Security

7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF
Presenting 7 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Mockup PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF
Presenting 9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Management Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF
Presenting 12 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Infographics PDF to dispense important information. This template comprises tweleve stages. It also presents valuable insights into the topics including Continuously Improve, Business Goals, Security Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Administration Plan Icon To Improve Cyber Security Project Summary PDF
Presenting Risk Administration Plan Icon To Improve Cyber Security Project Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Risk Administration Plan, Icon To Improve, Cyber Security, Project. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security Incident Management Icon Ppt Infographics Design Templates PDF
Presenting Managing Cyber Security Incident Management Icon Ppt Infographics Design Templates PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Managing Cyber Security, Incident Management, Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Managing Cyber Security Incident Response Plan Icon Ppt Ideas Example Introduction PDF
Presenting Managing Cyber Security Incident Response Plan Icon Ppt Ideas Example Introduction PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Managing Cyber Security, Incident Response, Plan Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF
Pitch your topic with ease and precision using this Virus Cyber Security Attack Warning On Web Browser Icon Ppt Example 2015 PDF. This layout presents information on Virus Cyber Security, Attack Warning, Web Browser Icon. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Top 5 Issues In Security Problem Management Ppt Slides Show PDF
Presenting Top 5 Issues In Security Problem Management Ppt Slides Show PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Lack Threat Program, No Operational Exercises, Security Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security Awareness Training Program Icon Ppt Slides Example File PDF
Presenting IT Security Awareness Training Program Icon Ppt Slides Example File PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security, Awareness Training, Program Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
IT Security Awareness Training Program Plan Icon Ppt Ideas Graphics PDF
Presenting IT Security Awareness Training Program Plan Icon Ppt Ideas Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security Awareness, Training Program Plan, Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security For Cloud Based Systems Icon To Reduce Data Breaches Download PDF
Presenting Security For Cloud Based Systems Icon To Reduce Data Breaches Download PDF to dispense important information. This template comprises Three stages. It also presents valuable insights into the topics including Security For Cloud, Based Systems Icon, Reduce Data Breaches . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Payment Security Technology In Market Investor Transactions Summary PDF
Presenting Icon For Payment Security Technology In Market Investor Transactions Summary PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Icon For Payment Security, Technology Market Investor, Transactions Summary. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF
Pitch your topic with ease and precision using this Pathway Of Change Framework For Food Security And Sustainable Agriculture Clipart PDF. This layout presents information on Pathway Change Framework, Food Security Sustainable. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Icon Of Digital Transformation To Boost Financial Institution Industry Security Graphics PDF
Presenting Icon Of Digital Transformation To Boost Financial Institution Industry Security Graphics PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Digital Transformation, Boost Financial Institution, Industry Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Use Of AI In Financial Institution Industry To Improve Security Mockup PDF
Presenting Use Of AI In Financial Institution Industry To Improve Security Mockup PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Financial Institution, Industry Improve Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Icon Showcasing IT Security Risk Management And Risk Analysis Designs PDF
Presenting Icon Showcasing IT Security Risk Management And Risk Analysis Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Icon Showcasing IT Security, Risk Management Risk Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Risk Management Icon Showcasing Risk Assessment Checklist Graphics PDF
Presenting IT Security Risk Management Icon Showcasing Risk Assessment Checklist Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including IT Security Risk Management, Icon Showcasing Risk, Assessment Checklist. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Cases Action Plan Response Icon Ppt PowerPoint Presentation Gallery Display PDF
Presenting Cyber Security Cases Action Plan Response Icon Ppt PowerPoint Presentation Gallery Display PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security Cases, Action Plan Response, Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF
Pitch your topic with ease and precision using this Icon Showcasing Application Of Computer Vision Technologyin Digital Security Sample PDF. This layout presents information on Showcasing Application, Computer Vision, Technologyin Digital Security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Digital Device Icon To Improve Information Technology Security Communication Plan Infographics PDF
Presenting Digital Device Icon To Improve Information Technology Security Communication Plan Infographics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Digital Device Icon, Improve Information Technology, Security Communication Plan. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Team Data Security And Communication Plan Icon Graphics PDF
Presenting Information Technology Team Data Security And Communication Plan Icon Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Information Technology, Team Data Security, Communication Plan Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF
Presenting Icon For Strategic Plan Roadmap To Improve Cyber Security Clipart PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Strategic Plan, Roadmap Improve, Cyber Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
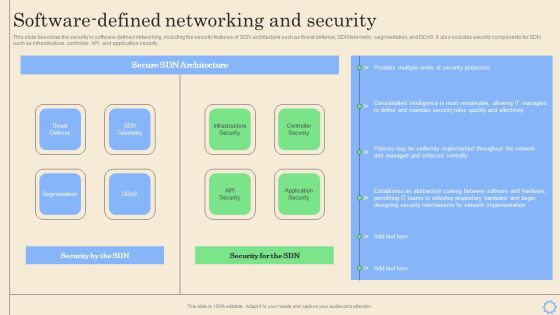
Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Get a simple yet stunning designed Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

5G Network Applications And Features Security Architecture In 5G Technology Elements PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Whether you have daily or monthly meetings, a brilliant presentation is necessary. 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF can be your best option for delivering a presentation. Represent everything in detail using 5G Network Applications And Features Security Architecture In 5G Technology Elements PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Security Management Plan Steps In Detail Training And Building Role Competencies Topics PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies topics pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Clipart PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies clipart pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security management roles, training required, competencies required. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail Training And Building Role Competencies Portrait PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. This is a security management plan steps in detail training and building role competencies portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management system, information security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Training And Building Role Competencies Slides PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Training and Building Role Competencies. Presenting security management plan steps in detail training and building role competencies slides pdf to provide visual cues and insights. Share and navigate important information on five tages that need your due attention. This template can be used to pitch topics like security management roles, training required, role description In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF
This slide depicts the security services on the google cloud platform. The purpose of this slide is to show the various security services available on the google cloud platform. The main components include a cloud resource manager, cloud identity and access management, cloud security scanner, and cloud platform security. Welcome to our selection of the Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF
This slide represents the ways to implement SecOps into security operations. The purpose of this slide is to highlight the main methods to combine SecOps and SOC and the strategies that cater to distributing security operations, building a security center of excellence, and establishing a culture of collaboration. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Methods To Integrate Secops Into Security Rules PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Demonstration PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Data Backup and Data Loss Recovery Plan. Presenting Security management plan steps in detail data backup and data loss recovery plan demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security management plan steps in detail - data backup and data loss recovery plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
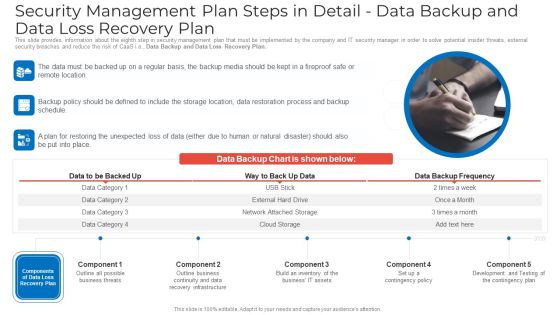
Security Management Plan Steps In Detail Data Backup And Data Loss Recovery Plan Ideas PDF
This slide provides information about the eighth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Data Backup and Data Loss Recovery Plan. This is a security management plan steps in detail data backup and data loss recovery plan ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail data backup and data loss recovery plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Graphics PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives graphics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail identifying goals and objectives. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Portrait PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. System Maintenance and Monitoring. This is a security management plan steps in detail system maintenance and monitoring portrait pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security management plan steps in detail system maintenance and monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Identifying Goals And Objectives Download PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Identifying Goals and Objectives. This is a security management plan steps in detail identifying goals and objectives download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation, security, management, organizational, information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF
Purpose of this slide is to educate team members about different security incidents and attacks. It includes information about traditional security incidents, cyber security attacks and common techniques. Create an editable Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Cyber Risks And Incident Response Playbook Addressing The Various Security Incidents And Attacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF
This slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Welcome to our selection of the Cybersecurity Operations Cybersecops Roles And Responsibilities Of Security Operations Microsoft PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
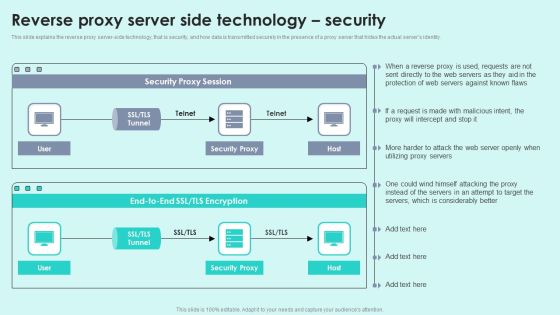
Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity.Deliver and pitch your topic in the best possible manner with this Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF. Use them to share invaluable insights on Security Proxy, Protection Servers, Considerably Better and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Picture Editing Company Outline Canva Security Processes And Systems Elements PDF
This slide highlights the Canva security systems encryption, data security, attack, monitoring, staged releases, secure development, account safety and in- app permissions. Welcome to our selection of the Picture Editing Company Outline Canva Security Processes And Systems Elements PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Develop Corporate Cyber Security Risk Mitigation Plan Cover Letter For Organization Cyber Protection Services Inspiration PDF
Presenting develop corporate cyber security risk mitigation plan cover letter for organization cyber protection services inspiration pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like systems and servers, achieve goals, secure organization information, network security monitoring. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Impact Analysis For Effective Threat Management Slides PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative corporate security and risk management impact analysis for effective threat management slides pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration Selecting Suitable Security Incident Management Software Demonstration PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration selecting suitable security incident management software demonstration pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
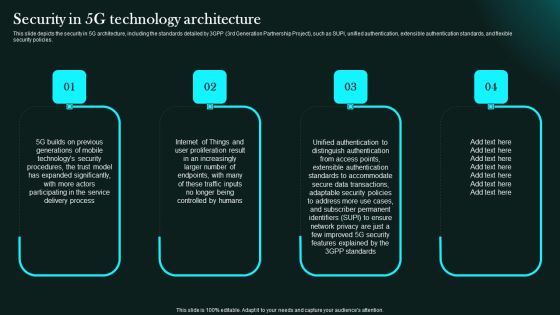
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
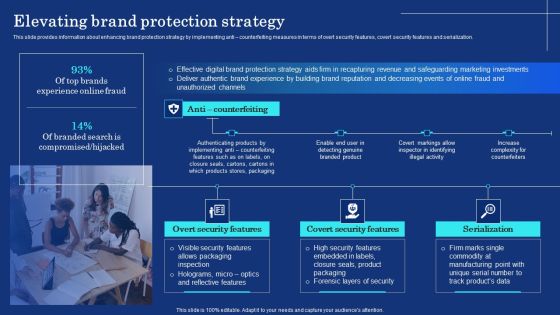
Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF
This slide shows framework which can be used by organizations to develop cloud security for data protection. It includes authentication, access control, user behavior analytics, logging an reporting, etc. Persuade your audience using this Security For Cloud Based Systems Framework To Ensure Data Safety Pictures PDF. This PPT design covers Eight stages, thus making it a great tool to use. It also caters to a variety of topics including Security For Cloud, Based Systems Framework, To Ensure Data Safety . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the action plan timeline for security guard service proposal as it displays steps of the process such as training and evaluating etc. Presenting you an exemplary Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Action Plan Timeline For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Case Study For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the case study for security guard service proposal, as it highlights the project description, project results, project budget and project timeline. Presenting you an exemplary Case Study For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Cover Letter For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the security guard service proposal , as it highlights the key issues being faced by the organization and a brief background about the company. Presenting you an exemplary Cover Letter For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Cover Letter For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Next Step For Safety And Security System Services Proposal One Pager Sample Example Document
The following slide displays the next step that the organization has to take once the security proposal has been signed, these steps can be team meeting ,on-site visit etc. Presenting you an exemplary Next Step For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Next Step For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Companys Data Safety Recognition Impact Of Security Awareness Training Demonstration PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative companys data safety recognition impact of security awareness training demonstration pdf bundle. Topics like system misconfiguration, inadvertent disclosure, network intrusion can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home