Security Strategy

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Tips To Create Cyber Safety And Security Evaluation Report Pictures PDF
This slide shows various tips to prepare cyber security evaluation report. It includes points such as general approach, analyze, scope assessment and conclusion. Persuade your audience using this Tips To Create Cyber Safety And Security Evaluation Report Pictures PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including General Approach, Analyze, Scope Assessment. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Elements Of IT Security IT End User Education Ppt Model Deck PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a elements of it security it end user education ppt model deck pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hire professional, train often, password protocols, microlearning opportunities, effective training. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Integrating Data Privacy System To Enhance Security Ppt Professional Layout PDF
Find a pre-designed and impeccable Agenda For Integrating Data Privacy System To Enhance Security Ppt Professional Layout PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cyber Security Disaster Recuperation Five Years Roadmap To Eradicate Intrusion Professional
We present our cyber security disaster recuperation five years roadmap to eradicate intrusion professional. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched cyber security disaster recuperation five years roadmap to eradicate intrusion professionalin different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Tactic For Process Management For IT Roadmap Five Year Designs
We present our cyber security tactic for process management for it roadmap five year designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security tactic for process management for it roadmap five year designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
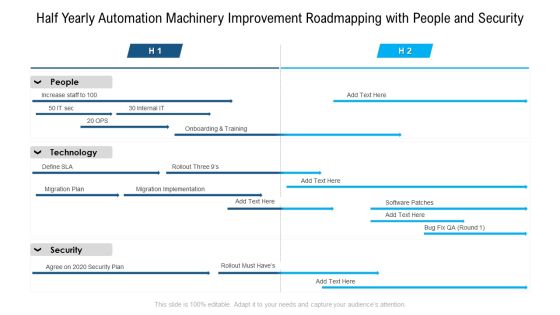
Half Yearly Automation Machinery Improvement Roadmapping With People And Security Topics
We present our half yearly automation machinery improvement roadmapping with people and security topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly automation machinery improvement roadmapping with people and security topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
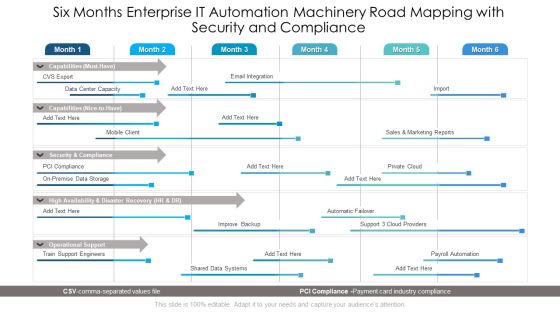
Six Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Professional
We present our six months enterprise it automation machinery road mapping with security and compliance professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise it automation machinery road mapping with security and compliance professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver and pitch your topic in the best possible manner with this ISO 27001 Organizational Qualifying Procedure Dashboard For Information Security Risk Management Background PDF. Use them to share invaluable insights on Analysis Progress, Response Progress, Plan Breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT System Risk Management Guide Table Of Contents Security Background PDF
Are you searching for a IT System Risk Management Guide Table Of Contents Security Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download IT System Risk Management Guide Table Of Contents Security Background PDF from Slidegeeks today.

Organizations Risk Management And IT Security Integration Of Risk Management Into SDLC Inspiration PDF
This slide highlights the risk management integration with software development life cycle which includes SDLC phases Initiation, development, implementation and maintenance with risk management activities. The Organizations Risk Management And IT Security Prioritized Cyber Security Threats With Risk Mitigation Plan Demonstration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF
Are you searching for a Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF from Slidegeeks today.
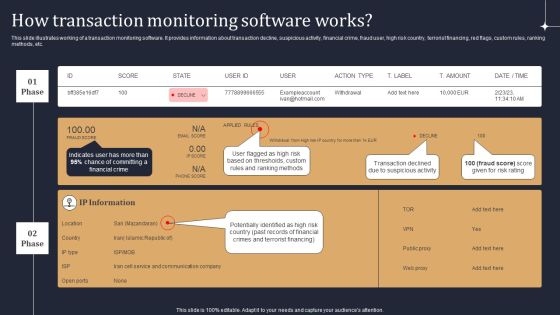
KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Are you searching for a KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF from Slidegeeks today.

Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide depicts the SaaS security process to acknowledge the gap and have proactive approach. It mainly constitutes of three phases discover, monitor and protect. Persuade your audience using this Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Discover, Monitor, Protect, Identify Utility, Assess Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
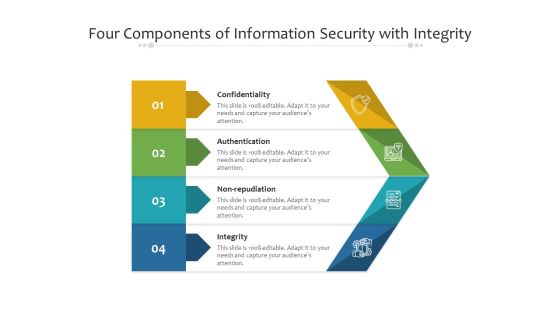
Four Components Of Information Security With Integrity Ppt PowerPoint Presentation File Gallery PDF
Presenting four components of information security with integrity ppt powerpoint presentation file gallery pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including confidentiality, authentication, integrity. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Post It Notes Hacking Prevention Awareness Training For IT Security Slides PDF
Presenting post it notes hacking prevention awareness training for it security slides pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like post it notes. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agenda For Series Of Cyber Security Attacks Against Ukraine 2022 Sample PDF
Find a pre designed and impeccable Agenda For Series Of Cyber Security Attacks Against Ukraine 2022 Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Organizing Security Awareness Training To Minimize Downtime Ideas PDF
Find a pre-designed and impeccable Agenda For Organizing Security Awareness Training To Minimize Downtime Ideas PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For KYC Transaction Monitoring System For Business Security Sample PDF
Find a pre designed and impeccable Agenda For KYC Transaction Monitoring System For Business Security Sample PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Agenda For Comprehensive Guide For Ensuring IT Infrastructure Security Graphics PDF
Find a pre-designed and impeccable Agenda For Comprehensive Guide For Ensuring IT Infrastructure Security Graphics PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. This modern and well-arranged Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF
This slide demonstrates how CDN protects data by issuing TLS or SSL certificates, blocking Bots and crawlers, and defending against DDoS assaults. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cloud Content Delivery Network Data Security Handled By CDN Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
IT Security IT Prepare And Deploy Strong IT Policies Ppt Icon Design Ideas PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security it prepare and deploy strong it policies ppt icon design ideas pdf bundle. Topics like it policies, management, access, policies, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Example PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative it security prepare and deploy strong it policies ppt icon graphics example pdf bundle. Topics like management, it policies, network access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. This modern and well arranged Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Info Security Prepare And Deploy Strong IT Policies Ppt PowerPoint Presentation File Model PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative info security prepare and deploy strong it policies ppt powerpoint presentation file model pdf bundle. Topics like build strong, it policies, data sharing, access data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Prepare And Deploy Strong IT Policies Ppt Gallery Images PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an awe inspiring pitch with this creative information security prepare and deploy strong it policies ppt gallery images pdf bundle. Topics like management, network, device, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Prepare And Deploy Strong It Policies Template PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this desktop security management prepare and deploy strong it policies template pdf. Use them to share invaluable insights on management, data, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF
This slide outlines the five data privacy rules, which are consent, purpose, disposal and destruction, access and security, accountability and disclosure. Slidegeeks is here to make your presentations a breeze with Information Security Five Data Privacy Rules Ppt PowerPoint Presentation File Deck PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF
This slide outlines the control layer of SDN architecture, which is the second layer in the model. It also includes its functions, such as receiving commands and requirements from the application layer and forwarding them to the networking components. If you are looking for a format to display your unique thoughts, then the professionally designed SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download SDN Security Architecture Control Layer Ppt PowerPoint Presentation File Files PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Information Technology Security Prepare And Deploy Strong IT Policies Ppt Icon Graphics Design PDF
This slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver and pitch your topic in the best possible manner with this information technology security prepare and deploy strong it policies ppt icon graphics design pdf. Use them to share invaluable insights on v and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
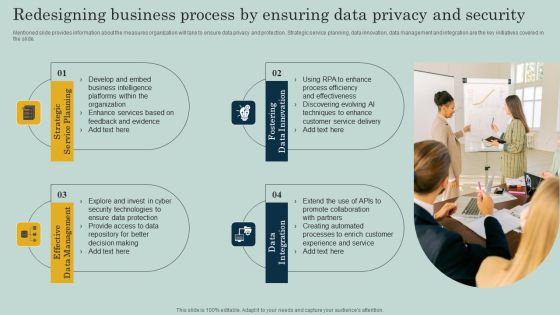
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Create an editable Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks. Slidegeeks is here to make your presentations a breeze with Cyber Risks And Incident Response Playbook Classifying Various Security Issues And Attacks Microsoft PD With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF
This slide showcases blockchain technology for anti money laundering AML and transaction monitoring. It provides information about transaction subsets, input data, monitoring, analysis, alerts, record, red flags, Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into KYC Transaction Monitoring System Business Security Blockchain Technology For AML Themes PDF.

KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF
This slide illustrates real time crime and fraud detection process flow for ATMS. It provides information about repeated transactions, counterfeit cards, hacked ATMS, skimmer, terminal, point of sale, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Real Time Atm Fraud And Crime Detection Themes PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF
This slide outlines the steps to implement a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to keep in mind while deploying a CASB model into a business and the steps include the deployment path, deployment model and releasing model. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Steps To Deploy Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Images PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF
The slide provides a list of companys clients in different sectors manufacturing, construction, financials services, energy. Mining, automobile etc. Along with the service which the company offers to specific client.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook T0p 30 Clients And Services Offered To Them Professional PDF bundle. Topics like Financials Services, Assets Management, Underwriting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF
This template covers working of Facebooks machine learning or algorithms to filter through a massive amount of data and generate a list of qualified, cold prospects.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF bundle. Topics like Interests Activity, Common Builds, Target Customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
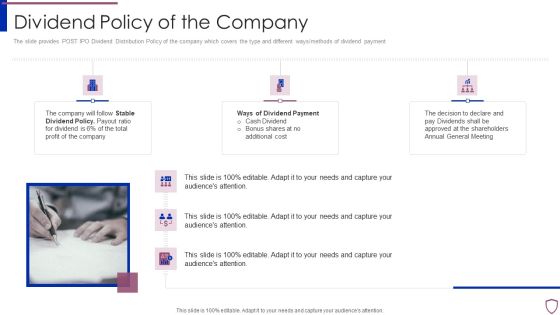
Financing Catalogue For Security Underwriting Agreement Dividend Policy Of The Company Elements PDF
The slide provides POST IPO Dividend Distribution Policy of the company which covers the type and different ways or methods of dividend payment. Presenting financing catalogue for security underwriting agreement dividend policy of the company elements pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like stable dividend policy, ways of dividend payment. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
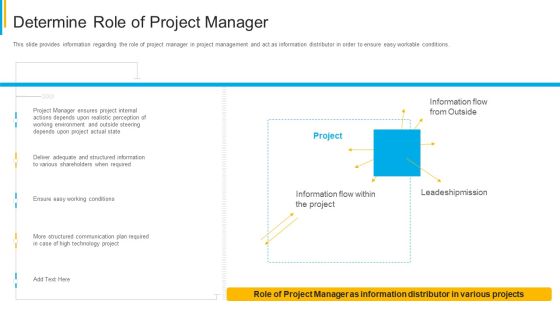
Project Security Administration IT Determine Role Of Project Manager Clipart PDF
This slide provides information regarding the role of project manager in project management and act as information distributor in order to ensure easy workable conditions. Deliver an awe inspiring pitch with this creative project security administration it determine role of project manager clipart pdf bundle. Topics like technology, communication, plan, leadeshipmission, environment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
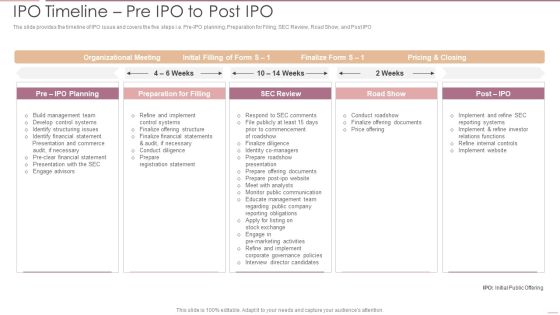
Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF
The slide provides the timeline of IPO issue and covers the five steps i.e. Pre-IPO planning, Preparation for Filing, SEC Review, Road Show, and Post IPODeliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Timeline Pre IPO To Post IPO Pictures PDF bundle. Topics like Organizational Meeting, Preparation Filling, Internal Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
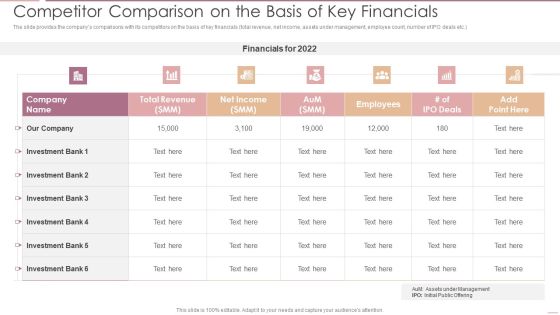
Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF
The slide provides the companys comparisons with its competitors on the basis of key financials total revenue, net income, assets under management, employee count, number of IPO deals etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Competitor Comparison On The Basis Of Key Financials Pictures PDF bundle. Topics like Total Revenue, Net Income, Investment Bank can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Investment Banking Security Underwriting Pitchbook Investment Bank Business Overview Themes PDF
The slide provides a brief information about the company including founding year, headquarter, employee count, business overview, clientele and five years financial summary .Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Investment Bank Business Overview Themes PDF bundle. Topics like Financials Overview, Business Overview, Geographies Presence can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
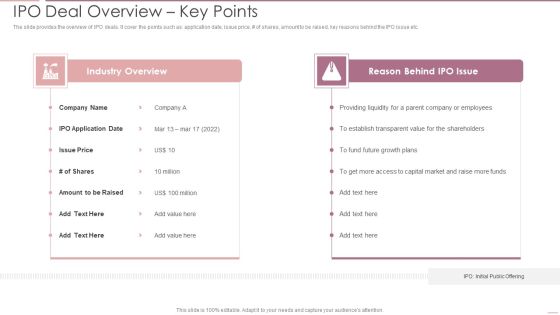
Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF
The slide provides the overview of IPO deals. It cover the points such as application date, issue price, of shares, amount to be raised, key reasons behind the IPO issue etc.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook IPO Deal Overview Key Points Brochure PDF bundle. Topics like Industry Overview, Reason Behind, Providing Liquidity can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Investment Banking Security Underwriting Pitchbook Major Investment Banking Deals Summary PDF
The slide provides the top five deals by profit amount of the company in last five years. It comprises, year, client name, deal type and brief information about all the five deals.Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook Major Investment Banking Deals Summary PDF bundle. Topics like Provided Underwriting, Provides Commitment, Healthcare Company can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Reasons And Impact Of Website Hacking On Business Template PDF
This slide represents the hacking of our website, including the reasons behind it and its overall impact on our business, such as loss of reputation, clients, and information.Deliver an awe inspiring pitch with this creative IT Security Hacker Reasons And Impact Of Website Hacking On Business Template PDF bundle. Topics like Recent Software, Inserted Harmful, Companys Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

KYC Transaction Monitoring System Business Security Machine Learning Cycle For Aml And Tms Demonstration PDF
This slide shows machine learning cycle for checking financial transactions. It provides information about self teaching, engineering, artificial intelligence, algorithms, finetuning, behaviors, red flags, criminality, detection, etc. There are so many reasons you need a KYC Transaction Monitoring System Business Security Machine Learning Cycle For Aml And Tms Demonstration PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF
The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download KYC Transaction Monitoring System Business Security Effective Ways To Report Fraudulent Transactions Summary PDF from Slidegeeks and deliver a wonderful presentation.
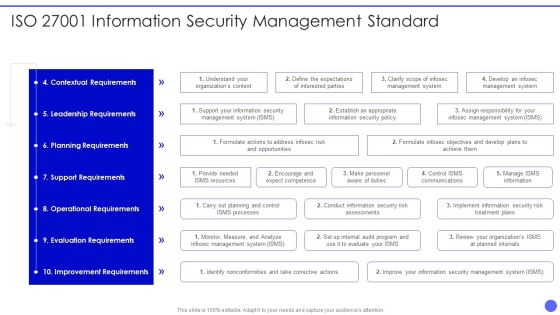
Info Safety And ISO 27001 Information Security Management Standard Download PDF
Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Information Security Management Standard Download PDF. Use them to share invaluable insights on Contextual Requirements, Leadership Requirements, Planning Requirements, Support Requirements, Operational Requirements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

NIST Internet Security Model With Functions And Categories Ppt PowerPoint Presentation Model Show PDF
Showcasing this set of slides titled NIST internet security model with functions and categories ppt powerpoint presentation model show pdf. The topics addressed in these templates are assets management, recovery planning, information protection producers. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cloud Computing Security Plan Half Yearly Roadmap For Data Protection Formats
Presenting our innovatively structured cloud computing security plan half yearly roadmap for data protection formats Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF
This slide showcases BYOD trust model architecture three stage process, it concentrates on securing resource access independent of network location, subject, or asset. It also includes phases such as authentication, record keeping. evidence collection , etc. Persuade your audience using this Bring Your Own Device Security Policy Trust Model Architecture Three Stage Process Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Record Keeping, Evidence Collection, Authentication . Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home