Security Operations
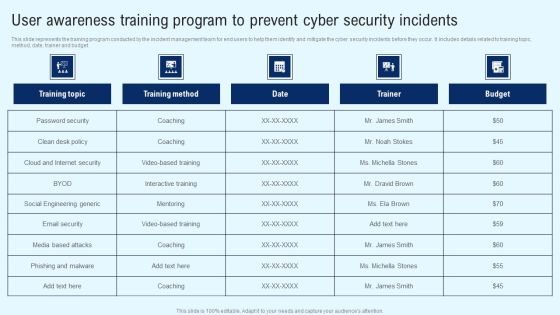
Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. Find highly impressive Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Implementing Cyber Security Incident User Awareness Training Program To Prevent Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Slidegeeks is here to make your presentations a breeze with Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable CYBER Security Breache Response Strategy Cyber Attacks Faced By The Company In Previous Year Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Safety Tips Protection Against Cyberattacks IT Security IT Ppt File Aids PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Presenting cyber safety tips protection against cyberattacks it security it ppt file aids pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like cyber safety tips protection against cyberattacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Cyber Safety Tips Protection Against Cyberattacks Ppt Portfolio Diagrams PDF
This slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. This is a it security cyber safety tips protection against cyberattacks ppt portfolio diagrams pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber safety tips protection against cyberattacks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Our Management For Safety And Security System Services Proposal One Pager Sample Example Document
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc. Presenting you an exemplary Our Management For Safety And Security System Services Proposal One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Management For Safety And Security System Services Proposal One Pager Sample Example Document brilliant piece now.

Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF
The following slide depicts the annual spending of organizations on SaaS security services to prevent data breaches. It constitutes of graph representing the varying expenditure based of the size of the company. Pitch your topic with ease and precision using this Yearly Saas Cloud Security Expenditure Analysis Ppt PowerPoint Presentation File Deck PDF. This layout presents information on Saas Investment, Employees. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

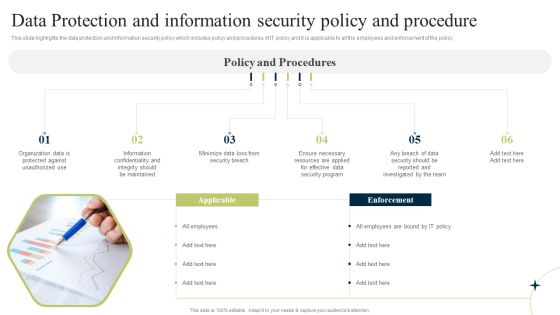
New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. This is a New Staff Orientation Session Data Protection And Information Security Policy And Procedure Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Applicable, Enforcement, Develop Good. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Want to ace your presentation in front of a live audience Our New Staff Onboarding Program Data Protection And Information Security Policy And Procedure Sample PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF
This slide represents the security awareness and training policy. It covers that the training program should be designed by management, and employees will sign a confidentiality agreement after getting the training. Take your projects to the next level with our ultimate collection of IT Policies And Procedures Security Awareness And Training Policy Overview Guidelines PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF
This slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Make sure to capture your audiences attention in your business displays with our gratis customizable Cloud Access Security Broker And User Authentication Ppt PowerPoint Presentation File Deck PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Our Management Proposal For Security Guard Services One Pager Sample Example Document
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc. Presenting you an exemplary Our Management Proposal For Security Guard Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Management Proposal For Security Guard Services One Pager Sample Example Document brilliant piece now.

Web App Firewall Services IT Security Use Cases Of Web Application Firewall Deployment Brochure PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. Presenting web app firewall services it security use cases of web application firewall deployment brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, application, performance, material. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Plan Best Practices To Defend Against Threats Icons PDF
This slide represents cyber security strategy best practices to defend against threats such a development of insider threat program, training employees, maintaining compliance etc. Persuade your audience using this IT Security Plan Best Practices To Defend Against Threats Icons PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Updating Systems And Software, Data Backup, Maintaining Compliance. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Presenting Cyber Intelligent Computing System Safety And Security Objectives In Cyber Physical Systems Ideas PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Availability, Authenticity, Robustness, Integrity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF
This slide represents e banking security measures and features. It includes login details, encrypted data, account management and two factor authorization. This Net Banking Channel And Service Management E Banking Security Measures And Features Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The product features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF
This slide represents cyber-physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. Present like a pro with Cyber Physical System To Enhance Safety And Security Objectives In Cyber Physical Systems Information PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
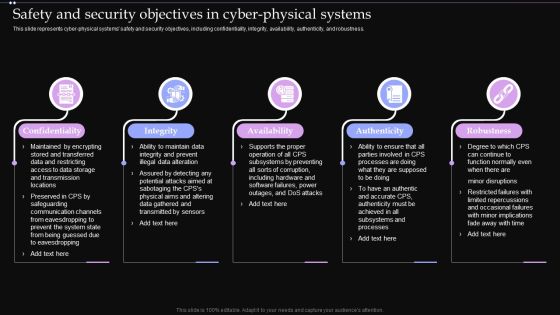
Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF
This slide represents cyber physical systems safety and security objectives, including confidentiality, integrity, availability, authenticity, and robustness. The Safety And Security Objectives In Cyber Physical Systems Ppt PowerPoint Presentation File Example PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
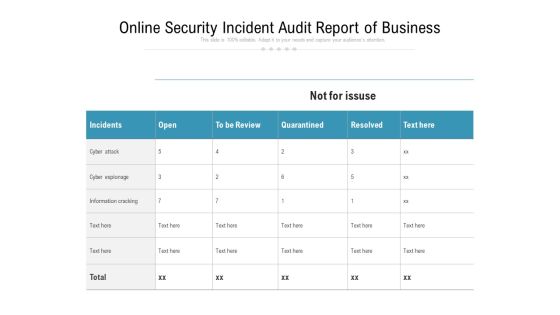
Online Security Incident Audit Report Of Business Ppt PowerPoint Presentation Inspiration Layout Ideas PDF
Pitch your topic with ease and precision using this online security incident audit report of business ppt powerpoint presentation inspiration layout ideas pdf. This layout presents information on incidents, cyber attack, cyber espionage, information cracking. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Proposal For Enterprise Security System Our Management One Pager Sample Example Document
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc. Presenting you an exemplary Proposal For Enterprise Security System Our Management One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Proposal For Enterprise Security System Our Management One Pager Sample Example Document brilliant piece now.

Our Management For Home Security Equipment Installation One Pager Sample Example Document
Purpose of the following slide is to show the team management of the organization as it displays the details of the team members such as name, designation image etc. Presenting you an exemplary Our Management For Home Security Equipment Installation One Pager Sample Example Document. Our one pager comprises all the must have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Management For Home Security Equipment Installation One Pager Sample Example Document brilliant piece now.

Our Team For Security Camera Sarvices One Pager Sample Example Document
This slide shows the project execution team with the individual members name, designation, and brief work description. Presenting you an exemplary Our Team For Security Camera Sarvices One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Our Team For Security Camera Sarvices One Pager Sample Example Document brilliant piece now.

Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF
This slide shows vital monitoring strategies for countering insider threat. It provides information about monitoring, protecting sensitive data, ascertaining user access, implementing least privilege model, applying security analytics and training employees. Persuade your audience using this Key Monitoring Strategies To Counter Insider Threat In Cyber Security Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitoring User Data, Protecting Sensitive Data, Protecting Sensitive Data. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Upgrading Total Project Safety IT Facilities Rendered By Security Centre Implementation Sample PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting upgrading total project safety it facilities rendered by security centre implementation sample pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage.Presenting Security And Surveillance Company Profile End To End Service Delivery Model Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Sales Representative, Experienced Engineers, Engineers Installers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
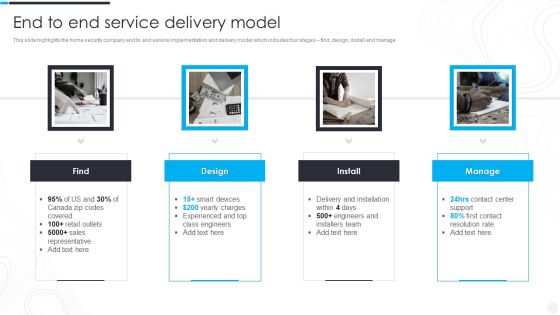
Security Camera System Company Profile End To End Service Delivery Model Clipart PDF
This slide highlights the home security company end to end service implementation and delivery model which includes four stages find, design, install and manage.Presenting Security Camera System Company Profile End To End Service Delivery Model Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Charges Experienced, Sales Representative, Delivery And Installation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Case Study For Security Camera Services One Pager Sample Example Document
This slide represents the case study highlighting the successful execution of a similar project in the past by the bidding company. It provides information about the business problem, solution, and results. Presenting you an exemplary Case Study For Security Camera Services One Pager Sample Example Document. Our one-pager comprises all the must-have essentials of an inclusive document. You can edit it with ease, as its layout is completely editable. With such freedom, you can tweak its design and other elements to your requirements. Download this Case Study For Security Camera Services One Pager Sample Example Document brilliant piece now.

Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF
This slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. The Net Banking Channel And Service Management Major Types Of E Banking Security Threats Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
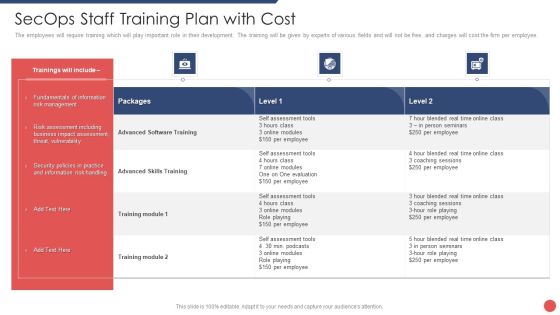
Security Functioning Centre Secops Staff Training Plan With Cost Information PDF
The employees will require training which will play important role in their development. The training will be given by experts of various fields and will not be free, and charges will cost the firm per employee. Deliver an awe inspiring pitch with this creative security functioning centre secops staff training plan with cost information pdf bundle. Topics like risk assessment, business, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
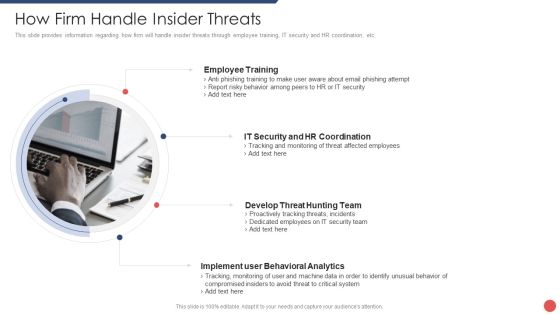
Security Functioning Centre How Firm Handle Insider Threats Ppt Summary Background Image PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a security functioning centre how firm handle insider threats ppt summary background image pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF
This slide describes the international cyber assistance to ukraine by 6 european union nations such as lithuania, the netherlands, poland, estonia, romania, and croatia. Get a simple yet stunning designed Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Series Of Cyber Security Attacks Against Ukraine 2022 International Cyber Aid To Ukraine Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Blockchain Security Solutions Deployment Preventive Measures Against Ddos Attacks Professional PDF
This slide represents the steps to prevent distributed daniel of service attacks in blockchain technology. The purpose of this slide is to showcase the different security measures against ddos attacks, including implementing traffic filtering, employing load balancing, utilizing rate limiting and so on.. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Blockchain Security Solutions Deployment Preventive Measures Against Ddos Attacks Professional PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Three Lines Of Defense Border Model For Cyber Security Designs PDF
This slide represents the model of lines of defense for products and services quality assurance. It includes activities performed in first, second and third line of defense for quality assurance such as risk management, monitor and support in risk related matters, internal quality audits etc. Presenting Three Lines Of Defense Border Model For Cyber Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security, Three Lines, Border Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
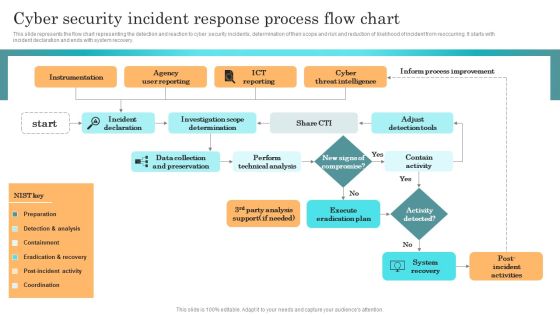
Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Incident Response Techniques Deployement Cyber Security Incident Response Process Flow Chart Slides PDF from Slidegeeks and deliver a wonderful presentation.

Elements Of IT Security IT End User Education Ppt Model Deck PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. This is a elements of it security it end user education ppt model deck pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hire professional, train often, password protocols, microlearning opportunities, effective training. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Problem Faced By The Organization Hacking Prevention Awareness Training For IT Security Rules PDF
This slide covers the problem faced by organization caused by employees due to lack of security awareness training programs. This is a problem faced by the organization hacking prevention awareness training for it security rules pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like corporate, cybersecurity, financial. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Evolving BI Infrastructure Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting evolving bi infrastructure facilities offered by implementation of security centre formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Current Potential Implications Faced By Firm As Threats Clipart PDF
This slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization current potential implications faced by firm as threats clipart pdf. Use them to share invaluable insights on infectiveness, expertise, issues, security, increase and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
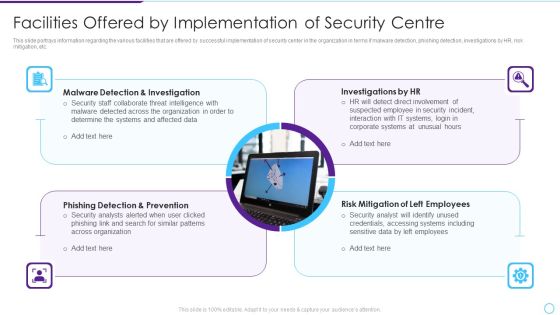
Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a Intelligent Infrastructure Facilities Offered By Implementation Of Security Centre Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Malware Detection And Investigation, Investigations by HR, Phishing Detection And Prevention, Risk Mitigation of Left Employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Presenting Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Incident Management, Asset Management, Risk Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting Developing Business Analytics Framework Facilities Offered By Implementation Of Security Centre Information PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Detection And Investigation, Phishing Detection, Left Employees In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How To Overcome The Security Awareness Training Program Challenges Clipart PDF
The purpose of this is to highlight various solutions which can be used to overcome the cyber security awareness challenges. The key solutions covered in the slide are introducing dynamic courses, fully managed training program, convenient program etc. Deliver and pitch your topic in the best possible manner with this How To Overcome The Security Awareness Training Program Challenges Clipart PDF. Use them to share invaluable insights on Burden On Administrators, Employee Participation, Lose Interest and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF
The purpose of this slide is to exhibit variety of strategies which can be used to engage employees in the security awareness training plan. The strategies highlighted in the slide are gamification, personalization, high-quality content and variety. This is a Strategies We Will Implement To Make Security Awareness Training Interactive Brochure PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Gamification, Personalization, High Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF
Purpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc.This is a IT Threats Response Playbook Best Work From Home Data Security Practices Icons PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Update, Malicious Attachments, Connection Accurately. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Want to ace your presentation in front of a live audience Our Budget For Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF
This slide represent roadmap for various cyber security task and process like response planning ,risk assessment progress in an organization with timeline. It includes hours per week ,owner and start date. Pitch your topic with ease and precision using this Cyber Security Roadmap With Process And Tasks Ppt PowerPoint Presentation Gallery Topics PDF. This layout presents information on Response Planning, Risk Assessment, Response Communication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
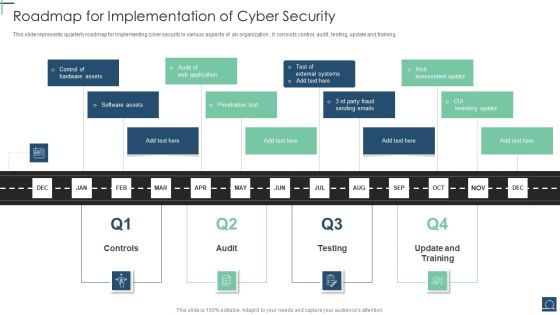
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
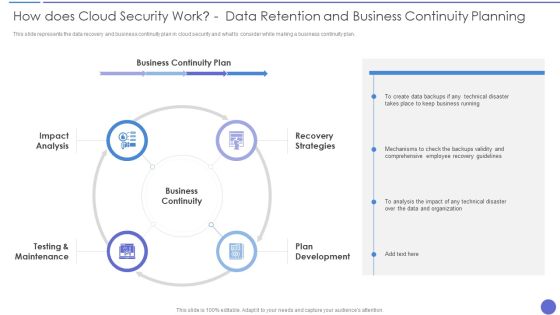
How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Presenting How Does Cloud Security Work Data Retention And Business Continuity Planning Template PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Continuity, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF
This slide represents the security use cases of web application firewall and how it would stop cyberattacks such as DDoS attacks, malicious bot abuse, and customer data breaches. This is a Security Use Cases Of Web Application Firewall Deployment WAF Platform Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Mitigate Ddos Attacks, Prevent Customer Data Breach, Block Malicious Bot Abuse. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Table Of Contents For Information Security Risk Administration And Mitigation Plan Slide Download PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Table Of Contents For Information Security Risk Administration And Mitigation Plan Slide Download PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Table Of Contents For Information Security Risk Administration And Mitigation Plan Slide Download PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
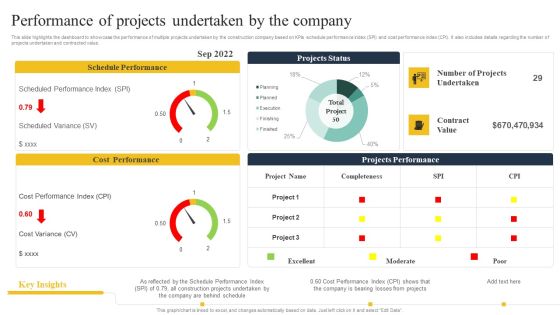
Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF
Do you have to make sure that everyone on your team knows about any specific topic. I yes, then you should give Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security Control Techniques For Real Estate Project Performance Of Projects Undertaken By The Company Brochure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Information Systems Security And Risk Management Plan Venn Diagram Topics PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Information Systems Security And Risk Management Plan Venn Diagram Topics PDF can be your best option for delivering a presentation. Represent everything in detail using Information Systems Security And Risk Management Plan Venn Diagram Topics PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF
Whether you have daily or monthly meetings, a brilliant presentation is necessary. Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF can be your best option for delivering a presentation. Represent everything in detail using Recent Technologies In IT Industry Objectives Of Cyber Security Technology Guidelines PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
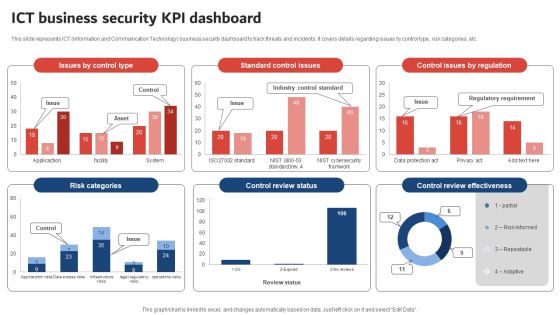
Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF
This slide represents ICT Information and Communication Technology business security dashboard to track threats and incidents. It covers details regarding issues by control type, risk categories, etc. Boost your pitch with our creative Execution Of ICT Strategic Plan ICT Business Security KPI Dashboard Designs PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. Make sure to capture your audiences attention in your business displays with our gratis customizable Incident Response Techniques Deployement Cyber Security Incident Communication Strategy Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
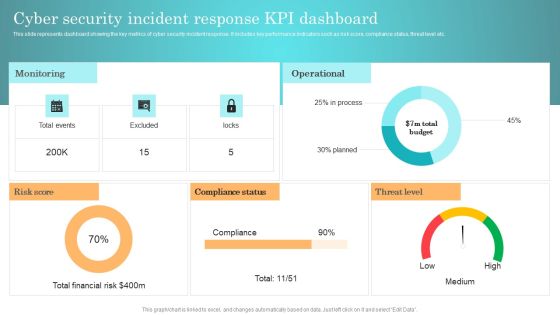
Incident Response Techniques Deployement Cyber Security Incident Response KPI Dashboard Background PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Incident Response Techniques Deployement Cyber Security Incident Handler Contact Information Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.
Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Security Software Company Investor Funding Pitch Deck Contact Us Thank You Sample PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Comprehensive Guide For Ensuring IT Infrastructure Security Table Of Contents Summary PDF
Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Comprehensive Guide For Ensuring IT Infrastructure Security Table Of Contents Summary PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Comprehensive Guide For Ensuring IT Infrastructure Security Table Of Contents Summary PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today

 Home
Home