Security Strategy

Types Of Disaster Recovery Plan IT Security IT Ppt Portfolio Graphics Pictures PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a types of disaster recovery plan it security it ppt portfolio graphics pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data center disaster recovery, cloud based disaster recovery, virtualization disaster recovery, disaster recovery as a service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Technology Security Types Of Disaster Recovery Plan Ppt Show Smartart PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. Presenting information technology security types of disaster recovery plan ppt show smartart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like data center disaster recovery, virtualization disaster recovery, disaster recovery as a service . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
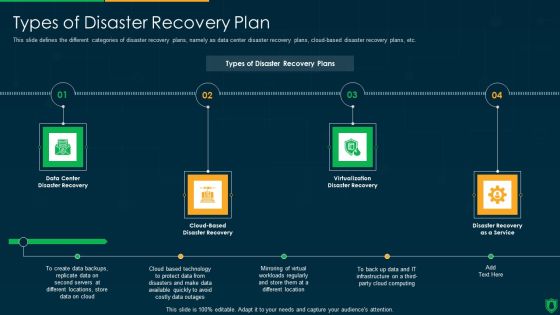
Info Security Types Of Disaster Recovery Plan Ppt PowerPoint Presentation File Clipart PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud-based disaster recovery plans, etc. This is a info security types of disaster recovery plan ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data center, disaster recovery, cloud based, disaster recovery, virtualization disaster recovery, disaster recovery as a service. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Several Food Ingredients Quality Food Security Excellence Ppt Styles Template PDF
This slide provides information regarding handling of food ingredients quality for various kinds of ingredients such as liquid, dry ingredient and oil. Presenting handling several food ingredients quality food security excellence ppt styles template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like liquid ingredients, dry ingredients, oil. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Contd Mockup PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. This is a corporate security and risk management determine sequence phases for threat attack contd mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like installation, command and control, actions and objectives, covering tracks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Determine Sequence Phases For Threat Attack Ideas PDF
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. Presenting corporate security and risk management determine sequence phases for threat attack ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like reconnaissance, weaponization, delivery, exploitation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
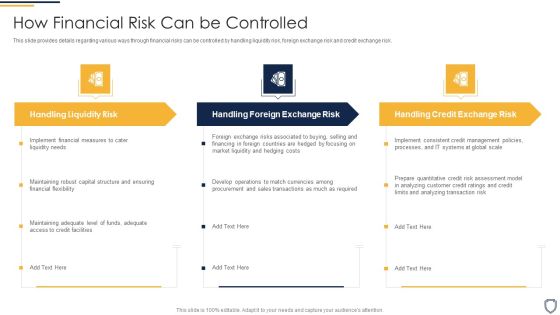
Corporate Security And Risk Management How Financial Risk Can Be Controlled Infographics PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting corporate security and risk management how financial risk can be controlled infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Roles And Responsibilities To Ensure Work Professional PDF
This slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment This is a corporate security and risk management roles and responsibilities to ensure work professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee responsibilities, unit supervisor manager responsibilities, internal investigations unit responsibilities, human resources responsibilities . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF
This slide outlines a few cyber attacks and fraud incidents that happened in the blockchain infrastructure. The purpose of this slide is to showcase the cyberattacks and fraud that occurred in the past, including code exploitation, stolen keys and employee computer hacking. There are so many reasons you need a Blockchain Security Solutions Deployment Cyberattacks And Fraud Incidents In Blockchain Clipart PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security Control Techniques For Real Estate Project Training Plan For Construction Site Safety Program Structure PDF
Slidegeeks is here to make your presentations a breeze with Security Control Techniques For Real Estate Project Training Plan For Construction Site Safety Program Structure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youare sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cloud Computing Technology Implementation Plan Security Related Challenges In Serverless Technology Ideas PDF
The purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency. Presenting cloud computing technology implementation plan security related challenges in serverless technology ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like improper monitoring and controlling, authentication issues, dependency on third party. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Types Of Disaster Recovery Plan Ppt Ideas Example PDF
This slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud based disaster recovery plans, etc. Presenting information security types of disaster recovery plan ppt ideas example pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like locations, technology, infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Mitigation Plan For Resolving Encountered Threat Icons PDF. Use them to share invaluable insights on Threat Encountered, Risk Level, Mitigation Plan, Resources Required and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF
This slide shows plan for managing insider risk with case status. It provides information about users, alert, status, severity, time detected, action plan, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Management Plan With Case Status Graphics PDF. This layout presents information on Requires Review, Action Plan, Case Status. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Security Administration In Organization Threat Management Action Plan Level Information PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver an awe inspiring pitch with this creative cyber security administration in organization threat management action plan level information pdf bundle. Topics like threat management action plan can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Mitigation Plan For Resolving Encountered Threat Themes PDF. Use them to share invaluable insights on Unpatched Servers, Attacks Including, Awareness Trainings and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Computing Security Plan Five Years Roadmap For IT Project Slides
Presenting the cloud computing security plan five years roadmap for it project slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Plan Half Yearly Roadmap With Key Enablers Diagrams
Presenting the cloud computing security plan half yearly roadmap with key enablers diagrams. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

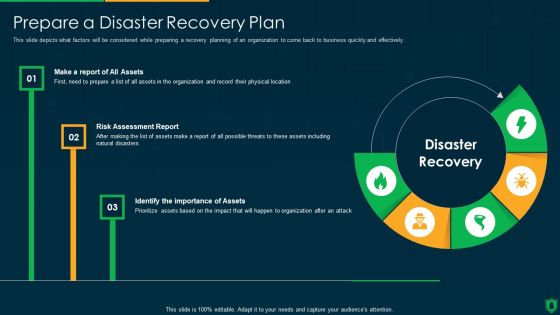
Information Security Prepare A Disaster Recovery Plan Ppt Model Aids PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting information security prepare a disaster recovery plan ppt model aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, location, risk assessment report. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Contingency Plan For Cyber Threat Handling Structure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Presenting corporate security and risk management contingency plan for cyber threat handling structure pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like contingency solutions, contingency considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

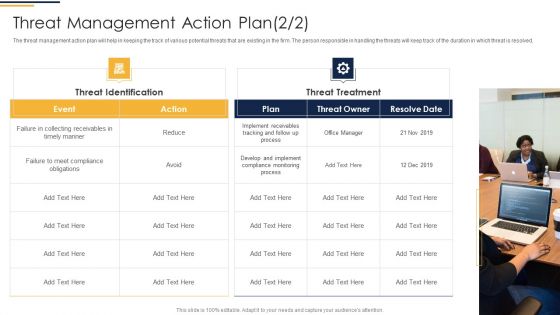
Corporate Security And Risk Management Threat Management Action Plan Risk Portrait PDF
The threat management action plan will help in keeping the track of various potential threats that are existing in the firm. The person responsible in handling the threats will keep track of the duration in which threat is resolved. Presenting corporate security and risk management threat management action plan risk portrait pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like threat identification, threat treatment . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Corporate Security And Risk Management Threat Management Action Plan Introduction PDF
The threat management action plan will help in keeping the track of potential threats that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Deliver and pitch your topic in the best possible manner with this corporate security and risk management threat management action plan introduction pdf. Use them to share invaluable insights on potential risk, risk level, action, duration, risk treated and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Prepare A Disaster Recovery Plan Ppt Show Templates PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a it security prepare a disaster recovery plan ppt show templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like make a report of all assets, risk assessment report, identify the importance of assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Info Security Prepare A Disaster Recovery Plan Ppt PowerPoint Presentation File Portfolio PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a info security prepare a disaster recovery plan ppt powerpoint presentation file portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disaster recovery, risk assessment report, identify importance assets, disaster recovery. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management Action Plan Mobile Device Security Management Rules PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.Deliver an awe inspiring pitch with this creative Mobile Device Management Action Plan Mobile Device Security Management Rules PDF bundle. Topics like Collecting Receivables, Compliance Obligations, Compliance Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF
This slide covers quarterly cybersecurity awareness training program plan. It involves activities such as cybersecurity knowledge and survey, compliance training, phishing simulation etc. Pitch your topic with ease and precision using this Quarterly IT Security Awareness Training Program Plan Ppt Gallery Topics PDF. This layout presents information on Key Message, Core Awareness Activities, Responsible Person, Budget. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF
The risk management action plan will help in keeping the track of various potential risks that are existing in the firm in context to mobile device management. The person responsible in handling the risk will keep track of the duration in which risk is resolved.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Mobile Device Management Action Plan Business Mobile Device Security Management And Mitigation Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Computing Security Plan Five Years Roadmap With Key Enablers Designs
Presenting our jaw dropping cloud computing security plan five years roadmap with key enablers designs. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Cloud Computing Security Plan Half Yearly Roadmap With Multiple Phases Topics
Presenting our jaw dropping cloud computing security plan half yearly roadmap with multiple phases topics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Cloud Computing Security Plan Three Months Roadmap For IT Project Pictures
Presenting our jaw dropping cloud computing security plan three months roadmap for it project pictures. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Information And Technology Security Operations Secops Staff Training Plan With Cost Introduction PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative information and technology security operations secops staff training plan with cost introduction pdf bundle. Topics like management, vulnerability, business, training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Secops Staff Training Plan With Cost Sample PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative organizational security solutions secops staff training plan with cost sample pdf bundle. Topics like management, vulnerability, business, training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Secops Staff Training Plan With Cost Background PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative security and process integration secops staff training plan with cost background pdf bundle. Topics like management, vulnerability, business, training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Asset Criticality Of Identified System Components Mockup PDF
Following slide demonstrates the asset criticality of identified system components. It covers details such as system name, component used, impact rating, criticality rating and failure cost. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan asset criticality of identified system components mockup pdf. Use them to share invaluable insights on system name, component used, impact rating, criticality rating, failure cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Risk Management Plan Threat Identification And Vulnerability Impact Assessment Brochure PDF
Following slide shows threat identification and vulnerability impact assessment. It covers information of threat agent, affected assets, potential vulnerability, vulnerability ranking, its rank and threats to firm. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan threat identification and vulnerability impact assessment brochure pdf. Use them to share invaluable insights on threat agent, affected assets, potential vulnerability, vulnerability ranking, threats to firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Administration And Mitigation Plan Ppt PowerPoint Presentation Complete Deck With Slides
Conduct adequate research on all facets of your business and grow its in sales, profit, etc using this ready-made PPT slide. This Information Security Risk Administration And Mitigation Plan Ppt PowerPoint Presentation Complete Deck With Slides displays parameters to help you evaluate business environment from all angles. Incorporate this organized PPT Design in seventy two slides to classify your top challengers. It is a customizable slide, so use it as per your requirement. Download now to showcase your expertise in all things business, and the specialized knowledge you may have.

KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF
The following slide represents training program for transaction monitoring and anti money laundering AML. It provides information about certification, assessment, compatibility, surveillance, operational efficiency, escalation, unusual transactions, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Transaction Monitoring And Aml Training Plan Ideas PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides
Use this Information Systems Security And Risk Management Plan Ppt PowerPoint Presentation Complete Deck With Slides to ensure the business world gets to know you as a presentation expert with tremendous recall value. With its focus on providing the worlds best designs to highlight business ideas that have the potential to change the world, this PPT Template is sure to win you clients. The complete deck in seventy eight slides is a compendium of information, structured in a manner that provides the best framework for a presentation. Use this completely editable and customizable presentation to make an impact and improve your order book. Download now.

Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Information Systems Security And Risk Management Plan Threat Identification And Vulnerability Assessment For Risk Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information Systems Security And Risk Management Plan Doughnut Chart Rules PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Information Systems Security And Risk Management Plan Doughnut Chart Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF
The following slide depicts fraud alert and case management approach. It provides information about anti money laundering, transaction monitoring system, request for information, fraud detection, suspicious activity reporting SAR, etc. The KYC Transaction Monitoring System Business Security Fraud Alert And Case Management Approach Diagrams PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Desktop Security Management Define Access Control Measures For Employees Icons PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a desktop security management define access control measures for employees icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF
This slide talks about the timeline for software defined network implementation, including the steps to be performed, such as defining the use case, creating a cross functional team, testing, and reviewing. Want to ace your presentation in front of a live audience Our SDN Security Architecture Timeline For Software Defined Network Implementation Elements PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.
Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF
This slide represents the schematic elements of software-defined networking, such as the northbound interface, SDN controller, and southbound interface. These components transmit the information throughout the SDN architecture. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Safeguarding Network With SDN Security Table Of Contents Ppt Visual Aids Files PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
How Is Automation Used In Information Technology Security Ppt File Icon PDF
This slide depicts the network protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting how is automation used in information technology security ppt file icon pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human detection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF
The following slide showcases solution offered by IT company for its customers which are see the new network, know current threats and protect with high ROI. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Security Software Company Investor Funding Pitch Deck Our Solution Demonstration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.
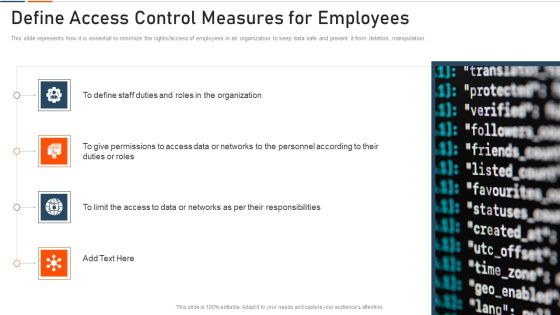
Information Technology Security Define Access Control Measures For Employees Ppt Professional Design Templates PDF
This slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a information technology security define access control measures for employees ppt professional design templates pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like staff duties, organization, roles, access, permissions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organization Compliance Metrics Hacking Prevention Awareness Training For IT Security Inspiration PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver and pitch your topic in the best possible manner with this organization compliance metrics hacking prevention awareness training for it security inspiration pdf. Use them to share invaluable insights on training completion, communication methods, policy sign off and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF
Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Table Of Contents For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Security Functioning Centre Various Technologies For Effective Secops Process Template PDF
This slide portrays information regarding the different technologies that can be used by firm in order to implement effective SecOps process in firm. Presenting security functioning centre various technologies for effective secops process template pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like event management, cyber threat intelligence, network traffic analysis. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Addressing Various Ways To Handle Insider Cyber Threats Designs PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of periodic risk assessment, end user informing, etc. This is a cyber security administration in organization addressing various ways to handle insider cyber threats designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like assessment, networks, individuals, determine. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF
This slide shows the monthly project management timeline for website development which includes two teams such as UX and Backend team whose main tasks are system designing, getting approval from client, creating wireframes of pages, defining website policies, etc. Showcasing this set of slides titled Business Project Management Calendar With Security And Technology Ppt Outline Clipart PDF. The topics addressed in these templates are Staffing Resource Planning, Staff Recruiting, Architecture Planning. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF
This template covers content creation tactics in account based marketing such as launching multi touch campaigns, use of marketing automated tools etc.This is a Security And Performance Digital Marketing Launch Multitouch Email Campaigns Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Campaign Launch, Campaign Workflow, Ensure Prospects. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Investment Banking Security Underwriting Pitchbook Services Offered By Investment Bank Designs PDF
The slide comprises key services of the company which includes underwriting, general advisory, merger and acquisition advisory, asset management and sales trading solutions. Presenting Investment Banking Security Underwriting Pitchbook Services Offered By Investment Bank Designs PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Advisory Services, Merger And Acquisition, Assets Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
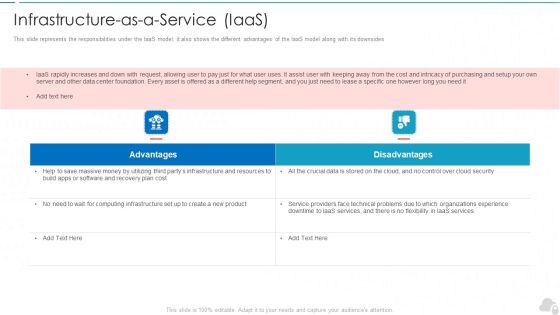
Infrastructure As A Service Iaas Cloud Computing Security IT Ppt Layouts Background Image PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a infrastructure as a service iaas cloud computing security it ppt layouts background image pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like advantages, disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SIEM Services Security Information And Event Management Logging Process Ppt Model Example Topics PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation Presenting siem services security information and event management logging process ppt model example topics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like determine, breaches, organization, investigate, aggregate. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
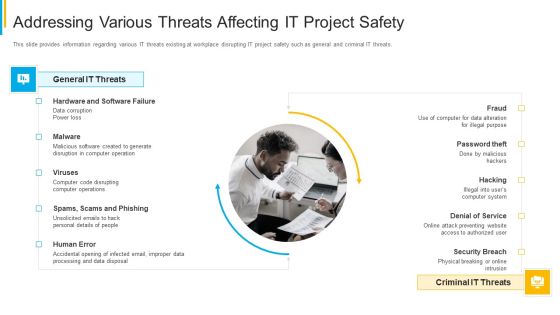
Project Security Administration IT Addressing Various Threats Affecting IT Project Safety Designs PDF
This slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Presenting project security administration it addressing various threats affecting it project safety designs pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like general it threats, criminal it threats. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
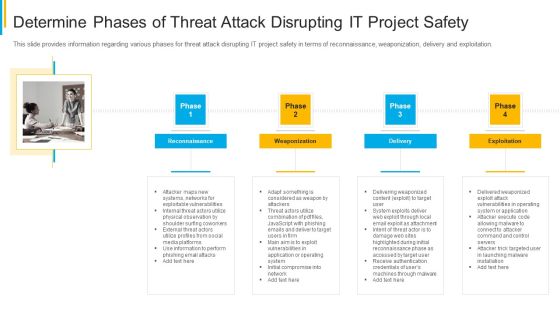
Project Security Administration IT Determine Phases Of Threat Attack Disrupting IT Project Safety Brochure PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. This is a project security administration it determine phases of threat attack disrupting it project safety brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reconnaissance, weaponization, delivery, exploitation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT Determine Phases Of Threat Attack Disrupting Project Safety Contd Icons PDF
This slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Presenting project security administration it determine phases of threat attack disrupting project safety contd icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like installation, command and control, actions and objectives, covering tracks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Roles And Responsibilities To Ensure Work Environment With Employee Safety Pictures PDF
This slide provides information regarding roles and responsibilities assigned to ensure minimum violence work environment. Presenting project security administration it roles and responsibilities to ensure work environment with employee safety pictures pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like employee responsibilities, unit supervisor or manager responsibilities, internal investigations unit responsibilities, human resources responsibilities. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF
The Safety Breach Response Playbook Checklist For Work From Home Data Security Slides PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Project Security Administration IT Addressing Three Essential Attributes Of Information Associated To Project Topics PDF
This slide provides information about essential attributes of information associated to IT project in terms of protecting confidentiality, ensuring integrity and maintaining availability. This is a project security administration it addressing three essential attributes of information associated to project topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protecting confidentiality, ensuring integrity, maintaining availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Workplace Employee Assistance Program Professional PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Presenting cyber security administration in organization workplace employee assistance program professional pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like clinical, services, employer, management, consultations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization addressing ways to handling financial threats summary pdf
This slide provides details regarding handling financial threats by safeguarding financial stability and protecting the firm from costly effects that financial threats can have. This is a cyber security administration in organization addressing ways to handling financial threats summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like financial, statements, requirement, preparing, balance . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF
Welcome to our selection of the Table Of Contents IT Security Automation Systems Guide Layer Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cyber Security Administration In Organization Workplace Incident Summary Report Brochure PDF
This slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. This is a cyber security administration in organization workplace incident summary report brochure pdf template with various stages. Focus and dispense information on eigt stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident, employees, location, emergency, assistance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Facilities Offered By Successful Implementation Guidelines PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a information and technology security operations facilities offered by successful implementation guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
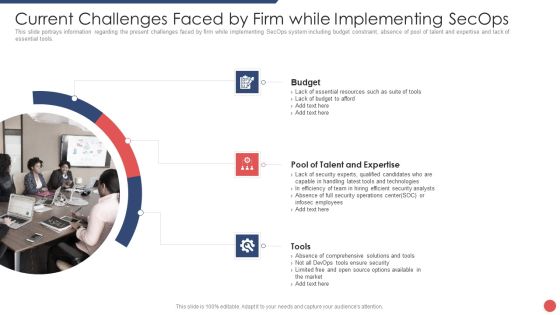
Security Functioning Centre Current Challenges Faced By Firm While Implementing Secops Topics PDF
This slide portrays information regarding the present challenges faced by firm while implementing SecOps system including budget constraint, absence of pool of talent and expertise and lack of essential tools. Presenting security functioning centre current challenges faced by firm while implementing secops topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like budget, pool of talent and expertise, tools. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Roles And Responsibilities Assigned In Quality Management Process Food Security Excellence Ppt Outline Design Templates PDF
This slide outlines roles and responsibilities such as project manager, quality manager, system integrator, etc. that are assigned to people who are involved in quality management process. Presenting roles and responsibilities assigned in quality management process food security excellence ppt outline design templates pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like project manager, technical manager, quality manager, system integrator, test team. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Dispose Data And Equipment Properly IT Security IT Ppt Icon Clipart Images PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting dispose data and equipment properly it security it ppt icon clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
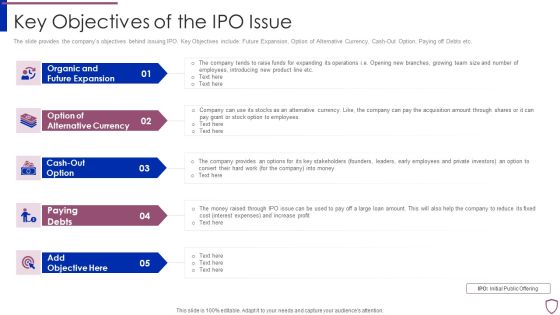
Financing Catalogue For Security Underwriting Agreement Key Objectives Of The IPO Issue Mockup PDF
The slide provides the companys objectives behind issuing IPO. Key Objectives include Future Expansion, Option of Alternative Currency, Cash-Out Option, Paying off Debts etc. Presenting financing catalogue for security underwriting agreement key objectives of the ipo issue mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organic and future expansion, option of alternative currency, cash out option, paying debts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Project Security Administration IT Addressing Frequent Communication For Project Quality Management Icons PDF
This slide provides information regarding meetings that held in order to keep consistent quality entire project. These meetings are held on quarterly, annual basis. Presenting project security administration it addressing frequent communication for project quality management icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like executive, leaders, coordinators, initiation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Determine Staff Training Schedule For Skills Enhancement Formats PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Presenting project security administration it determine staff training schedule for skills enhancement formats pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like determine staff training schedule for skills enhancement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Addressing Several Financial Scenarios And Signs Threat Template PDF
This slide provides information regarding the various financial scenarios that pose a threat to firm profitability and determine signs of financial distress. Presenting cyber security administration in organization addressing several financial scenarios and signs threat template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like insolvency, scenario, bankruptcy, situation, fluctuations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Evaluating Financial Practices In Firm Rules PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Presenting cyber security administration in organization evaluating financial practices in firm rules pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like evaluating financial practices in firm. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization determine sequence phases for threat attack access inspiration pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of installation, command and control, actions and objectives, covering tracks. Presenting cyber security administration in organization determine sequence phases for threat attack access inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like communication, platform, access, compromised, session . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

cyber security administration in organization determine sequence phases for threat attack infographics pdf
This slide provides details regarding sequence phases for threat attack by threat actor in terms of reconnaissance, weaponization, delivery and exploitation. This is a cyber security administration in organization determine sequence phases for threat attack infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like internal, threat, perform, phishing, combination . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
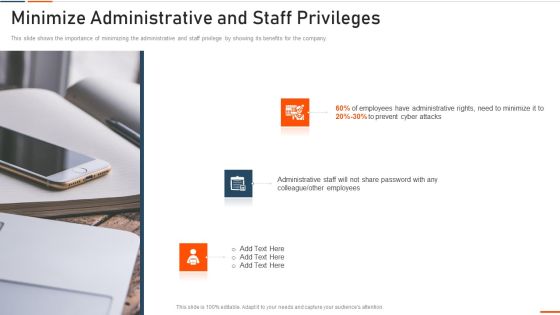
Information Technology Security Minimize Administrative And Staff Privileges Ppt Professional Graphics PDF
This slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Presenting information technology security minimize administrative and staff privileges ppt professional graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like minimize administrative and staff privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF
This template covers account based marketing through retargeting email campaigns. It also includes remarketing funnel for social media, emails and website landing pages.Presenting Security And Performance Digital Marketing Support Email Campaigns With Retargeting Elements PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Alternatives Available, Remarking Retargeting, Media Advertising. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
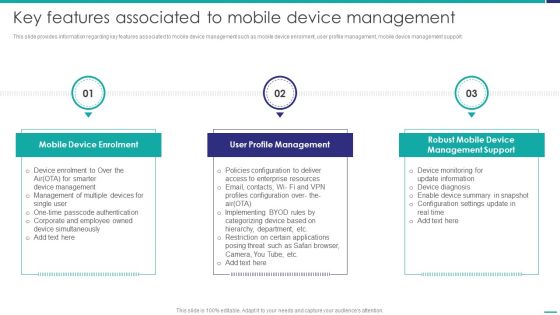
Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF
This slide provides information regarding key features associated to mobile device management such as mobile device enrolment, user profile management, mobile device management support. This is a Key Features Associated To Mobile Device Management Mobile Device Security Management Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Device Enrolment, Profile Management, Management Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF
Slidegeeks has constructed Table Of Contents Of Security Control Techniques For Real Estate Project Portrait PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF
The following slide depicts impact of advanced transaction monitoring system. It provides information about surveillance, behaviors, patterns, transactions, fraudulent transactions, money laundering, false positives, efficiency, etc. Boost your pitch with our creative KYC Transaction Monitoring System Business Security Analyzing Impact Of Advanced Transaction Guidelines PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Implementing Cybersecurity Awareness Program To Prevent Attacks Key Stakeholders Of Cyber Security Themes PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Template PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Table Of Contents Developing Information Technology Security Awareness Training Program For Employees Template PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

SDN Security Architecture Table Of Contents Ppt PowerPoint Presentation File Example PDF
Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download SDN Security Architecture Table Of Contents Ppt PowerPoint Presentation File Example PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF
This slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Biometric Technology For Enhancing Mobile Banking Security Ppt Model Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Agenda Development And Integration Of Cyber Security Incident Administration Information PDF
Slidegeeks is here to make your presentations a breeze with Agenda Development And Integration Of Cyber Security Incident Administration Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Table Of Contents Enhancing Cloud Security With CASB Ppt PowerPoint Presentation File Deck PDF
Present like a pro with Table Of Contents Enhancing Cloud Security With CASB Ppt PowerPoint Presentation File Deck PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF
The purpose of this slide is to outline different techniques which can be used to protect organization from business email compromise attack. The techniques covered in the slide are sender policy framework SPF, using strong password policy and process for wire transfers. Find a pre-designed and impeccable Organizing Security Awareness Various Techniques To Successfully Prevent Business Email Diagrams PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Project Security Administration IT Various Ways To Manage Project Safety By Managing Threats Contd Sample PDF
This slide provides information regarding various ways to handle threats to ensure project safety in terms of active remediation implementation, deactivating orphaned user accounts, etc. This is a project security administration it various ways to manage project safety by managing threats contd sample pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deactivate orphaned user accounts, develop strict access management policies, implement active remediation, investigate remote access policies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Addressing Various Ways To Handle Insider Cyber Threats Contd Guidelines PDF
This slide provides details regarding various ways to handle insider cyber threats in terms of active remediation implementation, deactivating orphaned user accounts, etc. Presenting corporate security and risk management addressing various ways to handle insider cyber threats contd guidelines pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like develop strict access management policies, deactivate orphaned user accounts, implement active remediation, investigate remote access policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF
This slide provides information regarding different mobile device management approach such as container and platform approach that can be selected by vendor based on requirement. This is a Addressing Mobile Device Management Approach Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Container Approach, Platform Approach, Critical Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Addressing Timeframe For Incident Management At Business Mobile Device Security Management Sample PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Welcome to our selection of the Addressing Timeframe For Incident Management At Business Mobile Device Security Management Sample PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 precent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

IT Risk Management Approaches Organizations Risk Management And IT Security Graphics PDF
This slide highlights the information technology risks management approaches which includes risk avoidance, risk sharing, risks reduction and risk retention. Want to ace your presentation in front of a live audience Our IT Risk Management Approaches Organizations Risk Management And IT Security Graphics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Manpower Corporate Security Business Profile CSR Initiatives And Spending Structure PDF
This slide highlights the CSR spend distribution by inhouse and partner spend. It also highlights the CSR initiatives that are carbon footprint reduction, labor policies, hunger program, community development and healthcare services. Deliver and pitch your topic in the best possible manner with this Manpower Corporate Security Business Profile CSR Initiatives And Spending Structure PDF. Use them to share invaluable insights on Community Development, Environment Safety, Healthcare Services and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Officer Service Company Profile Csr Initiatives And Spending Ppt PowerPoint Presentation Gallery Shapes PDF
This slide highlights the CSR spend distribution by inhouse and partner spend. It also highlights the CSR initiatives that are carbon footprint reduction, labor policies, hunger program, community development and healthcare services. Deliver an awe inspiring pitch with this creative Security Officer Service Company Profile Csr Initiatives And Spending Ppt PowerPoint Presentation Gallery Shapes PDF bundle. Topics like CSR Total Spend, Hunger Program, Skills Training, Community Development can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financing Catalogue For Security Underwriting Agreement Share Allocation Process Clipart PDF
The slide provides the methods of share allocation in different subscription cases oversubscription and under subscription. Key methods include lottery basis, pro rata basis, and combination of both. Presenting financing catalogue for security underwriting agreement share allocation process clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like in case undersubscription, in case of oversubscription. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
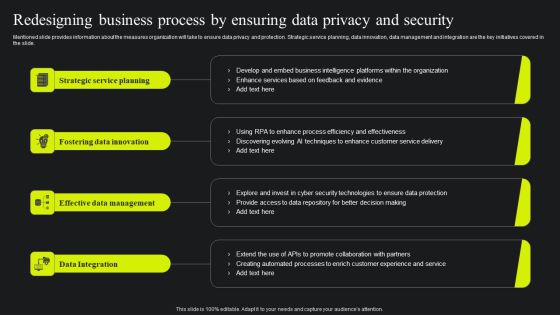
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Slidegeeks is here to make your presentations a breeze with Redesigning Business Process By Ensuring Data Privacy And Security Ppt Portfolio Elements PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
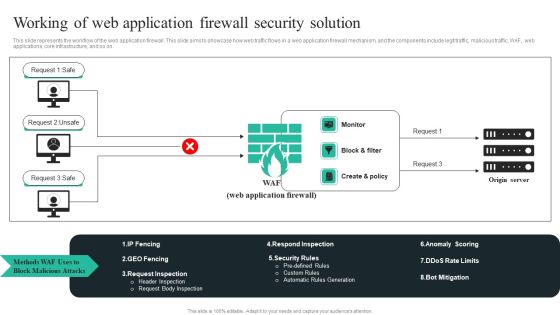
WAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF
This slide represents the workflow of the web application firewall. This slide aims to showcase how web traffic flows in a web application firewall mechanism, and the components include legit traffic, malicious traffic, WAF, web applications, core infrastructure, and so on. Take your projects to the next level with our ultimate collection ofWAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Security Control Techniques For Real Estate Project Budget Plan For Construction Site Safety Program Microsoft PDF
The purpose of this slide is to highlight the budget plan for the construction site safety program. It includes details regarding the breakup of multiple costs, such as equipment and training costs along with the units required, cost per unit and total cost. This slide showcase the major barriers to successfully implement of construction site safety program such as limited awareness, limited employee participation, insufficient legislation, and behavioral rigidity. It also contains details of recommended solutions to overcome them. Make sure to capture your audiences attention in your business displays with our gratis customizable Security Control Techniques For Real Estate Project Budget Plan For Construction Site Safety Program Microsoft PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF
This slide shows facts and figures indicating insider threat root causes and methods. It contains information such as unawareness about guidelines, phishing email, shared with wrong person, etc. Showcasing this set of slides titled Statistics For Root Causes Of Insider Threat In Cyber Security Inspiration PDF. The topics addressed in these templates are Employee Replied, Spear Phishing Email, Employee Clicked, Phishing Email. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
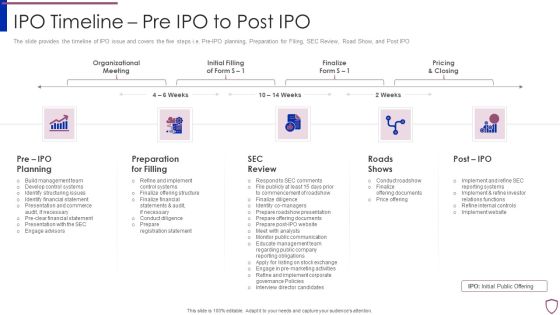
Financing Catalogue For Security Underwriting Agreement IPO Timeline Pre IPO To Post IPO Microsoft PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPO. Presenting financing catalogue for security underwriting agreement ipo timeline pre ipo to post ipo microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like pre ipo planning, preparation for filling, sec review, roads shows, post ipo. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Ensuring Collaboration Among Various Functional Areas Brochure PDF
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. This is a corporate security and risk management ensuring collaboration among various functional areas brochure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan and collet, review and analyze, develop strategic framework. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck
Landing corporate business deals can be a huge achievement, both in terms of reputation and finance. This highlights the importance of drafting a comprehensive plan for this business segment that this Development And Integration Of Cyber Security Incident Administration Ppt PowerPoint Presentation Complete Deck does perfectly for you. Given below is a perfectly curated service proposal in Seventy slides that is sure to give your presentation the desired edge. It will display all the details enabling the company to analyze standout components and make an informed decision. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

Cyber Security Disaster Recuperation Six Months Roadmap To Eradicate Intrusion Icons
Presenting the cyber security disaster recuperation six months roadmap to eradicate intrusion icons. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cyber Security Tactic For Process Management For IT Roadmap Six Months Clipart
Presenting the cyber security tactic for process management for it roadmap six months clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Half Yearly Information Technology Security Roadmap For Continuous Threat Analysis Rules
Presenting the half yearly information technology security roadmap for continuous threat analysis rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Information Technology Security Roadmap For Continuous Threat Analysis Microsoft
Presenting the six months information technology security roadmap for continuous threat analysis microsoft. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
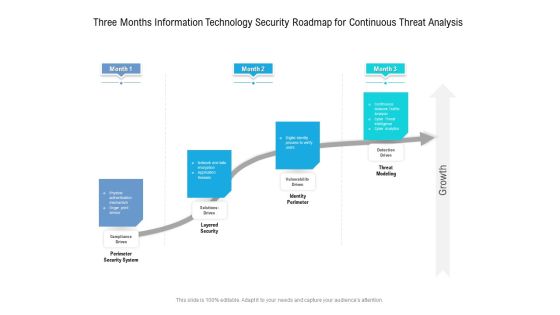
Three Months Information Technology Security Roadmap For Continuous Threat Analysis Professional
Presenting the three months information technology security roadmap for continuous threat analysis professional. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Five Years Enterprise IT Automation Machinery Road Mapping With Security And Compliance Ideas
Presenting the five years enterprise it automation machinery road mapping with security and compliance ideas. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Organization Five Years Automation Machinery Roadmapping With Security And Compliance Diagrams
Presenting the organization five years automation machinery roadmapping with security and compliance diagrams. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
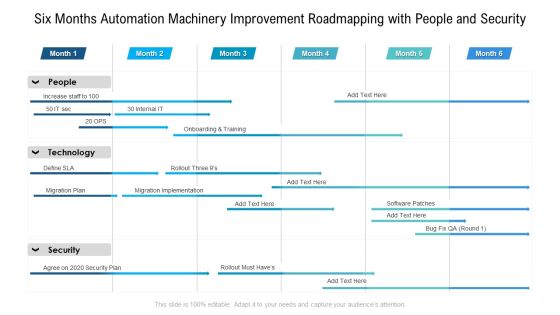
Six Months Automation Machinery Improvement Roadmapping With People And Security Brochure
Presenting the six months automation machinery improvement roadmapping with people and security brochure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

cyber security administration in organization key activities checklist associated program icons pdf
This slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Presenting cyber security administration in organization key activities checklist associated program icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like program, present, management, consequence, considerations . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Systems Guide Ppt PowerPoint Presentation Complete With Slides
This is a professional and ready to use PowerPoint deck for entrepreneurs, who want to showcase their business in the best light possible. Use this IT Security Automation Systems Guide Ppt PowerPoint Presentation Complete With Slides and prepare an engaging pitch to showcase potential in the industry of your choice. Whether you are just starting out or business or planning to scale, deploy this forty three slide complete deck to demonstrate your ideas for bringing innovation and creativity in the business. The presentation template is also equipped to do this with its 100 percent editable and customizable capability. Download now.

Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 parcent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Asset Identification For Information Security Risk Management Cybersecurity Risk Assessment Inspiration PDF from Slidegeeks and deliver a wonderful presentation.

Cyber Physical System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides
This incisive, comprehensive Cyber Physical System To Enhance Security Ppt PowerPoint Presentation Complete Deck With Slides details important features of running a business. One learns about things like result areas, planning and strategic framework just a glance of this comprehensive deck of fifty seven slides. Use this PPT template to present your unique perspective of business technicalities and experience the way a good presentation can give new meaning to similarly-placed facts. Use this template to leave a roomful of people wondering at the expert you have gathered in closing a business deal. The completely editable and customisable nature of the presentation is a unique bonus. Download now.

 Home
Home