AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Threat actions PowerPoint Presentation Templates and Google Slides
29 Item(s)


Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Get a simple yet stunning designed Threat Management Action Plan Ppt File Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Management Action Plan Ppt File Introduction PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Slide 1 of 2
Pitch your topic with ease and precision using this icon of information security strategic action plan to prevent threats clipart pdf. This layout presents information on icon of information security strategic action plan to prevent threats. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this threat management at workplace threat management action plan responsible person template pdf. Use them to share invaluable insights on cyber incident recovery coordination through meetings, confidential information security at risk, cyber security officer and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver an awe inspiring pitch with this creative threat management at workplace threat management action plan identification clipart pdf bundle. Topics like collecting receivables in timely manner, meet compliance obligations, implement compliance monitoring process can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative handling cyber threats digital era action plan in case of breaches ppt styles objects pdf bundle. Topics like action plan in case of breaches can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this corporate security and risk management threat management action plan introduction pdf. Use them to share invaluable insights on potential risk, risk level, action, duration, risk treated and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting corporate security and risk management threat management action plan risk portrait pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber safety incident management threat management action plan sample pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this cyber safety incident management threat management action plan risk professional pdf. Use them to share invaluable insights on potential risk, risk level, action, responsible person, duration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
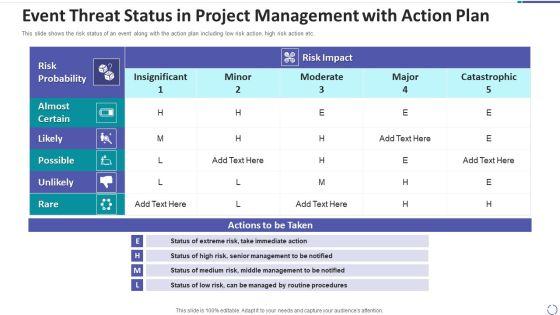

Slide 1 of 2
This slide shows the risk status of an event along with the action plan including low risk action, high risk action etc. Pitch your topic with ease and precision using this event threat status in project management with action plan summary pdf. This layout presents information on event threat status in project management with action plan. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative mitigating cybersecurity threats and vulnerabilities threat management action graphics pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver and pitch your topic in the best possible manner with this mitigating cybersecurity threats and vulnerabilities threat management action plan mockup pdf. Use them to share invaluable insights on threat identification, threat treatment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Presenting threat administration bundle risk contingency worksheet and action plan background pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like risk score, likelihood of occurrence, severity of consequence, contributing causes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting cyber security administration in organization threat management action plan introduction pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like responsibilities, manager, assessment, manager . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Risk Management For Organization Essential Assets Threat Management Action Plan Process Elements PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Deliver an awe inspiring pitch with this creative risk management for organization essential assets threat management action plan process elements pdf bundle. Topics like threat identification, threat treatment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this risk management for organization essential assets threat management action plan communication ideas pdf. Use them to share invaluable insights on potential risk, risk level, duration, communication, action, required resources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide provides the glimpse about the current challenges faced by the organization such as customer churn rate, companys revenues, etc. Deliver an awe inspiring pitch with this creative how to intensify project threats project risk register with mitigating action elements pdf bundle. Topics like date raised, risk description, likehood of the risk occurring, impact if the risk occurs, severity, owner, mitigating action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Presenting this set of slides with name threat management plan template with name action ppt powerpoint presentation visual aids show. The topics discussed in these slides are name, actions, type, pre response probability, pre response schedule, pre response cost. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.






Slide 1 of 6
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Welcome to our selection of the Software Development Life Cycle Planning IT Vulnerabilities With Threat Source And Action Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.






Slide 1 of 6
Pitch your topic with ease and precision using this Event Threat Mitigation Action Plan Themes PDF. This layout presents information on Failure To Meet, Compliance Obligations, Failure In Collecting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.






Slide 1 of 6
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.






Slide 1 of 6
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created IT System Risk Management Guide IT Vulnerabilities With Threat Source And Action Guidelines PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.






Slide 1 of 6
This slide highlights the risks assessment table which includes three type of groups risks, group description of risks, action required for risk and risk escalation. Deliver an awe inspiring pitch with this creative Information Technology Threat Mitigation Methods Risk Assessment Table With Actions And Escalation Level Elements PDF bundle. Topics like Action Required For Risk, Risk Escalation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.






Slide 1 of 6
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.






Slide 1 of 6
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. This is a Information Technology Threat Mitigation Methods IT Vulnerabilities With Threat Source And Action Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerabilities, Threat Source, Threat Action. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.






Slide 1 of 6
This slide focuses on the risk mitigation plan which shows the risk matrix covering likelihood and impacted sections with risk mitigation based upon grade covering grades and its possible actions to be taken at the different stages of the project management. Pitch your topic with ease and precision using this Threat Management Strategy With Possible Actions Background PDF. This layout presents information on Reduce Risk, Implement, Required. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Slide 1 of 1
Purpose of this slide is to address companys fraud risk prevention plan covering details about the activity, fraud risk and mitigation plan.Presenting Corrective Action Plan To Prevent Fraud In Future Fraud Threat Administration Guide Graphics PDF to provide visual cues and insights. Share and navigate important information on onestage that need your due attention. This template can be used to pitch topics like Financial Transactions, Personal Identification, Incorporate Identity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.






Slide 1 of 6
This slide shows report which can be used by an organization to prepare server security threat report. It includes date, time, description, action plan and remarks related to incident. Presenting Safety And Security Threat Report With Action Plan Mockup PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Action Plan, Remarks, Diagnostic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
29 Item(s)
