AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
Computing risk PowerPoint Presentation Templates and Google Slides
30 Item(s)


Slide 1 of 2
This slide exhibits risk and mitigation techniques for cloud platform. It cover threats such as security, data ownership, record management, SLA, change management and portability. Persuade your audience using this cloud management cloud computing platform and technologies risk and mitigation strategies summary pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including Risks, Mitigation Strategies, Data Ownership, Records Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Slide 1 of 2
Presenting cloud computing platform and technologies risk management icon infographics pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cloud computing platform and technologies risk management icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.


Slide 1 of 2
This slide depicts the challenges of end user computing and it includes time sharing, enter virtualization, enter PC, re aggregation and complexity reigns supreme. Presenting customer mesh computing it potential risks of end user computing summary pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like time sharing, complexity reigns supreme, enter virtualization. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Slide 1 of 2
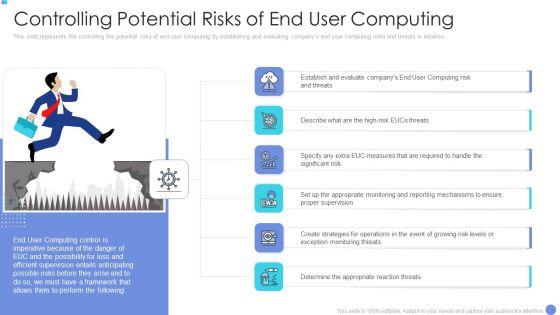
This slide represents the controlling the potential risks of end user computing by establishing and evaluating companys end user computing risks and threats in advance. Presenting customer mesh computing it controlling potential risks of end user computing structure pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like controlling potential risks of end user computing. In addition, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide provides a detailed strategy for identifying and mitigation major risks hampering the cloud infrastructure. It shows key risks, key challenges, control action and mitigation measures.Deliver an awe inspiring pitch with this creative mesh computing infrastructure adoption process cloud risk mitigation strategy with challenges template pdf bundle. Topics like damage to application, exchange management, clustering and organizing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.


Slide 1 of 2
This is a business risk related to cloud computing data ppt outline slide portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data security, technology, financial, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Slide 1 of 2
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting cloud security risks or threats cloud computing security it ppt icon pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like revenue losses, loss of data, shared vulnerabilities, compliance violations, malware attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this phase 1 understand cloud utilization and risk cloud computing security it ppt summary smartart pdf. Use them to share invaluable insights on recognize critical data, infrastructure, evaluation, vulnerabilities, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.


Slide 1 of 2
Technology Guide For Serverless Computing Business Risk Related To Cloud Computing Data Portrait PDF
This is a technology guide for serverless computing business risk related to cloud computing data portrait pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, data security and regulatory, technology, operational, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Presenting technology guide for serverless computing business risk related to cloud computing vendor brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
This is a business risk related to cloud computing ppt gallery design ideas pdf. template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, vendor, data security and regulatory, technology, operational. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
This is a mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing vendor designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, data security and regulatory, technology, operational, vendor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.


Slide 1 of 2
Presenting mesh computing technology hybrid private public iaas paas saas workplan business risk related to cloud computing data diagrams pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like financial, data security, technology, operational, vendor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling determining roles and responsibilities for risk handling mockup pdf. This is a four stage process. The stages in this process are chief risk officer, chief information security officer, senior management and executive, line management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling risk assessment matrix ppt show design ideas pdf. This is a four stage process. The stages in this process are minor, significant, serious, catastrophic, insignificant. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling categorization of cyber risks ppt gallery template pdf. This is a five stage process. The stages in this process are low risk, medium risk, high risk, severe risk, extreme risk. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling dashboard cyber risk management download pdf. The topics discussed in these slides are risk rating breakdown, risk heat map, action plan breakdown, risk analysis progress, response progress for risks. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling cybersecurity risk management worksheet ideas pdf. The topics discussed in these slides are identified risk, risk likelihood, risk severity, implement controls, risk treatment, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security incident handling cybersecurity risk management action plan diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason for risk rating, action, required resources, responsible person, duration, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.


Slide 1 of 2
Presenting this set of slides with name computer security risk assessment ppt powerpoint presentation portfolio layouts cpb pdf. This is an editable Powerpoint four stages graphic that deals with topics like computer security risk assessment to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.






Slide 1 of 6
This slide presents issue categories and their solutions in cloud computing, helpful for businesses to take advantage of digital transformation. It includes challenges such as security issues, cost management, lack of resources and compliance Presenting Issues Classification And Risks In Cloud Computing Background PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Security Issues, Cost Management, Lack Resources. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.






Slide 1 of 6
This slide depicts the challenges of end user computing and it includes time sharing, enter virtualization, enter PC, re aggregation and complexity reigns supreme. This Potential Risks Of End User Computing Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Potential Risks Of End User Computing Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.






Slide 1 of 6
This slide represents the controlling the potential risks of end user computing by establishing and evaluating companys end user computing risks and threats in advance. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Controlling Potential Risks Of End User Computing Ppt PowerPoint Presentation File Pictures PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Controlling Potential Risks Of End User Computing Ppt PowerPoint Presentation File Pictures PDF today and make your presentation stand out from the rest.






Slide 1 of 6
This slide depicts the challenges of end user computing and it includes time sharing, enter virtualization, enter PC, re-aggregation and complexity reigns supreme.This is a Computer Virtualization Potential Risks Of End User Computing Clipart PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Degrees Complexity, Reigns Supreme, Enter Virtualization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.






Slide 1 of 6
This slide represents the controlling the potential risks of end user computing by establishing and evaluating companys end user computing risks and threats in advance.This is a Computer Virtualization Controlling Potential Risks Of End User Computing Structure PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Exception Monitoring, Proper Supervision, Monitoring Reporting. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.






Slide 1 of 6
This slide depicts the challenges of end user computing and it includes time sharing, enter virtualization, enter PC, re-aggregation and complexity reigns supreme.This is a End User Computing Potential Risks Of End User Computing Inspiration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enter Virtualization, Complexity Reigns, Processing Power. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.






Slide 1 of 6
This slide represents the controlling the potential risks of end user computing by establishing and evaluating companys end user computing risks and threats in advance.Presenting End User Computing Controlling Potential Risks Of End User Computing Designs PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Reporting Mechanisms, Proper Supervision, Appropriate Monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.






Slide 1 of 6
This slide depicts the challenges of end user computing and it includes time sharing, enter virtualization, enter PC, re aggregation and complexity reigns supreme.This is a VID Potential Risks Of End User Computing Structure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enter Virtualization, Complexity Reigns, Administrators Desire. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.






Slide 1 of 6
This slide represents the controlling the potential risks of end user computing by establishing and evaluating companys end user computing risks and threats in advance.This is a VID Controlling Potential Risks Of End User Computing Formats PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Computing Control, Efficient Supervision, Anticipating Possible. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.






Slide 1 of 6
This slide illustrates different digitally enabled cyber computing applications. It includes risk severity chart, action cost along with risk owner details and implementation due date. Showcasing this set of slides titled Cyber Computing Services Risk Analysis Software Status Chart Portrait PDF. The topics addressed in these templates are Risk Treatment, Risk Owner, Implementation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
30 Item(s)
