Security
Financing Catalogue For Security Underwriting Agreement Timeline Ideas PDF
This is a financing catalogue for security underwriting agreement timeline ideas pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2017 to 2021. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
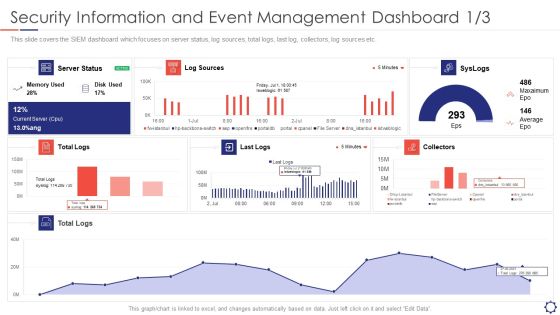
SIEM Security Information And Event Management Dashboard Average Structure PDF
This slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver an awe inspiring pitch with this creative siem security information and event management dashboard average structure pdf bundle. Topics like log sources, server status, collectors, syslogs, last logs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.b
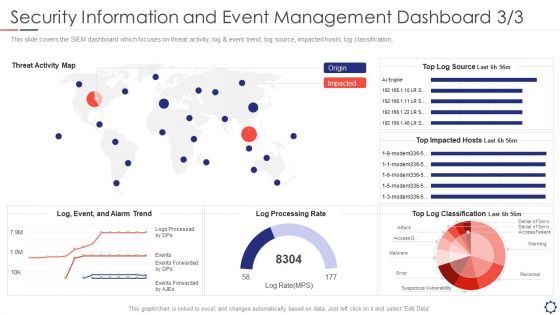
SIEM Security Information And Event Management Dashboard Rate Summary PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification,. Deliver an awe inspiring pitch with this creative siem security information and event management dashboard rate summary pdf bundle. Topics like reconnel, suspicious vulnerability, access, warming can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda Of Cyber Security Administration In Organization Information PDF
This is a agenda of cyber security administration in organization information pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda, purpose, management, valuable, assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Dispose Data And Equipment Properly Graphics PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Deliver an awe inspiring pitch with this creative desktop security management dispose data and equipment properly graphics pdf bundle. Topics like dispose data and equipment properly can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Cyber Attacks Experienced By Company Summary PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2021. Deliver and pitch your topic in the best possible manner with this desktop security management cyber attacks experienced by company summary pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Problems Faced By The Organization Ideas PDF
This slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Deliver an awe inspiring pitch with this creative desktop security management problems faced by the organization ideas pdf bundle. Topics like problems faced by the organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective IT Risk Management Process Information Security Decision Template PDF
Presenting effective it risk management process information security decision template pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like implement, resource allocation, risk factors, standardize. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Incident Reporting Dashboard Brochure PDF
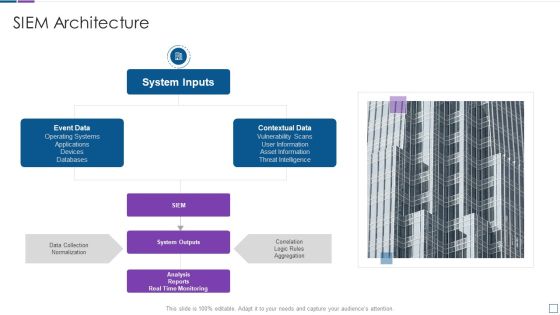
Real Time Assessment Of Security Threats SIEM Architecture Sample PDF
This is a real time assessment of security threats siem architecture sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system inputs, event data, contextual data, system outputs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Information Technology Security Ppt Model Maker PDF
This is a agenda for information technology security ppt model maker pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, availability, integrity, information, strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Deliver an awe inspiring pitch with this creative it security assessment matrix of cyber risks infographics pdf bundle. Topics like data center, industrial, retail, health care can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For IT Security Ppt Example File PDF
This is a agenda for it security ppt example file pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strategies, cybersecurity, plan, safeguard, policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Info Security Ppt PowerPoint Presentation Icon Pictures PDF
This is a agenda for info security ppt powerpoint presentation icon pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employees, common threats, data and information systems, integrity and availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
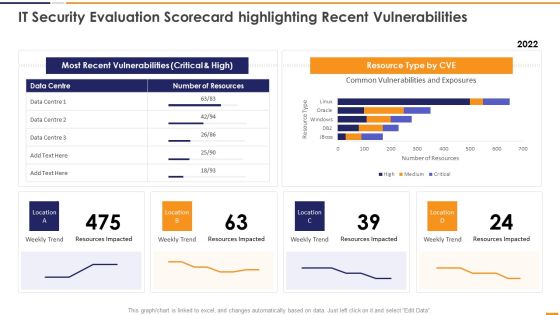
IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an awe inspiring pitch with this creative IT Security Evaluation Scorecard Highlighting Recent Vulnerabilities Introduction PDF bundle. Topics like Most Recent Vulnerabilities, Resource Type CVE, Weekly Trend Location can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
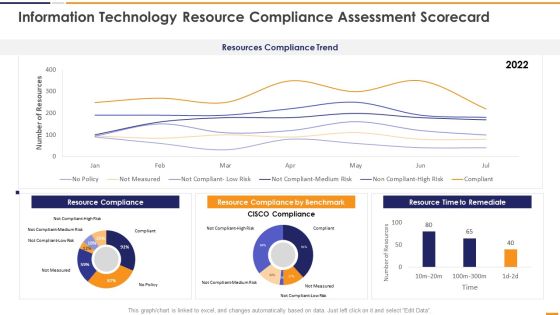
IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this IT Security Evaluation Scorecard Information Technology Resource Compliance Background PDF. Use them to share invaluable insights on Resources Compliance Trend, Resource Compliance 2022, Resource Compliance Benchmark, Resource Time Remediate and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Three Types Of Home Security Coverage Demonstration PDF
This slide shows types of coverage in home insurance. It includes dwelling, contents and personal liability. Showcasing this set of slides titled Three Types Of Home Security Coverage Demonstration PDF. The topics addressed in these templates are Contents Coverage, Dwelling Coverage, Personal Liability. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Project Risk Administration Life Cycle Summary PDF
This slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting Cyber Security Project Risk Administration Life Cycle Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Monitoring, Identification, Analyse, Prioritize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Security Threats Contract Breaches With Clients Download PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting Cloud Security Threats Contract Breaches With Clients Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Organization, Business Partners, Information Could. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Budget For New Recruited Professionals Infographics PDF
This slide represents the budget for newly recruited professionals, including new professionals, number of total posts, annual salaries, and total funding for salaries.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Budget For New Recruited Professionals Infographics PDF. Use them to share invaluable insights on New Professionals, Certified Ethical, Annual Salaries and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Hacking Impact On The Company Information PDF
This slide represents the impact of hacking, such as damaged reputation, crisis communication PR, additional damage repair costs, loss of clients and business partners, and restoration of the original operation. Deliver an awe inspiring pitch with this creative IT Security Hacker Hacking Impact On The Company Information PDF bundle. Topics like Company Reputation, Crisis Communication, Damage Repair can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Phases Of Hacking Topics PDF
This slide represents the phases of hacking, including reconnaissance, scanning, gaining access to the victims computer, maintaining access, and clearing tracks.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Phases Of Hacking Topics PDF. Use them to share invaluable insights on Maintaining Access, Reconnaissance, Gaining Access and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Purpose Of Ethical Hacking Slides PDF
This slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Purpose Of Ethical Hacking Slides PDF. Use them to share invaluable insights on Vulnerabilities Discovered, Malevolent Hackers, Malevolent Hackers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
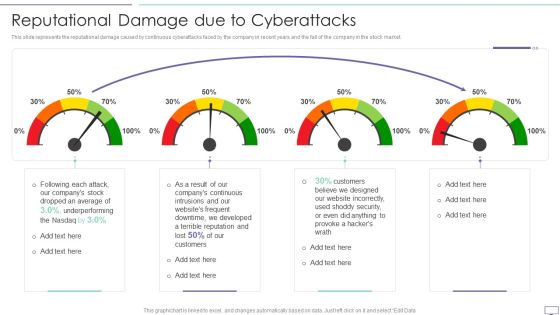
IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF
This slide represents the reputational damage caused by continuous cyberattacks faced by the company in recent years and the fall of the company in the stock market.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Reputational Damage Due To Cyberattacks Guidelines PDF. Use them to share invaluable insights on Website Incorrectly, Underperforming, Dropped An Average and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For IT Security Hacker Background PDF
This is a Table Of Contents For IT Security Hacker Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Current Situation, Impact Of Hacking, Repairing Damages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Security Management Four Phase Process Topics PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting Business Security Management Four Phase Process Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Evaluate, Treat, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Table Of Contents Cyber Security Automation Framework Ideas PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Cyber Security Automation Framework Ideas PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Framework Of IT Security Awareness Training Program Information PDF
This slide covers framework of cybersecurity awareness training program. It involves five steps such as analyse, plan, deploy, measure and optimize. Presenting Framework Of IT Security Awareness Training Program Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Analyze, Plan, Deploy, Measure, Optimize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
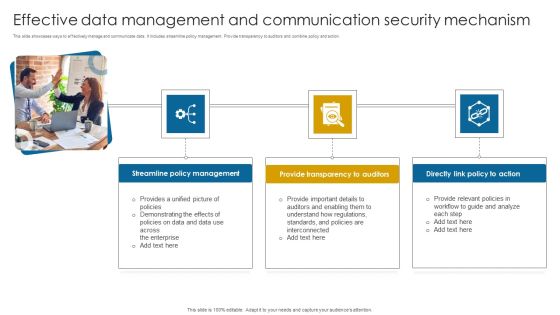
Effective Data Management And Communication Security Mechanism Themes PDF
This slide showcases ways to effectively manage and communicate data. It includes streamline policy management. Provide transparency to auditors and combine policy and action. Presenting Effective Data Management And Communication Security Mechanism Themes PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Streamline Policy Management, Provide Transparency, Directly Action. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
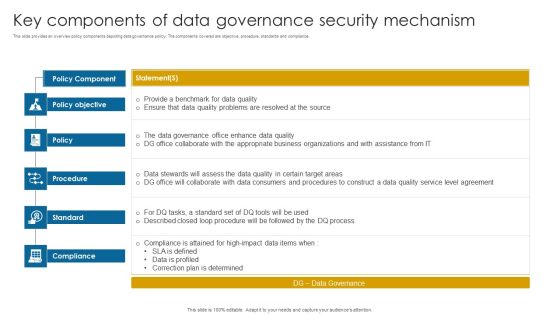
Key Components Of Data Governance Security Mechanism Information PDF
This slide provides an overview policy components depicting data governance policy. The components covered are objective, procedure, standards and compliance.Pitch your topic with ease and precision using this Key Components Of Data Governance Security Mechanism Information PDF. This layout presents information on Data Governance, Compliance Attained, Correction Determined. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF
This slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Showcasing this set of slides titled Mitigation Plan For Cyber Security Risk Assessment Management Sample PDF. The topics addressed in these templates are Threat, Risk, Risk Priority. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Agenda Security Automation To Analyze And Mitigate Cyberthreats Brochure PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Agenda Security Automation To Analyze And Mitigate Cyberthreats Brochure PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cyber Security Business Project Investment Evaluation With Goals Structure PDF
This slide signifies the budget distribution table on developing business objectives. It includes stages like goals, investment, analysis, strategies to implement and key result. Showcasing this set of slides titled Cyber Security Business Project Investment Evaluation With Goals Structure PDF. The topics addressed in these templates are Project Goals, Investment, Analysis, Strategies To Implement, Key Result. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Quotes Guidelines PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Quotes Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
IT Security Risk Management And Incident Management Dashboard Icons PDF
This slide displays dashboard to help company in designing initiatives to mitigate cybersecurity risks. It includes kpis such as incident management, patches, compliance, vulnerabilities, etc. Showcasing this set of slides titled IT Security Risk Management And Incident Management Dashboard Icons PDF. The topics addressed in these templates are Compliance, Patches, Incident Management, Vulnerabilities Management, Cybersecurity Initiatives. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Risk Management Process For Organization Template PDF
This slide displays flow diagram to illustrate cybersecurity risk management process to ensure continuous monitoring. It includes components such as threats, vulnerabilities, impacts, intelligence, etc. Showcasing this set of slides titled IT Security Risk Management Process For Organization Template PDF. The topics addressed in these templates are Organization, Cyber Intelligence, Continuous Monitoring, Vulnerabilities. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF
The following slide showcases evolution of cybersecurity infrastructure with developments in communication strategy. It presents information related to unawareness, reactive, proactive, etc. Presenting Evolution Of Effective Infra Cyber Security Infrastructure Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unaware, Reactive, Proactive. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
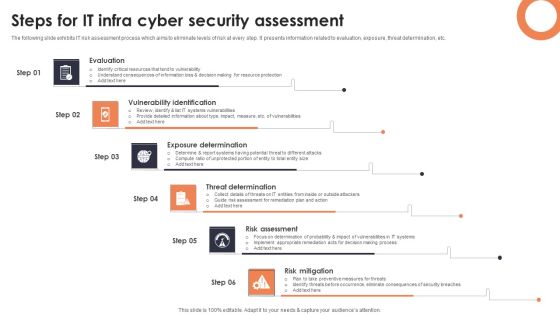
Steps For IT Infra Cyber Security Assessment Background PDF
The following slide exhibits IT risk assessment process which aims to eliminate levels of risk at every step. It presents information related to evaluation, exposure, threat determination, etc. Presenting Steps For IT Infra Cyber Security Assessment Background PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Evaluation, Vulnerability Identification, Exposure Determination. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Timeframe For Incident Management In Security Centre Portrait PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Timeframe For Incident Management In Security Centre Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
Security Software Company Investor Funding Pitch Deck Quotes Background PDF
This Security Software Company Investor Funding Pitch Deck Quotes Background PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cyber Security Breache Response Strategy Table Of Contents Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Breache Response Strategy Table Of Contents Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF
Slidegeeks has constructed Table Of Contents For Blockchain Security Solutions Deployment Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Security Training Program Frameworks Ppt Infographics Show PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.This is a security training program frameworks ppt infographics show pdf. template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like build and maintain a secure network and systems, protect cardholder data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Why Choose Us For Data Privacy Graphics PDF
This slide explains why you should choose us, including faster product delivery to market, decreased complexity, and secured integrations. Slidegeeks is here to make your presentations a breeze with Information Security Why Choose Us For Data Privacy Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
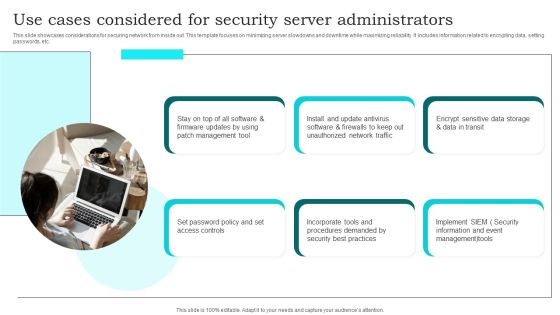
Use Cases Considered For Security Server Administrators Brochure PDF
This slide showcases considerations for securing network from inside out. This template focuses on minimizing server slowdowns and downtime while maximizing reliability. It includes information related to encrypting data, setting passwords, etc. Presenting Use Cases Considered For Security Server Administrators Brochure PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Management Tool, Set Password Policy, Unauthorized Network Traffic. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Benefits Of Blockchain Networks For Business Security Structure PDF
This slide defines the blockchain technology used to secure business data. The purpose of this template is to define blockchain technologies benefits, limitations and industry usage. It includes information related to public, private, hybrid and consortium technologies along with its advantages, disadvantages and industry usage. Pitch your topic with ease and precision using this Benefits Of Blockchain Networks For Business Security Structure PDF. This layout presents information on Public Permission Less, Private Permissioned, Hybrid Consortium. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Smart Phone Device Security Best Practices Structure PDF
This slide shows key practices for protecting business data of mobile. The purpose of this slide is to highlight latest practices that can be used for securing mobile data. It include practices such as enable user authentication, update OS system, etc. Presenting Smart Phone Device Security Best Practices Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Enable User Authentication, Avoid Using Public Wi Fi, Follow BYOD Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Scan Principle For Smart Phone Security Model Clipart PDF
This slide shows SCAN framework for securing phone against possible threats to prevent loss of business data. It include components such as system, configuration, application and network, etc. Persuade your audience using this Scan Principle For Smart Phone Security Model Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including System, Configuration, App. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Applications Of Confidential Computing Security Management Technology Sample PDF
The following slide contains the area of benefits where confidential computing is used to ensure data is secured and encrypted against malware attacks. Key uses are data protection, guard business process, collaboration and customer satisfaction. Presenting Applications Of Confidential Computing Security Management Technology Sample PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Data Protection, Guard Business Process, Collaboration, Customer Satisfaction. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Tools And Techniques Ppt PowerPoint Presentation Styles Vector
Presenting this set of slides with name cyber security tools and techniques ppt powerpoint presentation styles vector. This is a eight stage process. The stages in this process are fairly and lawfully processed, processed for limited purposes, adequate, relevant and not excessive, accurate and up to data, not kept for longer than necessary, processed in line with data subjects rights, secure, protected in international transfer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security Training Program For Employees Background PDF
This slide represents digital safety training program courses used to spread awareness amongst employees. It provides information regarding courses offered, delivery mode, duration, trainer and certification. Pitch your topic with ease and precision using this Online Security Training Program For Employees Background PDF. This layout presents information on Digital Risk Analysis, Securing Data And Information, Employees. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Approaches Of Disaster Recovery Plan For Data Security Topics PDF
This slide shows four approaches of cloud disaster recovery that can be used by an organization to create a data secure environment. It includes backup and restore, warm study, pilot light and multi site active or active approach. Presenting Approaches Of Disaster Recovery Plan For Data Security Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Warm Standby, Backup And Restore, Pilot Light. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF
This slide describes the different responsibilities of a secure operations center. The purpose of this slide is to showcase the multiple functions SOC teams perform, including communication with DevOps teams, coordinating incident response process, incident investigation, and prioritization of threats. There are so many reasons you need a Cybersecurity Operations Cybersecops Main Responsibilities Of Security Operations Template PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

User Authentication And Authorization Security Management Technology Summary PDF
This slide provides the use of multiple authentication and authorization technology which are used to protect systems and user information. Key categories are password based, multi factor, certificate based, biometrics and token based. Persuade your audience using this User Authentication And Authorization Security Management Technology Summary PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Based, Multi Factor, Certificate Based, Biometrics, Token Based. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Desktop Security Management Implementation Of Strong Password Policy Brochure PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. This is a desktop security management implementation of strong password policy brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation of strong password policy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Drivers Of Data Protection And Security Mechanism Infographics PDF
The following slide showcases data protection drivers to assist businesses with their legitimate use of personal data. The drivers covered are data location, sensitivity, protection, access and flow.Presenting Key Drivers Of Data Protection And Security Mechanism Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Data Location, Data Sensitivity, Data Protection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security GDPR Law Governing Data Privacy Formats PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Welcome to our selection of the Information Security GDPR Law Governing Data Privacy Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cyber Risk Strategies For Security Protection Mockup PDF
This slide highlights the cyber threat strategies that include risk assessment, phishing program, software protocols and end point protection. Persuade your audience using this cyber risk strategies for security protection mockup pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including proactive risk assessment, phishing program, software protocols. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
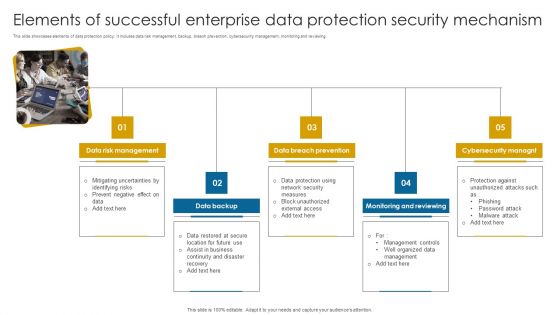
Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF
This slide showcases elements of data protection policy. It includes data risk management, backup, breach prevention, cybersecurity management, monitoring and reviewing.Persuade your audience using this Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Breach Prevention, Monitoring Reviewing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Solutions For Critical Infra Cyber Security Protection Download PDF
The following slide showcases various solutions to cyber vulnerabilities that can be detected and prevented from physical attacks. It presents information related to maintenance holes, ladder rack, etc. Presenting Solutions For Critical Infra Cyber Security Protection Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Maintenance Holes, Perimeter Fence, Ladder Rack . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Data Privacy In Educational Institutions Introduction PDF
This slide depicts data privacy in educational Information , institutions should issue a notice period of two days for approval before disclosing any information. This modern and well arranged Information Security Data Privacy In Educational Institutions Introduction PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Information Security Impact Of Data Privacy Laws Implementation Slides PDF
This slide shows the impact of data privacy laws implementation, including a better understanding of the collected data, the business will be more dependable, and so on. Take your projects to the next level with our ultimate collection of Information Security Impact Of Data Privacy Laws Implementation Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Information Security Training Schedule For Data Privacy Microsoft PDF
This slide represents the data privacy training program by covering the details of topics such as benefits and laws and duration for each topic to be covered. Present like a pro with Information Security Training Schedule For Data Privacy Microsoft PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

IT Security Hacker Is Ethical Hacking Legal Rules PDF
This slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks.Presenting IT Security Hacker Is Ethical Hacking Legal Rules PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Improve Defense, Anonymous Thieves, Qualified Cybersecurity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Home Security Company Services And Contact Information Structure PDF
This slide showcases services provided to insured against losses from insurance company. The services provided are interior and exterior renovation and remodeling, general contracting and new home construction. Showcasing this set of slides titled Home Security Company Services And Contact Information Structure PDF. The topics addressed in these templates are Reimbursement, Contract For Protection, Representing Services Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
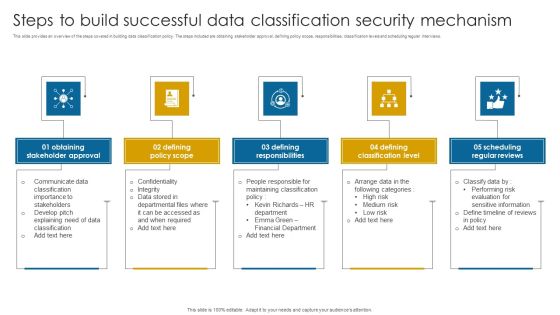
Steps To Build Successful Data Classification Security Mechanism Structure PDF
This slide provides an overview of the steps covered in building data classification policy. The steps included are obtaining stakeholder approval, defining policy scope, responsibilities, classification levels and scheduling regular interviews.Presenting Steps To Build Successful Data Classification Security Mechanism Structure PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Stakeholder Approval, Defining Policy Scope, Defining Responsibilities. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Hacker Email Prevention Guidelines For Employees Information PDF
This slide depicts the email prevention guidelines for employees, including spam filters and multi factor authentication for email login credentials.This is a IT Security Hacker Email Prevention Guidelines For Employees Information PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Authentication Process, Pieces Of Information, Factor Authentication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
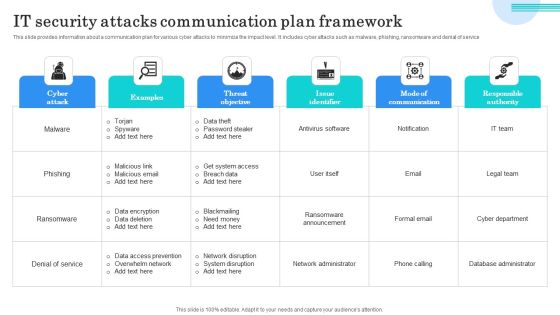
IT Security Attacks Communication Plan Framework Graphics PDF
This slide provides information about a communication plan for various cyber attacks to minimize the impact level. It includes cyber attacks such as malware, phishing, ransomware and denial of service. Showcasing this set of slides titled IT Security Attacks Communication Plan Framework Graphics PDF. The topics addressed in these templates are Data Theft, Password Stealer, Get System Access. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Advantages, Disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Csr Initiatives And Spending Mockup PDF
This slide highlights the CSR spend distribution by inhouse and partner spend. It also highlights the CSR initiatives that are carbon footprint reduction, labor policies, hunger program, community development and healthcare services. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Csr Initiatives And Spending Mockup PDF. Use them to share invaluable insights on Healthcare Services, Environment Safety, Community Development and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Cyber Security Risk Assessment Process Inspiration PDF
The slide shows cyber threat detection and protection measures in order to eliminate the potential risks to the business. The steps include identifying, detecting, responding, protecting, and recovering. Persuade your audience using this Business Cyber Security Risk Assessment Process Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identify, Detect, Respond, Protect, Recover. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Project Security Administration IT Workplace Employee Assistance Program Structure PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a project security administration it workplace employee assistance program structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Security Technology For Healthcare Industry Icons PDF
This slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification.Persuade your audience using this Blockchain Security Technology For Healthcare Industry Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authenticity Medicine, Electronic Health, Ensures Only Trusted. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Desktop Security Management Assessment Matrix Of Cyber Risks Infographics PDF
This slide depicts the cyberattacks surface based on different property types. It also covers the attacks based on web or mobile applications, online payments, employee devices. Presenting desktop security management assessment matrix of cyber risks infographics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like retail, systems, systems, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Hacker Introduction To Ethical Hacking Graphics PDF
This slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network.This is a IT Security Hacker Introduction To Ethical Hacking Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Approved Effort, Data Is Referred, Ethical Hacking. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Security Management Technology Working Flowchart Download PDF
This slide illustrates the working model of blockchain technology which is used to track and manage transaction in a business network. Process is divides into seven major steps. Persuade your audience using this Blockchain Security Management Technology Working Flowchart Download PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Completion, Cryptocurrency, Blockchain. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Data Breach Post Incident Communication Strategy Slides PDF
This slides provide information about post crisis communication plan how to handle it in effective manner. It includes elements such as crisis team, fast, precise, and sincereresponses, clear line of communication and restorative services Presenting Cyber Security Data Breach Post Incident Communication Strategy Slides PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Crisis Team, Communication, Restorative Services. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Highways Signs 2 PowerPoint Slides And Ppt Diagram Templates
Security Highways Signs 2 PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!

Security Table Collection PowerPoint Slides And Ppt Diagram Templates
Security Table Collection PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!

Security Tachometer Full Dial PowerPoint Slides And Ppt Diagram Templates
Security Tachometer Full Dial PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!
Security Traffic Direction PowerPoint Slides And Ppt Diagram Templates
Security Traffic Direction PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!

Security Warning Signs PowerPoint Slides And Ppt Diagram Templates
Security Warning Signs PowerPoint Slides And PPT Diagram Templates-These high quality powerpoint pre-designed slides and powerpoint templates have been carefully created by our professional team to help you impress your audience. All slides have been created and are 100% editable in powerpoint. Each and every property of any graphic - color, size, orientation, shading, outline etc. can be modified to help you build an effective powerpoint presentation. Any text can be entered at any point in the powerpoint template or slide. Simply DOWNLOAD, TYPE and PRESENT!

Data Security PowerPoint Slides And Ppt Diagram Templates
Data Security PowerPoint Slides And PPT Diagram Templates-These high quality, editable pre-designed powerpoint slides have been carefully created by our professional team to help you impress your audience. Each graphic in every slide is vector based and is 100% editable in powerpoint. Each and every property of any slide - color, size, shading etc can be modified to build an effective powerpoint presentation. Use these slides to convey complex business concepts in a simplified manner. Any text can be entered at any point in the powerpoint slide. Simply DOWNLOAD, TYPE and PRESENT!

Desktop Security Management Process Of Disaster Recovery Planning Professional PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a desktop security management process of disaster recovery planning professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plans, team, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Types Of Disaster Recovery Plan Topics PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a desktop security management types of disaster recovery plan topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, locations, service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Hacker Backup Of Sensitive Information Ideas PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization.This is a IT Security Hacker Backup Of Sensitive Information Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Different Service, Emergency Access, Natural Disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Threat Security Before And After Artificial Intelligence Formats PDF
This slide describes the four main cyber risks that currently threaten our digital world, as well as the difference between traditional methods and newer, AI based methods. It includes cyber threats such as malware, DDoS, IOT and endpoints and social engineering. Showcasing this set of slides titled Threat Security Before And After Artificial Intelligence Formats PDF. The topics addressed in these templates are Malware, Distributed Denial Service, Social Engineering. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

IT Security Management Technology User Market Guidelines PDF
The following slide provides the statistical data for user market of IT risk assessment and mitigation software to make business process efficient. The technology used are authentication, firewalls, encryption, data masking and data backup. Showcasing this set of slides titled IT Security Management Technology User Market Guidelines PDF. The topics addressed in these templates are Authentication, Firewalls, Encryption, Data Masking, Data Backup. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT Security Hacker Purpose Of Hackers Mockup PDF
This slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. This is a IT Security Hacker Purpose Of Hackers Mockup PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identity Theft, Computer Fraud, Privacy Breach. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
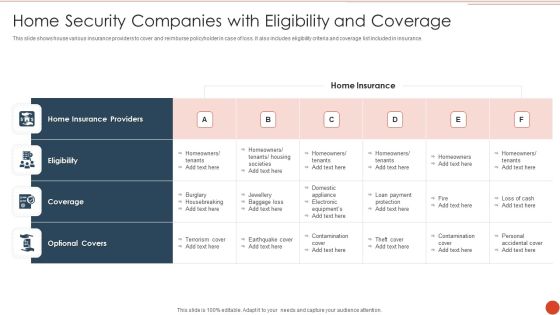
Home Security Companies With Eligibility And Coverage Infographics PDF
This slide shows house various insurance providers to cover and reimburse policyholder in case of loss. It also includes eligibility criteria and coverage list included in insurance. Showcasing this set of slides titled Home Security Companies With Eligibility And Coverage Infographics PDF. The topics addressed in these templates are Home Insurance Providers, Home Insurance, Loan Payment Protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Applications Of Data Masking Security Management Technology Sample PDF
This slide illustrates the multiple applications of data masking technology which helps to protect sensitive data by providing a functional alternative. Major elements include encryption, scrambling, nulling out, substitution, shuffling etc. Persuade your audience using this Applications Of Data Masking Security Management Technology Sample PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Date Aging, Shuffling, Substitution, Nulling Out, Scrambling, Encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Hacker Hacking Of Email Domain Inspiration PDF
This slide represents the hacking of the company email domain by hackers by sending spam emails to employees and stealing money from clients and customers.This is a IT Security Hacker Hacking Of Email Domain Inspiration PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like After Entering, Passwords And Other, Technological Upgrades. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
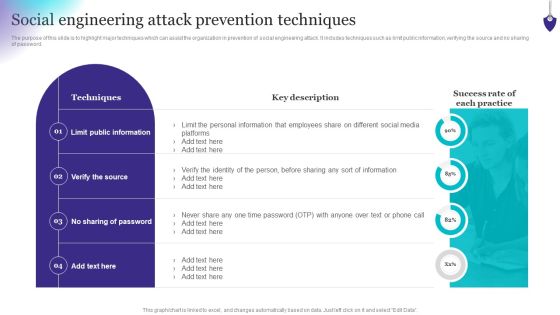
Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF
The purpose of this slide is to highlight major techniques which can assist the organization in prevention of social engineering attack. It includes techniques such as limit public information, verifying the source and no sharing of password. Want to ace your presentation in front of a live audience Our Organizing Security Awareness Social Engineering Attack Prevention Techniques Rules PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
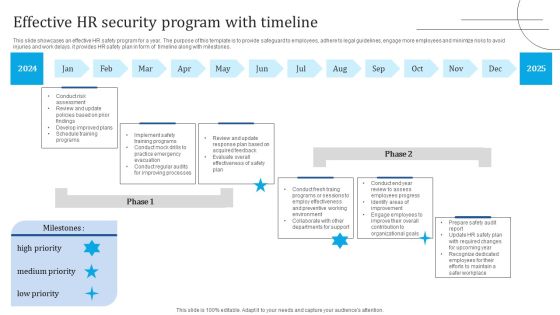
Effective HR Security Program With Timeline Portrait PDF
This slide showcases an effective HR safety program for a year. The purpose of this template is to provide safeguard to employees, adhere to legal guidelines, engage more employees and minimize risks to avoid injuries and work delays. it provides HR safety plan in form of timeline along with milestones. Showcasing this set of slides titled Effective HR Security Program With Timeline Portrait PDF. The topics addressed in these templates are Implement Safety Training Programs, Develop Improved Plans, Review Update. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Track Record Of Our Company Themes PDF
This slide highlights our past track record as a data privacy provider company and outlines that we promise 100 percent client satisfaction. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Security Track Record Of Our Company Themes PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Major Standard Compliances For Online Security Pictures PDF
This slide shows various standards that are established for digital safety and followed by organization to meet compliance regulations. It provides information for PCI DSS, SOC 2, NYDFS, NIST AND CCPA. Persuade your audience using this Major Standard Compliances For Online Security Pictures PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Develop Digital Safety, Requirements For Financial, Regulate Risk Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
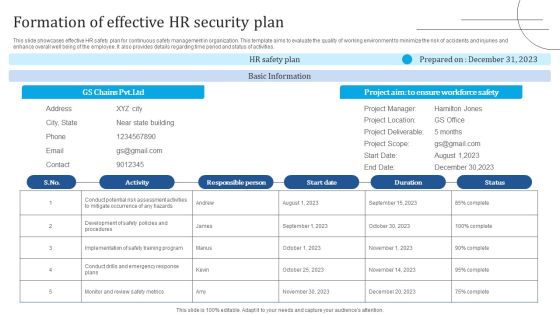
Formation Of Effective HR Security Plan Information PDF
This slide showcases effective HR safety plan for continuous safety management in organization. This template aims to evaluate the quality of working environment to minimize the risk of accidents and injuries and enhance overall well being of the employee. It also provides details regarding time period and status of activities. Presenting Formation Of Effective HR Security Plan Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Activity, Responsible Person, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Need Of Implementing HR Security Programs At Workplace Pictures PDF
This slide highlights the need of importance of workplace safety in an organization. This template aims to provide details regarding workplace safety to increase productivity, reduce turnover rates, safe working conditions, reduction in risk factors, avoid loss of resources, reduction in expenses, foster employee wellbeing and follow legal guidelines, etc. Showcasing this set of slides titled Need Of Implementing HR Security Programs At Workplace Pictures PDF. The topics addressed in these templates are Productivity, Working Environment, Absenteeism. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workplace Risk Mitigation Strategies For HR Security Portrait PDF
This slide highlights techniques for minimizing risk factors in the workplace. the purpose of this template is to employ effective strategies for ensuring workforce safety eventually enhancing overall productivity and efficiency. It also provides details regarding the status of performance along with insights. Showcasing this set of slides titled Workplace Risk Mitigation Strategies For HR Security Portrait PDF. The topics addressed in these templates are Risk Assessment Management, Safety Training And Education, Compliance Regulations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mobile Application Security Architecture For Clients Summary PDF
This slide represents the architecture designed to enable the mobile application safety to gain trust of clients. It includes details related to windows and web applications, smart card resource manager, Bluetooth smart card reader. Pitch your topic with ease and precision using this Mobile Application Security Architecture For Clients Summary PDF. This layout presents information on Windows Applications, Web Applications, Resource Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Comparative Assessment Of Online Security Management Software Summary PDF
This slide showcases comparative assessment of various digital safety management software used to boost performance across organization. It provides information regarding software, features, price, free trail and user ratings. Pitch your topic with ease and precision using this Comparative Assessment Of Online Security Management Software Summary PDF. This layout presents information on Price, Absence Management System, Softwares. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key Benefits Of Implementing Online Security Management System Infographics PDF
This slide showcases key benefits of implementing digital safety management system which help focus on higher priority business tasks. It provides information regarding quality data, improves productivity, compliance requirements, minimize error and reporting and tracking. Presenting Key Benefits Of Implementing Online Security Management System Infographics PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Improves Productivity, Quality Data, Minimize Error. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Online Security Threat And Risk Assessment Matrix Formats PDF
This slide showcases digital safety risk assessment matrix which helps analyze impact of threat on business processes. It provides information regarding hacking, data breaches, information misuse, malicious attacks and system failure. Showcasing this set of slides titled Online Security Threat And Risk Assessment Matrix Formats PDF. The topics addressed in these templates are Information Misuse, Data Breaches, Malicious Attacks. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

HR Security Training And Wellbeing KPI Dashboard Professional PDF
This slide showcases dashboard for HR safety training and wellbeing. This template aims to improve employee working efficiency and enhance working conditions to foster their working efficiency. It provides details regarding incidents reported, training programs implemented to reduce number of incidents, cost of providing training and level of employee satisfaction with training. Showcasing this set of slides titled HR Security Training And Wellbeing KPI Dashboard Professional PDF. The topics addressed in these templates are Severity, Injury Consequence, Employee Satisfaction Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Internet Banking Security Technology PowerPoint Templates And PowerPoint Themes 1112
We present our Internet Banking Security Technology PowerPoint Templates And PowerPoint Themes 1112.Use our Money PowerPoint Templates because, Inform your team of your ideas using our illustrative slides. Use our Technology PowerPoint Templates because, Demonstrate how they contribute to the larger melting pot. Use our Signs PowerPoint Templates because, Now put it up there for all to see. Use our Finance PowerPoint Templates because, Anoint it with your really bright ideas. Use our Business PowerPoint Templates because,Now use this slide to bullet point your views.Use these PowerPoint slides for presentations relating to Internet banking, money, technology, signs, finance, business. The prominent colors used in the PowerPoint template are Blue, Pink, Black

Access Regulations Technology Half Yearly Roadmap With Security Solution Guidelines
Presenting the access regulations technology half yearly roadmap with security solution guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Access Regulations Technology Three Months Roadmap With Security Solution Guidelines
Presenting our jaw dropping access regulations technology three months roadmap with security solution guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Five Year Individual Data Security Career Roadmap Guidelines
Presenting the five year individual data security career roadmap guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
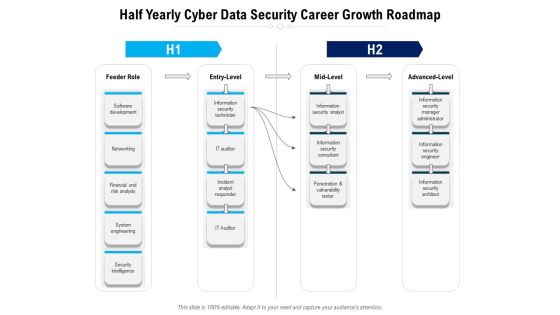
Half Yearly Cyber Data Security Career Growth Roadmap Topics
Presenting the half yearly cyber data security career growth roadmap topics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
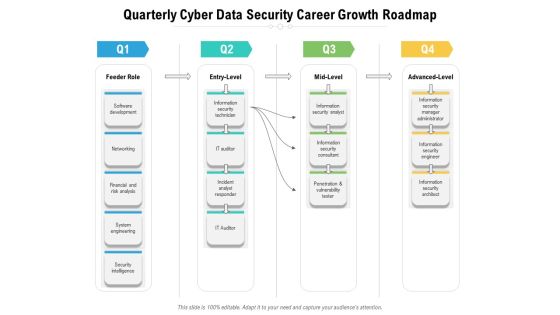
Quarterly Cyber Data Security Career Growth Roadmap Infographics
Presenting the quarterly cyber data security career growth roadmap infographics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Individual Data Security Career Roadmap Slides
Presenting the six months individual data security career roadmap slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Individual Data Security Career Roadmap Inspiration
Presenting the three months individual data security career roadmap inspiration. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
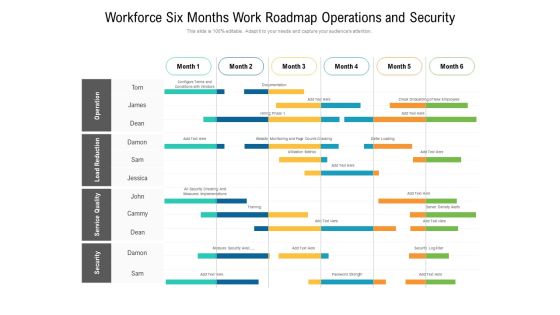
Workforce Six Months Work Roadmap Operations And Security Elements
Presenting the workforce six months work roadmap operations and security elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
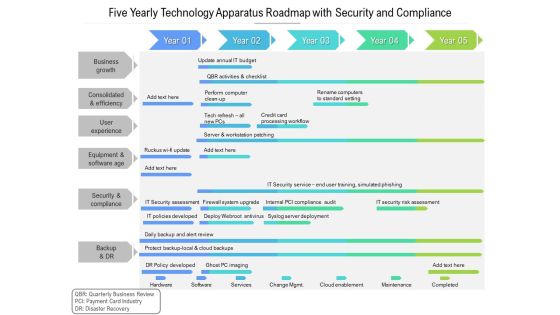
Five Yearly Technology Apparatus Roadmap With Security And Compliance Template
Presenting the five yearly technology apparatus roadmap with security and compliance template. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
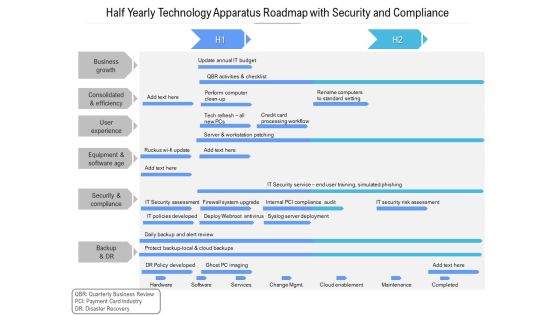
Half Yearly Technology Apparatus Roadmap With Security And Compliance Download
Presenting the half yearly technology apparatus roadmap with security and compliance download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Quarterly Technology Apparatus Roadmap With Security And Compliance Rules
Presenting the quarterly technology apparatus roadmap with security and compliance rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
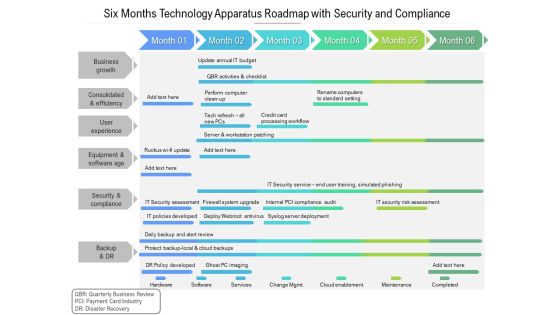
Six Months Technology Apparatus Roadmap With Security And Compliance Information
Presenting the six months technology apparatus roadmap with security and compliance information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
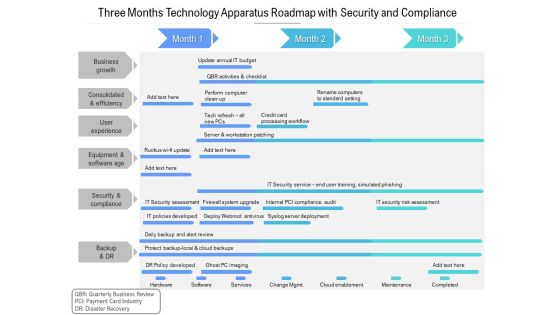
Three Months Technology Apparatus Roadmap With Security And Compliance Designs
Presenting the three months technology apparatus roadmap with security and compliance designs. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Plan Quarterly Roadmap With Multiple Phases Download
Presenting the cloud computing security plan quarterly roadmap with multiple phases download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Six Months Roadmap With Deployment Plan Themes
Presenting the cloud computing security six months roadmap with deployment plan themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Three Months Roadmap With Deployment Plan Introduction
Presenting our jaw dropping cloud computing security three months roadmap with deployment plan introduction. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
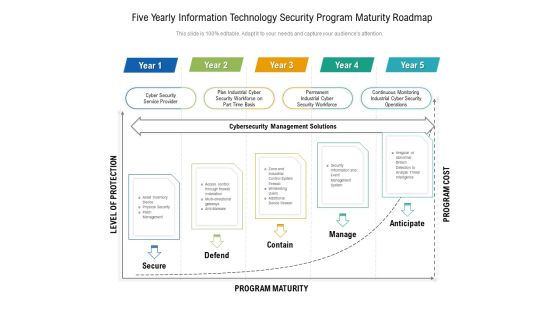
Five Yearly Information Technology Security Program Maturity Roadmap Information
Presenting the five yearly information technology security program maturity roadmap information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Quarterly Information Technology Security Roadmap For Continuous Threat Analysis Download
Presenting the quarterly information technology security roadmap for continuous threat analysis download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
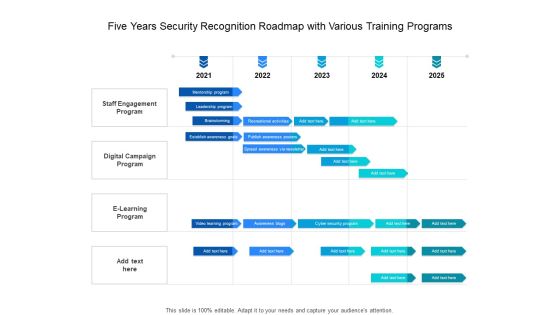
Five Years Security Recognition Roadmap With Various Training Programs Slides
Presenting the five years security recognition roadmap with various training programs slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
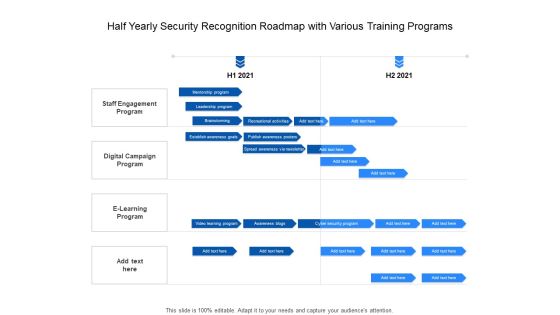
Half Yearly Security Recognition Roadmap With Various Training Programs Themes
Presenting the half yearly security recognition roadmap with various training programs themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
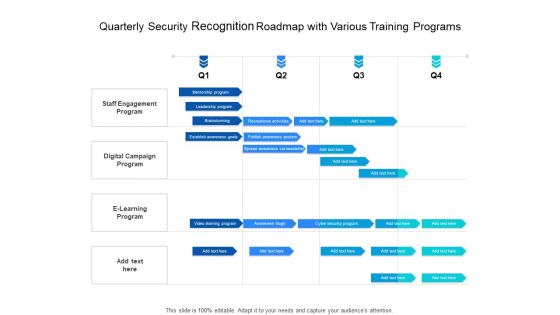
Quarterly Security Recognition Roadmap With Various Training Programs Download
Presenting the quarterly security recognition roadmap with various training programs download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Security Recognition Roadmap With Various Training Programs Summary
Presenting the six months security recognition roadmap with various training programs summary. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Security Recognition Roadmap With Various Training Programs Elements
Presenting the three months security recognition roadmap with various training programs elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
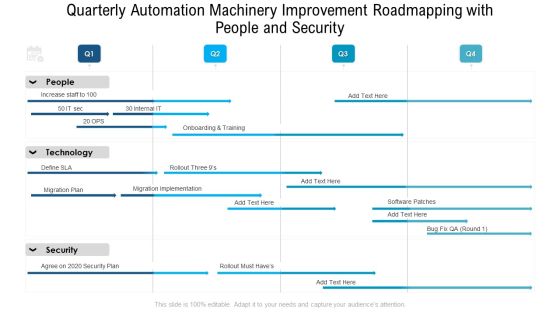
Quarterly Automation Machinery Improvement Roadmapping With People And Security Themes
Presenting our jaw dropping quarterly automation machinery improvement roadmapping with people and security themes. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Workforce Security Realization Coaching Plan Organization Compliance Metrics Introduction PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan organization compliance metrics introduction pdf. Use them to share invaluable insights on organization compliance metrics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Strategic Process Management Three Months Timeline Introduction
Presenting the cyber security strategic process management three months timeline introduction. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Effective Digital Security Six Months Strategic Timeline Information
Presenting the effective digital security six months strategic timeline information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Organizational Security Solutions Facilities Offered By Successful Implementation Clipart PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a organizational security solutions facilities offered by successful implementation clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Case Study 2 Banks Cyber Security Infrastructure Topics PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Presenting case study 2 banks cyber security infrastructure topics pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like implemented, integrated, our approach. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Functioning Centre Facilities Offered By Successful Implementation Infographics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting security functioning centre facilities offered by successful implementation infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like risk mitigation, investigations, employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
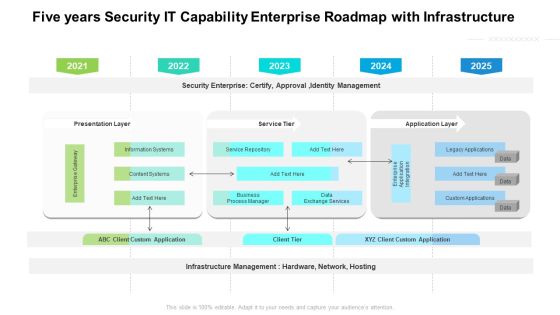
Five Years Security IT Capability Enterprise Roadmap With Infrastructure Guidelines
Presenting our jaw dropping five years security it capability enterprise roadmap with infrastructure guidelines. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Half Yearly Security IT Capability Enterprise Roadmap With Infrastructure Background
Presenting our jaw dropping half yearly security it capability enterprise roadmap with infrastructure background. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Six Months Security IT Capability Enterprise Roadmap With Infrastructure Icons
Presenting our jaw dropping six months security it capability enterprise roadmap with infrastructure icons. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Three Months Security IT Capability Enterprise Roadmap With Infrastructure Clipart
Presenting our jaw dropping three months security it capability enterprise roadmap with infrastructure clipart. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
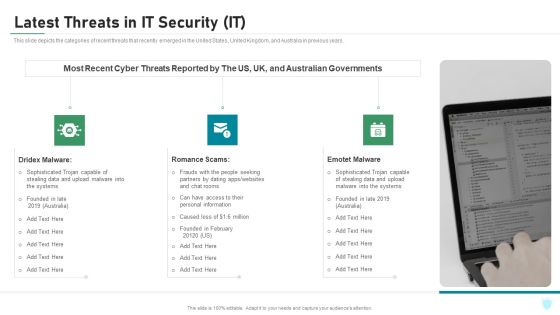
Latest Threats In IT Security IT Ppt Gallery Elements PDF
This slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Presenting latest threats in it security it ppt gallery elements pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dridex malware, romance scams, emotet malware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine New Roles Pivotal For Successful Devops Security Designs PDF
This slide provides information regarding the new roles considered as pivotal for successful DevOps in terms of DevOps evangelist, release manager, automation architect integration specialist. Presenting determine new roles pivotal for successful devops security designs pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like manager, management, coordination. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Year IT Upgradation Roadmap For Organizational Security Rules
Presenting the five year it upgradation roadmap for organizational security rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Financing Catalogue For Security Underwriting Agreement IPO Roadshow Topics PDF
The slide provides an overview of the IPO Roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc. This is a financing catalogue for security underwriting agreement ipo roadshow topics pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like merchant bankers, portfolio managers, financials institutions, foreign investors, insurance companies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Minimize Administrative And Staff Privileges Download PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. This is a desktop security management minimize administrative and staff privileges download pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimize administrative and staff privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Prepare A Disaster Recovery Plan Demonstration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a desktop security management prepare a disaster recovery plan demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, location, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Strategies To Manage Cyber Risks Rules PDF
This slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Presenting desktop security management strategies to manage cyber risks rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like strategic, risk, implementation, awareness, invest. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
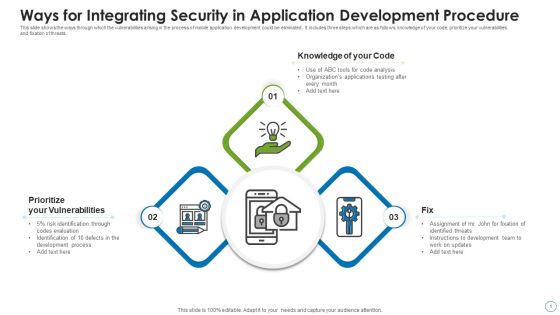
Ways For Integrating Security In Application Development Procedure Structure PDF
This slide shows the ways through which the vulnerabilities arising in the process of mobile application development could be eliminated. It includes three steps which are as follows knowledge of your code, prioritize your vulnerabilities and fixation of threats. Persuade your audience using this ways for integrating security in application development procedure structure pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including prioritize your vulnerabilities, knowledge of your code, fix. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Information And Event Management Logging Process Diagrams PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collect data from various sources, normalize and aggregate collected data, organization to investigate alerts. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF
This slide shows worksheet representing comparison of insurance premium of different firms for insured or customer to help in making decision . it includes various facilities provided by insurance firms. Showcasing this set of slides titled Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF. The topics addressed in these templates are Purchase Price, Insurance, Medical Payments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
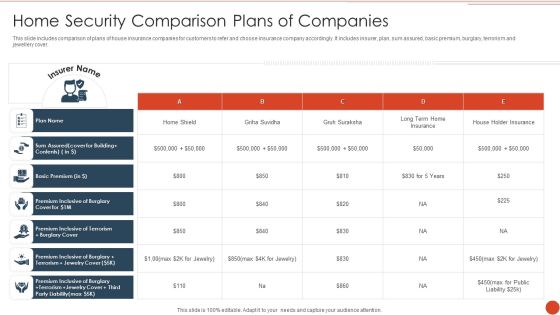
Home Security Comparison Plans Of Companies Formats PDF
This slide includes comparison of plans of house insurance companies for customers to refer and choose insurance company accordingly. It includes insurer, plan, sum assured, basic premium, burglary, terrorism and jewellery cover. Pitch your topic with ease and precision using this Home Security Comparison Plans Of Companies Formats PDF. This layout presents information on Basic Premium, Plan Name, House Holder Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
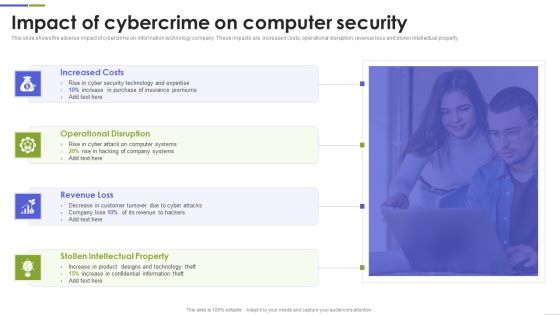
Impact Of Cybercrime On Computer Security Formats PDF
This slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Persuade your audience using this Impact Of Cybercrime On Computer Security Formats PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Increased Costs, Operational Disruption, Revenue Loss Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
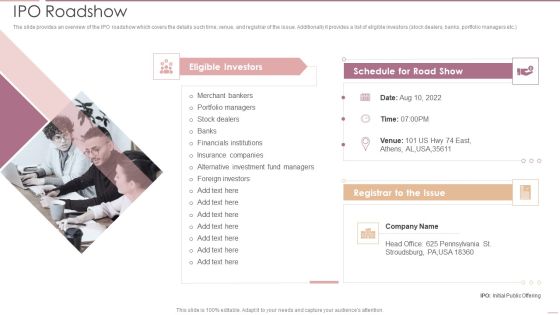
Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF
The slide provides an overview of the IPO roadshow which covers the details such time, venue, and registrar of the issue. Additionally it provides a list of eligible investors stock dealers, banks, portfolio managers etc.Presenting Investment Banking Security Underwriting Pitchbook IPO Roadshow Mockup PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Eligible Investors, Portfolio Managers, Alternative Investment In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
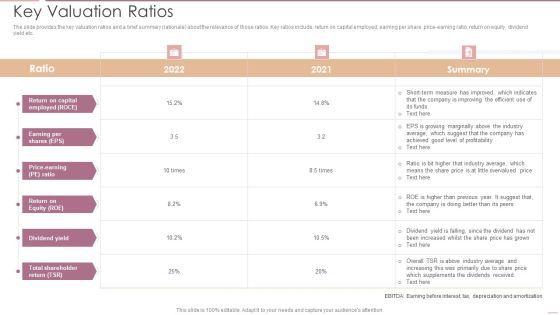
Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF
The slide provides the key valuation ratios and a brief summary rationale about the relevance of those ratios. Key ratios include return on capital employed, earning per share, price-earning ratio, return on equity, dividend yield etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF Use them to share invaluable insights on Measure Improved, Dividends Received, Total Shareholder and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Investment Banking Security Underwriting Pitchbook Post IPO Plan Microsoft PDF
The slide provides the post acquisition consolidated financials of acquiring company and acquired company. Key heading include, revenue, operating and selling, general, and administration expenses, operating income, and net income.Presenting Investment Banking Security Underwriting Pitchbook Post IPO Plan Microsoft PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Market Capitalization, Fund Allocation, Business Expansion In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. This is a Investment Banking Security Underwriting Pitchbook Share Allocation Process Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Case Undersubscription, Interested Investors, Normal Subscription You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF
The slide provides the key unique points product differentiation of the products comparing to its competitors. Key points include low product cost, large portfolio of assets under management, industry experience etc. Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Product Differentiation Comparing Clipart PDF. Use them to share invaluable insights on Under Management, Transaction Cost, Minimum Transaction and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF
This slide depicts what factors will be considered while preparing a disaster recovery planning of an organization to come back to business quickly and effectively.This is a IT Security Hacker Preparation Of Disaster Recovery Plan Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Natural Disasters, Physical Location, Assessment Report. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Security Management 4 Step Workflow Icons PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Persuade your audience using this Business Security Management 4 Step Workflow Icons PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate, Identify, Treat, Monitor. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Addressing Mobile Device Management Mobile Device Security Management Slides PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. Presenting Addressing Mobile Device Management Mobile Device Security Management Slides PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Corporate Owned, Personally Enabled, Equipment Personal. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Resolving Integrate IOT Security Challenges With Blockchain Platform Structure PDF
This slide covers various challenges and issues faced while using IoT applications. The purpose of this slide is to provide information about various challenges and proposed solutions. It includes challenges such as RPL routing attack, cost and capacity constraints, cloud server downtime along with description and blockchain solutions. Pitch your topic with ease and precision using this Resolving Integrate IOT Security Challenges With Blockchain Platform Structure PDF. This layout presents information on Iot Challenges, Blockchain Solutions, Cloud Server Downtime. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Phases Of Information IT Security Awareness Training Program Mockup PDF
This slide covers phases of information cybersecurity awareness training program. It involves four phases such as design, development, execution and continual improvement. Persuade your audience using this Phases Of Information IT Security Awareness Training Program Mockup PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Design, Development, Execution, Continual Improvement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF
The purpose of this slide is to showcase an example of social engineering attack. It also covers information about how the social engineering attack work and spread malware. Slidegeeks has constructed Organizing Security Awareness Outlook Of Social Engineering Attack Ideas PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Table of contents Information Security Risk Administration Sample PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Table of contents Information Security Risk Administration Sample PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Best Practices To Create Data Retention Security Mechanism Topics PDF
This slide showcases best practices of data retention policy. The practices covered are data classification, determine business needs, understand legal aspects and regular data backup.Presenting Best Practices To Create Data Retention Security Mechanism Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Understand Legal Aspect, Determine Business Needs, Regular Data Backup . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Data Backup Security Mechanism For Business Leaders Infographics PDF
This slide showcases organization data backup policy that includes data type, backup frequency, onsite, offsite retention and comments. The data covered is related to server operating system, workforce records and ERP system database.Showcasing this set of slides titled Data Backup Security Mechanism For Business Leaders Infographics PDF. The topics addressed in these templates are Operating Systems, Workforce Records, Employee Home Directories. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Steps Included In Data Retention Security Mechanism Introduction PDF
This slide depicts the steps covered in data retention policy. The steps included are determine applicable regulations, catalogue data, decision making, policy documentation and implementation.Persuade your audience using this Steps Included In Data Retention Security Mechanism Introduction PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Catalogue Data, Decision Making, Document Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Competitor Analysis Grid Of Security Software Inspiration PDF
This slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Pitch your topic with ease and precision using this Competitor Analysis Grid Of Security Software Inspiration PDF. This layout presents information on System Cleansing, Everyday Backup Option, Anti Spyware. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Information Security Lawfulness Fairness And Transparency Principle Slides PDF
This slide shows the lawfulness, fairness, and transparency concept, which establishes explanations for data processing and includes six legitimate basis for personal data. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Security Lawfulness Fairness And Transparency Principle Slides PDF from Slidegeeks and deliver a wonderful presentation.

Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Slidegeeks has constructed Information Security Purpose Limitation Principle Of GDPR Law Graphics PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Information Systems Security And Risk Management Plan Roadmap Clipart PDF
Present like a pro with Information Systems Security And Risk Management Plan Roadmap Clipart PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information Systems Security And Risk Management Plan Timeline Professional PDF
Slidegeeks has constructed Information Systems Security And Risk Management Plan Timeline Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

IT Security Risk Management Plan Implementation Stages Summary PDF
This slide explains various steps for implementation of cybersecurity risk management plan in the organization to ensure time and budget compliance. It includes elements such as current state analysis, assessment, target state, etc. Presenting IT Security Risk Management Plan Implementation Stages Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Current State Analysis, Assessment, Target State, Roadmap. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Major Statistics Of Cyber Security Awareness Ppt Professional Deck PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Major Statistics Of Cyber Security Awareness Ppt Professional Deck PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

SDN Security Architecture Ppt PowerPoint Presentation Complete Deck With Slides
This is a professional and ready to use PowerPoint deck for entrepreneurs, who want to showcase their business in the best light possible. Use this SDN Security Architecture Ppt PowerPoint Presentation Complete Deck With Slides and prepare an engaging pitch to showcase potential in the industry of your choice. Whether you are just starting out or business or planning to scale, deploy this ffity nine slide complete deck to demonstrate your ideas for bringing innovation and creativity in the business. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF
This slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Take your projects to the next level with our ultimate collection of SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Security Software Company Investor Funding Elevator Pitch Deck Complete Deck
In this Security Software Company Investor Funding Elevator Pitch Deck Complete Deck, we detail the way one can plan on timelines innovation and making the best of resources. We also present to you the importance of documenting every major strategic move. In this thirty eight slide presentation template, we also include umbrella concepts to make sure your authority as a handsome business person is enhanced. As always, the editable and customizable benefit is also provided making you emerge as the business Guru. Download now to establish your superiority in both running a business, and being confident enough to present about it.

 Home
Home