Security
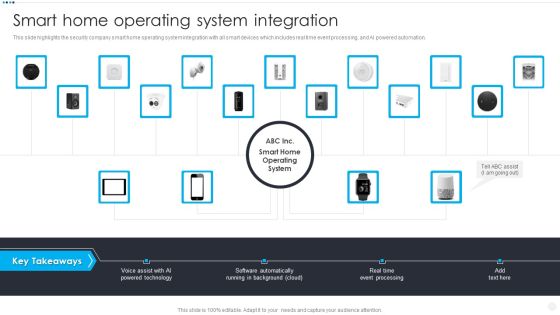
Smart Home Security Solutions Company Profile Smart Home Operating System Integration Elements PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. This is a Smart Home Security Solutions Company Profile Smart Home Operating System Integration Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Voice Assist AI, Powered Technology Software, Automatically Running Background. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Detection And Investigation, Phishing Detection, Left Employees In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
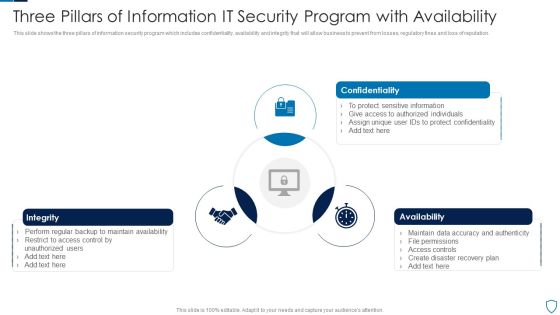
Three Pillars Of Information IT Security Program With Availability Summary PDF
This slide shows the three pillars of information security program which includes confidentiality, availability and integrity that will allow business to prevent from losses, regulatory fines and loss of reputation.Presenting Three Pillars Of Information IT Security Program With Availability Summary PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Confidentiality, Integrity, Availability This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF
Following slide illustrates a scorecard that company will use to check its preparedness against various cyber security and digital risk events. Sections covered here are fraud prevention considerations, score and notes. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Scorecard To Check Cybersecurity And Digital Risk Preparedness Professional PDF. Use them to share invaluable insights on Risk Prevention, Risk Prevention, Risk Occurrence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Ways To Accomplish ISO 27001 Accreditation Current Security Management Capabilities Overview Summary PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Current Security Management Capabilities Overview Summary PDF. Use them to share invaluable insights on Core Functions, Key Enablers, Required Standard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
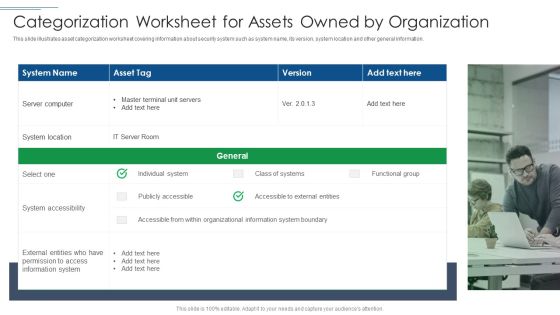
IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like System Location, System Accessibility, Information System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Presenting Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Management Training, Potential Mitigation, Already Developed In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF
This slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date. Pitch your topic with ease and precision using this Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF. This layout presents information on Response Planning, Risk Assessment, Response Communication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
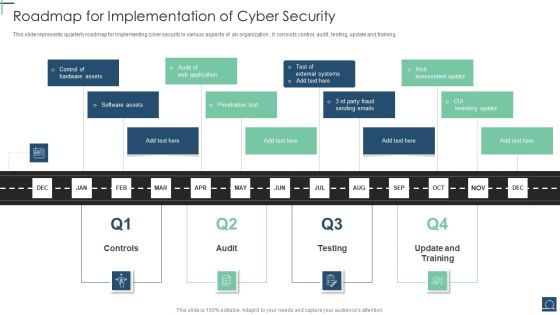
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
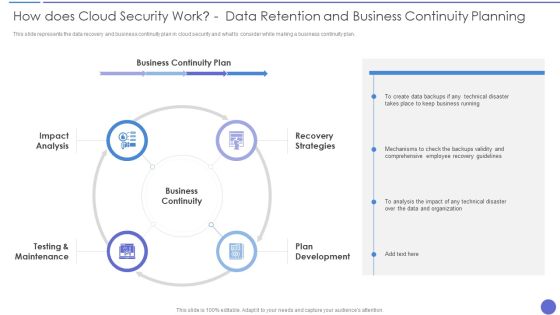
How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Presenting How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Continuity, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

30 60 90 Days Plan To Implement Cloud Security In Business Formats PDF
This slide defines the 30,60 and 90 days plan to implement cloud security in the organization and what tasks would be performed on each 30 days interval.This is a 30 60 90 Days Plan To Implement Cloud Security In Business Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyze Different, Provided By Vendors, Categorized Data You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
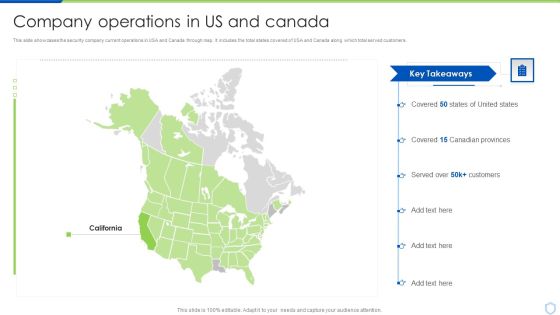
Security And Surveillance Company Profile Company Operations In US And Canada Demonstration PDF
This slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers.Presenting Security And Surveillance Company Profile Company Operations In US And Canada Demonstration PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Canadian Provinces, Covered, Key Takeaways. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Camera System Company Profile Company Operations In US And Canada Mockup PDF
This slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers.Presenting Security Camera System Company Profile Company Operations In US And Canada Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Key Highlights, Customers, Canadian Provinces. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
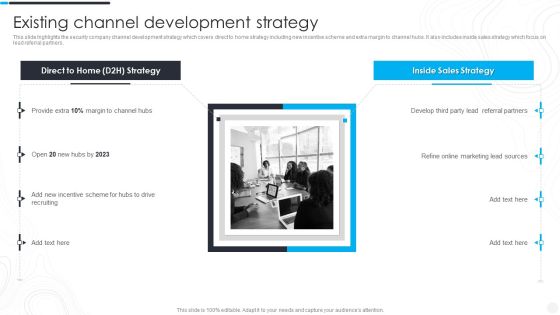
Security Camera System Company Profile Existing Channel Development Strategy Designs PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Security Camera System Company Profile Existing Channel Development Strategy Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Referral Partners, Incentive Scheme, Marketing Lead. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Overcome The Security Awareness Training Program Challenges Clipart PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver and pitch your topic in the best possible manner with this How To Overcome The Security Awareness Training Program Challenges Clipart PDF. Use them to share invaluable insights on Burden On Administrators, Employee Participation, Lose Interest and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Presenting Practices To Improve Security Awareness Level Amongst The Employees Contd Structure PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Management Involved, Develop Robust, Set Guidelines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF
The purpose of this slide is to outline various statistics showing the lack of security awareness amongst the employees. The statistics covered in the slide is related to malware infection, using personal cloud server, malicious attachment etc.Presenting Statistics Highlighting Lack Of Cyber Security Awareness Amongst Employees Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Employees Believe, Store Confidential, Malicious Attachments. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. This is a Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gamification, Personalization, High Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF
This slide highlights the security audit which showcase the risks related to accounts and user computers and also states the data which are at high risk. Presenting Website And Social Media IT Security Audit With Risk Level Ppt Styles Pictures PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Current Value, Risk, Risk Level. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
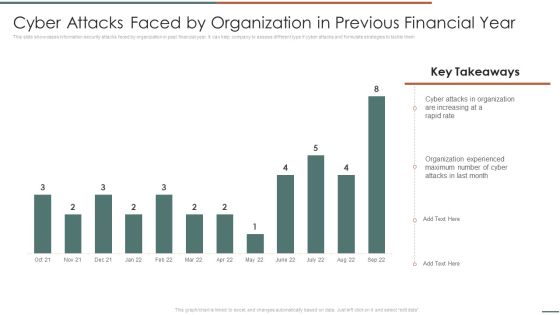
Information Security Risk Evaluation Cyber Attacks Faced By Organization In Previous Financial Year Template PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Cyber Attacks Faced By Organization In Previous Financial Year Template PDF. Use them to share invaluable insights on Attacks In Organization, Organization Experienced, Attacks Last and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Matrix For Threat Solution And Risk Management Ideas PDF
This slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Matrix For Threat Solution And Risk Management Ideas PDF bundle. Topics like Privilege Abuse, Storage Exposure, Database Activity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF
This slide showcase matrix that can help organization to identify the probability of different information security attacks and formulate mitigation strategy in advance. It can help organization to manage the major risks and safeguard the information.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Probability Assessment Matrix For Risk Management Demonstration PDF. Use them to share invaluable insights on Accidental Intentional, Unauthorized, Critical Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook Security Controls To Reduce The Risk Of Ransomware Information PDF bundle. Topics like Gains Access, Takes Control, Impacts Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF
This slide covers objectives challenges catalysts and benefits of the security in IT or OT convergence and reduce systems cyberattack surface. This is a Digitalization Of Operative Enterprises IT OT Convergence Security Objectives Challenges Catalysts And Benefits Download PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF. Use them to share invaluable insights on Analysis Progress, Response Progress, Plan Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
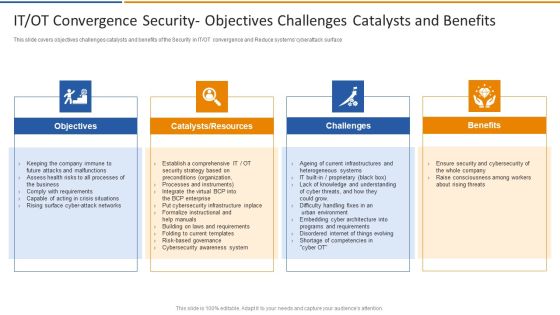
IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT or OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Smart Venture Digitial Transformation Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts, Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Staff Recruiting Criteria And Training Centre Designs PDF
This slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Presenting Security Agency Business Profile Staff Recruiting Criteria And Training Centre Designs PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Selection Criteria, Authorized Training Centre. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF
This slide shows user tracking sheet for insider threat with impact assessment. It provides details such as user behavior, indicator type, impact on security information and event manage SIEM, impact on interference framework, etc. Showcasing this set of slides titled Insider Threat In Cyber Security User Tracking Sheet With Impact Assessment Inspiration PDF. The topics addressed in these templates are Indicator Type, Impact On SIEM, Interference Framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Awareness Campaign Roadmap With Goal And Target Audience Mockup PDF
This slide shows timeline for campaign to raise security awareness . It covers target audience, goal, phase 1 and 2. Persuade your audience using this Security Awareness Campaign Roadmap With Goal And Target Audience Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Target Audience, Goal, awareness. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

AI Playbook For Business Stage Five Security Breach Readiness Checklist Microsoft PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. This is a AI Playbook For Business Stage Five Security Breach Readiness Checklist Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Operations, Organizations Transforming, Related To Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF
This slide covers objectives challenges catalysts and benefits of the Security in IT OT convergence and Reduce systems cyberattack surface. This is a IT OT Convergence Security Objectives Challenges Managing Organizational Transformation Professional PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Objectives, Catalysts Resources, Challenges, Benefits. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. This is a Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mitigate Ddos Attacks, Prevent Customer Data Breach, Block Malicious Bot Abuse. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. This is a Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Article Surveillance, Install Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. This is a Information Technology Threat Mitigation Methods Prioritized Cyber Security Threats With Risk Mitigation Plan Sample PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Owner, Risk Priority, Risk Mitigation Plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF
This slide signifies the six stage implementation plan to create effective cyber security project. It covers information about steps like identify, analyse, evaluate, prioritise, treat and monitor. Presenting Six Steps Action Plan To Develop Effective Cyber Security Strategy Ppt Layouts Designs Download PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Identify, Monitor, Priorities, Evaluate. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. This is a IT Security Automation Tools Integration Managed Detection And Response Layer For Expert Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Alert Monitoring, Attack Investigation, Threat Hunting, Incident Response. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Project Evaluation Plan To Safeguard Business Operation Designs PDF
This slide signifies the cyber security project evaluation plan for safeguarding organisation operations. It covers information regarding to the stages like initiation, planning, execution, implement and monitor. Persuade your audience using this Cyber Security Project Evaluation Plan To Safeguard Business Operation Designs PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Planning, Execution, Implement, Initiation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF
This This slide signifies the six step process for successful implementation of risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor. Presenting 6 Stage Process For Implementation Of Risk Administration In Cyber Security Project Ideas PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Prioritize, Evaluate, Analyse, Treat. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
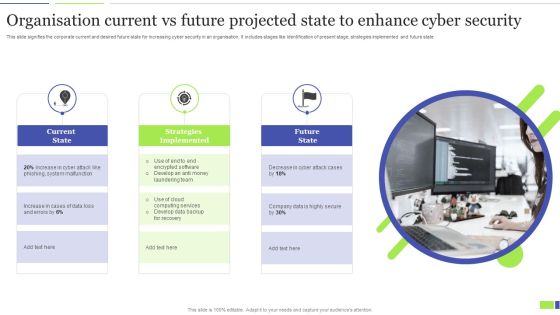
Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF
This slide signifies the corporate current and desired future state for increasing cyber security in an organisation. It includes stages like identification of present stage, strategies implemented and future state. Presenting Organisation Current Vs Future Projected State To Enhance Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Current State, Strategies Implemented, Future State. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents For Cyber Security Components To Enhance Processes Template PDF
Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Table Of Contents For Cyber Security Components To Enhance Processes Template PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Table Of Contents For Cyber Security Components To Enhance Processes Template PDF today and make your presentation stand out from the rest.

Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF
This slide covers cyber security incident response KPI dashboard. It involves details such as intent alarm, event trend sources, event trend, sensor activity, major operating systems and asset information. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF. This layout presents information on Top Alarms Method, Alarms Intent, Timely Event Trend. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF
This slide covers comparative assessment of cyber security incident response tools. It involves features such as advanced threat hunting ability, net flow analysis, user behavior analytics and superior forensic analysis. Presenting Comparative Assessment Of Managing Cyber Security Incident Response Tools Demonstration PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Superior Forensic Analysis, User Behavior Analytics, Netflow Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
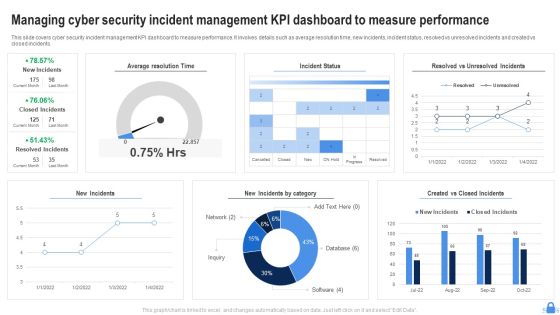
Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF
This slide covers cyber security incident management KPI dashboard to measure performance. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled Managing Cyber Security Incident Management KPI Dashboard To Measure Performance Download PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF
This slide covers cyber security incident response framework for performance enhancement. It involves four aspects such as develop policies and procedures, training, monitor systems and test incident response plan. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response Framework For Performance Enhancement Formats PDF. This layout presents information on Report Incidents, Threat, Restore System. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF
This slide shows risk landscape dashboard for cyber security program management which contains threat level by month, current threat posture, threats by source, threats by owner, risks by threat and threat register. This can help businesses in effective management of risks and counter measures. Showcasing this set of slides titled Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF. The topics addressed in these templates are Current Threat Posture, Threat Register, Source. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Welcome to our selection of the IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

IT System Risk Management Guide Table Of Contents Security Background PDF
Are you searching for a IT System Risk Management Guide Table Of Contents Security Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT System Risk Management Guide Table Of Contents Security Background PDF from Slidegeeks today.

Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Automation Framework Managed Detection And Response Layer For Expert Monitoring Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
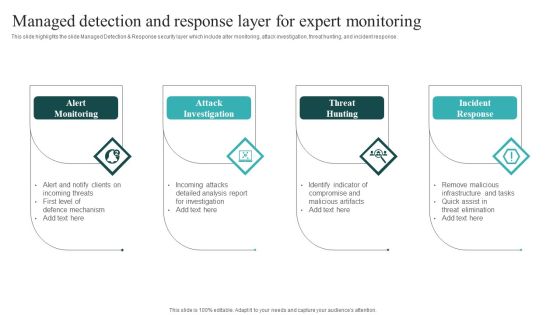
IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Table Of Contents Organizations Risk Management And IT Security Formats PDF
Find highly impressive Table Of Contents Organizations Risk Management And IT Security Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents Organizations Risk Management And IT Security Formats PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF
This slide depicts the hermetic wiper attack on ukrainian corporations, detected by a threat intelligence agency on february 23rd, and it damaged the master boot record through eases partition master. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Hermetic Wiper Cyber Attack Against Ukraine Icons PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
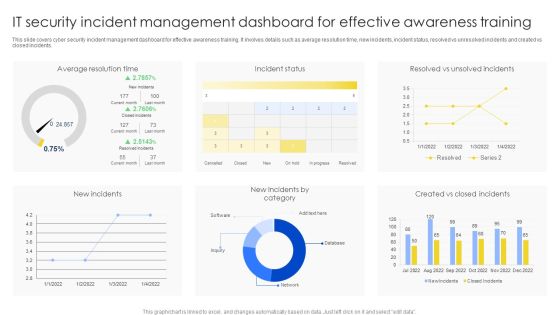
IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF
This slide covers cyber security incident management dashboard for effective awareness training. It involves details such as average resolution time, new incidents, incident status, resolved vs unresolved incidents and created vs closed incidents. Showcasing this set of slides titled IT Security Incident Management Dashboard For Effective Awareness Training Pictures PDF. The topics addressed in these templates are Average Resolution Time, Incident Status, New Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizing Security Awareness Tracking Sheet To Monitor The Performance Of Employees Elements PDF
Get a simple yet stunning designed Organizing Security Awareness Tracking Sheet To Monitor The Performance Of Employees Elements PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Organizing Security Awareness Tracking Sheet To Monitor The Performance Of Employees Elements PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Agenda For Information Security Risk Administration And Mitigation Plan Download PDF
Explore a selection of the finest Agenda For Information Security Risk Administration And Mitigation Plan Download PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Agenda For Information Security Risk Administration And Mitigation Plan Download PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks.Boost your pitch with our creative Cyber Attacks Faced By Different Departments Information Security Risk Administration Clipart PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
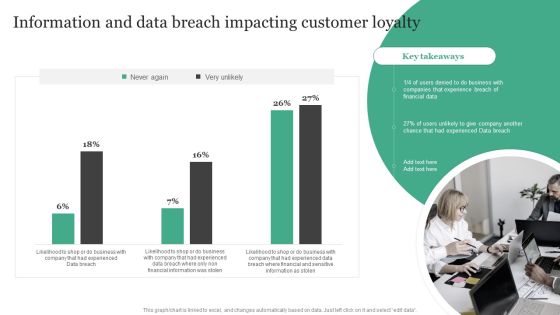
Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF
Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Information And Data Breach Impacting Customer Loyalty Information Security Risk Administration Demonstration PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Table Of Contents For Information Security Risk Administration And Mitigation Plan Slide Download PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Table Of Contents For Information Security Risk Administration And Mitigation Plan Slide Download PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Table Of Contents For Information Security Risk Administration And Mitigation Plan Slide Download PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

 Home
Home