AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Security processes PowerPoint Presentation Templates and Google Slides
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 302 Item(s)
Page





















































Slide 1 of 53
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fifty three slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.














Slide 1 of 14
This content ready template on Cyber Security Components To Enhance Processes Ppt PowerPoint Presentation Complete With Slides has all the details you need to mention in a presentation. The template also emphasizes critical business service details and charges as a separate package. You can customize each slide of this forteen part complete deck into creative bundles and turn your business visitors into customers. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download with a click below and gain instant access to this handy preset.












Slide 1 of 12
Presenting this set of slides with name managing security incidents management magnifying glass process ppt powerpoint presentation complete deck. The topics discussed in these slides are management, magnifying glass, process, escalation, team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.











Slide 1 of 11
Boost your confidence and team morale with this well-structured industrial security system for large areas technology process ppt powerpoint presentation complete deck. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of eleven slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.










Slide 1 of 10
Presenting this set of slides with name security thesis process research introduction ppt powerpoint presentation complete deck. The topics discussed in these slides are process, research, introduction, interests, conclusions. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.







Slide 1 of 7
This is a security process sample powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.







Slide 1 of 7
This is a security process diagram powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.







Slide 1 of 7
This is a security policy process diagram layout ppt gallery. This is a five stage process. The stages in this process are executions, commercial bank, customer service assistance, bank office, custodian.







Slide 1 of 7
This is a process of information security system diagram powerpoint slide background picture. This is a four stage process. The stages in this process are information security, confidentiality, availability, integrity.







Slide 1 of 7
This is a strategy of proactive security process ppt presentation. This is a three stage process. The stages in this process are environment scanning, pear networking, result, threat detection, incident response, cyber incident.







Slide 1 of 7
This is a enterprise information security process ppt sample ppt files. This is a six stage process. The stages in this process are security policy, access control, compliance, physical security, operations security, business continuity.







Slide 1 of 7
This is a process of web security testing and analysis ppt design. This is a six stage process. The stages in this process are error handing, controlled access, session management, network security, server and code management, data access.





Slide 1 of 5
Presenting this set of slides with name tqm model security process ppt powerpoint presentation infographic template file formats. This is a five stage process. The stages in this process are marketing, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Slide 1 of 5
Presenting this set of slides with name five stages circular process business cyber security ppt powerpoint presentation icon tips. This is a five stage process. The stages in this process are technology, strategy, steps approach. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.





Slide 1 of 5
Presenting this set of slides with name secure payment processing ppt powerpoint presentation styles visual aids cpb. This is an editable Powerpoint three stages graphic that deals with topics like secure payment processing to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.





Slide 1 of 5
This is a marketing communications collaboration business security system process management ppt powerpoint presentation graphics. This is a five stage process. The stages in this process are marketing communications collaboration, business security system, process management.
Slide 1 of 3
Your Grasp Of Economics Is Well Known. Help Your Audience Comprehend Issues With Our Business Strategy Process 3d Render Of Round Chain Security Concept Icons Images Powerpoint Templates.



Slide 1 of 3
We present our hexagonal unidirectional shape for process flow ppt security business plan PowerPoint templates.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Present our Puzzles or Jigsaws PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Present our Hexagon PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Download our Leadership PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape.Use these PowerPoint slides for presentations relating to hexagon, honeycomb, 3d, abstract, background, vector, shelf, design, decoration, layout, achievement, business, blank, concept, sign, success, presentation, cube, bright, symbol, template, commercial, graphic, clean, element, marketing, technology, development, shape, modern, creative, illustration, decorative, up, frame, science, cover, trendy, banner, art, style, space. The prominent colors used in the PowerPoint template are Blue light, Gray, White. Exhibit high fibre with our Hexagonal Unidirectional Shape For Process Flow Ppt Security Business Plan PowerPoint Templates. They display your fearless character.

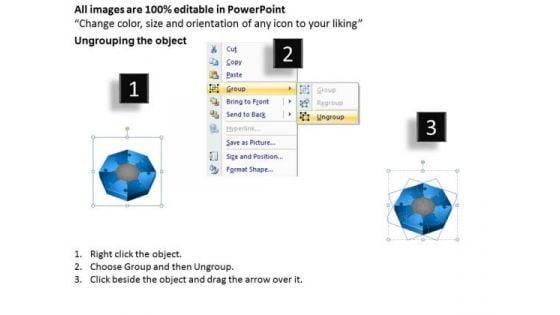

Slide 1 of 3
We present our 3d puzzle 8 staged process diagram ppt security business plan PowerPoint Slides.Download and present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject. Present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Download our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Download and present our Puzzles or Jigsaws PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Present our Flow Charts PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market.Use these PowerPoint slides for presentations relating to Puzzle, wheel, circular, colorful, concept, render, bright, circle, element, abstract, multicolored, creative, palette, illustration, creativity, shade, collection, design, blue, style, part, contrast, pattern . The prominent colors used in the PowerPoint template are Blue, White, Gray. Erase all ambiguity with our 3d Puzzle 8 Staged Process Diagram Ppt Security Business Plan PowerPoint Slides. They will put your point across in a decisive way.



Slide 1 of 3
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black. Aim for the skies with our Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides. You will come out on top.



Slide 1 of 3
We present our pie chart circular 8 stages process ppt security business plan PowerPoint templates.Download our Business PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape. Download and present our Circle Charts PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Download and present our Flow Charts PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience.Use these PowerPoint slides for presentations relating to Chart, market, sales, business, concept, success, presentation, symbol, diagram, circle, finance, stock, report, marketing, analyzing, shape, graph, illustration, piece, pie, division, round, growth, progress, account, profit, part, information, background, statistic, financial. The prominent colors used in the PowerPoint template are Blue, Gray, White. Exert some pressure with our Pie Chart Circular 8 Stages Process Ppt Security Business Plan PowerPoint Templates. Get the decision in your favour.



Slide 1 of 3
Security Process Success PowerPoint Templates And PowerPoint Themes PPT designs-Microsoft Powerpoint Templates and Background with security process Encourage your community to take action. Get them to back the cause you champion.



Slide 1 of 3
Security Process In Business PowerPoint Templates And PowerPoint Themes PPT designs-Microsoft Powerpoint Templates and Background with security process Become the crowd favourite with our Security Process In Business PowerPoint Templates And PowerPoint Themes 0512. Get them all clamouring for you.



Slide 1 of 3
Microsoft Powerpoint Templates and Background with security process-Security Process Business PowerPoint Templates And PowerPoint Themes 0512-These PowerPoint designs and slide layouts can be used for themes relating to -Security process business, background, success, symbol, security, business Present to top tier executives with our Security Process Business PowerPoint Templates And PowerPoint Themes 0512. They will make you look good.



Slide 1 of 3
Microsoft Powerpoint Templates and Background with security process concept in business and technology Let your thoughts evolve. Our Security Process Business PowerPoint Templates And PowerPoint Themes 0312 will nurture their growth.


Slide 1 of 2
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.


Slide 1 of 2
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. This is a Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Case Undersubscription, Interested Investors, Normal Subscription You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Pillars Of Cloud Security Process Based Security Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Application, Security Requires. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting Four Computer Security Processes Portrait PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Penetration Testing, Configuration, Password Management This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. This is a Steps To Ensure Robotic Process Automated Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Protect Log Respectability, Empower Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver and pitch your topic in the best possible manner with this Security Strategic Planning Process For CPS Ppt Slides Icons PDF. Use them to share invaluable insights on Business Strategy, Technology Roadmap, Environmental Trends and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date. Pitch your topic with ease and precision using this Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF. This layout presents information on Response Planning, Risk Assessment, Response Communication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Eliminating Manual Security Processes Through Automation Guidelines PDF bundle. Topics like Security Team, Developers Fix Vulnerabilities, Security Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
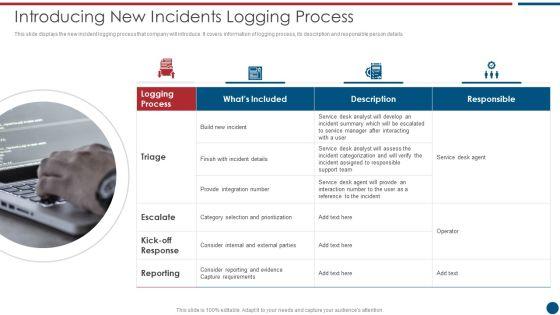
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF. Use them to share invaluable insights on Logging Process, Capture Requirements, Service Desk Agent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF bundle. Topics like Incident Management, Potential can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide represents the process-based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Cloud Information Security Pillars Of Cloud Security Process Based Security Ppt Slides Topics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Controlled Operations, Vulnerability Management, Application Lifecycle. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Slide 1 of 2
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. This is a Risk Based Procedures To IT Security Introducing New Incidents Logging Process Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Desk, Support Team, Provide Integration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF bundle. Topics like Cyberrisk Management, Security Organization, Technology Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manual Vulnerability, Vulnerability Scanning, Automation Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. This is a Gap Identification Current Approach Process Flaws And Cost Risk Based Procedures To IT Security Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cyberrisk Management, Security Organization, Formation Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Incident Occurs, Organize Team, Incident Resolution, Fail Over Report, Auto Alerting, Team Takes Action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Addressing The Incidents Logging Process Professional PDF bundle. Topics like Procedure or Decision, Create New Incident, Integration Number can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
The following slide highlights the information security management system audit methodology illustrating key headings which includes steps and activities, where steps consists of document review, audit review, plan audit, perform audit and reporting Showcasing this set of slides titled Information Security Management System Auditing Process Microsoft PDF. The topics addressed in these templates are Plan Audit, Reporting, Audit Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Presenting reverse proxy server it process of secure reverse proxying ppt slides mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like proxy server, data transmission, secure content server. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a info security process of disaster recovery planning ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like approval, perform risk analysis, define recovery plans, data collection, forming data recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a data safety initiatives eliminating manual security processes through automation topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like manual vulnerability, scanning and resolution, vulnerability scanning, team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide signifies the technical assessment process on company security. It steps include identify, analyse, prioritize and monitoring. Presenting computer security technology evaluation process download pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including identify, analyse, prioritize, monitoring. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Slide 1 of 2
This slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Persuade your audience using this cyber security technology evaluation process ppt powerpoint presentation file visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, execution, closure, monitor, planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting it security process of disaster recovery planning ppt portfolio microsoft pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like plan testing, perform risk analysis, data collection, prioritize procedures and operations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Presenting information technology security process of disaster recovery planning ppt portfolio summary pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like approval, plan testing, recovery plan, data collection, perform . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era eliminating manual security processes ppt show influencers pdf. Use them to share invaluable insights on eliminating manual security processes through automation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collect data from various sources, normalize and aggregate collected data, organization to investigate alerts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
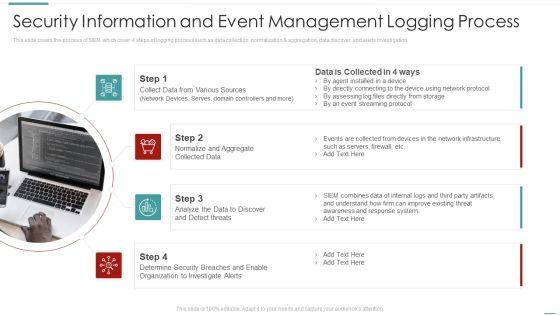

Slide 1 of 2
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation This is a risk recognition automation security information and event management logging process ppt inspiration example introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a real time assessment of security threats security information and event management logging process demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Persuade your audience using this cyber threat security planning process with risk tolerance and threats formats pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including establish governance, actively manage and report, built risk tolerance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.


Slide 1 of 2
SIEM Services Security Information And Event Management Logging Process Ppt Model Example Topics PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Presenting siem services security information and event management logging process ppt model example topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine, breaches, organization, investigate, aggregate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 302 Item(s)
Page
