AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Cybersecurity risks PowerPoint Presentation Templates and Google Slides
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 198 Item(s)
Page








































































Slide 1 of 72
Take advantage of this well-researched and professionally-designed Cybersecurity Risk Assessment And Administration Plan Ppt PowerPoint Presentation Complete Deck With Slides to ace your next business meeting. Use this PPT complete deck to impress the management with your ideas for business growth and revenue increase. Use the seventy two slide Template Bundle to leave no stone unturned as you present each step of your process. Employ the visual tools within the slides such as graphs, charts, and tables to ensure that the audience can never look away from the presentation. With attractive visuals, easy to understand structure, and your knowledge, your presentation will have the attention it deserves. Download this PPT Template from the link below.


























































Slide 1 of 58
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the fifty eight slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.














































Slide 1 of 46
Pitch yourself both in house and outside by utilizing this complete deck. This modern security observation plan to eradicate cybersecurity risk and data breach ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty six slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.


























Slide 1 of 26
Induce strategic thinking by presenting this complete deck. Enthrall your audience by deploying this thought provoking PPT deck. It can be downloaded in both standard and widescreen aspect ratios, thus making it a complete package to use and deploy. Convey your thoughts and actions using the twentysix slides presented in this complete deck. Additionally, feel free to alter its components like color, graphics, design, etc, to create a great first impression. Grab it now by clicking on the download button below.


Slide 1 of 2
There are so many reasons you need a Table Of Contents For Cybersecurity Risk Assessment And Administration Plan Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.


Slide 1 of 2
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. This Risk Management Dashboard For Information Security Cybersecurity Risk Assessment Sample PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.


Slide 1 of 2
Retrieve professionally designed Information And Data Breach Impacting Customer Loyalty Cybersecurity Risk Assessment Infographics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.


Slide 1 of 2
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.


Slide 1 of 2
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Assessing Cost Of Information Breach In Different Countries Cybersecurity Risk Assessment Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.


Slide 1 of 2
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Boost your pitch with our creative Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.


Slide 1 of 2
This slide showcases graph for information security industry market growth in past and upcoming financial years. It can help to forecast the compounded annual growth rate of industry. Do you know about Slidesgeeks Market Growth Of Information Security Industry Cybersecurity Risk Assessment Portrait PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.


Slide 1 of 2
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. Retrieve professionally designed Cyber Attacks Faced By Organization In Previous Financial Year Cybersecurity Risk Assessment Background PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.


Slide 1 of 2
This graph covers the variety of activities such as enforcing Policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Reshaping Business In Digital Steps Required To Demonstrating Cybersecurity Risk Mitigation Brochure PDF bundle. Topics like Enforcing Security Policy, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Organization Transition Steps Required To Demonstrating Cybersecurity Risk Mitigation Download PDF. Use them to share invaluable insights on Enforcing Security Policy, Good Security Practices, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver an awe inspiring pitch with this creative Integration Of Digital Technology In Organization Steps Required To Demonstrating Cybersecurity Risk Mitigation Information PDF bundle. Topics like Practices Themselves, Providing Security, Appropriate Funding can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Slide 1 of 2
This is a IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technical Control, Management Controls, Operational Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Global Market Insights Cybersecurity Rules PDF bundle. Topics like Business Growth, Risk Management, Organizational Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. This is a IT Security Risk Management Approach Introduction Scorecard To Check Cybersecurity And Digital Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Specific Measures, Security Control, Cybersecurity Risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver an awe inspiring pitch with this creative Organization Reinvention Steps Required To Demonstrating Cybersecurity Risk Mitigation Designs PDF bundle. Topics like Steps Required Demonstrating, Cybersecurity Risk Mitigation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide illustrates the global market insights of cybersecurity covering statistics related to integrated risk management, investment in cybersecurity and digital transformation. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Global Market Insights Cybersecurity Ppt PowerPoint Presentation Gallery Clipart PDF bundle. Topics like Market Summary, Largest Market, Business Led can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
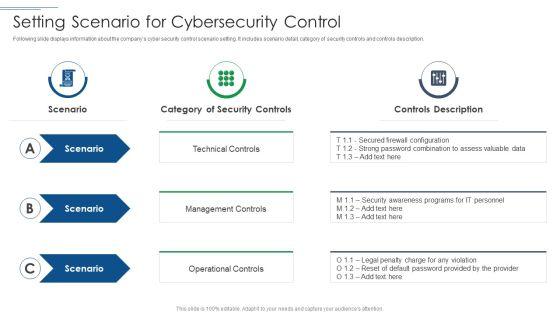
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF. Use them to share invaluable insights on Risk Prevention, Risk Prevention, Risk Occurrence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks.Deliver and pitch your topic in the best possible manner with this Accelerate Online Journey Now Steps Required To Demonstrating Cybersecurity Risk Mitigation Summary PDF Use them to share invaluable insights on Practices Themselves, Awareness Training, Appropriate Funding and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This graph covers the variety of activities such as enforcing policy, providing appropriate funding, mandating awareness training, etc. to avoid cybersecurity risks. Deliver and pitch your topic in the best possible manner with this Revolution In Online Business Steps Required To Demonstrating Cybersecurity Risk Mitigation Template PDF. Use them to share invaluable insights on Enforcing Security Policy, Providing Security Appropriate, Funding Mandating Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Following slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Threat And Vulnerability Management Dashboard Elements PDF Use them to share invaluable insights on Exposure Score, Remediation Tasks, Severity Distribution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Mentioned slide shows performance impact on security infrastructure after introducing risk assessment process. Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact On Security Infrastructure Performance Background PDF Use them to share invaluable insights on Assessment Process, Target Met After Introducing, Standard And Technology and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide displays performance analysis of current security infrastructure based on NIST core functions. Core functions included are identify, protect, detect, respond, recover. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Current Security Infrastructure Performance Analysis Clipart PDF bundle. Topics like Asset Management, Protect Data Security, Incident Mitigation Plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This is a Table Of Contents Cybersecurity Risk Administration Plan Introduction PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Present Scenario, Training And Budget, Managing The Risks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
Download our innovative and attention grabbing Icons Slide For Cybersecurity Risk Administration Plan Brochure PDF template. The set of slides exhibit completely customizable icons. These icons can be incorporated into any business presentation. So download it immediately to clearly communicate with your clientele.


Slide 1 of 2
This is a Cybersecurity Risk Administration Plan Table Of Contents Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Managing The Risk, Defining Risk Level, Setting Scenario For Security Control You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Following slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description.Presenting Cybersecurity Risk Administration Plan Setting Scenario For Security Control Topics PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Category Of Security Controls, Controls Description, Secured Firewall Configuration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide provides information regarding role and responsibilities of QA in DevOps for quality management. This is a Cybersecurity Risk Administration Plan Role And Responsibilities Of QA In Devops Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development And Implementation, Asset Classification And Control, Development Of Organizational You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Mitigation Plan For Resolving Encountered Threat Professional PDF Use them to share invaluable insights on Resources Required, Responsible Person, Expected Resolution Time and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration.This is a Cybersecurity Risk Administration Plan Employee Training Schedule Graphics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training Schedule You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Following slide defines the vulnerability ranking set by the firm. It includes information about vulnerability ranking, criteria and its description.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Defining Vulnerability Rating Introduction PDF Use them to share invaluable insights on Organization Is Not Capable, Resisting The Occurrence Of Attack, Drawback Is Identified and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Slide 1 of 2
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Defining Risk Level Icons PDF bundle. Topics like Extremely Critical, Requires Immediate, Operations Of Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures.This is a Cybersecurity Risk Administration Plan Defining Categories Of Information Security Threats Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disaster, Environmental Control Failures, Deliberate Software Attacks You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Presenting Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Incident Management, Asset Management, Risk Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This is a Agenda Of Cybersecurity Risk Administration Plan Demonstration PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Threat Identification And Vulnerability Impact Assessment Slides PDF bundle. Topics like Potential Vulnerability, Vulnerability Ranking, Vulnerability Impact can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide displays system management checklist. It includes system management activities and frequency of performing them.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Management Checklist Background PDF Use them to share invaluable insights on System Monitoring, Security Patches, Virus Scanning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan System Disposal Checklist Guidelines PDF bundle. Topics like Information Is Transferred, Hardcopy Information, Stored Information Is Removed can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF Use them to share invaluable insights on Accessible Within Organization, Individual System, Accessible To Key Shareholders and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Risk Reporting And Likelihood Summary PDF bundle. Topics like Unavailability Of Power, Risk Encountered, Attack Scenario can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Present Security Management Capabilities Of The Firm Rules PDF Use them to share invaluable insights on Assessing Information Security, Safeguarding Valuable, Vulnerability Intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Slide 1 of 2
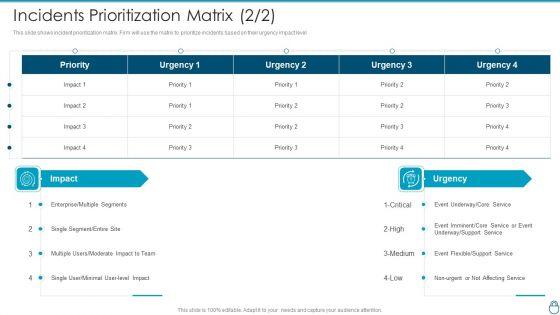
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Service Information PDF Use them to share invaluable insights on Enterprise Or Multiple Segments, Event Imminent, Affecting Service and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Slide 1 of 2
This slide shows incident prioritization matrix. Firm will use the matrix to prioritize incidents based on their urgency impact level.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incidents Prioritization Matrix Business Introduction PDF bundle. Topics like Business Unit Department, Functions Impaired, Medium Multiple can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide displays incident logging process of the firm. It covers information of process ID, procedure, its description and responsible person.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Incidents Logging Process Sample PDF Use them to share invaluable insights on Incident Assigned, Select Category And Priority, Reference To The Incident and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incident Management Tool We Will Use Summary PDF bundle. Topics like Automated Workflow, Notify Employee, Feature Description can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Impact Assessment Matrix Graphics PDF Use them to share invaluable insights on Minor To No Infringement, Suspected Malicious Intent, Operational and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Asset Criticality Of Identified System Components Professional PDF bundle. Topics like Impact Rating On Business, Criticality Rating, Impact Rating can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Presenting Cybersecurity Risk Administration Plan Multitiered Risk Management Framework Diagram Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Organization, Mission Or Business Processes, Information Systems In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Service Slides PDF bundle. Topics like Effects Of Damage, Vulnerability And Possible, Unauthorized Disclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Information Security Decision Framework PRISM Workflow Topics PDF Use them to share invaluable insights on Prioritization Weighting, Resource Allocation, Risk Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Incident Management Workflow Guidelines PDF bundle. Topics like Organize Your Team, Incident Resolution, Team Takes Action can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This slide represents risk assessment software dashboard for cybersecurity. It includes risk percentage, number of risks, risk analysis progress, risk response progress, risk rating etc. Showcasing this set of slides titled Risk Assessment Software Dashboard For Cybersecurity Ppt PowerPoint Presentation Gallery Pictures PDF. The topics addressed in these templates are Risk Rating Breakdown, Action Plan Breakdown, Top 5 Entities Prone To Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.


Slide 1 of 2
This slide represents the cybersecurity risks associated with Russia and Ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions.This is a data wiper spyware attack cybersecurity risks of an escalating russia ukraine conflict background pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like extensive cyber capabilities, russian invasion would, measures as economic warfare You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
SHOW
- 60
- 120
- 180
DISPLAYING: 60 of 198 Item(s)
Page
