Security
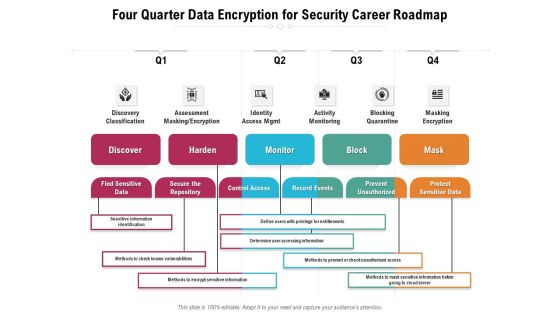
Four Quarter Data Encryption For Security Career Roadmap Sample
We present our four quarter data encryption for security career roadmap sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched four quarter data encryption for security career roadmap sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
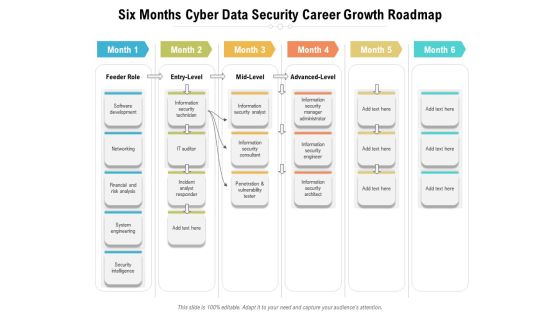
Six Months Cyber Data Security Career Growth Roadmap Diagrams
We present our six months cyber data security career growth roadmap diagrams. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months cyber data security career growth roadmap diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Three Months Cyber Data Security Career Growth Roadmap Diagrams
We present our three months cyber data security career growth roadmap diagrams. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched three months cyber data security career growth roadmap diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Year Organization Product Development Roadmap With Advanced Security Sample
We present our five year organization product development roadmap with advanced security sample. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five year organization product development roadmap with advanced security sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Workforce Five Years Work Roadmap Operations And Security Pictures
We present our workforce five years work roadmap operations and security pictures. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched workforce five years work roadmap operations and security pictures in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Years Engineering Roadmap With Security And Compliance Clipart
We present our five years engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five years engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
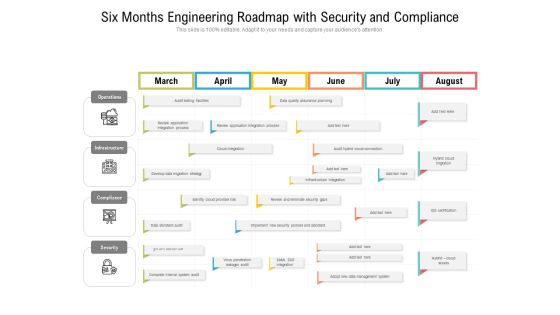
Six Months Engineering Roadmap With Security And Compliance Clipart
We present our six months engineering roadmap with security and compliance clipart. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months engineering roadmap with security and compliance clipart in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Crisis Program Presentation Risk Management Action Plan Security Inspiration PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Deliver an awe-inspiring pitch with this creative crisis program presentation risk management action plan security inspiration pdf bundle. Topics like potential risk, communication, confidential information security, required resources, data backup team plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Security Five Years Roadmap With Deployment Plan Designs
We present our cloud computing security five years roadmap with deployment plan designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security five years roadmap with deployment plan designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Five Year Information Technology Security Analytics Improvement Roadmap Infographics
We present our five year information technology security analytics improvement roadmap infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched five year information technology security analytics improvement roadmap infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Enterprise Information Technology Security Roadmap Through Identification Summary
We present our half yearly enterprise information technology security roadmap through identification summary. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly enterprise information technology security roadmap through identification summary in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Quarterly Enterprise Information Technology Security Roadmap Through Identification Topics
We present our quarterly enterprise information technology security roadmap through identification topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly enterprise information technology security roadmap through identification topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Enterprise Information Technology Security Roadmap Through Identification Infographics
We present our six months enterprise information technology security roadmap through identification infographics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise information technology security roadmap through identification infographics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Three Months Enterprise Information Technology Security Roadmap Through Identification Introduction
We present our three months enterprise information technology security roadmap through identification introduction. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched three months enterprise information technology security roadmap through identification introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
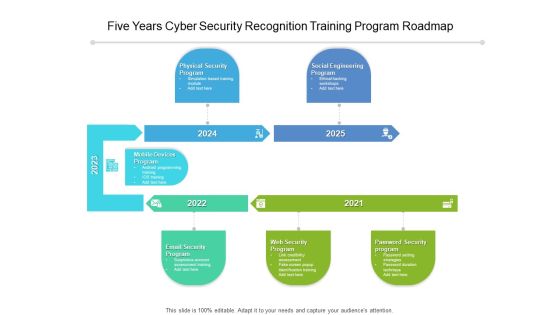
Five Years Cyber Security Recognition Training Program Roadmap Diagrams
We present our five years cyber security recognition training program roadmap diagrams. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched five years cyber security recognition training program roadmap diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Cyber Security Recognition Training Program Roadmap Elements
We present our half yearly cyber security recognition training program roadmap elements. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched half yearly cyber security recognition training program roadmap elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Six Months Cyber Security Recognition Training Program Roadmap Introduction
We present our six months cyber security recognition training program roadmap introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months cyber security recognition training program roadmap introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Three Months Cyber Security Recognition Training Program Roadmap Icons
We present our three months cyber security recognition training program roadmap icons. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched three months cyber security recognition training program roadmap icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
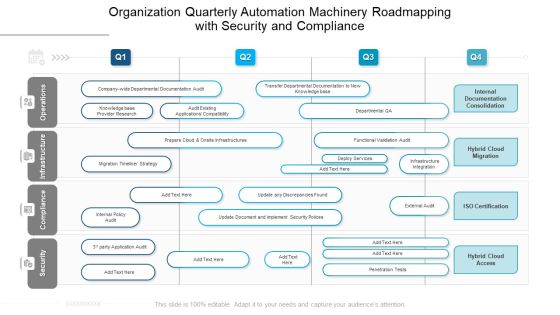
Organization Quarterly Automation Machinery Roadmapping With Security And Compliance Brochure
We present our organization quarterly automation machinery roadmapping with security and compliance brochure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched organization quarterly automation machinery roadmapping with security and compliance brochure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Automated Security Awareness Platform And Cost Graphics PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks.Presenting automated security awareness platform and cost graphics pdf. to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like automated learning management, actionable reporting, available anytime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Effect After Implementing Cyber Risk Security Awareness Program Professional PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments.This is a effect after implementing cyber risk security awareness program professional pdf. template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like lowest mobile malware infections, lowest computer malware infections. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Strategic Process Management Four Quarter Timeline Diagrams
We present our cyber security strategic process management four quarter timeline diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security strategic process management four quarter timeline diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
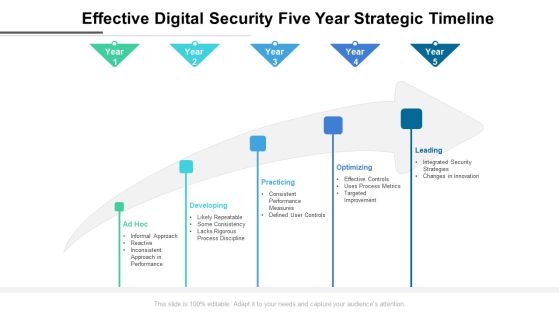
Effective Digital Security Five Year Strategic Timeline Formats
We present our effective digital security five year strategic timeline formats. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched effective digital security five year strategic timeline formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Organizational Security Solutions Analyzing Different SOC Deployment Models Themes PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a organizational security solutions analyzing different soc deployment models themes pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Security Solutions Prerequisites For Effective Secops Implementation Summary PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a organizational security solutions prerequisites for effective secops implementation summary pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Prerequisites For Effective Secops Implementation Professional PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a security functioning centre prerequisites for effective secops implementation professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development team, operations team, performing, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Months Action Plan Advantage Roadmap For Cyber Security Inspiration
We present our 3 months action plan advantage roadmap for cyber security inspiration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 3 months action plan advantage roadmap for cyber security inspiration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

6 Months Action Plan Advantage Roadmap For Cyber Security Diagrams
We present our 6 months action plan advantage roadmap for cyber security diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 6 months action plan advantage roadmap for cyber security diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Action Plan Advantage Roadmap For Cyber Security Themes
We present our half yearly action plan advantage roadmap for cyber security themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly action plan advantage roadmap for cyber security themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
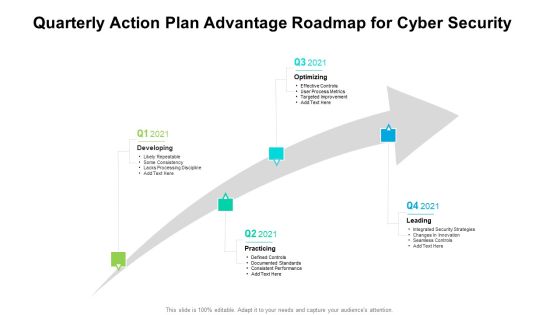
Quarterly Action Plan Advantage Roadmap For Cyber Security Sample
We present our quarterly action plan advantage roadmap for cyber security sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly action plan advantage roadmap for cyber security sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Internet Security Threat Analysis Process By Backdoor Graphics PDF
This slide exhibits data and security breach attack process conducted by hackers to get access to company data. It includes multiple activities such as link forwarding by emails, data sharing and attacking and so on. Showcasing this set of slides titled internet security threat analysis process by backdoor graphics pdf. The topics addressed in these templates are exfiltrate, stage attack, research. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
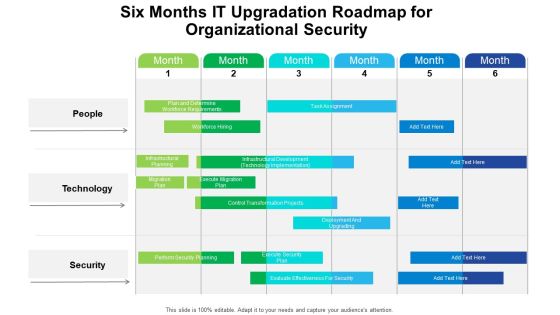
Six Months IT Upgradation Roadmap For Organizational Security Structure
We present our six months it upgradation roadmap for organizational security structure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months it upgradation roadmap for organizational security structure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Information And Event Management Logging Process Structure PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a security information and event management logging process structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Management System Auditing Methodology Download PDF
The following slide highlights the information security system audit framework illustrating key headings which includes act, plan, do and check which are used for update and improve isms, establish isms, implement policy and control and monitor and review performance Presenting Information Security Management System Auditing Methodology Download PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Analysis, Data, Risk. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Security Management System Auditing Process Microsoft PDF
The following slide highlights the information security management system audit methodology illustrating key headings which includes steps and activities, where steps consists of document review, audit review, plan audit, perform audit and reporting Showcasing this set of slides titled Information Security Management System Auditing Process Microsoft PDF. The topics addressed in these templates are Plan Audit, Reporting, Audit Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Smart Home Security Solutions Company Profile Customer Testimonials Formats PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Smart Home Security Solutions Company Profile Customer Testimonials Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Testimonials. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Program To Measure Likelihood Of Impact Topics PDF
This slide represents the information security program to measure likelihood of impact which includes effects, system operationality that will help company to categorize risk level and develop risk mitigation strategies.Pitch your topic with ease and precision using this IT Security Program To Measure Likelihood Of Impact Topics PDF This layout presents information on System Operationality, Uncontrollable Situations, Confidentiality It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Steps To Develop Strategic IT Security Program Structure PDF
This slide shows the steps to develop strategic security program which covers program assessment, organizational culture, emerging threats, measuring outcome, continual learning and development, etc.Persuade your audience using this Steps To Develop Strategic IT Security Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Program Assessment, Emerging Threats, Organizational Culture Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Computer Security Dashboard With Incident And Threat Management Rules PDF
This slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc.Showcasing this set of slides titled Computer Security Dashboard With Incident And Threat Management Rules PDF The topics addressed in these templates are Critical Incidents, Risks Identified, Compliance All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Various Kpis To Measure Computer Security System Portrait PDF
This slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Persuade your audience using this Various Kpis To Measure Computer Security System Portrait PDF This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Performance Indicators, Excepted Results, Actual Results Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

How To Manage Security In Cloud Background PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting How To Manage Security In Cloud Background PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Firewalls, Access Controls, Data Recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

What Are The Downsides Of A Cloud Security Download PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting What Are The Downsides Of A Cloud Security Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats End User Control Themes PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Security Threats End User Control Themes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Centralized Data, Customer, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certified Information Systems Security Professional CISSP Examination Details Designs PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. This is a Certified Information Systems Security Professional CISSP Examination Details Designs PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Requirements, Risk Management, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Business Development Strategy Icons PDF
This slide highlights the security company channel expansion strategy which showcases strategies for retail, multifamily and professional channels including instore lead generation and robust product offerings.Presenting Security And Surveillance Company Profile Business Development Strategy Icons PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Professional Channels, National Operations, Remove Insurance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Camera System Company Profile Customer Testimonials Summary PDF
This slide highlights the security company customer testimonials which showcases that ABC Inc. is value for money product, now people are confident that there home and valuables are safe. This is a Security Camera System Company Profile Customer Testimonials Summary PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Testimonials. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile SWOT Analysis Infographics PDF
This slide highlights the security company SWOT analysis which includes one high quality products as strengths, 1 year subscription as weakness, high industry growth as opportunity and competitive market as threats. This is a Security Camera System Company Profile SWOT Analysis Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strengths, Weaknesses, Opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
IT Security Hacker Dashboard For Threat Tracking Rules PDF
This slide depicts the dashboard for threat tracking through cyber security measures and ethical hackers by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report.Deliver an awe inspiring pitch with this creative IT Security Hacker Dashboard For Threat Tracking Rules PDF bundle. Topics like Threat Dashboard, Loss Of Information, Regulations And Contracts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF
The purpose of this slide is to highlight the security gap analysis of the organization. Information covered in this slide is related to current vs desired state of the company, reasons identified, techniques to be used and the priority level.Deliver an awe inspiring pitch with this creative Conducting Cyber Security Gap Analysis Of Organization Contd Formats PDF bundle. Topics like Facing Ransomware, Reasons Identified, Organization Malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Impact Of Cyber Security Breach General Consequences Ideas PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. This is a Impact Of Cyber Security Breach General Consequences Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reputational Damage, Monetary Penalty, Operational Disruption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Benefits Of Cyber Security Awareness Training Background PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide.This is a Key Benefits Of Cyber Security Awareness Training Background PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Drive Awareness, Reduce Threat, Amongst Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
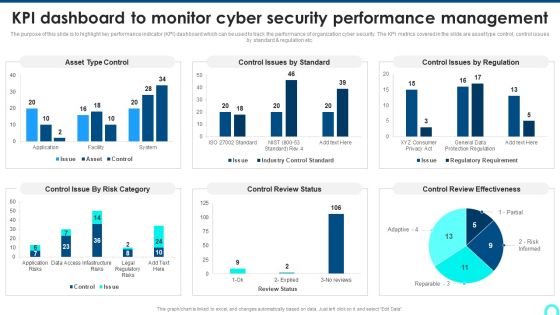
KPI Dashboard To Monitor Cyber Security Performance Management Background PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc.Deliver and pitch your topic in the best possible manner with this KPI Dashboard To Monitor Cyber Security Performance Management Background PDF. Use them to share invaluable insights on Control Issue, Control Review, Review Effectiveness and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
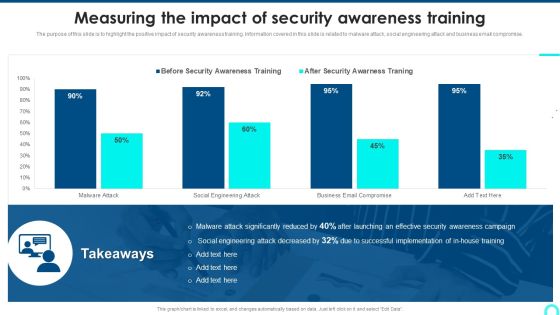
Measuring The Impact Of Security Awareness Training Structure PDF
The purpose of this slide is to highlight the positive impact of security awareness training. Information covered in this slide is related to malware attack, social engineering attack and business email compromise. Deliver and pitch your topic in the best possible manner with this Measuring The Impact Of Security Awareness Training Structure PDF. Use them to share invaluable insights on Attack Significantly, Awareness Campaign, Social Engineering and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Overview Of Cyber Security Awareness Course Clipart PDF
The purpose of this slide is to provide a glimpse of the selected cyber security awareness course. It covers information about the instructor details, course content, attendees and learning outcome. This is a Overview Of Cyber Security Awareness Course Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Learning Outcome, Attendees, Course Content. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Components Of People Centric Work Culture Security Ideas PDF
The following slide highlights the key elements of people centric security to prevent data breaches and IT damages. It includes activities such as personalized training, artificial intelligence AI and machine learning ML tools and prompt social engineering attacks etc. Persuade your audience using this Key Components Of People Centric Work Culture Security Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Personalized Training, Artificial Intelligence, Engineering Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Agency Business Profile Case Study Elements PDF
This slide highlights the case study of security guard company which includes key problems robberies and theft, with integrated solution and key benefits. Presenting Security Agency Business Profile Case Study Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like The Problem, Solution, Benefits. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Agency Business Profile Executive Summary Graphics PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures. This is a Security Agency Business Profile Executive Summary Graphics PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Total Revenue, Employees, Customers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Our Business Approach Diagrams PDF
This slide highlights the business approach of security company which includes strategic planning, human resource management, participatory management and productivity management. This is a Security Agency Business Profile Our Business Approach Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Planning, Participatory Management, Productivity Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Practices To Implement Digitization Of Security Systems Icons PDF
The following slide highlights best practices which can be implemented by firm for digitization of security systems. The major practices are prioritize automation, start with manual playbooks, adopt automation gradually and invest in the training of IT team. Presenting Key Practices To Implement Digitization Of Security Systems Icons PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Prioritize Automation, Start Manual Playbooks, Adopt Automation Gradually. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organization Security Issues And Solution Assessment Ideas PDF
This slide showcases problems in firm related to security of crucial data important for organization. The issues include data breach, SPAM, phishing and insider threat. Persuade your audience using this Organization Security Issues And Solution Assessment Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Data Breach, SPAM And Phishing, Insider Threat. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home