Security Controls

Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF
This slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Timeline For Information Security Risk Management Training Information Security Risk Administration Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Security Assessment Precautions Need To Take In Cloud Security Elements PDF
This slide depicts the cloud security precautions that one organization should take while signing up for a cloud service.This is a Cloud Security Assessment Precautions Need To Take In Cloud Security Elements PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Computing Administrations, Service Provider, Managed Administrations. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing IT Security Strategy Identifying Employees For Information Security Training Sample PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner. If you are looking for a format to display your unique thoughts, then the professionally designed Developing IT Security Strategy Identifying Employees For Information Security Training Sample PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Developing IT Security Strategy Identifying Employees For Information Security Training Sample PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Project Security Administration IT Enabling Data Security Risk Management Action Plan Download PDF
This slide provide details about data security risk management action plan which will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. This is a project security administration it enabling data security risk management action plan download pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like potential risk, risk level, action, responsible person, communication. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF
This slide outlines the critical security concerns related to blockchain networks. The purpose of this slide is to showcase the major risks associated with blockchain technology, including confidentiality, integrity, non-repudiation, and authentication. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Blockchain Security Solutions Deployment Major Security Concerns For Blockchain Graphics PDF today and make your presentation stand out from the rest

Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF
This slide showcases software that can help organization to monitor and manage the information security. It provides information about Cyber Risk Quantification, vvulnerability management, Ccentralized rrepository for aassets etc. Explore a selection of the finest Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Selecting Suitable Software For Information Security Risk Inspiration PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Desktop Security Management Common Methods Used To Threaten Computer Security Template PDF
This slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. This is a desktop security management common methods used to threaten computer security template pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like system, information, services, network, database. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Cyber Security Crisis Management Action Pictures PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment And Management Matrix Rules PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Deploying Cyber Security Incident Response Administration Cyber Security Risk Assessment And Management Matrix Rules PDF from Slidegeeks and deliver a wonderful presentation.

Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Implementing Cyber Security Incident Cyber Security Crisis Action Plan Timeline Summary PDF

Cyber Security Risk Management Plan Introducing Information Security Risk Assessment Process Workflow Elements PDF
Following slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. This is a cyber security risk management plan introducing information security risk assessment process workflow elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like characterize system, identify vulnerabilities, identify threats, recommend remediation measures, analyze risks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
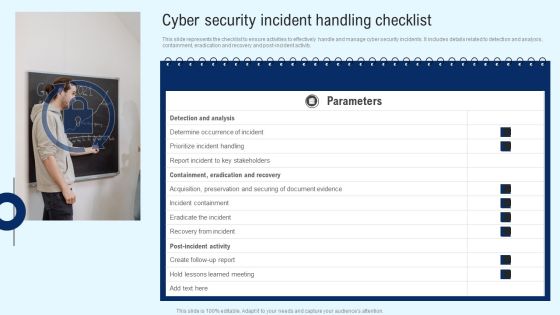
Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. This Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Get a simple yet stunning designed Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Cyber Security Risk Assessment And Matrix Introduction PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab CYBER Security Breache Response Strategy Cyber Security Incident Handling Checklist Professional PDF today and make your presentation stand out from the rest.

Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF. Use them to share invaluable insights on Core Functions, Key Enablers, Required Standard Rating, Actual Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. This Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Security Automation Framework Time To Fix Security Threat With Manual Testing Inspiration PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into CYBER Security Breache Response Strategy Cyber Security Incident Response Plan Timeline Demonstration PDF

Security Automation To Analyze And Mitigate Cyberthreats Criteria To Automate Security Brochure PDF
This slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats.Slidegeeks is here to make your presentations a breeze with Security Automation To Analyze And Mitigate Cyberthreats Criteria To Automate Security Brochure PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF can be your best option for delivering a presentation. Represent everything in detail using Implementing Cyber Security Incident Impact Of Implementing Cyber Security Incident Mockup PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Security Automation Framework Criteria To Automate Security Analysis And Response Sample PDF
This slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Security Automation Framework Criteria To Automate Security Analysis And Response Sample PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Security Automation To Analyze And Mitigate Cyberthreats Security Automation Stages Infographics PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process.This Security Automation To Analyze And Mitigate Cyberthreats Security Automation Stages Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Security Automation To Analyze And Mitigate Cyberthreats Security Automation Stages Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
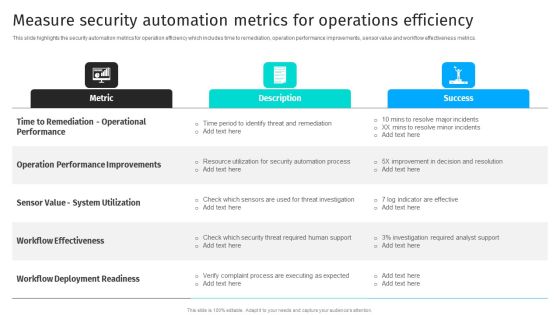
Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics.Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Security Automation To Analyze And Mitigate Cyberthreats Measure Security Automation Metrics Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Cloud Security Threats Compliance Violations Cloud Computing Security IT Ppt Layouts Slide Portrait PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a cloud security threats compliance violations cloud computing security it ppt layouts slide portrait pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like businesses, organizations, serious repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
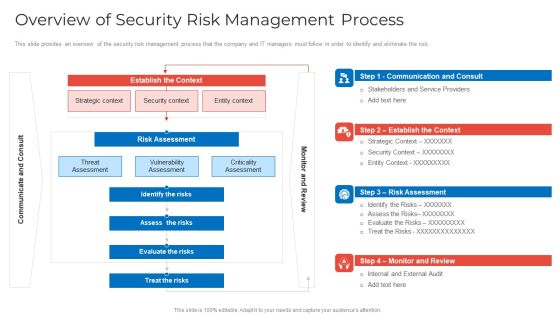
Implementing Security Management Strategy To Mitigate Risk Overview Of Security Risk Management Process Pictures PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative implementing security management strategy to mitigate risk overview of security risk management process pictures pdf bundle. Topics like identify the risks, assess the risks, evaluate the risks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section.Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Security Automation To Analyze And Mitigate Cyberthreats Determine Ideal Tasks For Security Clipart PDF today and make your presentation stand out from the rest.

Information Systems Security And Risk Management Plan Checklist For Information Security Risk Management Mockup PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Find a pre designed and impeccable Information Systems Security And Risk Management Plan Checklist For Information Security Risk Management Mockup PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
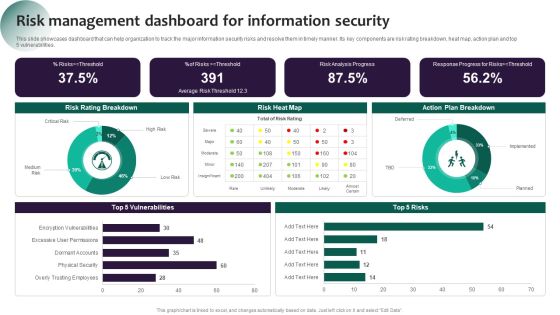
Information Systems Security And Risk Management Plan Risk Management Dashboard For Information Security Pictures PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Systems Security And Risk Management Plan Risk Management Dashboard For Information Security Pictures PDF from Slidegeeks and deliver a wonderful presentation.

Developing Firm Security Strategy Plan Information Security Process To Manage Firms Sensitive Data Contd Brochure PDF
This slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Presenting developing firm security strategy plan information security process to manage firms sensitive data contd brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like firewall audit checklist, vpn configuration, penetrating testing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Camera System Company Profile Security Company Organization Chart Ideas PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Security Camera System Company Profile Security Company Organization Chart Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like President Finance, President And Chief, Executive Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Main Principle Of Information Security Ppt Infographics Example Topics PDF
This slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. This is a it security main principle of information security ppt infographics example topics pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like confidentiality, integrity, availability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Deploying Cyber Security Incident Response Administration Key Parameters To Select Cyber Security Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Identifying Employees For Information Security Training Programme Information Security Risk Administration Microsoft PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner.If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Identifying Employees For Information Security Training Programme Information Security Risk Administration Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
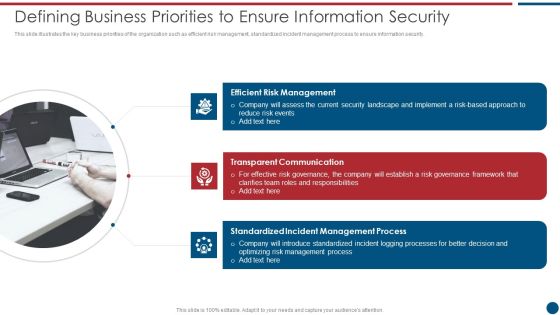
Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Risk Management, Transparent Communication, Standardized Incident. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risks Organizations, Data Business, Serious Repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
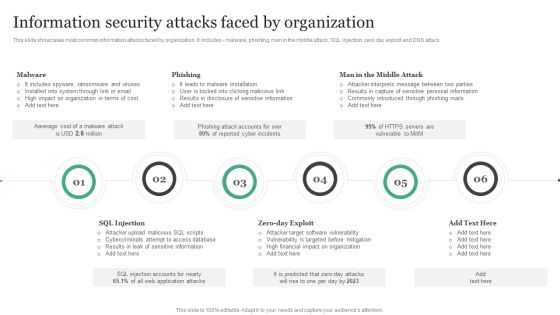
Information Security Attacks Faced By Organization Information Security Risk Administration Guidelines PDF
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Security Attacks Faced By Organization Information Security Risk Administration Guidelines PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Security Attacks Faced By Organization Information Security Risk Administration Guidelines PDF.

Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF
This slide defines the architecture of the cloud security system and how data is kept, managed, and secured based on customer and service providers responsibilities. This is a Architecture Of Cloud Security Cloud Information Security Ppt Inspiration Samples PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer Responsibility, Cloud Service, Provider Responsibility. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Developing Firm Security Strategy Plan Security Incidents Tracking Dashboard Alerts Graphics PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Presenting developing firm security strategy plan security incidents tracking dashboard alerts graphics pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like application whitelisting, patch applications, patch operating systems, restrict admin privileges. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
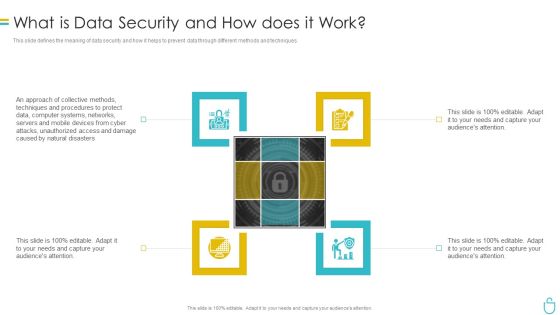
Information Security What Is Data Security And How Does It Work Ppt Professional Infographics PDF
This slide defines the meaning of data security and how it helps to prevent data through different methods and techniques. Presenting information security what is data security and how does it work ppt professional infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like techniques, computer systems, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Risk Management Plan Present Security Management Capabilities Of The Firm Template PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan present security management capabilities of the firm template pdf. Use them to share invaluable insights on actual standard rating, required standard rating, key enablers, description, core functions and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Desktop Security Management Types Of Threats In Desktop Security Management Themes PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting desktop security management types of threats in desktop security management themes pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like target systems, devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
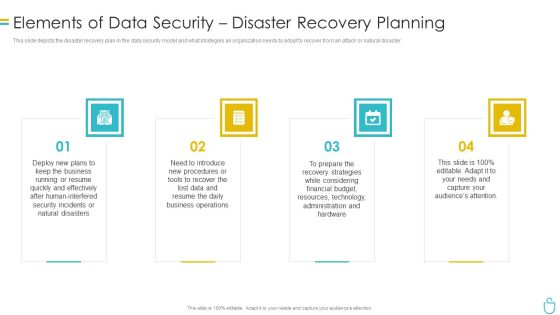
Information Security Elements Of Data Security Disaster Recovery Planning Ppt Inspiration Example Topics PDF
This slide depicts the disaster recovery plan in the data security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a information security elements of data security disaster recovery planning ppt inspiration example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plans, procedures, strategies, technology, resources. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Loss Of Data Cloud Computing Security IT Ppt Infographics Graphic Tips PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups. This is a cloud security threats loss of data cloud computing security it ppt infographics graphic tips pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like locations, cloud service, strategies, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
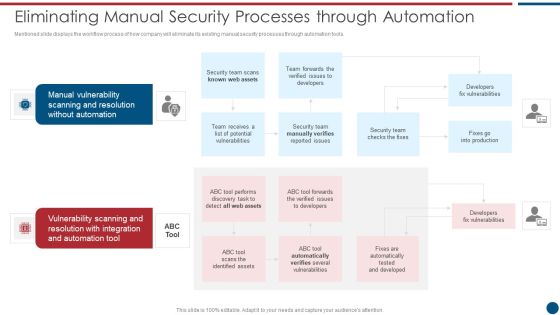
Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manual Vulnerability, Vulnerability Scanning, Automation Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan Determine Overview Of Established Security Centre Download PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a developing firm security strategy plan determine overview of established security centre download pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like functional business units, management staff, steering committee, internal systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
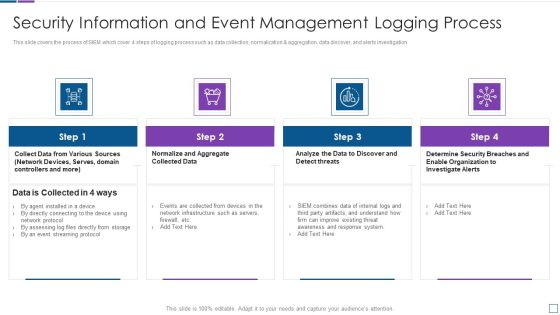
Real Time Assessment Of Security Threats Security Information And Event Management Logging Process Demonstration PDF
This slide covers the process of SIEM which cover 4 steps of logging process such as data collection, normalization and aggregation, data discover, and alerts investigation. This is a real time assessment of security threats security information and event management logging process demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security information and event management logging process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Cyber Security Incident Response Administration Ways To Detect Cyber Security Incidents Background PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Ways To Detect Cyber Security Incidents Background PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

IT Security Risk Management Approach Introduction Defining Business Priorities To Ensure Information Security Microsoft PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting IT Security Risk Management Approach Introduction Defining Business Priorities To Ensure Information Security Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Transparent Communication, Efficient Risk Management, Standardized Incident Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
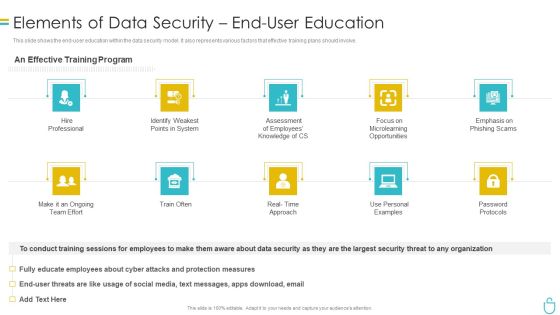
Information Security Elements Of Data Security End User Education Ppt Ideas Professional PDF
This slide shows the end user education within the data security model. It also represents various factors that effective training plans should involve. Presenting information security elements of data security end user education ppt ideas professional pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like system, opportunities, employees, measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF
This slide outline the security operations automation process that enables to ease of the burden of cybersecurity organizations by automating repetitive tasks. It includes determine standard operating procedures SOPs, analyse tools, verify existing API connectors, etc. Presenting Steps To Implement Cyber Security Automation In Security Operations Demonstration PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Progressive Automation, Enhance Processes, Analyse Tools. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
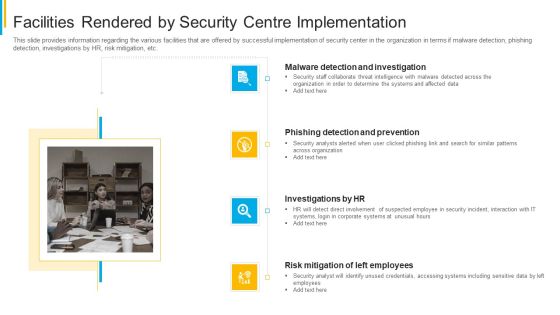
Project Security Administration IT Facilities Rendered By Security Centre Implementation Clipart PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Presenting project security administration it facilities rendered by security centre implementation clipart pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Security Intelligence Services Formats PDF
This slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Presenting real time assessment of security threats security intelligence services formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like incident response and management, cyber analytics, vulnerability management, infrastructure management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF
This slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Presenting Cloud Security Assessment Cloud Security Threats Loss Of Data Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Storage Locations, Natural Disasters, Massive Impact. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF. Use them to share invaluable insights on Identification Assess, Protecting Safeguarding, Detect Threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF
The following slide highlights key members of financial security department . It provides information about chief financial officer CFO, compliance auditor, senior analyst, customer support manager, operations manager, etc. Want to ace your presentation in front of a live audience Our KYC Transaction Monitoring System Business Security Key Members Of Financial Security Department Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Risk Management Model For Data Security Budget For Information Security Management Sample PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Budget For Information Security Management Sample PDF bundle. Topics like Functional Area, Training Duration, Risk Management, Incident Management, Asset Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Security Security Framework In Cloud Computing Ppt Outline Graphics Design PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a information technology security security framework in cloud computing ppt outline graphics design pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recover, respond, identify, protect . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
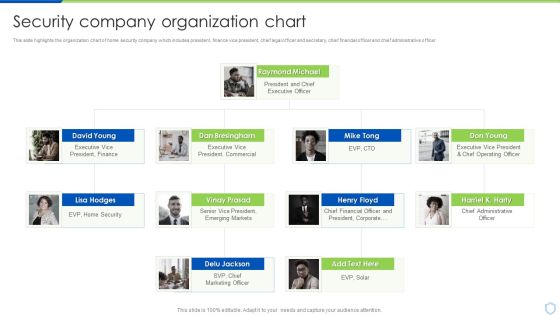
Security And Surveillance Company Profile Security Company Organization Chart Portrait PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. This is a Security And Surveillance Company Profile Security Company Organization Chart Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Raymond Michael, Executive President, Emerging Markets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

 Home
Home