Security Services

Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF
This slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Execution Of ICT Strategic Plan Data Encryption Model For Effective Information Security Guidelines PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.
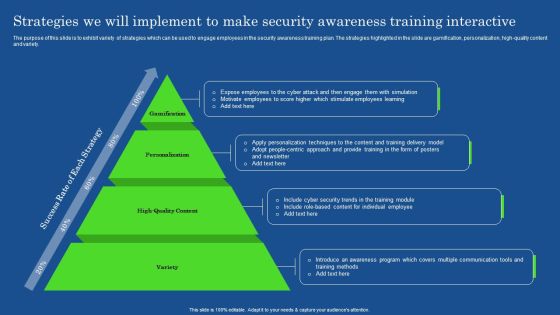
Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. Explore a selection of the finest Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Strategies We Will Implement To Make Security Awareness Training Interactive Structure PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF
This slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF can be your best option for delivering a presentation. Represent everything in detail using Integrating Chatgpt With Other Systems Security And Compliance Management Themes PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF
This slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Incident Response Techniques Deployement Cyber Security Incident Management Checklist After An Incident Summary PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Incident Response Techniques Deployement Cyber Security Incident Management Checklist After An Incident Summary PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF
This slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident Management before the occurrence of the incident. This modern and well arranged Incident Response Techniques Deployement Cyber Security Incident Management Checklist Before An Incident Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Incident Response Techniques Deployement Cyber Security Incident Response Plan Timeline Pictures PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Explore a selection of the finest Incident Response Techniques Deployement Cyber Security Incident Response Plan Timeline Pictures PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Incident Response Techniques Deployement Cyber Security Incident Response Plan Timeline Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Get a simple yet stunning designed IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Reducing Costs And Management Tips How Management Enables Effective Corporate Security Governance Mockup PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF
This slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF can be your best option for delivering a presentation. Represent everything in detail using Timeline To Implement Cloud Access Security Broker Ppt Visual Aids Example File PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Casb Overview Ppt Professional Design Inspiration PDF today and make your presentation stand out from the rest.

Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF
This slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Implementation Models Ppt Slides Visual Aids PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
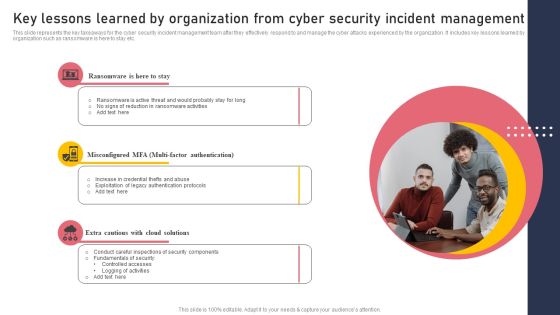
Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Key Lessons Learned By Organization From Cyber Security Incident Management Graphics PDF today and make your presentation stand out from the rest.

CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF
This slide represents the key metrics dashboard representing details related to management of cyber security incidents by an enterprise. It includes key performance indicators such as risk analysis progress, risk rating breakdown etc. Are you searching for a CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download CYBER Security Breache Response Strategy Enterprise Cyber Risk Management Dashboard Summary PDF from Slidegeeks today.

CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF
This slide represents the stages of the process which aims towards minimizing the impact of cyber security incidents on operational functions. It includes cyber security incident management stages such as plan and prepare, detect and report etc. Retrieve professionally designed CYBER Security Breache Response Strategy Five Phases Of Cybersecurity Incident Management Structure PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Get a simple yet stunning designed Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Get a simple yet stunning designed Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. If you are looking for a format to display your unique thoughts, then the professionally designed Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Chief Information Officers Guide On Technology Plan Information Security And Governance Formats PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Dashboard To Track IT Security Incidents Prevailing Across Firm Infographics PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF
This slide outlines the critical outcomes that are handled by the security operations team. The purpose of this slide is to demonstrate the various key outcomes, their activities, responsible person and remarks. The main outcomes include incident management, incident preparation and threat intelligence. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cybersecurity Operations Cybersecops Key Outcomes Manage By Security Operations Demonstration PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Dashboard To Track IT Security Incidents Prevailing Across Firm Demonstration PDF today and make your presentation stand out from the rest

Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. Find highly impressive Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Transforming Manufacturing With Automation Role Of Cyber Security In Manufacturing Rules PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF
This slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Get a simple yet stunning designed Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cloud Access Security Broker Architectural Components Ppt PowerPoint Presentation File Show PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF
This slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Find highly impressive Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Working Process Ppt PowerPoint Presentation File Infographic Template PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF
This slide gives an overview of cloud access security broker architecture. The purpose of this slide is to highlight architecture and its main components covering immediate enterprise core, secondary enterprise core, PaaS, SaaS, IaaS, connectivity gateway, security and compliance rules, etc. Slidegeeks has constructed Overview Of Cloud Access Security Broker Architecture Ppt PowerPoint Presentation Diagram Lists PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF
This slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Cloud Access Security Broker CASB Introduction Ppt PowerPoint Presentation File Portfolio PDF.

Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.

Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF
This slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the Benefits Of Cloud Access Security Broker Ppt PowerPoint Presentation File Model PDF.

Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Security Management Plan Steps In Detail Training And Building Role Competencies Infographics PDF
This is a security management plan steps in detail training and building role competencies infographics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like responsible for conducting, responsible for managing, project management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF
Find a pre designed and impeccable Agenda For Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Template PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF
Boost your pitch with our creative Building Security Awareness Among Workforce To Minimize Cybersecurity Threats Table Of Contents Download PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Piggy Bank Saving And Security Real Estate PowerPoint Templates Ppt Backgrounds For Slides 1112
We present our Piggy Bank Saving And Security Real Estate PowerPoint Templates PPT Backgrounds For Slides 1112.Download our Business PowerPoint Templates because you can Lead your flock steadily to greater heights. Look around at the vast potential of achievement around you. Download and present our Money PowerPoint Templates because that was the well known Musketeers call. Download and present our Finance PowerPoint Templates because it describes the benefits of healthy food habits and lifestyles in respect of vital organs of the human anatomy. Present our Real estate PowerPoint Templates because this slide helps you to give your team an overview of your capability and insight into the minute details of the overall picture highlighting the interdependence at every operational level. Download and present our Success PowerPoint Templates because your quest has taken you well onto the path of success.Use these PowerPoint slides for presentations relating to Piggy bank saving and security, business, money, finance, real estate, success. The prominent colors used in the PowerPoint template are Brown, Black, Red. People tell us our Piggy Bank Saving And Security Real Estate PowerPoint Templates PPT Backgrounds For Slides 1112 are Pretty. Presenters tell us our money PowerPoint templates and PPT Slides are Lush. Presenters tell us our Piggy Bank Saving And Security Real Estate PowerPoint Templates PPT Backgrounds For Slides 1112 are Elegant. Use our saving PowerPoint templates and PPT Slides are incredible easy to use. We assure you our Piggy Bank Saving And Security Real Estate PowerPoint Templates PPT Backgrounds For Slides 1112 are Nice. The feedback we get is that our security PowerPoint templates and PPT Slides are Breathtaking.
Workforce Security Realization Coaching Plan Different Training Formats For Different Organizational Levels Icons PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. Presenting workforce security realization coaching plan different training formats for different organizational levels icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like interactive protection simulation, cybersecurity for it online, automated security awareness platform. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
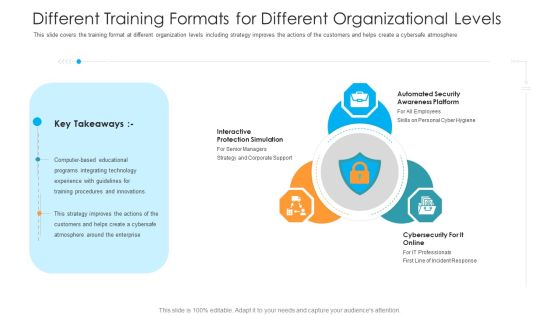
Different Training Formats For Different Organizational Levels Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. This is a different training formats for different organizational levels hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like interactive protection simulation, automated security awareness platform, cybersecurity for it online. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF
This slide shows information technology company flowchart indicating insider threat discovery. It provides information such as user request for service, authentication check, starting session, role based access control RBAC, permission checks, etc. Persuade your audience using this Insider Threat In Cyber Security Discovery Flowchart Of IT Company Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Terminate Session, Allow Access, Authentication Service. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Evolving BI Infrastructure Enabling Data Security Risk Management Action Plan Background PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative evolving bi infrastructure enabling data security risk management action plan background pdf bundle. Topics like potential risk, risk level, action, duration, communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
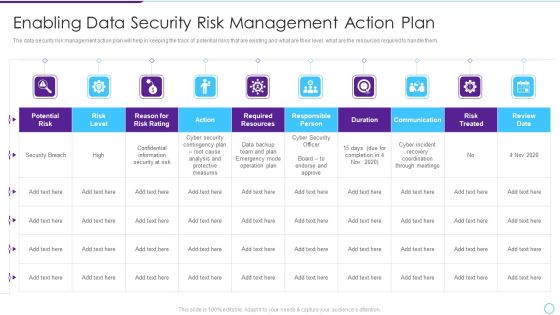
Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Intelligent Infrastructure Enabling Data Security Risk Management Action Plan Graphics PDF bundle. Topics like Potential Risk, Risk Level, Action, Risk Treated, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
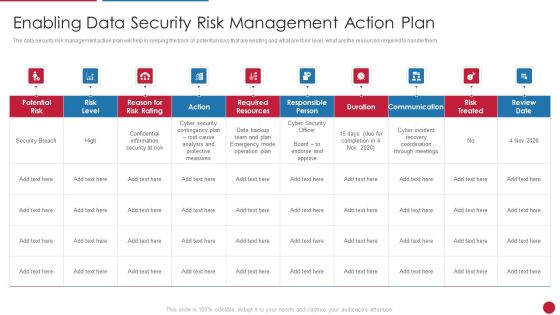
Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Facilitating IT Intelligence Architecture Enabling Data Security Risk Management Action Plan Themes PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
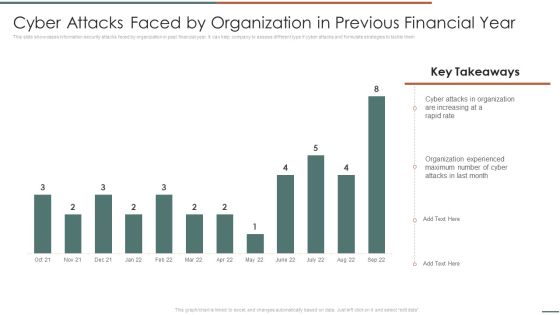
Information Security Risk Evaluation Cyber Attacks Faced By Organization In Previous Financial Year Template PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type if cyber attacks and formulate strategies to tackle them.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Cyber Attacks Faced By Organization In Previous Financial Year Template PDF. Use them to share invaluable insights on Attacks In Organization, Organization Experienced, Attacks Last and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF
This slide shows risk landscape dashboard for cyber security program management which contains threat level by month, current threat posture, threats by source, threats by owner, risks by threat and threat register. This can help businesses in effective management of risks and counter measures. Showcasing this set of slides titled Business Threats Landscape Dashboard For Cyber Security Program Management Ppt Gallery Images PDF. The topics addressed in these templates are Current Threat Posture, Threat Register, Source. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF
This slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Welcome to our selection of the IT System Risk Management Guide Prioritized Cyber Security Threats With Risk Mitigation Plan Ideas PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
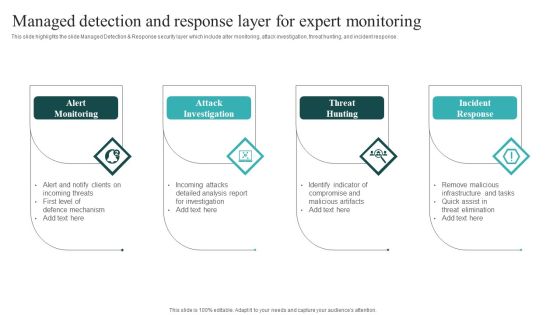
IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF
This slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. IT Security Automation Systems Guide Managed Detection And Response Layer For Expert Monitoring Download PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

IT Policies And Procedures Information Security Policy For Employees Download PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Policies And Procedures Information Security Policy For Employees Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Policies And Procedures Information Security Policy For Employees Download PDF.

ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF
This slide displays the steps that helps to stay away from the threats of cyber security and makes clients feel safe from the cyber attacks. The steps includes Identifying digital assets, audit data, perform assessments, analyze risk level, establish committee ,etc. Persuade your audience using this ERM Plan For Cyber Security Ppt PowerPoint Presentation File Ideas PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Establish Risk Assessment Committee, Create Response Plan, Educate Employees On Policies. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Want to ace your presentation in front of a live audience Our Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Analysing The Impact Of Security Threats On Organization Cybersecurity Risk Assessment Elements PDF

Prevention Of Information Comparative Assessment Of Security Awareness Online Courses Icons PDF
The purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Want to ace your presentation in front of a live audience Our Prevention Of Information Comparative Assessment Of Security Awareness Online Courses Icons PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF
Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Table Of Contents For Cyber Physical System To Enhance Security Portrait PDF.
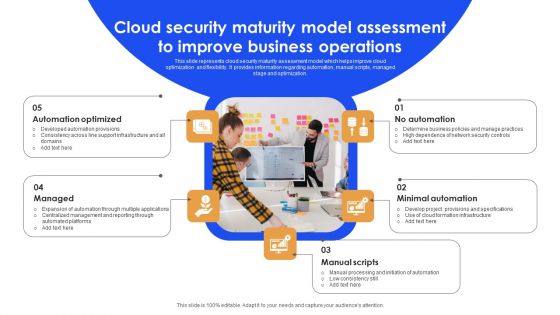
Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF
This slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Persuade your audience using this Cloud Security Maturity Model Assessment To Improve Business Operations Background PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Automation Optimized, Minimal Automation, Manual Scripts. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Want to ace your presentation in front of a live audience Our Intelligent Manufacturing Managing Cyber Security In Manufacturing 30 Days Plan Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF
This slide illustrates malware analysis phases which help security analysts in identifying and understanding depth of sources of threats. Stages covered in this slide are static properties, interactive behavior, full automated analysis and manual code reversing. Presenting Key Stages Of Malware Assessment Utilized By Security Analysts Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Static Properties Analysis, Interactive Behavior Analysis, Full Automated Analysis. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
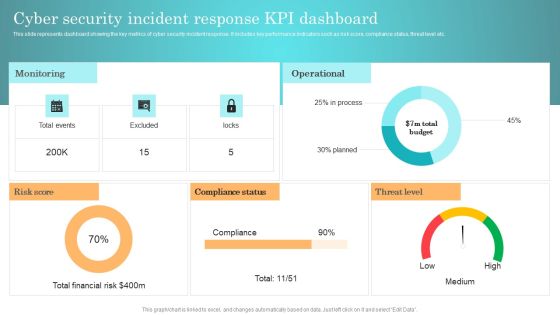
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF
The following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Want to ace your presentation in front of a live audience Our Prioritize Cyber Security Risk With Severity Matrix Ppt PowerPoint Presentation File Icon PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF
This slide shows the challenges faced by enterprise due to increase in cyber attacks. It includes cyber security incidents experienced by the organization such as cloud computing issues, theft of sensitive information, ransomware attacks etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Implementing Cyber Security Incident Key Issues Faced By Organization Due To Cybersecurity Brochure PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Enhancing Information Technology With Strategic Information Security And Governance Icons PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Enhancing Information Technology With Strategic Information Security And Governance Icons PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF
This slide showcases steps to enhance bring your own device security to protect devices. It also includes steps such as cloud networks, password protection, routine back ups, data access, etc. Persuade your audience using this Steps To Enhance Bring Your Own Device Security Policy In Devices Icons PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Password Protection, Data Access, Antivirus Software. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF
This slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. This is a IT Security Automation Tools Integration Extended Detection And Response For Endpoint Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Endpoint Protection, Network Protection, User Protection, Deception. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF
This slide signifies the three stage cyber security program to improve data protection. It covers information about steps like prevention, response and remediation. Persuade your audience using this 3 Stage Plan Cyber Security Plan For Data Protection Ppt Icon Picture PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Prevention, Response, Remediation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. This is a New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Applicable, Enforcement, Develop Good. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF
Get a simple yet stunning designed Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security Control Techniques For Real Estate Project Personal Protective Equipment For Construction Themes PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.
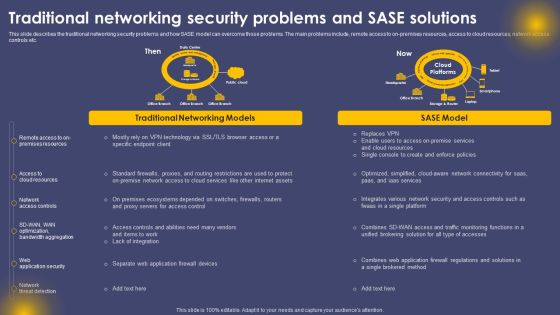
Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.

Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF
If you are looking for a format to display your unique thoughts, then the professionally designed Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Agenda For Safeguarding Network With SDN Security Ppt Layouts Information PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF
The following slide illustrates the seven pillars of SaaS security to protect organizations from cyber attack and data breaches. It includes elements such as access management, network control, VM management, data protection, incident management etc. Presenting Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including VM Management, Data Protection, Network Control, Perimeter Network Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Boost your pitch with our creative Cybersecurity Guidelines IT Overview Of Network Security Policy For Workers Portrait PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
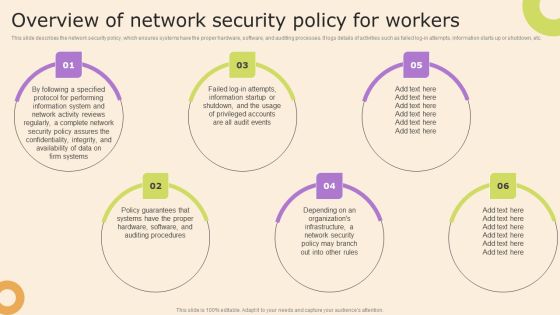
Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF
This slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Strategy To Provide Layered Security Across Networks Brochure PDF. Use them to share invaluable insights on Formulate Network, Access Rules, Particular Applications, Bandwidth Access Limitation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Role Of ZTNA To Improve Business Operations And Security Slides PDF
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. There are so many reasons you need a Role Of ZTNA To Improve Business Operations And Security Slides PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CPS Security And Privacy Life Cycle Ppt PowerPoint Presentation File Files PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF
The following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Deliver and pitch your topic in the best possible manner with this Supply Chain Management Iot Security Lock For Safe Fleet Management Download PDF. Use them to share invaluable insights on Key Applications, Potential Impact, Multiple Positioning Methods and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Based Email Security Market Report Issues Faced By Companies Data Ppt Icon Templates PDF
Various issues faced by the end user in E Mail marketing Industry are shown in this slide. Presenting cloud based email security market report issues faced by companies data ppt icon templates pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
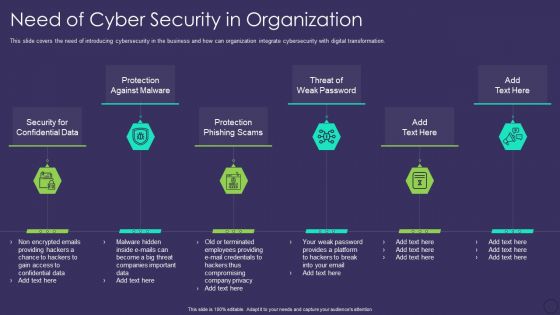
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
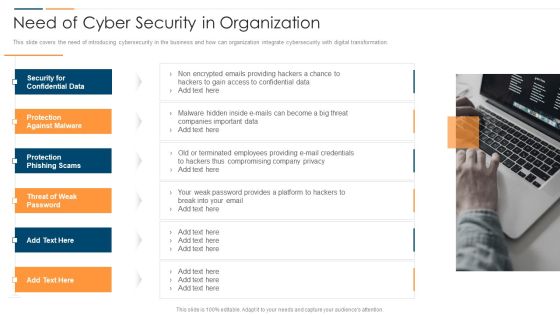
Revolution In Online Business Need Of Cyber Security In Organization Professional PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. This is a Revolution In Online Business Need Of Cyber Security In Organization Professional PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Confidential Data, Protection Against Malware, Protection Phishing Scams, Threat Weak Password. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
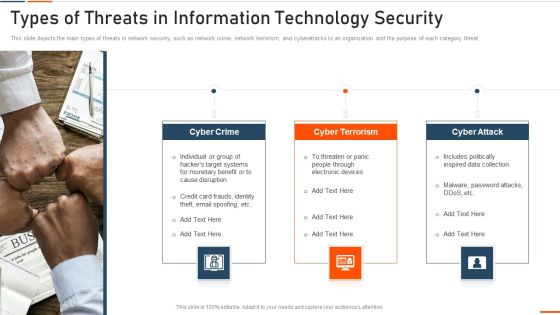
Types Of Threats In Information Technology Security Ppt Slides Example File PDF
This slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a types of threats in information technology security ppt slides example file pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Certified Information Systems Security Collection Of Information Technology Certifications Download PDF
This slide covers CISSP certification details such as what is the CISSP how to become certified, how to prepare for CISSP and why to get CISSP certifications. Presenting certified information systems security collection of information technology certifications download pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like information systems, network security, information network, organization, average. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
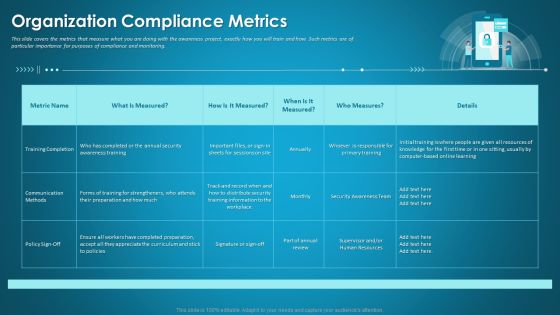
Organizational Network Security Awareness Staff Learning Organization Compliance Metrics Introduction PDF
This slide covers the metrics that measure what you are doing with the awareness project, exactly how you will train and how. Such metrics are of particular importance for purposes of compliance and monitoring. Deliver an awe inspiring pitch with this creative organizational network security awareness staff learning organization compliance metrics introduction pdf bundle. Topics like training completion, communication methods, security training information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF
This slide covers cyber security incident response proposition. The purpose of this plan is to provide direction of action to the whole response team. It includes elements such as list of incidents, their responses, responsible person and resolve date. Showcasing this set of slides titled Cyber Security Cases Action Response Plan Ppt PowerPoint Presentation File Visuals PDF. The topics addressed in these templates are Data Stealing Through, Network Monitoring, Server Crashing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Challenge And Solutions 2 Cloud Threats And Security Ppt Styles Graphics PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt styles graphics pdf bundle. Topics like problem, recommendation, potential cloud threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Steps To Ensure Machine Driven Learning Security Ppt Inspiration Structure PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Presenting steps to ensure machine driven learning security ppt inspiration structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like system, management, development, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF
The following slide depicts the SaaS security process to acknowledge the gap and have proactive approach. It mainly constitutes of three phases discover, monitor and protect. Persuade your audience using this Key Steps Of Saas Cloud Security Process Ppt PowerPoint Presentation Gallery Design Ideas PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Discover, Monitor, Protect, Identify Utility, Assess Risk. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Real Time Assessment Of Security Threats Next Evolution Of SIEM Software Sample PDF
This slide focuses on the upcoming evolution of SIEM software which covers SIEM foundation, threat intelligence, user entity and behavior analytics, network traffic analysis, endpoint monitoring, and SOAR. This is a real time assessment of security threats next evolution of siem software sample pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network traffic analysis, endpoint monitoring, threat intelligence, siem foundation, security orchestration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF
This slide shows dashboard for detecting and preventing insider threats. It provides details about antivirus, vector detection, patch, admin access, email security, network and endpoint threat, etc. Pitch your topic with ease and precision using this Insider Threat In Cyber Security Detection And Prevention Dashboard Diagrams PDF. This layout presents information on Active Clients, Network Threat Prevention, Endpoint Threat Prevention. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Understanding The Kubernetes Concepts And Architecture Best Security Measures In Kubernetes Ppt Outline Templates PDF
Presenting this set of slides with name understanding the kubernetes concepts and architecture best security measures in kubernetes ppt outline templates pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Driving Digital Transformation Through Kubernetes And Containers Best Security Measures In Kubernetes Template PDF
Presenting this set of slides with name driving digital transformation through kubernetes and containers best security measures in kubernetes template pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
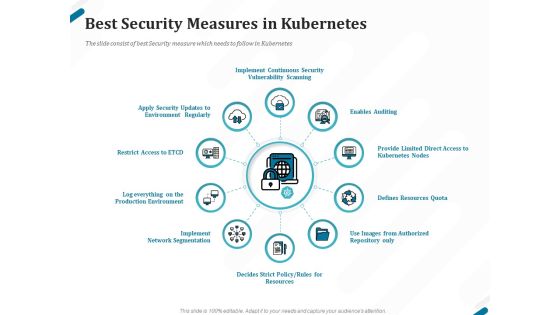
Kubernetes Containers Architecture Overview Best Security Measures In Kubernetes Ppt Pictures File Formats PDF
Presenting this set of slides with name kubernetes containers architecture overview best security measures in kubernetes ppt pictures file formats pdf. This is a ten stage process. The stages in this process are implement continuous security vulnerability scanning, enables auditing, provide limited direct access to kubernetes nodes, defines resources quota, use images from authorized repository only, defines strict policy, rules for resources, implement network segmentation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
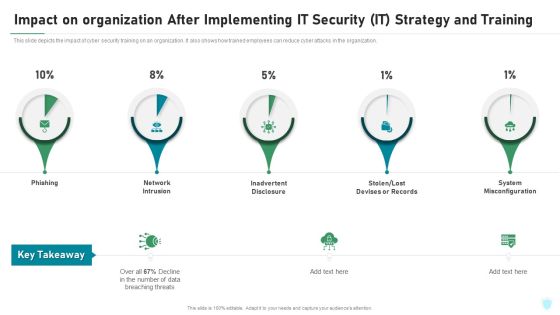
Impact On Organization After Implementing IT Security IT Strategy And Training Ppt File Portrait PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing it security it strategy and training ppt file portrait pdf. Use them to share invaluable insights on phishing, network intrusion, inadvertent disclosure, stolen or lost devises or records, system misconfiguration and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Hardware And Software Update In Company Ppt Outline Graphics Pictures PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a information security hardware and software update in company ppt outline graphics pictures pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like networks, technology, devices, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Hardware And Software Update In Company Portrait PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. This is a desktop security management hardware and software update in company portrait pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like technology, servers, devices, network, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact On Organization After Implementing Computer Security Strategy And Training Ideas PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. This is a impact on organization after implementing computer security strategy and training ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network intrusion, system misconfiguration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
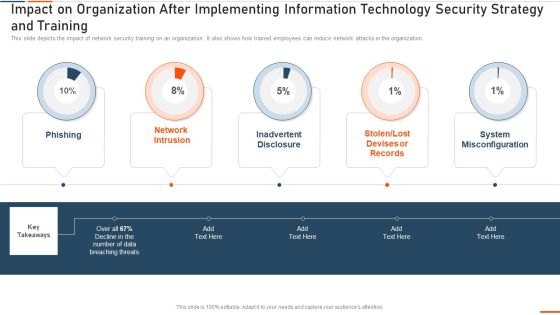
Impact On Organization After Implementing Information Technology Security Ppt Infographic Template Examples PDF
This slide depicts the hardware software update measure under the network security model. It also tells the current status of the devices that need to update in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information technology security ppt infographic template examples pdf. Use them to share invaluable insights on hardware and software update in company and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Impact On Organization After Implementing Information Security Strategy Ppt PowerPoint Presentation Gallery Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this impact on organization after implementing information security strategy ppt powerpoint presentation gallery deck pdf. Use them to share invaluable insights on system misconfiguration, phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Develop Corporate Cyber Security Risk Mitigation Plan Roadmap For Organization Cyber Protection Proposal Summary PDF
Presenting develop corporate cyber security risk mitigation plan roadmap for organization cyber protection proposal summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap, organization cyber protection. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Develop Corporate Cyber Security Risk Mitigation Plan Timeline For Organization Protection Proposal Themes PDF
This is a develop corporate cyber security risk mitigation plan timeline for organization protection proposal themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2019 to 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Existing Channel Development Strategy Formats PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Security And Surveillance Company Profile Existing Channel Development Strategy Formats PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Motion Awareness, Flood Protection, Thermostat Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
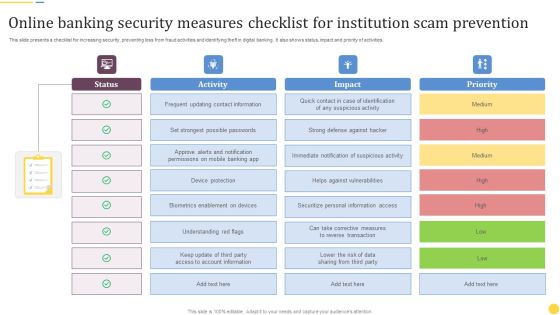
Online Banking Security Measures Checklist For Institution Scam Prevention Formats PDF
This slide presents a checklist for increasing security, preventing loss from fraud activities and identifying theft in digital banking. It also shows status, impact and priority of activities. Pitch your topic with ease and precision using this Online Banking Security Measures Checklist For Institution Scam Prevention Formats PDF. This layout presents information on Frequent Updating, Contact Information, Device Protection. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Deliver and pitch your topic in the best possible manner with this Cyber Intelligent Computing System Steps For CPS Security Strategy Plan Mockup PDF. Use them to share invaluable insights on Gap Analysis, Protect Resources, Communicate Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF
This slide covers framework depicting top risks and threats for IIOT disrupting the operations and processes. It also includes integration of different technologies used to increase the security for IIOT operations such as virtual patching, behaviour analysis, anti malware, risk detection, anti spear phishing, spam protection, etc. Pitch your topic with ease and precision using this Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF. This layout presents information on Operational Technology, IT Business Process, Iot Platform Middleware . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Elements Of IT Security IT End User Education Ppt Model Deck PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a elements of it security it end user education ppt model deck pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hire professional, train often, password protocols, microlearning opportunities, effective training. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
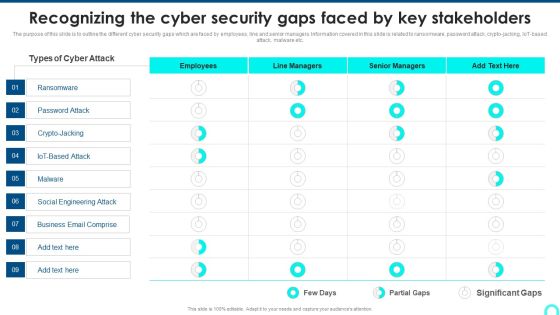
Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Deliver and pitch your topic in the best possible manner with this Recognizing The Cyber Security Gaps Faced By Key Stakeholders Portrait PDF. Use them to share invaluable insights on Ransomware, Engineering Attack, Email Comprise and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF
This slide shows potential threats along with prevention for online business websites that could damage the business and also lose trust of online customers. the certain threats includes direct site attacks, password assault, social engineering and malwares. Showcasing this set of slides titled E Commerce Business Cyber Security Assessment Threats And Solutions Guidelines PDF. The topics addressed in these templates are Business Security Risks, Threat Type, Solutions. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre-designed and impeccable Prevention Of Information Recognizing The Cyber Security Gaps Faced By Key Stakeholders Background PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF
This side showcase the checklist of working condition and firewall security of smart home to know updates of standard devices and their benchmarks. It includes status of devices such as garage locks, remote access, data sharing, door openers, policies of devices and update cycle. Presenting Checklist For Technological Smart Homes Devices And Firewall Security Microsoft PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Devices Firewall, Working Condition, Access Points. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Presenting CRM System Implementation Stages Implementation Steps Enable Data Security Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Marketing Executive, Marketing Intern, Sales Executive. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Presenting Risk Based Procedures To IT Security Threat Drivers And Emerging Technologies Impact On Information PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Internet Of Things, Artificial Intelligence, Human Machine. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
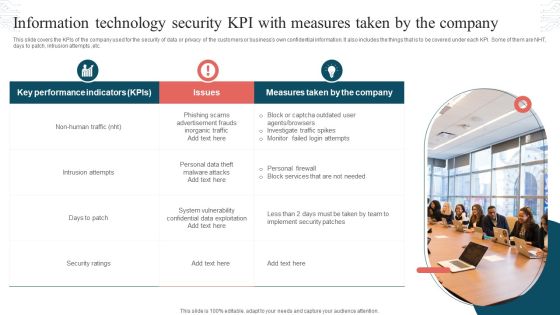
Information Technology Security KPI With Measures Taken By The Company Formats PDF
This slide covers the KPIs of the company used for the security of data or privacy of the customers or businesss own confidential information. It also includes the things that is to be covered under each KPI. Some of them are NHT, days to patch, intrusion attempts ,etc. Presenting Information Technology Security KPI With Measures Taken By The Company Formats PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Key Performance Indicators, Measures Taken, Intrusion Attempts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

3 Months IT Innovation Approach Roadmap For Value And Security Benefit Pictures
We present our 3 months it innovation approach roadmap for value and security benefit pictures. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 3 months it innovation approach roadmap for value and security benefit pictures in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

5 Year IT Innovation Approach Roadmap For Value And Security Benefit Information
We present our 5 year it innovation approach roadmap for value and security benefit information. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 5 year it innovation approach roadmap for value and security benefit information in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

6 Months IT Innovation Approach Roadmap For Value And Security Benefit Pictures
We present our 6 months it innovation approach roadmap for value and security benefit pictures. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 6 months it innovation approach roadmap for value and security benefit pictures in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
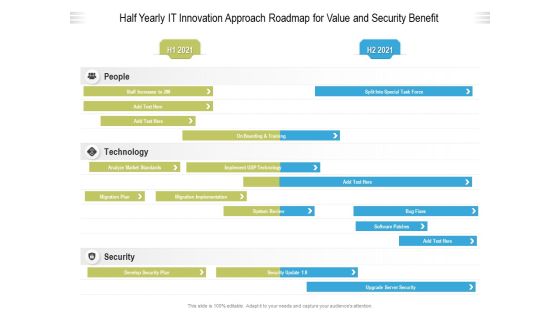
Half Yearly IT Innovation Approach Roadmap For Value And Security Benefit Professional
We present our half yearly it innovation approach roadmap for value and security benefit professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly it innovation approach roadmap for value and security benefit professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Quarterly IT Innovation Approach Roadmap For Value And Security Benefit Elements
We present our quarterly it innovation approach roadmap for value and security benefit elements. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly it innovation approach roadmap for value and security benefit elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Disaster Recuperation Five Years Roadmap To Eradicate Intrusion Professional
We present our cyber security disaster recuperation five years roadmap to eradicate intrusion professional. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched cyber security disaster recuperation five years roadmap to eradicate intrusion professionalin different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Tactic For Process Management For IT Roadmap Five Year Designs
We present our cyber security tactic for process management for it roadmap five year designs. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security tactic for process management for it roadmap five year designs in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Plan Five Years Roadmap With Multiple Phases Microsoft
We present our cloud computing security plan five years roadmap with multiple phases microsoft. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security plan five years roadmap with multiple phases microsoft in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Plan Six Months Roadmap For IT Project Template
We present our cloud computing security plan six months roadmap for it project template. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security plan six months roadmap for it project template in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Plan Three Months Roadmap With Key Enablers Elements
We present our cloud computing security plan three months roadmap with key enablers elements. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security plan three months roadmap with key enablers elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Online Settlement Revolution Payment Security And Fraud Management Solutions Browser Icons PDF
Payment security and fraud management solutions for the user to limit losses while maintain a high level of customer satisfaction. Presenting online settlement revolution payment security and fraud management solutions browser icons pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like costs, process, analytics, development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
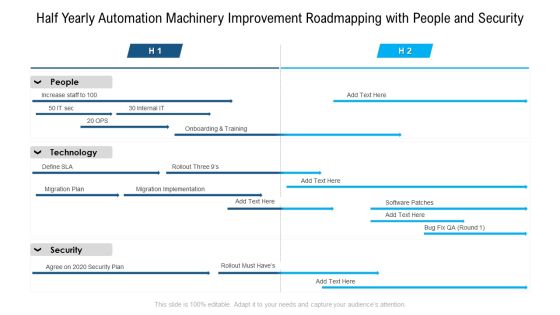
Half Yearly Automation Machinery Improvement Roadmapping With People And Security Topics
We present our half yearly automation machinery improvement roadmapping with people and security topics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly automation machinery improvement roadmapping with people and security topics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
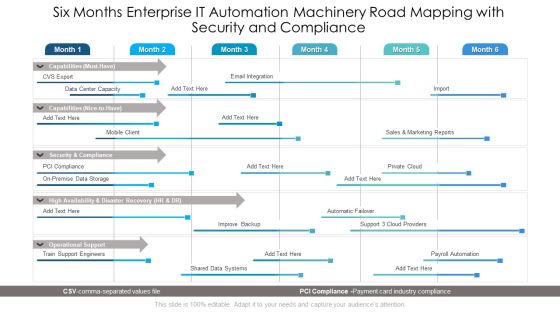
Six Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Professional
We present our six months enterprise it automation machinery road mapping with security and compliance professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise it automation machinery road mapping with security and compliance professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Where Is The Gap In Security Programs Ppt Icon Layout Ideas PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps Presenting where is the gap in security programs ppt icon layout ideas pdf. to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like problems, gap, solution. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Intelligence Framework For Application Consumption Case Study 2 Banks Cyber Security Infrastructure Microsoft PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges. This is a cloud intelligence framework for application consumption case study 2 banks cyber security infrastructure microsoft pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process workflows, industry standard security metrics, implemented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Where Is The Gap In Security Programs Summary PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a data breach prevention recognition where is the gap in security programs summary pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, solutions, gap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Problem Faced By The Organization Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a problem faced by the organization hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, cybersecurity, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Budget For Effective Secops System Management Slides PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this information and technology security operations budget for effective secops system management slides pdf. Use them to share invaluable insights on functional area, software, implement duration, cost of implementation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information And Technology Security Operations Various Metrics To Measure Secops System Performance Mockup PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting information and technology security operations various metrics to measure secops system performance mockup pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
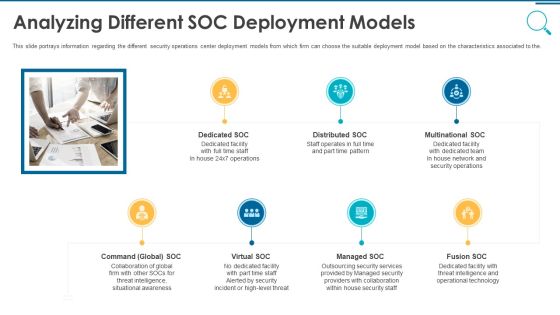
Information And Technology Security Operations Analyzing Different SOC Deployment Models Rules PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a information and technology security operations analyzing different soc deployment models rules pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information And Technology Security Operations Impact Of Successful Implementation Of Secops System Download PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting information and technology security operations impact of successful implementation of secops system download pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information And Technology Security Operations Prerequisites For Effective Secops Implementation Designs PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a information and technology security operations prerequisites for effective secops implementation designs pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Security Solutions Various Metrics To Measure Secops System Performance Portrait PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting organizational security solutions various metrics to measure secops system performance portrait pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
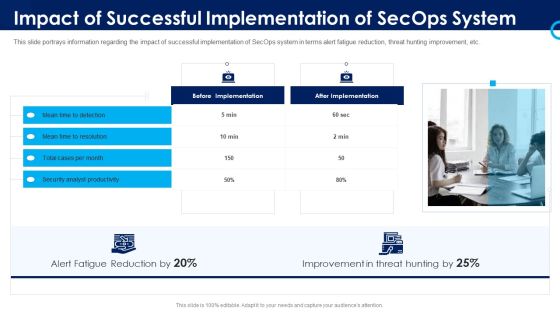
Organizational Security Solutions Impact Of Successful Implementation Of Secops System Designs PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting organizational security solutions impact of successful implementation of secops system designs pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
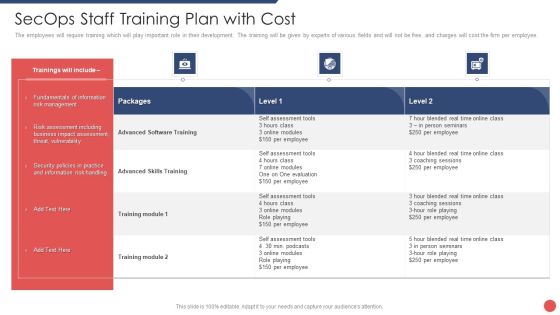
Security Functioning Centre Secops Staff Training Plan With Cost Information PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative security functioning centre secops staff training plan with cost information pdf bundle. Topics like risk assessment, business, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Security Functioning Centre Various Metrics To Measure Secops System Performance Icons PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. This is a security functioning centre various metrics to measure secops system performance icons pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security analysts productivity, escalation breakdown, average time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
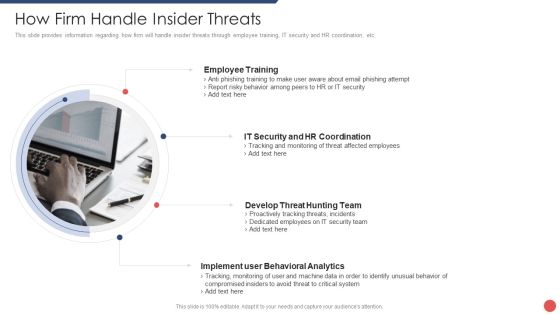
Security Functioning Centre How Firm Handle Insider Threats Ppt Summary Background Image PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security functioning centre how firm handle insider threats ppt summary background image pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Effect After Implementing Cyber Risk Security Awareness Program Ppt Portfolio Example Topics PDF
This slide covers the impact on organization departments of cyber security awareness training program including lowest number of malware attacks by departments. This is a effect after implementing cyber risk security awareness program ppt portfolio example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sales department, accounts department, lowest financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
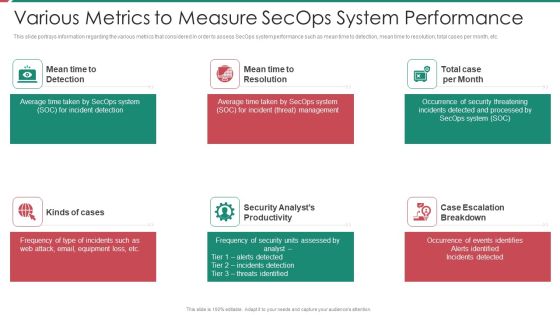
Security And Process Integration Various Metrics To Measure Secops System Performance Introduction PDF
This slide portrays information regarding the various metrics that considered in order to assess SecOps system performance such as mean time to detection, mean time to resolution, total cases per month, etc. Presenting security and process integration various metrics to measure secops system performance introduction pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, analyst, escalation, management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
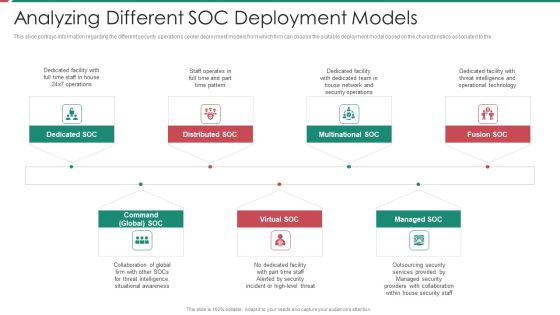
Security And Process Integration Analyzing Different SOC Deployment Models Diagrams PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a security and process integration analyzing different soc deployment models diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
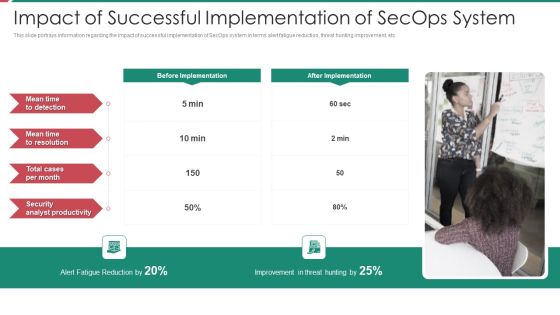
Security And Process Integration Impact Of Successful Implementation Of Secops System Diagrams PDF
This slide portrays information regarding the impact of successful implementation of SecOps system in terms alert fatigue reduction, threat hunting improvement, etc. Presenting security and process integration impact of successful implementation of secops system diagrams pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like security, analyst, improvement, reduction. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Prerequisites For Effective Secops Implementation Microsoft PDF
This slide portrays information regarding the prerequisites that essential for effective implementation of SecOps in terms of development and operations team, etc. This is a security and process integration prerequisites for effective secops implementation microsoft pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like development, data available, security with compliance, operations team. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5 Year Action Plan And Advantage Roadmap For Cyber Security Icons
We present our 5 year action plan and advantage roadmap for cyber security icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 5 year action plan and advantage roadmap for cyber security icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
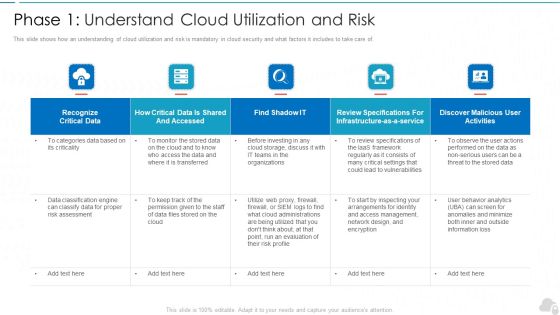
Phase 1 Understand Cloud Utilization And Risk Cloud Computing Security IT Ppt Summary Smartart PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of. Deliver and pitch your topic in the best possible manner with this phase 1 understand cloud utilization and risk cloud computing security it ppt summary smartart pdf. Use them to share invaluable insights on recognize critical data, infrastructure, evaluation, vulnerabilities, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
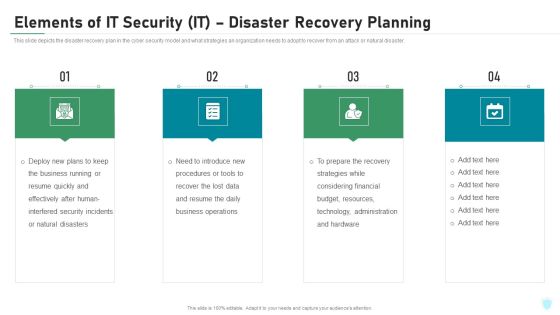
Elements Of IT Security IT Disaster Recovery Planning Ppt Styles Influencers PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Presenting elements of it security it disaster recovery planning ppt styles influencers pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like effectively, business, technology, budget, resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
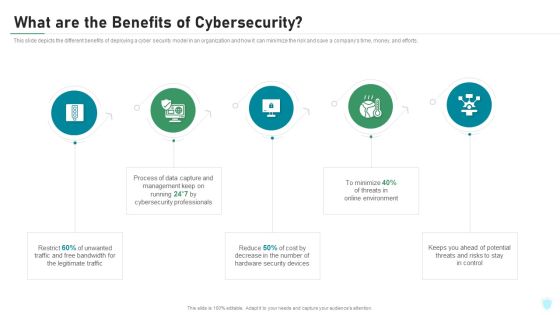
What Are The Benefits Of Cybersecurity IT Security IT Ppt Summary Professional PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. This is a what are the benefits of cybersecurity it security it ppt summary professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like legitimate traffic, cybersecurity, management, process, potential. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Types Of Threats In IT Security IT Ppt Summary Graphics Tutorials PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting types of threats in it security it ppt summary graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Dashboard For Threat Tracking In IT Security IT Ppt Outline Examples PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative dashboard for threat tracking in it security it ppt outline examples pdf bundle. Topics like monthly threat status, threats by owners, risk by threats, current risk status, threats based on role, threat report can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Evolving BI Infrastructure Determine Overview Of Established Security Centre Slides PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Presenting evolving bi infrastructure determine overview of established security centre slides pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like management staff, steering committee, internal systems, backup, functional business units. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Evolving BI Infrastructure Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting evolving bi infrastructure facilities offered by implementation of security centre formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
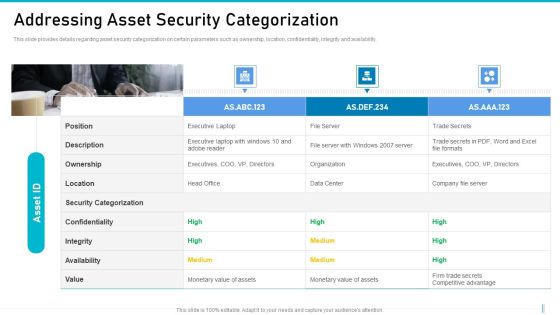
Risk Management For Organization Essential Assets Addressing Asset Security Categorization Diagrams PDF
This slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Presenting risk management for organization essential assets addressing asset security categorization diagrams pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like ownership, location, confidentiality, integrity, availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
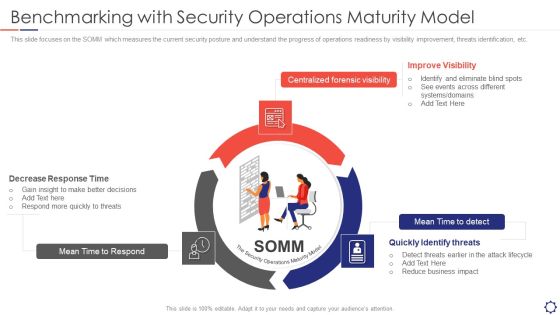
SIEM Benchmarking With Security Operations Maturity Model Ppt Layouts Templates PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. This is a siem benchmarking with security operations maturity model ppt layouts templates pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like mean time to respond, centralized forensic visibility, mean time to detect. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
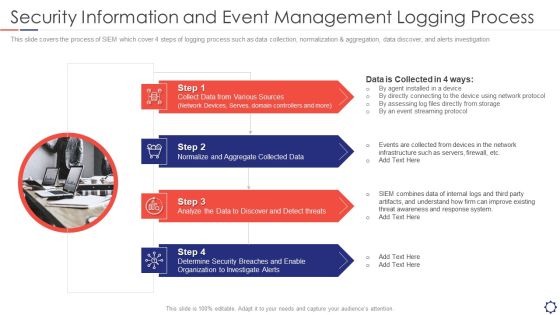
SIEM Security Information And Event Management Logging Process Ppt Slides Graphics Template PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. Presenting siem security information and event management logging process ppt slides graphics template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sources, Collected Data, Analyze threats, Security Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Different Kinds Of Insider Digital Threats Microsoft PDF
This slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. This is a cyber security administration in organization different kinds of insider digital threats microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like disgruntled, employee, criminal, agents, damage, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity What Are The Benefits Of Electronic Information Security Ppt Infographics Ideas PDF
This slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting cybersecurity what are the benefits of electronic information security ppt infographics ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, process, cybersecurity, environment, potential. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Main Steps Of Operational Security Ppt Infographic Template Topics PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a cybersecurity main steps of operational security ppt infographic template topics pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine, potential, risks, technologies, systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Requirement Of Electronic Information Security In Different Sectors Ppt Slides Summary PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver and pitch your topic in the best possible manner with this cybersecurity requirement of electronic information security in different sectors ppt slides summary pdf. Use them to share invaluable insights on financial, organizations, process, information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Types Of Threats In Electronic Information Security Ppt Examples PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a cybersecurity types of threats in electronic information security ppt examples pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber crime. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Threat Security Planning Process With Risk Tolerance And Threats Formats PDF
This following slide illustrates the cyber security threat program planning which include steps like identify key personnel, risk tolerance strategy and developing frequency. Persuade your audience using this cyber threat security planning process with risk tolerance and threats formats pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including establish governance, actively manage and report, built risk tolerance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
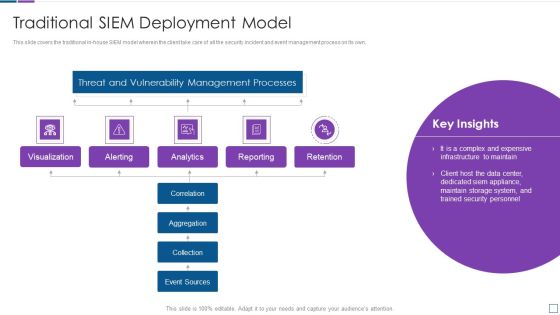
Real Time Assessment Of Security Threats Traditional SIEM Deployment Model Background PDF
This slide covers the traditional in house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats traditional siem deployment model background pdf. Use them to share invaluable insights on threat and vulnerability management processes, visualization, retention, analytics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
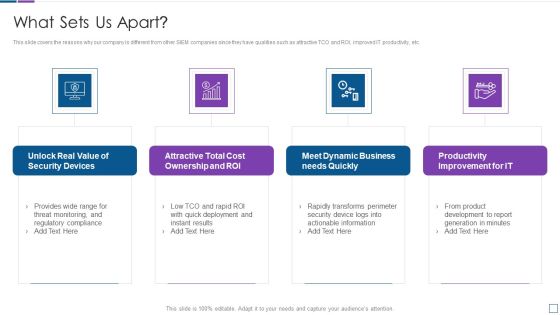
Real Time Assessment Of Security Threats What Sets Us Apart Microsoft PDF
This slide covers the reasons why our company is different from other SIEM companies since they have qualities such as attractive TCO and ROI, improved IT productivity, etc. Presenting real time assessment of security threats what sets us apart microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, cost ownership and roi, dynamic business, productivity improvement. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
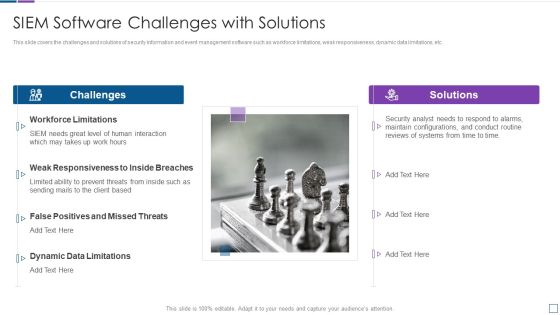
Real Time Assessment Of Security Threats SIEM Software Challenges With Solutions Inspiration PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a real time assessment of security threats siem software challenges with solutions inspiration pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, false positives and missed threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Real Time Assessment Of Security Threats Cloud SIEM Model Icons PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this real time assessment of security threats cloud siem model icons pdf. Use them to share invaluable insights on threat and vulnerability management processes, aggregation, collection, correlation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Real Time Assessment Of Security Threats Our Organization SIEM Log Flow Topics PDF
This slide covers the companys log flow and understand how the data is gathered, security alerts are notified to the clients. This is a real time assessment of security threats our organization siem log flow topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like our organization siem log flow. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance Cloud SIEM Model Diagrams PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance cloud siem model diagrams pdf. Use them to share invaluable insights on visualization, alerting, analytics, reporting, retention and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Software Challenges Professional PDF
This slide covers the challenges and solutions of security information and event management software such as workforce limitations, weak responsiveness, dynamic data limitations, etc. This is a security information and event management strategies for financial audit and compliance siem software challenges professional pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like challenges, solutions, workforce limitations, siem needs great level of human interaction, dynamic data limitations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
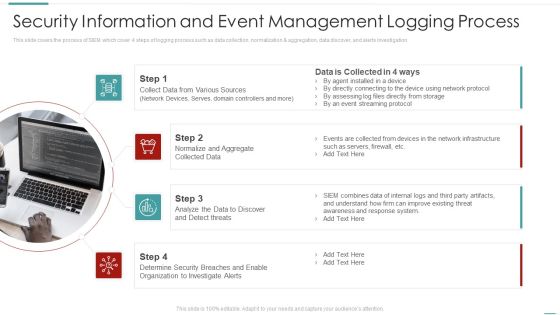
Risk Recognition Automation Security Information And Event Management Logging Process Ppt Inspiration Example Introduction PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation This is a risk recognition automation security information and event management logging process ppt inspiration example introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Recognition Automation Benchmarking With Security Operations Maturity Model Ppt Pictures Infographic Template PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Presenting risk recognition automation benchmarking with security operations maturity model ppt pictures infographic template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like improve visibility, quickly identify threats, decrease response time. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Handling Cyber Threats Digital Era Information Security Program Values To Business Ppt Slides Background Designs PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. This is a handling cyber threats digital era information security program values to business ppt slides background designs pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information security program values to business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Handling Cyber Threats Digital Era KPI Dashboard To Track Security Risk Events Ppt Inspiration PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this handling cyber threats digital era kpi dashboard to track security risk events ppt inspiration pdf. Use them to share invaluable insights on kpi dashboard to track security risk events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Technology Evaluation Process Ppt PowerPoint Presentation File Visual Aids PDF
This slide signifies the technical assessment process of cyber security. It include stages like identify, planning, execution, monitor and closure. Persuade your audience using this cyber security technology evaluation process ppt powerpoint presentation file visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including identify, execution, closure, monitor, planning. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Info Security Hardware And Software Update In Company Ppt PowerPoint Presentation File Mockup PDF
This slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Presenting info security hardware and software update in company ppt powerpoint presentation file mockup pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like peripheral devices, technology, computers and servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Essentials Of Information System Data And Application Security Auditing Clipart PDF
The following slide highlights the essentials of information system data and application security audit illustrating key headings which includes data confidentiality, information backup, application development and configuration management Persuade your audience using this Essentials Of Information System Data And Application Security Auditing Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Data Confidentiality, Application Development, Information Backup. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
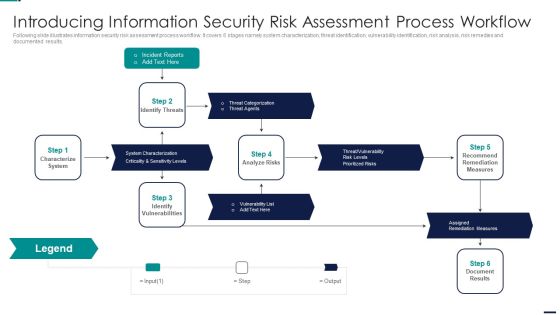
Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
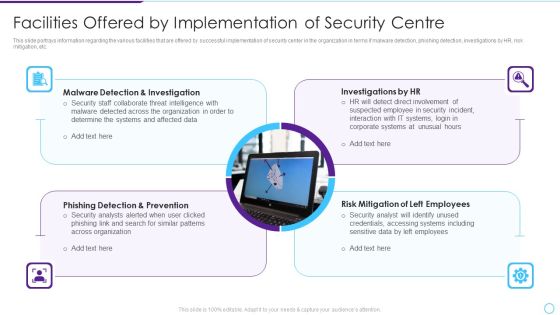
Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Investigations by HR, Phishing Detection And Prevention, Risk Mitigation of Left Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
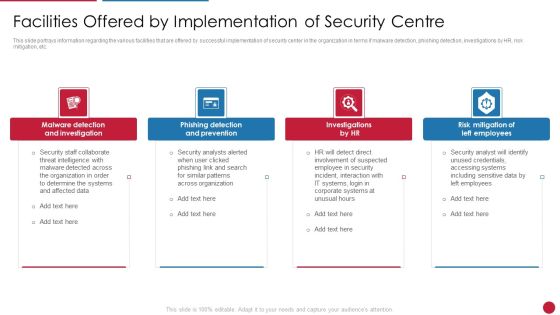
Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Facilitating IT Intelligence Architecture Facilities Offered By Implementation Of Security Centre Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Phishing Detection And Prevention, Risk Mitigation Of Left You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan Introducing Information Security Risk Assessment Process Workflow Slides PDF Use them to share invaluable insights on System Characterization, Threat Categorization, Recommend Remediation Measures and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Presenting Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Incident Management, Asset Management, Risk Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
 Home
Home