Security Operating Model
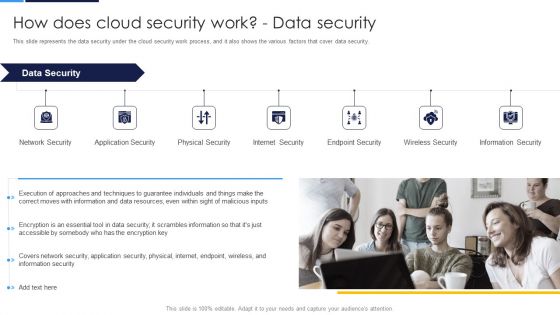
Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Presenting Cloud Security Assessment How Does Cloud Security Work Data Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Impact Analysis, Recovery Strategies, Plan Development. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
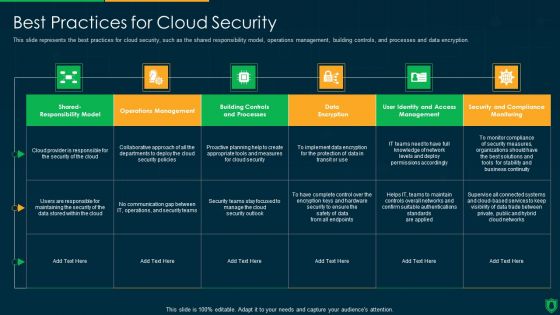
Info Security Best Practices For Cloud Security Ppt PowerPoint Presentation Gallery Visual Aids PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver and pitch your topic in the best possible manner with this info security best practices for cloud security ppt powerpoint presentation gallery visual aids pdf. Use them to share invaluable insights on communication gap, data encryption, operations management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

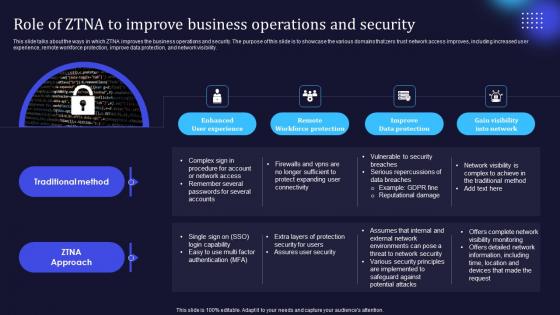
Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Take your projects to the next level with our ultimate collection of Role Of ZTNA To Improve Business Operations And Security Zero Trust Network Security Inspiration Pdf. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest
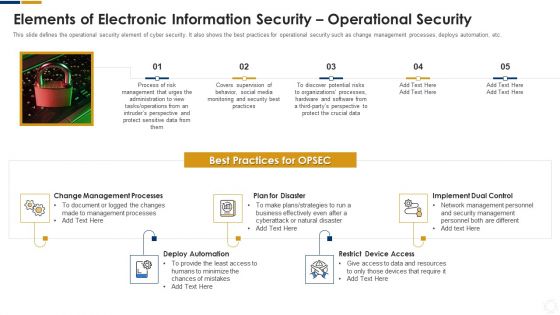
Cybersecurity Elements Of Electronic Information Security Operational Security Ppt Portfolio Rules PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting cybersecurity elements of electronic information security operational security ppt portfolio rules pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, risk, plans, strategies, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
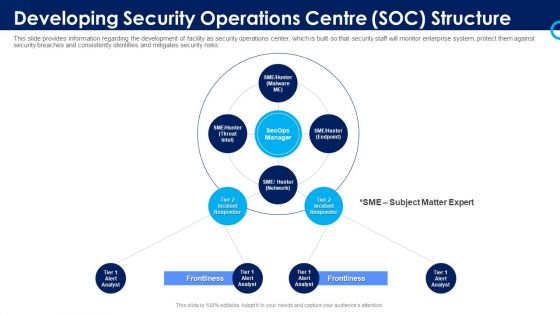
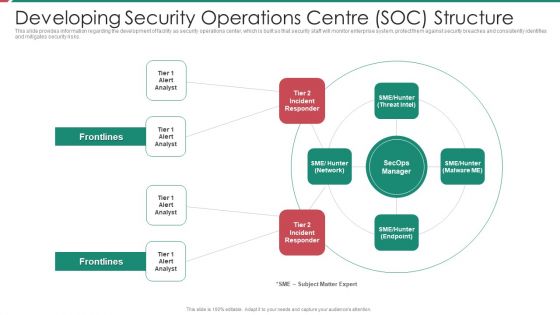
Organizational Security Solutions Developing Security Operations Centre SOC Structure Introduction PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting organizational security solutions developing security operations centre soc structure introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Security And Process Integration Developing Security Operations Centre SOC Structure Inspiration PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting security and process integration developing security operations centre soc structure inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Operations Center With Integrated Security Framework Ppt Gallery Graphics Design PDF
Showcasing this set of slides titled cyber security operations center with integrated security framework ppt gallery graphics design pdf. The topics addressed in these templates are security, framework, management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
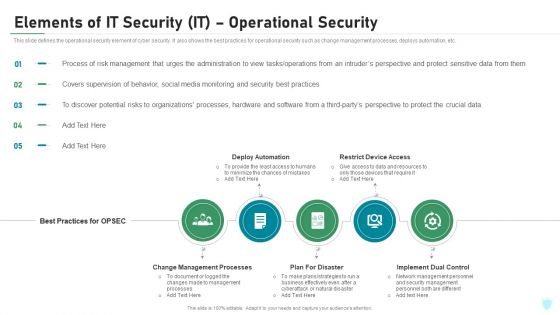
Elements Of IT Security IT Operational Security Ppt Outline Ideas PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Presenting elements of it security it operational security ppt outline ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like change management processes, deploy automation, restrict device access, plan for disaster, implement dual control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
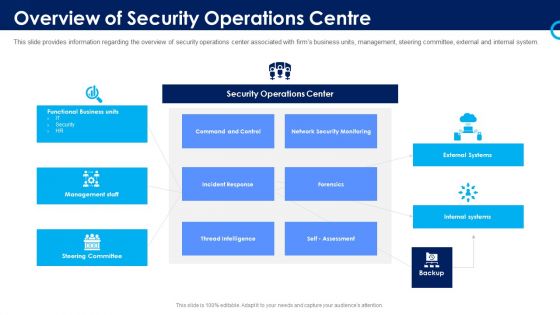
Organizational Security Solutions Overview Of Security Operations Centre Ppt Styles Graphics Pictures PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this organizational security solutions overview of security operations centre ppt styles graphics pictures pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
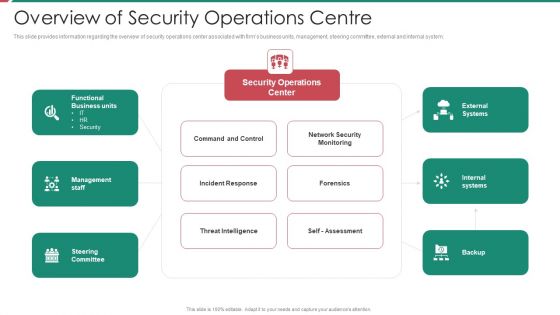
Security And Process Integration Overview Of Security Operations Centre Portrait PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security and process integration overview of security operations centre portrait pdf. Use them to share invaluable insights on intelligence, security, monitoring, business, management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Elements Of Information Technology Security Operational Security Ppt Icon Guidelines PDF
This slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. This is a elements of information technology security operational security ppt icon guidelines pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process, sensitive, management, administration, operations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
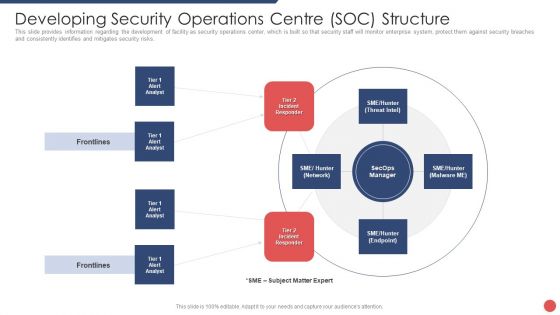
Security Functioning Centre Developing Security Operations Centre SOC Structure Guidelines PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Deliver and pitch your topic in the best possible manner with this security functioning centre developing security operations centre soc structure guidelines pdf. Use them to share invaluable insights on incident responder, analyst, network and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Information And Technology Security Operations Impact Of Effective Security Management Icons PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative information and technology security operations impact of effective security management icons pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
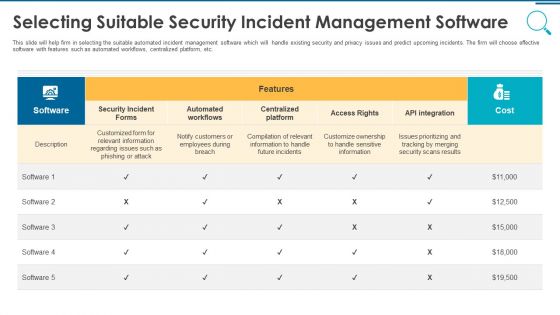
Information And Technology Security Operations Selecting Suitable Security Incident Management Software Diagrams PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative information and technology security operations selecting suitable security incident management software diagrams pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
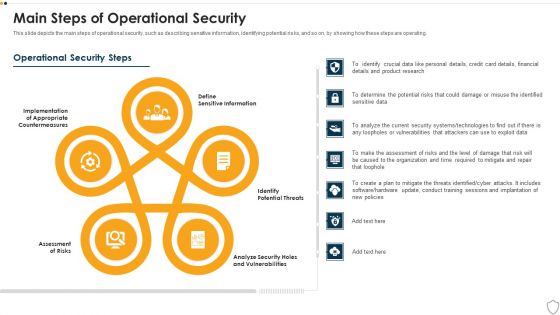
IT Security Main Steps Of Operational Security Ppt Show Design Inspiration PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Presenting it security main steps of operational security ppt show design inspiration pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like assessment of risks, potential threats, sensitive information, analyze security holes and vulnerabilities, implementation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Security Operations Implementation Timeline Staff Ideas PDF
This slide provides information regarding the security operations system implementation timeline with key activities mentioned. Deliver and pitch your topic in the best possible manner with this security and process integration security operations implementation timeline staff ideas pdf. Use them to share invaluable insights on assess resources, develop soc structure, determine secops deliverables and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
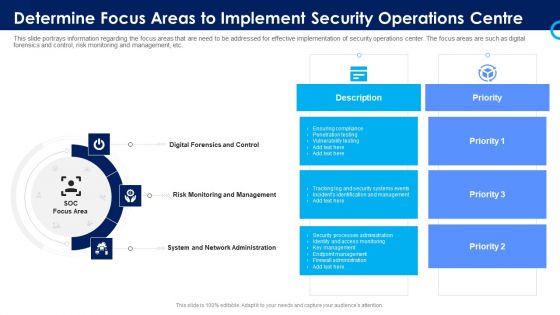
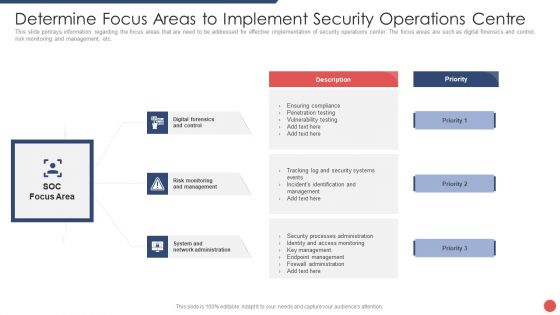
Organizational Security Solutions Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a organizational security solutions determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Security Functioning Centre Determine Focus Areas To Implement Security Operations Centre Demonstration PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security functioning centre determine focus areas to implement security operations centre demonstration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk monitoring, management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration Determine Focus Areas To Implement Security Operations Centre Sample PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. This is a security and process integration determine focus areas to implement security operations centre sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital forensics and control, risk monitoring and management, system and network administration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
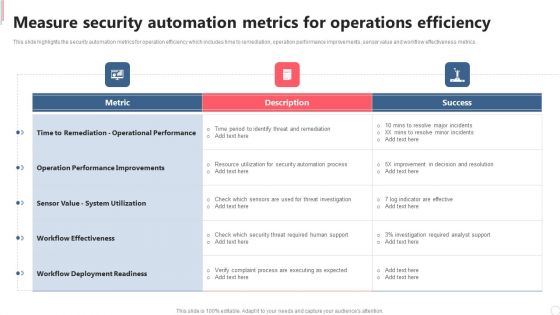
Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Information And Technology Security Operations How Security Concerns Affect Firm In Present Times Rules PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative information and technology security operations how security concerns affect firm in present times rules pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
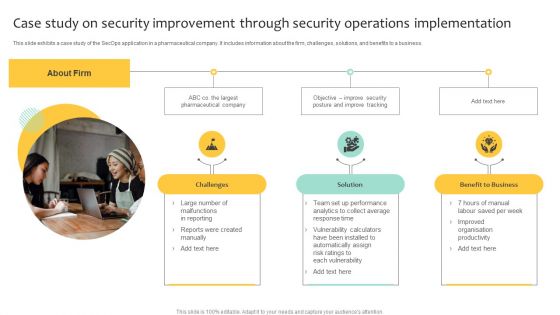
Case Study On Security Improvement Through Security Operations Implementation Mockup PDF
This slide exhibits a case study of the SecOps application in a pharmaceutical company. It includes information about the firm, challenges, solutions, and benefits to a business. Persuade your audience using this Case Study On Security Improvement Through Security Operations Implementation Mockup PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Benefit To Business, Organisation Productivity, Average. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Retrieve professionally designed Organizing Security Awareness Operational Outlook Of Security Awareness Training Ideas PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Workforce Security Realization Coaching Plan Organization Cyber Security Dashboard Template PDF
This slide covers the cyber security key performance indicators for the organization including application health, device license consumption, data encryption status and many more. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan organization cyber security dashboard template pdf bundle. Topics like makes and models, operating systems, encryption status, application health, license consumption can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Zero Trust Model Role Of ZTNA To Improve Business Operations And Security
This slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Boost your pitch with our creative Zero Trust Model Role Of ZTNA To Improve Business Operations And Security. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.
IT Security Best Practices For Cloud Security Ppt Icon Pictures PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting it security best practices for cloud security ppt icon pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like operations management, security and compliance monitoring, data encryption. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
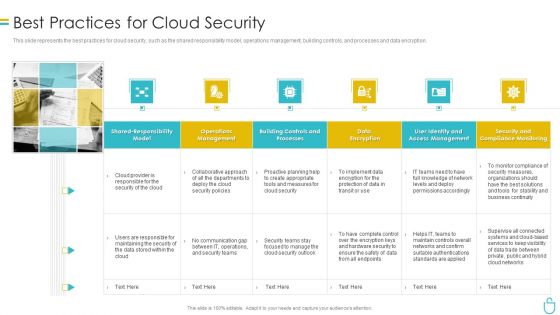
Information Security Best Practices For Cloud Security Ppt Ideas Deck PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting information security best practices for cloud security ppt ideas deck pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security, measures, planning, teams, network. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Devsecops Development Security And Operations Role Of Devsecops Ppt Template
This slide discusses the working process of development, security and operations in DevSecOps. The purpose of this slide is to highlight the process followed by DevSecOps for providing, monitoring and managing security at each level of the software system. Find highly impressive Devsecops Development Security And Operations Role Of Devsecops Ppt Template on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Devsecops Development Security And Operations Role Of Devsecops Ppt Template for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
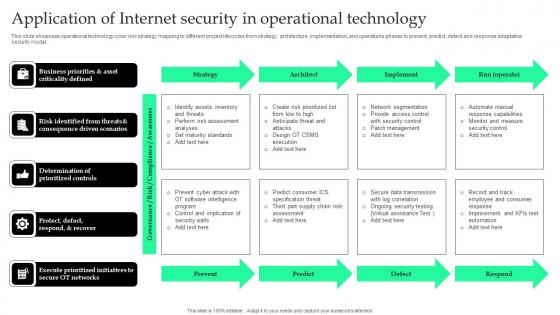
Application Of Internet Security In Operational Technology Pictures Pdf
This slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model.Showcasing this set of slides titled Application Of Internet Security In Operational Technology Pictures Pdf The topics addressed in these templates are Consequence Driven Scenarios, Execute Prioritized, Risk Identified All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Operations Training Department Program Chart Infographics PDF
This slide covers employees training in organizations based on different security operations. It includes training based on security policy, incident management, security audit, cybersecurity, malware analysis, etc. Showcasing this set of slides titled Information Security Operations Training Department Program Chart Infographics PDF. The topics addressed in these templates are Induction Complete, Company Security Policy, Incident Management. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Android Operating System Of Smartphones Vector Icon Ppt PowerPoint Presentation Gallery Design Templates PDF
Presenting android operating system of smartphones vector icon ppt powerpoint presentation gallery design templates pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including android operating system of smartphones vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Operations Center Framework Ppt Styles Portfolio PDF
Showcasing this set of slides titled cyber security operations center framework ppt styles portfolio pdf. The topics addressed in these templates are cyber security operations center framework. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Operations Team Roles And Responsibilities Infographics PDF
This slide exhibits key roles on the SecOps team with their roles and responsibilities that manage cybersecurity threats and attacks. It includes a security investigator, advanced security analyst, SOC manager, and security manager. Presenting Security Operations Team Roles And Responsibilities Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Skills Required, Determine, Develop Mitigation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Technology Operations Security Management Icon Designs PDF
Presenting Information Technology Operations Security Management Icon Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Information Technology Operations, Security Management Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Operations Management Skills Software Security Skills Pictures PDF
This slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Presenting operations management skills software security skills pictures pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Methods To Improve Online Banking Security Incorporating Banking Operational Growth
The purpose of the mentioned slide is to showcase the various ways to improve Internet banking security from hackers and fraudants. It includes methods such as industry-standard security protocol, avoiding public Wi-Fi, etc. Do you know about Slidesgeeks Methods To Improve Online Banking Security Incorporating Banking Operational Growth These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Developing Security Operations Centre SOC Structure Microsoft PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting developing security operations centre soc structure microsoft pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident responder, tier 2 incident responder, frontlines. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF
This slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Get a simple yet stunning designed Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cybersecurity Operations Cybersecops Key Responsibilities Of Command Security Rules PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Cyber Security Operations Center Vector Icon Ppt Pictures Shapes PDF
Presenting cyber security operations center vector icon ppt pictures shapes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cyber security operations center vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

5G Network Operations Security Architecture In 5G Technology Inspiration PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications cloud infrastructure, and user ID administration. Presenting this PowerPoint presentation, titled 5G Network Operations Security Architecture In 5G Technology Inspiration PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this 5G Network Operations Security Architecture In 5G Technology Inspiration PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable 5G Network Operations Security Architecture In 5G Technology Inspiration PDFthat is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
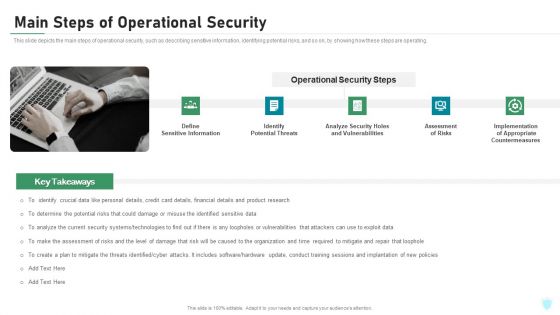
Main Steps Of Operational Security Ppt Ideas Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a main steps of operational security ppt ideas summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential threats, analyze security holes and vulnerabilities, assessment of risks, implementation of appropriate countermeasures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Operations Compliance And Security Testing Ppt PowerPoint Presentation Summary Icon
This is a operations compliance and security testing ppt powerpoint presentation summary icon. This is a three stage process. The stages in this process are quality assurance, quality analysis, qa, testing process, bugs analysis.

Security Operations Center Ppt PowerPoint Presentation Gallery Template
Presenting this set of slides with name security operations center ppt powerpoint presentation gallery template. This is an editable Powerpoint three stages graphic that deals with topics like security operations center to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Operational Technology Security Ppt PowerPoint Presentation Professional Show Cpb Pdf
Presenting this set of slides with name operational technology security ppt powerpoint presentation professional show cpb pdf. This is an editable Powerpoint seven stages graphic that deals with topics like operational technology security to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Effective Security Operations Tools To Prevent Cyber Threats Formats PDF
This slide includes some SecOps tools that provide a more secure working environment to organisations by improving collaboration between operations and security teams. It includes elements such as tools, pricing, features, rating, free version, and free trial. Pitch your topic with ease and precision using this Effective Security Operations Tools To Prevent Cyber Threats Formats PDF. This layout presents information on Develops, Organization Security, Compliance Requirements. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
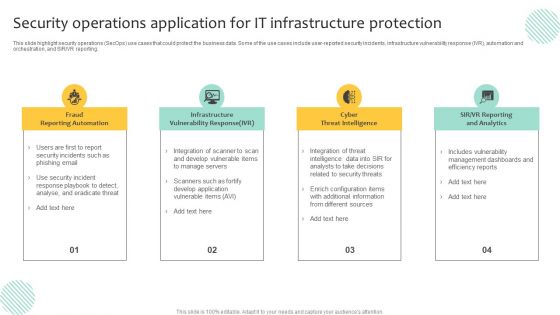
Security Operations Application For IT Infrastructure Protection Template PDF
This slide highlight security operations SecOps use cases that could protect the business data. Some of the use cases include user-reported security incidents, infrastructure vulnerability response IVR, automation and orchestration, and SIR or VR reporting. Presenting Security Operations Application For IT Infrastructure Protection Template PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Infrastructure Vulnerability Response, Cyber Threat Intelligence, Fraud Reporting Automation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Information Security Operations Training Department Program Icon Introduction PDF
Persuade your audience using this Information Security Operations Training Department Program Icon Introduction PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Information Security, Operations Training, Department Program, Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
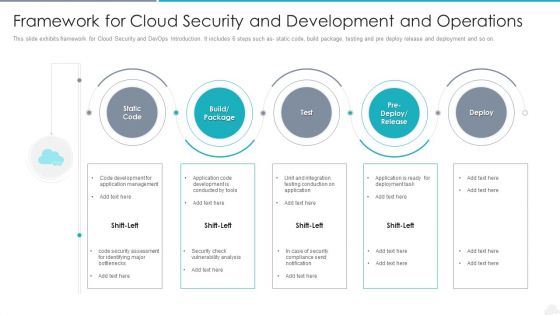
Framework For Cloud Security And Development And Operations Elements PDF
Presenting framework for cloud security and development and operations elements pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including management, application, development. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Facility Operations Contol 4 Dimensions Of Infrastructure Security Brochure PDF
Presenting this set of slides with name facility operations contol 4 dimensions of infrastructure security brochure pdf. The topics discussed in these slides are people, data, applications, infrastructure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Operations Essential Functions For Customer Satisfaction Inspiration PDF
This slide highlights key functions performed by SecOps team members in order to meet IT infrastructure network security objectives. It includes security monitoring, threat intelligence, triage and investigations, incident response, and root cause analysis. Persuade your audience using this Security Operations Essential Functions For Customer Satisfaction Inspiration PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Triage And Investigation, Incident Response, Root Course Analysis. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Operational Outlook Of Security Awareness Training Software Icons PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Deliver an awe inspiring pitch with this creative Operational Outlook Of Security Awareness Training Software Icons PDF bundle. Topics like Educate Employees, Dynamic Training, Customized Content can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Determine Focus Areas To Implement Security Operations Centre Diagrams PDF
This slide portrays information regarding the focus areas that are need to be addressed for effective implementation of security operations center. The focus areas are such as digital forensics and control, risk monitoring and management, etc. Deliver an awe inspiring pitch with this creative determine focus areas to implement security operations centre diagrams pdf bundle. Topics like digital forensics and control, risk monitoring and management, system and network administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Operations Metrics For Detection And Response Effectiveness Structure PDF
Showcasing this set of slides titled Security Operations Metrics For Detection And Response Effectiveness Structure PDF. The topics addressed in these templates are Operations Metrics, Detection, Response Effectiveness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Security Agreement Operate Ppt PowerPoint Presentation Complete Deck
Presenting this set of slides with name data security agreement operate ppt powerpoint presentation complete deck. The topics discussed in these slides are operate, data, accountability framework, data privacy, public interest, risk assessment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Comparison Analysis Between Security Operations And Devops Inspiration PDF
This slide summarizes the difference between SecOps and DevOps methodologies that increase the efficiency and scalability of complex operations. It includes parameters such as goal, processing strategy, change implementation, focus on, team involved, etc. Showcasing this set of slides titled Comparison Analysis Between Security Operations And Devops Inspiration PDF. The topics addressed in these templates are Implementation, Processing Strategy, Security Infrastructure. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Information And Technology Security Operations Icons Slide Elements PDF
Introducing our well designed information and technology security operations icons slide elements pdf set of slides. The slide displays editable icons to enhance your visual presentation. The icons can be edited easily. So customize according to your business to achieve a creative edge. Download and share it with your audience.
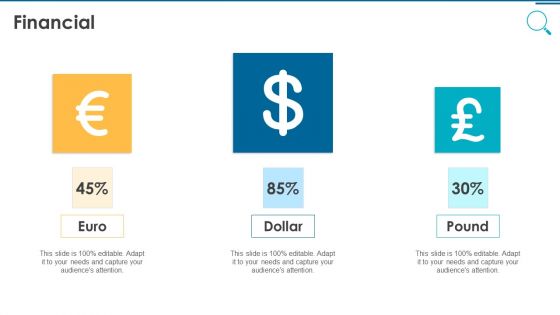
Information And Technology Security Operations Financial Information PDF
Presenting information and technology security operations financial information pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like euro, dollar, pound. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
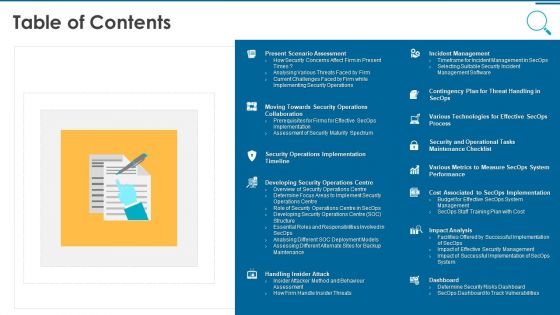
Information And Technology Security Operations Table Of Contents Pictures PDF
This is a information and technology security operations table of contents pictures pdf template with various stages. Focus and dispense information on thirteen stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like management, implementation, analysis, technologies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Workforce Half Yearly Work Roadmap Operations And Security Ideas
Presenting our innovatively structured workforce half yearly work roadmap operations and security ideas Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Workforce Quarterly Work Roadmap Operations And Security Demonstration
Introducing our workforce quarterly work roadmap operations and security demonstration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Workforce Three Months Work Roadmap Operations And Security Ideas
Presenting our jaw dropping workforce three months work roadmap operations and security ideas. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Prevention Of Information Operational Outlook Of Security Awareness Structure PDF
The purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered. Slidegeeks has constructed Prevention Of Information Operational Outlook Of Security Awareness Structure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

International Security Operations Financial Ppt PowerPoint Presentation Complete Deck
Improve your presentation delivery using this international security operations financial ppt powerpoint presentation complete deck. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Security Operations Ppt PowerPoint Presentation Complete Deck With Slides
If designing a presentation takes a lot of your time and resources and you are looking for a better alternative, then this Security Operations Ppt PowerPoint Presentation Complete Deck With Slides is the right fit for you. This is a prefabricated set that can help you deliver a great presentation on the topic. All the seventeen slides included in this sample template can be used to present a birds-eye view of the topic. These slides are also fully editable, giving you enough freedom to add specific details to make this layout more suited to your business setting. Apart from the content, all other elements like color, design, theme are also replaceable and editable. This helps in designing a variety of presentations with a single layout. Not only this, you can use this PPT design in formats like PDF, PNG, and JPG once downloaded. Therefore, without any further ado, download and utilize this sample presentation as per your liking.

Deploying Safe Operating Procedures In The Organization Operational Safety Guidelines Air Compressor Demonstration PDF
This slides highlights the operational safety guidelines to minimize air compressor hazards. It showcases different protective gears with pre operation, operation and post operation. This modern and well arranged Deploying Safe Operating Procedures In The Organization Operational Safety Guidelines Air Compressor Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
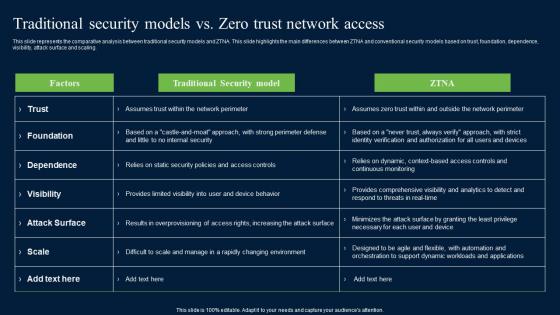
Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Traditional Security Models Vs Zero Trust Network Access Security Mockup Pdf and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
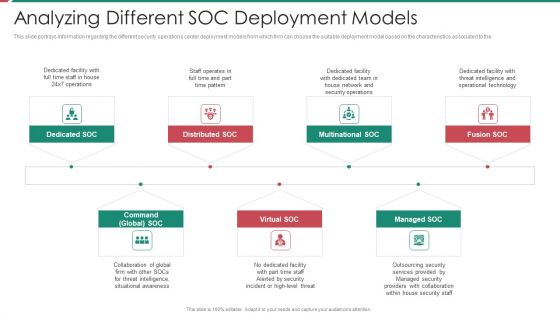
Security And Process Integration Analyzing Different SOC Deployment Models Diagrams PDF
This slide portrays information regarding the different security operations center deployment models from which firm can choose the suitable deployment model based on the characteristics associated to the. This is a security and process integration analyzing different soc deployment models diagrams pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like multinational soc, distributed soc, dedicated soc, command global soc, virtual soc. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
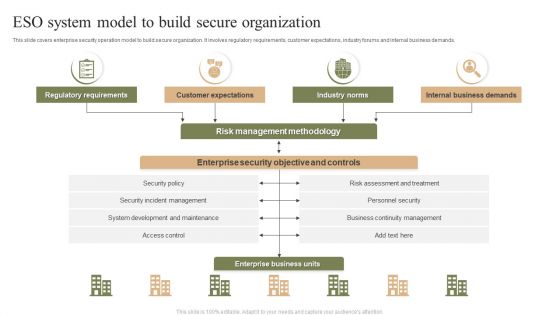
ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF
This slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Showcasing this set of slides titled ESO System Model To Build Secure Organization Ppt PowerPoint Presentation File Layout PDF. The topics addressed in these templates are Customer Expectations, Industry Norms, Internal Business Demands. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Strategies To Mitigate Cyber Security Risks Role Of Management In Effective Information Security Governance Ppt Model File Formats PDF
Presenting this set of slides with name strategies to mitigate cyber security risks role of management in effective information security governance ppt model file formats pdf. The topics discussed in these slides are strategic alignment, risk management, measuring performance, value delivery, managing resource, integration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Zero Trust Model Traditional Security Models Vs Zero Trust Network Access
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Zero Trust Model Traditional Security Models Vs Zero Trust Network Access and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Business Model Canvas Security Service Provider Business Model BMC SS V
This slide provides the business model canvas of the company. It involves key partners, key activities, USP, customer relationships, customer segments, channels, revenue streams, channels, key resources, cost structure. Find a pre-designed and impeccable Business Model Canvas Security Service Provider Business Model BMC SS V. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
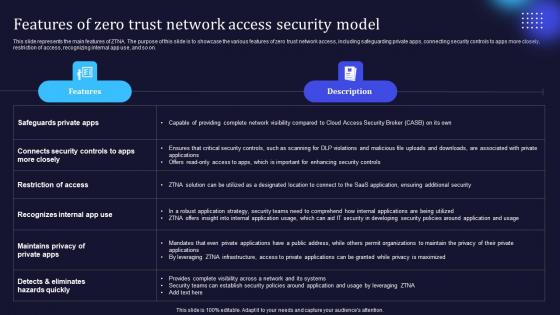
Zero Trust Model Features Of Zero Trust Network Access Security Model
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. This modern and well-arranged Zero Trust Model Features Of Zero Trust Network Access Security Model provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
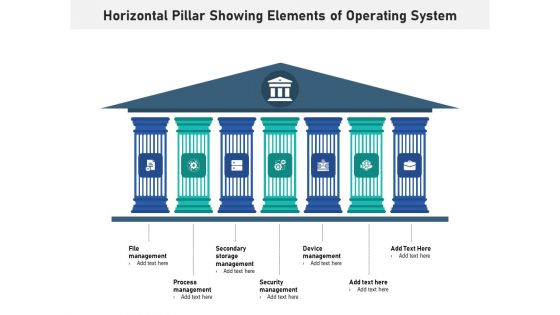
Horizontal Pillar Showing Elements Of Operating System Ppt PowerPoint Presentation Layouts Graphics Pictures PDF
Presenting horizontal pillar showing elements of operating system ppt powerpoint presentation layouts graphics pictures pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including file management, process management, secondary storage management, security management, device management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF
This slide represents the comparison between zero trust network access versions 1.0 and 2.0. The purpose of this slide is to demonstrate the overview of both versions, including differences. It also includes the architecture of both versions of zero-trust network access. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Secure Access Service Edge Cloud Security Model ZTNA 10 Vs ZTNA 20 Ppt Gallery Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Portable Home Safety Systems Company Profile Smart Home Operating System Integration Structure PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. This is a Portable Home Safety Systems Company Profile Smart Home Operating System Integration Structure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Voice Assist, Powered Technology, Software Automatically Running, Real Time. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.

Enterprise Security Business Template Ppt Images
This is a enterprise security business template ppt images. This is a eight stage process. The stages in this process are enterprise security, authentication, applications, network security, infrastructure security, audit and monitoring, system security, active security, operational excellence.

Cybersecurity Best Practices For Cloud Security Ppt Ideas Images PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Presenting cybersecurity best practices for cloud security ppt ideas images pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like measures, security, planning, network, systems. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Best Practices For Cloud Security Ppt Infographics Show PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. This is a best practices for cloud security ppt infographics show pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like processes, management, monitoring, data encryption, implement. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security And Policy Example Ppt Design
This is a information security and policy example ppt design. This is a six stage process. The stages in this process are client and operation structure, training and presentation, information flow, aggregation control, department size vs operation size, access control and network infrastructure.

Security Awareness Training Program Challenges Rules PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Presenting Security Awareness Training Program Challenges Rules PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Outdated Content, Burden On Administrators, Employee Participation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
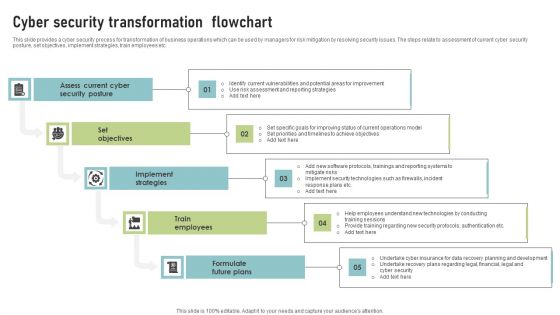
Cyber Security Transformation Flowchart Template PDF
This slide provides a cyber security process for transformation of business operations which can be used by managers for risk mitigation by resolving security issues. The steps relate to assessment of current cyber security posture, set objectives, implement strategies, train employees etc. Presenting Cyber Security Transformation Flowchart Template PDF to dispense important information. This template comprises Five stages. It also presents valuable insights into the topics including Assess Current Cyber, Security Posture, Set Objectives. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Strategic Agenda Checklist Mockup Pdf
This slide represents action plan of checklist of cyber security. It further includes tasks such as determine potential areas like challenges regarding cyber security and security loopholes, etc and their status. Showcasing this set of slides titled Cyber Security Strategic Agenda Checklist Mockup Pdf. The topics addressed in these templates are Cyber Security, Strategic Agenda Checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Evaluation Matrix Survey SS
This slide shows risk assessment table of cyber security that tells about the severity of different threats. It includes threats like phishing, ransomware and web app attacks etc. Pitch your topic with ease and precision using this Cyber Security Risk Evaluation Matrix Survey SS. This layout presents information on Cyber Security, Risk Evaluation Matrix, Web App Attacks. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
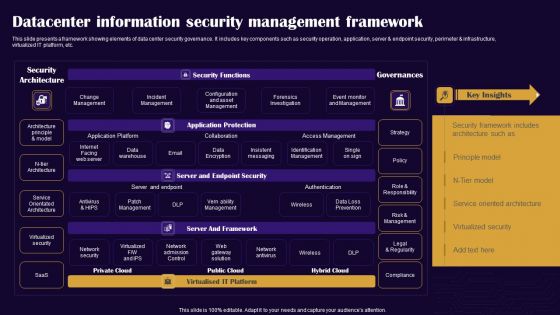
Datacenter Information Security Management Framework Professional PDF
This slide presents a framework showing elements of data center security governance. It includes key components such as security operation, application, server and endpoint security, perimeter and infrastructure, virtualized IT platform, etc. Pitch your topic with ease and precision using this Datacenter Information Security Management Framework Professional PDF. This layout presents information on Security Architecture, Security Functions, Governances. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
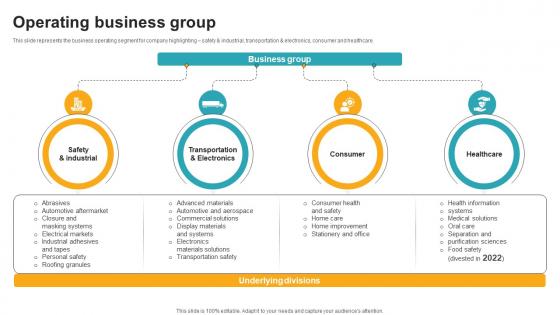
Operating Business Group Innovative Industrial Solutions Company Profile CP SS V
This slide represents the business operating segment for company highlighting safety and industrial, transportation and electronics, consumer and healthcare.Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Operating Business Group Innovative Industrial Solutions Company Profile CP SS V to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
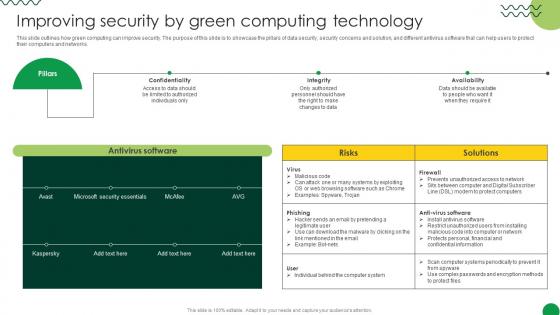
Sustainable Improving Security By Green Computing Technology
This slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Create an editable Sustainable Improving Security By Green Computing Technology that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Sustainable Improving Security By Green Computing Technology is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
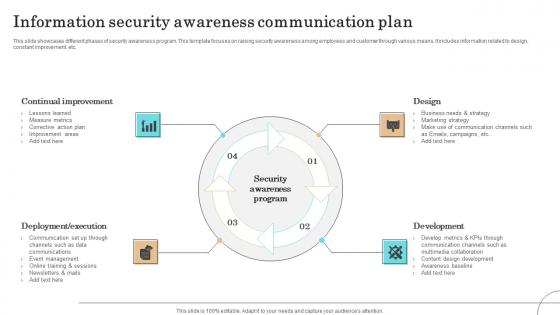
Information Security Awareness Communication Plan Formats Pdf
This slide showcases different phases of security awareness program. This template focuses on raising security awareness among employees and customer through various means. It includes information related to design, constant improvement, etc.Pitch your topic with ease and precision using this Information Security Awareness Communication Plan Formats Pdf This layout presents information on Continual Improvement, Deployment Execution, Communication It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Managing IT Operating System Ppt PowerPoint Presentation Complete Deck With Slides
Presenting this set of slides with name managing it operating system ppt powerpoint presentation complete deck with slides. The topics discussed in these slides are introduction, process, management, security, inventory. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security Handbook For Corporate Personnel Information Pdf
Create an editable Security Handbook For Corporate Personnel Information Pdf that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Security Handbook For Corporate Personnel Information Pdf is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
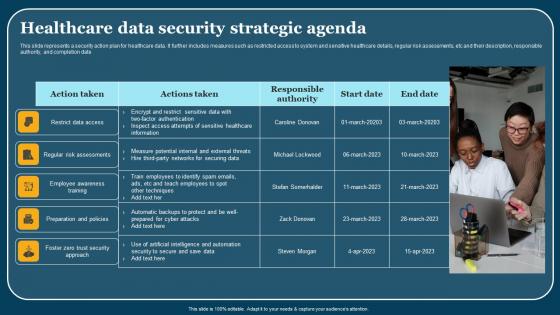
Healthcare Data Security Strategic Agenda Themes Pdf
This slide represents a security action plan for healthcare data. It further includes measures such as restricted access to system and sensitive healthcare details, regular risk assessments, etc and their description, responsible authority, and completion date. Showcasing this set of slides titled Healthcare Data Security Strategic Agenda Themes Pdf. The topics addressed in these templates are Employee Awareness Training, Action Taken. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Computer Operating System Services Investment Fundraising Problems Faced By Companies Demonstration PDF
This slide provides the glimpse about the problem faced by the companies such as network security, professional and qualified experience, backup issues, hardware and software concerns, etc.This is a computer operating system services investment fundraising problems faced by companies demonstration pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hardware and software concerns, poor network security, lack of professional and qualified experience. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Smartphone Operating System Development IT Linux Kernel As Layer Of Android Architecture Information PDF
This slide represents the Linux kernel as layer of android architecture which is the core component of android architecture.Deliver an awe inspiring pitch with this creative smartphone operating system development it linux kernel as layer of android architecture information pdf bundle. Topics like process management for security, memory administration, device administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Smartphone Operating System Development IT Top Benefits Of Ios App Development For Business Infographics PDF
This slide depicts the top benefits of iOS app development for business, including high security, upgraded user experience, increased return on investment, etc.Presenting smartphone operating system development it top benefits of ios app development for business infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like high security, increased return on investment, upgraded user experience In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
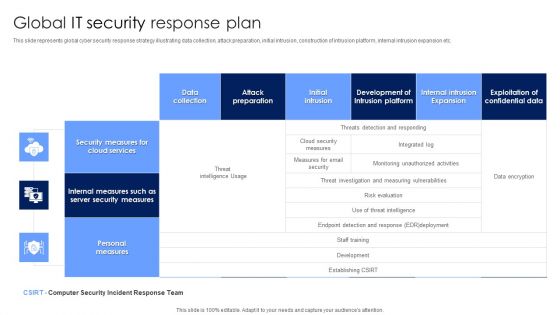
Global IT Security Response Plan Diagrams PDF
This slide represents global cyber security response strategy illustrating data collection, attack preparation, initial intrusion, construction of intrusion platform, internal intrusion expansion etc. Showcasing this set of slides titled Global IT Security Response Plan Diagrams PDF. The topics addressed in these templates are Security Measures, Cloud Services, Personal Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
IT Security Hacker Agenda Background PDF
Presenting IT Security Hacker Agenda Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Agenda. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
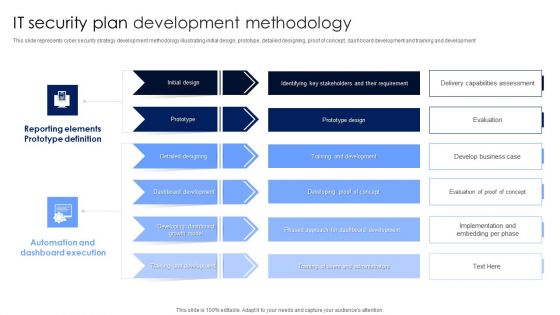
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
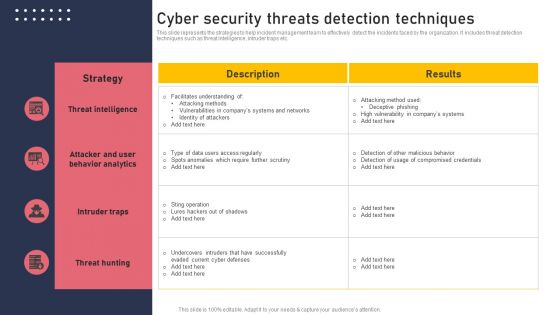
Cyber Security Threats Detection Techniques Demonstration PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Create an editable Cyber Security Threats Detection Techniques Demonstration PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Cyber Security Threats Detection Techniques Demonstration PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
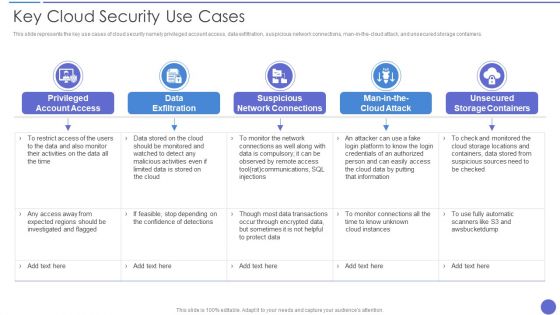
Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
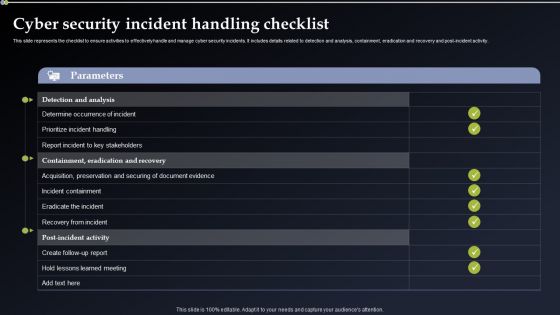
Cyber Security Incident Handling Checklist Elements PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Take your projects to the next level with our ultimate collection of Cyber Security Incident Handling Checklist Elements PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.
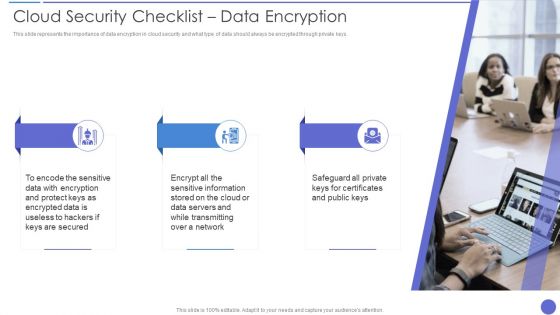
Cloud Security Checklist Data Encryption Professional PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Presenting Cloud Security Checklist Data Encryption Professional PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Protect Keys, Encrypted Data, Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Revenue Losses Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Security Threats Revenue Losses Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Organizations, Revenue, Investing Money. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
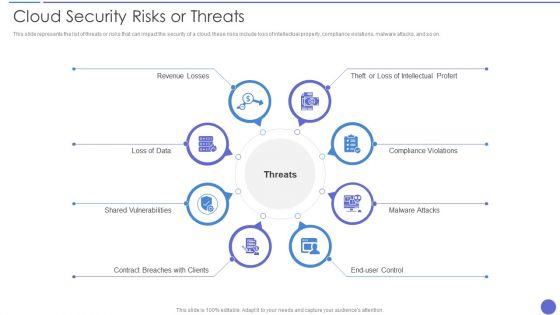
Cloud Security Risks Or Threats Brochure PDF
This slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Security Risks Or Threats Brochure PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Revenue Losses, Shared Vulnerabilities, Malware Attacks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
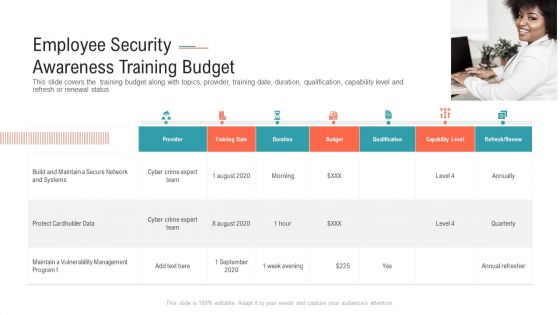
Employee Security Awareness Training Budget Sample PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status Presenting employee security awareness training budget sample pdf. to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like build and maintain a secure network and systems, protect cardholder data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Incident Communication Strategy Formats PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Cyber Security Incident Communication Strategy Formats PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cyber Security Incident Handling Checklist Information PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Welcome to our selection of the Cyber Security Incident Handling Checklist Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
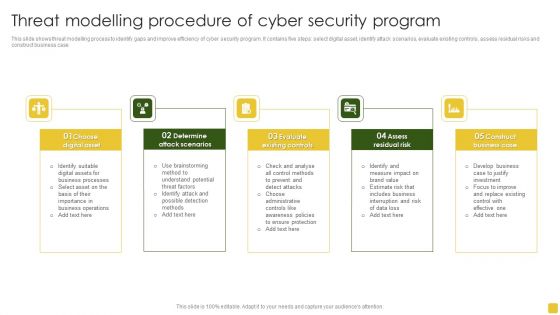
Threat Modelling Procedure Of Cyber Security Program Elements PDF
This slide shows threat modelling process to identify gaps and improve efficiency of cyber security program. It contains five steps select digital asset, identify attack scenarios, evaluate existing controls, assess residual risks and construct business case.Presenting Threat Modelling Procedure Of Cyber Security Program Elements PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Digital Asset, Attack Scenarios, Evaluate Existing. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
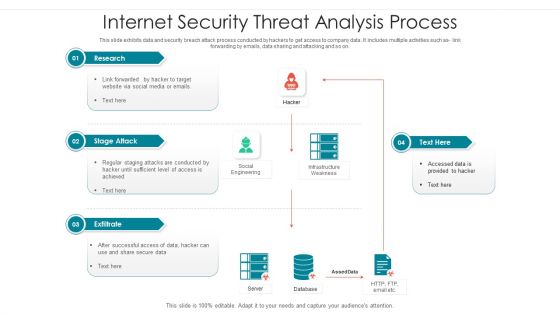
Internet Security Threat Analysis Process Brochure PDF
Following slide showcase how a data breach process is performed by hacker to collect and utilize company data. It includes following activities such as code integration with company software, so on. Showcasing this set of slides titled internet security threat analysis process brochure pdf. The topics addressed in these templates are supply chain attack, execution persistence, defense evasion, exfiltration, keyboard attack. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Traditional Security Models Vs Zero Trust Network Access Summary PDF
This slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. This modern and well-arranged Traditional Security Models Vs Zero Trust Network Access Summary PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Deploying Safe Operating Procedures In The Organization Core Elements And Recommended Practices Safety Elements PDF
This slide highlights the recommended practices for safety management at organization level which includes management leadership, worker participation, hazard identification and prevention and education and training program. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Safe Operating Procedures In The Organization Core Elements And Recommended Practices Safety Elements PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Safe Operating Procedures In The Organization Core Elements And Recommended Practices Safety Elements PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
Deploying Safe Operating Procedures In The Organization Safety Guidelines To Control Fire At Workplace Designs PDF
This slide highlights the measures to control fire at workplace which includes steps such as raise the alarm, alert everyone, fight fire and evacuate from the worksite. Are you searching for a Deploying Safe Operating Procedures In The Organization Safety Guidelines To Control Fire At Workplace Designs PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Deploying Safe Operating Procedures In The Organization Safety Guidelines To Control Fire At Workplace Designs PDF from Slidegeeks today.
Deploying Safe Operating Procedures In The Organization Objectives Of Workplace Safety Rules PDF
The following slide highlights the major objectives for workplace safety in accordance with organization. The multiple objectives could be having safety in organization, increase in productivity and considering safety as of utmost priority. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Deploying Safe Operating Procedures In The Organization Objectives Of Workplace Safety Rules PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Deploying Safe Operating Procedures In The Organization Objectives Of Workplace Safety Rules PDF
Deploying Safe Operating Procedures In The Organization Safety Education And Training Program For Workers Inspiration PDF
This slide highlights the safety training program for workers which includes safe lifting, chemical hazards, fire extinguisher safety, forklift training, respiratory training and lockout training. Explore a selection of the finest Deploying Safe Operating Procedures In The Organization Safety Education And Training Program For Workers Inspiration PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Deploying Safe Operating Procedures In The Organization Safety Education And Training Program For Workers Inspiration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Important Attributes Of Mobile Operating With Webview Ppt PowerPoint Presentation Inspiration Icon PDF
Persuade your audience using this important attributes of mobile operating with webview ppt powerpoint presentation inspiration icon pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including application planning, application backup, authentication. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home