Security Incident
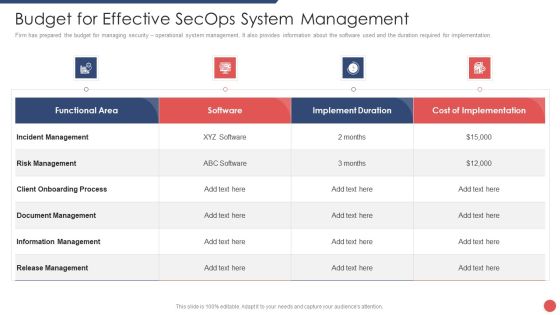
Security Functioning Centre Budget For Effective Secops System Management Formats PDF
Firm has prepared the budget for managing security operational system management. It also provides information about the software used and the duration required for implementation. Deliver and pitch your topic in the best possible manner with this security functioning centre budget for effective secops system management formats pdf. Use them to share invaluable insights on incident management, risk management, client onboarding process and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

COVID 19 Mitigating Impact On High Tech Industry Security Maturity Hierarchy Including Five Levels Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry security maturity hierarchy including five levels brochure pdf. The topics discussed in these slides are business unit, awareness and training, compliance and it audit, emerging it threats, incident response ir, operations and support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
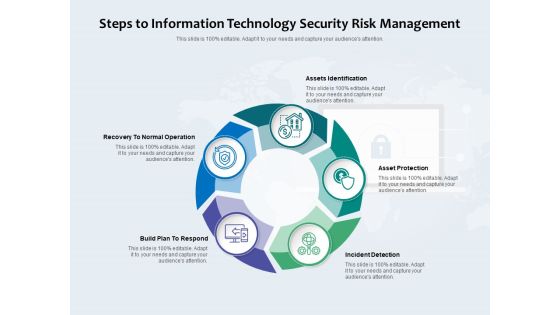
Steps To Information Technology Security Risk Management Ppt PowerPoint Presentation Gallery Example File PDF
Presenting steps to information technology security risk management ppt powerpoint presentation gallery example file pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including assets identification, asset protection, incident detection, build plan to respond, recovery to normal operation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
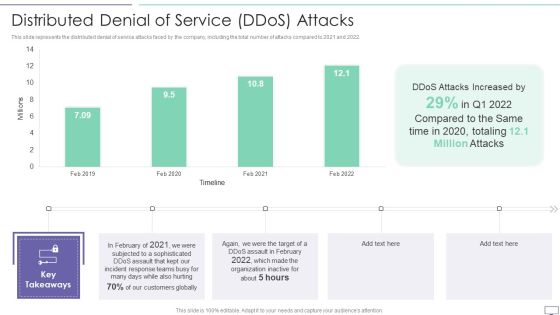
IT Security Hacker Distributed Denial Of Service Ddos Attacks Template PDF
This slide represents the distributed denial of service attacks faced by the company, including the total number of attacks compared to 2021 and 2022.Deliver and pitch your topic in the best possible manner with this IT Security Hacker Distributed Denial Of Service Ddos Attacks Template PDF. Use them to share invaluable insights on Attacks Increased, Incident Response, Customers Globally and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Strategies To Mitigate Cyber Security Risks Table Of Contents Ppt Inspiration Professional PDF
Presenting this set of slides with name strategies to mitigate cyber security risks table of contents ppt inspiration professional pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role personnel, cost associated to firm, impact analysis dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Implementation Framework Table Of Contents Ppt PowerPoint Presentation Icon Portfolio PDF
Presenting this set of slides with name cyber security implementation framework table of contents ppt powerpoint presentation icon portfolio pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, cybersecurity contingency plan, role of personnel, cost associated to firm, impact analysis, dashboard. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Budget For Effective Cybersecurity Management Ppt Ideas Objects PDF
Presenting this set of slides with name cyber security for your organization budget for effective cybersecurity management ppt ideas objects pdf. This is a one stage process. The stages in this process are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Administration In Organization Budget For Effective Threat Management At Workplace Structure PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative cyber security administration in organization budget for effective threat management at workplace structure pdf bundle. Topics like incident management, onboarding, process, release can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Risk Management Model For Data Security Diagrams PDF
This is a Table Of Contents For Risk Management Model For Data Security Diagrams PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Present Scenario, Incident Management, Managing Risks, Dashboards, Training And Budget. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Risk Management Plan Defining The Severity Levels Of Risk Template PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan defining the severity levels of risk template pdf. Use them to share invaluable insights on risk level, risk score, description and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Supporting Policies Microsoft PDF
Presenting cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like transactional monitoring, develop and execute, incident management plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF
Mentioned slide delineates comparison of managed security service packages on the basis of bronze, silver and gold plan. The services covered in the packages are incident prevention, detection and response. Showcasing this set of slides titled Comparative Assessment Of Managed Cyber Security Solutions Service Packages Ppt Gallery Inspiration PDF. The topics addressed in these templates are Threat Intelligence, Vulnerability Management, Monitoring. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF
The following slide illustrates the seven pillars of SaaS security to protect organizations from cyber attack and data breaches. It includes elements such as access management, network control, VM management, data protection, incident management etc. Presenting Seven Pillars Of Saas Application Cloud Security Ppt PowerPoint Presentation File Tips PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including VM Management, Data Protection, Network Control, Perimeter Network Control. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost.Presenting Cybersecurity Risk Administration Plan Budget For Information Security Management Elements PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Incident Management, Asset Management, Risk Management In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
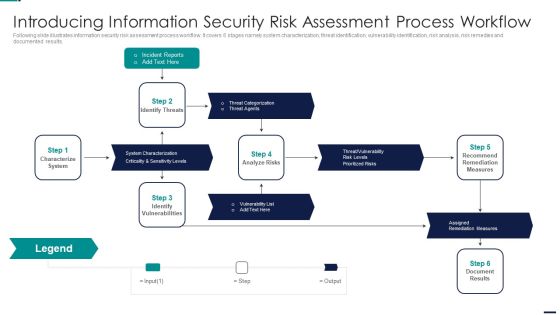
Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a Risk Management Model For Data Introducing Information Security Risk Assessment Process Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incident Reports, Characterize System, Identify Vulnerabilities, Assigned Remediation Measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Security And Risk Management Determine Threat Management Team Structure Topics PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a corporate security and risk management determine threat management team structure topics pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like determine threat management team structure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Administration In Organization Determine Threat Management Team Structure Information PDF
The threat management team generally comprise of senior management personnel that have authority and resources to accelerate the companys internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Presenting cyber security administration in organization determine threat management team structure information pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like determine threat management team structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Administration In Organization Impact Analysis Of Successful Threat Management Ideas PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization impact analysis of successful threat management ideas pdf. Use them to share invaluable insights on handling, service, resolution, customer, relationship and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Budget For Effective Threat Management At Workplace Portrait PDF
Firm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative corporate security and risk management budget for effective threat management at workplace portrait pdf bundle. Topics like incident management, risk management, client onboarding process, document management, information management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Corporate Security And Risk Management Impact Analysis Of Successful Threat Sample PDF
This slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the Deliver and pitch your topic in the best possible manner with this corporate security and risk management impact analysis of successful threat sample pdf. Use them to share invaluable insights on focus area, past state, present state, benefit and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
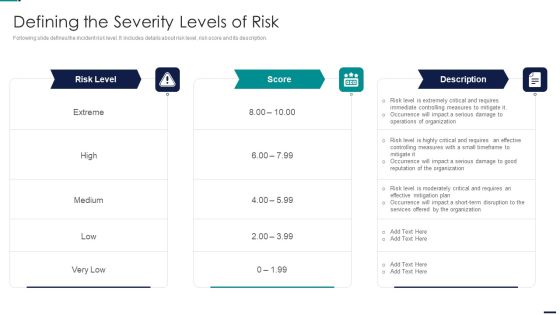
Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. This is a Risk Management Model For Data Security Defining The Severity Levels Of Risk Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risk Level, Score, High, Low, Medium, Operations, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF
This slide provides information about enabling online brand protection by tracking incidents per seller, incident per platform and infringements per country. Presenting this PowerPoint presentation, titled Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Organizational Assets Security Management Strategy Dashboard To Ensure Online Brand Protection Pictures PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Presenting this PowerPoint presentation, titled Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Mitigation Strategies To Avoid Information Breach Information Security Risk Administration Rules PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Pictures PDF
This slide provides information about the first and the foremost step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e., Establishing a Security Monitoring Strategy and Supporting Policies. This is a cybersecurity monitoring plan steps in detail establish a security monitoring strategy and pictures pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident management, transactional monitoring, monitoring plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF
This slide showcases strategies that can help organization to avoid information breach. Key strategies include implement antivirus software, monitor network traffic, incident response plan, patch management schedule and establish network access controls. Explore a selection of the finest Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Information Systems Security And Risk Management Plan Mitigation Strategies To Avoid Information Breach Graphics PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Project Security Administration IT Determine Project Safety Management Team Structure Sample PDF
This slide provides information regarding project safety management team generally comprise of senior management personnel that have authority and resources to accelerate IT projects incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. This is a project security administration it determine project safety management team structure sample pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like public affair advisor, security manager, legal advisor, medical advisor, crisis management advisor. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF
This slide represents the common sources of signs which indicates that an incident may occur in the future. It includes details related to common sources of precursors and indicators such as IDPSs, SIEMs, network device logs etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate CYBER Security Breache Response Strategy Common Sources Of Precursors And Indicators Elements PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Developing IT Security Strategy Mitigation Strategies To Avoid Information Breach Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Governance Risk Management And Compliance Services Overview Introduction PDF
Mentioned slide outlines various governance, risk and compliance GRC services offered by third party to a company. The key services mentioned in the slide are vulnerability response, risk management, security incident response, internal audit management, compliance management etc. Presenting Governance Risk Management And Compliance Services Overview Introduction PDF to dispense important information. This template comprises ten stages. It also presents valuable insights into the topics including Threat Detection, Risk Management, Security Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF
This slide highlights scorecard related to security breaches in gaming field. The purpose of this template is to rate the incidents based on severity. It includes elements such as account taken over, personal details posting on web, spyware, data breaches and cyber bullying. Showcasing this set of slides titled Gaming Cyber Security Cases Action Plan Scorecard For Response Ppt PowerPoint Presentation File Styles PDF. The topics addressed in these templates are Incident, Score, Data Breaches, Low, High. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF
This slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc. Pitch your topic with ease and precision using this Software Checklist To Respond Cyber Security Cases Action Plan Ppt PowerPoint Presentation File Visuals PDF. This layout presents information on Cyber Security, Confidential Information Leakage, Hacker Changed Password. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Key In The Labyrinth Choice Security PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212.Present our Business PowerPoint Templates because you have had your share of being a goldfish in a small bowl.you are ready to launch out and spread your wings. Download our Security PowerPoint Templates because our creative template will lay down your views. Present our Marketing PowerPoint Templates because networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilities. Download and present our Success PowerPoint Templates because your quest has taken you well onto the path of success. Download our Shapes PowerPoint Templates because you have the moves to sway the market.Use these PowerPoint slides for presentations relating to Key in the labyrinth security, security, business, marketing, success, shapes. The prominent colors used in the PowerPoint template are White, Yellow, Gray. We assure you our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Fun. Customers tell us our success PowerPoint templates and PPT Slides are Beautiful. Customers tell us our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Swanky. The feedback we get is that our success PowerPoint templates and PPT Slides are Spectacular. PowerPoint presentation experts tell us our Key In The Labyrinth Choice Security PowerPoint Templates PPT Backgrounds For Slides 1212 are Ultra. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides are Majestic.

Padlock And Coins Financial Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Security PowerPoint Templates because It is Aesthetically crafted by artistic young minds. Our PowerPoint Templates and Slides are designed to display your dexterity. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download and present our finance PowerPoint Templates because You can Connect the dots. Fan expectations as the whole picture emerges. Download our Money PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Use our Future PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow.Use these PowerPoint slides for presentations relating to Financial security with lock and coins, security, business, finance, money, future. The prominent colors used in the PowerPoint template are Yellow, Brown, Black. People tell us our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113 are designed by a team of presentation professionals. People tell us our business PowerPoint templates and PPT Slides are the best it can get when it comes to presenting. PowerPoint presentation experts tell us our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. PowerPoint presentation experts tell us our lock PowerPoint templates and PPT Slides have awesome images to get your point across. Presenters tell us our Padlock And Coins Financial Security PowerPoint Templates PPT Backgrounds For Slides 0113 are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. The feedback we get is that our finance PowerPoint templates and PPT Slides are visually appealing.

Project Security Administration IT Technological Assessment Of Firm Current Management Capabilities Professional PDF
This slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this project security administration it technological assessment of firm current management capabilities professional pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Technological Assessment Of Firm Current Management Elements PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization technological assessment of firm current management elements pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Corporate Security And Risk Management Technological Assessment Of Firm Current Designs PDF
This slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Deliver and pitch your topic in the best possible manner with this corporate security and risk management technological assessment of firm current designs pdf. Use them to share invaluable insights on technological assessment of firm current management capabilities and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
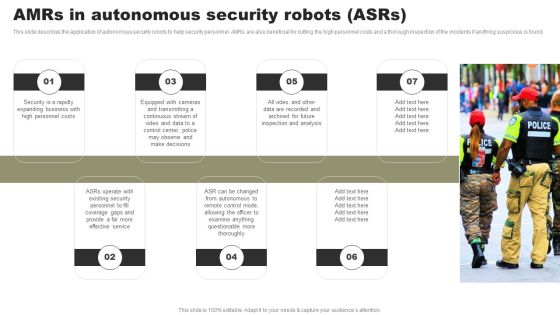
Types Of Independent Robotic System Amrs In Autonomous Security Robots Asrs Brochure PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Create an editable Types Of Independent Robotic System Amrs In Autonomous Security Robots Asrs Brochure PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Types Of Independent Robotic System Amrs In Autonomous Security Robots Asrs Brochure PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Amrs In Autonomous Security Robots Asrs Ppt PowerPoint Presentation File Outline PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Amrs In Autonomous Security Robots Asrs Ppt PowerPoint Presentation File Outline PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.
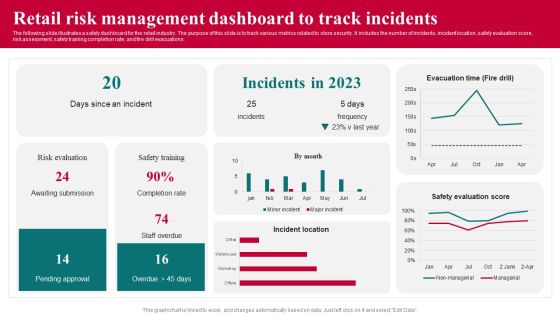
Retail Risk Management Dashboard To Track Incidents Professional PDF
The following slide illustrates a safety dashboard for the retail industry. The purpose of this slide is to track various metrics related to store security. It includes the number of incidents, incident location, safety evaluation score,risk assessment, safety training completion rate, and fire drill evacuations. Showcasing this set of slides titled Retail Risk Management Dashboard To Track Incidents Professional PDF. The topics addressed in these templates are Risk Evaluation, Retail Risk Management Dashboard, Track Incidents. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Key Template PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. Presenting global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats key template pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Global Cyber Terrorism Incidents On The Rise IT Checklist To Deal With Cyber Terrorism Threats Infographics PDF
This slide represents the checklist to deal with cyber-terrorism threats which involve 24 7 monitoring, employee training, keeping software updated. This is a global cyber terrorism incidents on the rise it checklist to deal with cyber terrorism threats infographics pdf template with various stages. Focus and dispense information on nine stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, monitoring, cyber security assessment, incident response plan, limited access privileges. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
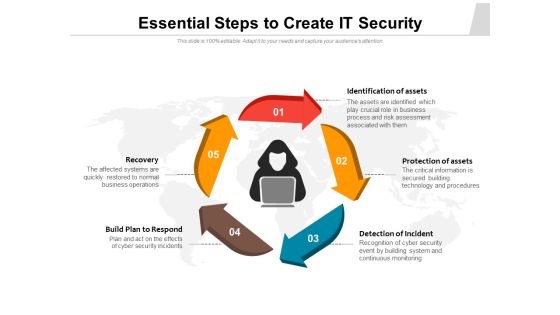
Essential Steps To Create IT Security Ppt PowerPoint Presentation Design Templates PDF
Presenting essential steps to create it security ppt powerpoint presentation design templates pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including identification of assets, protection of assets, detection of incident, recovery, build plan to respond. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF
This slide covers classification of cyber security events of financial organizations. The purpose of this classification is to identify events which needs immediate response. It includes elements such as severity level, cyber incidents, occurrence pattern, performance impact, data breach and financial costs Pitch your topic with ease and precision using this Cyber Security Cases Action Severity Level For Plan Ppt PowerPoint Presentation File Model PDF. This layout presents information on Severity Level, Cyber Incidents, Occurrence Pattern, Performance Impact. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organization Impact Metrics Strategic Hacking Prevention Awareness Training For IT Security Graphics PDF
This slide the metrics That assess how your security awareness plan serves the overall security system of your company, and therefore the organizations mission. Presenting organization impact metrics strategic hacking prevention awareness training for it security graphics pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like organization, policy violations, data loss incidents, human resources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
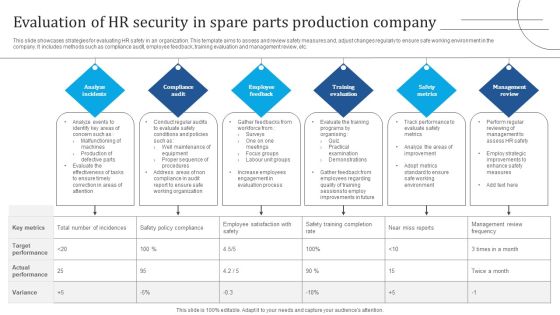
Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF
This slide showcases strategies for evaluating HR safety in an organization. This template aims to assess and review safety measures and, adjust changes regularly to ensure safe working environment in the company. It includes methods such as compliance audit, employee feedback, training evaluation and management review, etc. Presenting Evaluation Of HR Security In Spare Parts Production Company Demonstration PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Analyze Incidents, Compliance Audit, Employee Feedback. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Artificial Intelligence Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Deliver an awe inspiring pitch with this creative artificial intelligence playbook stage five security breach readiness checklist topics pdf bundle. Topics like questions related, security breach readiness, each organizational procedure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Emergency Strategic Action Plan Analysis Icon For System Security Designs PDF
Showcasing this set of slides titled emergency strategic action plan analysis icon for system security designs pdf. The topics addressed in these templates are emergency strategic action plan analysis icon for system security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF
The following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Presenting Managed Cyber Security Solutions Service Threat Detection Process Ppt Portfolio Pictures PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Event Resolution, Security Analysis, Use Cases, Operational Readiness Review. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Threat Drivers And Emerging Technologies Impact On Cyber Security Ppt Slides Graphic Images PDF
Mentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. This is a threat drivers and emerging technologies impact on cyber security ppt slides graphic images pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, developing, strategic, opportunities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Artificial Intelligence Transformation Playbook Stage Five Security Breach Readiness Checklist Topics PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. This is a artificial intelligence transformation playbook stage five security breach readiness checklist topics pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like stage five security breach readiness checklist. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.
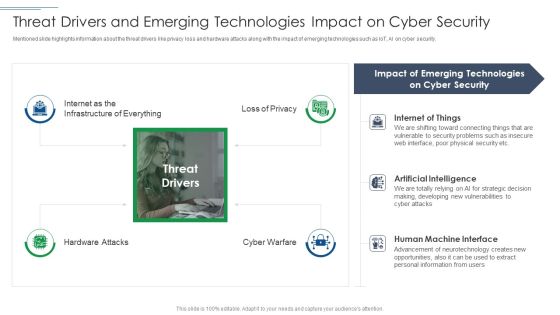
IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF
Presenting IT Security Risk Management Approach Introduction Threat Drivers And Emerging Technologies Download PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Cyber Security, Emerging Technologies, Artificial Intelligence. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
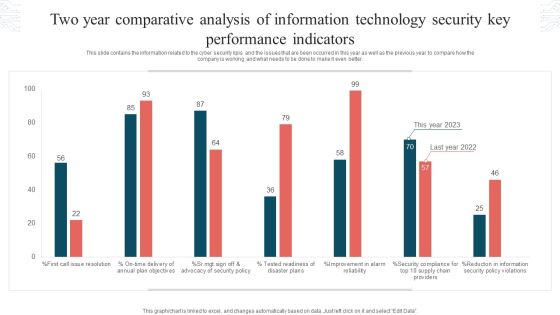
Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF
This slide contains the information related to the cyber security kpis and the issues that are been occurred in this year as well as the previous year to compare how the company is working and what needs to be done to make it even better. Showcasing this set of slides titled Two Year Comparative Analysis Of Information Technology Security Key Performance Indicators Graphics PDF. The topics addressed in these templates are Tested Readiness, Disaster Plans, Security Policy Violations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
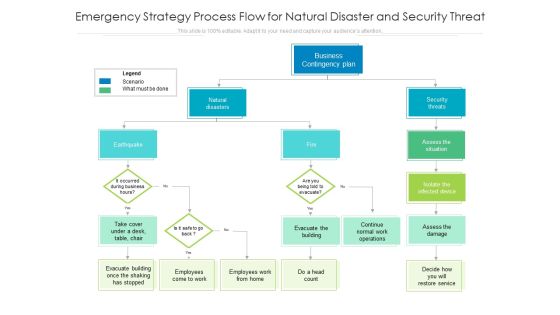
Emergency Strategy Process Flow For Natural Disaster And Security Threat Ppt PowerPoint Presentation Ideas Files PDF
Showcasing this set of slides titled emergency strategy process flow for natural disaster and security threat ppt powerpoint presentation ideas files pdf. The topics addressed in these templates are Business Contingency Plan, Natural Disasters, Earthquake. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Presenting Artificial Intelligence For IT Operations Playbook Stage Five Security Breach Readiness Checklist Rules PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Management Training, Potential Mitigation, Already Developed In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

AI Playbook For Business Stage Five Security Breach Readiness Checklist Microsoft PDF
Purpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. This is a AI Playbook For Business Stage Five Security Breach Readiness Checklist Microsoft PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Operations, Organizations Transforming, Related To Management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
 Home
Home