Threat Intelligence

Security Information And Event Management Strategies For Financial Audit And Compliance Next Evolution Of Siem Software Download PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting security information and event management strategies for financial audit and compliance next evolution of siem software download pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like user entity and behavior analytics, network traffic analysis, endpoint monitoring, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Enhancing Cyber Safety With Vulnerability Administration Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. Presenting enhancing cyber safety with vulnerability administration next evolution of siem software sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like endpoint monitoring, network traffic analysis, user entity and behavior analytics, threat intelligence, siem foundation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
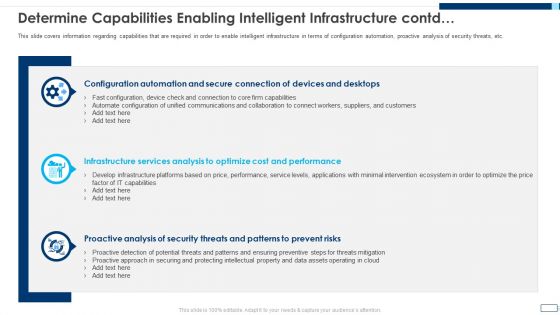
Evolving BI Infrastructure Determine Capabilities Enabling Intelligent Infrastructure Contd Template PDF
This slide covers information regarding capabilities that are required in order to enable intelligent infrastructure in terms of configuration automation, proactive analysis of security threats, etc. This is a evolving bi infrastructure determine capabilities enabling intelligent infrastructure contd template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like configuration automation, infrastructure services analysis, proactive analysis. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
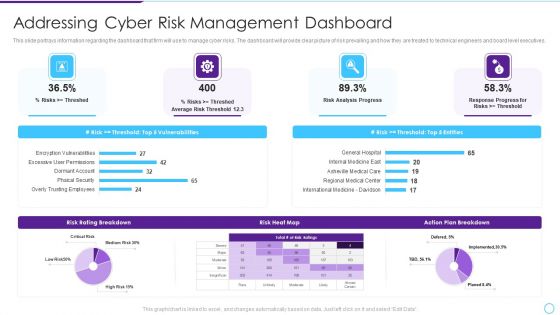
Intelligent Infrastructure Addressing Cyber Risk Management Dashboard Formats PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber risks. The dashboard will provide clear picture of risk prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this Intelligent Infrastructure Addressing Cyber Risk Management Dashboard Formats PDF. Use them to share invaluable insights on Risk Analysis Progress, Risk Rating Breakdown, Risk Heat Map, Action Plan Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Intelligent Infrastructure Determine Sprints Management Timeline Diagrams PDF
The slide displays information regarding various crucial activities such as release management, configuration management, etc. are transformed into small attainable sprints tasks by tracking their progress through the timeline associated to them. Deliver and pitch your topic in the best possible manner with this Intelligent Infrastructure Determine Sprints Management Timeline Diagrams PDF. Use them to share invaluable insights on Release Management, Configuration Management, Problem Management, Incident Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Use Case Of Intelligent Automation Sample PDF
Following slide showcases cognitive automation use case for service business to improve business performance and productivity. It includes problems such as payroll management and Invoice management with respective actions, and results. Presenting Business Use Case Of Intelligent Automation Sample PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Payroll Management, Invoice Management, Actions. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
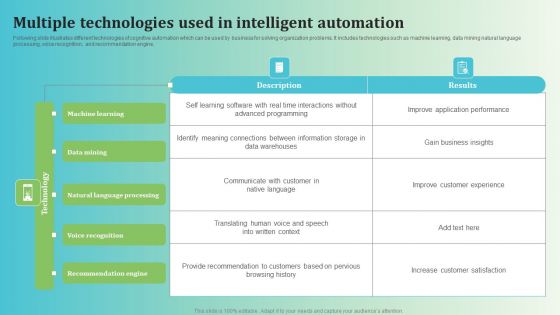
Multiple Technologies Used In Intelligent Automation Background PDF
Following slide illustrates different technologies of cognitive automation which can be used by business for solving organization problems. It includes technologies such as machine learning, data mining natural language processing, voice recognition, and recommendation engine. Showcasing this set of slides titled Multiple Technologies Used In Intelligent Automation Background PDF. The topics addressed in these templates are Machine Learning, Data Mining, Natural Language Processing . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
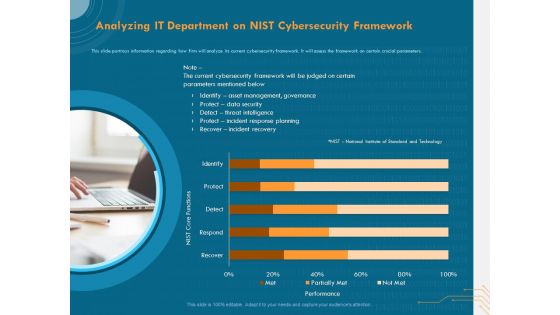
Cyber Security Implementation Framework Analyzing IT Department On NIST Cybersecurity Framework Topics PDF
Presenting this set of slides with name cyber security implementation framework analyzing it department on nist cybersecurity framework topics pdf. This is a one stage process. The stages in this process are asset management, governance, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
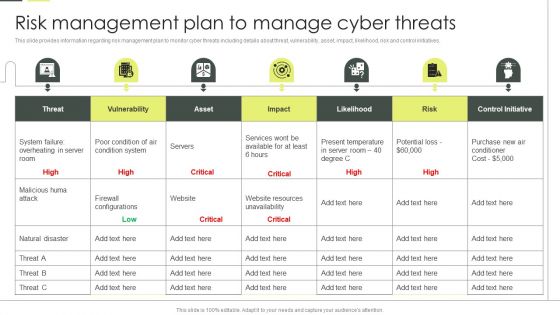
Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF
This slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Building An IT Strategy Plan For Business Expansion Risk Management Plan To Manage Cyber Threats Professional PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
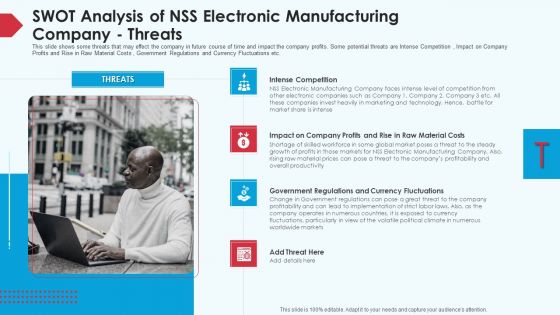
Skill Shortage In A Production Firm Case Study Solution SWOT Analysis Of NSS Electronic Manufacturing Company Threats Graphics PDF
This slide shows some threats that may effect the company in future course of time and impact the company profits. Some potential threats are Intense Competition , Impact on Company Profits and Rise in Raw Material Costs , Government Regulations and Currency Fluctuations etc. Presenting skill shortage in a production firm case study solution SWOT analysis of NSS electronic manufacturing company threats graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like threats, intense competition, company profits and rise in raw material costs, government regulations and currency fluctuations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
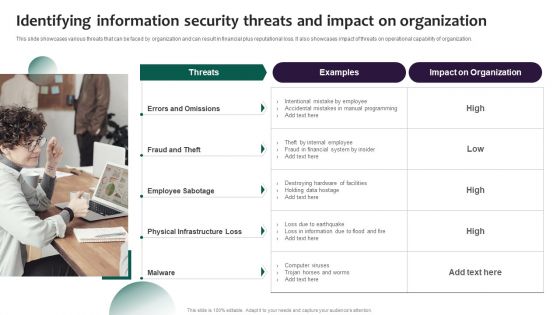
Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Apples Strategy To Achieve Top Brand Value Position Addressing Threats Associated With Apple That Negatively Clipart PDF
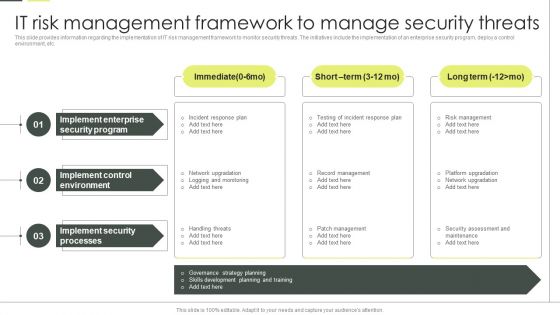
Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF
This slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Building An IT Strategy Plan For Business Expansion IT Risk Management Framework To Manage Security Threats Background PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Key Phase Of Crisis Communication Management Plan Stage 1 Pre Crisis Analysis For Identifying Potential Threats Mockup PDF
The slide illustrates the steps involved in pre-crisis stage to minimize the potential threats. Various steps included are crisis anticipation, crisis communication team, selection and training of spokesperson, etc Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Key Phase Of Crisis Communication Management Plan Stage 1 Pre Crisis Analysis For Identifying Potential Threats Mockup PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Ppt PowerPoint Presentation Complete Deck With Slides
With well-researched insights and carefully-constructed design, this Enhancing Process Improvement By Regularly Managing Real Estate Project Threats Ppt PowerPoint Presentation Complete Deck With Slides is all that you need for your next business meeting with clients and win them over. Add your data to graphs, charts, and tables that are already ready to display it with stunning visuals and help your audience recall your work. With this PPT Complete Deck, you will be able to display your knowledge of the subject as well as your skills as a communicator. Share your ideas and make an impact on the audience with this PowerPoint Layout and ensure that you are known as a presentation professional. Download this PPT Template Bundle to create the most interesting presentation anyone has ever seen.

Executing Security Management Program To Mitigate Threats And Safeguard Confidential Organizational Data Ppt PowerPoint Presentation Complete Deck
This complete deck acts as a great communication tool. It helps you in conveying your business message with personalized sets of graphics, icons etc. Comprising a set of fourtytwo slides, this complete deck can help you persuade your audience. It also induces strategic thinking as it has been thoroughly researched and put together by our experts. Not only is it easily downloadable but also editable. The color, graphics, theme any component can be altered to fit your individual needs. So grab it now.
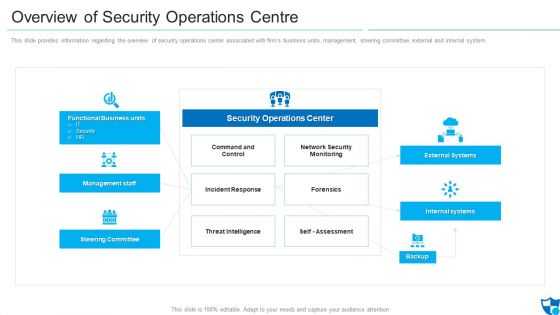
Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
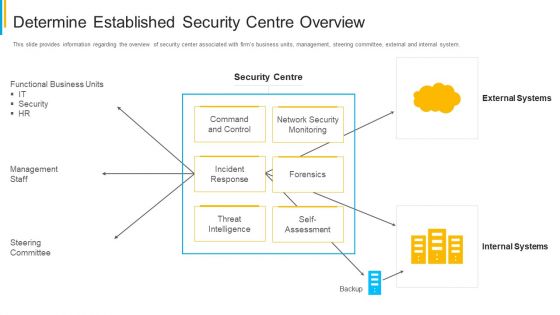
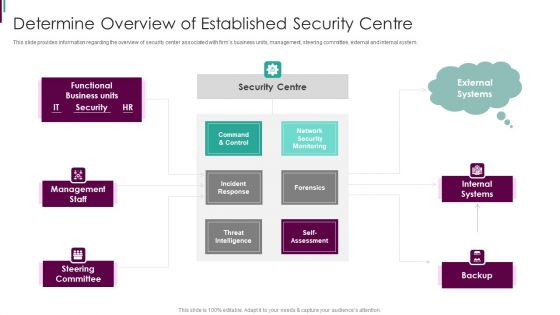
Project Security Administration IT Determine Established Security Centre Overview Infographics PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this project security administration it determine established security centre overview infographics pdf. Use them to share invaluable insights on functional business units, management staff, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
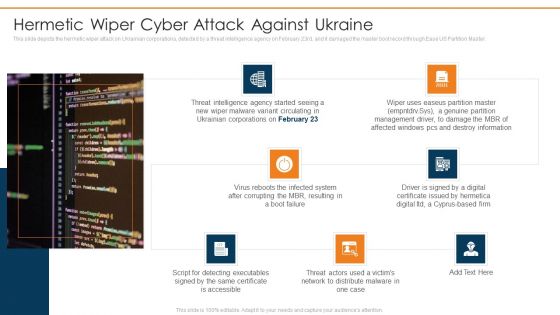
Data Wiper Spyware Attack Hermetic Wiper Cyber Attack Against Ukraine Slides PDF
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Ease US Partition Master.Deliver an awe inspiring pitch with this creative data wiper spyware attack hermetic wiper cyber attack against ukraine slides pdf bundle. Topics like hermetic wiper cyber attack against ukraine can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
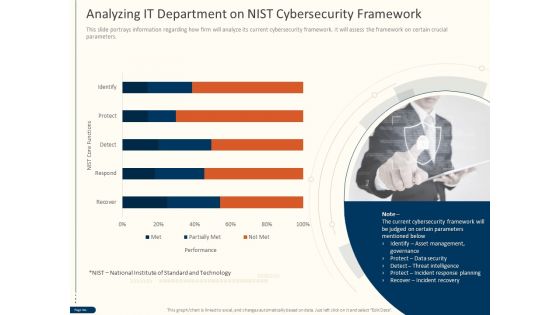
Cyber Security For Your Organization Analyzing IT Department On Nist Cybersecurity Framework Ppt Gallery Show PDF
Presenting this set of slides with name cyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdfcyber security for your organization analyzing it department on nist cybersecurity framework ppt gallery show pdf. This is a one stage process. The stages in this process are performance, nist core functions, technology, data security, threat intelligence, incident response planning, incident recovery. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
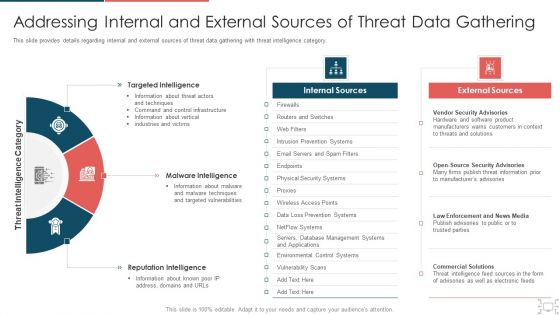
cyber security administration in organization addressing internal and external sources of gathering structure pdf
This slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. This is a cyber security administration in organization addressing internal and external sources of gathering structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like targeted, sources, internal, intelligence, reputation . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
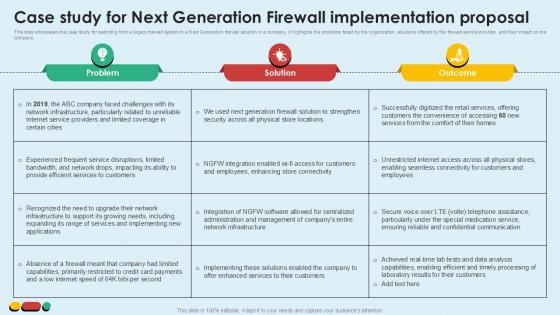
Case Study For Next Generation Intelligent Intrusion Prevention System Ppt Example
This slide showcases the case study for switching from a legacy firewall system to a Next Generation firewall solution in a company. It highlights the problems faced by the organization, solutions offered by the firewall service provider, and their impact on the company.Create an editable Case Study For Next Generation Intelligent Intrusion Prevention System Ppt Example that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Case Study For Next Generation Intelligent Intrusion Prevention System Ppt Example is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Case Study Intelligent Food Packaging Quality Control Guide For Food PPT Sample
This slide brings forth a case study related to intelligent food packaging, which can be implemented by companies to monitor food quality for perishable items. The elements covered in the slide, her problems, solutions, and diagrammatic representation of the model. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Case Study Intelligent Food Packaging Quality Control Guide For Food PPT Sample a try. Our experts have put a lot of knowledge and effort into creating this impeccable Case Study Intelligent Food Packaging Quality Control Guide For Food PPT Sample. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

How Sentiment Analysis Operates While Preprocessing Emotionally Intelligent Insights Leveraging AI SS V
This slide provides information regarding the functioning of the sentiment analysis approach while detecting the core message of the text. The technique works by determining core message of the text with preprocessing and it also detect toxic content and categorizes it categories such as threats, insults, etc. Are you searching for a How Sentiment Analysis Operates While Preprocessing Emotionally Intelligent Insights Leveraging AI SS V that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download How Sentiment Analysis Operates While Preprocessing Emotionally Intelligent Insights Leveraging AI SS V from Slidegeeks today.
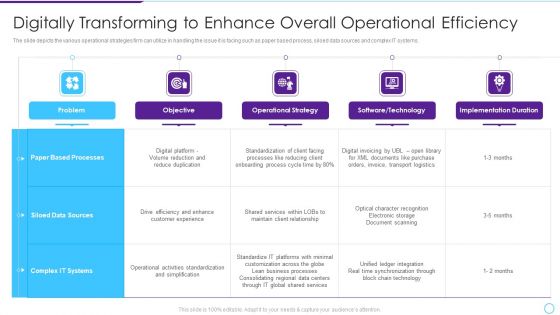
Intelligent Infrastructure Digitally Transforming To Enhance Overall Operational Efficiency Ideas PDF
The slide depicts the various operational strategies firm can utilize in handling the issue it is facing such as paper based process, siloed data sources and complex IT systems. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Digitally Transforming To Enhance Overall Operational Efficiency Ideas PDF bundle. Topics like Problem, Objective, Operational Strategy, Software, Technology, Implementation Duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
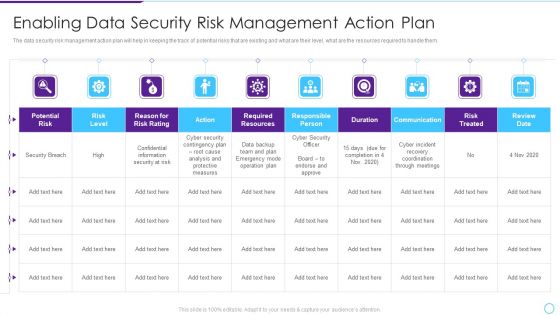
Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF bundle. Topics like Potential Risk, Risk Level, Action, Risk Treated, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Process Automation IPA Risk And Safety Factors Associated With Cobots Diagrams PDF
This slide represents the risk and safety factors associated with cobots so humans can work with them without harm. The safety measures include safety monitored stop, hand guiding, speed and separation monitoring, and power and force limiting. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Intelligent Process Automation IPA Risk And Safety Factors Associated With Cobots Diagrams PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Investigations by HR, Phishing Detection And Prevention, Risk Mitigation of Left Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
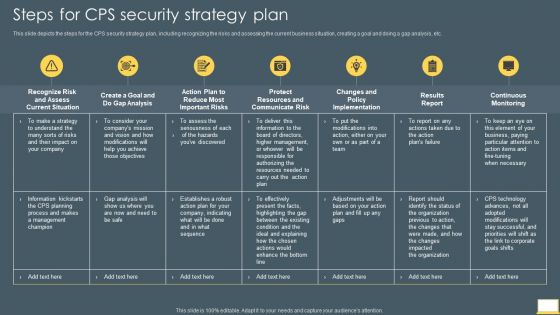
Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF. Use them to share invaluable insights on Gap Analysis, Protect Resources, Communicate Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
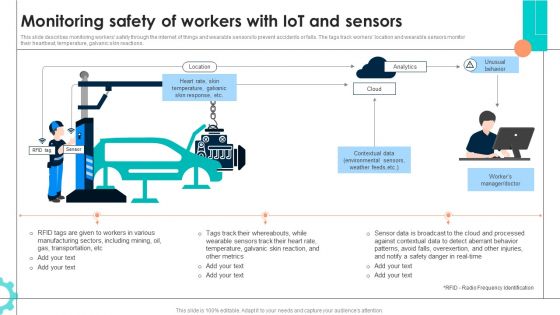
Intelligent Manufacturing Monitoring Safety Of Workers With Iot And Sensors Inspiration PDF
This slide describes monitoring workers safety through the internet of things and wearable sensors to prevent accidents or falls. The tags track workers location and wearable sensors monitor their heartbeat, temperature, galvanic skin reactions. Present like a pro with Intelligent Manufacturing Monitoring Safety Of Workers With Iot And Sensors Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well arranged Intelligent Manufacturing Role Of Cyber Security In Manufacturing Automation Ideas PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
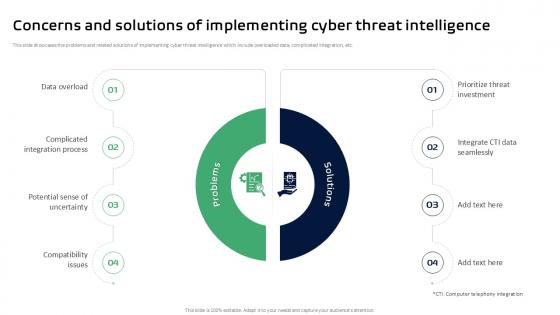
Concerns And Solutions Of Implementing Cyber Ppt Sample
This slide showcases the problems and related solutions of implementing cyber threat intelligence which include overloaded data, complicated integration, etc. Get a simple yet stunning designed Concerns And Solutions Of Implementing Cyber Ppt Sample. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Concerns And Solutions Of Implementing Cyber Ppt Sample can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
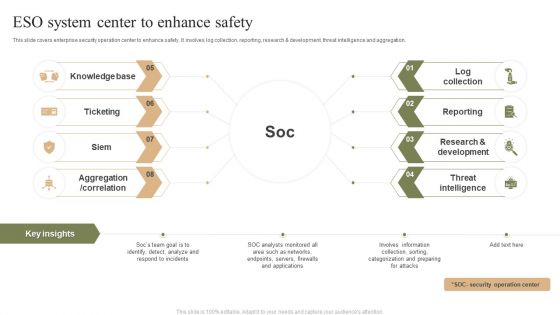
ESO System Center To Enhance Safety Ppt PowerPoint Presentation Gallery Demonstration PDF
This slide covers enterprise security operation center to enhance safety. It involves log collection, reporting, research and development, threat intelligence and aggregation. Persuade your audience using this ESO System Center To Enhance Safety Ppt PowerPoint Presentation Gallery Demonstration PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Knowledge Base, Ticketing, Siem, Aggregation, Correlation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

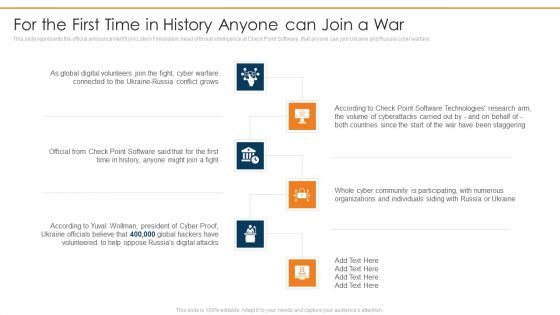
Russian Cyber Attacks On Ukraine IT For The First Time In History Ideas PDF
This slide represents the official announcement from Lotem Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare. Presenting russian cyber attacks on ukraine it for the first time in history ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like technologies, global, organizations, community. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Data Wiper Spyware Attack For The First Time In History Anyone Can Join A War Clipart PDF
This slide represents the official announcement from Lotem Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare.This is a data wiper spyware attack for the first time in history anyone can join a war clipart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like global digital volunteers, connected to the ukraine russia, official from check You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Developing Business Analytics Framework Determine Overview Of Established Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Developing Business Analytics Framework Determine Overview Of Established Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Command And Control, Incident Response, Threat Intelligence You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF
This slide depicts the hermetic wiper attack on ukrainian corporations, detected by a threat intelligence agency on february 23rd, and it damaged the master boot record through eases partition master. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
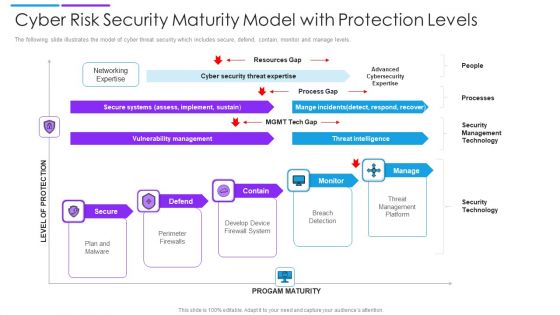
Cyber Risk Security Maturity Model With Protection Levels Mockup PDF
The following slide illustrates the model of cyber threat security which includes secure, defend, contain, monitor and manage levels. Persuade your audience using this cyber risk security maturity model with protection levels mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including secure systems, vulnerability management, threat intelligence. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Technology Evaluation Process Checklist For IT Process Excellence Rules PDF
This slide signifies the checklist on risk assessment for effective IT process excellence. It includes various questions related to the strategies that are either implemented in an organisation for growth. Persuade your audience using this technology evaluation process checklist for it process excellence rules pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including integrate threat intelligence, security strategy, develop and implement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
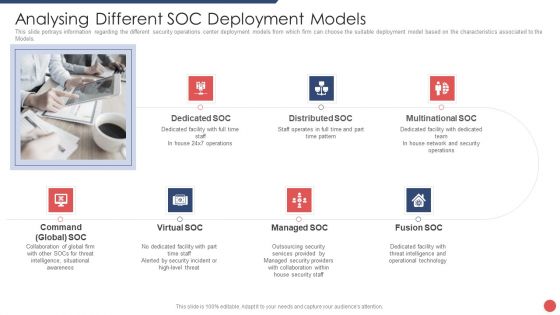
Security Functioning Centre Analysing Different SOC Deployment Models Template PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the Models. This is a security functioning centre analysing different soc deployment models template pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like distributed, network, security operations, operational technology, threat intelligence. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
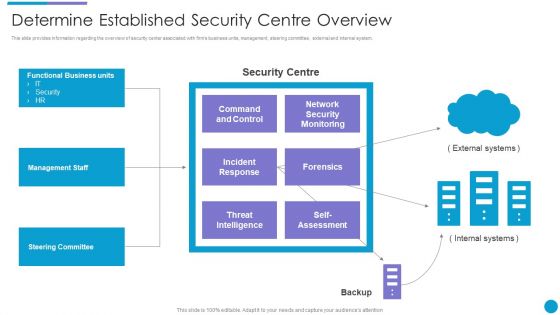
Major Techniques For Project Safety IT Determine Established Security Centre Overview Summary PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting major techniques for project safety it determine established security centre overview summary pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, functional business units, threat intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
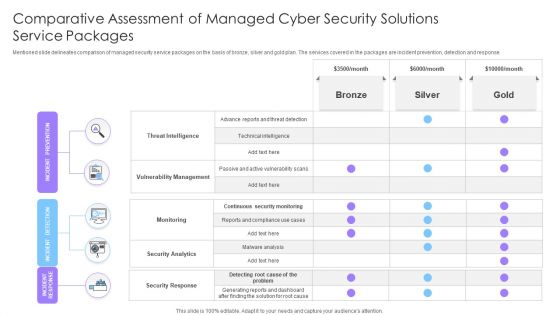
Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

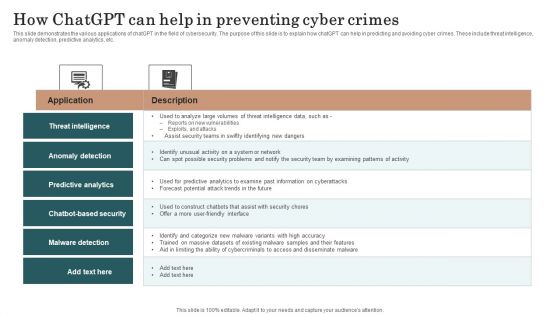
How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Make sure to capture your audiences attention in your business displays with our gratis customizable How Chatgpt Can Help In Preventing Cyber Crimes Chat Generative Pre Trained Transformer Summary PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
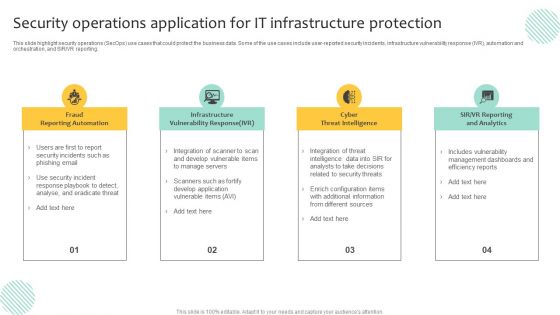
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Applications Of Big Data Monitoring In Cyber Security Themes pdf
This slide depicts the applications of big data analytics in implementing cybersecurity. The purpose of this slide is to help the business utilize big data security analytics in an appropriate manner for safeguarding business information. It includes data segmentation and clustering, tie series analysis and forecasting, etc. Pitch your topic with ease and precision using this Applications Of Big Data Monitoring In Cyber Security Themes pdf. This layout presents information on Data Segmentation, Security Research, Threat Intelligence. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Ukraine Cyberwarfare For The First Time In History Anyone Can Join A War Mockup Pdf
This slide represents the official announcement from Lotte Finkelstein, head of threat intelligence at Check Point Software, that anyone can join Ukraine and Russia cyber warfare. This is a ukraine cyberwarfare for the first time in history anyone can join a war mockup pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like as global digital volunteers join the fight, cyber warfare connected to the ukraine russia conflict grows, official from check point software said that for the first time in history, anyone might join a fight. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ukraine Cyberwarfare Hermetic Wiper Cyber Attack Against Ukraine Designs Pdf
This slide depicts the hermetic wiper attack on Ukrainian corporations, detected by a threat intelligence agency on February 23rd, and it damaged the master boot record through Eases Partition Master. This is a ukraine cyberwarfare hermetic wiper cyber attack against ukraine designs pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like script for detecting executables signed by the same certificate is accessible, virus reboots the infected system after corrupting the mbr, resulting in a boot failure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF
This slide represents the official announcement from lotem finkelstein, head of threat intelligence at check point software, that anyone can join ukraine and russia cyber warfare. Slidegeeks is here to make your presentations a breeze with Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Risk Approaches For Security Protection Structure PDF
The following slide highlights the cyber threat approaches which include traditional and artificial intelligence based approaches to counter threats. Showcasing this set of slides titled cyber risk approaches for security protection structure pdf. The topics addressed in these templates are traditional approach, ai based approach, cybersecurity threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF
This slide describes the critical functions of security operations. The purpose of this slide is to demonstrate the various functions performed by SecOps teams in an organization. The main functions include threat intelligence, security monitoring, incident response, forensics and root cause analysis, etc. Boost your pitch with our creative Cybersecurity Operations Cybersecops Critical Functional Areas Of Secops Teams Background PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
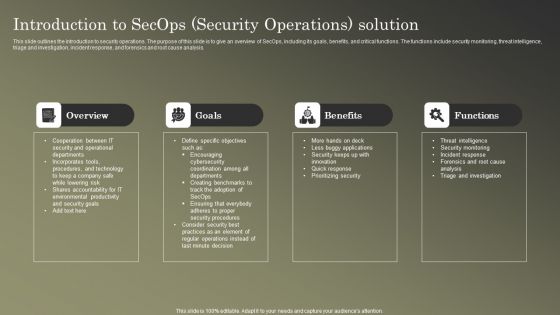
Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF
This slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Want to ace your presentation in front of a live audience Our Cybersecurity Operations Cybersecops Introduction To Secops Security Operations Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF
This slide outlines the critical outcomes that are handled by the security operations team. The purpose of this slide is to demonstrate the various key outcomes, their activities, responsible person and remarks. The main outcomes include incident management, incident preparation and threat intelligence. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF
This slide demonstrates the various applications of chatGPT in the field of cybersecurity. The purpose of this slide is to explain how chatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Boost your pitch with our creative Chatgpt Incorporation Into Web Apps How Chatgpt Can Help In Preventing Cyber Crimes Clipart PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
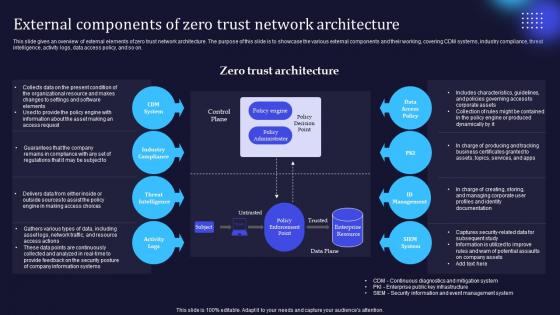
Zero Trust Model External Components Of Zero Trust Network Architecture
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Zero Trust Model External Components Of Zero Trust Network Architecture to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
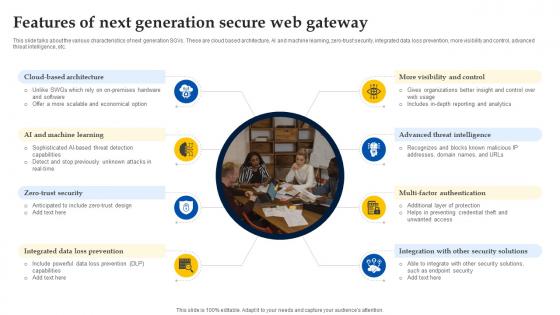
Web Access Control Solution Features Of Next Generation Secure Web Gateway
This slide talks about the various characteristics of next generation SGVs. These are cloud based architecture, AI and machine learning, zero-trust security, integrated data loss prevention, more visibility and control, advanced threat intelligence, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Web Access Control Solution Features Of Next Generation Secure Web Gateway to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF
This slide demonstrates the various applications of ChatGPT in the field of cybersecurity. The purpose of this slide is to explain how ChatGPT can help in predicting and avoiding cyber crimes. These include threat intelligence, anomaly detection, predictive analytics, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Chatgpt Can Help In Preventing Cyber Crimes Slides PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
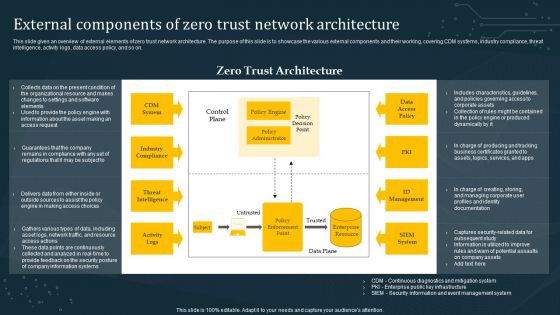
External Components Of Zero Trust Network Architecture Information PDF
This slide gives an overview of external elements of zero trust network architecture. The purpose of this slide is to showcase the various external components and their working, covering CDM systems, industry compliance, threat intelligence, activity logs, data access policy, and so on. Welcome to our selection of the External Components Of Zero Trust Network Architecture Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today

 Home
Home