Security Operations

Project Security Administration IT Workplace Employee Assistance Program Structure PDF
The employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. This is a project security administration it workplace employee assistance program structure pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like clinical services, work and life services, employer services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Asset Identification For Information Security Risk Management Topics PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack This is a Asset Identification For Information Security Risk Management Topics PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customers Database, Products Database, Sales Database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security GDPR Law Governing Data Privacy Formats PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Welcome to our selection of the Information Security GDPR Law Governing Data Privacy Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Information Security Impact Of Data Privacy Laws Implementation Slides PDF
This slide shows the impact of data privacy laws implementation, including a better understanding of the collected data, the business will be more dependable, and so on. Take your projects to the next level with our ultimate collection of Information Security Impact Of Data Privacy Laws Implementation Slides PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Information Security Training Schedule For Data Privacy Microsoft PDF
This slide represents the data privacy training program by covering the details of topics such as benefits and laws and duration for each topic to be covered. Present like a pro with Information Security Training Schedule For Data Privacy Microsoft PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Home Security Company Services And Contact Information Structure PDF
This slide showcases services provided to insured against losses from insurance company. The services provided are interior and exterior renovation and remodeling, general contracting and new home construction. Showcasing this set of slides titled Home Security Company Services And Contact Information Structure PDF. The topics addressed in these templates are Reimbursement, Contract For Protection, Representing Services Provided. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

HR Security Training And Wellbeing KPI Dashboard Professional PDF
This slide showcases dashboard for HR safety training and wellbeing. This template aims to improve employee working efficiency and enhance working conditions to foster their working efficiency. It provides details regarding incidents reported, training programs implemented to reduce number of incidents, cost of providing training and level of employee satisfaction with training. Showcasing this set of slides titled HR Security Training And Wellbeing KPI Dashboard Professional PDF. The topics addressed in these templates are Severity, Injury Consequence, Employee Satisfaction Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
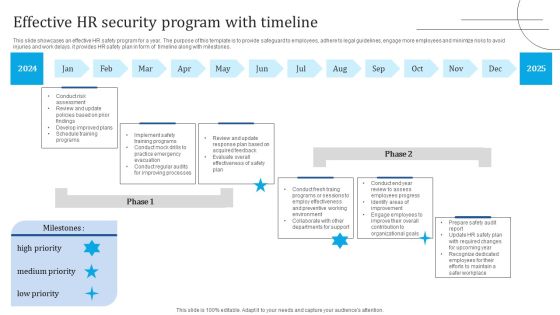
Effective HR Security Program With Timeline Portrait PDF
This slide showcases an effective HR safety program for a year. The purpose of this template is to provide safeguard to employees, adhere to legal guidelines, engage more employees and minimize risks to avoid injuries and work delays. it provides HR safety plan in form of timeline along with milestones. Showcasing this set of slides titled Effective HR Security Program With Timeline Portrait PDF. The topics addressed in these templates are Implement Safety Training Programs, Develop Improved Plans, Review Update. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF
This slide represents the responsibilities under the IaaS model it also shows the different advantages of the IaaS model along with its downsides. This is a Cloud Data Security Infrastructure As A Service Iaas Demonstration PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Advantages, Disadvantages. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Process Of Disaster Recovery Planning Professional PDF
This slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. This is a desktop security management process of disaster recovery planning professional pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plans, team, risk. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
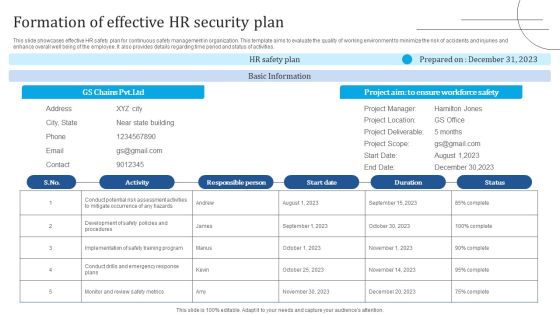
Formation Of Effective HR Security Plan Information PDF
This slide showcases effective HR safety plan for continuous safety management in organization. This template aims to evaluate the quality of working environment to minimize the risk of accidents and injuries and enhance overall well being of the employee. It also provides details regarding time period and status of activities. Presenting Formation Of Effective HR Security Plan Information PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Activity, Responsible Person, Basic Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Need Of Implementing HR Security Programs At Workplace Pictures PDF
This slide highlights the need of importance of workplace safety in an organization. This template aims to provide details regarding workplace safety to increase productivity, reduce turnover rates, safe working conditions, reduction in risk factors, avoid loss of resources, reduction in expenses, foster employee wellbeing and follow legal guidelines, etc. Showcasing this set of slides titled Need Of Implementing HR Security Programs At Workplace Pictures PDF. The topics addressed in these templates are Productivity, Working Environment, Absenteeism. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Mobile Application Security Architecture For Clients Summary PDF
This slide represents the architecture designed to enable the mobile application safety to gain trust of clients. It includes details related to windows and web applications, smart card resource manager, Bluetooth smart card reader. Pitch your topic with ease and precision using this Mobile Application Security Architecture For Clients Summary PDF. This layout presents information on Windows Applications, Web Applications, Resource Manager. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Checklist For Online Security Threat And Risk Assessment Designs PDF
This slide represents digital safety threat and assessment checklist which ensure risk management in cost effective manner. It provides information regarding conducting assessment, perform threat analysis, risk mitigation and process completion. Showcasing this set of slides titled Checklist For Online Security Threat And Risk Assessment Designs PDF. The topics addressed in these templates are Perform Threat Analysis, Conduct Assessment, Risk Mitigation And Recommendations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Organizational Security Solutions Facilities Offered By Successful Implementation Clipart PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a organizational security solutions facilities offered by successful implementation clipart pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Functioning Centre Facilities Offered By Successful Implementation Infographics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting security functioning centre facilities offered by successful implementation infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like risk mitigation, investigations, employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF
This slide shows worksheet representing comparison of insurance premium of different firms for insured or customer to help in making decision . it includes various facilities provided by insurance firms. Showcasing this set of slides titled Annual Premium Comparison Worksheet Of Homeowners Security Diagrams PDF. The topics addressed in these templates are Purchase Price, Insurance, Medical Payments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF
This slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Take your projects to the next level with our ultimate collection of SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

SDN Security Architecture Infrastructure Layer And Apis Professional PDF
This slide represents the infrastructure layer and Application programming interfaces of SDN architecture. The layer contains the physical switches and other devices that help redirect the network traffic, and APIs are used to interact between the three layers of the SDN architecture. Slidegeeks has constructed SDN Security Architecture Infrastructure Layer And Apis Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Hacker Trojan Security PowerPoint Templates And PowerPoint Backgrounds 0811
Microsoft PowerPoint Template and Background with background concept of computer trojan horse

IT Security Hacker Ppt PowerPoint Presentation Complete Deck With Slides
This complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fivty eight slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready made presentation. Click the download button now.

Insurance Agent Protection Security PowerPoint Templates And PowerPoint Backgrounds 0711
Microsoft PowerPoint Template and Background with in the field giving you the best protection

Insurance Agent Protection Security PowerPoint Themes And PowerPoint Slides 0711
Microsoft PowerPoint Theme and Slide with in the field giving you the best protection

Insurance Agent Protection Security PowerPoint Presentation Slides C
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere

Insurance Agent Protection Security PowerPoint Presentation Slides Cc
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere

Insurance Agent Protection Security PowerPoint Presentation Slides F
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere

Insurance Agent Protection Security PowerPoint Presentation Slides R
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere

Insurance Agent Protection Security PowerPoint Presentation Slides S
Microsoft PowerPoint Slides and Backgrounds with in the field giving you the best protection everywhere

Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Want to ace your presentation in front of a live audience Our Information Systems Security And Risk Management Plan Identifying Information Security Threats And Impact On Organization Topics PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Difference Between Cloud Security Solutions And Traditional It Solutions Cloud Computing Security IT Ppt Ideas Example Topics PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative difference between cloud security solutions and traditional it solutions cloud computing security it ppt ideas example topics pdf bundle. Topics like cloud security, traditional it security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effect After Implementing Cyber Risk Security Awareness Program Hacking Prevention Awareness Training For IT Security Information PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative effect after implementing cyber risk security awareness program hacking prevention awareness training for it security information pdf bundle. Topics like accounts department, sales department, it department, r and d department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
What Are The Benefits Of A Cloud Security System Cloud Computing Security IT Ppt Icon Clipart Images PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. Deliver an awe inspiring pitch with this creative what are the benefits of a cloud security system cloud computing security it ppt icon clipart images pdf bundle. Topics like efficient recovery, openness, no hardware required, ddos protection, efficient data security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Retail Store Administration Operational Challenges Retail Outlet Operations Performance Evaluation Diagrams PDF
This slide represents the major challenges associated with successful retail store administrations such as staff time keeping, managing store cleanliness, proper cash handling, ensuring premises security.This is a Retail Store Administration Operational Challenges Retail Outlet Operations Performance Evaluation Diagrams PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Premises Security, Time Keeping, Store Cleanliness. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
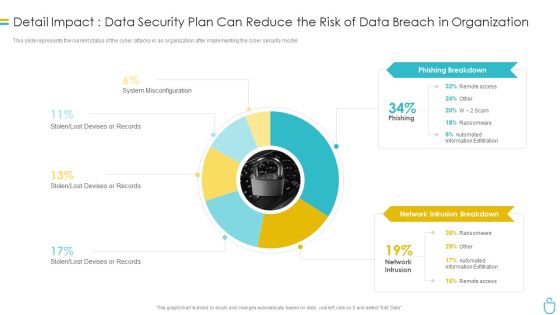
Information Security Detail Impact Data Security Plan Can Reduce The Risk Of Data Breach In Organization Ppt Slides Influencers PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this information security detail impact data security plan can reduce the risk of data breach in organization ppt slides influencers pdf. Use them to share invaluable insights on phishing breakdown, network intrusion breakdown and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security What Are The Benefits Of A Cloud Security System Ppt Gallery Infographic Template PDF
This slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security. This is a Cloud Information Security What Are The Benefits Of A Cloud Security System Ppt Gallery Infographic Template PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Efficient Recovery, DDOS Protection, Efficient Data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
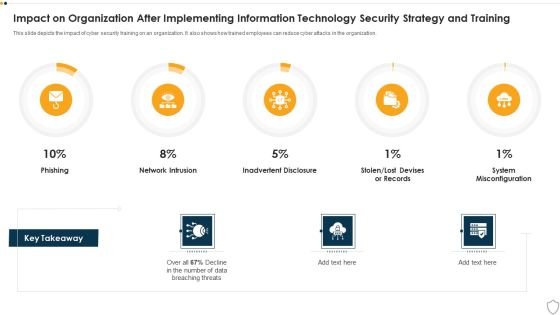
IT Security Impact On Organization After Implementing Information Technology Security Strategy And Training Ppt Slides Deck PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Deliver and pitch your topic in the best possible manner with this it security impact on organization after implementing information technology security strategy and training ppt slides deck pdf. Use them to share invaluable insights on phishing, network intrusion, inadvertent disclosure and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How Does Cloud Security Work Identity And Access Management Iam Cloud Computing Security IT Ppt Infographics Picture PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting how does cloud security work identity and access management iam cloud computing security it ppt infographics picture pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like authentication, authorization, access management, central user repository. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
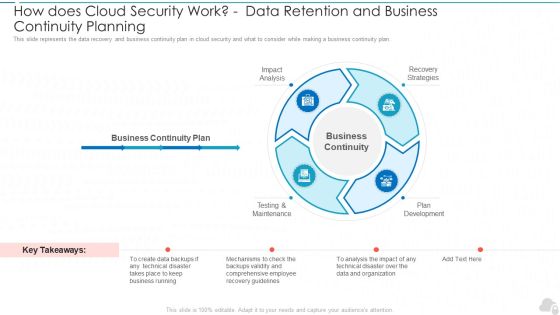
How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Statistics Indicating Recurring Business Operational Expenditure In Telecom Operations Icons PDF
This slide shows statistics indicating recurring operating expenditure OPEX in telecom operations which can benefit their executives in evaluating the current expenses and make cost effective amendments for future operations. It includes information about maintenance, repair, network charging and billing, customer support, marketing and operational planning costs. Pitch your topic with ease and precision using this Statistics Indicating Recurring Business Operational Expenditure In Telecom Operations Icons PDF. This layout presents information on Company, Costs, Marketing Costs. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
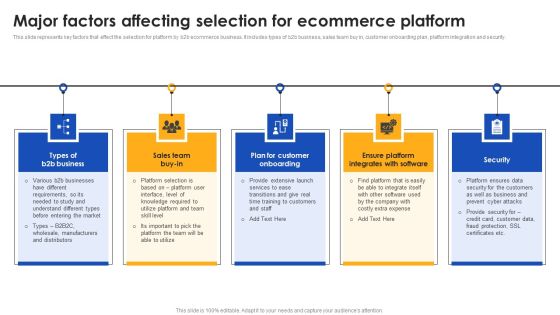
E Commerce Operations In B2b Major Factors Affecting Selection For Ecommerce Designs PDF
This slide represents key factors that effect the selection for platform by b2b ecommerce business. It includes types of b2b business, sales team buy in, customer onboarding plan, platform integration and security. Welcome to our selection of the E Commerce Operations In B2b Major Factors Affecting Selection For Ecommerce Designs PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Business Operations Assessment Obtaining And Laying Out Operating Facilities Ppt PowerPoint Presentation Icon Clipart Images PDF
This is a business operations assessment obtaining and laying out operating facilities ppt powerpoint presentation icon clipart images pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ease of future expansion or change, flow movement, materials handling, output needs, space utilization, shipping and receiving, ease communication and support, promotional value, impact on employee morale and job, safety. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 60 Days Plan Topics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Deploying AI To Enhance Managing Cyber Security In Manufacturing 60 Days Plan Clipart PDF today and make your presentation stand out from the rest.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF can be your best option for delivering a presentation. Represent everything in detail using Deploying AI To Enhance Managing Cyber Security In Manufacturing 90 Days Plan Download PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Intelligent Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Background PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Get a simple yet stunning designed Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Iot Integration In Manufacturing Managing Cyber Security In Manufacturing 90 Days Plan Summary PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF
This slide depicts the next 90 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Transforming Manufacturing With Automation Managing Cyber Security 90 Days Plan Diagrams PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today
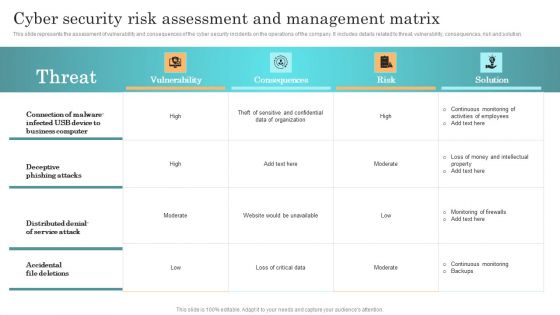
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF
This slide represents the best practices to be adopted by the organizations which aim to minimize impact of cyber security incidents on business operations and prevent them from happening again. It includes best practices such as create cyber incident management plan etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Implementing Cyber Security Incident Best Practices For Cybersecurity Incident Guidelines PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF
This slide represents the next 60 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. This modern and well arranged Transforming Manufacturing With Automation Managing Cyber Security 60 Days Plan Structure PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Slidegeeks is here to make your presentations a breeze with Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Transforming Manufacturing With Automation Managing Cyber Security 30 Days Plan Download PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Security Officer Service Company Profile Organization Chart Ppt PowerPoint Presentation File Designs Download PDF
This slide highlights the organization structure of security company which includes managing director, HR and finance department, training and operations department with site supervisor. Presenting Security Officer Service Company Profile Organization Chart Ppt PowerPoint Presentation File Designs Download PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Finance, Accounts, Payroll, Purchasing, Operations Supervisor. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
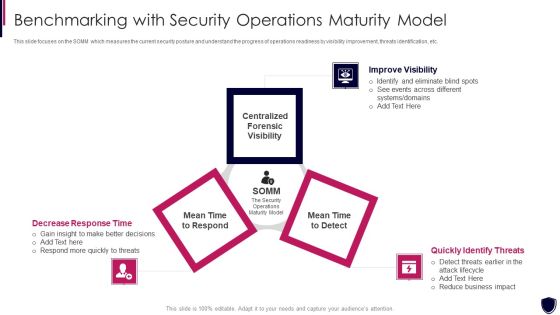
Enhancing Cyber Safety With Vulnerability Administration Benchmarking With Security Inspiration PDF
This slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. This is a enhancing cyber safety with vulnerability administration benchmarking with security inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like improve visibility, quickly identify threats, decrease response time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. Presenting Smart Home Security Solutions Company Profile Company Journey From 2010 To 2022 Introduction PDF to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like Smart Home Services, Acquired Bluestone Security, System Product Catalogue, Launched Different CCTV, 2010 To 2022. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile Company Journey From 2010 To 2022 Pictures PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. This is a Security And Surveillance Company Profile Company Journey From 2010 To 2022 Pictures PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Raymond Michael, Product Catalogue, Bluestone Security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
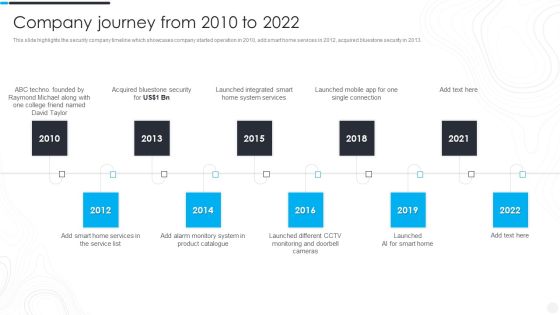
Security Camera System Company Profile Company Journey From 2010 To 2022 Inspiration PDF
This slide highlights the security company timeline which showcases company started operation in 2010, add smart home services in 2012, acquired bluestone security in 2013. This is a Security Camera System Company Profile Company Journey From 2010 To 2022 Inspiration PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Raymond, Acquired Bluestone, Launched Integrated. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
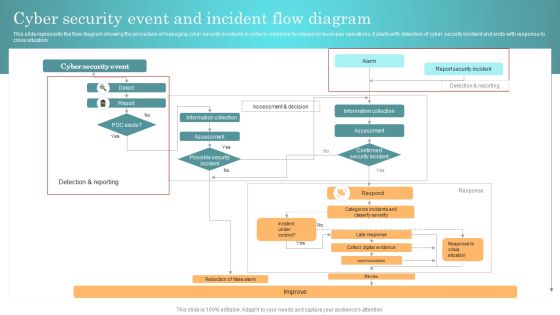
Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Incident Response Techniques Deployement Cyber Security Event And Incident Flow Diagram Structure PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.
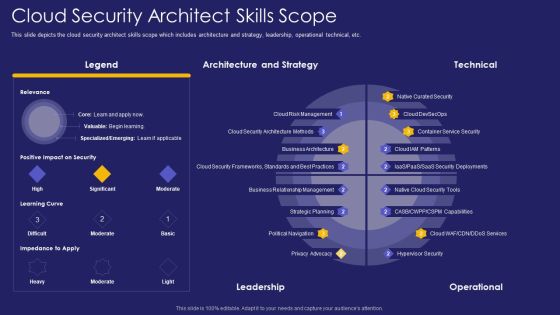
Role IT Team Digital Transformation Cloud Security Architect Skills Scope Rules PDF
This slide depicts the cloud security architect skills scope which includes architecture and strategy, leadership, operational technical, etc. Deliver an awe inspiring pitch with this creative role it team digital transformation cloud security architect skills scope rules pdf bundle. Topics like architecture, strategy, leadership can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home