AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Security management technology PowerPoint Presentation Templates and Google Slides
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 199 Item(s)
Page




















































Slide 1 of 52
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fifty two slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.



















































Slide 1 of 51
This presentation deck enables you to communicate the message, idea, and proposal to your audience in a clear and effective manner. The slides of this PowerPoint Bundle are professional and visually appealing, engaging your audience and gaining their heartful interest in your content. In addition to its spectacular design, this PPT deck is easy to use and altered to fit the specific needs of the user. All fifty one slides in this set are compatible with multiple data handling and presentation platforms like Google Slides, MS Excel, Tableau, etc., so you can present your information hassle free. Begin your journey to tremendous success using our Organizations Risk Management And IT Security Ppt PowerPoint Presentation Complete With Slides in many settings, including meetings, pitches, and conference presentations In fact, customer testimonials.

















Slide 1 of 17
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Security Management Technology Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the seventeen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.












Slide 1 of 12
Boost your confidence and team morale with this well-structured IT Security Risk Management Ppt PowerPoint Presentation Complete Deck With Slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.





Slide 1 of 5
This is a it security risk management ppt powerpoint presentation outline guidelines cpb. This is a five stage process. The stages in this process are it security risk management.


Slide 1 of 2
This side showcase the dashboard of security system management for tracking and forecasting matrices for better functioning of devices. It include the statistic data such as temperature, power consumed, devices working, and list of devices connected. Showcasing this set of slides titled Dashboard For Technological Smart Homes Security System Management Designs PDF. The topics addressed in these templates are Smart Light, Smart Heating, Smart Cooling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. Welcome to our selection of the Developing IT Security Strategy Risk Management Dashboard For Information Security Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Slide 1 of 2
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Slidegeeks has constructed Developing IT Security Strategy Dashboard For Data Security Risk Management Pictures PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.


Slide 1 of 2
This slide displays statistical report to analyze year wise total number of malware reported in organization. It includes years such as 2023, 2022, 2021, 2020, etc. Showcasing this set of slides titled Malware Assessment For Effective Management Of IT Security Risk Portrait PDF. The topics addressed in these templates are Malware Assessment For Effective, Management IT Security Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
This slide displays dashboard for real- time tracking and management of cybersecurity risk to help company formulate appropriate mitigation strategies. It includes kpis such as response plan progress, heat map, action plan, top 5 vulnerabilities, etc. Pitch your topic with ease and precision using this IT Security Risk Management Dashboard With Risk Rating And Breakdown Pictures PDF. This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Probability Score, Risk Analysis Progress. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Slide 1 of 2
This slide displays dashboard to help company in designing initiatives to mitigate cybersecurity risks. It includes kpis such as incident management, patches, compliance, vulnerabilities, etc. Showcasing this set of slides titled IT Security Risk Management And Incident Management Dashboard Icons PDF. The topics addressed in these templates are Compliance, Patches, Incident Management, Vulnerabilities Management, Cybersecurity Initiatives. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Slide 1 of 2
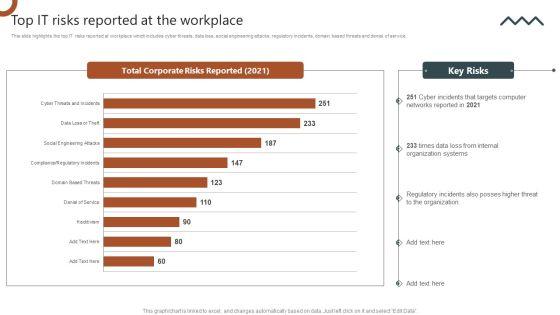
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.


Slide 1 of 2
This slide highlights the impacts of information technology risks on organization which includes graph for overspend project budget and data breach for 2021 year. Explore a selection of the finest Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Organizations Risk Management And IT Security Impact Of IT Risks On Organization Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.


Slide 1 of 2
This slide highlights the enterprise information technology risk management reporting dashboard which includes risk rating breakdown risk heat map, action plan breakdown and thresholds. This Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizations Risk Management And IT Security Enterprise IT Risk Management Reporting Dashboard Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Slide 1 of 2
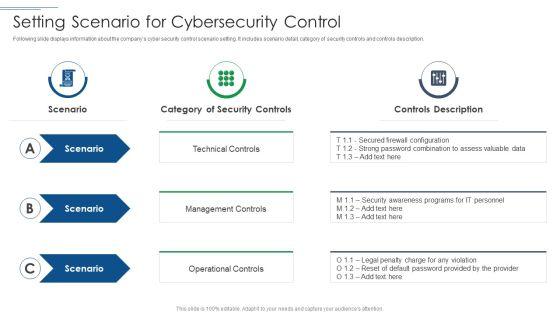
This is a IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technical Control, Management Controls, Operational Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
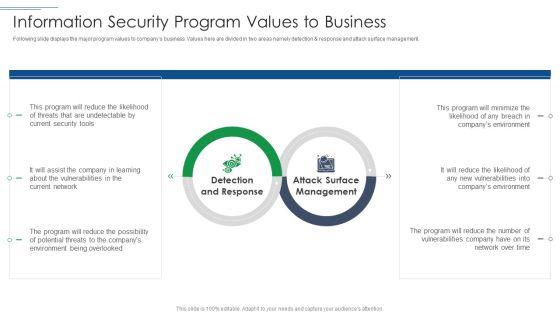

Slide 1 of 2
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting IT Security Risk Management Approach Introduction Information Security Program Values To Business Sample PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Detection And Response, Attack Surface Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
Mentioned slide displays a five day employee upskilling training program that company will use to provide an in dept details about information security program activities and deliverables. This is a IT Security Risk Management Approach Introduction Employee Upskilling Training Program Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Develop Gap Initiatives, Communicate And Implement, Assess Security Requirements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
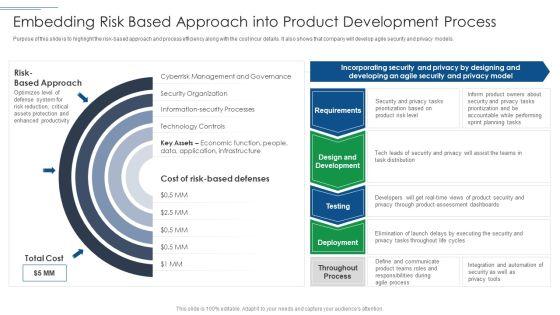
Slide 1 of 2
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF bundle. Topics like Technology Controls, Information Security Processes, Security Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Eliminating Manual Security Processes Through Automation Guidelines PDF bundle. Topics like Security Team, Developers Fix Vulnerabilities, Security Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Threat Vulnerability Asset Matrix Icons PDF. Use them to share invaluable insights on Social Engineering, Server Systems, Internet and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Required Standard Rating, Asset Management, Protect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
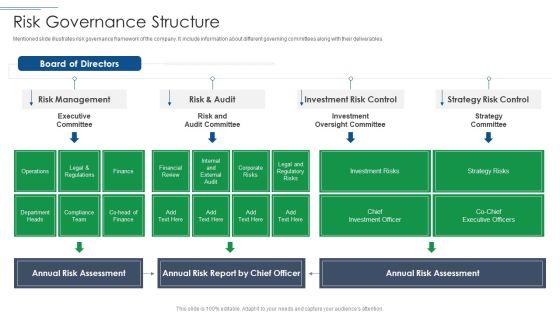
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Risk Governance Structure Mockup PDF. Use them to share invaluable insights on Risk Management, Investment Risk Control, Strategy Risk Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF. Use them to share invaluable insights on Logging Process, Capture Requirements, Service Desk Agent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Criticality Assessment Of Identified Assets Graphics PDF bundle. Topics like Server Computers, Infrastructure Hardware, Failure Cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF. Use them to share invaluable insights on Sprint Report, Product Report, Delivery Method and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide illustrates the mitigation plan of the company in case of any security breach. Sections covered are threat encountered, risk level, resources required and expected resolution time. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Action Plan In Case Of Breaches Demonstration PDF bundle. Topics like Security Breach, System Failure, Risk Level can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
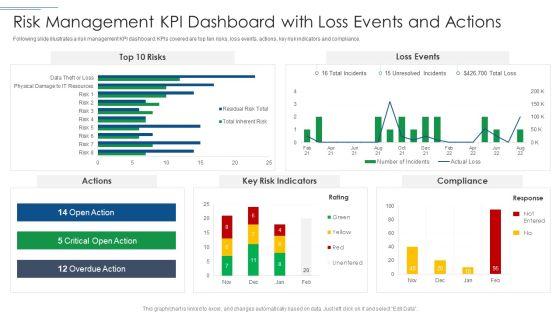

Slide 1 of 2
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Risk Management KPI Dashboard With Loss Events Brochure PDF bundle. Topics like Key Risk Indicators, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Kpi Dashboard To Track Security Risk Events Icons PDF. Use them to share invaluable insights on System Technology Risk, Governance Risk, Security Risk Events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF bundle. Topics like Business Growth, Risk Management, Organizational Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Mentioned slide provides information about the risks encountered by the company till date and their impact on existing business operations. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Encountered Risks Summary And Their Impact Assessment Professional PDF. Use them to share invaluable insights on Moderate Inherent Risk, Risks By Category, Financial and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
IT Security Risk Management Approach Introduction Determining The Priority Requirements Diagrams PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Determining The Priority Requirements Diagrams PDF bundle. Topics like Development Processes, Technology Environments, Purchasing Iot Products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This is a Table Of Contents It Security Risk Management Approach Introduction Matrix Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Governance Structure, Responsibility Matrix, Risk Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting IT Security Risk Management Approach Introduction Defining Business Priorities To Ensure Information Security Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Transparent Communication, Efficient Risk Management, Standardized Incident Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a IT Security Risk Management Approach Introduction Checklist For Effectively Managing Asset Security Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like System Location, System Accessibility, Information System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This is a Agenda Of IT Security Risk Management Approach Introduction Infographics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Security, Business Agility, Risk Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Deliver and pitch your topic in the best possible manner with this Table Of Contents For It Security Risk Management Approach Introduction Guidelines PDF. Use them to share invaluable insights on Companies Digitization Levels, Global Market Insights, About Security Program and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting IT Security Risk Management Approach Introduction Overview Of New It Policy Framework Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like It Security, It Policy Framework, Data Policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Information Security Program Themes PDF bundle. Topics like Evaluation And Direction, Organization Structure, Information Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Gap Identification Current Approach Formats PDF. Use them to share invaluable insights on Privacy Requirements, Mandatory Security, Planning Tasks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF bundle. Topics like Incident Management, Potential can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide provides information about risk based events that company will use to define the risks based on impact size and likelihood of occurrence. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Defining Risk Events Based On Impact Size Demonstration PDF bundle. Topics like Risk Level, Defining Risk Events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Addressing The Companies Digitization Levels By Sectors Clipart PDF bundle. Topics like Overall Digitization, Professional Services, Business Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
Presenting our innovatively structured Icons Slide For IT Security Risk Management Approach Introduction Template PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.

Slide 1 of 2
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF bundle. Topics like Risk Management, Measuring Performance, Managing Resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Summary Existing Security Management Capabilities Topics PDF bundle. Topics like Asset Management, Key Enablers, Communication Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Risk Management KPI Dashboard With Loss Events And Actions Mockup PDF bundle. Topics like Key Risk, Indicators Compliance, Loss Events can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide shows the stages involved in data security management program which also includes initiatives and activities such as develop data security team, analyze requirements, monitor policies periodically.Pitch your topic with ease and precision using this Stages Involved In Data IT Security Management Program Diagrams PDF This layout presents information on Identify Stakeholders, Security Requirements, Execute Maintain It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.


Slide 1 of 2
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
This slide provides information regarding entire duration of incident handling process which occur in various phases.This is a Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Categorization, Incident Resolution, Incident Prioritization You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 90 days plan sample pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide represents the plan for 60 days after implementing the cyber security model in the organization. Deliver an awe inspiring pitch with this creative it security managing information technology security 60 days plan professional pdf bundle. Topics like time to detect an incident, policy violations, data loss incidents, infected computers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
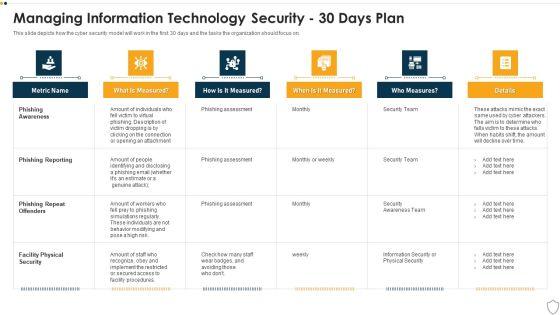
Slide 1 of 2
This slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Deliver and pitch your topic in the best possible manner with this it security managing information technology security 30 days plan themes pdf. Use them to share invaluable insights on phishing awareness, phishing reporting, phishing repeat offenders, facility physical security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 199 Item(s)
Page
