Security Services

Portable Home Safety Systems Company Profile Security Company Executive Summary Information PDF
This slide highlights the executive summary of security company which includes company overview, founder, USP, company shareholding, achievements and key facts. Deliver an awe inspiring pitch with this creative Portable Home Safety Systems Company Profile Security Company Executive Summary Information PDF bundle. Topics like Company Shareholding, Achievements, Overview can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
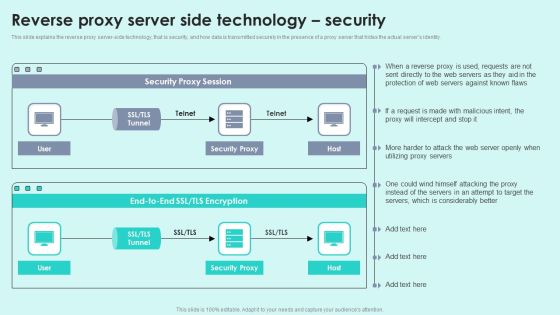
Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF
This slide explains the reverse proxy server-side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity.Deliver and pitch your topic in the best possible manner with this Reverse Proxy Server Side Technology Security Reverse Proxy For Load Balancing Portrait PDF. Use them to share invaluable insights on Security Proxy, Protection Servers, Considerably Better and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Machine To Machine Communication Outline What Is Iot Security Ppt PowerPoint Presentation Show PDF
The slide highlights brief introduction about IoT security. Presenting machine to machine communication outline what is iot security ppt powerpoint presentation show pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like database, command and control center, building automation, business. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study 4 Improving Patient Security And Reducing Risk Of Violence Graphics PDF
Presenting case study 4 improving patient security and reducing risk of violence graphics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like building management, security management, power management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF
This slide showcases identifying inherent risk factors and measures. It provides information about customer base, products, services, delivery channels, jurisdictions, qualitative factors, location, customer risk rating, transparency, fund transfer, etc. Create an editable KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. KYC Transaction Monitoring System Business Security Identifying Inherent Risk Factors And Measures Portrait PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Impact On Food Demand And Food Security Due To Covid Crisis Ppt Pictures Layout PDF
This template covers Impact On Food Demand And Food Security such as demand of food has affected due to reduction in income and purchasing capacity. It also covers the impact of school closure on childrens who are dependent on school meal programs. This is a impact on food demand and food security due to covid crisis ppt pictures layout pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management strategy, price, source, services, production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Artificial Intelligence Transformation Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. This is a artificial intelligence transformation playbook stage five security breach readiness checklist topics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stage five security breach readiness checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Various Strategies To Ensure Food Safety Food Security Excellence Ppt Icon Slide PDF
This slide provides information regarding various strategies used by firm in ensuring food safety in terms of streamlining global safety requirements, digitalization of food, food safety network. This is a various strategies to ensure food safety food security excellence ppt icon slide pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like streamlining global safety requirements, digitalization of food security or safety data, building food safety network. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement Major Investment Banking Deals In Last Summary PDF
The slide provides the top five deals by profit amount of the company in last five years. It comprises, year, client name, deal type and brief information about all the five deals. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement major investment banking deals in last summary pdf bundle. Topics like automobile, financials services, healthcare, construction can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
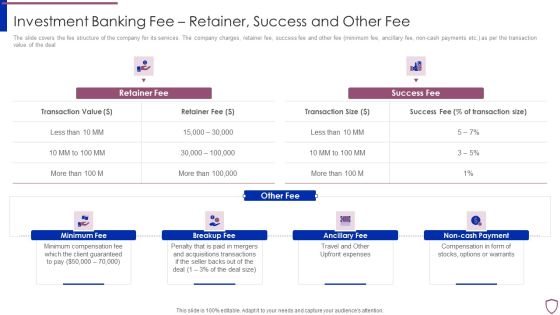
Financing Catalogue For Security Underwriting Agreement Investment Banking Fee Retainer Success Guidelines PDF
The slide covers the fee structure of the company for its services. The company charges, retainer fee, success fee and other fee minimum fee, ancillary fee, non-cash payments etc. as per the transaction value of the deal. This is a financing catalogue for security underwriting agreement investment banking fee retainer success guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like minimum fee, breakup fee, ancillary fee, non cash payment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Financing Catalogue For Security Underwriting Agreement IPO Deals Count In Different Sectors Diagrams PDF
The slide provides the graph of number of IPO deals by sector which the company has handled in last five years. It also covers key facts CAGR growth, raised amount etc. related to IPO deals of the company. Deliver an awe inspiring pitch with this creative financing catalogue for security underwriting agreement ipo deals count in different sectors diagrams pdf bundle. Topics like manufacturing, financial services, automobile, food and beverages can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
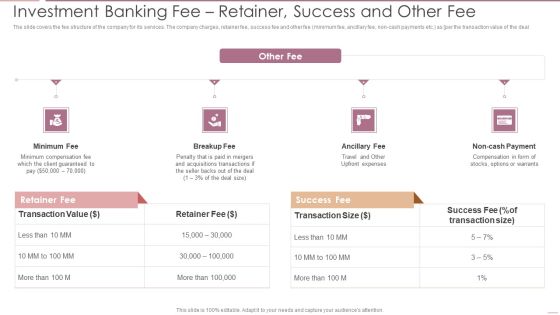
Investment Banking Security Underwriting Pitchbook Investment Banking Feer Retainer Success Demonstration PDF
The slide covers the fee structure of the company for its services. The company charges, retainer fee, success fee and other fee minimum fee, ancillary fee, non cash payments etc. as per the transaction value of the deal.This is a Investment Banking Security Underwriting Pitchbook Investment Banking Feer Retainer Success Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Minimum Compensation, Acquisitions Transactions, Compensation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Enhanced Protection Corporate Event Administration Selecting Suitable Security Incident Management Software Demonstration PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration selecting suitable security incident management software demonstration pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Impact Analysis For Effective Threat Management Slides PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative corporate security and risk management impact analysis for effective threat management slides pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
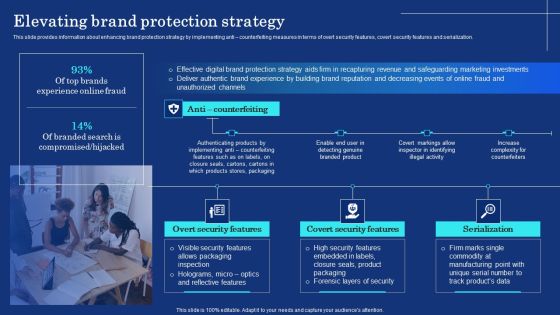
Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Information And Technology Security Operations Contingency Plan For Threat Handling Clipart PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative information and technology security operations contingency plan for threat handling clipart pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Process Integration Contingency Plan For Threat Handling Template PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative security and process integration contingency plan for threat handling template pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Welcome to our selection of the Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
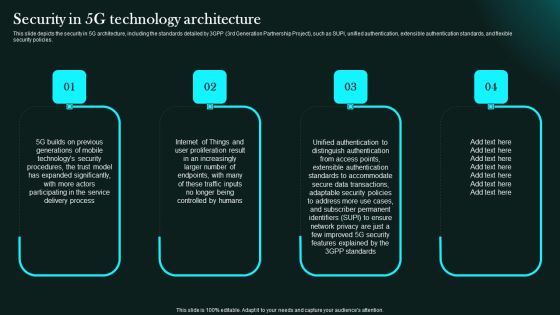
Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies.Slidegeeks has constructed Security In 5G Technology Architecture 5G Network Functional Architecture Clipart PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.
Enabling Data Security Risk Management Action Plan Ppt Slides Icon PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative enabling data security risk management action plan ppt slides icon pdf bundle. Topics like risk, security, information, measures, analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Executing Advance Data Analytics At Workspace Enabling Data Security Risk Demonstration PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk demonstration pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Executing Advance Data Analytics At Workspace Enabling Data Security Risk Icons PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver and pitch your topic in the best possible manner with this executing advance data analytics at workspace enabling data security risk icons pdf. Use them to share invaluable insights on enabling data security risk management action plan and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
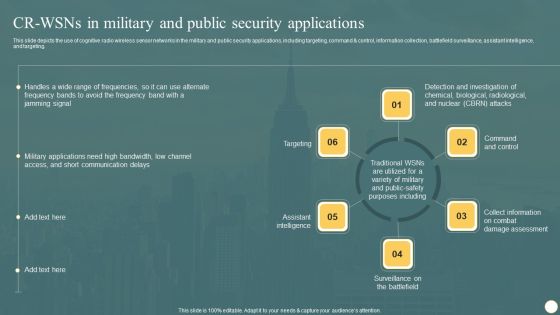
Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Presenting this PowerPoint presentation, titled Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF
This slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Pitch your topic with ease and precision using this Security For Cloud Based Systems Strategic Checklist For IT Business Background PDF. This layout presents information on Security For Cloud Based, Systems Strategic Checklist, For IT Business. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Website Programming IT What Is The Cyber Security Ppt PowerPoint Presentation Gallery Example File PDF
This slide represents how data security keeps in mind while developing websites, and security measures are already added to designed websites to protect them from malicious attacks. This is a website programming it what is the cyber security ppt powerpoint presentation gallery example file pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect information, digital assets, computers, servers, mobile devices, networks, and resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
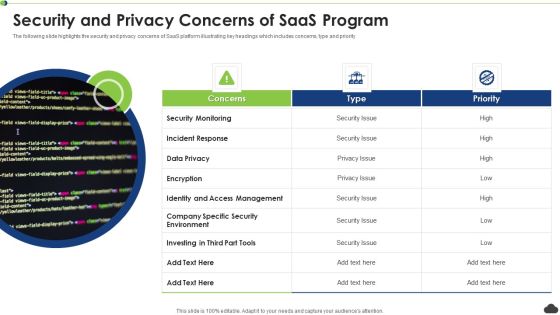
Security And Privacy Concerns Of Saas Program Ppt PowerPoint Presentation File Background PDF
The following slide highlights the security and privacy concerns of SaaS platform illustrating key headings which includes concerns, type and priority. Persuade your audience using this security and privacy concerns of saas program ppt powerpoint presentation file background pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including security monitoring, incident response, encryption. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Elements Of IT Security Disaster Recovery Planning Ppt Icon Rules PDF
This slide depicts the disaster recovery plan in the network security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a elements of information technology security disaster recovery planning ppt outline background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business, security, operations, business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Challenge And Solutions 2 Cloud Threats And Security Ppt Outline Design Inspiration PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt outline design inspiration pdf bundle. Topics like implement data encryption techniques to eliminate risk of infiltration, security and compliance risks are major considerations for the company, professional business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenge And Solutions 2 Cloud Threats And Security Ppt Gallery Images PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver an awe inspiring pitch with this creative challenge and solutions 2 cloud threats and security ppt gallery images pdf bundle. Topics like challenge and solutions 2 cloud threats and security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Challenge And Solutions 2 Cloud Threats And Security Ppt Inspiration Slideshow PDF
This slide shows the problem that the company is facing related to cloud threats and security issues due to improper encryption and password protection. Additionally, the slide covers the key majors or solutions which the company needs to follow. Deliver and pitch your topic in the best possible manner with this challenge and solutions 2 cloud threats and security ppt inspiration slideshow pdf. Use them to share invaluable insights on security, risks, encryption methods, echniques and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
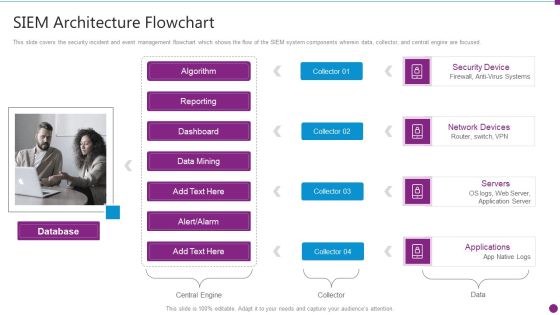
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Flowchart Microsoft PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a security information and event management strategies for financial audit and compliance siem architecture flowchart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
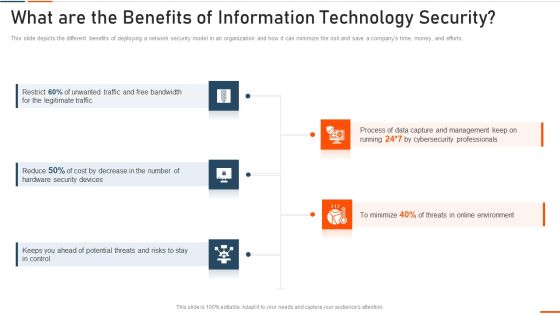
What Are The Benefits Of Information Technology Security Ppt Styles Model PDF
This slide depicts the different benefits of deploying a network security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Presenting what are the benefits of information technology security ppt styles model pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like bandwidth, legitimate, security devices, potential . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Key Smart Phone Security Techniques With Business Economy Level Brochure PDF
This slide shows various phone security techniques that can be adopted by an organization to prevent loss of business data and theft. It include techniques such as user authentication, one-time password and smartcard, etc. Showcasing this set of slides titled Key Smart Phone Security Techniques With Business Economy Level Brochure PDF. The topics addressed in these templates are Security Level, Usage, Economy Value. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Elements Of IT Security End User Education Ppt Summary Portrait PDF
This slide shows the end-user education within the network security model. It also represents various factors that effective training plans should involve. Presenting elements of information technology security end user education ppt model graphics pictures pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like elements of information technology security end user education. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats SIEM Logging Sources Infographics PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. This is a real time assessment of security threats siem logging sources infographics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security devices, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Logging Sources Mockup PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting security information and event management strategies for financial audit and compliance siem logging sources mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, network devices, applications, servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solarwinds Security Event Manager Ethical Hacking Tool Ppt Show Clipart Images PDF
This slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy to use user interface, built-in compliance reports, etc. Presenting solarwinds security event manager ethical hacking tool ppt show clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, security program, dashboard, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Dashboard For Threat Tracking In Information Technology Security Ppt Portfolio Shapes PDF
This slide depicts the dashboard for threat tracking in network security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver and pitch your topic in the best possible manner with this dashboard for threat tracking in information technology security ppt portfolio shapes pdf. Use them to share invaluable insights on dashboard for threat tracking in information technology security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a Facilitating IT Intelligence Architecture Determine Overview Of Established Security Centre Introduction PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Security Monitoring, Internal Systems, Steering Committee You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
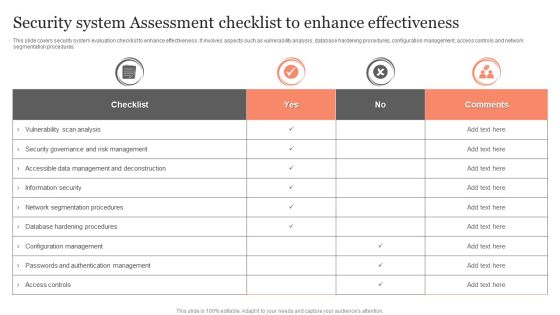
Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF
This slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Showcasing this set of slides titled Security System Assessment Checklist To Enhance Effectiveness Ppt Visual Aids PDF. The topics addressed in these templates are Checklist, Vulnerability Scan Analysis, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Virtual WAN Architecture How Does SD WAN Improve Security Professional PDF
This slide depicts the various security benefits of the software-defined wide-area network. These advantages include centralized and scalable security, zero-touch and segmentation, traffic prioritization from remote locations, traffic encryption and firewalls, cloud connectivity and threat detection and response. Find a pre-designed and impeccable Virtual WAN Architecture How Does SD WAN Improve Security Professional PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Current Market Trends Inspiration PDF
This slide provides information about the current market trends that are increasing the importance of security monitoring and motivating the company to implement a security monitoring plan in the company and follow monitoring strategies. This is a modern security observation plan to eradicate cybersecurity risk and data breach current market trends inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like increasing digitization of sensitive data, outsourcing, general data protection laws. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF
The following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Slidegeeks has constructed IT System Risk Management Guide Technical Security Control Model With Supporting Function Themes PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. There are so many reasons you need a Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
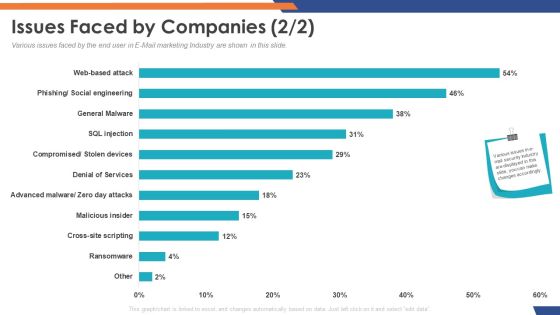
Email Security Market Research Report Issues Faced By Companies Cross Site Download PDF
Presenting this set of slides with name email security market research report issues faced by companies cross site download pdf. The topics discussed in these slides are general malware, social engineering, cross site scripting, denial of service, web based attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
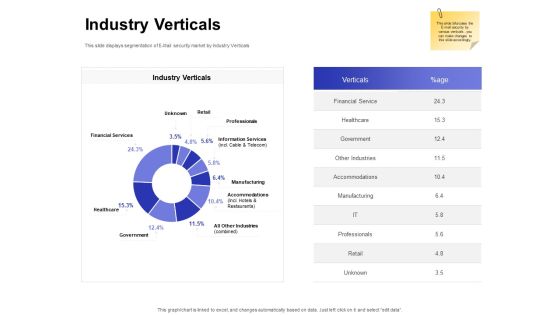
Global Cloud Based Email Security Market Industry Verticals Retail Demonstration PDF
Presenting this set of slides with name global cloud based email security market industry verticals retail demonstration pdf. The topics discussed in these slides are financial service, healthcare, government, accommodations, professionals, manufacturing, retail. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Global Cloud Based Email Security Market Issues Faced By Companies Download PDF
Presenting this set of slides with name global cloud based email security market issues faced by companies download pdf. The topics discussed in these slides are general malware, social engineering, cross site scripting, denial of service, web based attack. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
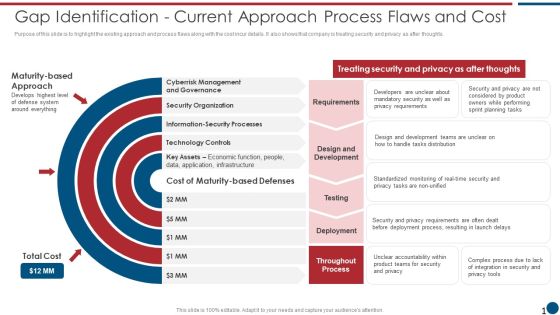
Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF bundle. Topics like Cyberrisk Management, Security Organization, Technology Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF
The purpose of this slide is to showcase various key performance indicator kpis which can assist the company to effectively track cyber security awareness campaign results. The kpis are phishing rate, self-reported incidents, security breaches, cost of security breach and campaign participation rate. This modern and well-arranged Measuring Security Awareness Campaign Results With Kpis Ppt Summary Sample PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF
This slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Find highly impressive Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Cloud Access Security Broker Use Cases Ppt Ideas Layout Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.
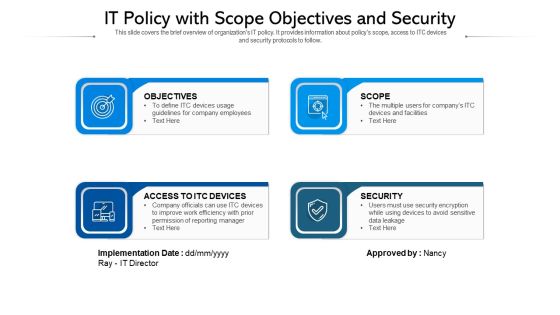
IT Policy With Scope Objectives And Security Ppt PowerPoint Presentation Infographics Show PDF
This slide covers the brief overview of organizations IT policy. It provides information about policys scope, access to ITC devices and security protocols to follow. Persuade your audience using this IT policy with scope objectives and security ppt powerpoint presentation infographics show pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including objectives, access to itc devices, security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Workforce Security Realization Coaching Plan Problem Faced By The Organization Ppt Styles PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a workforce security realization coaching plan problem faced by the organization ppt styles pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity, social engineering, financial impact, organization, security awareness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Data Breach Prevention Recognition Security Awareness Training Roadmap Ppt Gallery Graphics PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. This is a data breach prevention recognition security awareness training roadmap ppt gallery graphics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like threats, data security, information, awareness, roadmap. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
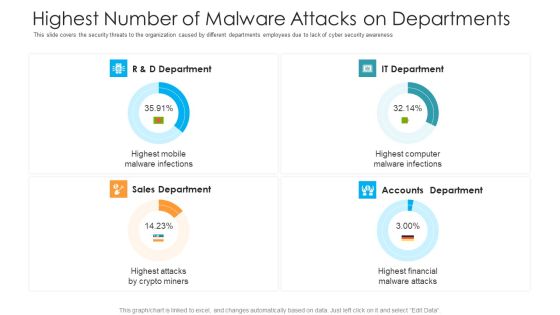
Highest Number Of Malware Attacks On Departments Hacking Prevention Awareness Training For IT Security Themes PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver and pitch your topic in the best possible manner with this highest number of malware attacks on departments hacking prevention awareness training for it security themes pdf. Use them to share invaluable insights on r and d department, it department, accounts department, sales department and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
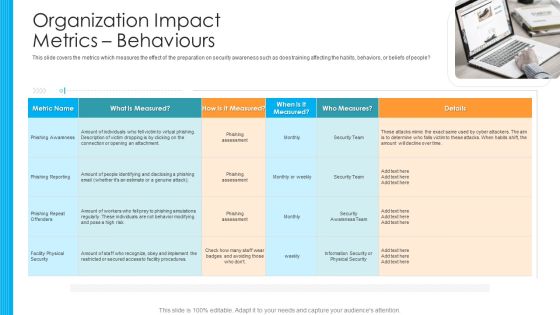
Organization Impact Metrics Behaviours Hacking Prevention Awareness Training For IT Security Designs PDF
This slide covers the metrics which measures the effect of the preparation on security awareness such as does training affecting the habits, behaviors, or beliefs of people. This is a organization impact metrics behaviours hacking prevention awareness training for it security designs pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like phishing awareness, phishing reporting, phishing repeat offenders, facility physical security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
 Home
Home