Access Control
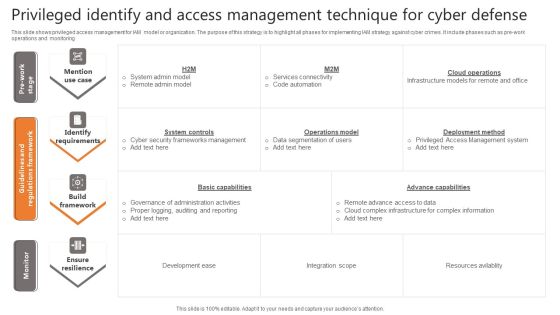
Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF
This slide shows privileged access management for IAM model or organization. The purpose of this strategy is to highlight all phases for implementing IAM strategy against cyber crimes. It include phases such as pre work operations and monitoring Pitch your topic with ease and precision using this Privileged Identify And Access Management Technique For Cyber Defense Infographics PDF. This layout presents information on Identify Requirements, Build Framework, Ensure Resilience. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

5G Network Applications And Features Multi Access Edge Computing MEC Overview Microsoft PDF
This slide represents the overview of multi-access edge computing, including its characteristics, such as low latency, high bandwidth, and real-time access to RAN. This method eliminates the lengthy network channel that separates the user and host while transferring data. Boost your pitch with our creative 5G Network Applications And Features Multi Access Edge Computing MEC Overview Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you dont have to invest time in any additional work. Just grab the template now and use them.

Open Radio Access Network IT How Is Open RAN Important To 5G Telecommunication System Sample PDF
This slide depicts the importance of an open random access network to a 5G telecommunication system. It will help the 5G system widen the range and cut the CapEx of telecoms. Want to ace your presentation in front of a live audience Our Open Radio Access Network IT How Is Open RAN Important To 5G Telecommunication System Sample PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF
This slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Create an editable Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Benefits Of Cloud Access Security Broker 2 0 Ppt PowerPoint Presentation File Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Types Of Zero Trust Network Access ZTNA Models Ppt Portfolio Example Topics PDF
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Types Of Zero Trust Network Access ZTNA Models Ppt Portfolio Example Topics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Business Objectives Of Implementing Identify And Access Management Technique Clipart PDF
This slide shows business goals that can be achieved by identification and access management strategy by systematically implementing concerned business activities. It include objectives such as security system, business verticals integration , etc. Showcasing this set of slides titled Business Objectives Of Implementing Identify And Access Management Technique Clipart PDF. The topics addressed in these templates are Business Activities, Impact, Objective. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
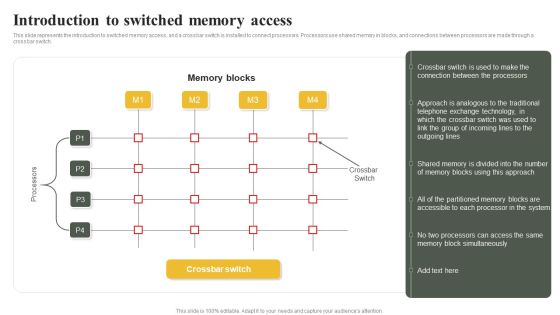
Parallel Computing System To Enhance Process Efficiency Introduction To Switched Memory Access Template PDF
This slide represents the introduction to switched memory access, and a crossbar switch is installed to connect processors. Processors use shared memory in blocks, and connections between processors are made through a crossbar switch. There are so many reasons you need a Parallel Computing System To Enhance Process Efficiency Introduction To Switched Memory Access Template PDF. The first reason is you can notspend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Information Security Monitor Access To Sensitive And Regulated Data Structure PDF
This slide explains we help you with data privacy by monitoring access of sensitive and regulated data, in which automation engine assists you in achieving the least privilege and compliance faster. The Information Security Monitor Access To Sensitive And Regulated Data Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. This Cloud Access Security Broker Use Cases Ppt PowerPoint Presentation File Background Images PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF
This slide depicts privacy and company access to workers personal devices. It is stated that organizations have the right to analyze personal and work-related data during an emergency. Want to ace your presentation in front of a live audience Our Cybersecurity Guidelines IT Privacy And Company Access To Personal Devices Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
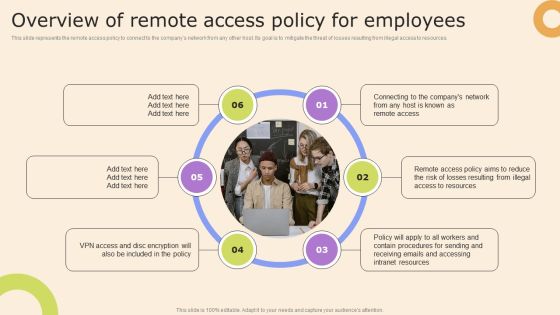
Information Technology Policy And Processes Overview Of Remote Access Policy For Employees Structure PDF
This slide represents the remote access policy to connect to the companys network from any other host. Its goal is to mitigate the threat of losses resulting from illegal access to resources. The Information Technology Policy And Processes Overview Of Remote Access Policy For Employees Structure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

5G Network Technology Determine Identity And Access Management With 5G Ppt Inspiration Outfit PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. This is a 5g network technology determine identity and access management with 5g ppt inspiration outfit pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 5g identifiers, 5g authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. This is a Developing 5G Wireless Cellular Network Determine Identity And Access Management With 5G Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 5G Identifiers, 5G Authentication . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Technology Development For Digital Transformation Determine Identity And Access Management With 5G Background PDF
This slide provides details regarding identity and access management with 5G in terms of 5G identifiers and 5G authentication. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download 5G Technology Development For Digital Transformation Determine Identity And Access Management With 5G Background PDF from Slidegeeks and deliver a wonderful presentation.

Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. There are so many reasons you need a Best Practices To Implement Cloud Access Security Broker Ppt Portfolio Influencers PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Open Radio Access Network IT Terminologies Used For Open RAN Rules PDF
This slide depicts the terminologies used for O RAN in an open random access network. O RAN is used for Alliance, ORAN is referred to as the open RAN movement, and oRAN or ORAN is used on social media for O RAN alliance. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Open Radio Access Network IT Terminologies Used For Open RAN Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Open Radio Access Network IT Terminologies Used For Open RAN Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
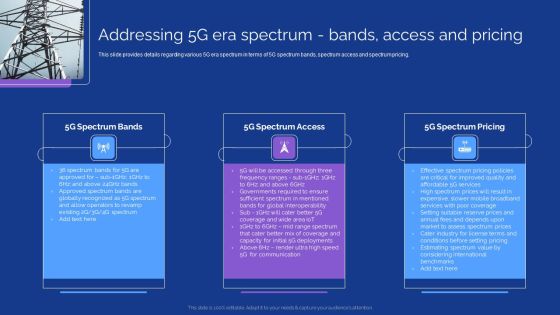
Development Guide For 5G World Addressing 5G Era Spectrum Bands Access And Pricing Graphics PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. Boost your pitch with our creative Development Guide For 5G World Addressing 5G Era Spectrum Bands Access And Pricing Graphics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Open Radio Access Network IT Key Components Of Open RAN O RAN Ideas PDF
This slide represents the key components of an open random access network, including cloudification, intelligence and automation, and open internal RAN interfaces. Cloudification includes the separation of hardware and software and to use of RAN apps as cloud-native functions. There are so many reasons you need a Open Radio Access Network IT Key Components Of Open RAN O RAN Ideas PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Cognitive Sensing Innovation Comparison Of Cognitive Radio Access Paradigms Infographics PDF
This slide describes the comparison between different cognitive radio access paradigms, such as underlay, overlay, and interweave. The difference is based on network side information, simultaneous transmission, transmit power limits, and hardware. If you are looking for a format to display your unique thoughts, then the professionally designed Cognitive Sensing Innovation Comparison Of Cognitive Radio Access Paradigms Infographics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cognitive Sensing Innovation Comparison Of Cognitive Radio Access Paradigms Infographics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
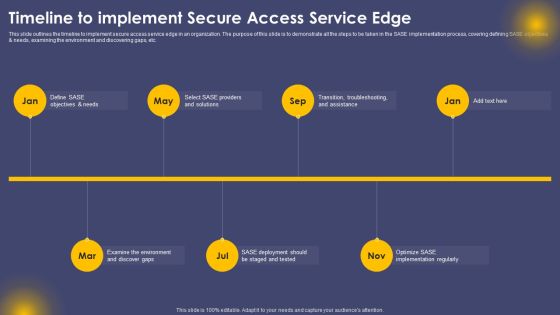
Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF
This slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Find highly impressive Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Timeline To Implement Secure Access Service Edge Ppt Infographics Display PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
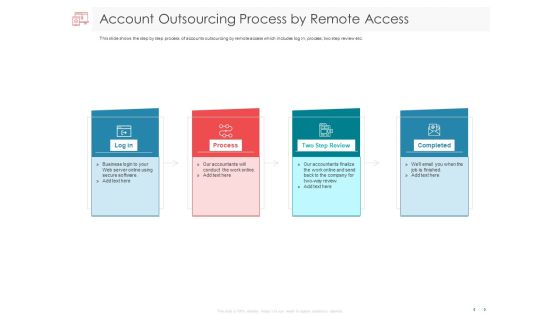
Managing CFO Services Account Outsourcing Process By Remote Access Ppt Model Designs Download PDF
Presenting this set of slides with name managing cfo services account outsourcing process by remote access ppt model designs download pdf. This is a four stage process. The stages in this process are log in, process, two step review, completed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

BPO Managing Enterprise Financial Transactions Account Outsourcing Process By Remote Access Demonstration PDF
Presenting this set of slides with name bpo managing enterprise financial transactions account outsourcing process by remote access demonstration pdf. This is a four stage process. The stages in this process are log in, process, two step review, completed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF
This slide describes the comparison between different cognitive radio access paradigms, such as underlay, overlay, and interweave. The difference is based on network side information, simultaneous transmission, transmit power limits, and hardware. Get a simple yet stunning designed Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cognitive Sensor Network Comparison Of Cognitive Radio Access Paradigms Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.

Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.

5G Technology Development For Digital Transformation Addressing 5G Era Spectrum Bands Access And Pricing Designs PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. Find a pre designed and impeccable 5G Technology Development For Digital Transformation Addressing 5G Era Spectrum Bands Access And Pricing Designs PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Open Radio Access Network IT What Is The Current Status Of Open RAN Structure PDF
This slide talks about the current status of open random access networks, which are gaining popularity and adopted by many telecom operators such as Vodafone, and Rakuten Mobile. The third pillar, disaggregation, makes it in demand. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Open Radio Access Network IT What Is The Current Status Of Open RAN Structure PDF from Slidegeeks and deliver a wonderful presentation.

Data Preparation Infrastructure And Phases Data Preparation Process Step 2 Discover And Access Data Brochure PDF
This slide shows the second step that is involved in the data preparation process i.e. discover and access data along with the details.Presenting Data Preparation Infrastructure And Phases Data Preparation Process Step 2 Discover And Access Data Brochure PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Preparation Process, Existing Catalogue, Analysts Aware In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Preparation Process Step 2 Discover And Access Data Topics PDF
This slide shows the second step that is involved in the data preparation process i.e. discover and access data along with the details.This is a Data Preparation Process Step 2 Discover And Access Data Topics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Important To Discover, Collection Of Datasets, Data And Learning You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Empowering Organization With Zero Trust Network Access Topics PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Agenda For Empowering Organization With Zero Trust Network Access Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Agenda For Empowering Organization With Zero Trust Network Access Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Get a simple yet stunning designed Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Outsourcing Of Finance And Accounting Processes Account Outsourcing Process By Remote Access Diagrams PDF
Presenting this set of slides with name outsourcing of finance and accounting processes account outsourcing process by remote access diagrams pdf. This is a four stage process. The stages in this process are log in, process, two step review, completed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
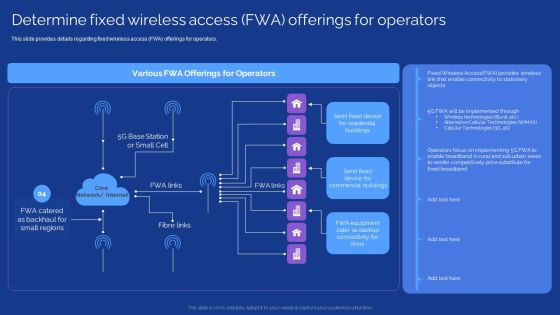
Development Guide For 5G World Determine Fixed Wireless Access FWA Offerings For Operators Pictures PDF
This slide provides details regarding fixed wireless access FWA offerings for operators. If you are looking for a format to display your unique thoughts, then the professionally designed Development Guide For 5G World Determine Fixed Wireless Access FWA Offerings For Operators Pictures PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Development Guide For 5G World Determine Fixed Wireless Access FWA Offerings For Operators Pictures PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Open Radio Access Network IT Three Main Pillars Of Open RAN Information PDF
This slide depicts the three main pillars of open random access networks, including O-RAN, virtual RAN, and centralized or cloud RAN. Open RAN refers to many techniques that telecom operators anticipate will overcome vendor lock in. Find highly impressive Open Radio Access Network IT Three Main Pillars Of Open RAN Information PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Open Radio Access Network IT Three Main Pillars Of Open RAN Information PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cognitive Sensing Innovation Cognitive Radio CR Access Paradigms Overview Professional PDF
This slide represents the overview of three cognitive radio access paradigms such as underlay, overlay, and interweave. It includes the subcategories of interweave that are full-duplex and half-duplex. The full-duplex further caters to transmit-sense and transmit-receiver. Find highly impressive Cognitive Sensing Innovation Cognitive Radio CR Access Paradigms Overview Professional PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cognitive Sensing Innovation Cognitive Radio CR Access Paradigms Overview Professional PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF
This slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Budget To Implement Secure Access Service Edge Ppt Icon Outfit PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
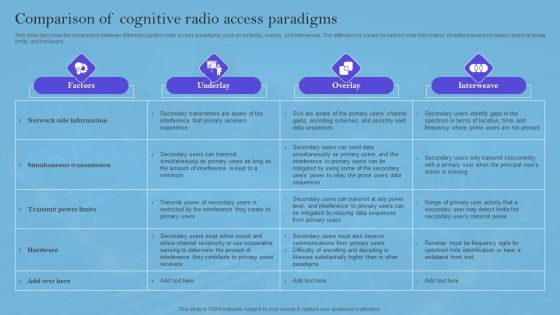
Smart Wireless Sensor Networks Comparison Of Cognitive Radio Access Paradigms Microsoft PDF
This slide describes the comparison between different cognitive radio access paradigms, such as underlay, overlay, and interweave. The difference is based on network side information, simultaneous transmission, transmit power limits, and hardware. Take your projects to the next level with our ultimate collection of Smart Wireless Sensor Networks Comparison Of Cognitive Radio Access Paradigms Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Accounting Bookkeeping Services Account Outsourcing Process By Remote Access Infographics PDF
Presenting this set of slides with name accounting bookkeeping services account outsourcing process by remote access infographics pdf. This is a four stage process. The stages in this process are log in, process, two step review, completed. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

File Sharing And Document Management Access Change Review Ppt PowerPoint Presentation Styles Format
Presenting this set of slides with name file sharing and document management access change review ppt powerpoint presentation styles format. This is a five stage process. The stages in this process are document review, document analysis, document evaluation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
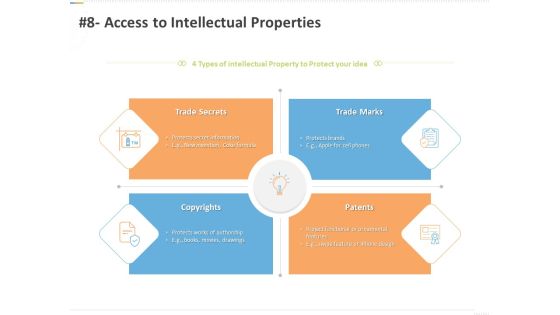
Sustainable Competitive Advantage Management Strategy 8 Access To Intellectual Properties Ppt Styles Format Ideas PDF
Presenting this set of slides with name sustainable competitive advantage management strategy 8 access to intellectual properties ppt styles format ideas pdf. This is a four stage process. The stages in this process are trade secrets, trade marks, patents, copyrights. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Open Radio Access Network IT Roadmap For Open RAN Deployment Topics PDF
This slide represents the roadmap for open RAN deployment. It covers the steps to be performed for the practical implementation of an open random access network, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Open Radio Access Network IT Roadmap For Open RAN Deployment Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Open Radio Access Network IT Timeline For Open RAN Deployment Themes PDF
This slide represents the timeline for open random access network deployment, including the steps to be performed to effectively implement open RAN, such as hardware deployment, entering open RAN, open specifications, transport, and network automation. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Open Radio Access Network IT Timeline For Open RAN Deployment Themes PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
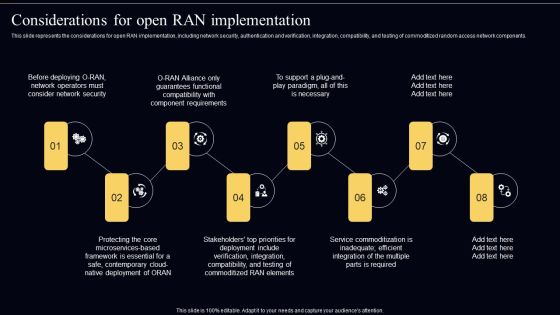
Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF
This slide represents the considerations for open RAN implementation, including network security, authentication and verification, integration, compatibility, and testing of commoditized random access network components. Boost your pitch with our creative Open Radio Access Network IT Considerations For Open RAN Implementation Topics PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cloud Access Security Broker Life Cycle Protection Ppt PowerPoint Presentation File Diagrams PDF.

Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Secure Access Service Edge Cloud Security Model Ppt Professional Backgrounds PDF today and make your presentation stand out from the rest.
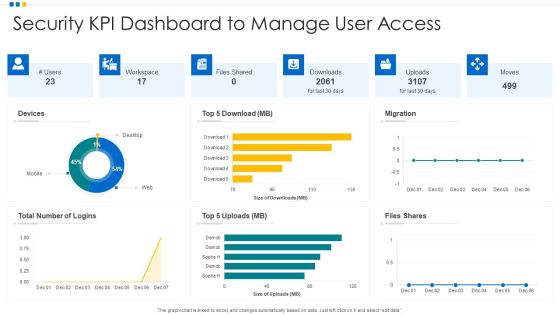
Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF
Pitch your topic with ease and precision using this Security KPI Dashboard To Manage User Access Ppt Infographic Template Graphics Pictures PDF. This layout presents information on Devices, Security KPI Dashboard, Workspace. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Document Encryption File Access Vector Icon Ppt PowerPoint Presentation Inspiration Guidelines
Presenting this set of slides with name document encryption file access vector icon ppt powerpoint presentation inspiration guidelines. This is a one stage process. The stages in this process are market asses, strategic market, business. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Projected Access Documents With Key Vector Icon Ppt PowerPoint Presentation Model Samples
Presenting this set of slides with name projected access documents with key vector icon ppt powerpoint presentation model samples. This is a one stage process. The stages in this process are market asses, strategic market, business. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Market Access With Research And Planning Ppt PowerPoint Presentation Icon Graphics Download
Presenting this set of slides with name market access with research and planning ppt powerpoint presentation icon graphics download. This is a eight stage process. The stages in this process are development, strategy, research. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
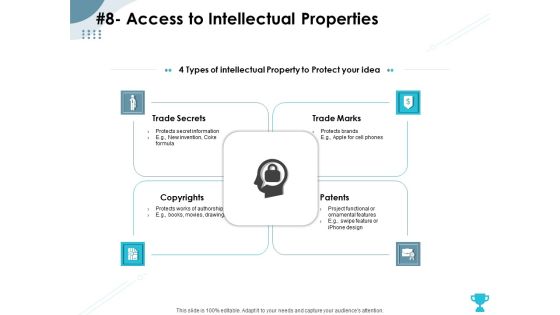
Strategies Take Your Retail Business Ahead Competition 8 Access To Intellectual Properties Rules PDF
Presenting this set of slides with name strategies take your retail business ahead competition 8 access to intellectual properties rules pdf. This is a four stage process. The stages in this process are trade marks, patents, copyrights, trade secrets. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
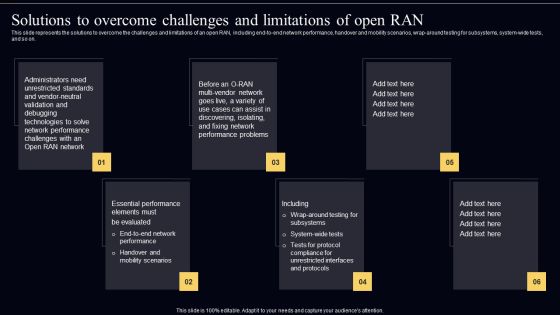
Open Radio Access Network IT Solutions To Overcome Challenges And Limitations Of Open RAN Guidelines PDF
This slide represents the solutions to overcome the challenges and limitations of an open RAN, including end-to-end network performance, handover and mobility scenarios, wrap-around testing for subsystems, system-wide tests, and so on. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Open Radio Access Network IT Solutions To Overcome Challenges And Limitations Of Open RAN Guidelines PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Open Radio Access Network IT Solutions To Overcome Challenges And Limitations Of Open RAN Guidelines PDF today and make your presentation stand out from the rest.
Key Stages For Project Intake Workflow With Discover And Access Ppt PowerPoint Presentation Gallery Icons PDF
Presenting key stages for project intake workflow with discover and access ppt powerpoint presentation gallery icons pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including discover, assess, plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Three Level Structure For Server Data Access Ppt PowerPoint Presentation Gallery Layouts PDF
Presenting three level structure for server data access ppt powerpoint presentation gallery layouts pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including presentation tier, logic tier, data tier. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home