Security

Promotion Standard Practices Tools And Templates 7 Cs Compass Model With Cardinal Directions Professional PDF
This slide shows 7 C compass model along with cardinal directions. The slide also includes compass of consumers where the directions represents needs, education, security and wants. This is a promotion standard practices tools and templates 7 cs compass model with cardinal directions professional pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like communication, commodity, channel You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Merger And Acquisition Due Diligence Checklist IT Landscape Evaluation Designs PDF
Following slide illustrates IT landscape evaluation of target company. Points covered in evaluation are proprietary technology, data and analytics, security and compliance, infrastructure, organization and process, business systems Presenting merger and acquisition due diligence checklist it landscape evaluation designs pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like key financial highlights In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Lake Architecture Critical Challenges Related To Data Lake Slides PDF
This slide depicts the challenges of data lakes such as high cost, managed difficulty, long time-to-value, immature data security And governance, and lack of skills. Deliver and pitch your topic in the best possible manner with this Data Lake Architecture Critical Challenges Related To Data Lake Slides PDF. Use them to share invaluable insights on High Cost, Management Difficulty, Long Time To Value, Lack Skills and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Lake Architecture How To Decide If You Need A Data Lake Information PDF
This slide depicts the key pointers to help to understand organizations if they need to maintain a data lake for critical business information and perform analytics on that data. Deliver an awe inspiring pitch with this creative Data Lake Architecture How To Decide If You Need A Data Lake Information PDF bundle. Topics like Make Data Administration Easier, Accelerate Analytics, Enhance Security And Governance, Businesses Depend can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
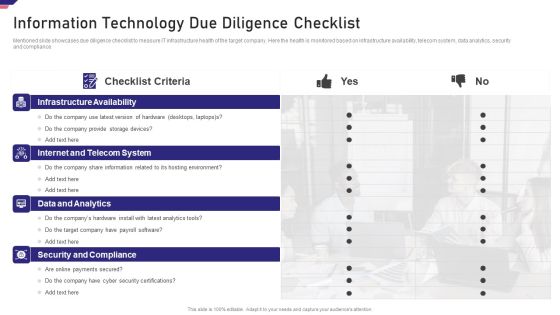
Mergers Acquisition Playbook Mergers Acquisition Playbook Information Technology Due Ideas PDF
Mentioned slide showcases due diligence checklist to measure IT infrastructure health of the target company. Here the health is monitored based on infrastructure availability, telecom system, data analytics, security and compliance.This is a Mergers Acquisition Playbook Mergers Acquisition Playbook Information Technology Due Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Infrastructure Availability, Internet And Telecom System, Data And Analytics You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
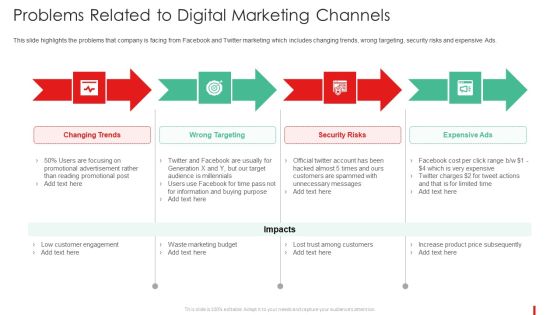
Promotion Guide To Advertise Brand On Youtube Problems Related To Digital Marketing Channels Sample PDF
This slide highlights the problems that company is facing from Facebook and Twitter marketing which includes changing trends, wrong targeting, security risks and expensive Ads.This is a Promotion Guide To Advertise Brand On Youtube Problems Related To Digital Marketing Channels Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Promotional Advertisement, Reading Promotional, Increase Product You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Convergence Strategy Information IT OT Roles And Competencies Ppt Guide PDF
In this slide we have Listed a variety of IT or OT integration competencies that suited certain types of roles. This is a Convergence Strategy Information IT OT Roles And Competencies Ppt Guide PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like IT Roles, OT Competencies, Developer, Technical Applications Architect, Information Security Officer. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF
This slide covers IT or OT cyber security strategy and approaches such as raining of an internal employee in cybersecurity, from the OT side, to keep the near job relation to OT Teams etc. This is a Convergence Strategy Information Launch Of Cyber IT OT Strategy Ppt Summary Portrait PDF template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Audit Demanded, Enable Collaboration, Industrialize Process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Current Potential Implications Faced By Firm Intelligent Infrastructure Rules PDF
This slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an awe inspiring pitch with this creative Current Potential Implications Faced By Firm Intelligent Infrastructure Rules PDF bundle. Topics like Issues Related To Employees, Reported Financial Losses, Due To Increase Security Threats, Data Breaches And can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ukraine Vs Russia Examining War Timeline Highlighting Major Events Occurred Cont Sample PDF
This slide provides information regarding Russia Ukraine war timeline highlighting major events occurred in FY2022 and FY2021 in terms of initiation of military training by Russian soldiers, security assistance to Ukraine by US, etc. . Deliver an awe inspiring pitch with this creative Ukraine Vs Russia Examining War Timeline Highlighting Major Events Occurred Cont Sample PDF bundle. Topics like US Tracked Unusual Russian, Russia Initiated Military Maneuvers, Controlled Crimea editable template. It is available for immediate download depending on the needs and requirements of the user.
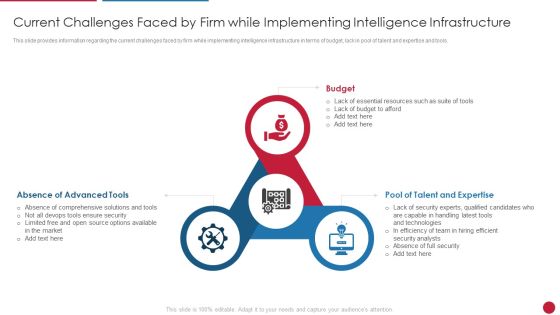
Facilitating IT Intelligence Architecture Current Challenges Faced By Firm While Implementing Graphics PDF
This slide provides information regarding the current challenges faced by firm while implementing intelligence infrastructure in terms of budget, lack in pool of talent and expertise and tools. This is a Facilitating IT Intelligence Architecture Current Challenges Faced By Firm While Implementing Graphics PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Absence Of Advanced Tools, Pool Of Talent And Expertise, Efficient Security Analysts You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
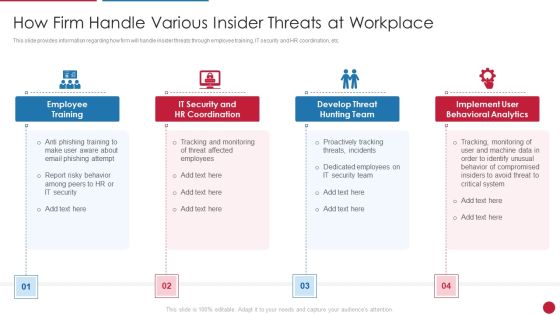
Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a Facilitating IT Intelligence Architecture How Firm Handle Various Insider Threats At Workplace Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training, Develop Threat Hunting Team, Implement User Behavioral Analytics You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
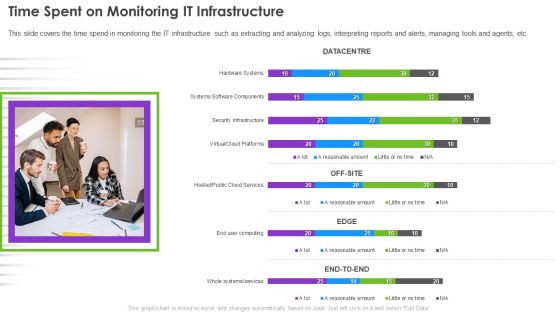
Infrastructure Supervision Time Spent On Monitoring IT Infrastructure Demonstration PDF
This slide covers the time spend in monitoring the IT infrastructure such as extracting and analyzing logs, interpreting reports and alerts, managing tools and agents, etc. Deliver and pitch your topic in the best possible manner with this Infrastructure Supervision Time Spent On Monitoring IT Infrastructure Demonstration PDF. Use them to share invaluable insights on Virtual, Cloud Platforms, Security Infrastructure, Systems Software Components, Hardware Systems and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF
This slide exhibits risk rating breakdown and heat map for analyzing current cyber security measures effectiveness. It covers top 5 vulnerabilities and clients under scrutiny. Pitch your topic with ease and precision using this Cyber Intelligence Risk Assessment Dashboard With Heat Map Portrait PDF This layout presents information on Risk Rating Breakdown, Action Plan Breakdown, Risk Possibility It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
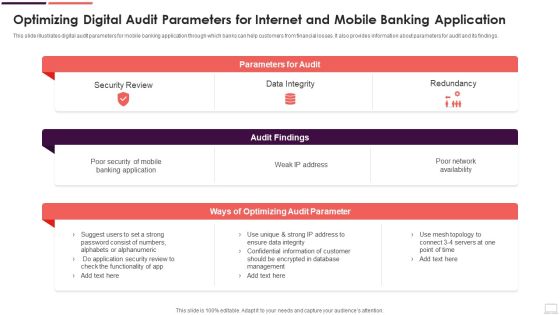
Optimizing Digital Audit Parameters For Internet And Mobile Banking Application Designs PDF
This slide illustrates digital audit parameters for mobile banking application through which banks can help customers from financial losses. It also provides information about parameters for audit and its findings. Pitch your topic with ease and precision using this Optimizing Digital Audit Parameters For Internet And Mobile Banking Application Designs PDF. This layout presents information on Security Review, Data Integrity, Redundancy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Strengths Weaknesses Opportunities And Threats Analysis Of Electronic Gadgets Business Microsoft PDF
This slide covers the SWOT analysis of the electronics computer systems business which will be needed to know how the competitors are growing and what are the opportunities that we could grab to make our business grow.Presenting Strengths Weaknesses Opportunities And Threats Analysis Of Electronic Gadgets Business Microsoft PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Standards, High Investment, Organization Culture This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF
This slide illustrates the incidents of the transition project. It covers the details such as explanation, status, priority, and resolution of the incident to ensure that technological change is successfully completed in the organization. Deliver and pitch your topic in the best possible manner with this Incident Management Chart Change Execution Plan Ppt PowerPoint Presentation Icon Diagrams PDF. Use them to share invaluable insights on Incident Status Priority, Cyber Attack Sensitive, Added Data Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

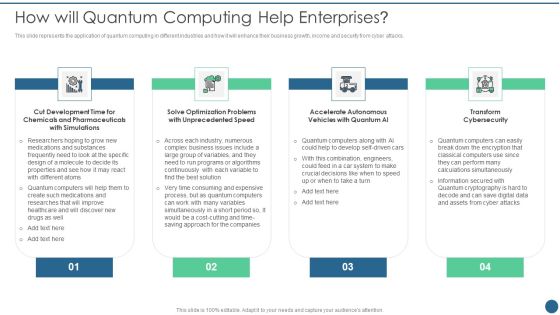
How Will Quantum Computing Help Enterprises Ppt Gallery Ideas PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. This is a How Will Quantum Computing Help Enterprises Ppt Gallery Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Development Time, Optimization Problems, Transform Cybersecurity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
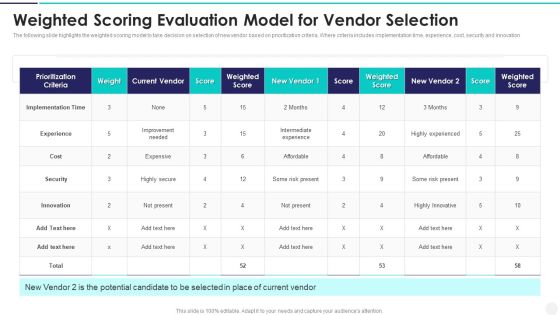
Weighted Scoring Evaluation Model For Vendor Selection Themes PDF
The following slide highlights the weighted scoring model to take decision on selection of new vendor based on prioritization criteria. Where criteria includes implementation time, experience, cost, security and innovation Pitch your topic with ease and precision using this Weighted Scoring Evaluation Model For Vendor Selection Themes PDF This layout presents information on Improvement Needed, Intermediate Experience, Highly Experienced It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Developing Business Analytics Framework Determine Overview Of Established Themes PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Developing Business Analytics Framework Determine Overview Of Established Themes PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Command And Control, Incident Response, Threat Intelligence You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Business Analytics Framework How Firm Handle Various Insider Threats At Workplace Infographics PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a Developing Business Analytics Framework How Firm Handle Various Insider Threats At Workplace Infographics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Employee Training, Behavioral Analytics, Threat Hunting You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
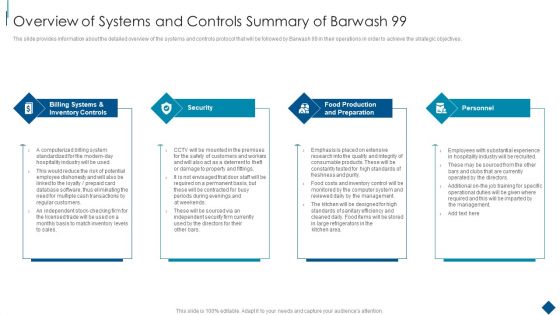
Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Billing Systems Inventory, Controls Security Personnel, Food Production Preparation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cios Value Optimization Addressing Critical IT Budgeting Measures Checklist Formats PDF
This slide provides information regarding critical IT budgeting measures checklist comprising of categorizing IT expenses, focus on IT security and disaster recovery risks, budget planning for work from home scenario, tax calculation, etc. Presenting Cios Value Optimization Addressing Critical IT Budgeting Measures Checklist Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like IT Infrastructure, Project Expenses, Tax Calculation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cios Value Optimization Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Guidelines PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. Deliver an awe inspiring pitch with this creative Cios Value Optimization Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Guidelines PDF bundle. Topics like Overall Reduction, Operational Expenses, Reduction IT can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
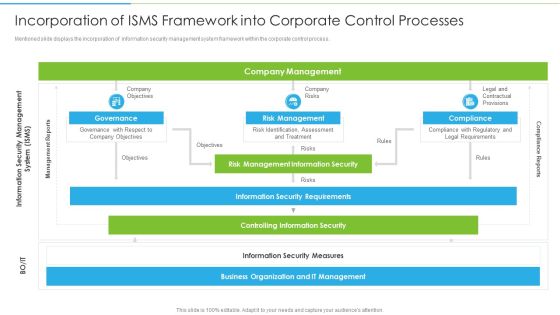
Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process. This is a Ways To Accomplish ISO 27001 Accreditation Incorporation Of ISMS Framework Into Corporate Microsoft PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Company Objectives, Company Management, Company Risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Ways To Accomplish ISO 27001 Accreditation Mitigation Plan To Resolve Encountered Icons PDF
Mentioned slide portrays mitigation plan to resolve the encountered risk events. It includes information of risk encountered, its description, threat level, mitigation plan, resources required, responsibility, resolution time and communication channel. Deliver and pitch your topic in the best possible manner with this Ways To Accomplish ISO 27001 Accreditation Mitigation Plan To Resolve Encountered Icons PDF. Use them to share invaluable insights on Security Breach, System Failure, Mitigation Plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Risk Associated With Team Working Environment In Workplace Ppt Icon Examples PDF
This slide represents risk associated with collaborative working environment in workplace. It covers risk such as wasting time, poor project management poor strategy execution, negative impact n employee morale and security risk. Pitch your topic with ease and precision using this Risk Associated With Team Working Environment In Workplace Ppt Icon Examples PDF. This layout presents information on Risk, Strategy Execution, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Financial Report Of An IT Firm Major Risk Factors For The Company Demonstration PDF
This slide provides key risk factors that might affect companys operational and financials performance. Key factors covered in the slide are growing competition, cyberattacks, economic risks, issues in the use of AI etc.This is a Financial Report Of An IT Firm Major Risk Factors For The Company Demonstration PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Growing Competition, Government Litigation, Cyberattacks Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Credit Management And Recovery Policies Detailed Analysis Of Debt Collection Process Sample PDF
Purpose of the following slide is to display the detailed analysis of the debt collection process as it highlights the key steps in the process, these steps can be detailed analysis of case, establishing contact with client, Assessing the case, security adjustment. Presenting Credit Management And Recovery Policies Detailed Analysis Of Debt Collection Process Sample PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Detailed Analysis, Establishing Contact, Assessing Case. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Playbook For Managing Information Additional Roles Pivotal For Successful Infrastructure Topics PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect or integration specialist, software tester or developer and security engineer. Presenting Playbook For Managing Information Additional Roles Pivotal For Successful Infrastructure Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Release Manager, Automation Architect, Software Tester. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks. Presenting How Will Quantum Computing Help Enterprises Ppt Icon Deck PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Transform Cybersecurity, Complex Business, Accelerate Autonomous Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agile Approach To Digital Transformation IT Impact Of Successful Transformation Of Digital Agile System Professional PDF
This slide provides information regarding the impact of successful transformation of Digital Agile system by addressing various KPIs such as mean lead time to changes, change failure rate, security test pass rate, etc. Deliver an awe inspiring pitch with this creative Agile Approach To Digital Transformation IT Impact Of Successful Transformation Of Digital Agile System Professional PDF bundle. Topics like Overall Project, Cost Reduced, Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Robotic Process Automated Roles Introduction PDF
This slide depicts the roles and responsibilities of the staff in robotic process automation. The roles include solution architecture, project manager, business analyst, process owner and RPA support. This is a Robotic Process Automated Roles Introduction PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Process Owner, IT Security Admin, Business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Due Diligence In Amalgamation And Acquisition IT Landscape Evaluation Infographics PDF
Following slide illustrates IT landscape evaluation of target company. Points covered in evaluation are proprietary technology, data and analytics, security and compliance, infrastructure, organization and process, business systems. This is a Due Diligence In Amalgamation And Acquisition IT Landscape Evaluation Infographics PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Systems, Proprietary Technology, Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
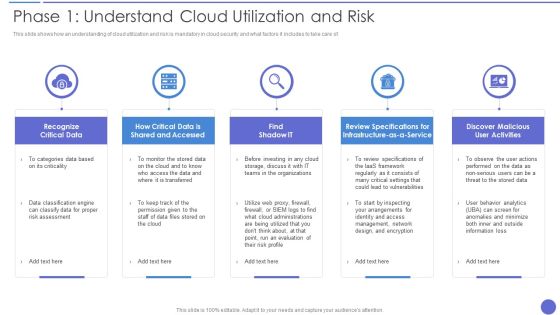
Phase 1 Understand Cloud Utilization And Risk Topics PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. This is a Phase 1 Understand Cloud Utilization And Risk Topics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Recognize Critical Data, Risk Assessment, Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF
This slide represents the application of quantum computing in different industries and how it will enhance their business growth, income and security from cyber attacks.This is a Quantum Key Distribution How Will Quantum Computing Help Enterprises Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Optimization Problems, Accelerate Autonomous, Vehicles Quantum You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain And DLT Framework Public Blockchain Technology Clipart PDF
This slide depicts the public blockchain technology framework and how data is stored in the public blockchain, bitcoin, voting are few examples of the public blockchain. Presenting Blockchain And DLT Framework Public Blockchain Technology Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Public Blockchain, Security Protocols Sincerely, Litecoin Blockchains. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
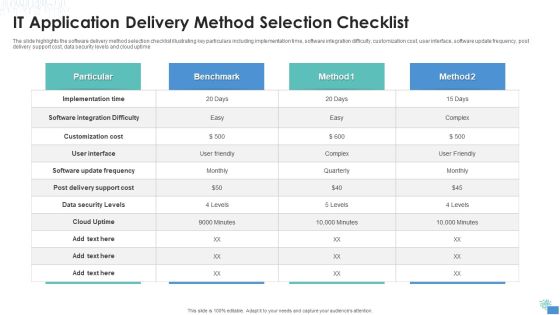
IT Application Delivery Method Selection Checklist Themes PDF
The slide highlights the software delivery method selection checklist illustrating key particulars including implementation time, software integration difficulty, customization cost, user interface, software update frequency, post delivery support cost, data security levels and cloud uptime.Pitch your topic with ease and precision using this IT Application Delivery Method Selection Checklist Themes PDF This layout presents information on Implementation Time, Customization Cost, Software Integration It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Top Recruitment Consulting Employers For Multiple Job Position Ideas PDF
The Following slide highlights the top recruitment consulting employers for multiple job positions illustrating job positions which includes business consultant, sales executive, financial consultant, software security manager, research consultant and scm managers.Showcasing this set of slides titled Top Recruitment Consulting Employers For Multiple Job Position Ideas PDF The topics addressed in these templates are Business Consultant, Financial Consultant, Research Consultant All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Technology Disaster Resilience Plan Cloud-Based Disaster Recovery Plan Summary PDF
This slide represents the cloud based disaster recovery plan and the various factors such as bandwidth, cloud storage, and security under consideration before implementing DR.This is a Information Technology Disaster Resilience Plan Cloud Based Disaster Recovery Plan Summary PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Implementing Disaster, Regulatory Compliance, Factors Bandwidth. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CRM Implementation Strategy CRM Training Program For Employees Infographics PDF
This slide highlights the CRM training Program for employees which includes overview training, lead management session, customization and data security session.This is a CRM Implementation Strategy CRM Training Program For Employees Infographics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Session, Customization Session, Overview Training You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Migration Project Process With Estimated Time And Cost Demonstration PDF
This slow showcases process that can help organization to formulate the migration project design and perform data security checks. Its key steps are planning, data preparation, migration design, testing and go live. Pitch your topic with ease and precision using this Data Migration Project Process With Estimated Time And Cost Demonstration PDF. This layout presents information on Planning, Data Preparation, Migration Design. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Data Lake Architecture Future Of Data Analysis Risks Associated With Data Lake Usage Rules PDF
This slide depicts the risks of using data lake such as the higher risk involved in data lake construction, storage and computing expenses, complex tools, and so on.This is a Data Lake Architecture Future Of Data Analysis Risks Associated With Data Lake Usage Rules PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Regulatory Implications, Security And Access, Enterprise Collaboration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

VID Managing End User Computing In The Company Infographics PDF
This slide represents how we will manage to end user computing and it includes to adopt centralized application deployment, preparation for changing job roles, know users and so on.Presenting VID Managing End User Computing In The Company Infographics PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Implications, Application Performance, Endeavor And Metrics. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
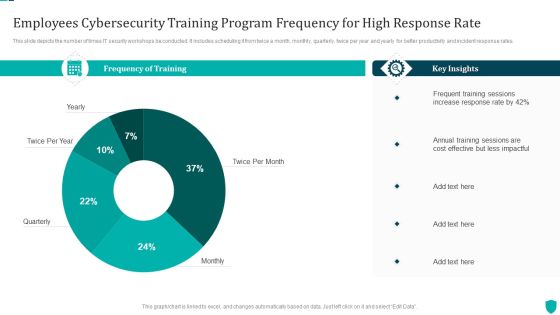
Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF
This slide depicts the number of times IT security workshops be conducted. It includes scheduling it from twice a month, monthly, quarterly, twice per year and yearly for better productivity and incident response rates.Showcasing this set of slides titled Employees Cybersecurity Training Program Frequency For High Response Rate Inspiration PDF. The topics addressed in these templates are Frequency Of Training, Key Insights, Frequent Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
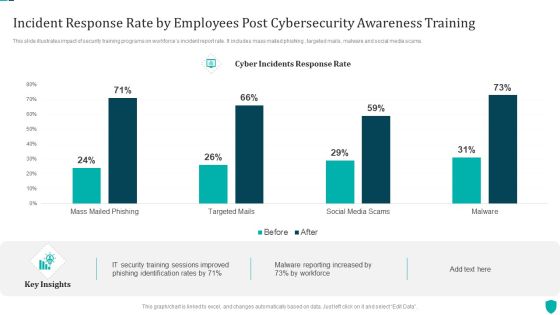
Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF
This slide illustrates impact of security training programs on workforces incident report rate. It includes mass mailed phishing , targeted mails, malware and social media scams.Pitch your topic with ease and precision using this Incident Response Rate By Employees Post Cybersecurity Awareness Training Demonstration PDF. This layout presents information on Training Sessions, Phishing Identification, Malware Reporting. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
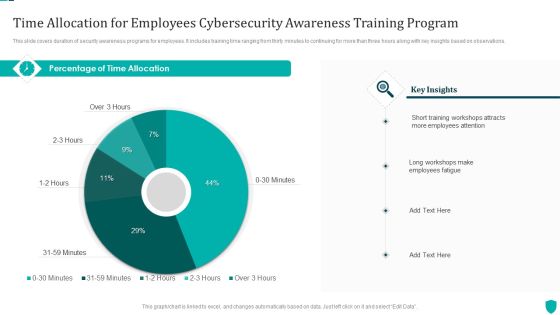
Time Allocation For Employees Cybersecurity Awareness Training Program Themes PDF
This slide covers duration of security awareness programs for employees. It includes training time ranging from thirty minutes to continuing for more than three hours along with key insights based on observations.Pitch your topic with ease and precision using this Time Allocation For Employees Cybersecurity Awareness Training Program Themes PDF. This layout presents information on Training Workshops, Employees Attention, Employees Fatigue. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Knowledge Process Outsourcing Company Profile Integrated Performance Of The Company Clipart PDF
This slide highlights the integrated performance of call center which covers different elements such as jobs created, percentage of women, renewable energy consumption, employees trained on data security and code of conduct.Deliver an awe inspiring pitch with this creative Knowledge Process Outsourcing Company Profile Integrated Performance Of The Company Clipart PDF bundle. Topics like Percentage Of Women, Agents Trained, Technology And Analytics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

AIOPS Implementation Artificial Intelligence For IT Operations In Healthcare Industry Formats PDF
This slide depicts the application of AIOps in the healthcare industry that includes maintaining the security of personal health information, defending against ransomware attacks, etc. This is a AIOPS Implementation Artificial Intelligence For IT Operations In Healthcare Industry Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Electronic Personal, Health Information, Medical Practitioners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF
The following slide exhibits various approaches which can be used to prevent cybersecurity risk faced by the real estate enterprise. The key approaches highlighted in the slide are updating the security system, installing anti-phishing add-ons, using a customized web application firewall etc. Deliver an awe inspiring pitch with this creative Approaches To Overcome Cybersecurity Risk Faced By Real Estate Company Professional PDF bundle. Topics like Ransomware, Reduce Ransomware, Cybersecurity Awareness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Benefits Of ISO 27001 Certification Summary PDF
This slide displays various organizational benefits after getting ISO 27001 certification. Benefits included are information confidentiality, low operational cost, increase in the trust of valuable partners and customers and competitive advantage.Presenting Benefits Of ISO 27001 Certification Summary PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Security Breaches, Competitive Advantage, Recognized Standard. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Solutions Business Profile Our Management Team Introduction PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting Information Technology Solutions Business Profile Our Management Team Introduction PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Executive Officer, Executive Assistant, Financial Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Small Business Venture Company Profile Our Management Team Formats PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting Small Business Venture Company Profile Our Management Team Formats PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Chief Executive, Executive Assistant, Chief Financial. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategic Database Lifecycle Management Objectives To Streamline Information Flow Graphics PDF
This slide covers key goals to ensure data is managed and useful to draw adequate insights. It includes objectives such as appointment of data management roles, ensure data accessibility, produce documentation and adapt to data culture.Presenting Strategic Database Lifecycle Management Objectives To Streamline Information Flow Graphics PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Data Availability, Structural Integrity, Security Confidentiality. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Additional Roles Pivotal For Successful Infrastructure Management Demonstration PDF
This slide provides information regarding the additional roles considered as pivotal for successful infrastructure management in terms of release manager, automation architect integration specialist, software tester developer and security engineer.This is a Additional Roles Pivotal For Successful Infrastructure Management Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Release Manager, Automation Architect, Integration Specialist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF
The following slide highlights the cyber security incident response plan for attack illustrating objective, planning and action, which helps the management to take decision for risk mitigation strategy and allocation of budget and resources depending on criticality of cyber attack. Persuade your audience using this Digital Risk Assessment Incident Response Plan For Attack Ppt Backgrounds PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Objective, Planning, Action. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF
The following slide highlights the cyber security threat intelligence cycle illustrating direction, collection, processing, analysis, reporting and action for quick fix of cyber threat and incident of breach to minimize the downtime of system. Persuade your audience using this Digital Risk Assessment Threat Intelligence Cycle Ppt Ideas Outfit PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Reporting, Analysis, Processing, Direction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF
The following slide highlights the five phase of risk based cyber security which includes business impact analysis, risk assessment, controls, report and monitor, it provides activity, value and outcome for each phase which helps company to develop a consistent incident response process. Presenting Five Phase Of Based Digital Risk Assessment Ppt Summary Rules PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Business Impact Analysis, Risk Assessment, Controls, Report, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF
The following slide highlights the phase of cyber security incident response cycle depicting preparation phase, analysis phase, response phase, and post event phase. Persuade your audience using this Phases Of Digital Risk Assessment Incident Response Cycle Ppt Gallery Format Ideas PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Post Event Phase, Response Phase, Preparation Phase, Analysis Phase. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF
The following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting Three Layers Of Digital Risk Assessment Management Process Ppt Summary Visual Aids PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including People, Process, Technology. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

 Home
Home