Table Of Safety Contents

Comparing Tools Required For Implementing Technology Transformation Template PDF
This slide shows the comparison of technology transformation tools on the basis of features such as team progress tracking, real time communication functionality, data security and task automation.Find highly impressive Comparing Tools Required For Implementing Technology Transformation Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Comparing Tools Required For Implementing Technology Transformation Template PDF for your upcoming presentation. All the presentation templates are 100precent editable and you can change the color and personalize the content accordingly. Download now.

Transform Management Instruction Schedule Technological Change Management Designs PDF
This slide represents the strategic plan developed to facilitate training to employees related to introducing new technological advancements in the enterprise. It includes details related to training topics such as cloud computing, cyber security, data storage etc. Find highly impressive Transform Management Instruction Schedule Technological Change Management Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Transform Management Instruction Schedule Technological Change Management Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Characteristics Impact Of Blockchain On Modern Systems Introduction PDF
This slide represents the critical features of hybrid blockchain technology. The purpose of this slide is to showcase the characteristics of hybrid blockchains over private and public blockchains. These include data security, low transaction costs, a closed ecosystem, new rules, and so on. Boost your pitch with our creative Characteristics Impact Of Blockchain On Modern Systems Introduction PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Cios Guide To Optimize Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Diagrams PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. Explore a selection of the finest Cios Guide To Optimize Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Diagrams PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cios Guide To Optimize Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Diagrams PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Workplace Portable Device Monitoring And Administration Determining Firm Current Capabilities In Managing Mobile Devices Icons PDF
This slide portrays information regarding assessment of current mobile device security framework on certain standards. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Workplace Portable Device Monitoring And Administration Determining Firm Current Capabilities In Managing Mobile Devices Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
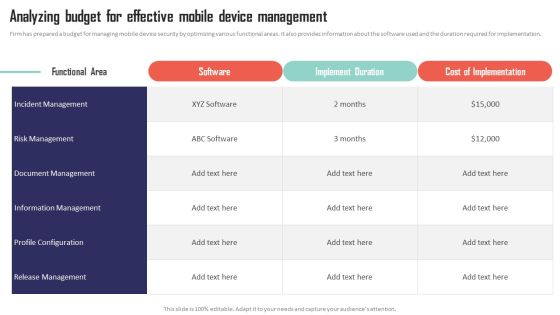
Mobile Device Management Analyzing Budget For Effective Mobile Device Management Sample PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Find highly impressive Mobile Device Management Analyzing Budget For Effective Mobile Device Management Sample PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Mobile Device Management Analyzing Budget For Effective Mobile Device Management Sample PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Deploying Banking Transaction Major Roles And Responsibilities Of Financial Diagrams PDF
The following slide Major roles and responsibilities of financial security department . It includes information about risk level determination, laws and regulations, team training, operational compliance, automatic workflows, red flags, etc. Explore a selection of the finest Deploying Banking Transaction Major Roles And Responsibilities Of Financial Diagrams PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Deploying Banking Transaction Major Roles And Responsibilities Of Financial Diagrams PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Critical Measures For Ensuring Streamlining Employee Verification Process To Ensure Designs PDF
This slide provides information about streamlining employee verification process at workplace to ensure people security by performing pre and post employee verification. Find highly impressive Critical Measures For Ensuring Streamlining Employee Verification Process To Ensure Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Critical Measures For Ensuring Streamlining Employee Verification Process To Ensure Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Mobile Device Management For Improving IT Operations Analyzing Budget For Effective Mobile Elements PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Mobile Device Management For Improving IT Operations Analyzing Budget For Effective Mobile Elements PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Non Fungible Token Methodology IT How Nfts Benefit Businesses Designs PDF
This slide describes the benefits of NFTs to businesses as they prevent the decline of consumer engagement by generating secure revenue resources and so on. Find highly impressive Non Fungible Token Methodology IT How Nfts Benefit Businesses Designs PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Non Fungible Token Methodology IT How Nfts Benefit Businesses Designs PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
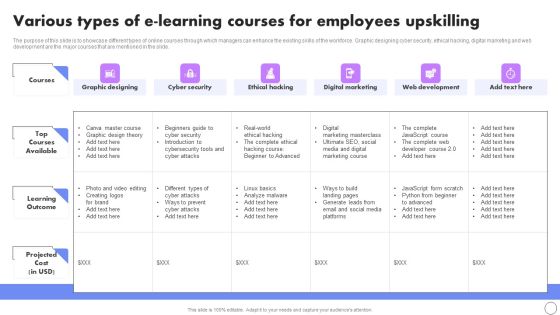
Various Types Of E Learning Courses For Employees Upskilling Rules PDF
The purpose of this slide is to showcase different types of online courses through which managers can enhance the existing skills of the workforce. Graphic designing cyber security, ethical hacking, digital marketing and web development are the major courses that are mentioned in the slide. Boost your pitch with our creative Various Types Of E Learning Courses For Employees Upskilling Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
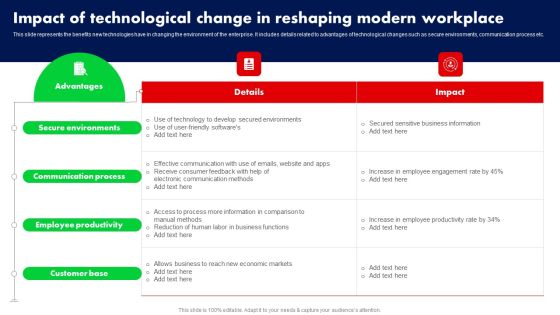
Impact Of Technological Change In Reshaping Modern Workplace Ppt PowerPoint Presentation File Professional PDF
This slide represents the benefits new technologies have in changing the environment of the enterprise. It includes details related to advantages of technological changes such as secure environments, communication process etc. Find highly impressive Impact Of Technological Change In Reshaping Modern Workplace Ppt PowerPoint Presentation File Professional PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Impact Of Technological Change In Reshaping Modern Workplace Ppt PowerPoint Presentation File Professional PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Deployment Of Omnichannel Banking Solutions Ways To Improve IVR Payment Platform For Customers Diagrams PDF
This slide covers strategies to enhance interactive voice response payment technology used by customers. The purpose of this template is to provide procedure for improving customer experience. It includes ways such as faster billing dispute resolution, advanced security authentication, fast payment processing, no hidden charges, etc. Find highly impressive Deployment Of Omnichannel Banking Solutions Ways To Improve IVR Payment Platform For Customers Diagrams PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Deployment Of Omnichannel Banking Solutions Ways To Improve IVR Payment Platform For Customers Diagrams PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
Omnichannel Strategy Implementation For Banking Solutions Techniques To Optimize API Bill Payment Option Icons PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Omnichannel Strategy Implementation For Banking Solutions Techniques To Optimize API Bill Payment Option Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Email Security Encryption And Data Loss Prevention Your Investment For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed investment of your client into various security softwares. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention your investment for e mail security proposal diagrams pdf bundle. Topics like product, free version, starting price, frequency, per user can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Clinical Trial Phases With Goals And Patients Number Clinical Research Trial Phases Download PDF
In this slide, tabulation is done of key objectives of each step of clinical research trials. It also provides information regarding the count of volunteers that underwent trials to check drug safety. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Clinical Trial Phases With Goals And Patients Number Clinical Research Trial Phases Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Clinical Trial Phases With Goals And Patients Number Clinical Research Trial Phases Download PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Advantages Of Using Robots In Industrial Sector Icons PDF
This slide illustrates the benefits of using robots in industries. The purpose of this slide is to explain how industrial sector is getting optimized from robotic automation. Their key pros included are high speed, increased load capacity, improved safety, etc. This Advantages Of Using Robots In Industrial Sector Icons PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Email Security Encryption And Data Loss Prevention Training Schedule Timeline For E Mail Security Proposal Diagrams PDF
This Slide shows the detailed training schedule for E-Mail Security Proposal. Deliver an awe-inspiring pitch with this creative email security encryption and data loss prevention training schedule timeline for e mail security proposal diagrams pdf bundle. Topics like case study, security, development, timeline can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Implementation Framework Vital Records Maintenance Register Ppt PowerPoint Presentation Layouts PDF
Presenting this set of slides with name cyber security implementation framework vital records maintenance register ppt powerpoint presentation layouts pdf. The topics discussed in these slides are settlement agreements, litigation files, department file room, primary location records. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
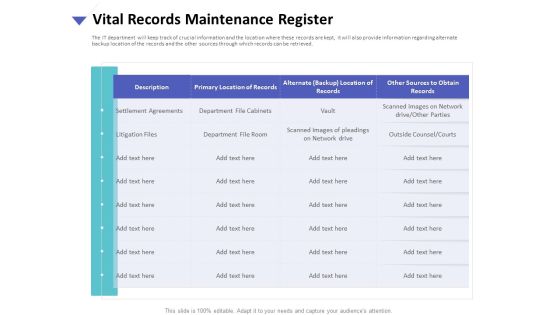
Strategies To Mitigate Cyber Security Risks Vital Records Maintenance Register Ppt Ideas Clipart Images PDF
Presenting this set of slides with name strategies to mitigate cyber security risks vital records maintenance register ppt ideas clipart images pdf. The topics discussed in these slides are settlement agreements, litigation files, department file cabinets, department file room, vault. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security Process To Manage Firms Sensitive Data Ppt Infographics Background Image PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an awe inspiring pitch with this creative information security process to manage firms sensitive data ppt infographics background image pdf bundle. Topics like management, system, security, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
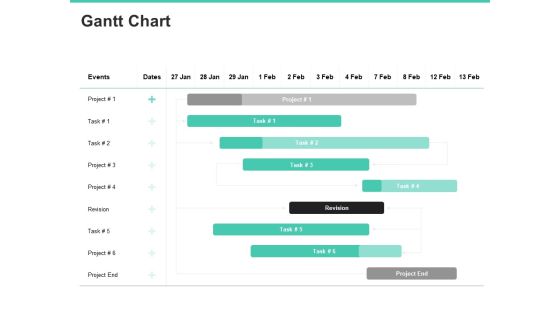
Email Security Encryption And Data Loss Prevention Gantt Chart Information PDF
Your complex projects can be managed and organized simultaneously using this detailed email security encryption and data loss prevention gantt chart information pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well-crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.

Cyber Security Implementation Framework Role Of Management In Effective Information Security Governance Download PDF
Presenting this set of slides with name cyber security implementation framework role of management in effective information security governance download pdf. The topics discussed in these slides are board directors, senior executives, steering committees, chief information security officer, measuring performance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Cyber Security Implementation Framework Recovery Task List Maintenance Ppt PowerPoint Presentation Icon Format Ideas PDF
Presenting this set of slides with name cyber security implementation framework recovery task list maintenance ppt powerpoint presentation icon format ideas pdf. The topics discussed in these slides are retrieve business continuity plans, retrieval department vital records, identify recovery site, actual time, estimated time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
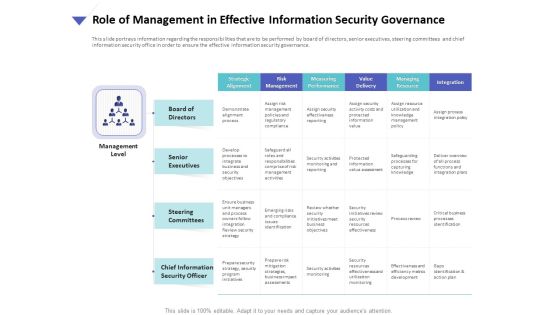
Strategies To Mitigate Cyber Security Risks Role Of Management In Effective Information Security Governance Ppt Model File Formats PDF
Presenting this set of slides with name strategies to mitigate cyber security risks role of management in effective information security governance ppt model file formats pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Selecting Security Incident Management Software Microsoft PDF
Presenting this set of slides with name cyber security implementation framework selecting security incident management software microsoft pdf. The topics discussed in these slides are security incident forms, automated workflows, centralized platform, access rights, api integration, cost, information security prevention. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Crisis Program Presentation Risk Management Action Plan Security Inspiration PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Deliver an awe-inspiring pitch with this creative crisis program presentation risk management action plan security inspiration pdf bundle. Topics like potential risk, communication, confidential information security, required resources, data backup team plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
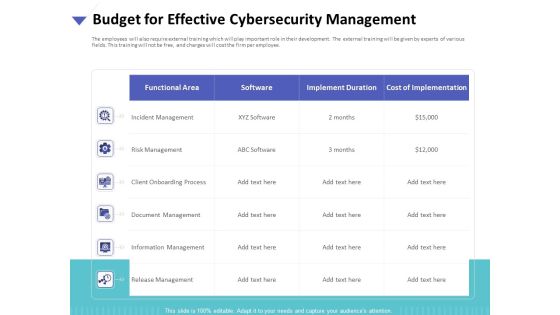
Strategies To Mitigate Cyber Security Risks Budget For Effective Cybersecurity Management Ppt Infographic Template Styles PDF
Presenting this set of slides with name strategies to mitigate cyber security risks budget for effective cybersecurity management ppt infographic template styles pdf. The topics discussed in these slides are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

5 Phases Of Data Protection Regulations Ppt PowerPoint Presentation Summary Images PDF
Pitch your topic with ease and precision using this 5 phases of data protection regulations ppt powerpoint presentation summary images pdf. This layout presents information on business, processes, security, management, working. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
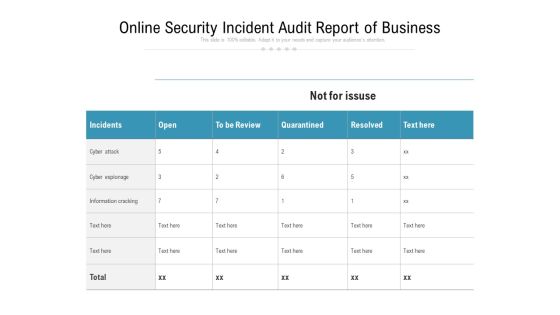
Online Security Incident Audit Report Of Business Ppt PowerPoint Presentation Inspiration Layout Ideas PDF
Pitch your topic with ease and precision using this online security incident audit report of business ppt powerpoint presentation inspiration layout ideas pdf. This layout presents information on incidents, cyber attack, cyber espionage, information cracking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
IT Security Analysis Checklist With Software And Hardware Risk Ppt PowerPoint Presentation Icon Examples PDF
Pitch your topic with ease and precision using this it security analysis checklist with software and hardware risk ppt powerpoint presentation icon examples pdf. This layout presents information on hardware risk, software risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Android Framework For Apps Development And Deployment Competitive Analysis With Various Factors Icons PDF
Presenting this set of slides with name android framework for apps development and deployment competitive analysis with various factors icons pdf. The topics discussed in these slides are superior quality, low price, unique features, installation, data security, user engagement. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Android Framework For Apps Development And Deployment Approximate Healthcare Application Development Cost Structure PDF
Presenting this set of slides with name android framework for apps development and deployment approximate healthcare application development cost structure pdf. The topics discussed in these slides are simple application, medium complexity application, high complex application, extra features, moderate data security like passcode. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Android Framework For Apps Development And Deployment Cost Breakdown Of Healthcare Application Development Ideas PDF
Presenting this set of slides with name android framework for apps development and deployment cost breakdown of healthcare application development ideas pdf. The topics discussed in these slides are development, data security, project management, quality assurance, work, basic application, medium application, complex application. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Determinants Of Product Quality Ppt PowerPoint Presentation Infographic Template Files
This is a determinants of product quality ppt powerpoint presentation infographic template files. This is a seven stage process. The stages in this process are performance, reliability, durability, evaluation, safety.

Information Security Common Methods Used To Threaten Data Security Ppt Show Model PDF
This slide depicts the standard methods used to threaten data security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Deliver and pitch your topic in the best possible manner with this information security common methods used to threaten data security ppt show model pdf. Use them to share invaluable insights on system, daniel of service, man in the middle and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Best Data Security Software Additional Services For Company Online Database Security Proposal Pictures PDF
Presenting this set of slides with name best data security software additional services for company online database security proposal pictures pdf. The topics discussed in these slides are software development, security and networking, cloud services. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Risk Management Plan Information Security Risk Assessment Worksheet Service Graphics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan information security risk assessment worksheet service graphics pdf. Use them to share invaluable insights on monetary loss, reputation loss, loss of customer confidence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Ensuring Vital Records Maintenance Summary PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver an awe inspiring pitch with this creative corporate security and risk management ensuring vital records maintenance summary pdf bundle. Topics like ensuring vital records maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Assets Security Management Strategy Addressing Vital Records Maintenance Centre Rules PDF
The team will keep the track of crucial information and the location where these records are kept also the alternate backup location of the records and the other sources through which records can be retrieved. Want to ace your presentation in front of a live audience Our Organizational Assets Security Management Strategy Addressing Vital Records Maintenance Centre Rules PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Present like a pro with Developing IT Security Strategy Information Security And Risk Management User Spending Structure PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cloud Information Security Hybrid Cloud Security Solutions Ppt Infographics Professional PDF
This slide describes the hybrid cloud security solutions, which include categorization of services and redundancy. Deliver an awe inspiring pitch with this creative Cloud Information Security Hybrid Cloud Security Solutions Ppt Infographics Professional PDF bundle. Topics like Categorization Services, Enable Organizations, Security Properly can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
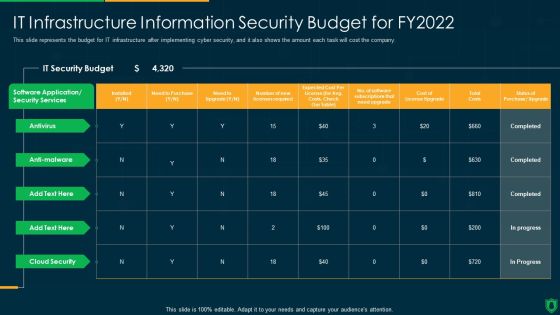
Info Security IT Infrastructure Information Security Budget For FY2022 Ppt PowerPoint Presentation File Pictures PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative info security it infrastructure information security budget for fy2022 ppt powerpoint presentation file pictures pdf bundle. Topics like it security budget, security services, cost license upgrade can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Infrastructure As A Service Iaas Ppt Ideas Information PDF
This slide represents the responsibilities under the IaaS model, it also shows the different advantages of the IaaS model along with its downsides. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Infrastructure As A Service Iaas Ppt Ideas Information PDF. Use them to share invaluable insights on Cloud Security, Organizations Experience, IaaS Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Effective IT Risk Management Process Information Security Risk Clipart PDF
Deliver and pitch your topic in the best possible manner with this effective it risk management process information security risk clipart pdf. Use them to share invaluable insights on equipment, software application, service denial, valuable information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Best Practices For Cloud Security Ppt Gallery Visuals PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this information technology security best practices for cloud security ppt inspiration example file pdf. Use them to share invaluable insights on best practices for cloud security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
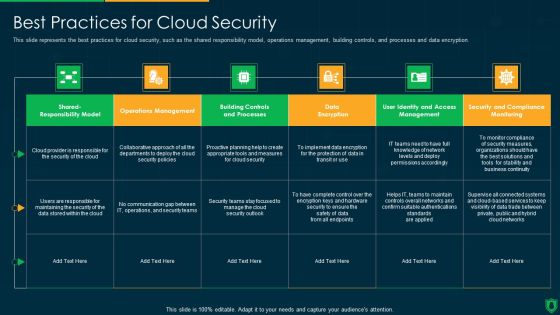
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparison Between ZTNA And Secure Access Service Edge Professional PDF
This slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Comparison Between ZTNA And Secure Access Service Edge Professional PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cloud Information Security Platform As A Service Paas Ppt Portfolio Skills PDF
This slide defines the platform-as-a-service model of cloud security and the various advantages and disadvantages of the PaaS model. Deliver an awe inspiring pitch with this creative Cloud Information Security Platform As A Service Paas Ppt Portfolio Skills PDF bundle. Topics like Service Providers, Business Applications, Considerable Money can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Software As A Service Saas Ppt Designs PDF
This slide describes the software-as-a-service responsibilities in the cloud security environment. It also shows the advantages and disadvantages of the SaaS model. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Software As A Service Saas Ppt Designs PDF. Use them to share invaluable insights on Saas Service, Providers Crucial, Providers Server and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Service Slides PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Service Slides PDF bundle. Topics like Effects Of Damage, Vulnerability And Possible, Unauthorized Disclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Information Technology Security Service Excellence For Risk Mitigation Clipart PDF
This slide signifies the types of security provided through information technology services. It includes surveillance like network, internet, cloud and application for mitigating risk. Pitch your topic with ease and precision using this Effective Information Technology Security Service Excellence For Risk Mitigation Clipart PDF. This layout presents information on Automated Workflows, Customization Option, Multi Channel Deployment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF. Use them to share invaluable insights on Required Standard Rating Actual, Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Phase 2 Secure Your Cloud Cloud Computing Security IT Ppt Slides Skills PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Deliver an awe inspiring pitch with this creative phase 2 secure your cloud cloud computing security it ppt slides skills pdf bundle. Topics like implement, security policies, data encryption, services, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
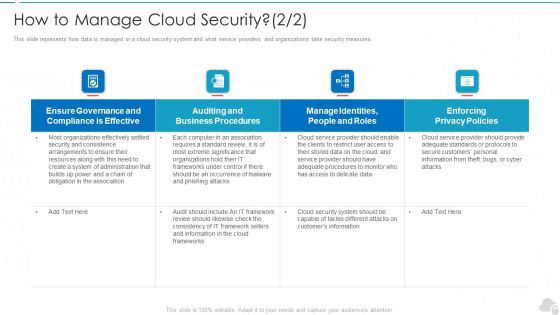
How To Manage Cloud Security Cloud Computing Security IT Ppt Infographic Template Inspiration PDF
This slide represents how data is managed in a cloud security system and what service providers and organizations take security measures. Deliver an awe inspiring pitch with this creative how to manage cloud security cloud computing security it ppt infographic template inspiration pdf bundle. Topics like effective, privacy policies, business procedures, frameworks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
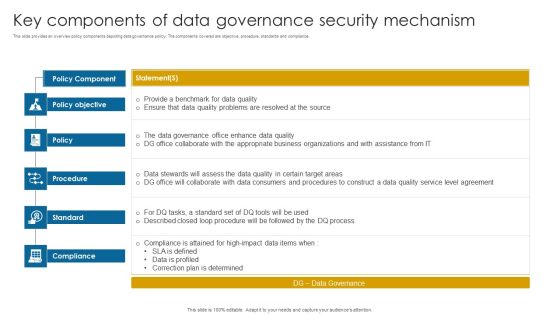
Key Components Of Data Governance Security Mechanism Information PDF
This slide provides an overview policy components depicting data governance policy. The components covered are objective, procedure, standards and compliance.Pitch your topic with ease and precision using this Key Components Of Data Governance Security Mechanism Information PDF. This layout presents information on Data Governance, Compliance Attained, Correction Determined. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Key Security Considerations For 5G For Threat Handling Icons PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling Icons PDF. Use them to share invaluable insights on Denial Of Service, Information Interception, Application Plane Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security And Risk Management User Spending By Segment Portrait PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include - application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Presenting this PowerPoint presentation, titled Information Security And Risk Management User Spending By Segment Portrait PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Information Security And Risk Management User Spending By Segment Portrait PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Information Security And Risk Management User Spending By Segment Portrait PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
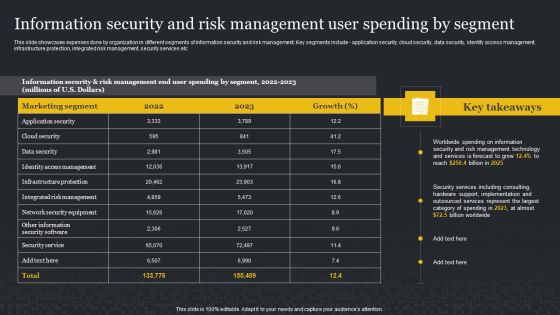
Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF
This slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. This Information Security And Risk Management User Spending By Segment Cybersecurity Risk Assessment Rules PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
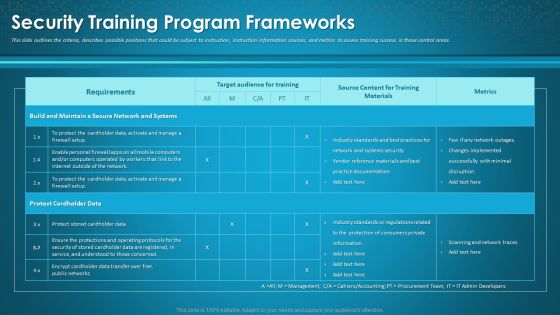
Organizational Network Awareness Staff Learning Security Training Program Frameworks Sample PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this organizational network awareness staff learning security training program frameworks sample pdf. Use them to share invaluable insights on target audience for training, source content, metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Breach Prevention Recognition Security Awareness New Strategies For Learning Download PDF
This slide covers effective ways to build cybersafe across an organization including key programs and approaches for the learning programs. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security awareness new strategies for learning download pdf bundle. Topics like cybersafe across, organization, key programs, approaches, learning programs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods Financial Burden To Company From IT Security Breaches Formats PDF. Use them to share invaluable insights on Professional Services, Lost Business Opportunities, Expense and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Organizations Risk Management And IT Security Financial Burden To Company From IT Security Breaches Brochure PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Welcome to our selection of the Organizations Risk Management And IT Security Financial Burden To Company From IT Security Breaches Brochure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Key Security Considerations For 5G For Threat Handling Elements PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Key Security Considerations For 5G For Threat Handling Elements PDF bundle. Topics like System Configuration, Security Policies, Information Interception can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Timeline For The Implementation Of Data Security Ppt Gallery Topics PDF
This slide shows the timeline for data security model implementation in an organization and the tasks to be performed every month. Deliver and pitch your topic in the best possible manner with this information security timeline for the implementation of data security ppt gallery topics pdf. Use them to share invaluable insights on timeline for the implementation of data security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Managing Data Security 60 Days Plan Ppt Inspiration Slide Download PDF
This slide represents the plan for 60 days after implementing the data security model in the organization. Deliver and pitch your topic in the best possible manner with this information security managing data security 60 days plan ppt inspiration slide download pdf. Use them to share invaluable insights on measured, procedures, team, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Managing Data Security 90 Days Plan Ppt Infographic Template Slides PDF
This slide depicts the 90 days plan of the data security model in an organization and training compliance and methods used for communication. Deliver an awe inspiring pitch with this creative information security managing data security 90 days plan ppt infographic template slides pdf bundle. Topics like security, measured can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Data Security Awareness Training For Staff Ppt Visual Aids Pictures PDF
This slide represents the data security awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this information security data security awareness training for staff ppt visual aids pictures pdf. Use them to share invaluable insights on project managers, developers, senior executives, planning and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
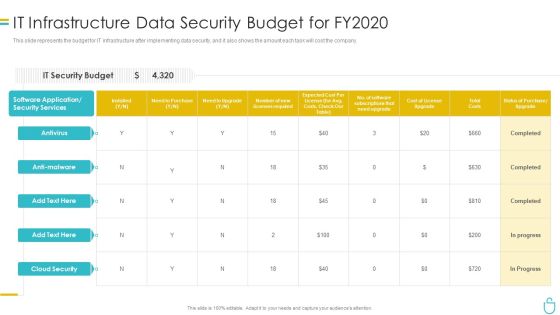
Information Security It Infrastructure Data Security Budget For FY2020 Ppt Inspiration File Formats PDF
This slide represents the budget for IT infrastructure after implementing data security, and it also shows the amount each task will cost the company. Deliver and pitch your topic in the best possible manner with this information security it infrastructure data security budget for fy2020 ppt inspiration file formats pdf. Use them to share invaluable insights on costs, need to purchase, required, application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
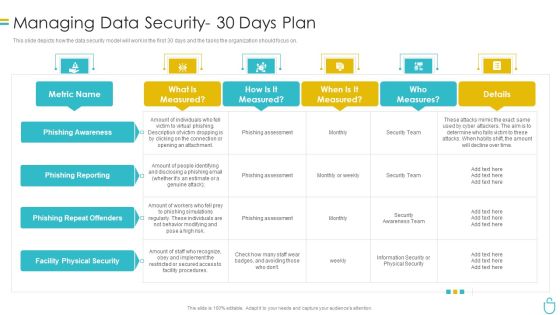
Information Security Managing Data Security 30 Days Plan Ppt Summary Slides PDF
This slide depicts how the data security model will work in the first 30 days and the tasks the organization should focus on. Deliver an awe inspiring pitch with this creative information security managing data security 30 days plan ppt summary slides pdf bundle. Topics like risk, procedures, implement, metric can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
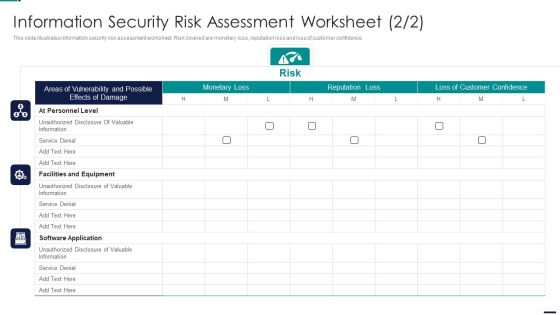
Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF
This slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Information Security Risk Assessment Worksheet Infographics PDF. Use them to share invaluable insights on Facilities And Equipment, Software Application, At Personnel Level, Monetary Loss, Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Information Security Decision Framework Prism Diagrams PDF
Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Information Security Decision Framework Prism Diagrams PDF bundle. Topics like Key Risk Areas, Vectors, Risk Factors, Prioritization Weighting, Resource Allocation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Service Price Matrix For Big Data Analytics Themes PDF
This slide includes various data management services which can be used by companies to build competitive advantage. It includes services such as data migration, data integration, data security, data analytics and data quality management. Pitch your topic with ease and precision using this Service Price Matrix For Big Data Analytics Themes PDF. This layout presents information on Assessment Of Business, Financial Data, Data Quality Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Developing IT Security Strategy Current Information And Data Security Capabilities Designs PDF from Slidegeeks and deliver a wonderful presentation.

Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this Cloud Information Security Phase 3 Respond To Cloud Protection Issues Ppt Layouts Influencers PDF. Use them to share invaluable insights on Advanced Authentication, Cloud Access, Eliminate Malware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
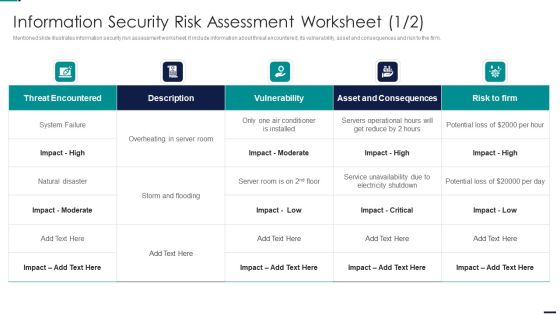
Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF. Use them to share invaluable insights on Threat Encountered, Vulnerability, Asset And Consequences, Risk To Firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Budget For Information Security Management Sample PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Budget For Information Security Management Sample PDF bundle. Topics like Functional Area, Training Duration, Risk Management, Incident Management, Asset Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Cyber Threat Landscape In Data Security Ppt Layouts Brochure PDF
This slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an awe inspiring pitch with this creative information security cyber threat landscape in data security ppt layouts brochure pdf bundle. Topics like organized criminals, financial, business disruption, reputation damage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity IT Infrastructure Electronic Information Security Budget For FY2020 Ppt Infographics Graphics Download PDF
This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Deliver an awe inspiring pitch with this creative cybersecurity it infrastructure electronic information security budget for fy2020 ppt infographics graphics download pdf bundle. Topics like required, application, security services, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Template PDF
This slide provides information about the second step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Evaluating Information Processing Assets. Deliver an awe inspiring pitch with this creative security management plan steps in detail evaluating information processing assets template pdf bundle. Topics like information, network infrastructure, services, customer information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Main Principle Of Information Security Introduction PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver and pitch your topic in the best possible manner with this desktop security management main principle of information security introduction pdf. Use them to share invaluable insights on availability, integrity, confidentiality and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF
This slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present like a pro with Risk Evaluation Of Information Technology Systems Financial Burden To Company From IT Security Breaches Inspiration PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Cyber Security Asset Risk Analysis Software Report Pictures PDF
This slide covers the risk identification status report for different cyber incidents. It includes malicious insider activity, confidential data loss, system failure and denial of service attacks. Pitch your topic with ease and precision using this Cyber Security Asset Risk Analysis Software Report Pictures PDF. This layout presents information on Cyber Security Asset Risk, Analysis Software Report. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF
This slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. This Benefits Of Secure Access Service Edge SASE Ppt Pictures Demonstration PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF
This slide outlines the security advantages of the platform as a service framework. It covers data governance, client endpoints, account and access management, identity and directory infrastructure, and application and network controls. Make sure to capture your audiences attention in your business displays with our gratis customizable Integration Of Paas Security Advantages Of Platform As A Service Framework Elements PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF
This slide represents e banking security measures and features. It includes login details, encrypted data, account management and two factor authorization. This Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Healthcare Information Security Risk Management And Management Plan Information PDF
This slide shows information security risk treatment and acceptance plan for hospitals which can benefit them in securing their data. It contains details such as possession type, risk acceptance criteria, treating the risk, techniques and approaches for risk, residual risk acceptance measures, etc. Pitch your topic with ease and precision using this Healthcare Information Security Risk Management And Management Plan Information PDF. This layout presents information on Measures, Risk Acceptance Criteria, Treating The Risk. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF
This slide outlines the business plan for managed security service which includes services such as antivirus, anti-malware, anti-spam etc. it also provides information about the total cost of services, status of purchase, security goal, etc. Pitch your topic with ease and precision using this Business Plan For Managed Cyber Security Solutions Service Ppt Infographic Template Topics PDF. This layout presents information on Revenue, Security Goal, IT Security Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Building An IT Strategy Plan For Business Expansion Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. There are so many reasons you need a Building An IT Strategy Plan For Business Expansion Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF
This slide shows comparison of different managed security service packages like silver, gold, platinum and diamond offered by service providers to the companies. It provides information about malware protection, security awareness, ransomware prevention etc. Pitch your topic with ease and precision using this Comparison Of Managed Cyber Security Solutions Service Packages Ppt Ideas Mockup PDF. This layout presents information on Email Security, Phishing Awareness, Security Awareness. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF
The following slide outlines a comprehensive training plan for managed security service and awareness for employees. It provides information about the training subject, trainer name, training hours, status and learning outcome. Pitch your topic with ease and precision using this Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF. This layout presents information on Training Plan, Managed Cyber Security, Solutions Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Building An IT Strategy Plan For Business Expansion How Management Enables Effective Corporate Security Governance Diagrams PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Slidegeeks is here to make your presentations a breeze with Building An IT Strategy Plan For Business Expansion How Management Enables Effective Corporate Security Governance Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Budget For Information Security Risk Management Diagrams PDF bundle. Topics like Training Of Employees, Software Implementation, Risk Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative organizational security solutions impact of effective security management information pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF. Use them to share invaluable insights on Identification Assess, Protecting Safeguarding, Detect Threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Checklist For Information Security Risk Management Information Security Risk Administration Portrait PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Take your projects to the next level with our ultimate collection of Checklist For Information Security Risk Management Information Security Risk Administration Portrait PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they all make your projects stand out from the rest.

Information Systems Security And Risk Management Plan Checklist For Information Security Risk Management Mockup PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Find a pre designed and impeccable Information Systems Security And Risk Management Plan Checklist For Information Security Risk Management Mockup PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Developing IT Security Strategy Budget For Information Security Risk Management Information PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. This Developing IT Security Strategy Budget For Information Security Risk Management Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Developing IT Security Strategy Budget For Information Security Risk Management Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Information Security Risk Management Form Guidelines PDF
This slide shows information security risk acceptance form which contains accountable person details, risk acceptance summary, acceptance advantages, justification, advice, etc. This can benefit cyber security department in careful review prior to the acceptance of major risks involved. Pitch your topic with ease and precision using this Information Security Risk Management Form Guidelines PDF. This layout presents information on Risk Modification, Risk Acceptance, Cyber Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver and pitch your topic in the best possible manner with this impact of effective security management information pdf. Use them to share invaluable insights on malicious codes prevented, unauthorized ip addresses ports and traffic, security incidents and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Process To Manage Firms Sensitive Data Contd Ppt Portfolio Portrait PDF
Deliver and pitch your topic in the best possible manner with this information security process to manage firms sensitive data contd ppt portfolio portrait pdf. Use them to share invaluable insights on information security process to manage firms sensitive data contd and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative Developing 5G Wireless Cellular Network Key Security Considerations For 5G For Threat Handling Demonstration PDF bundle. Topics like Information Interception, Virtualization Threats, Denial Of Service can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
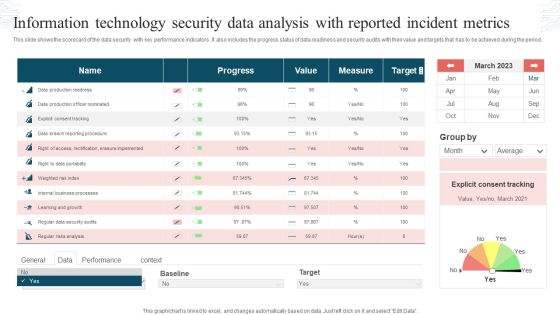
Information Technology Security Data Analysis With Reported Incident Metrics Rules PDF
This slide shows the scorecard of the data security with key performance indicators. It also includes the progress status of data readiness and security audits with their value and targets that has to be achieved during the period. Pitch your topic with ease and precision using this Information Technology Security Data Analysis With Reported Incident Metrics Rules PDF. This layout presents information on Progress, Value, Measure, Target. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. The Current Information And Data Security Capabilities Of Firm Cybersecurity Risk Assessment Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security Incident Handling Checklist Information PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Welcome to our selection of the Cyber Security Incident Handling Checklist Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Capital Raising Pitch Presentation Competitive Landscape For LBS App Designs PDF
Following slide differentiates the offering of companies with its competitors based on self-service features namely secure login, reward codes, customer support and popup notifications. Deliver and pitch your topic in the best possible manner with this Capital Raising Pitch Presentation Competitive Landscape For LBS App Designs PDF. Use them to share invaluable insights on Location Based Services, Offline Access To Content, Customer Support, Popup Notifications and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
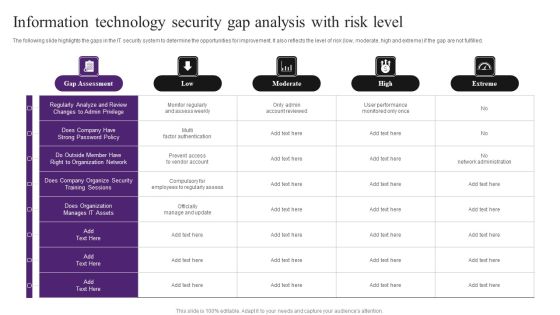
Information Technology Security Gap Analysis With Risk Level Information PDF
The following slide highlights the gaps in the IT security system to determine the opportunities for improvement. It also reflects the level of risk low, moderate, high and extreme if the gap are not fulfilled. Pitch your topic with ease and precision using this Information Technology Security Gap Analysis With Risk Level Information PDF. This layout presents information on Organize Security, Regularly Analyze, Gap Assessment. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Incident Handler Contact Information Information PDF
This slide represents the contact information of the members responsible for handling and managing the cyber security incidents. It includes details related to name, organization, role and contact details of cyber security incident handler. This Cyber Security Incident Handler Contact Information Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Incident Handler Contact Information Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Selecting Data Centre Management Solution Workplace Security Management Program Information PDF
This slide will help firm in choosing the suitable data center management solution by analyzing on various parameters such as server health management, firmware update, ghost server detection, equipment scheduling, etc. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Selecting Data Centre Management Solution Workplace Security Management Program Information PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

5G Network Technology Key Security Considerations For 5G For Threat Handling Ppt Gallery Gridlines PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an awe inspiring pitch with this creative 5g network technology key security considerations for 5g for threat handling ppt gallery gridlines pdf bundle. Topics like virtualization threats, information interception, security policies, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment What Are The Benefits Of A Cloud Security System Information PDF. Use them to share invaluable insights on Efficient Recovery, Hardware Required, Efficient Data and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security Main Principle Of Information Security Ppt PowerPoint Presentation File Background Designs PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an awe inspiring pitch with this creative info security main principle of information security ppt powerpoint presentation file background designs pdf bundle. Topics like integrity, confidentiality, availability, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man-in-the-cloud attack, and unsecured storage containers. Deliver an awe inspiring pitch with this creative Cloud Information Security Key Cloud Security Use Cases Ppt Gallery Templates PDF bundle. Topics like Privileged Account, Data Exfiltration, Suspicious Network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Info Security Employee Awareness Training Budget For FY2022 Ppt PowerPoint Presentation File Graphics Download PDF
This slide represents the organizations staff training budget through a graph covering trainer name, date, and capability levels. Deliver an awe inspiring pitch with this creative info security employee awareness training budget for fy2022 ppt powerpoint presentation file graphics download pdf bundle. Topics like build and maintain, secure network and system, protect cardholder data, maintain a vulnerability, management program can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
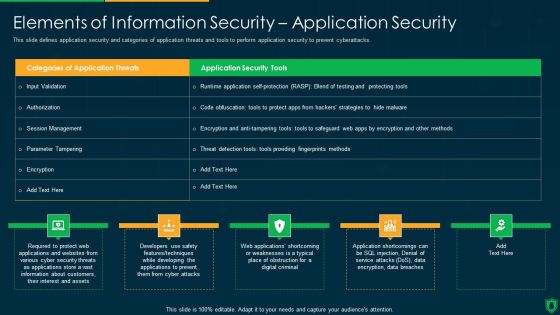
Info Security Elements Of Information Security Application Security Ppt PowerPoint Presentation File Graphics Download PDF
This slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Deliver and pitch your topic in the best possible manner with this info security elements of information security application security ppt powerpoint presentation file graphics download pdf. Use them to share invaluable insights on application security tools, parameter tampering, encryption and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF
Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Challenges And Solutions In Information Security Risk Management Template PDF. Use them to share invaluable insights on Internal Vulnerabilities, Employee Awareness, Comprehensive Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Checklist For Information Security Risk Management Microsoft PDF bundle. Topics like Identifying Potential, Defining Mitigation, Created Sales can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home