Security Strategy

Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF
Find highly impressive Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Use Cases Of Cloud Access Security Broker Ppt PowerPoint Presentation Diagram Graph Charts PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Manpower Corporate Security Business Profile Mission Vision And Core Values Professional PDF
This slide highlights the security company long term and short term objectives which includes trust, collaboration, service, and innovation as base of core values. Presenting Manpower Corporate Security Business Profile Mission Vision And Core Values Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Mission, Vision, Core Values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF
Introducing our well designed Icons Slide For SDN Security Architecture Ppt PowerPoint Presentation File Model PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Icons Slide Security Software Company Investor Funding Elevator Pitch Deck Elements PDF
Presenting our innovatively structured Icons Slide Security Software Company Investor Funding Elevator Pitch Deck Elements PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF
Introducing our well designed Icons Slide Development And Integration Of Cyber Security Incident Administration Slides PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Cyber Risk Dashboard With Current Risks And Security Service Formats PDF
The following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Pitch your topic with ease and precision using this cyber risk dashboard with current risks and security service formats pdf. This layout presents information on current threats, current risks, regulation and policy coverage. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Workforce Security Realization Coaching Plan Icons Slide Ppt Ideas Topics PDF
Introducing our well-designed workforce security realization coaching plan icons slide ppt ideas topics pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.

Data Security Methods With Disaster Recovery Ppt PowerPoint Presentation Pictures Vector
Presenting this set of slides with name data security methods with disaster recovery ppt powerpoint presentation pictures vector. This is a five stage process. The stages in this process are data deduplication, disaster recovery, the encryption algorithm, disk mirroring and storage replication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Phase 3 Respond To Cloud Protection Issues Cloud Computing Security IT Ppt Gallery Rules PDF
This slide represents phase 3 of cloud security, such as respond to cloud protection issues. It includes an advanced authentication process, manages cloud access standards when new services come up, and eliminates malware from cloud services. Deliver and pitch your topic in the best possible manner with this phase 3 respond to cloud protection issues cloud computing security it ppt gallery rules pdf. Use them to share invaluable insights on authentication process, service, web policies and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
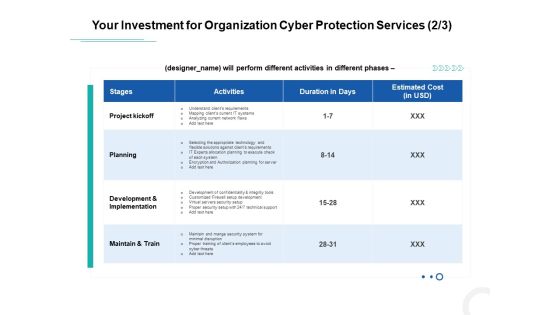
Develop Corporate Cyber Security Risk Mitigation Plan Your Investment For Organization Cyber Protection Service Mockup PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan your investment for organization cyber protection service mockup pdf bundle. Topics like project kickoff, planning, development and implementation, maintain and train can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Develop Corporate Cyber Security Risk Mitigation Plan Contact Us For Organization Cyber Protection Services Portrait PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan contact us for organization cyber protection services portrait pdf bundle. Topics like contact us, organization, cyber protection services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Develop Corporate Cyber Security Risk Mitigation Plan Mode Communication Organization Protection Services Introduction PDF
Deliver an awe-inspiring pitch with this creative develop corporate cyber security risk mitigation plan mode communication organization protection services introduction pdf bundle. Topics like communicate medium, weekly calls, monthly catch up, review sessions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying Cyber Security Incident Response Administration Cyber Supply Chain Risk Management Dashboard Themes PDF today and make your presentation stand out from the rest.
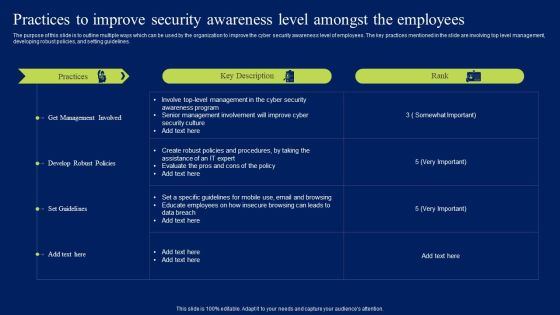
Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF
The purpose of this slide is to outline multiple ways which can be used by the organization to improve the cyber security awareness level of employees. The key practices mentioned in the slide are involving top level management, developing robust policies, and setting guidelines. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Practices To Improve Security Awareness Level Amongst The Employees Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this Key Security Considerations For 5G For Threat Handling 5G Network Architecture Instructions Diagrams PDF. Use them to share invaluable insights on Nodes Authentication, Rule Consistency, Policy Enforcement and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
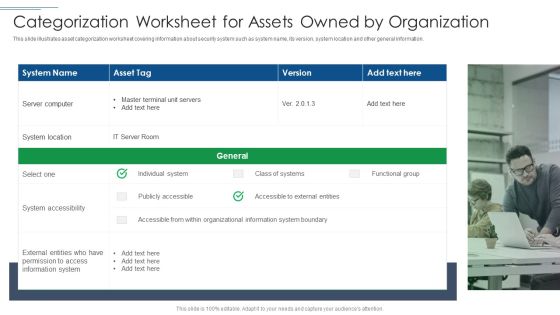
IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Presenting IT Security Risk Management Approach Introduction Categorization Worksheet For Assets Owned By Organization Portrait PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like System Location, System Accessibility, Information System. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Icon Slide For Security Control Techniques For Real Estate Project Clipart PDF
Presenting our innovatively structured Icon Slide For Security Control Techniques For Real Estate Project Clipart PDF set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF
Introducing our well designed Icons Slide For Comprehensive Guide For Ensuring IT Infrastructure Security Inspiration PDF set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
Guidelines To Create An Advanced Security Management Plan Comparison Template PDF
This is a guidelines to create an advanced security management plan comparison template pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like comparison. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF
This is a Agenda For Information Security Risk Evaluation And Administration Plan Pictures PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Agenda. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Icons PDF
Presenting 3 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Business Goals, Management Program, Continuously Improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda For Information Systems Security And Risk Management Plan Designs PDF
Find a pre-designed and impeccable Agenda For Information Systems Security And Risk Management Plan Designs PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

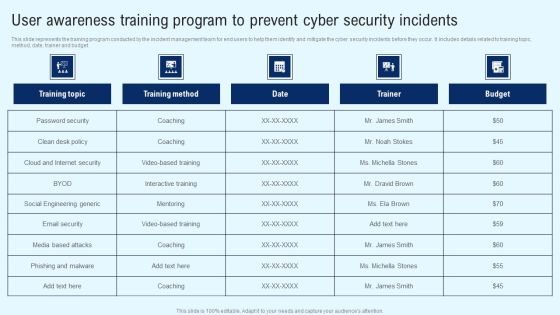
User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. If you are looking for a format to display your unique thoughts, then the professionally designed User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download User Awareness Training Program To Prevent Cyber Security Incidents Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.
Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

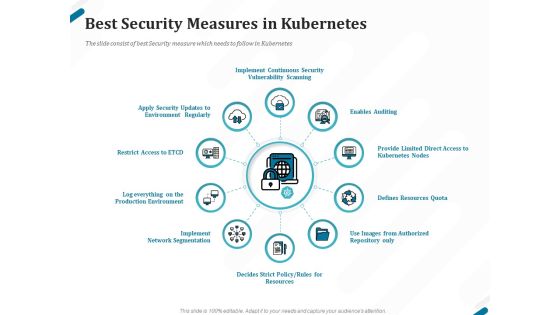
Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
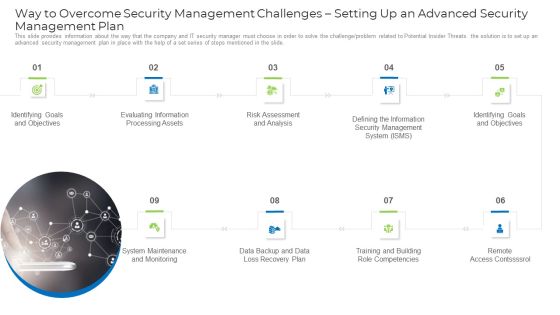
Implementing Safety Administration Initiative For Risk Mitigation Way To Overcome Security Demonstration PDF
This slide provides information about the way that the company and IT security manager must choose in order to solve the challenge or problem related to Potential Insider Threats. the solution is to set up an advanced security management plan in place with the help of a set series of steps mentioned in the slide. This is a implementing safety administration initiative for risk mitigation way to overcome security demonstration pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like goals, information, risk, analysis, management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Mobile Device Management For Android Platform Business Mobile Device Security Management Graphics PDF
This slide provides information regarding mobile device management for android platform with device settings policy, device security settings, etc. Slidegeeks is here to make your presentations a breeze with Mobile Device Management For Android Platform Business Mobile Device Security Management Graphics PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
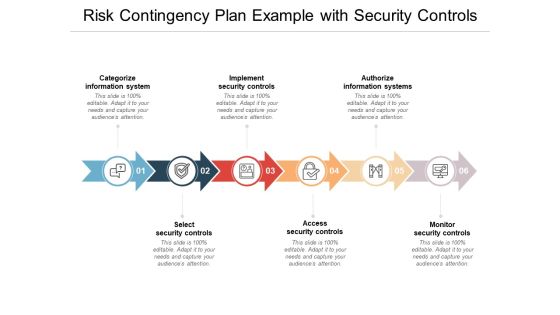
Risk Contingency Plan Example With Security Controls Ppt PowerPoint Presentation File Outline
Presenting this set of slides with name risk contingency plan example with security controls ppt powerpoint presentation file outline. This is a six stage process. The stages in this process are risk framework, risk management, planning process. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling 30 60 90 Days Plan Ppt File Templates PDF
Presenting this set of slides with name computer security incident handling 30 60 90 days plan ppt file templates pdf. This is a three stage process. The stages in this process are 30 60 90 days plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework 30 60 90 Days Plan Ppt PowerPoint Presentation Summary Background Image PDF
Presenting this set of slides with name cyber security implementation framework 30 60 90 days plan ppt powerpoint presentation summary background image pdf. This is a three stage process. The stages in this process are 30 60 90 days plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Cybersecurity Management Action Plan Risk Ppt Icon Layout PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity management action plan risk ppt icon layout pdf. The topics discussed in these slides are risk identification, risk treatment, plan, action, risk owner. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF
The following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Create an editable Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Organize Cyber Security Training For Employees Regularly Ppt PowerPoint Presentation File Diagrams PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF
This slide outlines the Leading cloud access security broker platforms. The purpose of this slide is to highlight the leading CASB platforms, including G-suite, office 365, and Amazon Web Services, and it also represents the benefits and features of these cloud platforms. Are you searching for a Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Leading Cloud Access Security Broker Platforms Ppt PowerPoint Presentation File Styles PDF from Slidegeeks today.

Cyber Security For Your Organization Backup Maintenance Recovery Budget Planning Ppt Inspiration Slide Portrait PDF
Presenting this set of slides with name cyber security for your organization backup maintenance recovery budget planning ppt inspiration slide portrait pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, travel shipping costs, labor contractor costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Backup Maintenance Recovery Budget Planning Professional PDF
Presenting this set of slides with name computer security incident handling backup maintenance recovery budget planning professional pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, testing costs, supply costs, labor or contractor costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Contingency Plan Business Impact Analysis Rules PDF
Presenting this set of slides with name computer security incident handling cybersecurity contingency plan business impact analysis rules pdf. The topics discussed in these slides are business processes, vital resources, impact, recovery priorities, max allowable outage time. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Security Incident Handling Cybersecurity Risk Management Action Plan Diagrams PDF
Presenting this set of slides with name computer security incident handling cybersecurity risk management action plan diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason for risk rating, action, required resources, responsible person, duration, communication. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Cybersecurity Contingency Plan Business Impact Analysis Icons PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity contingency plan business impact analysis icons pdf. The topics discussed in these slides are assign recovery priorities, determining vital it resources, determining issues impacts and acceptable outage time, vital resources, recovery priorities. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Cybersecurity Risk Management Action Plan Potential Diagrams PDF
Presenting this set of slides with name cyber security implementation framework cybersecurity risk management action plan potential diagrams pdf. The topics discussed in these slides are potential risk, risk level, reason risk rating, action, required resources, responsible person. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Backup Maintenance Recovery Budget Planning Clipart PDF
Presenting this set of slides with name cyber security implementation framework backup maintenance recovery budget planning clipart pdf. The topics discussed in these slides are vendor costs, hardware costs, software costs, testing costs, supply costs. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Icons Slide For Develop A Proposal For Corporate Cyber Security And Risk Mitigation Plan Graphics PDF
Presenting our innovatively-structured icons slide for develop a proposal for corporate cyber security and risk mitigation plan graphics pdf set of slides. The slides contain a hundred percent editable icons. You can replace these icons without any inconvenience. Therefore, pick this set of slides and create a striking presentation.
Develop Corporate Cyber Security Risk Mitigation Plan Organization Mission And Vision Statement Download PDF
Presenting develop corporate cyber security risk mitigation plan organization mission and vision statement download pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like vision, mission. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Governance Plan Framework With Security And Auditing Ppt PowerPoint Presentation File Template PDF
Presenting data governance plan framework with security and auditing ppt powerpoint presentation file template pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including data architecture, data quality, change management and deployment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
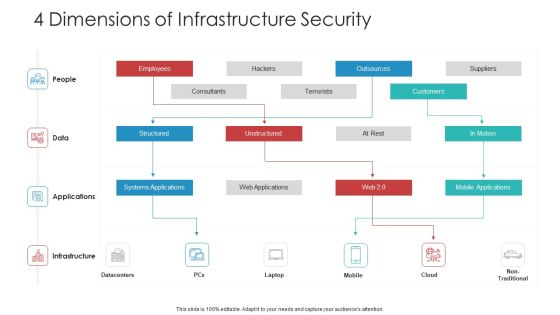
Landscape Architecture Planning And Management 4 Dimensions Of Infrastructure Security Sample PDF
Deliver an awe inspiring pitch with this creative landscape architecture planning and management 4 dimensions of infrastructure security sample pdf bundle. Topics like people, data, applications, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Guidelines To Create An Advanced Security Management Plan Roadmap Sample PDF
This is a guidelines to create an advanced security management plan roadmap sample pdf template with various stages. Focus and dispense information on five tages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF
The purpose of this slide is to outline a comprehensive assessment test which can be used by the trainer to evaluate the effectiveness of cyber security training plan. The questions covered in the slide is related to spam, ways to protect from cyberbullying etc. Create an editable Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre-designed presentation templates help save time. Organizing Security Awareness Assessment Test To Measure Effectiveness Of Training Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Organizing Security Awareness In House Training Schedule We Will Implement Background PDF
The purpose of this slide is to exhibit a comprehensive cyber security awareness training plan for the stakeholders. Information covered in this slide is related to malware, social engineering attack, business email compromise, ransomware, password attack, crypto-jacking and iot-based attack. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Organizing Security Awareness In House Training Schedule We Will Implement Background PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Organizing Security Awareness In House Training Schedule We Will Implement Background PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
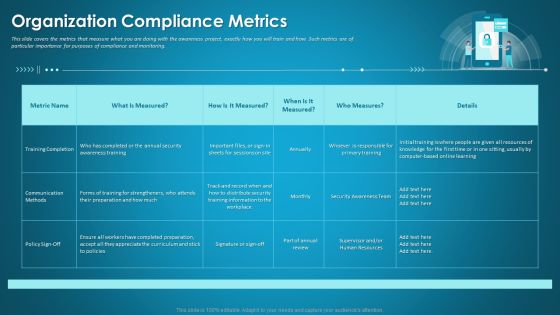
Organizational Network Security Awareness Staff Learning Organization Compliance Metrics Introduction PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver an awe inspiring pitch with this creative organizational network security awareness staff learning organization compliance metrics introduction pdf bundle. Topics like training completion, communication methods, security training information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Are you searching for a Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort youve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Ai To Enhance Role Of Cyber Security In Manufacturing Automation Background PDF from Slidegeeks today.

Folder And Alarm Clock Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212.Download and present our Time Planning PowerPoint Templates because the vision of being the market leader is clear to you. Download our Internet PowerPoint Templates because there are a bucketful of brilliant ideas swirling around within your group. Download our Computer PowerPoint Templates because you can Transmit your thoughts via our slides and proud your team to action. Download and present our Success PowerPoint Templates because the success of your venture depends on the performance of every team member. Present our Business PowerPoint Templates because everybody knows The world over it is a priority for many. Along with it there are so many oppurtunities waiting to be utilised.Use these PowerPoint slides for presentations relating to Alarm clock and folder, business, time planning, internet, computer, success. The prominent colors used in the PowerPoint template are Red, Yellow, White. Professionals tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Stylish. Use our folder PowerPoint templates and PPT Slides are Fantastic. We assure you our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Efficient. We assure you our time PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy. Presenters tell us our Folder And Alarm Clock Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Reminiscent. PowerPoint presentation experts tell us our business PowerPoint templates and PPT Slides are Cheerful.

Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF
This slide covers cyber security incident response KPI dashboard. It involves details such as intent alarm, event trend sources, event trend, sensor activity, major operating systems and asset information. Pitch your topic with ease and precision using this Managing Cyber Security Incident Response KPI Dashboard Ppt Layouts Shapes PDF. This layout presents information on Top Alarms Method, Alarms Intent, Timely Event Trend. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
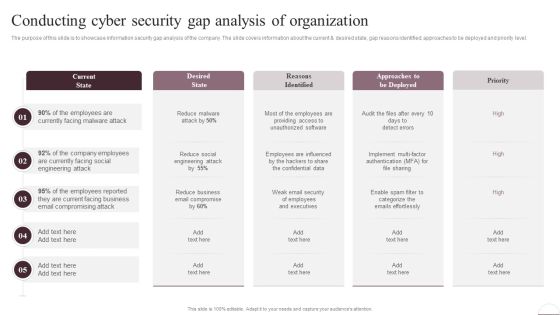
Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Prevention Of Information Conducting Cyber Security Gap Analysis Of Organization Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today
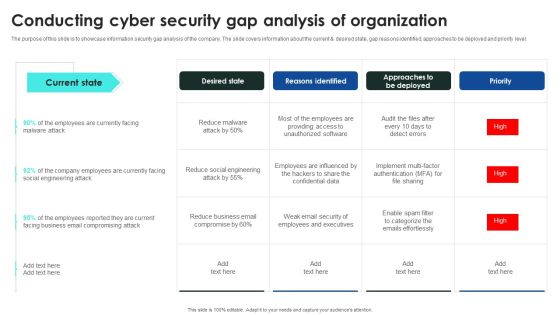
Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF
The purpose of this slide is to showcase information security gap analysis of the company. The slide covers information about the current and desired state, gap reasons identified, approaches to be deployed and priority level. Get a simple yet stunning designed Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cybersecurity Awareness Program To Prevent Attacks Conducting Cyber Security Gap Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF
This slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date. Pitch your topic with ease and precision using this Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF. This layout presents information on Response Planning, Risk Assessment, Response Communication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc.Want to ace your presentation in front of a live audience Our Ensuring Mobile Device Compliance And Policy Enforcement Business Mobile Device Security Formats PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.
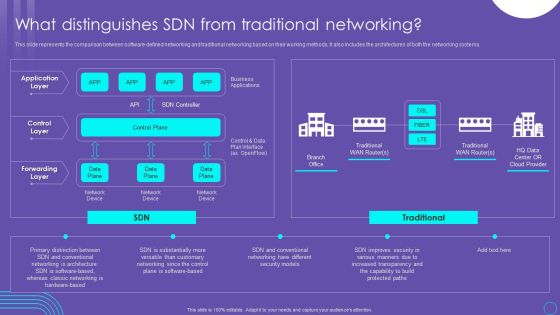
SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF
This slide represents the comparison between software defined networking and traditional networking based on their working methods. It also includes the architectures of both the networking systems. Get a simple yet stunning designed SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit SDN Security Architecture What Distinguishes SDN From Traditional Networking Microsoft PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

 Home
Home