Access Control
Market Access With Arrow Icon Ppt PowerPoint Presentation File Smartart
Presenting this set of slides with name market access with arrow icon ppt powerpoint presentation file smartart. This is a one stage process. The stage in this process is market access with arrow icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Zero Trust Network Access Architecture Overview Icons PDF
This slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Retrieve professionally designed Zero Trust Network Access Architecture Overview Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
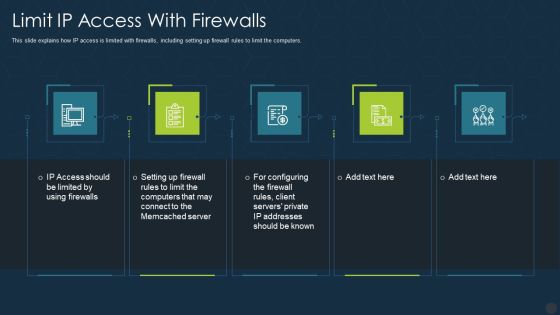
Memcache Technology IT Limit Ip Access With Firewalls Pictures PDF
This slide explains how IP access is limited with firewalls, including setting up firewall rules to limit the computers. This is a memcache technology it limit ip access with firewalls pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like limit ip access with firewalls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
System Access To Management Ppt PowerPoint Presentation Topics
This is a system access to management ppt powerpoint presentation topics. This is a five stage process. The stages in this process are business, management, analysis, strategy, success, process.

Identity Access Management Lifecycle Ppt Powerpoint Slide Presentation Guidelines
This is a identity access management lifecycle ppt powerpoint slide presentation guidelines. This is a five stage process. The stages in this process are relationship begins, provisioning, authentication, authorization, self service, compliance, deprovisioning, password management, relationship ends.

Zero Trust Network Access System Use Cases Summary PDF
This slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Boost your pitch with our creative Zero Trust Network Access System Use Cases Summary PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Difference Identity Access Management Ppt PowerPoint Presentation Outline Introduction Cpb
Presenting this set of slides with name difference identity access management ppt powerpoint presentation outline introduction cpb. This is an editable Powerpoint five stages graphic that deals with topics like difference identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Ethical Hacking Phase 3 Gaining Access Ppt Pictures Vector PDF
This slide represents the gaining access phase of ethical hacking and how access can be gained through a phishing attack, man in the middle, brute force attack, and so on. This is a ethical hacking phase 3 gaining access ppt pictures vector pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, required. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Parallel Computing Processing Introduction To Switched Memory Access Icons PDF
This slide represents the introduction to switched memory access, and a crossbar switch is installed to connect processors. Processors use shared memory in blocks, and connections between processors are made through a crossbar switch. Deliver and pitch your topic in the best possible manner with this Parallel Computing Processing Introduction To Switched Memory Access Icons PDF. Use them to share invaluable insights on Introduction To Switched, Memory Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Critical Principles Of Zero Trust Network Access Model Graphics PDF
This slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Critical Principles Of Zero Trust Network Access Model Graphics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Critical Principles Of Zero Trust Network Access Model Graphics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
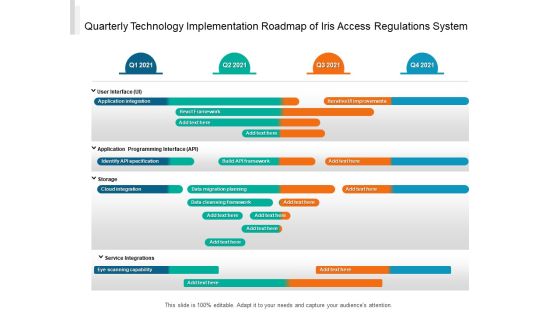
Quarterly Technology Implementation Roadmap Of Iris Access Regulations System Topics
We present our quarterly technology implementation roadmap of iris access regulations system topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly technology implementation roadmap of iris access regulations system topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Addressing 5G Era Spectrum Bands Access And Pricing Clipart PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. This is a Addressing 5G Era Spectrum Bands Access And Pricing Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Spectrum Bands, Spectrum Access, Spectrum Pricing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Access Systems Ppt PowerPoint Presentation Layouts Gridlines Cpb
Presenting this set of slides with name data access systems ppt powerpoint presentation layouts gridlines cpb. This is an editable Powerpoint eight stages graphic that deals with topics like data access systems to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
User Access Provisioning Process Ppt PowerPoint Presentation Portfolio Layouts Cpb
Presenting this set of slides with name user access provisioning process ppt powerpoint presentation portfolio layouts cpb. This is an editable Powerpoint four stages graphic that deals with topics like user access provisioning process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Access Review Process Ppt PowerPoint Presentation Show Graphic Images Cpb
Presenting this set of slides with name access review process ppt powerpoint presentation show graphic images cpb. This is an editable Powerpoint four stages graphic that deals with topics like access review process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Access Management Roles Responsibilities Ppt PowerPoint Presentation Ideas Example Cpb
Presenting this set of slides with name access management roles responsibilities ppt powerpoint presentation ideas example cpb. This is an editable Powerpoint three stages graphic that deals with topics like access management roles responsibilities to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Business Value Identity Access Management Ppt PowerPoint Presentation Summary Cpb
Presenting this set of slides with name business value identity access management ppt powerpoint presentation summary cpb. This is an editable Powerpoint three stages graphic that deals with topics like business value identity access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Secure Access Management Ppt PowerPoint Presentation Pictures Layout Cpb Pdf
Presenting this set of slides with name secure access management ppt powerpoint presentation pictures layout cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like secure access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
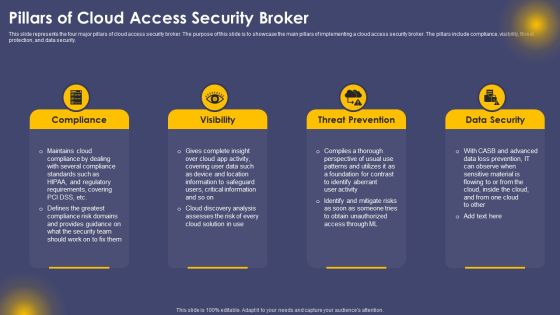
Pillars Of Cloud Access Security Broker Ppt Show Background PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Pillars Of Cloud Access Security Broker Ppt Show Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Pillars Of Cloud Access Security Broker Ppt Show Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Open Access Box With Gears Ppt PowerPoint Presentation Inspiration Demonstration
This is a open access box with gears ppt powerpoint presentation inspiration demonstration. This is a six stage process. The stages in this process are computer software, operating system, open source.
Open Access Collaborative Customizable Sharable Ppt PowerPoint Presentation File Backgrounds
This is a open access collaborative customizable sharable ppt powerpoint presentation file backgrounds. This is a seven stage process. The stages in this process are computer software, operating system, open source.

Benefits Access Management Ppt PowerPoint Presentation Professional Smartart Cpb
Presenting this set of slides with name benefits access management ppt powerpoint presentation professional smartart cpb. This is an editable Powerpoint four stages graphic that deals with topics like benefits access management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Identity Access Management Framework Ppt PowerPoint Presentation Portfolio Summary Cpb
Presenting this set of slides with name identity access management framework ppt powerpoint presentation portfolio summary cpb. This is an editable Powerpoint four stages graphic that deals with topics like identity access management framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
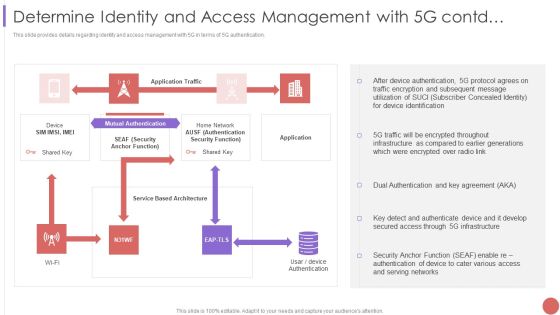
Determine Identity And Access Management With 5G Contd Structure PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Determine Identity And Access Management With 5G Contd Structure PDF Use them to share invaluable insights on Mutual Authentication, Device Authentication, Traffic Encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Determine Identity And Access Management With 5G Contd Information PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Determine Identity And Access Management With 5G Contd Information PDF. Use them to share invaluable insights on Application Traffic, Security, Network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Application Of AI For Database Access Governance Summary PDF
This slide represents the applications of artificial intelligence systems for data access governance. The purpose of this slide is to demonstrate the AI application in secure data access. The use cases include threat detection and prediction, system configuration, adaptability, data interpretation, and predictive forecasting. Presenting Application Of AI For Database Access Governance Summary PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Prediction, System Configuration, Adaptability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Database Access Security Measures For Businesses Portrait PDF
This slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data-centric security plan, deploying a multi-factor authentication policy, etc. Pitch your topic with ease and precision using this Database Access Security Measures For Businesses Portrait PDF. This layout presents information on Methods, Benefits, Actions. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Access Provisioning Lifecycle Ppt PowerPoint Presentation Show Cpb Pdf
Presenting this set of slides with name access provisioning lifecycle ppt powerpoint presentation show cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like access provisioning lifecycle to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Next Generation Access Ppt PowerPoint Presentation Portfolio Design Ideas Cpb
Presenting this set of slides with name next generation access ppt powerpoint presentation portfolio design ideas cpb. This is an editable Powerpoint six stages graphic that deals with topics like next generation access to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
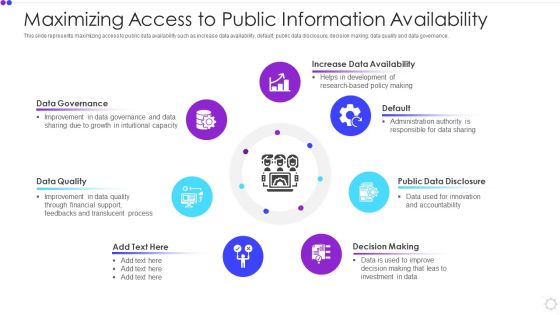
Maximizing Access To Public Information Availability Rules PDF
This slide represents maximizing access to public data availability such as increase data availability, default, public data disclosure, decision making, data quality and data governance. Presenting maximizing access to public information availability rules pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including data governance, data quality, decision making. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

User Access Provisioning Process Ppt PowerPoint Presentation Example Cpb
Presenting this set of slides with name user access provisioning process ppt powerpoint presentation example cpb. This is an editable Powerpoint three stages graphic that deals with topics like user access provisioning process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Secure Access Lock Clipart Ppt PowerPoint Presentation Summary File Formats
This is a secure access lock clipart ppt powerpoint presentation summary file formats. This is a four stage process. The stages in this process are computer software, operating system, open source.
Secure Server Access Ppt PowerPoint Presentation Icon Show Cpb
Presenting this set of slides with name secure server access ppt powerpoint presentation icon show cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure server access to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Enterprise Access Governance Ppt PowerPoint Presentation Model Mockup Cpb
Presenting this set of slides with name enterprise access governance ppt powerpoint presentation model mockup cpb. This is an editable Powerpoint four stages graphic that deals with topics like enterprise access governance to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Secure Data Access Ppt PowerPoint Presentation Inspiration Guidelines Cpb
Presenting this set of slides with name secure data access ppt powerpoint presentation inspiration guidelines cpb. This is an editable Powerpoint four stages graphic that deals with topics like secure data access to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Individual Access Security Ppt PowerPoint Presentation Design Ideas Cpb
Presenting this set of slides with name individual access security ppt powerpoint presentation design ideas cpb. This is an editable Powerpoint three stages graphic that deals with topics like individual access security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Provider Access Ppt PowerPoint Presentation Summary Graphics Pictures Cpb Pdf
Presenting this set of slides with name provider access ppt powerpoint presentation summary graphics pictures cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like provider access to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Sensitive Access Analysis Ppt PowerPoint Presentation Styles Influencers Cpb Pdf
Presenting this set of slides with name sensitive access analysis ppt powerpoint presentation styles influencers cpb pdf. This is an editable Powerpoint six stages graphic that deals with topics like sensitive access analysis to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Access Database Replication Ppt PowerPoint Presentation Inspiration Show Cpb Pdf
Presenting this set of slides with name access database replication ppt powerpoint presentation inspiration show cpb pdf. This is an editable Powerpoint three stages graphic that deals with topics like access database replication to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Secure Database Access Methods For Cloud Computing Formats PDF
This slide describes the various methods to access the data stored in a cloud environment securely. The purpose of this slide is to represent secure data access for cloud computing users. The methods include cloud-based access through a relational database management system, cloud-based data warehousing and a cloud data lake. Persuade your audience using this Secure Database Access Methods For Cloud Computing Formats PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Cloud Data Lake, Data Warehousing, Cloud Service Provider. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Multiple Access Techniques Ppt PowerPoint Presentation Summary Portrait Cpb
Presenting this set of slides with name multiple access techniques ppt powerpoint presentation summary portrait cpb. This is an editable Powerpoint four stages graphic that deals with topics like multiple access techniques to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
Market Access Strategy Example Powerpoint Slide Background Picture
This is a market access strategy example powerpoint slide background picture. This is a four stage process. The stages in this process are resource allocation, market assessment, economic modelling, product assessment.

Main Pillars Of Zero Network Trust Access Sample PDF
This slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Presenting this PowerPoint presentation, titled Main Pillars Of Zero Network Trust Access Sample PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Main Pillars Of Zero Network Trust Access Sample PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Main Pillars Of Zero Network Trust Access Sample PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
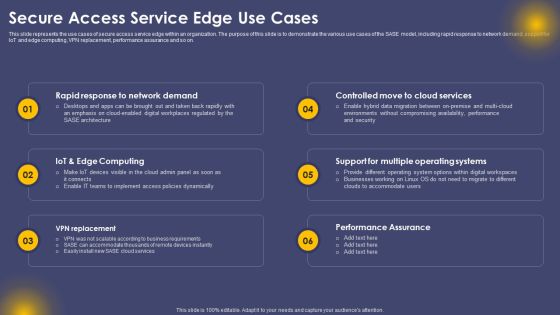
Secure Access Service Edge Use Cases Ppt Outline Images PDF
This slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Explore a selection of the finest Secure Access Service Edge Use Cases Ppt Outline Images PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Secure Access Service Edge Use Cases Ppt Outline Images PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Training Program For Zero Trust Network Access Model Microsoft PDF
This slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. This Training Program For Zero Trust Network Access Model Microsoft PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Training Program For Zero Trust Network Access Model Microsoft PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Database Access Management Checklist For Businesses Formats PDF
This slide outlines the checklist for data access management in an organization. The purpose of this slide is to enlist all the crucial tasks and steps. The key points include creating an inventory, identifying data ownership and location of data, creating security groups, conducting regular data audits, and creating a certification program. Showcasing this set of slides titled Database Access Management Checklist For Businesses Formats PDF. The topics addressed in these templates are Description, Status, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Identification Access Lifecycle Framework Of IT Company Portrait PDF
This slide depicts identity identification lifecycle model of information technology IT company. It provides information about identity onboarding, identity management, account management, entitlement management and access management.Persuade your audience using this identification access lifecycle framework of it company portrait pdf This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identity onboarding, identity management, account management Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Pillars Of Identify And Access Management Technique Topics PDF
This slide shows main features of an effective IAM strategy. The purpose of this strategy is to highlight major components of IAM strategy. It include features such as provisioning identities, access security certification and security management , etc. Presenting Key Pillars Of Identify And Access Management Technique Topics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Provisioning Identities, Security Certification, Security Management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Working Functions Of Zero Trust Network Access Architecture Introduction PDF
This slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Explore a selection of the finest Working Functions Of Zero Trust Network Access Architecture Introduction PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Working Functions Of Zero Trust Network Access Architecture Introduction PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Zero Trust Network Access ZTNA Introduction Structure PDF
This slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. There are so many reasons you need a Zero Trust Network Access ZTNA Introduction Structure PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Zero Trust Network Access User Flow Overview Mockup PDF
This slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Create an editable Zero Trust Network Access User Flow Overview Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Zero Trust Network Access User Flow Overview Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
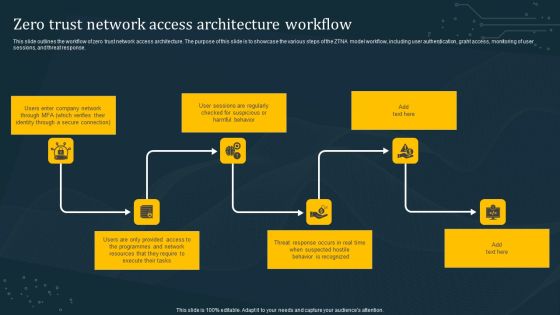
Zero Trust Network Access Architecture Workflow Microsoft PDF
This slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Slidegeeks has constructed Zero Trust Network Access Architecture Workflow Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
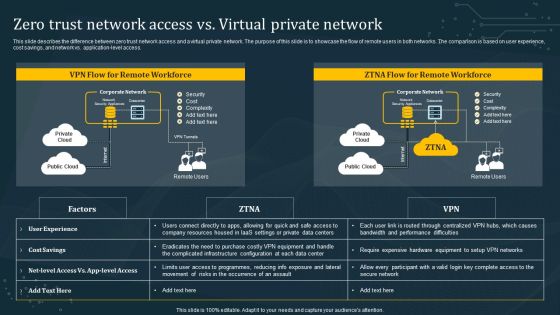
Zero Trust Network Access Vs Virtual Private Network Ideas PDF
This slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Zero Trust Network Access Vs Virtual Private Network Ideas PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Challenges Of VPN Based Remote Access Solutions Template PDF
This slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Challenges Of VPN Based Remote Access Solutions Template PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Challenges Of VPN Based Remote Access Solutions Template PDF today and make your presentation stand out from the rest
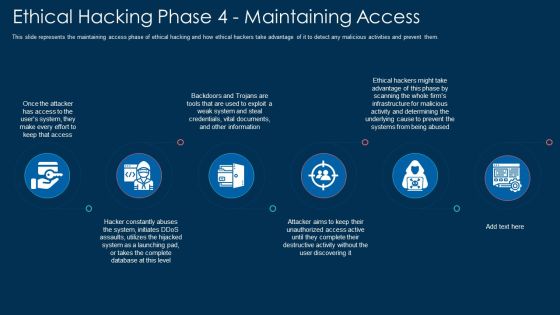
Ethical Hacking Phase 4 Maintaining Access Ppt Professional Grid PDF
This slide represents the maintaining access phase of ethical hacking and how ethical hackers take advantage of it to detect any malicious activities and prevent them. This is a ethical hacking phase 4 maintaining access ppt professional grid pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, determining. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing 5G Era Spectrum Bands Access And Pricing Download PDF
This slide provides details regarding various 5G era spectrum in terms of 5G spectrum bands, spectrum access and spectrum pricing. Presenting Addressing 5G Era Spectrum Bands Access And Pricing Download PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Approved Spectrum, Globally Recognized, Operators To Revamp In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Zero Trust Network Access Implementation Challenges Rules PDF
This slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on. Presenting this PowerPoint presentation, titled Zero Trust Network Access Implementation Challenges Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Zero Trust Network Access Implementation Challenges Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Zero Trust Network Access Implementation Challenges Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cloud Storage Access Methods Ppt Model Maker PDF
This slide depicts the cloud storage access methods such as web service APIs Application Programming Interface, file based APIs, block-based APIs, and other APIs. This is a cloud storage access methods ppt model maker pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service, network internet, implement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Checklist To Build Zero Trust Network Access Architecture Diagrams PDF
This slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Checklist To Build Zero Trust Network Access Architecture Diagrams PDF can be your best option for delivering a presentation. Represent everything in detail using Checklist To Build Zero Trust Network Access Architecture Diagrams PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
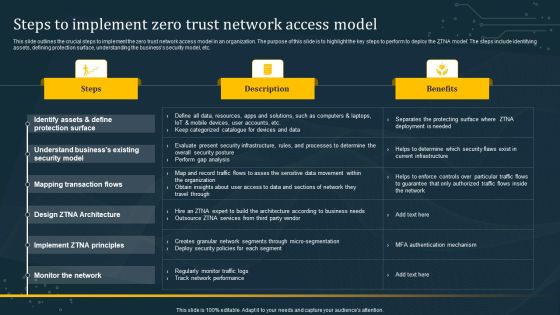
Steps To Implement Zero Trust Network Access Model Graphics PDF
This slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Steps To Implement Zero Trust Network Access Model Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Top Zero Trust Network Access Software Solutions Microsoft PDF
This slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Top Zero Trust Network Access Software Solutions Microsoft PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Top Zero Trust Network Access Software Solutions Microsoft PDF.

Secure Access Service Edge Architecture Characteristics Ppt Summary Portfolio PDF
This slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Make sure to capture your audiences attention in your business displays with our gratis customizable Secure Access Service Edge Architecture Characteristics Ppt Summary Portfolio PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Agenda For Open Radio Access Network Icons PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Open Radio Access Network Icons PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Open Radio Access Network Icons PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Top Tenets Of Zero Trust Network Access Model Brochure PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Top Tenets Of Zero Trust Network Access Model Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
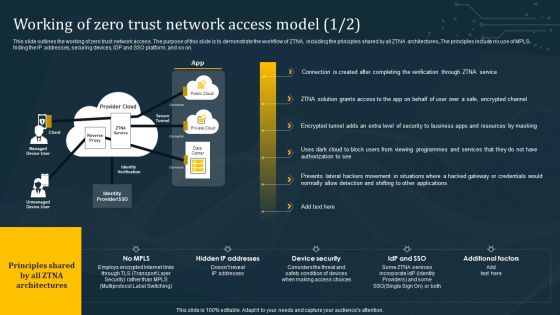
Working Of Zero Trust Network Access Model Summary PDF
This slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Working Of Zero Trust Network Access Model Summary PDF from Slidegeeks and deliver a wonderful presentation.

Cloud Access Security Broker Working Process Ppt Slides Portrait PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Boost your pitch with our creative Cloud Access Security Broker Working Process Ppt Slides Portrait PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
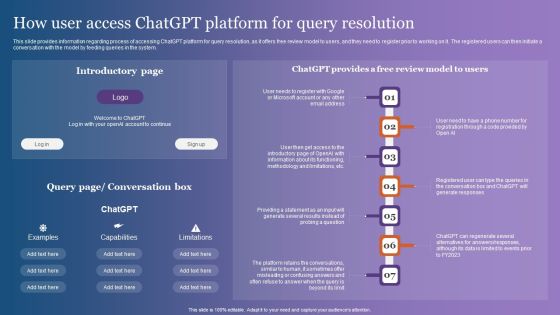
How User Access Chatgpt Platform For Query Resolution Template PDF
This slide provides information regarding process of accessing ChatGPT platform for query resolution, as it offers free review model to users, and they need to register prior to working on it. The registered users can then initiate a conversation with the model by feeding queries in the system. Present like a pro with How User Access Chatgpt Platform For Query Resolution Template PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cloud-Based Identify And Access Management Technique Best Practices Slides PDF
This slide shows ideal practices for IAM strategy. The purpose of this strategy is to highlight all effective practices along with concerned activities. It include practices such as defining IAM vision, building strong foundation , etc. Presenting Cloud-Based Identify And Access Management Technique Best Practices Slides PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Vision Clearly, Strong Foundation, Secure Generic Accounts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
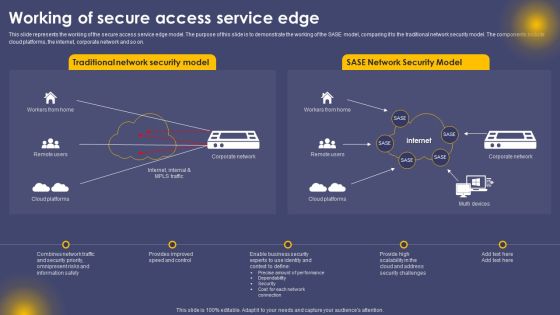
Working Of Secure Access Service Edge Ppt Summary Ideas PDF
This slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. The Working Of Secure Access Service Edge Ppt Summary Ideas PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
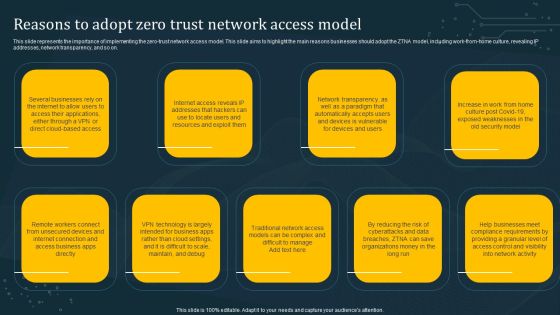
Reasons To Adopt Zero Trust Network Access Model Demonstration PDF
This slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Reasons To Adopt Zero Trust Network Access Model Demonstration PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Business Advantages Of Open Database Access Structure PDF
This slide represents the benefits of open data access to businesses. The purpose of this slide is to describe the gains for organizations. The benefits include encouraging and facilitating research, data transparency, reduced data loss and theft, and publicly funded research. It maintains data transparency through data integrity and peer review. Persuade your audience using this Business Advantages Of Open Database Access Structure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Research, Transparency, Reduce Data Loss . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Types Of Zero Trust Network Access ZTNA Models Formats PDF
This slide describes the various types of zero-trust network access models. The purpose of this slide is to demonstrate the various ZTNA models and core elements of ZTNA implementation. The model types include user protection, workload protection, and device protection. Welcome to our selection of the Types Of Zero Trust Network Access ZTNA Models Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Secure Access Service Edge Importance Ppt Outline Graphics Example PDF
This slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. This modern and well arranged Secure Access Service Edge Importance Ppt Outline Graphics Example PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
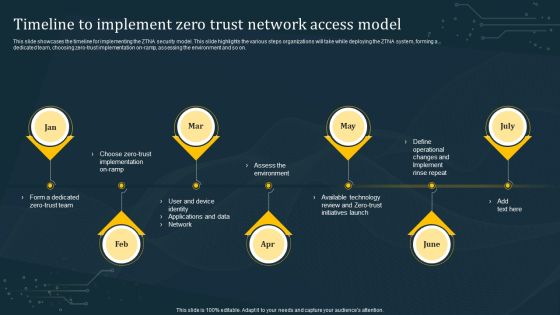
Timeline To Implement Zero Trust Network Access Model Rules PDF
This slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Timeline To Implement Zero Trust Network Access Model Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Timeline To Implement Zero Trust Network Access Model Rules PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
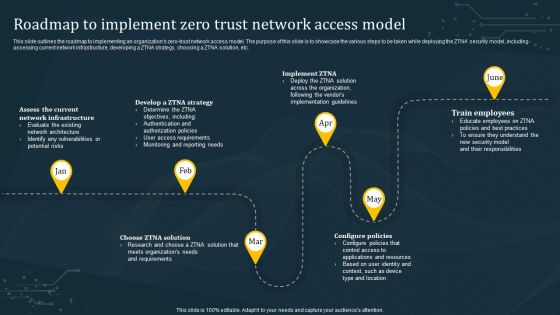
Roadmap To Implement Zero Trust Network Access Model Structure PDF
This slide outlines the roadmap to implementing an organizations zero-trust network access model. The purpose of this slide is to showcase the various steps to be taken while deploying the ZTNA security model, including assessing current network infrastructure, developing a ZTNA strategy, choosing a ZTNA solution, etc. Want to ace your presentation in front of a live audience Our Roadmap To Implement Zero Trust Network Access Model Structure PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Access Regulations Technology Five Years Roadmap With Security Solution Inspiration
Presenting our innovatively structured access regulations technology five years roadmap with security solution inspiration Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Access Regulations Technology Quarterly Roadmap For Biometrics Solution Background
Presenting our jaw dropping access regulations technology quarterly roadmap for biometrics solution background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Access Regulations Technology Six Months Roadmap For Biometrics Solution Mockup
Presenting our innovatively structured access regulations technology six months roadmap for biometrics solution mockup Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
Facial Recognition Access Regulations Technology Half Yearly Roadmap Icons
Presenting our innovatively structured facial recognition access regulations technology half yearly roadmap icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.
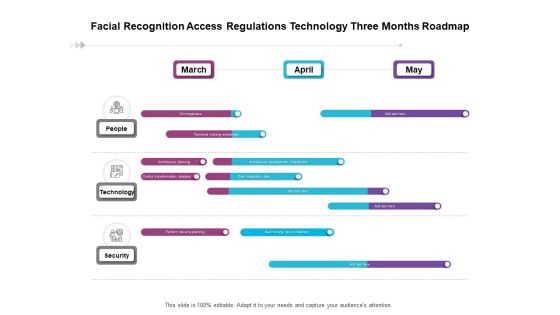
Facial Recognition Access Regulations Technology Three Months Roadmap Formats
Presenting our jaw dropping facial recognition access regulations technology three months roadmap formats. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
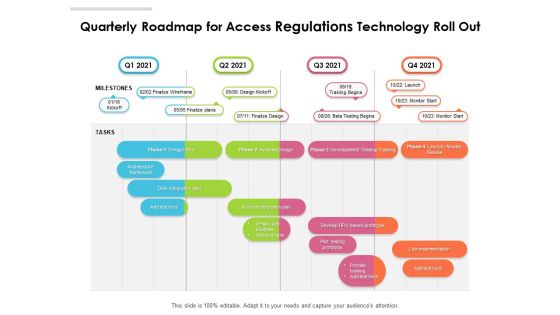
Quarterly Roadmap For Access Regulations Technology Roll Out Demonstration
Presenting our jaw dropping quarterly roadmap for access regulations technology roll out demonstration. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
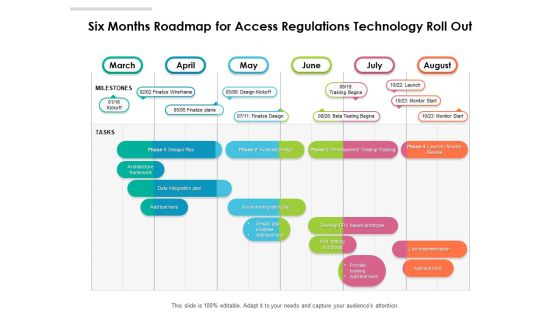
Six Months Roadmap For Access Regulations Technology Roll Out Summary
Presenting our innovatively structured six months roadmap for access regulations technology roll out summary Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cloud Storage Access Methods Ppt PowerPoint Presentation File Backgrounds PDF
This slide depicts the cloud storage access methods such as web service APIs Application Programming Interface, file based APIs, block based APIs, and other APIs. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Storage Access Methods Ppt PowerPoint Presentation File Backgrounds PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Technologies Used In Zero Trust Network Access Infographics PDF
This slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Technologies Used In Zero Trust Network Access Infographics PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Secure Access Service Edge SASE Architecture Ppt Inspiration Grid PDF
This slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. This Secure Access Service Edge SASE Architecture Ppt Inspiration Grid PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Access Regulations Technology Half Yearly Roadmap For Biometrics Solution Diagrams
Introducing our access regulations technology half yearly roadmap for biometrics solution diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Access Regulations Technology Six Months Roadmap With Security Solution Brochure
Introducing our access regulations technology six months roadmap with security solution brochure. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
Facial Recognition Access Regulations Technology Quarterly Roadmap Icons
Introducing our facial recognition access regulations technology quarterly roadmap icons. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
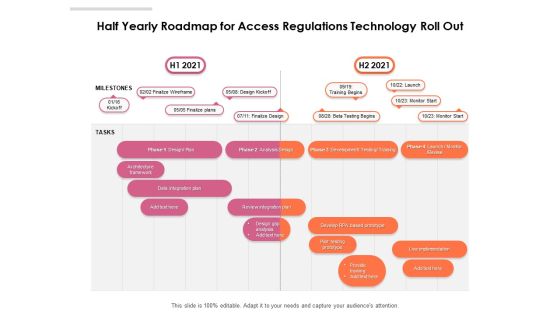
Half Yearly Roadmap For Access Regulations Technology Roll Out Topics
Introducing our half yearly roadmap for access regulations technology roll out topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Identify And Access Management Technique Implementation Tools Demonstration PDF
This slide show efficient tools for execution of IAM strategy. The purpose of this slide is to highlight all effective tools for executing IAM strategy in organization. It includes toll name, features, rating and prices , etc. Pitch your topic with ease and precision using this Identify And Access Management Technique Implementation Tools Demonstration PDF. This layout presents information on Tool Name, Features, Rating. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Gain Access To Lifecycle Management Tools Microsoft PDF
This template depicts that use application management tools to manage project, track clients requirements, track bugs, manage software or app source code, collaborate with team, and run scans on application.This is a Gain Access To Lifecycle Management Tools Microsoft PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Lifecycle Management, Clients Requirements, Collaborate Team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
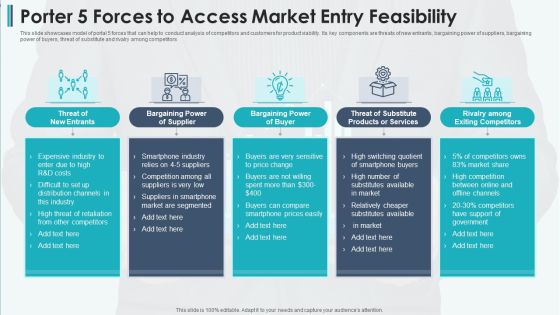
Porter 5 Forces To Access Market Entry Feasibility Professional PDF
This slide showcases model of portal 5 forces that can help to conduct analysis of competitors and customers for product viability. Its key components are threats of new entrants, bargaining power of suppliers, bargaining power of buyers, threat of substitute and rivalry among competitors Presenting porter 5 forces to access market entry feasibility professional pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including bargaining power of supplier, bargaining power of buyer, threat of substitute products or services This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Open Radio Access Network Background PDF
Slidegeeks has constructed Table Of Contents For Open Radio Access Network Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Internet Computer World Access PowerPoint Slides And Ppt Diagram Templates
Internet computer world access PowerPoint Slides And PPT Diagram TemplatesThese high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT!

Identity Card Employee Access Ppt PowerPoint Presentation Complete Deck
This identity card employee access ppt powerpoint presentation complete deck acts as backup support for your ideas, vision, thoughts, etc. Use it to present a thorough understanding of the topic. This PPT slideshow can be utilized for both in-house and outside presentations depending upon your needs and business demands. Entailing twelve slides with a consistent design and theme, this template will make a solid use case. As it is intuitively designed, it suits every business vertical and industry. All you have to do is make a few tweaks in the content or any other component to design unique presentations. The biggest advantage of this complete deck is that it can be personalized multiple times once downloaded. The color, design, shapes, and other elements are free to modify to add personal touches. You can also insert your logo design in this PPT layout. Therefore a well-thought and crafted presentation can be delivered with ease and precision by downloading this identity card employee access ppt powerpoint presentation complete deck PPT slideshow.

Access Regulations Technology Three Months Roadmap With Security Solution Guidelines
Presenting our jaw dropping access regulations technology three months roadmap with security solution guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Access Regulations Technology Half Yearly Roadmap With Security Solution Guidelines
Presenting the access regulations technology half yearly roadmap with security solution guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Access Regulations Technology Three Months Roadmap For Biometrics Solution Ideas
Presenting the access regulations technology three months roadmap for biometrics solution ideas. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
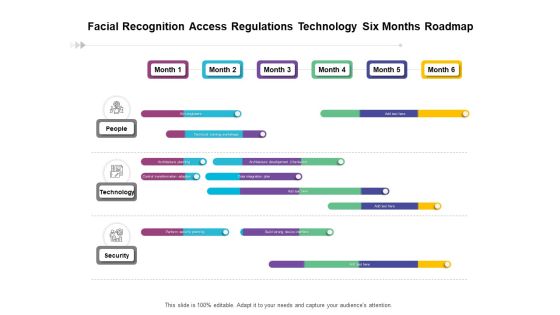
Facial Recognition Access Regulations Technology Six Months Roadmap Background
Presenting the facial recognition access regulations technology six months roadmap background. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Roadmap For Access Regulations Technology Roll Out Slides
Presenting the three months roadmap for access regulations technology roll out slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Before Vs After Zero Trust Network Access Implementation Background PDF
This slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Before Vs After Zero Trust Network Access Implementation Background PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Access Card Employee Corporate Ppt PowerPoint Presentation Complete Deck
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this access card employee corporate ppt powerpoint presentation complete deck is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the twelve slides slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Business Diagram Lock Graphics For Secure Internet Access Presentation Template
This power point template has been crafted with graphic of 3d world map and lock. This PPT contains the concept of security. Use this PPT for your business and marketing related presentations.
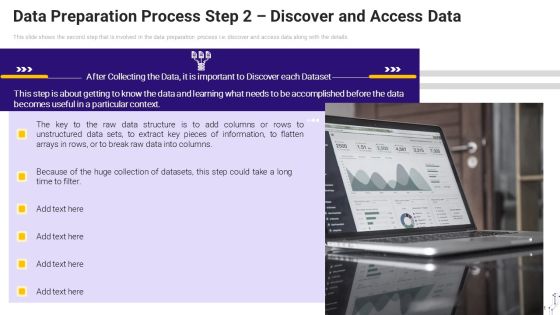
Effective Data Arrangement For Data Accessibility And Processing Readiness Data Preparation Process Step 2 Discover And Access Data Diagrams PDF
This slide shows the second step that is involved in the data preparation process i.e. discover and access data along with the details. This is a effective data arrangement for data accessibility and processing readiness data preparation process step 2 discover and access data diagrams pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data preparation process step 2 discover and access data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Central Repository, Access Management, Authorization Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
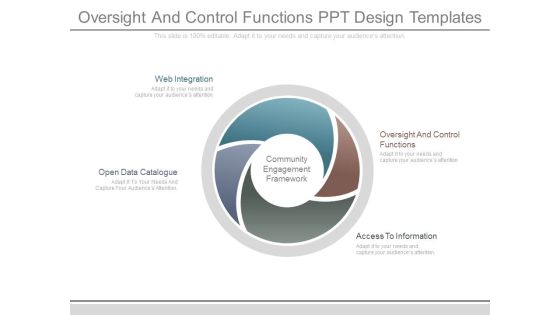
Oversight And Control Functions Ppt Design Templates
This is a oversight and control functions ppt design templates. This is a four stage process. The stages in this process are web integration, oversight and control functions, access to information, open data catalogue, community engagement framework.

IT Infrastructure Library Permission Administration Value Of ITIL Access Management To Business Background PDF
Presenting it infrastructure library permission administration value of itil access management to business background pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like confidentiality of the information will be ensured, if access to different it services is controlled. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
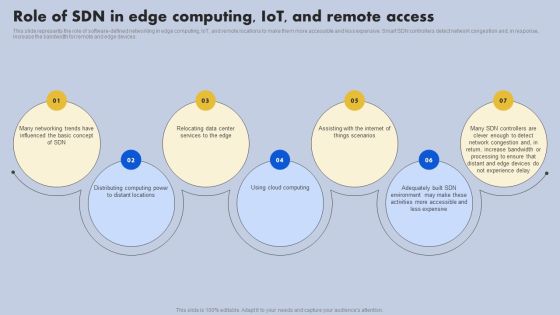
Role Of SDN In Edge Computing Iot And Remote Access Ppt Infographics Display PDF
This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Get a simple yet stunning designed Role Of SDN In Edge Computing Iot And Remote Access Ppt Infographics Display PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Role Of SDN In Edge Computing Iot And Remote Access Ppt Infographics Display PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Role Of SDN In Edge Computing Iot And Remote Access Ppt Infographic Template Icons PDF
This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Get a simple yet stunning designed Role Of SDN In Edge Computing Iot And Remote Access Ppt Infographic Template Icons PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Role Of SDN In Edge Computing Iot And Remote Access Ppt Infographic Template Icons PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Deploying SDN System Role Of Sdn In Edge Computing Iot And Remote Access Graphics PDF
This slide represents the role of software-defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. This modern and well-arranged Deploying SDN System Role Of Sdn In Edge Computing Iot And Remote Access Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
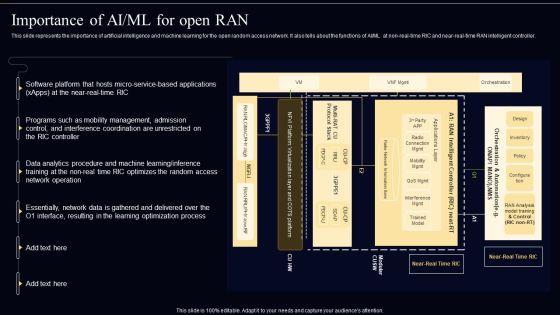
Open Radio Access Network IT Importance Of AI Ml For Open RAN Structure PDF
This slide represents the importance of artificial intelligence and machine learning for the open random access network. It also tells about the functions of AI or ML at non real time RIC and near real time RAN intelligent controller. This Open Radio Access Network IT Importance Of AI Ml For Open RAN Structure PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Open Radio Access Network IT Whos Working On Open RAN Graphics PDF
This slide outlines the organizations or groups working on open RAN, including the O-RAN Alliance Group, Nokia, and Samsung. O RAN alliance group has launched RAN intelligent controller, distributed unit, and RRU specifications. The Open Radio Access Network IT Whos Working On Open RAN Graphics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
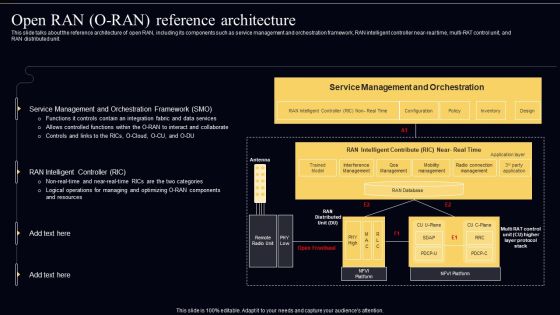
Open Radio Access Network IT Open RAN O RAN Reference Architecture Inspiration PDF
This slide talks about the reference architecture of open RAN, including its components such as service management and orchestration framework, RAN intelligent controller nea real time, multi RAT control unit, and RAN distributed unit. Get a simple yet stunning designed Open Radio Access Network IT Open RAN O RAN Reference Architecture Inspiration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Open Radio Access Network IT Open RAN O RAN Reference Architecture Inspiration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF
This slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Access Security Broker And Secure Web Gateway Ppt PowerPoint Presentation Diagram Images PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
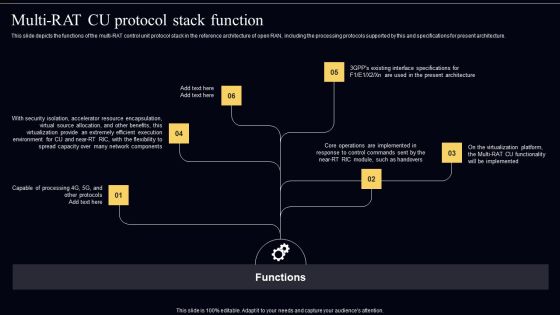
Open Radio Access Network IT Multi RAT CU Protocol Stack Function Structure PDF
This slide depicts the functions of the multi RAT control unit protocol stack in the reference architecture of open RAN, including the processing protocols supported by this and specifications for present architecture. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Open Radio Access Network IT Multi RAT CU Protocol Stack Function Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Open Radio Access Network IT Multi RAT CU Protocol Stack Function Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Benefits Of Zero Trust Network Access ZTNA Ppt Layouts Example PDF
This slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Benefits Of Zero Trust Network Access ZTNA Ppt Layouts Example PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
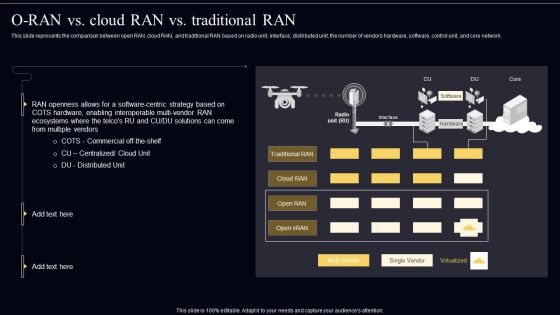
Open Radio Access Network IT O RAN Vs Cloud RAN Vs Traditional RAN Download PDF
This slide represents the comparison between open RAN, cloud RAN, and traditional RAN based on radio unit, interface, distributed unit, the number of vendors hardware, software, control unit, and core network. Do you know about Slidesgeeks Open Radio Access Network IT O RAN Vs Cloud RAN Vs Traditional RAN Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.

 Home
Home