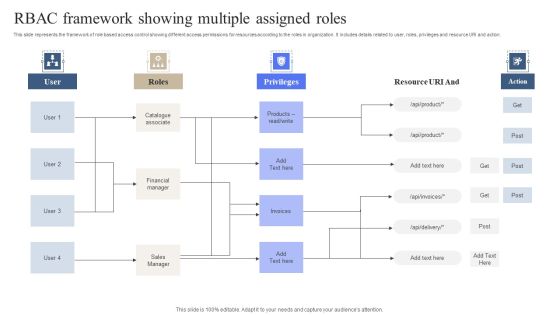
RBAC Framework Showing Multiple Assigned Roles Download PDF
This slide represents the framework of role based access control showing different access permissions for resources according to the roles in organization. It includes details related to user, roles, privileges and resource URI and action. Pitch your topic with ease and precision using this RBAC Framework Showing Multiple Assigned Roles Download PDF. This layout presents information on Catalogue Associate, Financial Manager, Sales Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Business Information Protection Methodologies For Organizational Facilities Demonstration PDF
This slide covers business security methodologies for organizational facilities which are security plan documentation, access control, installing surveillance system and reinforce data security.Presenting Business Information Protection Methodologies For Organizational Facilities Demonstration PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Plan Documentation, Implement Access, Surveillance System. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a Cloud Information Security Zero Trust Policy And Why You Should Embrace IT Ppt File Outfit PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Device, Validation Network, Restrict Access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Zero Trust Policy And Why You Should Embrace It Cloud Computing Security IT Ppt Infographics Gridlines PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a zero trust policy and why you should embrace it cloud computing security it ppt infographics gridlines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication, device validation, restrict access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Network Operations 5G Protocol Layers Mapped With OSI Stack Topics PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C-Plane protocol stack, and so on. There are so many reasons you need a 5G Network Operations 5G Protocol Layers Mapped With OSI Stack Topics PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

5G Network Applications And Features 5G NR Radio Protocol Stack Architecture Topics PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C-Plane protocol stack, and so on. Make sure to capture your audiences attention in your business displays with our gratis customizable 5G Network Applications And Features 5G NR Radio Protocol Stack Architecture Topics PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

5G Nr Radio Protocol Stack Architecture 5G Functional Architecture Structure PDF
This slide represents the overview of the 5G radio protocol stack architecture, and it includes service data adaptation protocol, packet data convergence protocol, radio link control, media access control address, PHY, NAS, RRC, UE, Gnb, AMF, C Plane protocol stack, and so on.Deliver and pitch your topic in the best possible manner with this 5G Nr Radio Protocol Stack Architecture 5G Functional Architecture Structure PDF. Use them to share invaluable insights on protocol stack includes, data processes, information travels and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Project Assistance Templates Bundle Application Users Ppt Inspiration Demonstration PDF
Deliver and pitch your topic in the best possible manner with this Project Assistance Templates Bundle Application Users Ppt Inspiration Demonstration PDF. Use them to share invaluable insights on Access Settings, Control Center, Activation Pending and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
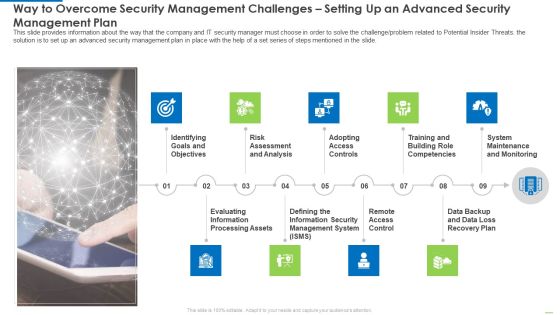
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Introduction PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide.This is a way to overcome security management challenges setting up an advanced security management plan introduction pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment and analysis, adopting access controls, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
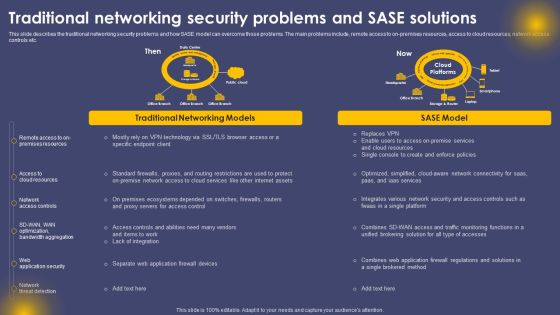
Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.
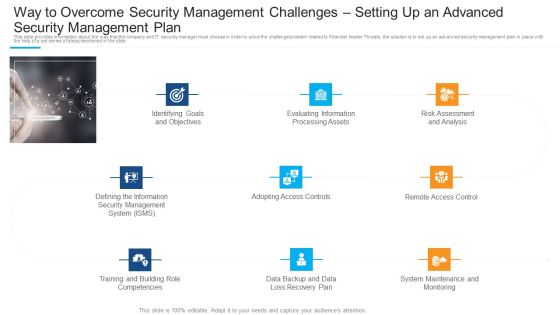
Way To Overcome Security Management Challenges Setting Up An Advanced Security Management Plan Pictures PDF
Presenting way to overcome security management challenges setting up an advanced security management plan pictures pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, evaluating information processing assets, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Machine To Machine Communication Outline Iot Security Challenges Ppt File Background Designs PDF
The slide highlights key Challenges in IoT security. Presenting machine to machine communication outline iot security challenges ppt file background designs pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like authentication, access control, privacy, policy enforcement, trust, mobile security, secure middleware, confidentiality. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Circular Process For Enterprise Resource Planning With Data Services Ppt PowerPoint Presentation Infographics Ideas PDF
Persuade your audience using this circular process for enterprise resource planning with data services ppt powerpoint presentation infographics ideas pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including finance accounting, human resources, engineering, purchasing, project management, crm, data services, access control. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Techniques And Strategies To Reduce Security Management Risks Table Of Contents Structure PDF
Presenting techniques and strategies to reduce security management risks table of contents structure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like identifying goals and objectives, risk assessment and analysis, adopting access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF
This slide shows how we can build a successful cloud security strategy. It explains about data privacy, keeping access control, responsibilities of cloud and providing training.Presenting How To Build A Successful Cloud Management Action Plan Security Strategy Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security, Enterprise, Data Privacy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly Internet Defence Protection Evolution And Metrics Roadmap Sample PDF
This slide exhibits quarterly based cybersecurity roadmap showcasing evolution and metrics such as access control, vulnerability management, assessment and testing etc.Presenting Quarterly Internet Defence Protection Evolution And Metrics Roadmap Sample PDF to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including Auditing Documentation, Penetration Test, Administrative Privileges. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Improve IT Service Desk Pre Deployment Audit Checklist For Service Desk Tool Icons PDF
The following slide showcases audit checklist for deploying service desk tool. It provides information about usability, customization, integration, access control, encryption, quick issue resolution, automation, etc.Deliver and pitch your topic in the best possible manner with this Improve IT Service Desk Pre Deployment Audit Checklist For Service Desk Tool Icons PDF. Use them to share invaluable insights on Customizable Integrable, Operational Automation, Service Desk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF. Use them to share invaluable insights on Cloud Frameworks, Information Division, Cautious Scaling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Agency Business Profile Corporate And Industrial Security Services Information PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Corporate And Industrial Security Services Information PDF. Use them to share invaluable insights on Corporate Security, Industrial Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Corporate And Industrial Security Services Designs PDF bundle. Topics like Corporate Security, Industrial Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web App Firewall Services IT Web Application Firewall With Traditional Firewall Professional PDF
This slide represents the difference between a web application firewall and a traditional firewall based on functionality, implementation, threat prevention, OSI layers, and access control. Deliver an awe inspiring pitch with this creative web app firewall services it web application firewall with traditional firewall professional pdf bundle. Topics like organization, applications, implementation, networks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Web Application Firewall With Traditional Firewall WAF Platform Summary PDF
This slide represents the difference between a web application firewall and a traditional firewall based on functionality, implementation, threat prevention, OSI layers, and access control. Deliver and pitch your topic in the best possible manner with this Web Application Firewall With Traditional Firewall WAF Platform Summary PDF. Use them to share invaluable insights on Network, Applications, Data Protection and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
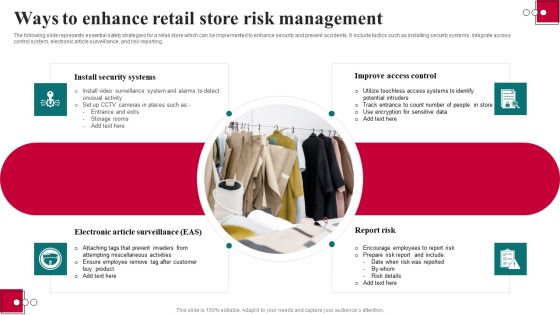
Ways To Enhance Retail Store Risk Management Introduction PDF
The following slide represents essential safety strategies for a retail store which can be implemented to enhance security and prevent accidents. It include tactics such as installing security systems, integrate access control system, electronic article surveillance, and risk reporting. Pitch your topic with ease and precision using this Ways To Enhance Retail Store Risk Management Introduction PDF. This layout presents information on Electronic Article Surveillance, Report Risk, Install Security Systems. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

High Level Hyperledger Architecture For Blockchain Creation Involving Cryptographic Ledger To Enhance Topics PDF
This slide depicts the high-level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Present like a pro with High Level Hyperledger Architecture For Blockchain Creation Involving Cryptographic Ledger To Enhance Topics PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Overview For Configuration Management Database With Characteristics Microsoft PDF
This slide represents meaning of CMDB Configuration Management Database with its key characteristics. It covers details regarding asset configuration, dashboards, access control etc. Present like a pro with Overview For Configuration Management Database With Characteristics Microsoft PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
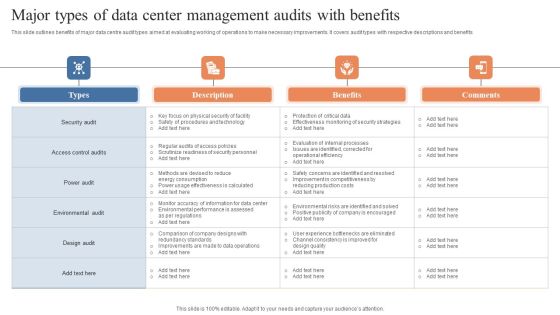
Major Types Of Data Center Management Audits With Benefits Pictures PDF
This slide outlines benefits of major data centre audit types aimed at evaluating working of operations to make necessary improvements. It covers audit types with respective descriptions and benefits. Showcasing this set of slides titled Major Types Of Data Center Management Audits With Benefits Pictures PDF. The topics addressed in these templates are Security Audit, Access Control Audits, Power Audit . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Execution Of ICT Strategic Plan Selection For Cloud Management Platform Tools Summary PDF
This slide represents selection for cloud management tools. It covers asset inventory management, workflow automation, security, access control etc. Want to ace your presentation in front of a live audience Our Execution Of ICT Strategic Plan Selection For Cloud Management Platform Tools Summary PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

IT Security Complete IT Security Implementation Checklist Ppt Layouts Graphics PDF
This slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Presenting complete information technology security implementation checklist ppt file introduction pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like secure communications, device security, access control measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. The Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Blockchain Technology Framework IT High Level Hyperledger Architecture For Blockchain Creation Rules PDF
This slide depicts the high level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Presenting blockchain technology framework it high level hyperledger architecture for blockchain creation rules pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like high level hyperledger architecture for blockchain creation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
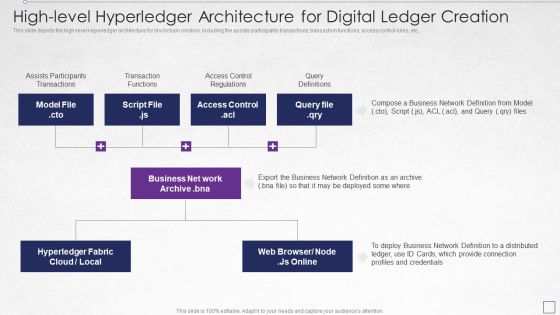
Digitized Record Book Technology High Level Hyperledger Architecture Information PDF
This slide depicts the high level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Presenting digitized record book technology high level hyperledger architecture information pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high level hyperledger architecture for digital ledger creation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF
This slide represents the zero trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy.This is a Cloud Security Assessment Zero Trust Policy And Why You Should Embrace It Designs PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Best Example, Authentication, Implement Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Benefits Of RBAC For Companies And Employees Introduction PDF
This slide represents the role based access control benefits for both the companies and the employees. It includes benefits of RBAC for company such as reduced costs, improvement in security, better compliance and reporting capabilities etc. Showcasing this set of slides titled Key Benefits Of RBAC For Companies And Employees Introduction PDF. The topics addressed in these templates are Benefits For Company, Benefits For Employees. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. This is a Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Article Surveillance, Install Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

DLT Technology High Level Hyperledger Architecture For Blockchain Creation Topics PDF
This slide depicts the high-level Hyperledger architecture for blockchain creation, including the assists participants transactions, transaction functions, access control rules, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward DLT Technology High Level Hyperledger Architecture For Blockchain Creation Topics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal DLT Technology High Level Hyperledger Architecture For Blockchain Creation Topics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
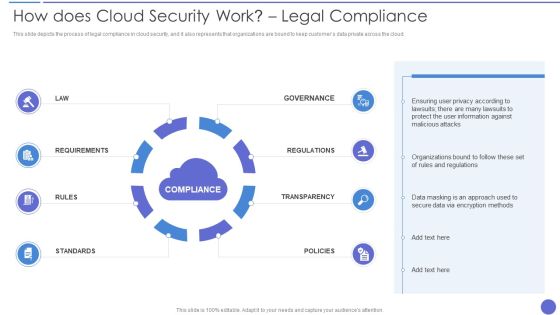
How Does Cloud Security Work Legal Compliance Background PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting How Does Cloud Security Work Legal Compliance Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Authorization, Authentication, Access Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Trending Features Of Ai In Technological Smart Homes Products Background PDF
This side showcase the features of artificial intelligence for power efficiency, time saving alerts, evolved smart appliances in smart homes. It include the features such as smart security, controlled power, energy saving, better device functioning and better user experience. Presenting Trending Features Of Ai In Technological Smart Homes Products Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Smart Security Access Control, Energy Saving Right Utilization, Better Device Functioning. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Comparative Assessment For Brand Element Management Software Slides PDF
This slide signifies the comparative assessment of different of different softwares on brand asset management. It includes features like asset creation, indexing, accessing control, collaboration and distribution. Showcasing this set of slides titled Comparative Assessment For Brand Element Management Software Slides PDF. The topics addressed in these templates are User Friendly Interface, Indexing, Storage Digital Assets. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
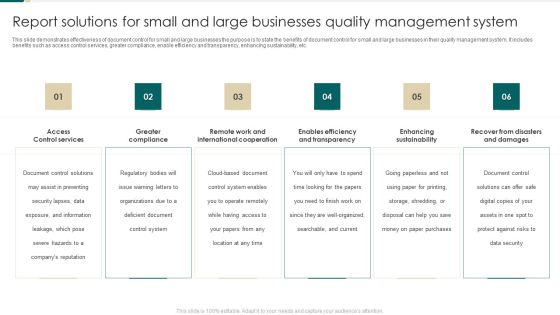
Report Solutions For Small And Large Businesses Quality Management System Guidelines PDF
This slide demonstrates effectiveness of document control for small and large businesses the purpose is to state the benefits of document control for small and large businesses in their quality management system. It includes benefits such as access control services, greater compliance, enable efficiency and transparency, enhancing sustainability, etc. Persuade your audience using this Report Solutions For Small And Large Businesses Quality Management System Guidelines PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Control Services, Greater Compliance, Enables Efficiency And Transparency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
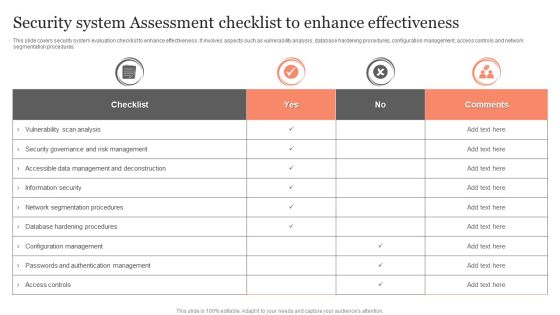
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Components Of Customer Server Network Architecture Professional PDF
This slide contains components which makes it easier to protect database with access controls imposed by security policies. The main components includes workstations, network devices and server Persuade your audience using this Components Of Customer Server Network Architecture Professional PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Workstations, Network Devices, Servers . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF
This slide shows framework which can be used by organizations to develop cloud security for data protection. It includes authentication, access control, user behavior analytics, logging an reporting, etc. Persuade your audience using this Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF. This PPT design covers Eight stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Framework, To Ensure Data Safety . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Global Cyber Terrorism Incidents On The Rise IT Techniques To Protect SCADA Elements PDF
This slide depicts the techniques to protect SCADA from cyber-attacks which include security training of employees, strict firewalls. This is a global cyber terrorism incidents on the rise it techniques to protect scada elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security training of employee, access controls, strict firewalls, network security procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF
This slide highlights the industrial and corporate security services by manpower security company which includes administer electronic access control, respond to alarms, visitor pass management and patrol inside the factory. Presenting Security Officer Service Company Profile Corporate And Industrial Security Services Demonstration PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Corporate Security, Industrial Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home