Security

Corporate Security And Risk Management Different Kinds Of Insider Digital Threats Themes PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Presenting corporate security and risk management different kinds of insider digital threats themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like malicious insider, negligent or careless insider, third party insider . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Functional Areas Brochure PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a corporate security and risk management ensuring collaboration among various functional areas brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collet, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Ensuring Collaboration Among Various Rules PDF
This slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Presenting corporate security and risk management ensuring collaboration among various rules pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like finance, human resources, procurement, public relations, collaboration. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Vital Records Maintenance Summary PDF
This slide provides information regarding vital record maintenance in order to store crucial information and the location where these records are kept also details about the alternate backup location of the records and the other sources through which records can be retrieved. Deliver an awe inspiring pitch with this creative corporate security and risk management ensuring vital records maintenance summary pdf bundle. Topics like ensuring vital records maintenance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Evaluating Financial Practices In Firm Graphics PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. This is a corporate security and risk management evaluating financial practices in firm graphics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluating financial practices in firm. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
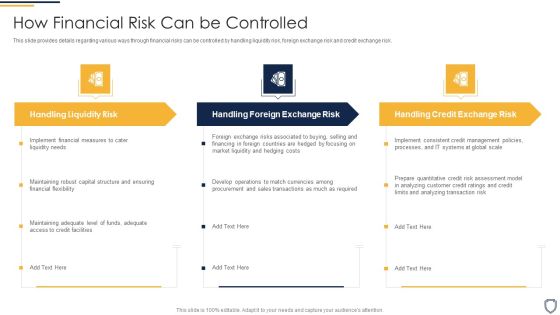
Corporate Security And Risk Management How Financial Risk Can Be Controlled Infographics PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting corporate security and risk management how financial risk can be controlled infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Impact Analysis Of Successful Threat Sample PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the Deliver and pitch your topic in the best possible manner with this corporate security and risk management impact analysis of successful threat sample pdf. Use them to share invaluable insights on focus area, past state, present state, benefit and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Roles And Responsibilities To Ensure Work Professional PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a corporate security and risk management roles and responsibilities to ensure work professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, unit supervisor manager responsibilities, internal investigations unit responsibilities, human resources responsibilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Threat Management Action Plan Risk Portrait PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting corporate security and risk management threat management action plan risk portrait pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
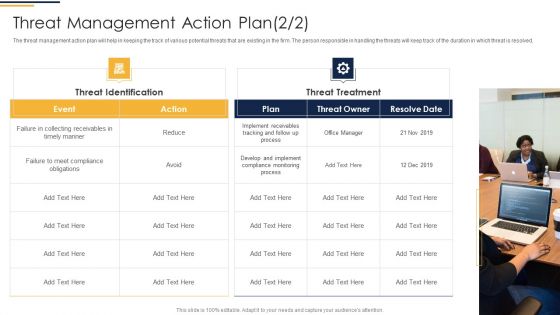
Corporate Security And Risk Management Threat Management Action Plan Introduction PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this corporate security and risk management threat management action plan introduction pdf. Use them to share invaluable insights on potential risk, risk level, action, duration, risk treated and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Various Types Of Workplace Violence And Threats Designs PDF
This slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Presenting corporate security and risk management various types of workplace violence and threats designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like threats or threatening behavior, physical assault, property damage, stalking, harassment or intimidation . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Current Potential Implications Faced By Firm As Threats Inspiration PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative corporate security and risk management current potential implications faced by firm as threats inspiration pdf bundle. Topics like current potential implications faced by firm as threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Cyber Threats Management Dashboard Ideas PDF
This slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver and pitch your topic in the best possible manner with this corporate security and risk management cyber threats management dashboard ideas pdf. Use them to share invaluable insights on cyber threats management dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Estimating Total Cost Of Ownership Of SIEM Real Time Assessment Of Security Threats Infographics PDF
This slide covers the cost breakdown of SIEM solution based on initial expenses, recurring expenses and amount saved by the client if they choose our company. Deliver and pitch your topic in the best possible manner with this estimating total cost of ownership of siem real time assessment of security threats infographics pdf. Use them to share invaluable insights on ongoing expenses, cost breakdown, siem solution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
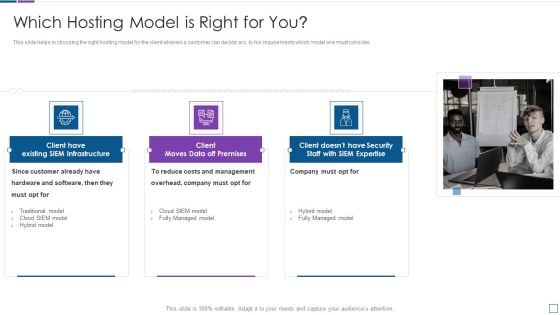
Real Time Assessment Of Security Threats Which Hosting Model Is Right For You Clipart PDF
This slide helps in choosing the right hosting model for the client wherein a customer can decide acc. to his requirements which model one must consider. This is a real time assessment of security threats which hosting model is right for you clipart pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like costs and management, company, hardware and software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
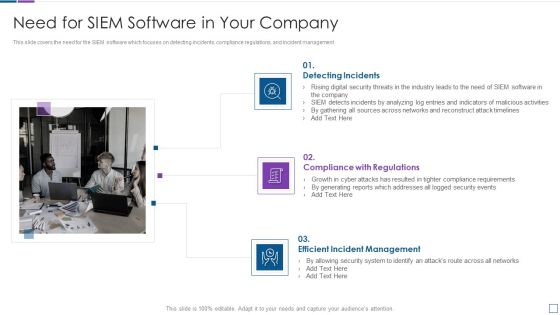
Real Time Assessment Of Security Threats Need For SIEM Software In Your Company Template PDF
This slide covers the need for the SIEM software which focuses on detecting incidents, compliance regulations, and incident management. Presenting real time assessment of security threats need for siem software in your company template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like detecting incidents, compliance with regulations, efficient incident management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Our Management Team Graphics PDF
This slide covers the details of the management team along with their job profile and brief description about their work. This is a real time assessment of security threats our management team graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our management team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Real Time Assessment Of Security Threats About Our SIEM Company Structure PDF
This slide provides the glimpse about the SIEM company which covers the companys background, firms operations and offerings. This is a real time assessment of security threats about our siem company structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like about our siem company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Our SIEM Companys Security Information And Event Management Strategies For Financial Audit And Compliance Portrait PDF
This slide provides the milestones of our company such as foundation year, revenue generation, profitability, etc. Presenting our siem companys security information and event management strategies for financial audit and compliance portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like our siem companys milestones. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Information And Event Management Strategies For Financial Audit And Compliance Our Management Team Graphics PDF
This slide covers the details of the management team along with their job profile and brief description about their work. Presenting security information and event management strategies for financial audit and compliance our management team graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like our management team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
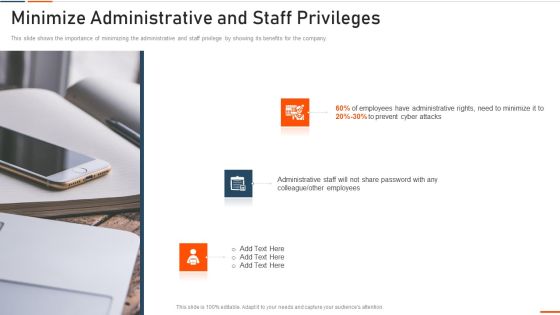
Information Technology Security Minimize Administrative And Staff Privileges Ppt Professional Graphics PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting information technology security minimize administrative and staff privileges ppt professional graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like minimize administrative and staff privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Prepare A Disaster Recovery Plan Ppt Ideas Inspiration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a information technology security prepare a disaster recovery plan ppt ideas inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment report, identify importance assets, report assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

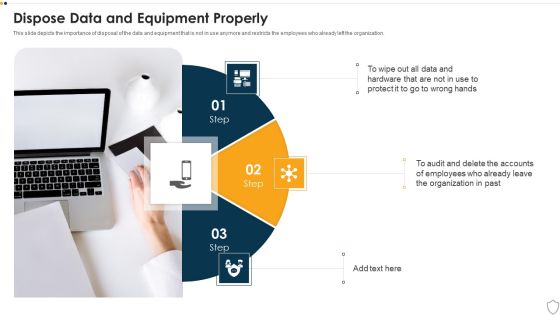
IT Security Dispose Data And Equipment Properly Ppt Icon Example PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting information technology security dispose data and equipment properly ppt outline layouts pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Dispose Data And Equipment Properly Ppt Portfolio Good PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. This is a it security dispose data and equipment properly ppt portfolio good pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like dispose data and equipment properly. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Minimize Administrative And Staff Privileges Ppt Inspiration Summary PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a it security minimize administrative and staff privileges ppt inspiration summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Prepare Data Backup For Sensitive Information Ppt Portfolio Slide Download PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Presenting it security prepare data backup for sensitive information ppt portfolio slide download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prepare data backup for sensitive information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Methods To Develop Advanced IT Security Monitoring Plan Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This methods to develop advanced it security monitoring plan ppt powerpoint presentation complete deck with slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.
Info Security Minimize Administrative And Staff Privileges Ppt PowerPoint Presentation Icon Files PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting info security minimize administrative and staff privileges ppt powerpoint presentation icon files pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like employees, prevent cyber attacks, administrative staff. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
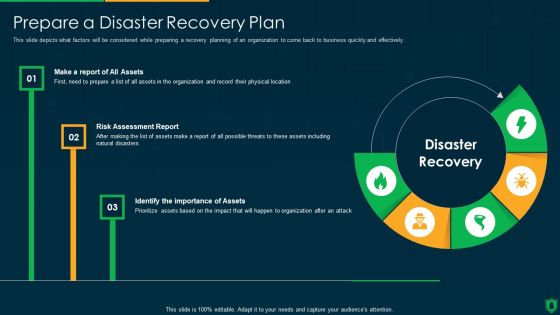
Info Security Prepare A Disaster Recovery Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a info security prepare a disaster recovery plan ppt powerpoint presentation file portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disaster recovery, risk assessment report, identify importance assets, disaster recovery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
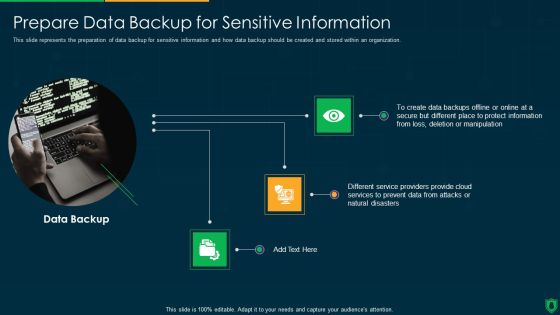
Info Security Prepare Data Backup For Sensitive Information Ppt PowerPoint Presentation File Rules PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a info security prepare data backup for sensitive information ppt powerpoint presentation file rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data backup, provide cloud, prevent data, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Update And Installation Of Antivirus Software Ppt PowerPoint Presentation File Designs PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this info security update and installation of antivirus software ppt powerpoint presentation file designs pdf. Use them to share invaluable insights on antivirus software usage chart across us, choose best antivirus, organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Terrorism Assault Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism Template PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts.Presenting cyber terrorism assault roadmap to implement cyber security to mitigate cyber terrorism template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating personal accounts, awareness training, keep the hardware In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Phishing Scams And Attacks Assessment And Cyber Security Training Inspiration PDF
Mentioned slide showcases phishing awareness training program used to prevent cyber attacks. It provides detailed information about deploying phishing program within the organization, analyzing and preparing reports, developing training and education etc. Persuade your audience using this phishing scams and attacks assessment and cyber security training inspiration pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including analyze, develop, measure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Asset Criticality Of Identified System Components Topics PDF. Use them to share invaluable insights on Impact Rating On Business, Criticality Rating, Failure Cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
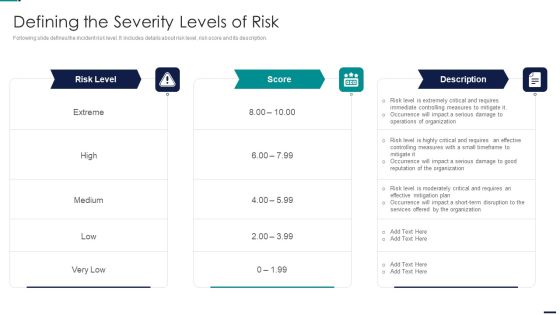
Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. This is a Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Level, Score, High, Low, Medium, Operations, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
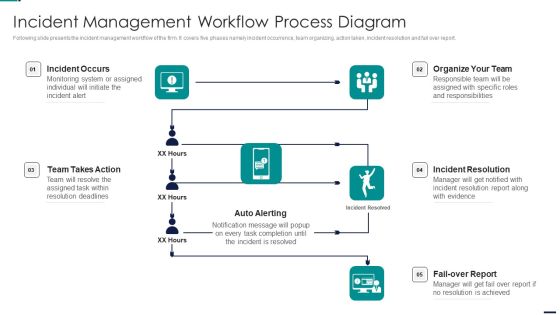
Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF
Following slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Presenting Risk Management Model For Data Security Incident Management Workflow Process Diagram Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Incident Occurs, Organize Team, Incident Resolution, Fail Over Report, Auto Alerting, Team Takes Action. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF. Use them to share invaluable insights on Threat Encountered, Risk Level, Mitigation Plan, Resources Required and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
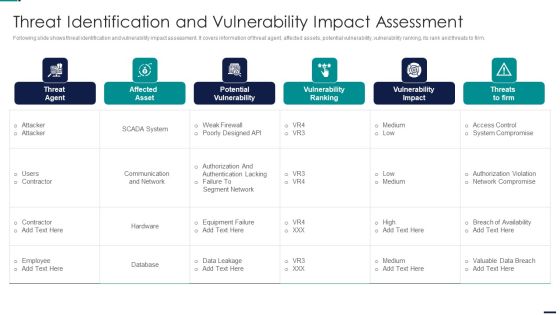
Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Threat Identification And Vulnerability Impact Slides PDF. Use them to share invaluable insights on Threat Agent, Affected Asset, Potential Vulnerability, Vulnerability Ranking and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.This is a Facilitating IT Intelligence Architecture Timeframe For Incident Management In Security Centre Guidelines PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Categorization, Incident Resolution, Incident Prioritization You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smart Home Security Solutions Company Profile Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Smart Home Security Solutions Company Profile Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fourty one slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

IT Security Evaluation Scorecard Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes IT Security Evaluation Scorecard Ppt PowerPoint Presentation Complete Deck With Slides and has templates with professional background images and relevant content. This deck consists of total of twenty nine slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Presenting Accelerate Online Journey Now Need Of Cyber Security In Organization Professional PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Confidential Data, Against Malware, Phishing Scams In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides
Pitch yourself both in house and outside by utilizing this complete deck. This Risk Based Procedures To IT Security Ppt PowerPoint Presentation Complete Deck With Slides focuses on key fundamentals of the topic, displayed using different slides. With a total of fifty four slides, this template is the best tool you can use to persuade your audience. It will not only help you create great presentations but also induce strategic thinking because of its well researched content and graphics. You can easily personalize any of the elements to suit your unique business setting. Additionally, it can be saved in PNG, JPG, and PDF formats to save your time and resources.

Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Presenting Risk Based Procedures To IT Security Communication Plan For Cyber Breaches Structure PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Sprint Report, Delivery Method, Frequency Responsible. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
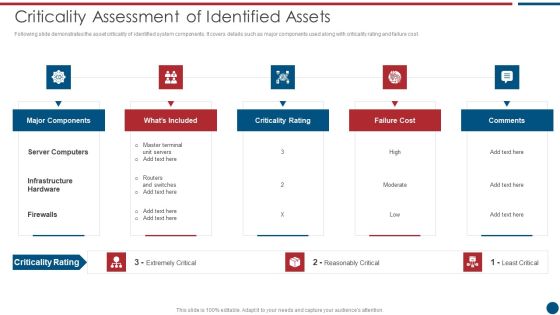
Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as major components used along with criticality rating and failure cost. This is a Risk Based Procedures To IT Security Criticality Assessment Of Identified Assets Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Major Components, Criticality Rating, Failure Cost. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. This is a Risk Based Procedures To IT Security Flow Diagram Of Incident Response Process Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Core Response, Contain Mitigate, Remediate Eradicate. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF
Mentioned slide portrays communication plan that company will use for effectively managing cyber breaches. Sections covered here are what to communicate, description, delivery method, frequency and responsible. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Communication Plan For Cyber Breaches Pictures PDF. Use them to share invaluable insights on Sprint Report, Product Report, Delivery Method and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF
This slide shows comparison of different house insurance companies and their net earned premium, amount and ratio of claim incurred. Pitch your topic with ease and precision using this Competitive Analysis Of Home Security Firms With Premium Earned And Claim Incurred Microsoft PDF. This layout presents information on Incurred Claim Ratio, Claims Incurred Net, Net Earned Premium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cloud Data Security Theft Or Loss Of Intellectual Property Microsoft PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks. This is a Cloud Data Security Theft Or Loss Of Intellectual Property Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Businesses, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Brief Introduction About The Company Portrait PDF
The slide provides the brief introduction about the company introducing IPO. Key points included are business overview, mission, vision, five years financials revenue, operating net margin and revenue split by business operations.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Brief Introduction About The Company Portrait PDF Use them to share invaluable insights on Financial Highlights, Business Operations, Asset Management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook Companys Strategic Decisions For IPO Issue Slides PDF
The slide covers the strategic steps taken by the company before introducing its IPO. Key strategic steps include IPO decision, IPO qualification, IPO preparation.This is a Investment Banking Security Underwriting Pitchbook Companys Strategic Decisions For IPO Issue Slides PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cost And Benefit, Qualification Criteria, Preparation Required You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
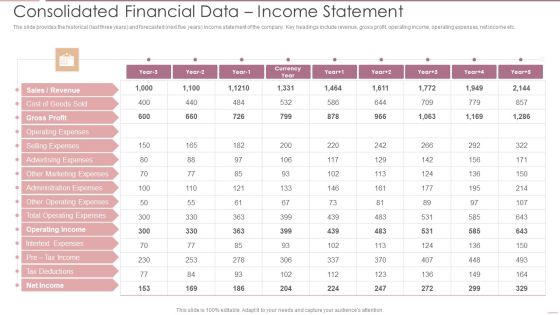
Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF
The slide provides the historical last three years and forecasted next five years income statement of the company. Key headings include revenue, gross profit, operating income, operating expenses, net income etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Consolidated Financial Data Income Statement Diagrams PDF Use them to share invaluable insights on Gross Profit, Operating Expenses, Advertising Expenses and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
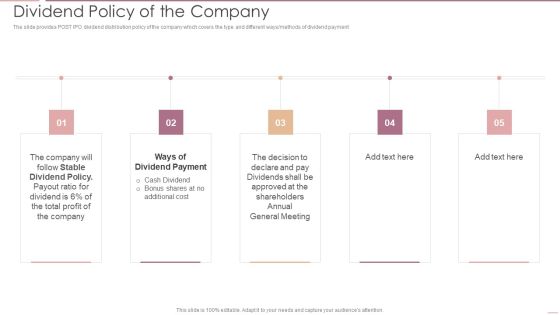
Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF
The slide provides POST IPO dividend distribution policy of the company which covers the type and different ways methods of dividend payment.Presenting Investment Banking Security Underwriting Pitchbook Dividend Policy Of The Company Portrait PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Stable Dividend, Dividend Payment, General Meeting In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Investment Banking Security Underwriting Pitchbook Geographic Presence Map Of The Company Designs PDF
The slide provides the geographic presence of the company along with the number of offices in each country in which the has presence.This is a Investment Banking Security Underwriting Pitchbook Geographic Presence Map Of The Company Designs PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Geographic Presence, Map Company You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Industry Overview And Market Trends Ideas PDF
The slide provides the industry overview and key facts market trends of the industry. Additionally, it provides market size for the year 2014 to 202 and market share 2019 of the industry.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Industry Overview And Market Trends Ideas PDF Use them to share invaluable insights on Assets Management, Leveraged Finance, Restructuring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook Investment Bank Underwriting Overview Topics PDF
The slide provides the key points related to underwriting agreement between the company and the investment bank. Key points covered in the slide includes type of offering, underwriting fee, number of banks involved in the deal etc. This is a Investment Banking Security Underwriting Pitchbook Investment Bank Underwriting Overview Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Investment Banks, Firm Commitment, Underwriting Fee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
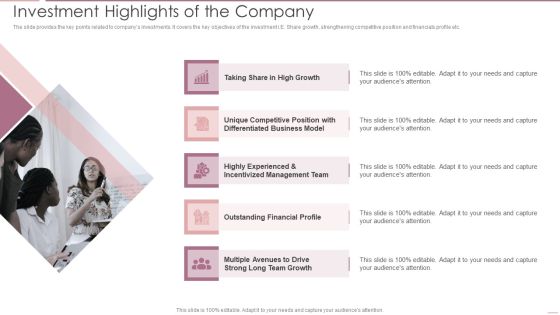
Investment Banking Security Underwriting Pitchbook Investment Highlights Of The Company Elements PDF
The slide provides the key points related to companys investments. It covers the key objectives of the investment i.E. Share growth, strengthening competitive position and financials profile etc.Presenting Investment Banking Security Underwriting Pitchbook Investment Highlights Of The Company Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Unique Competitive, Differentiated Business, Incentivized Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
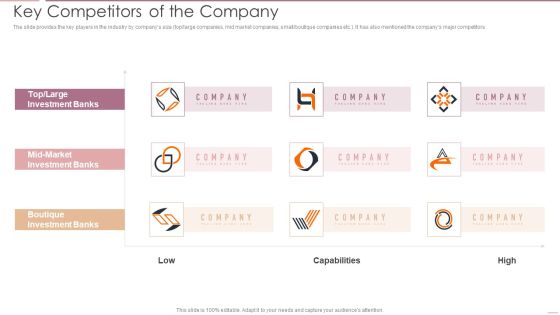
Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF
The slide provides the key players in the industry by companys size top large companies, mid market companies, small or boutique companies etc.. It has also mentioned the companys major competitors.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Competitors Of The Company Graphics PDF Use them to share invaluable insights on Investment Banks, Boutique Investment, Large Investment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
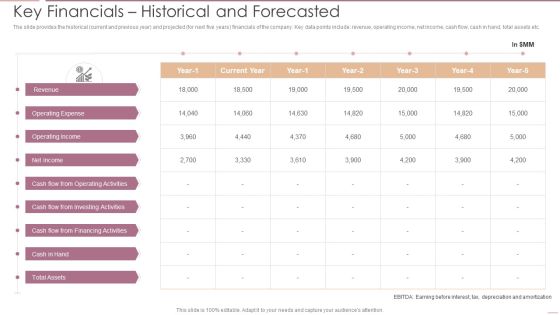
Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF
The slide provides the historical current and previous year and projected for next five year financials of the company. Key data points include revenue, operating income, net income, cash flow, cash in hand, total assets etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Key Financials Historical And Forecasted Professional PDF bundle. Topics like Operating Expense, Operating Income, Operating Activities can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF
The slide provides the companys objectives behind issuing IPO. Key objectives include future expansion, option of alternative currency, cash out option, paying off debts etc. Presenting Investment Banking Security Underwriting Pitchbook Key Objectives Of The IPO Issue Slides PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Expansion, Alternative Currency, Paying Debts In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Investment Banking Security Underwriting Pitchbook Leadership Senior Executive Team Inspiration PDF
The slide provides the name and designation of the key management team members CEO, CFO, department head etc. Of the company. It also provides the major transaction experience work experience of the executives.This is a Investment Banking Security Underwriting Pitchbook Leadership Senior Executive Team Inspiration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Transaction Experience, Designation, Introduced You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Senior Management Biographies And Other Details Microsoft PDF
The slide provides the name and designation of senior management teams CEO, CFO, department head etc. Of the company. It also covers brief information about their work experience, prior industry experience and education. This is a Investment Banking Security Underwriting Pitchbook Senior Management Biographies And Other Details Microsoft PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Industry Experience, Designation, Education You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks.This is a Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intellectual Property, Examination Uncovered, Danger Presented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Overcome Cyber Security Workforce Shortage To Address Demand And Supply Gaps Topics PDF
This slide covers different techniques to overcome cyber workforce shortage. It includes expanding talent pool, identifying existing talent, re-train staff and introduce innovations to reduce demand. Persuade your audience using this Strategies To Overcome Cyber Security Workforce Shortage To Address Demand And Supply Gaps Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expand Talent Pool, Identify Existing Talent, Re Train Existing Staff. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF
This slide showcases criticality rating that can be allocated to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating.Presenting Information Security Risk Evaluation Assigning Criticality Rating To Information Assets Template PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Customer Database, Product Database, Sales Records. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF. Use them to share invaluable insights on Unpatched Servers, Attacks Including, Awareness Trainings and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF. Use them to share invaluable insights on Vulnerability Severity, Unprotected Storage, Unprotected Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description.This is a Information Security Risk Evaluation Vulnerability Rating For Risk Identification Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drawback And Organization, Drawback Asset, Vulnerability Score. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF
This template covers first step for LinkedIn marketing such as update company profile and position the company account according to the target audience. This is a Security And Performance Digital Marketing Align And Position Account For Linkedin Marketing Mockup PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Profiles Position, Target Audience, Account According. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Content Creation Tactics Draft Personalized Email Messages Pictures PDF
This template covers tactics to create account-based marketing emails. It also includes the tools that can be used create emails and set appointments. This is a Security And Performance Digital Marketing Content Creation Tactics Draft Personalized Email Messages Pictures PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Efficient Conversational, Personalized, Specific About. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF
This template covers account based marketing strategy such as create content that provide value to the customers. It also depicts that Different types of target accounts require additional content focuses.Presenting Security And Performance Digital Marketing Create Content Strategy That Resonates With Targets Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Competitors Customers, Strategic Importance, Different. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Digital Marketing Problem And Solution In New Normal Guidelines PDF
This template covers the statistics of the digital marking industry in the new normal. It also depicts that due to Covid, B2B traditional marketing approaches have been digitalized.This is a Security And Performance Digital Marketing Digital Marketing Problem And Solution In New Normal Guidelines PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Prospect Meetings, Digital Solution, Traditional Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF
template covers guidelines to drive unpaid traffic with Search engine optimization. It also depicts that SEO is the process of optimizing webpages so that they rank higher in search engines.Presenting Security And Performance Digital Marketing Drive Organic Traffic With SEO Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Relevant Information, Inbound Outbound, Engage Positively. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Facebook And Instagram Advertising Audit The Company Profile Mockup PDF
This template covers Facebook and Instagram marketing strategy. All these sections on Facebook, Instagram pages add an important value to the business. This is a Security And Performance Digital Marketing Facebook And Instagram Advertising Audit The Company Profile Mockup PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Conducting Events, Regularly Post, Corporate Announcements. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF
This template covers content creation tactics in account based marketing such as launching multi touch campaigns, use of marketing automated tools etc.This is a Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Campaign Launch, Campaign Workflow, Ensure Prospects. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF
This template covers the email marketing strategy to leverage the in house email database for email automation, customer retargeting and audience creation. Presenting Security And Performance Digital Marketing Leverage Inhouse Email Database Introduction PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Communications Towards, Automated Messages, Social Platforms. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
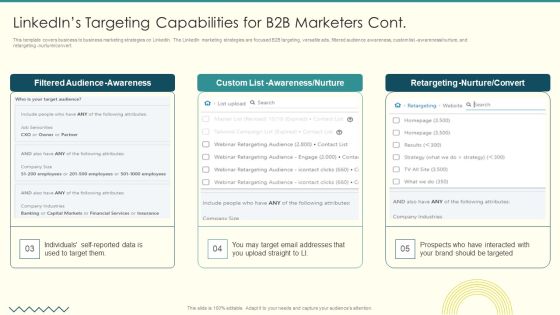
Security And Performance Digital Marketing Linkedins Targeting Capabilities For B2B Marketers Cont Graphics PDF
This template covers business to business marketing strategies on LinkedIn. The LinkedIn marketing strategies are focused B2B targeting, versatile ads, filtered audience awareness, custom list awareness nurture, and retargeting nurture convert.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Linkedins Targeting Capabilities For B2B Marketers Cont Graphics PDF bundle. Topics like Filtered Audience, Awareness Nurture, Retargeting Nurture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF
This template covers search engine optimization guidelines for images. It also depicts that Alt Attributes must be added at backend of the images to assists search engine crawlers in indexing. This is a Security And Performance Digital Marketing Optimize Onpage SEO Include ALT Tags For Images Infographics PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Descriptions, Search Engine, Assisting Indexing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF
This template covers search engine optimization guidelines to optimal title length for title tag and to write meta description displayed on the SERPs . Presenting Security And Performance Digital Marketing Optimize Onpage SEO Include Title Tag And Meta Descriptions Formats PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Currently Limited, Typically Displays, Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Optimize Onpage SEO Review Body Content Pictures PDF
This template covers search engine optimization guidelines for maintaining web page content quality such as removal of duplicate content, less website load time, mobile friendly sites and maintaining minimum Ad volume. .This is a Security And Performance Digital Marketing Optimize Onpage SEO Review Body Content Pictures PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Removing Duplicated, Keeping Minimum, Maintaining Volume. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF
This template covers the use of automated software for email marketing. It also depicts that email marketing platforms engage allows users to create multiple sales flow with combination of manual and automated emails and phone calls.Presenting Security And Performance Digital Marketing Scale The Outreach Efforts With Automated Platforms Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Combination Manual, Leads Prioritize, Identify Most. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF
This template depicts that Facebook Ads needs three parts to run such as a campaign, ad set, and ad. All these parts are called campaign structure and help run ads the way the company wants and reach the right prospects.his is a Security And Performance Digital Marketing Structure Of Facebook Campaigns Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Powerful Consisting, Features Campaigns, Define Creative. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF
This template covers account based marketing through retargeting email campaigns. It also includes remarketing funnel for social media, emails and website landing pages.Presenting Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Alternatives Available, Remarking Retargeting, Media Advertising. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Understand Campaign Anatomy For Advertising Management Topics PDF
This template covers the basic structure for google ads. It also depicts that google ads is the advertising management platform for google paid search pay per click search engine ads. Deliver and pitch your topic in the best possible manner with this Security And Performance Digital Marketing Understand Campaign Anatomy For Advertising Management Topics PDF. Use them to share invaluable insights on Throughout Campaign, Topic Incorporated, Numerous Content and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Performance Digital Marketing Use Accountbased Marketing To Target Strategic Accounts Topics PDF
This template covers the five-step account-based marketing approach. The strategy includes identification profiling of accounts by the sales team, creating content, and launching campaigns by the marketing team. Lastly, it includes campaign performance measurement analysis. This is a Security And Performance Digital Marketing Use Accountbased Marketing To Target Strategic Accounts Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Personalized Campaign, Revenue Potential, Launch Campaigns. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF
This template covers email marketing strategy such as use of automation email sequences for customers at all different stages in their customer journey . Presenting Security And Performance Digital Marketing Use Automation Throughout The Sales Funnel Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Past Customers, Existing Customers, Assist Businesses. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF
This template depicts that by uploading existing email lists to Google, Facebook, and LinkedIn, user may target those customers with display advertising or create fresh unique lookalike audiences. This is a Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Lookalike Audience, Retargeted Advertising, Lookalike Retargeting. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF
This template covers account-based marketing strategy such as the use of social media channels and techniques to increase brand recognition, and nurture the target prospects and lead through the digital marketing funnel.This is a Security And Performance Digital Marketing Use Social Media To Further Support Campaigns Clipart PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Prospects Obtained, Nurturing Sequences, Channels Techniques. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF
This template covers the cold calling email campaign strategy. It also depicts that TOFU should include introductory content focusing on brand, MOFU should include useful information about brand and, BOFU should include social proofs.Presenting Security And Performance Digital Marketing Use Top Of Funnel Content In Cold Calling Campaigns Template PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Sample Reports, Testimonials, Landing Pages. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. This is a IT Professional Data Certification Program Certified Information Systems Security Professional CISSP Details Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organization, Customers, Access Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF
This slide shows comparison of software available for detecting insider threat. It provides information about tools, features, user reviews, detection rate, free trial and pricing. Pitch your topic with ease and precision using this Comparative Analysis Of Insider Threat In Cyber Security Detection Software Guidelines PDF. This layout presents information on User Reviews, Detection Rate, Free Trial. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF
This slide shows cyber kill chain for insider threats. It provides information about investigation, weaponization, delivery, exploitation, installation, command and control, action, etc. It can be helpful for companies in being aware and proactive for preventing such attacks in future. Presenting Cyber Kill Chain For Insider Threat In Cyber Security Slides PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Investigation, Delivery, Installation, Exploitation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
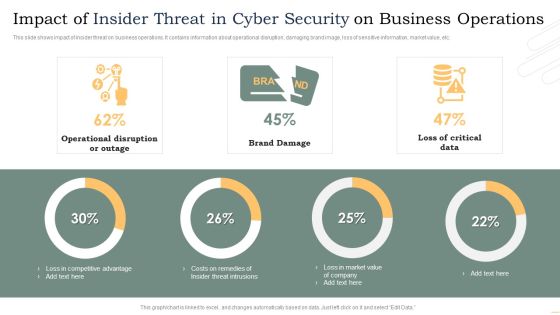
Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF
This slide shows impact of insider threat on business operations. It contains information about operational disruption, damaging brand image, loss of sensitive information, market value, etc. Pitch your topic with ease and precision using this Impact Of Insider Threat In Cyber Security On Business Operations Microsoft PDF. This layout presents information on Operational Disruption Or Outage, Brand Damage, Loss Critical Data. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF
This slide shows industry wise statistics of insider and outsider threat. It provides information about industry sector, malicious and involuntary insider, outsider, banking, production, retail, hospital, etc. Showcasing this set of slides titled Industry Wise Statistics Of Insider And Outsider Threat In Cyber Security Guidelines PDF. The topics addressed in these templates are Industry Sector, Malicious Insider, Inside Attacker. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF
This slide shows plan for managing insider risk with case status. It provides information about users, alert, status, severity, time detected, action plan, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF. This layout presents information on Requires Review, Action Plan, Case Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF
This slide shows user details tracked by insider threat dashboard. It provides information such as exposure events, file activity, archive, document, image, pdf, ppt, scripts, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Tracking Dashboard With User Details Portrait PDF. This layout presents information on Private Data, Exposure Events, User Activity, File Activity, Over Time. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF
This slide shows mitigation techniques for reduction of insider threats. It provides information such as precise data managed, user access reduction and maintaining vigilance. Presenting Mitigation Techniques To Reduce Insider Threat In Cyber Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Manage Data Precisely, Limit User Access, Maintain Vigilance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF
This slide shows technologies impact matrix for insider threat use cases. It contains details such as firewalls, data loss prevention, SIEM, user behavior analytics, process control system, etc. Showcasing this set of slides titled Assessment Matrix Indicating Impact Of Technologies On Insider Threat In Cyber Security Use Cases Themes PDF. The topics addressed in these templates are Key Insider, Threat, Use Cases, Key Technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
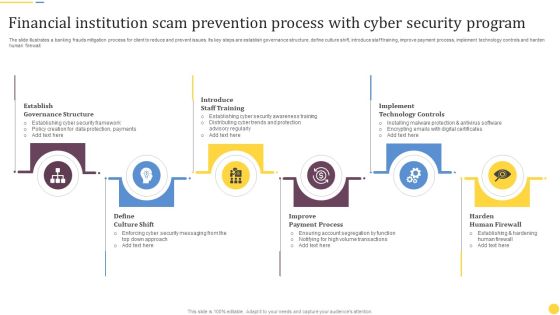
Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF
The slide illustrates a banking frauds mitigation process for client to reduce and prevent issues. Its key steps are establish governance structure, define culture shift, introduce staff training, improve payment process, implement technology controls and harden human firewall. Presenting Financial Institution Scam Prevention Process With Cyber Security Program Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Establish Governance Structure, Introduce Staff Training, Implement Technology Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Staff Training Schedule With Cost Mobile Device Security Management Diagrams PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Addressing Staff Training Schedule With Cost Mobile Device Security Management Diagrams PDF bundle. Topics like Advanced Skills, Coaching Sessions, Assessment Tools can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determine Current Scenario Of Mobile Devices Usage At Workplace Mobile Device Security Management Template PDF
This slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. Deliver and pitch your topic in the best possible manner with this Determine Current Scenario Of Mobile Devices Usage At Workplace Mobile Device Security Management Template PDF. Use them to share invaluable insights on Determine Frequency, Mobile Device, Workplace and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Determine Incident Reporting By Mobile Devices Departments Mobile Device Security Management Topics PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different IT departments. Deliver and pitch your topic in the best possible manner with this Determine Incident Reporting By Mobile Devices Departments Mobile Device Security Management Topics PDF. Use them to share invaluable insights on Person Involved, Average Cost, Department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
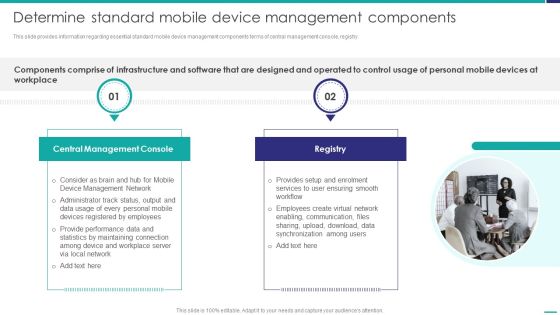
Determine Standard Mobile Device Management Components Mobile Device Security Management Information PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.This is a Determine Standard Mobile Device Management Components Mobile Device Security Management Information PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Console, Create Virtual, Synchronization Among. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF
This slide provides information regarding various configuration profiles using MDM technology such as basics, email accounts, internet and additional settings. Presenting Determine Various Configuration Profiles Using MDM Technology Mobile Device Security Management Infographics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Restrictions, Internet Settings, Additional Settings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. This is a Determine Various Mobile Device Management Deployment Methods Mobile Device Security Management Summary PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Enrollment Program, Configurator, Automatic Enrollment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative Determine Various Mobile Devices Existing At Workplace Mobile Device Security Management Guidelines PDF bundle. Topics like Corporate Data, Allowed Employees, Consumerization Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Presenting Ensuring Mobile Device Compliance And Policy Enforcement Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Automated Device, Enforcement Automation, Device Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF
This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. This is a Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Device Enrolment, Profile Management, Management Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Action Plan Mobile Device Security Management Rules PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.Deliver an awe inspiring pitch with this creative Mobile Device Management Action Plan Mobile Device Security Management Rules PDF bundle. Topics like Collecting Receivables, Compliance Obligations, Compliance Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mobile Device Management Assistance To Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. This is a Mobile Device Management Assistance To Mobile Device Security Management Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reducing Connection, Rendering Appropriate, Remote Configuration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Tools Integration Ppt PowerPoint Presentation Complete Deck With Slides
This complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes IT Security Automation Tools Integration Ppt PowerPoint Presentation Complete Deck With Slides and has templates with professional background images and relevant content. This deck consists of total of fourty two slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.

Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF
This slide shows the monthly project management timeline for website development which includes two teams such as UX and Backend team whose main tasks are system designing, getting approval from client, creating wireframes of pages, defining website policies, etc. Showcasing this set of slides titled Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF. The topics addressed in these templates are Staffing Resource Planning, Staff Recruiting, Architecture Planning. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF
This slide covers key steps cyber incident response plan process. It involves six stages such as preparation, detection, analysis, containment, eradication and recovery. Persuade your audience using this Key Steps Managing Cyber Security Incident Response Plan Process Portrait PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Preparation, Detection, Analysis, Eradication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Integrated IOT Blockchain Platform Applications To Enhance Security And Transparency Portrait PDF
This slide covers applications based on internet of things and blockchain technology. The purpose of this slide is to provide information about various features of these applications. It includes elements such as applications comprising of supply chain and logistics, automotive industry, smart homes, etc along with features, uses and major players. Pitch your topic with ease and precision using this Integrated IOT Blockchain Platform Applications To Enhance Security And Transparency Portrait PDF. This layout presents information on Automotive Industry, Smart Homes, Applications. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF
Welcome to our selection of the Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

IT Security Automation Systems Guide Ppt PowerPoint Presentation Complete With Slides
This is a professional and ready to use PowerPoint deck for entrepreneurs, who want to showcase their business in the best light possible. Use this IT Security Automation Systems Guide Ppt PowerPoint Presentation Complete With Slides and prepare an engaging pitch to showcase potential in the industry of your choice. Whether you are just starting out or business or planning to scale, deploy this forty three slide complete deck to demonstrate your ideas for bringing innovation and creativity in the business. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

IT Risk Management Approaches Organizations Risk Management And IT Security Graphics PDF
This slide highlights the information technology risks management approaches which includes risk avoidance, risk sharing, risks reduction and risk retention. Want to ace your presentation in front of a live audience Our IT Risk Management Approaches Organizations Risk Management And IT Security Graphics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Certified Information Systems Security Professional CISSP Salary And JOB Details IT Certifications To Enhance Introduction PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Present like a pro with Certified Information Systems Security Professional CISSP Salary And JOB Details IT Certifications To Enhance Introduction PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Series Of Cyber Security Attacks Against Ukraine 2022 Ppt PowerPoint Presentation Complete With Slides
People are consistently online to look for new ways to start a business or make money. What better than impressing that target audience with your Series Of Cyber Security Attacks Against Ukraine 2022 Ppt PowerPoint Presentation Complete With Slides, with its relatable and valuable content. This sixty one slide complete deck will turn a mundane session into a power-packed wow level presentation that your prospects will love to revisit over and over. This actionable preset will cover the nuances of all business slides. You can populate the slides in this template with your content and share the file with the presentation attendees as well.

Series Of Cyber Security Attacks Against Ukraine 2022 Weaknesses Of Russian Cyber Cell Pictures PDF
This slide represents the weaknesses of russian cyber cells, which are expected as in other countries, such as lack of skilled professionals and corrupted officials. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Series Of Cyber Security Attacks Against Ukraine 2022 Weaknesses Of Russian Cyber Cell Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF
Retrieve professionally designed Table Of Contents For Series Of Cyber Security Attacks Against Ukraine 2022 Website Template PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF
Slidegeeks has constructed Table Of Contents Series Of Cyber Security Attacks Against Ukraine 2022 Elements PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
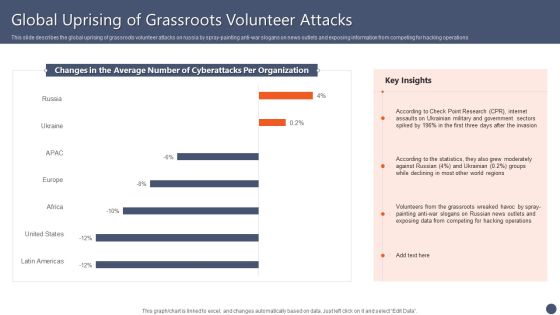
Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF
This slide describes the global uprising of grassroots volunteer attacks on russia by spray-painting anti-war slogans on news outlets and exposing information from competing for hacking operations. Boost your pitch with our creative Series Of Cyber Security Attacks Against Ukraine 2022 Global Uprising Of Grassroots Volunteer Attacks Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF
This slide covers key elements of cybersecurity awareness training program. It involves elements such as make message relevant, use real world examples, common language, present small messages and use continued reinforcement. Presenting Key Elements Of IT Security Awareness Training Program Ppt Model Example PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Make Message Relevant, Use Examples, Use Common Language. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF
This slide covers quarterly cybersecurity awareness training program plan. It involves activities such as cybersecurity knowledge and survey, compliance training, phishing simulation etc. Pitch your topic with ease and precision using this Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF. This layout presents information on Key Message, Core Awareness Activities, Responsible Person, Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Best Practices For Effective IT Security Awareness Training Program Background PDF
This slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Effective IT Security Awareness Training Program Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Including Everyone, Establishing Basics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF
This slide covers KPI dashboard to assess training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Pitch your topic with ease and precision using this Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF. This layout presents information on Major Training Course, Major Satisfactory, Training Course. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
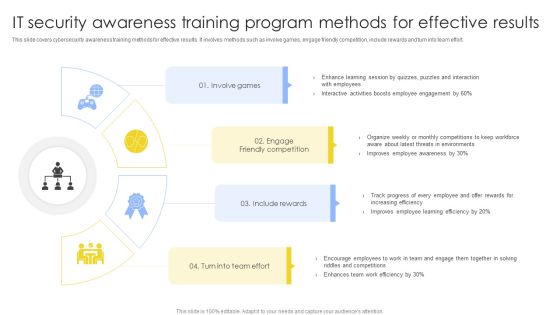
IT Security Awareness Training Program Methods For Effective Results Summary PDF
This slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Presenting IT Security Awareness Training Program Methods For Effective Results Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Involve Games, Engage Friendly Competition, Include Rewards. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Awareness Training Program Process To Ensure Effectiveness Diagrams PDF
This slide covers cybersecurity awareness training program process to ensure effectiveness. It involves steps such as identify training need, determine type of training, identify goals and objectives, implement and evaluate program. Persuade your audience using this IT Security Awareness Training Program Process To Ensure Effectiveness Diagrams PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Implement Training, Determine Type Training, Identify Training Need. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
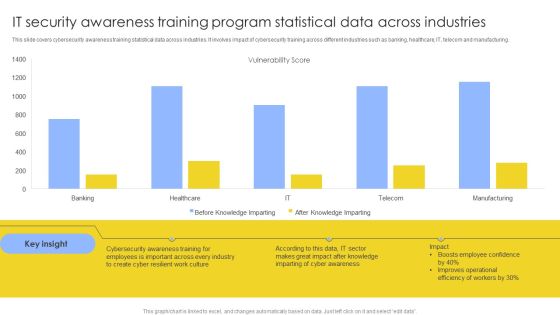
IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF
This slide covers cybersecurity awareness training statistical data across industries. It involves impact of cybersecurity training across different industries such as banking, healthcare, IT, telecom and manufacturing. Showcasing this set of slides titled IT Security Awareness Training Program Statistical Data Across Industries Mockup PDF. The topics addressed in these templates are Vulnerability Score, Cyber Awareness, Improves Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Why IT Security Awareness Training Program Is Essential For Employees Background PDF
This slide covers need of cybersecurity awareness training withing organization. It involves reasons such as increases employee awareness, assures educated staff, enhances organizational reputation and boosts confidence. Presenting Why IT Security Awareness Training Program Is Essential For Employees Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increases Awareness, Assures Educated Staff, Enhances Organizational Reputation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides
Use this Organizing Security Awareness Training To Minimize Downtime Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF
The purpose of this slide is to outline different actors who are involved in the most critical cyber attack. Online criminals, foreign governments, hackers and malicious insiders are some of the key players who are responsible for cyber attack. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Determining The Actors Behind Most Significant Cyber Mockup PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF
The Organizing Security Awareness Most Common Cyber Attack Faced By Our Employees Mockup PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Table Of Contents For Organizing Security Awareness Training To Minimize Downtime Rules PDF
Present like a pro with Table Of Contents For Organizing Security Awareness Training To Minimize Downtime Rules PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information Security Risk Administration And Mitigation Plan Ppt PowerPoint Presentation Complete Deck With Slides
Conduct adequate research on all facets of your business and grow its in sales, profit, etc using this ready-made PPT slide. This Information Security Risk Administration And Mitigation Plan Ppt PowerPoint Presentation Complete Deck With Slides displays parameters to help you evaluate business environment from all angles. Incorporate this organized PPT Design in seventy two slides to classify your top challengers. It is a customizable slide, so use it as per your requirement. Download now to showcase your expertise in all things business, and the specialized knowledge you may have.

Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF
Retrieve professionally designed Assessing Cost Of Information Breach In Different Countries Information Security Risk Administration Topics PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.
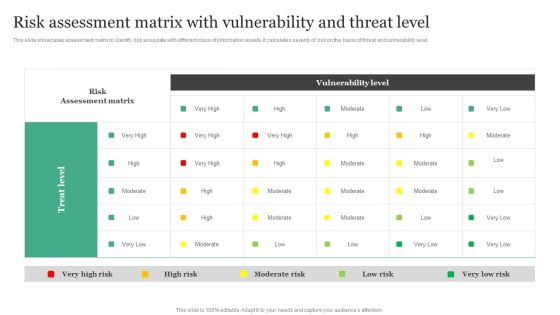
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF
This slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level.Boost your pitch with our creative Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Administration Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
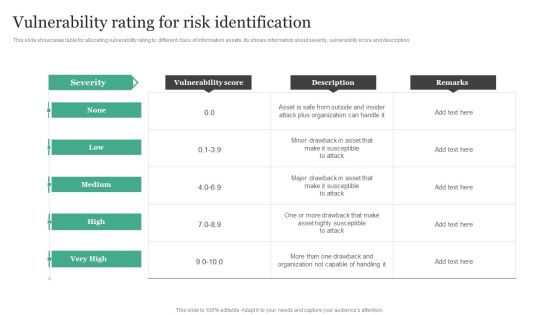
Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF
Retrieve professionally designed Vulnerability Rating For Risk Identification Information Security Risk Administration Introduction PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Business Mobile Device Security Management And Mitigation Ppt PowerPoint Presentation Complete Deck With Slides
If you are looking for Business Mobile Device Security Management And Mitigation Ppt PowerPoint Presentation Complete Deck With Slides to help improve your customer connect, this is the perfect option. Download this PowerPoint Template to make an effective observation on business strategies and policies. You can analyze techniques that prove beneficial or otherwise. You can easily monitor and compare other businesses on how they interact with customers and the industry benchmarks surrounding this with each of the sixty three slides of the complete deck a lesson the same. The 100 precent customizable feature of the presentation ensures that this has to be in your collection, at any cost. Download now.

Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF
This slide provides information regarding data inventory collection with mobile device management system storing information such as hardware, software, management and additional information. Make sure to capture your audiences attention in your business displays with our gratis customizable Addressing Data Inventory Collection With Mobile Business Mobile Device Security Management Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
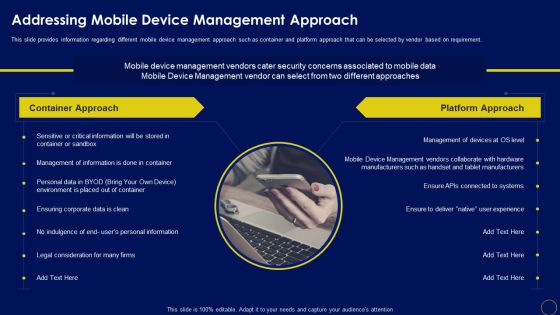
Addressing Mobile Device Management Business Mobile Device Security Management Download PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This modern and well-arranged Addressing Mobile Device Management Business Mobile Device Security Management Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Addressing Timeframe For Incident Management At Business Mobile Device Security Management Sample PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Welcome to our selection of the Addressing Timeframe For Incident Management At Business Mobile Device Security Management Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Determine Current Scenario Of Mobile Devices Usage At Workplace Business Mobile Device Security Structure PDF
This slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Determine Current Scenario Of Mobile Devices Usage At Workplace Business Mobile Device Security Structure PDF from Slidegeeks and deliver a wonderful presentation.

Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. The Determine Impact Of Effective Mobile Device Management Solution Business Mobile Device Security Guidelines PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF
This slide provides information regarding essential standard mobile device management components terms of central management console, registry.Slidegeeks has constructed Determine Standard Mobile Device Management Components Business Mobile Device Security Sample PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Want to ace your presentation in front of a live audience Our Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. Present like a pro with Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Best Practices For Assessing Cyber Security Risk Assessment Ppt PowerPoint Presentation File Graphics Template PDF
This slide depicts the best practices for assessing cybersecurity risk scenario which includes defining threat scenario, assessing inherent risk, evaluating impact of controls, assessing residual risks, actionable steps to improve, Presenting Best Practices For Assessing Cyber Security Risk Assessment Ppt PowerPoint Presentation File Graphics Template PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Feedback Loop, Assess Residual Risk, Evaluate Impacts, Assess Inherent Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF
Retrieve professionally designed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Slide Professional PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF
Slidegeeks has constructed Table Of Contents Security Automation To Analyze And Mitigate Cyberthreats Diagrams PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF
This slide covers steps utilised to breach data. It includes stages such as probing, performing initial attack, expansion of attacks and data lifting. Presenting Four Steps Of Cyber Security Data Breach Threats Process Ppt Icon Format Ideas PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Probe, Initial Attack, Expanded Attack, Data Lift. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and main reputation of business. Find a pre-designed and impeccable Mitigation Strategies To Tackle Information Security Threats Cybersecurity Risk Assessment Inspiration PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
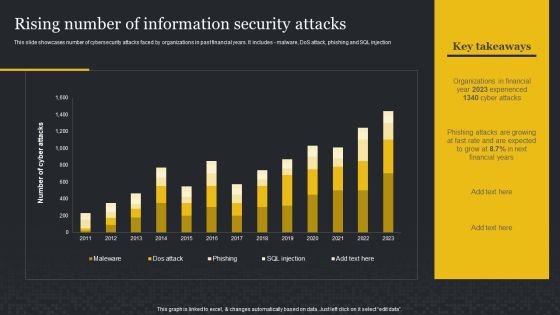
Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection. Boost your pitch with our creative Rising Number Of Information Security Attacks Cybersecurity Risk Assessment Brochure PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Slidegeeks has constructed Kpis To Measure Information Security Risk Management Cybersecurity Risk Assessment Infographics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF
This slide covers framework to ensure safe transactions on ecommerce platform. It includes regulatory strategies, financial and marketing operation strategies. Persuade your audience using this E Business Model Security Strategy Framework To Prevent Fraudulent Transactions Rules PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Customer Transactions, Assurance Metrics, Document Intellectual. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Prevention Of Information Key Stakeholders Of Cyber Security Awareness Training Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Prevention Of Information Key Statistics Showing The Impact Of Security Awareness Infographics PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. This modern and well-arranged Prevention Of Information Key Statistics Showing The Impact Of Security Awareness Infographics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides
This Security Control Techniques For Real Estate Project Ppt PowerPoint Presentation Complete Deck With Slides is designed to help you retain your audiences attention. This content-ready PowerPoint Template enables you to take your audience on a journey and share information in a way that is easier to recall. It helps you highlight the crucial parts of your work so that the audience does not get saddled with information download. This Fifty one slide PPT Deck comes prepared with the graphs and charts you could need to showcase your information through visuals. You only need to enter your own data in them. Download this editable PowerPoint Theme and walk into that meeting with confidence.

Security Control Techniques For Real Estate Project Solution To Overcome Construction Site Poor Guidelines PDF
Present like a pro with Security Control Techniques For Real Estate Project Solution To Overcome Construction Site Poor Guidelines PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Security Control Techniques For Real Estate Project Checklist For Construction Site Hazard Identification Introduction PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF
The Security Control Techniques For Real Estate Project Hazard Impact Analysis For Construction Site Icons PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Cyber Physical System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides
This incisive, comprehensive Cyber Physical System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas, planning and strategic framework just a glance of this comprehensive deck of fifty seven slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly-placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now.

Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF
The following slide depicts some key trends in cyber threats happening across the globe. It includes some facts and figures related to the malware attack, data breach records, annual losses etc. Presenting Annual Statistical Trends In Cyber Security Incident Ppt Outline Shapes PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Malware Attack, Business Fall, Data Breaches. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF
The given slide depicts some common sources of cybersecurity threats. It comprises of corporate spies, malicious insiders, hacktivists, terrorist groups, hackers, criminal groups etc. Persuade your audience using this Common And Prevalent Sources Of Cyber Security Incident Ppt Gallery Themes PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Spies, Malicious Insiders, Terrorist Group, Hacktivists. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Eight Phases Of Cyber Security Incident Lifecycle Ppt Summary Portrait PDF
The below slide gives insights of various stages in cyber attacks. It begins with initial reconnaissance, initial compromise, establish foothold, escalate privileges, internal reconnaissance, move laterally, maintain presence and ends with complete mission. Presenting Eight Phases Of Cyber Security Incident Lifecycle Ppt Summary Portrait PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Maintain Presence, Move Laterally, Internal Reconnaissance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF
The following slide showcases various tools to prevent cyber attacks. It comprises of tool name, period of free trial, its features and the estimated cost. Showcasing this set of slides titled Estimating Cost Of Tools Required To Prevent Cyber Security Incident Ppt Gallery Master Slide PDF. The topics addressed in these templates are Free Trial, Cost, User Friendly, Highly Automated. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF
This slide describes the integrity and confidentiality principle of GDPR, which implies putting suitable technologies and organizational safeguards to avoid hazards. Do you know about Slidesgeeks Information Security Integrity And Confidentiality Principle Of GDPR Law Structure PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
 Home
Home