Security Operations

Cyber Terrorism Assault Roadmap To Implement Cyber Security To Mitigate Cyber Terrorism Template PDF
This slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts.Presenting cyber terrorism assault roadmap to implement cyber security to mitigate cyber terrorism template pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like creating personal accounts, awareness training, keep the hardware In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determine Current Scenario Of Mobile Devices Usage At Workplace Mobile Device Security Management Template PDF
This slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. Deliver and pitch your topic in the best possible manner with this Determine Current Scenario Of Mobile Devices Usage At Workplace Mobile Device Security Management Template PDF. Use them to share invaluable insights on Determine Frequency, Mobile Device, Workplace and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Mobile Device Management Assistance To Mobile Device Security Management Professional PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. This is a Mobile Device Management Assistance To Mobile Device Security Management Professional PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Reducing Connection, Rendering Appropriate, Remote Configuration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF
This slide covers KPI dashboard to assess training program efficiency. It involves details such as overall responses on monthly basis, employee satisfaction rate, net promoter score and major training courses. Pitch your topic with ease and precision using this Dashboard To Assess IT Security Awareness Training Program Efficiency Brochure PDF. This layout presents information on Major Training Course, Major Satisfactory, Training Course. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Determine Current Scenario Of Mobile Devices Usage At Workplace Business Mobile Device Security Structure PDF
This slide covers details regarding the current scenario of mobile devices usage at workplace with mobile device usage frequency per day, employees considering tablet PCs as personal and work device. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 precent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Determine Current Scenario Of Mobile Devices Usage At Workplace Business Mobile Device Security Structure PDF from Slidegeeks and deliver a wonderful presentation.

Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF
This slide provides information regarding mobile device management technology assistance to employees and to IT department associated to firm. Present like a pro with Mobile Device Management Assistance Business Mobile Device Security Management And Mitigation Template PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
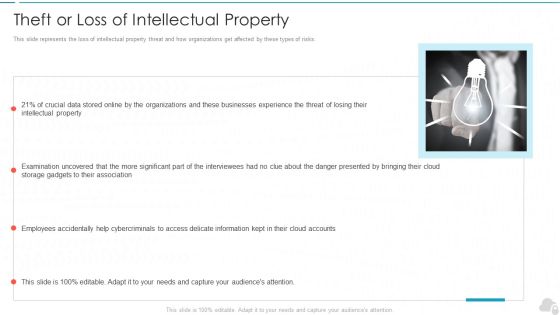
Theft Or Loss Of Intellectual Property Cloud Computing Security IT Ppt Styles Visual Aids PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks. This is a theft or loss of intellectual property cloud computing security it ppt styles visual aids pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organizations, cloud accounts, intellectual property. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Prepare Data Backup For Sensitive Information Ppt Portfolio Slide Download PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Presenting it security prepare data backup for sensitive information ppt portfolio slide download pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prepare data backup for sensitive information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
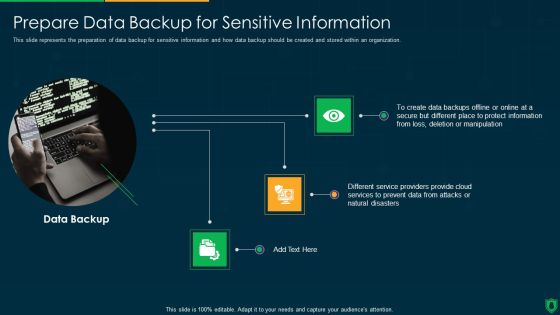
Info Security Prepare Data Backup For Sensitive Information Ppt PowerPoint Presentation File Rules PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a info security prepare data backup for sensitive information ppt powerpoint presentation file rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data backup, provide cloud, prevent data, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Data Security Theft Or Loss Of Intellectual Property Microsoft PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks. This is a Cloud Data Security Theft Or Loss Of Intellectual Property Microsoft PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Organizations, Businesses, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks.This is a Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intellectual Property, Examination Uncovered, Danger Presented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF
This slide represents the reverse proxy server-side technology, which is load balancing, and how reverse proxy side servers help high-traffic websites manage traffic. The Reverse Proxy Web Server Reverse Proxy Web Server Application Side Technology Security Designs PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF
This slide showcases most common information attacks faced by organization. It includes malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Take your projects to the next level with our ultimate collection of Information Security Attacks Faced By Organization Cybersecurity Risk Assessment Brochure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they well make your projects stand out from the rest.

KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF
This slide represents transaction monitoring system process flow. It provides information about data analytics, risk framework, alerting, ad hoc analysis, case management, external source entrance, stop list, politically exposed persons PEP, watch list, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. KYC Transaction Monitoring System Business Security Tms And Data Analytics Process Flow Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
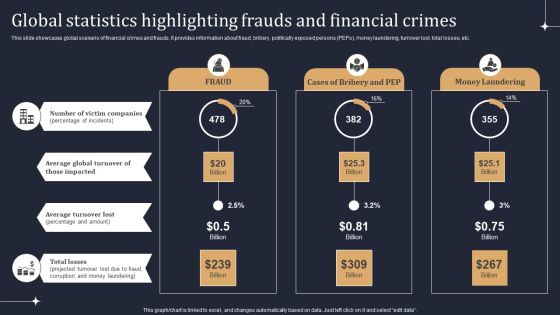
KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF
This slide showcases global scenario of financial crimes and frauds. It provides information about fraud, bribery, politically exposed persons PEPs, money laundering, turnover lost, total losses, etc. Take your projects to the next level with our ultimate collection of KYC Transaction Monitoring System Business Security Global Statistics Highlighting Frauds Diagrams PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Security Software Company Investor Funding Pitch Deck Company Introduction Structure PDF
This slide represents the overview of IT company which offers an NTA solution to IT customers . It showcases industry, customer, headquarters, type, founded year, founders, website and legal name. Want to ace your presentation in front of a live audience Our Security Software Company Investor Funding Pitch Deck Company Introduction Structure PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Boost your pitch with our creative Cyber Security Breache Response Strategy Consequences Of Data Breaches Faced By Organization Elements PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

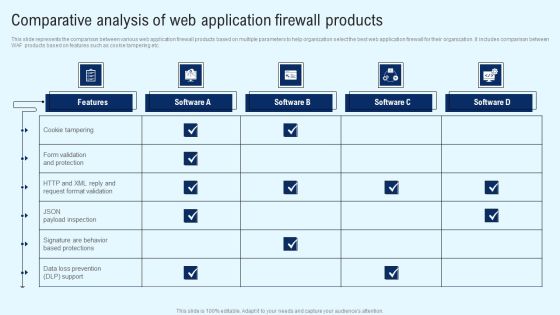
CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. There are so many reasons you need a CYBER Security Breache Response Strategy Comparative Analysis Of Web Application Firewall Products Slides PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF
This slide represents the advantages of implementing a software which protects web applications from variety of application layer attacks. It includes key benefits of implementing web application firewall such as defense, fights vulnerabilities etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Cyber Security Incident Response Administration Benefits Of Implementing Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

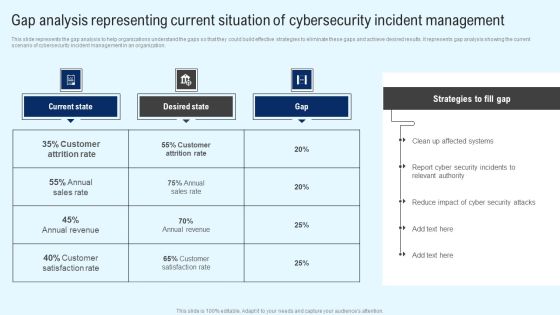
CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Slidegeeks has constructed CYBER Security Breache Response Strategy Gap Analysis Representing Current Situation Cybersecurity Incident Professional PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF
This slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results. It represents gap analysis showing the current scenario of cybersecurity incident management in an organization. Retrieve professionally designed Implementing Cyber Security Incident Gap Analysis Representing Current Situation Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF
This slide describes the primary attacks that hackers can use to exploit blockchain technology networks. The purpose of this slide is to showcase some basic threats that hackers can use to manipulate a blockchain network, such as phishing attacks, routing attacks, sybil, and 51 percent. Present like a pro with Blockchain Security Solutions Deployment How Fraudsters Attack Blockchain Network Sample PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Aftereffects Of IT Security Threats On Business And Customers Ppt PowerPoint Presentation Layouts Background PDF
Persuade your audience using this aftereffects of it security threats on business and customers ppt powerpoint presentation layouts background pdf. This PPT design covers two stages, thus making it a great tool to use. It also caters to a variety of topics including violation of law, crucial information loss, loss of productivity, cyber espionage, risk of losing work in future, contract breach, trust among business people, ransom ware, online banking transactions are compromised, identity theft, credit card detail theft, spam mails or other attacks violates the law, fraud to customers by scare ware or other fraud tools. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF
This slide highlights the damage control form information technology risk management strategies which includes data breach, cyber threats, social engineering attacks, domain based threats and increase in business opportunities. This modern and well arranged Organizations Risk Management And IT Security Damage Control Assessment From IT Risk Management Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Employee Security Coaching Matrix Ppt PowerPoint Presentation Complete Deck With Slides
Boost your confidence and team morale with this well-structured employee security coaching matrix ppt powerpoint presentation complete deck with slides. This prefabricated set gives a voice to your presentation because of its well-researched content and graphics. Our experts have added all the components very carefully, thus helping you deliver great presentations with a single click. Not only that, it contains a set of twelve slides that are designed using the right visuals, graphics, etc. Various topics can be discussed, and effective brainstorming sessions can be conducted using the wide variety of slides added in this complete deck. Apart from this, our PPT design contains clear instructions to help you restructure your presentations and create multiple variations. The color, format, design anything can be modified as deemed fit by the user. Not only this, it is available for immediate download. So, grab it now.

SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF
This slide depicts the four critical areas where SDN can make a difference in an organization, such as network programmability, centralized intelligence and control, abstraction of the network, and openness. Welcome to our selection of the SDN Security Architecture How SDN Can Have A Significant Impact On A Business Mockup PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today

SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF
This slide represents the role of software defined networking in edge computing, IoT, and remote locations to make them more accessible and less expensive. Smart SDN controllers detect network congestion and, in response, increase the bandwidth for remote and edge devices. Boost your pitch with our creative SDN Security Architecture Role Of SDN In Edge Computing Iot And Remote Access Information PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

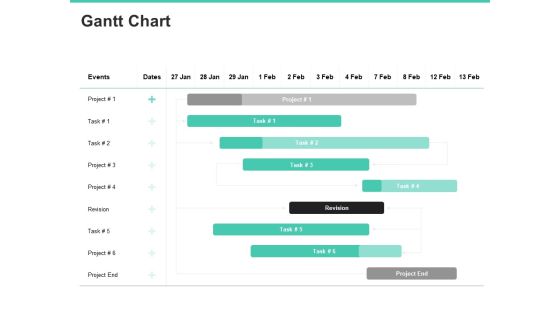
Damage Security Insurance Proposal Gantt Chart Ppt Gallery Graphic Tips PDF
Your complex projects can be managed and organized simultaneously using this detailed damage security insurance proposal gantt chart ppt gallery graphic tips pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.
SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF
This slide represents the importance of virtualization in software defined networking and how they complement one another. It also includes how SDN helps simplify the process of controlling data packet routing via a central server. Retrieve professionally designed SDN Security Architecture Importance Of Virtualization In Software Defined Networking Icons PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Security Control Techniques For Real Estate Project Budget Plan For Construction Site Safety Program Microsoft PDF
The purpose of this slide is to highlight the budget plan for the construction site safety program. It includes details regarding the breakup of multiple costs, such as equipment and training costs along with the units required, cost per unit and total cost. This slide showcase the major barriers to successfully implement of construction site safety program such as limited awareness, limited employee participation, insufficient legislation, and behavioral rigidity. It also contains details of recommended solutions to overcome them. Make sure to capture your audiences attention in your business displays with our gratis customizable Security Control Techniques For Real Estate Project Budget Plan For Construction Site Safety Program Microsoft PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Email Security Encryption And Data Loss Prevention Gantt Chart Information PDF
Your complex projects can be managed and organized simultaneously using this detailed email security encryption and data loss prevention gantt chart information pdf template. Track the milestones, tasks, phases, activities, and subtasks to get an updated visual of your project. Share your planning horizon and release plan with this well-crafted presentation template. This exemplary template can be used to plot various dependencies to distinguish the tasks in the pipeline and their impact on the schedules and deadlines of the project. Apart from this, you can also share this visual presentation with your team members and stakeholders. It a resourceful tool that can be incorporated into your business structure. Therefore, download and edit it conveniently to add the data and statistics as per your requirement.

Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. This modern and well arranged Deploying Cyber Security Incident Response Administration Common Sources Of Precursors Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF
The employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Do you know about Slidesgeeks Determine Various Mobile Devices Existing At Workplace Business Mobile Device Security Management Download PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
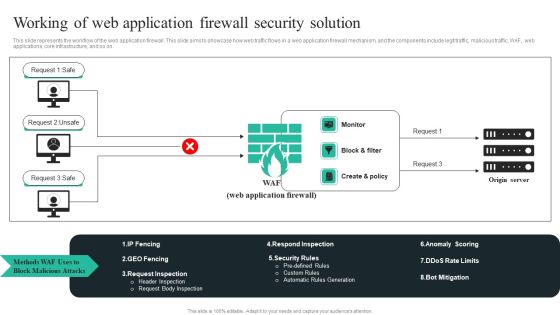
WAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF
This slide represents the workflow of the web application firewall. This slide aims to showcase how web traffic flows in a web application firewall mechanism, and the components include legit traffic, malicious traffic, WAF, web applications, core infrastructure, and so on. Take your projects to the next level with our ultimate collection ofWAF Introduction Working Of Web Application Firewall Security Solution Microsoft PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

4 Step Cycle To Ensure HR Security And Well Being Graphics PDF
This slide highlights four stage cycle to ensure HR safety and well being in an organization. The purpose of this template is to create an efficient and safe working culture and to improve employee wellbeing to increase their contribution. It includes stages of regular risk assessment, implementation of safety measures, monitoring regular compliance and continuous improvement. Presenting 4 Step Cycle To Ensure HR Security And Well Being Graphics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assess And Identify Risks, Implement Safety Measures, Monitor Safety Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. Boost your pitch with our creative Implementing Cyber Security Incident Comparative Analysis Of Web Application Microsoft PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
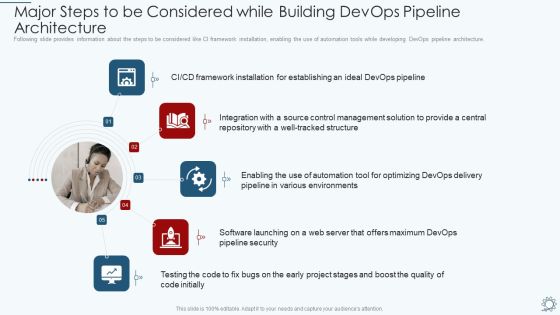
Development And Operations Pipeline IT Major Steps To Be Considered While Building Devops Pipeline Architecture Designs PDF
Following slide provides information about the steps to be considered like CI framework installation, enabling the use of automation tools while developing DevOps pipeline architecture. Presenting development and operations pipeline it major steps to be considered while building devops pipeline architecture designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, environments, management, integration, framework. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
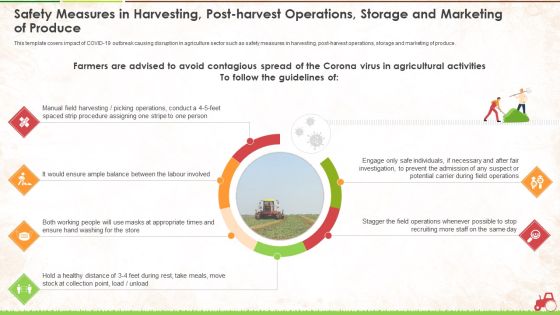
Safety Measures In Harvesting Post Harvest Operations Storage And Marketing Of Produce Ppt Infographics Graphics Design PDF
This is a safety measures in harvesting post harvest operations storage and marketing of produce ppt infographics graphics design pdf. template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safety measures in harvesting, post harvest operations, storage and marketing of produce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Solutions For Automotive Suppliers To Revive Their Operations And Supply Chains Post Pandemic Ppt Layouts Samples PDF
This slide shows various solutions like supplier network illumination and demand sensing capabilities for auto suppliers to revive their operations and supply chains post COVID 19. Deliver an awe inspiring pitch with this creative solutions for automotive suppliers to revive their operations and supply chains post pandemic ppt layouts samples pdf bundle. Topics like material, required, manufacturers, plans can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF
This slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Showcasing this set of slides titled ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF. The topics addressed in these templates are Customer Expectations, Industry Norms, Internal Business Demands. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Handling Cyber Threats Digital Era Key Security Controls To Be Addressed In The Program Ppt Infographics Samples PDF
Purpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Presenting handling cyber threats digital era key security controls to be addressed in the program ppt infographics samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like prevents attacks, limits extent of attacks, data recovery. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Attacks Experienced By The Company In Previous Financial Year Hacking Prevention Awareness Training For IT Security Template PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe inspiring pitch with this creative cyber attacks experienced by the company in previous financial year hacking prevention awareness training for it security template pdf bundle. Topics like phishing, network intrusion, inadvertent disclosure, stolen or lost device or records, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF
This slide depicts the official announcement to avoid russias kaspersky antivirus tool by german officials as kaspersky has been accused of working for the russian government. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Series Of Cyber Security Attacks Series Of Cyber Security Attacks Against Ukraine 2022 Germany Asks To Avoid Russias Kaspersky Antivirus Tool Diagrams PDF today and make your presentation stand out from the rest.

Detail Impact IT Security IT Plan Can Reduce The Risk Of Data Breach In Organization Ppt Infographic Template Objects PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver and pitch your topic in the best possible manner with this detail impact it security it plan can reduce the risk of data breach in organization ppt infographic template objects pdf. Use them to share invaluable insights on detail impact it security it plan can reduce the risk of data breach in organization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Detail Impact Information Security Plan Can Reduce The Risk Of Data Breach Ppt PowerPoint Presentation File Visual Aids PDF
This slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Deliver an awe inspiring pitch with this creative detail impact information security plan can reduce the risk of data breach ppt powerpoint presentation file visual aids pdf bundle. Topics like phishing breakdown, network intrusion breakdown, inadvertent desclosure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Shield With Gear Icon For Creating Employee Trust In Security System Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name shield with gear icon for creating employee trust in security system ppt powerpoint presentation file outline pdf. This is a two stage process. The stages in this process are shield with gear icon for creating employee trust in security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF
The purpose of this slide is to outline the different cyber security gaps which are faced by employees, line and senior managers. Information covered in this slide is related to ransomware, password attack, crypto-jacking, IoT-based attack, malware etc. Find a pre designed and impeccable Implementing Cybersecurity Awareness Program To Prevent Attacks Recognizing The Cyber Security Gaps Faced By Key Elements PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Creating An Effective Induction Programme For New Staff Data Protection And Information Security Policy And Procedure Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF
This slide showcases information security attacks faced by organization in past financial year. It can help company to assess different type of cyber attacks and formulate strategies to tackle them. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Information Systems Security And Risk Management Plan Cyber Attacks Faced By Organization In Previous Financial Year Graphics PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Series Of Cyber Security Attacks Against Ukraine 2022 Should We Be Concerned About Russian Cyberattacks Information PDF
This slide shows that US citizens should not be concerned about russian cyberattacks as nothing has happened so far. However, the US department of homeland security issued a warning to organizations to look for russian cyberattacks. Make sure to capture your audiences attention in your business displays with our gratis customizable Series Of Cyber Security Attacks Against Ukraine 2022 Should We Be Concerned About Russian Cyberattacks Information PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF
This slide depicts the anonymous organization and how they have started a cyberwar against russia by gathering worldwide hackers through twitter. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF can be your best option for delivering a presentation. Represent everything in detail using Series Of Cyber Security Attacks Against Ukraine 2022 Hacker Group Anonymous Has Waged A Cyberwar Against Russia Summary PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF
This slide represents the rapid announcements made by the united states about russian cyberattacks against ukraine within the 48 hours of the cyberwar. Explore a selection of the finest Series Of Cyber Security Attacks Against Ukraine 2022 Us Is Unmasking Russian Hackers Faster Than Ever Guidelines PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Series Of Cyber Security Atta to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF
This slide represents the continuous cyber espionage attacks held by the shuckworm group against ukraine. Most of these attacks were phishing emails to spread the malware among devices that could control remotely. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Series Of Cyber Security Attacks Against Ukraine 2022 Shuckworm Continues Cyber Espionage Attacks Against Ukraine Rules PDF.

Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF
This slide depicts the hacking groups such as the anonymous hacker group, conti ransomware gang, threat actors in belarus launching cyber proxy war over ukraine attacks by russia. Find highly impressive Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Series Of Cyber Security Attacks Against Ukraine 2022 Hacking Groups Launching Cyber Proxy War Against Russia Icons PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF
This slide describes the establishment of cyber policies by international laws, including the budapest convention on cybercrime and the united nations group of governmental experts. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 Are There International Laws Establishing Cyber Policies Microsoft PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF
This slide represents the ukraine and russia cyber warfare impact on western countries such as the united states, united kingdom, and estonia. This Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF
This slide depicts cyberattacks protection methods to follow throughout the country, such as multi-factor authentication, data backup, to keep a copy of all the backup information. Create an editable Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Series Of Cyber Security Attacks Against Ukraine 2022 How Can We Protect Ourselves From Cyberattacks Slides PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF
This slide represents the cybersecurity risks associated with russia and ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Series Of Cyber Security Attacks Against Ukraine 2022 Triolan Suffers Severe Cyberattacks During Russian Invasion Designs PDF
This slide describes the severe cyberattacks and infrastructure destruction experienced by major internet provider triolan during the russian invasion. This modern and well arranged Series Of Cyber Security AttaSeries Of Cyber Security Attacks Against Ukraine 2022 Triolan Suffers Severe Cyberattacks During Russian Invasion Designs PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Info Security Cyber Attacks Experienced By Company In Previous Financial Year Ppt PowerPoint Presentation Gallery Slideshow PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver an awe inspiring pitch with this creative info security cyber attacks experienced by company in previous financial year ppt powerpoint presentation gallery slideshow pdf bundle. Topics like comparatively low, cyber attacks experienced can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Series Of Cyber Security Attacks Against Ukraine 2022 Banks On Alert For Russian Reprisal Cyber Attacks On Swift Background PDF
This slide represents that banks are on alert for russian reprisal cyber attacks on society for worldwide interbank financial telecommunication swift. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 Banks On Alert For Russian Reprisal Cyber Attacks On Swift Background PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF
This slide represents the other attacks carried out by russia on ukraine, such as website defacement, distributed denial-of-service attacks, and website clones. The Series Of Cyber Security Attacks Against Ukraine 2022 Website Defacements Ddos Attacks And Website Clones Brochure PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Series Of Cyber Security Attacks Against Ukraine 2022 Impact Of Defacement Attacks And Fake News Topics PDF
This slide shows the impact of defacement attacks and fake news on the public, and meta has banned russian media on its platforms, and russia has restricted access to facebook. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Impact Of Defacement Attacks And Fake News Topics PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF
This slide talks about the cyber rapid response team deployed to protect ukraine from russian cyber attacks, including experts from lithuania, croatia, poland, estonia, romania, and the netherlands. Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Hybrid Warfare Cyber Rapid Response Team CRRT Themes PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Series Of Cyber Security Attacks Against Ukraine 2022 Does Ukraine And Russia Cyber Warfare Kill People Guidelines PDF
This slide describes if ukraine and russia cyber warfare is killing people and german cybersecurity expert matthias schulze said people have died due to misinformation efforts in earlier conflicts. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Does Ukraine And Russia Cyber Warfare Kill People Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Portrait PDF
This slide depicts the russian vigilante hacker who was able to bring down some official ukrainian websites and one military website along with his group of 6 hackers. Welcome to our selection of the Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Russian Vigilante Hacker Portrait PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF
This slide represents the steps to take right now to prepare for cyberattacks by russia, including access exposure, minimizing attack surface, executing the basics, and so on. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Series Of Cyber Security Attacks Against Ukraine 2022 Steps To Prepare For Cyberattacks By Russia Microsoft PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF
This slide shows the continued impact of ongoing cyberattacks on ukrainian internet providers and how these cyberattacks are causing internet outages throughout the country Want to ace your presentation in front of a live audience Our Series Of Cyber Security Attacks Against Ukraine 2022 Continued Impact Of Ongoing Cyberattacks On Internet Providers Microsoft PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF
This slide talks about how to protect yourself from ongoing russian cybersecurity attacks, including being on high alert, choosing a strong password, keeping antivirus software up to data, etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Series Of Cyber Security Attacks Against Ukraine 2022 How To Protect Yourself From Ongoing Cybersecurity Attacks Mockup PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF
This slide represents the technical analysis of ddos attacks against ukrainian websites by showing the internet traffic to the oschad bank website on 15 16 february 2022. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Technical Analysis Of Ddos Attacks Against Ukrainian Websites Elements PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Series Of Cyber Security Attacks Against Ukraine 2022 Reasons Behind Ukraine And Russia Cyber Warfare Structure PDF
This slide describes the reasons behind ukraine and russia cyber warfare, including natos eastward expansion, ukraine is not a real country according to putin, and so on. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Series Of Cyber Security Attacks Against Ukraine 2022 Reasons Behind Ukraine And Russia Cyber Warfare Structure PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF
This slide depicts facebook and twitters suggestion for ukrainian citizens to close or lock their social media accounts as there are high chances of getting hacked in the hours of the war. Present like a pro with Series Of Cyber Security Attacks Against Ukraine 2022 Facebook And Twitter Suggest Users In Ukraine Lock Their Accounts Professional PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Zero Trust Policy And Why You Should Embrace It Cloud Computing Security IT Ppt Infographics Gridlines PDF
This slide represents the zero-trust policy and why organizations should embrace it, and how user access control is managed under the zero-trust policy. This is a zero trust policy and why you should embrace it cloud computing security it ppt infographics gridlines pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like authentication, device validation, restrict access. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
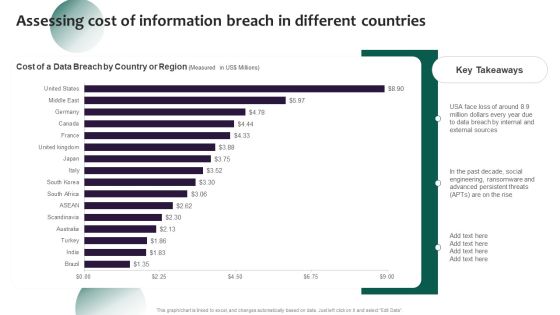
Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Systems Security And Risk Management Plan Assessing Cost Of Information Breach In Different Countries Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using Key Takeaways, Countries, Region and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
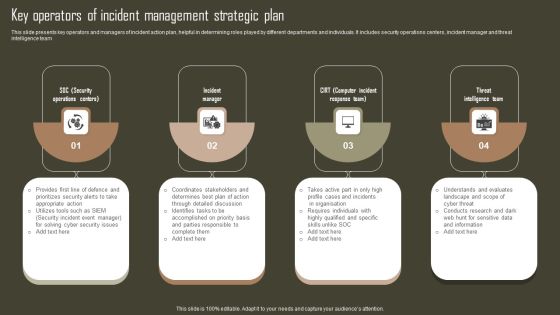
Key Operators Of Incident Management Strategic Plan Professional PDF
This slide presents key operators and managers of incident action plan, helpful in determining roles played by different departments and individuals. It includes security operations centers, incident manager and threat intelligence team. Presenting Key Operators Of Incident Management Strategic Plan Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Incident Manager, Threat Intelligence Team, Sensitive Data And Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Motel Safety Computers Operator Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name motel safety computers operator ppt powerpoint presentation complete deck. The topics discussed in these slides are wireless security, card access, security guard, operator, computers. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

System For Operational Performance Management Infographics PDF
This slide covers the framework for operational performance management which includes planning, executing, measuring and improving with key business drivers such as people, leadership, operational security, etc. Presenting System For Operational Performance Management Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Performance, Procedures, People, Plant. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
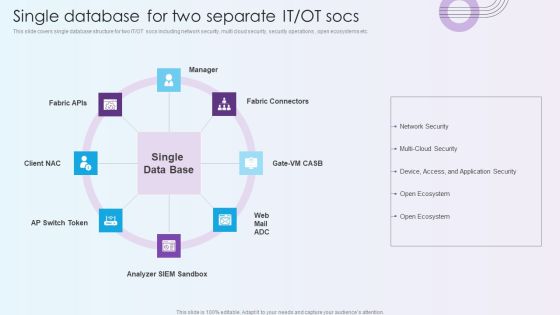
Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc.This is a Digitalization Of Operative Enterprises Single Database For Two Separate IT OT Socs Structure PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Analyzer, Network Security, Multi Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF
This slide represents the official announcement from lotem finkelstein, head of threat intelligence at check point software, that anyone can join ukraine and russia cyber warfare. Slidegeeks is here to make your presentations a breeze with Series Of Cyber Security Attacks Against Ukraine 2022 For The First Time In History Anyone Can Join A War Themes PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
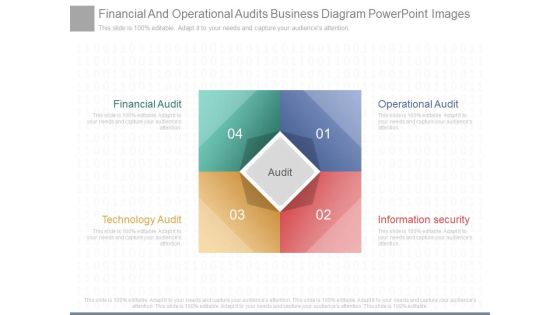
Financial And Operational Audits Business Diagram Powerpoint Images
This is a financial and operational audits business diagram powerpoint images. This is a four stage process. The stages in this process are financial audit, technology audit, operational audit, information security, audit.

IT Risk Control Strategies Risk Management With Human Capital Ppt Outline Format PDF
This slide covers the model for information technology risk management which focuses on risk strategy, governance risk and compliance, security operations and human capital that helps in considering the IT components for risk and threat management. Persuade your audience using this IT Risk Control Strategies Risk Management With Human Capital Ppt Outline Format PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Strategy, Security Operations, Human Capital. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Mutual Fund Operation Flow Chart Diagram Ppt Icon
This is a mutual fund operation flow chart diagram ppt icon. This is a four stage process. The stages in this process are return, securities, investors, fund, mutual fund operation.

Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF
This slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Pitch your topic with ease and precision using this Inclusion Of Automation In ESO System Ppt PowerPoint Presentation File Maker PDF. This layout presents information on Mission, Role, Tier. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

ESO System Center System Ppt PowerPoint Presentation File Portrait PDF
This slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Showcasing this set of slides titled ESO System Center System Ppt PowerPoint Presentation File Portrait PDF. The topics addressed in these templates are Security Risks, Business Security, Data Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Operational Review Plan For Strategic Management Ppt PowerPoint Presentation Infographic Template Graphic Tips PDF
Presenting this set of slides with name operational review plan for strategic management ppt powerpoint presentation infographic template graphic tips pdf. This is a seven stage process. The stages in this process are release, service, infrastructure, support, operations, security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. Presenting Supply Chain Management How Is Iot Significant In Overall Logistics Ideas PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Tracking Products, Securing Operations, Managing Vehicles. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Is Iot Significant In Overall Logistics Sample PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. This is a How Is Iot Significant In Overall Logistics Sample PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking Products, Securing Operations, Managing Vehicles. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

How Is Iot Significant In Overall Logistics Formats PDF
The following slide illustrates role of internet of things IoT in logistics. It provides information about tracking products, securing operations, managing vehicles, unexpected failures, efficiency, costs, sensors, warehouse, supply, etc. This is a How Is Iot Significant In Overall Logistics Formats PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Tracking Products, Securing Operations, Managing Vehicles. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
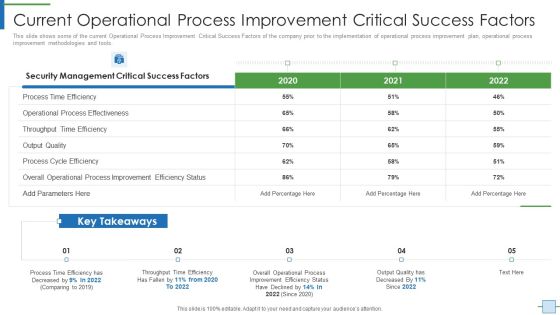
Operational Efficiency Execution Strategy Improve Quality Current Operational Process Topics PDF
This slide shows some of the current Operational Process Improvement Critical Success Factors of the company prior to the implementation of operational process improvement plan, operational process improvement methodologies and tools. Deliver an awe inspiring pitch with this creative operational efficiency execution strategy improve quality current operational process topics pdf bundle. Topics like security management, quality can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Areas Of Operation In Chief Information Officer Transition Plan Template PDF
This slide presents key areas of operation for chief information officer during transition plan, helpful in providing insights on assessment of workforce and strategies by CIO. It includes operating costs, delivery process, talent, architecture, security and compliance. Presenting Key Areas Of Operation In Chief Information Officer Transition Plan Template PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Operating Costs Delivery Process, Talent Architecture, Security Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Graphics PDF
This slide provides information about the fourth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Assigning Resources. This is a operational efficiency execution strategy improve quality operational process improvement plan graphics pdfS template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like team, resource, process, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps Icons PDF
This slide provides information about the first and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e. Process Mapping. Presenting operational efficiency execution strategy improve quality operational process improvement plan steps icons pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like process improvement, applications, graphic software, accountability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Analyzing Business Systems Cooperation Customization Analysis Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name analyzing business systems cooperation customization analysis ppt powerpoint presentation complete deck. The topics discussed in these slides are cooperation, customization, analysis, security, operators. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF
This slide consists of applicability of artificial intelligence and various dimensions in banking industry. The key areas are trend forecasting, customer support, transaction security and operation process. Persuade your audience using this Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Trend Forecasting, Transaction Security, Operation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
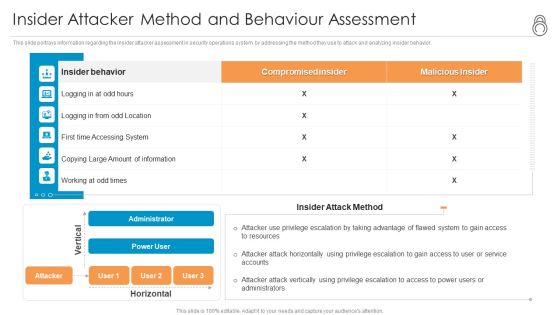
Enhanced Protection Corporate Event Administration Insider Attacker Method And Behaviour Assessment Topics PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver and pitch your topic in the best possible manner with this enhanced protection corporate event administration insider attacker method and behaviour assessment topics pdf. Use them to share invaluable insights on insider attacker method and behaviour assessment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Comparison Assessment Of ESO System Tools Ppt PowerPoint Presentation File Graphics Template PDF
This slide covers comparison assessment of enterprise security operations tools. It involves features such as vulnerability management, penetration testing and privacy standard compliance. Showcasing this set of slides titled Comparison Assessment Of ESO System Tools Ppt PowerPoint Presentation File Graphics Template PDF. The topics addressed in these templates are Cost Involved, Vulnerability Management, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Insider Attacker Method And Behaviour Assessment Information PDF
This slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver an awe inspiring pitch with this creative insider attacker method and behaviour assessment information pdf bundle. Topics like logging in at odd hours, first time accessing system, copying large amount of information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Operational Efficiency Execution Strategy Improve Quality Operational Process Improvement Plan Steps In Detail Formats PDF
This slide provides information about the seventh step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e Monitoring and Optimization. This is a operational efficiency execution strategy improve quality operational process improvement plan steps in detail formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like performance, process optimization, implementation costs. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
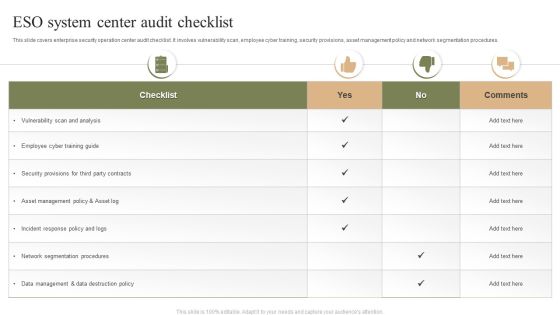
ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF
This slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Showcasing this set of slides titled ESO System Center Audit Checklist Ppt PowerPoint Presentation Gallery Clipart Images PDF. The topics addressed in these templates are Checklist, Employee Cyber, Training Guide. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
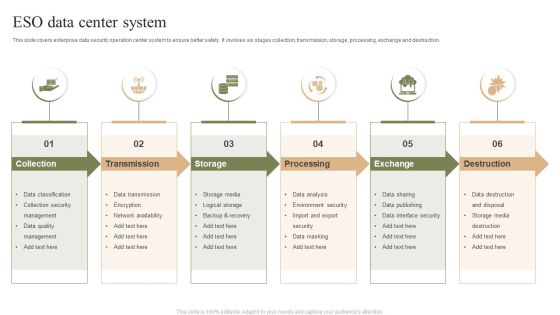
ESO Data Center System Ppt PowerPoint Presentation Gallery Grid PDF
This slide covers enterprise data security operation center system to ensure better safety. It involves six stages collection, transmission, storage, processing, exchange and destruction. Presenting ESO Data Center System Ppt PowerPoint Presentation Gallery Grid PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Collection, Transmission, Storage, Processing, Exchange. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Budget For Effective Secops System Management Themes PDF
Deliver and pitch your topic in the best possible manner with this budget for effective secops system management themes pdf. Use them to share invaluable insights on incident management, information management, client onboarding processFirm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Evolution Of ESO System Center Ppt PowerPoint Presentation File Show PDF
This slide covers evolution of enterprise security operation center. It involves availability monitoring, reactive monitoring, proactive monitoring and monitoring with automation. Pitch your topic with ease and precision using this Evolution Of ESO System Center Ppt PowerPoint Presentation File Show PDF. This layout presents information on Availability Monitoring, Reactive Monitoring, Proactive Monitoring. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Information Protection Policy And Program Implementation Brochure PDF
This slide covers business security policy and program implementation which includes business impact and effectiveness.Showcasing this set of slides titled Business Information Protection Policy And Program Implementation Brochure PDF. The topics addressed in these templates are Acceptable Loss, Business Value Earned, Secure Operational. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Securities Trading Platform Data Flow Charts Ppt PowerPoint Presentation Gallery Icons PDF
This Slides displays a thorough data flow chartsthat graphically illustrates the operations of a securities trading platform, as well as the sources and recipients of the information. It includes five processes such as open account, verify transaction, deposit cash, withdraw cash and place order. Presenting Securities Trading Platform Data Flow Charts Ppt PowerPoint Presentation Gallery Icons PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Account, Transaction, Consumer Service Assistant, Client. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Determine Various Business Models For 5G Operators Rules PDF
This slide provides details regarding various business models for 5G operators such as subscription model, bundling model, usage based model and differentiated pricing model. Deliver an awe inspiring pitch with this creative Determine Various Business Models For 5G Operators Rules PDF bundle. Topics like Customer, Security, Roaming Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Portable Home Safety Systems Company Profile Smart Home Operating System Integration Structure PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. This is a Portable Home Safety Systems Company Profile Smart Home Operating System Integration Structure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Voice Assist, Powered Technology, Software Automatically Running, Real Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Environments Best Suited For Efficient And Secure Supply Chains Ppt Show Example PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains ppt show example pdf bundle. Topics like efficient supply chains, operations strategy, inventory investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
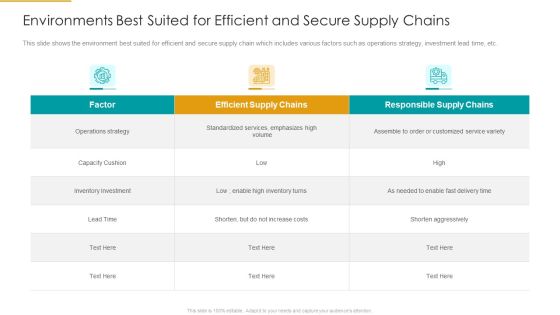
Environments Best Suited For Efficient And Secure Supply Chains Diagrams PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver and pitch your topic in the best possible manner with environments best suited for efficient and secure supply chains diagrams pdf. Use them to share invaluable insights on operations strategy, inventory investment, efficient supply chains, responsible supply chains and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

KPI Dashboard For ESO System Ppt PowerPoint Presentation File Template PDF
This slide covers kpi dashboard for enterprise security operations. It involves details such as active alerts, active automated investigation, devices with major issues and report of daily devices. Pitch your topic with ease and precision using this KPI Dashboard For ESO System Ppt PowerPoint Presentation File Template PDF. This layout presents information on Security Health, Misconfigured, Service Operating Normally. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Five Year Operational And Financial Summary One Pager Documents
Following slide portrays five-year operational summary of the organization covering information about loans, asset-backed securities and venture capital. Presenting you an exemplary Five Year Operational And Financial Summary One Pager Documents. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Five Year Operational And Financial Summary One Pager Documents brilliant piece now.

Enterprise It Evolution Knowledge Management Framework Designs PDF
This slide shows model of information technology knowledge management model. It includes innovation, business, data, information, operations and security model. Presenting Enterprise It Evolution Knowledge Management Framework Designs PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Security Model, Operations Model, Information Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Smart Venture Digitial Transformation Single Database For Two Separate IT OT Socs Inspiration PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Network Security, Multi Cloud Security, Device Access, Application Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
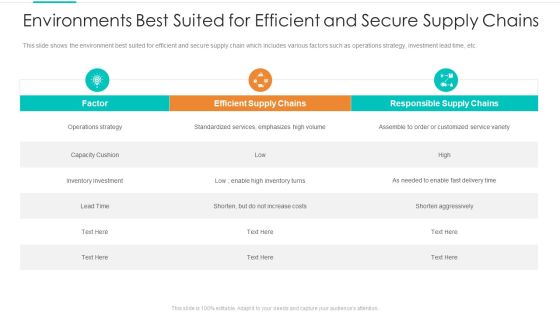
Environments Best Suited For Efficient And Secure Supply Chains Topics PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe-inspiring pitch with this creative environments best suited for efficient and secure supply chains topics pdf bundle. Topics like factor, efficient supply chains, responsible supply chains can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Environments Best Suited For Efficient And Secure Supply Chains Template PDF
This slide shows the environment best suited for efficient and secure supply chain which includes various factors such as operations strategy, investment lead time, etc. Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains template pdf bundle. Topics like inventory investment, strategy, costs can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Benefits Of Desktop As A Service With Operational Savings Ppt PowerPoint Presentation Gallery Visual Aids PDF
Persuade your audience using this benefits of desktop as a service with operational savings ppt powerpoint presentation gallery visual aids pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including operational savings, better security, business continuity. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Application Architecture And Evaluating Software Model Guidelines PDF
This slide defines the application architecture and program model evaluation. It includes information related to users, security, operational management, communication, etc.Showcasing this set of slides titled Application Architecture And Evaluating Software Model Guidelines PDF. The topics addressed in these templates are Interface Components, Interface Process, Business Components. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF
This slide covers single database structure for two IT or OT socs including network security, multi cloud security, security operations , open ecosystems etc. Presenting Convergence Strategy Information Single Database For Two Separate IT OT Socs Rules PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Fabric Connectors, Analyzer SIEM Sandbox, AP Switch Token, Client NAC, Fabric APIs. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home