Security Controls

Cyber Security Administration In Organization Comparative Assessment Of Various Threat Agents Infographics PDF
This slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization comparative assessment of various threat agents infographics pdf. Use them to share invaluable insights on social engineering, operations, maintenance, redundancy and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Contingency Plan For Cyber Threat Handling Brochure PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations Deliver an awe inspiring pitch with this creative cyber security administration in organization contingency plan for cyber threat handling brochure pdf bundle. Topics like contingency, implementation, components, documentation, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Financial Performance Tracking Dashboard Microsoft PDF
This slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver and pitch your topic in the best possible manner with this cyber security administration in organization financial performance tracking dashboard microsoft pdf. Use them to share invaluable insights on financial performance tracking dashboard and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Administration In Organization Determine Threat Scenario Analysis Introduction PDF
This slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an awe inspiring pitch with this creative cyber security administration in organization determine threat scenario analysis introduction pdf bundle. Topics like determine threat scenario analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Incident Reporting By Different Departments Download PDF
This slide will help in providing an overview of the various reported incidents, average cost per incident and number of people involved in the various incidents across different departments. Deliver an awe inspiring pitch with this creative cyber security administration in organization incident reporting by different departments download pdf bundle. Topics like incident reporting by different departments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF
This slide showcases process flow of suspicious activity reporting SAR. It provides information about transaction alert, purpose, patterns, customer behavior, client lifestyle, negative news, adverse media, sanctions, anti money laundering AML, etc. Get a simple yet stunning designed KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit KYC Transaction Monitoring System Business Security Suspicious Activity Reporting Process Flow Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Present like a pro with Impact Of Implementing Cyber Security Incident Management On Organization Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
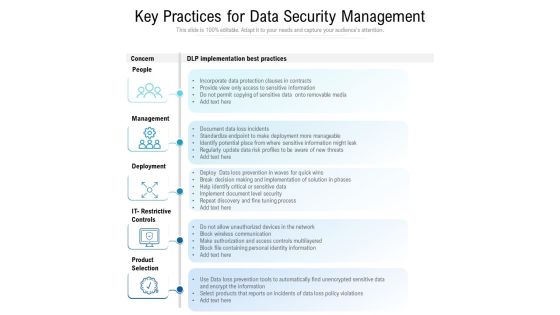
Key Practices For Data Security Management Ppt PowerPoint Presentation File Background Designs PDF
Persuade your audience using this key practices for data security management ppt powerpoint presentation file background designs pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including management, deployment, implementation. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
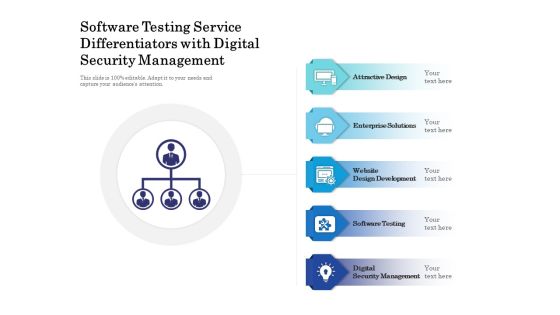
Software Testing Service Differentiators With Digital Security Management Ppt PowerPoint Presentation File Graphics Download PDF
Persuade your audience using this software testing service differentiators with digital security management ppt powerpoint presentation file graphics download pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including attractive design, enterprise solutions, software testing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
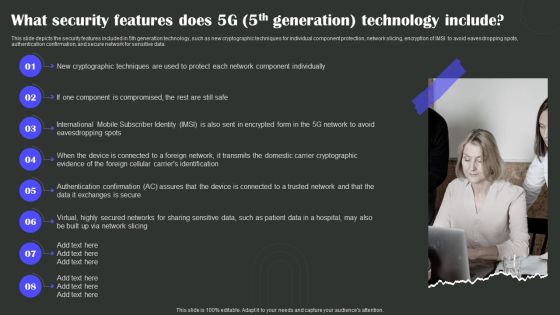
What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Present like a pro with What Security Features Does 5G 5Th Generation Technology Include Wireless Technology Transformation Mockup PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF
This slide showcases information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. This modern and well arranged Information Systems Security And Risk Management Plan Cyber Attacks Faced By Different Departments Download PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
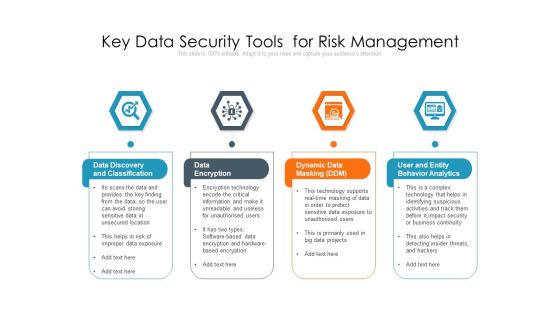
Key Data Security Tools For Risk Management Ppt PowerPoint Presentation Outline Guide PDF
Persuade your audience using this key data security tools for risk management ppt powerpoint presentation outline guide pdf. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including data discovery and classification, data encryption, dynamic data masking ddm, user and entity behavior analytics. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Management Plan Steps In Detail Evaluating Information Processing Assets Introduction PDF
This is a security management plan steps in detail evaluating information processing assets introduction pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluate information, processing assets, information processing. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT And Cloud Facilities Management 4 Dimensions Of Infrastructure Security Professional PDF
This is a it and cloud facilities management 4 dimensions of infrastructure security professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like structured, unstructured, systems applications, web applications, outsources, mobile applications, non traditional, datacenters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF
The following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into IT Vulnerabilities With Threat Source And Action Organizations Risk Management And IT Security Download PDF.

Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF
This slide represents the training program conducted by the incident management team for end users to help them identify and mitigate the cyber security incidents before they occur. It includes details related to training topic, method, date, trainer and budget. The Deploying Cyber Security Incident Response Administration User Awareness Training Program Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Cyber Security For Your Organization Budget For Effective Cybersecurity Management Ppt Ideas Objects PDF
Presenting this set of slides with name cyber security for your organization budget for effective cybersecurity management ppt ideas objects pdf. This is a one stage process. The stages in this process are incident management, risk management, client onboarding process, document management, information management, release management . This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents For Information Systems Security And Risk Management Plan Brochure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
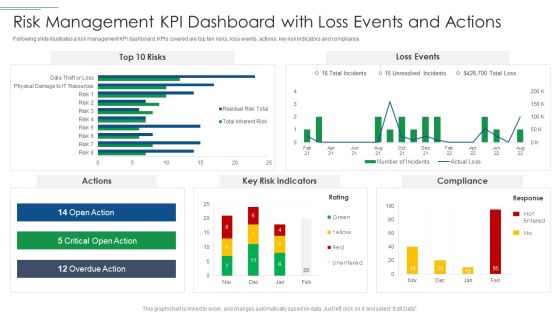
IT Security Risk Management Approach Introduction Risk Management KPI Dashboard With Loss Events Brochure PDF
Following slide illustrates a risk management KPI dashboard. KPIs covered are top ten risks, loss events, actions, key risk indicators and compliance. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Risk Management KPI Dashboard With Loss Events Brochure PDF bundle. Topics like Key Risk Indicators, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
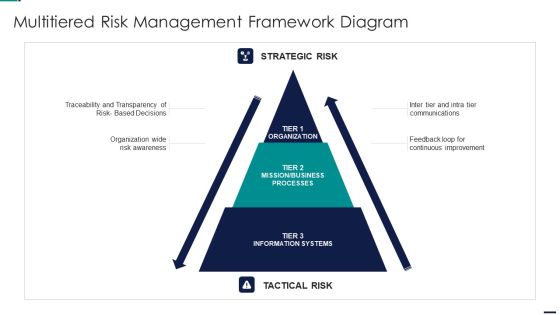
Risk Management Model For Data Security Multitiered Risk Management Framework Diagram Ideas PDF
This is a Risk Management Model For Data Security Multitiered Risk Management Framework Diagram Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Strategic Risk, Mission, Business Processes, Information Systems, Organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Tactic For Process Management For IT Roadmap Four Quarter Pictures
Presenting our innovatively structured cyber security tactic for process management for it roadmap four quarter pictures Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Tactic For Process Management For IT Roadmap Half Yearly Topics
Introducing our cyber security tactic for process management for it roadmap half yearly topics. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
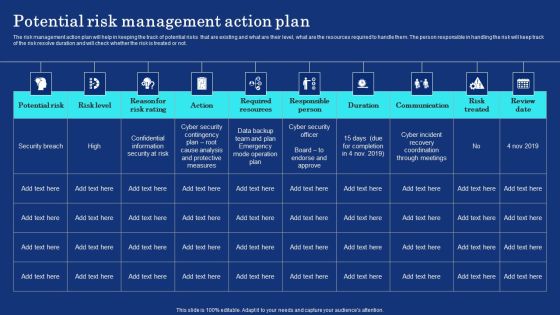
Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF
The risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. The person responsible in handling the risk will keep track of the risk resolve duration and will check whether the risk is treated or not. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF can be your best option for delivering a presentation. Represent everything in detail using Organizational Assets Security Management Strategy Potential Risk Management Action Plan Information PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Information Systems Security And Risk Management Plan Information And Data Breach Impacting Customer Loyalty Brochure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
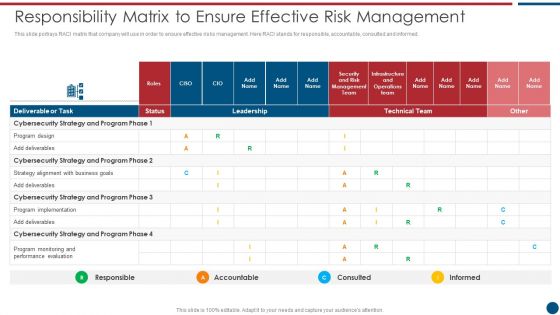
Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Responsibility Matrix To Ensure Effective Risk Management Slides PDF bundle. Topics like Technical Team, Cybersecurity Strategy, Program Implementation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
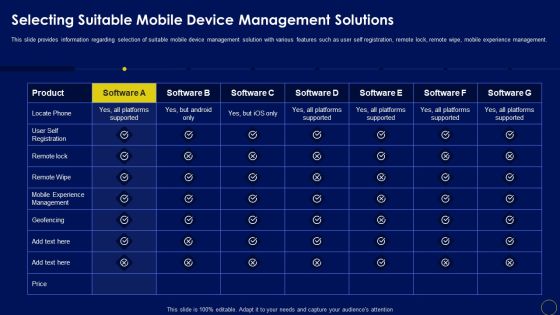
Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF
This slide provides information regarding selection of suitable mobile device management solution with various features such as user self registration, remote lock, remote wipe, mobile experience management. Find highly impressive Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Selecting Suitable Mobile Device Management Solutions Business Mobile Device Security Management Formats PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.

Key Stages Of IT Security Systems Development Process Ppt PowerPoint Presentation Slides Display PDF
Presenting key stages of it security systems development process ppt powerpoint presentation slides display pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including investigation, analysis, logical design, physical design, implementation, maintenance and change. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Slidegeeks has constructed Impact Of Implementing Cyber Security Incident Management On Organization Microsoft PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF
This slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizations Risk Management And IT Security Classification Of IT Risks With Threats Structure PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF
Presenting Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Process Formulate, Management Plan, Mitigating Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF
This slide represents the comparison between various web application firewall products based on multiple parameters to help organization select the best web application firewall for their organization. It includes comparison between WAF products based on features such as cookie tampering etc. This Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Deploying Cyber Security Incident Response Administration Comparative Analysis Of Web Application Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.

Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF
Mentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Systems Security And Risk Management Plan Mitigation Plan For Resolving Encountered Threat Structure PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Effective IT Risk Management Process Information Security Risk Assessment Formats PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this NAMEEEEEE. Use them to share invaluable insights on system failure, potential, vulnerability and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Stages To Develop Strong Cyber Security Analysis Process Ppt PowerPoint Presentation Outline Example File PDF
Persuade your audience using this stages to develop strong cyber security analysis process ppt powerpoint presentation outline example file pdf. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including formulate remediation steps and prioritize risks, analysing collected, recipient on the phone, teleconference. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Mobile Device Management For Ios Platform Business Mobile Device Security Management Themes PDF today and make your presentation stand out from the rest.

Cyber Security For Your Organization Table Of Contents Ppt Design Ideas PDF
Presenting this set of slides with name cyber security for your organization table of contents ppt design ideas pdf. The topics discussed in these slides are analyzing current scenario, initiating cyber risk management program, incident management, role personnel, dashboard, impact analysis, cost associated firm, cybersecurity contingency plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Get a simple yet stunning designed Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Deploying Cyber Security Incident Response Administration Cyber Attacks Faced By The Company Sample PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Online Security System For Technology Vulnerabilities Analysis Ppt PowerPoint Presentation Ideas Design Ideas PDF
Presenting this set of slides with name online security system for technology vulnerabilities analysis ppt powerpoint presentation ideas design ideas pdf. This is a three stage process. The stages in this process are cyber risk and strategy, compliance governance, external review, internal review, compromise assessment, annual cyber maintenance, monitorinag, advanced threat detection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security Data Privacy In IT Sector Ppt PowerPoint Presentation File Outline PDF
This slide shows the data privacy in the IT sector, companies are compelled to examine their personal identifiable information concerned operations, and so on. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Security Data Privacy In IT Sector Ppt PowerPoint Presentation File Outline PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Security Data Privacy In IT Sector Ppt PowerPoint Presentation File Outline PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Scm Process With Procurement Warehouse And Security Ppt PowerPoint Presentation Infographic Template Structure PDF
Pitch your topic with ease and precision using this SCR process with procurement warehouse and security ppt powerpoint presentation infographic template structure pdf. This layout presents information on procurement, warehouse, evaluation for correct products in shipment, inbound shipping schedule update, procuring and notifying for shipping. It is also available for immediate download and adjustment. So, changes can be made in the colour, design, graphics or any other component to create a unique layout.

Cyber Security Risk Management Plan Multitiered Risk Management Framework Diagram Inspiration PDF
This is a cyber security risk management plan multitiered risk management framework diagram inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like orgnization, mission or business processes, information systems. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Damage Security Insurance Proposal Insurance Claim Procedure For Liability Insurance Proposal Ppt Infographic Template Summary PDF
This is a damage security insurance proposal insurance claim procedure for liability insurance proposal ppt infographic template summary pdf template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cashless claim process, reimbursement claim process. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF
This slide displays the new incident logging process that company will introduce. It covers information of logging process, its description and responsible person details. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Introducing New Incidents Logging Process Slides PDF. Use them to share invaluable insights on Logging Process, Capture Requirements, Service Desk Agent and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF
This slide showcases risks identified during transaction monitoring. It provides information about anti money laundering fines, staff productivity, motivation, organizational profitability, compliance, fees, false positive, workload, etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable KYC Transaction Monitoring System Business Security Risks Identified During Transaction Monitoring Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Information Systems Security And Risk Management Plan Our Mission Infographics PDF
The Information Systems Security And Risk Management Plan Our Mission Infographics PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF
This slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets.Are you searching for a Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Analyzing The Impact On Assets Due To Information Breach Information Security Risk Administration Introduction PDF from Slidegeeks today.
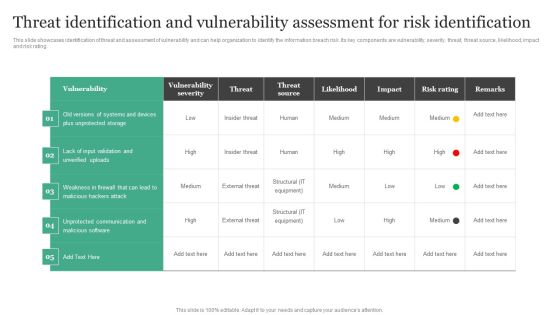
Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Get a simple yet stunning designed Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Threat Identification And Vulnerability Assessment For Risk Identification Information Security Risk Administration Slides PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Fordeploying Cyber Security Incident Response Administration Structure PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF
If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit Table Of Contents Development And Integration Of Cyber Security Incident Administration Portrait PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates
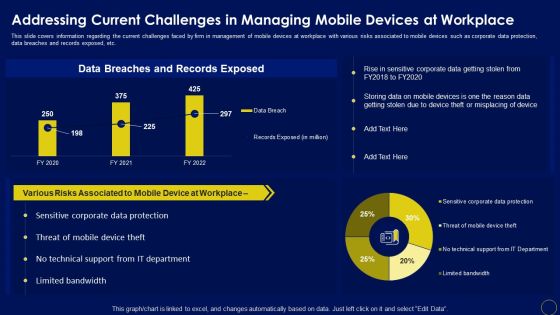
Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF
This slide covers information regarding the current challenges faced by firm in management of mobile devices at workplace with various risks associated to mobile devices such as corporate data protection, data breaches and records exposed, etc. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Addressing Current Challenges In Managing Business Mobile Device Security Management Summary PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Table Of Contents Data Safety Initiatives For Effective IT Security Threats Administration Summary PDF
Presenting table of contents data safety initiatives for effective it security threats administration summary pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like overcoming identified gaps, improved incident reporting, communication plan cyber breaches, ensuring effective risk governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
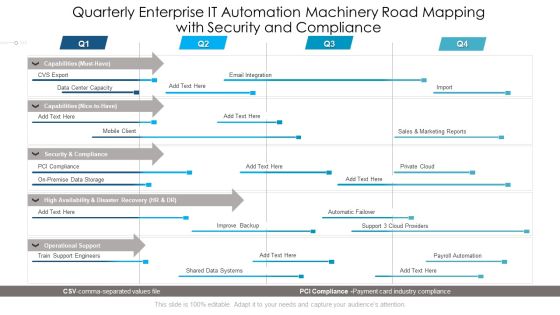
Quarterly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Diagrams
Presenting our innovatively structured quarterly enterprise it automation machinery road mapping with security and compliance diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Selecting Suitable Automated Systems Ensuring Optimum Process Performance Food Security Excellence Ppt Styles Slide Download PDF
This slide provides information regarding selection of appropriate automated system for ensuring optimum process performance and addressing them various parameters. Deliver and pitch your topic in the best possible manner with this selecting suitable automated systems ensuring optimum process performance food security excellence ppt styles slide download pdf. Use them to share invaluable insights on centralized monitoring, management, product traceability, standardization, process optimization and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

E Payment Transaction System Payment Security And Fraud Management Solutions Development Professional PDF
This is a E payment transaction system payment security and fraud management solutions development professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like recognizing users and streamlining the payments process with zero added friction, operational costs, software development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Develop Corporate Cyber Security Risk Mitigation Plan Roadmap For Organization Cyber Protection Proposal Summary PDF
Presenting develop corporate cyber security risk mitigation plan roadmap for organization cyber protection proposal summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like roadmap, organization cyber protection. In addtion, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Develop Corporate Cyber Security Risk Mitigation Plan Timeline For Organization Protection Proposal Themes PDF
This is a develop corporate cyber security risk mitigation plan timeline for organization protection proposal themes pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeline, 2019 to 2022. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF
This slide provides information regarding various mobile device management deployment methods such as device enrollment program, configurator, user initiated through URL that can be selected by vendor based on requirement. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Determine Various Mobile Device Manage Business Mobile Device Security Management And Mitigation Portrait PDF.
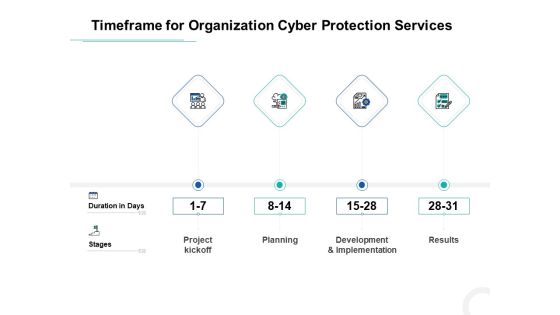
Develop Corporate Cyber Security Risk Mitigation Plan Timeframe For Organization Cyber Protection Services Structure PDF
This is a develop corporate cyber security risk mitigation plan timeframe for organization cyber protection services structure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like project kickoff, planning, development and implementation, results. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
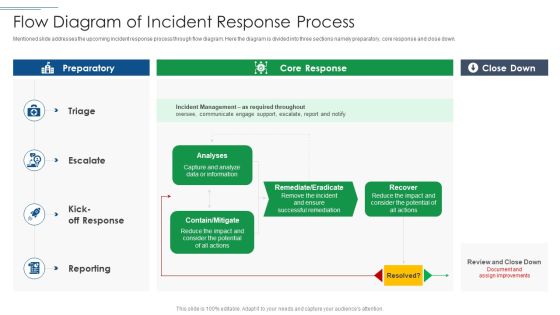
IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF
Mentioned slide addresses the upcoming incident response process through flow diagram. Here the diagram is divided into three sections namely preparatory, core response and close down. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Flow Diagram Of Incident Response Process Demonstration PDF bundle. Topics like Incident Management, Potential can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
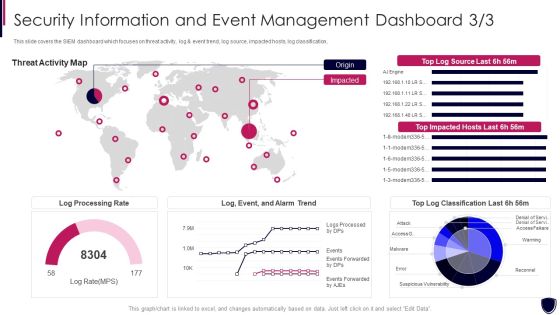
Security Information And Event Enhancing Cyber Safety With Vulnerability Administration Portrait PDF
This slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification. Deliver an awe inspiring pitch with this creative security information and event enhancing cyber safety with vulnerability administration portrait pdf bundle. Topics like log processing rate, threat activity map can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF
Presenting Table Of Contents For Mobile Device Security Management In Organization Tips Inspiration PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Current Scenario, Determine Current, Determine Various. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF
This slide represents the impact of data breaches experienced by an enterprise. It includes data breaches of hacking, unintended disclosure, physical loss, payment card fraud etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Deploying Cyber Security Incident Response Administration Consequences Of Data Breaches Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. The CYBER Security Breache Response Strategy Cyber Supply Chain Risk Management Dashboard Inspiration PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Essential Elements To Be Included In A Security Management Plan Slides PDF
Presenting Essential elements to be included in a security management plan slides pdf to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like program management, preparedness, recovery, training, response. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF
This slide provides information regarding information security and governance management framework. The key elements include compliance, audit, response and recovery, etc. Retrieve professionally designed Deploying Corporate Aligned IT Strategy Information Security And Governance Management Framework Download PDF to effectively convey your message and captivate your listeners. Save time by selecting pre made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Cyber Security Risk Management Plan Online And Onsite Training Schedule For Employee Elements PDF
This slide illustrates employee training schedule. It covers details about employee name, its position, software name, course type, training mode and duration. Deliver an awe inspiring pitch with this creative cyber security risk management plan online and onsite training schedule for employee elements pdf bundle. Topics like position, software name, course type, training mode, duration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Risk Reporting And Likelihood Elements PDF
Mentioned slide shows encountered risk reporting and its likelihood. It includes information about risk encountered, frequency, reported by status, attack scenario, affected asset and likelihood. Deliver an awe inspiring pitch with this creative cyber security risk management plan risk reporting and likelihood elements pdf bundle. Topics like risk encountered, frequency, reported by status, attack scenario, affected asset, likelihood can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mobile Device Management For Ios Platform Mobile Device Security Management Mockup PDF
This slide provides information regarding mobile device management for iOS platform with device enrollment program, anti theft protection, etc. Deliver an awe inspiring pitch with this creative Mobile Device Management For Ios Platform Mobile Device Security Management Mockup PDF bundle. Topics like Device Enrollment, Theft Protection, Remote Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
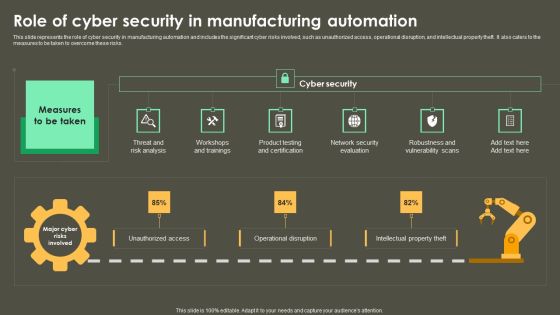
Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF
This slide represents the role of cyber security in manufacturing automation and includes the significant cyber risks involved, such as unauthorized access, operational disruption, and intellectual property theft. It also caters to the measures to be taken to overcome these risks. This modern and well-arranged Iot Integration In Manufacturing Role Of Cyber Security In Manufacturing Automation Elements PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
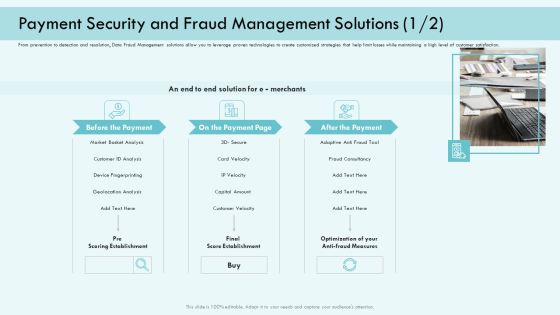
E Payment Transaction System Payment Security And Fraud Management Solutions Analysis Infographics PDF
Presenting E payment transaction system payment security and fraud management solutions analysis infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like market basket analysis, device fingerprinting, customer velocity, optimization of your anti fraud measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Plan Steps In Detail System Maintenance And Monitoring Sample PDF
Presenting security management plan steps in detail system maintenance and monitoring sample pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like corrective maintenance, adaptive maintenance, perfective maintenance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF
This slide represents russias whisper gate attack on ukrainian organizations, consists of three stages, and is designed to turn off the systems defenses, delete data, and format itself. Are you searching for a Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Series Of Cyber Security Attacks Against Ukraine 2022 Whispergate Attack On Ukrainian Organizations Information PDF from Slidegeeks today.

Info Security Implementation Of Strong Password Policy Ppt PowerPoint Presentation File Slide Download PDF
This slide depicts the importance of having strong passwords for different online accounts. It also shows the number of users who use the same password across other accounts. Deliver an awe inspiring pitch with this creative info security implementation of strong password policy ppt powerpoint presentation file slide download pdf bundle. Topics like implementation strong, password policy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF
This slide shows program for insider threat awareness training. It provides information such as program, details, system requirements, duration, fee or charge, etc. Showcasing this set of slides titled Training Program For Insider Threat In Cyber Security Awareness Guidelines PDF. The topics addressed in these templates are Indicators Insider Threat, Protection Confidential Data, Insider Threat. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Real Time Assessment Of Security Threats How SIEM Works Inspiration PDF
Presenting real time assessment of security threats how siem works inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like correlation, behavior analytics, taxonomy, normalization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Slidegeeks is here to make your presentations a breeze with Cyber Physical System To Enhance Security Strategic Planning Process For Cps Demonstration PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Risk Based Procedures To IT Security Risk Governance Structure Ppt PowerPoint Presentation Icon Gallery PDF
Mentioned slide illustrates risk governance framework of the company. It include information about different governing committees along with their deliverables. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Risk Governance Structure Ppt PowerPoint Presentation Icon Gallery PDF. Use them to share invaluable insights on Risk Management, Board Directors, Strategy Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF
The purpose of this slide is to highlight performance KPI dashboard used to monitor the cyber threat management.. The metrics highlighted in the slide are risk score, compliance status, threat level, monitoring and operational status. This Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Organizing Security Awareness KPI Metrics Dashboard To Effectively Track Cyber Threat Icons PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

COVID 19 Mitigating Impact On High Tech Industry Security Maturity Hierarchy Including Five Levels Brochure PDF
Presenting this set of slides with name covid 19 mitigating impact on high tech industry security maturity hierarchy including five levels brochure pdf. The topics discussed in these slides are business unit, awareness and training, compliance and it audit, emerging it threats, incident response ir, operations and support. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF
Purpose of this slide is to show the classification of different security issues and attacks. Categories covered are majorly internal as well as external issues and attacks.Slidegeeks is here to make your presentations a breeze with Classifying Various Security Issues And Attacks Improving Cybersecurity Incident Elements PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you Are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
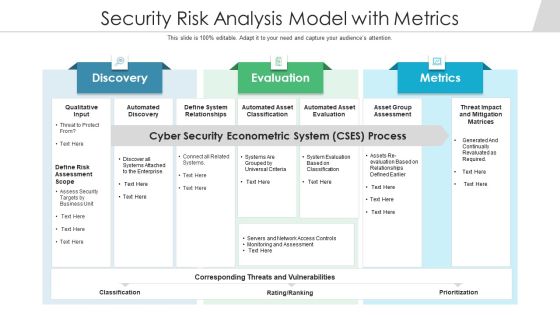
Security Risk Analysis Model With Metrics Ppt PowerPoint Presentation Outline Designs PDF
Persuade your audience using this security risk analysis model with metrics ppt powerpoint presentation outline designs pdf. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including automated discovery, define system relationships, automated asset classification. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Ensuring Food Safety Practices To Prevent Contamination Food Security Excellence Ppt Outline Styles PDF
This slide provides information regarding food safety practices and checklist implemented by firm in order to prevent food contamination. Deliver an awe inspiring pitch with this creative ensuring food safety practices to prevent contamination food security excellence ppt outline styles pdf bundle. Topics like ensuring food safety practices to prevent contamination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Risk Management Plan Defining The Severity Levels Of Risk Template PDF
Following slide defines the incident risk level. It includes details about risk level, risk score and its description. Deliver and pitch your topic in the best possible manner with this cyber security risk management plan defining the severity levels of risk template pdf. Use them to share invaluable insights on risk level, risk score, description and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Addressing Timeframe For Incident Management At Mobile Device Mobile Device Security Management Microsoft PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases.Deliver and pitch your topic in the best possible manner with this Addressing Timeframe For Incident Management At Mobile Device Mobile Device Security Management Microsoft PDF. Use them to share invaluable insights on Incident Categorization, Incident Prioritization, Incident Resolution and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF
The purpose of this slide is to exhibit biggest cyber security awareness challenges which is faced by the organization. Outdated content, burden on administrators, low employee participation rate and employees losing interest are some of the key challenges which are highlighted in the slide. Want to ace your presentation in front of a live audience Our Implementing Cybersecurity Awareness Program To Prevent Attacks Security Awareness Training Program Challenges Introduction PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Information Security Cyber Safety Tips Protection Against Cyberattacks Ppt Slides Ideas PDF
Presenting information security cyber safety tips protection against cyberattacks ppt slides ideas pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network, protect, systems, sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Are you searching for a Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Security Monitor And Detect Abnormal Activity On Sensitive Data Elements PDF from Slidegeeks today.
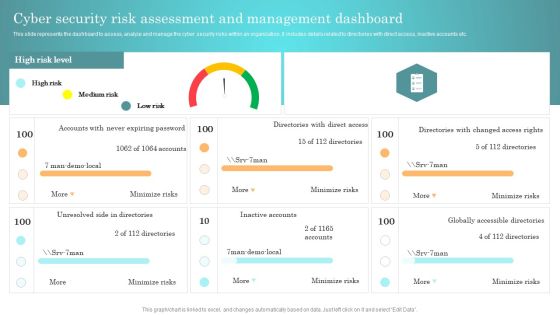
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF
This slide represents the dashboard to assess, analyze and manage the cyber security risks within an organization. It includes details related to directories with direct access, inactive accounts etc. Present like a pro with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Dashboard Themes PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.
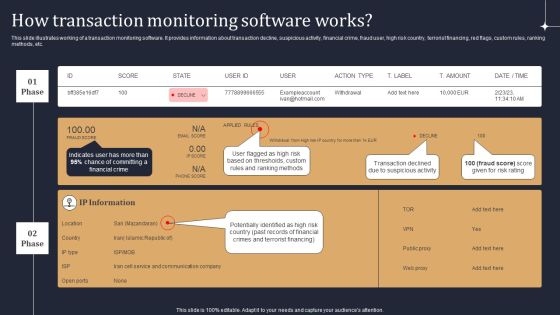
KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Are you searching for a KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF from Slidegeeks today.

Cyber Physical System To Enhance Steps For Cps Security Strategy Plan Elements PDF
This slide depicts the steps for the CPS security strategy plan, including recognizing the risks and assessing the current business situation, creating a goal and doing a gap analysis, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cyber Physical System To Enhance Steps For Cps Security Strategy Plan Elements PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF
This slide depicts the features of software defined networking that is intended to make a network more versatile and manageable. It includes streamlining operations, reducing time to market, developing customizable networks, and laying the foundation for intention. This SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The SDN Security Architecture Features Of Software Defined Networking SDN Infographics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cyber Security Risk Management Plan Incident Management Tool We Will Use Mockup PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative cyber security risk management plan incident management tool we will use mockup pdf bundle. Topics like incident management tool we will use can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
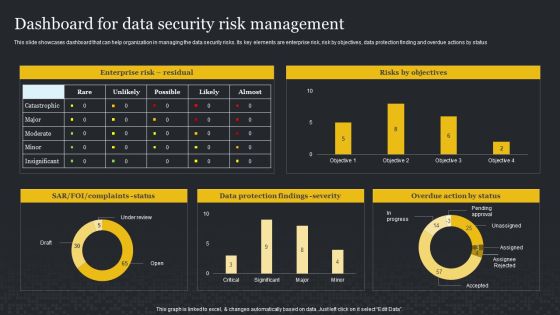
Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF
This slide showcases dashboard that can help organization in managing the data security risks. Its key elements are enterprise risk, risk by objectives, data protection finding and overdue actions by status. Welcome to our selection of the Dashboard For Data Security Risk Management Cybersecurity Risk Assessment Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 parcent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.
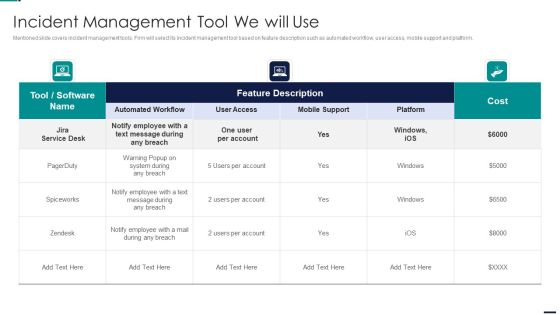
Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDF
Mentioned slide covers incident management tools. Firm will select its incident management tool based on feature description such as automated workflow, user access, mobile support and platform. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Incident Management Tool We Will Use Diagrams PDFbundle. Topics like Cost, Employee, Mobile Support, Automated Workflow, User Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF
This slide highlights the data protection and information security policy which includes policy and procedures of IT policy and it is applicable to all the employees and enforcement of the policy. Slidegeeks is here to make your presentations a breeze with Company Rules And Regulations Manual Data Protection And Information Security Policy And Procedure Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF
This slide portrays RACI matrix that company will use in order to ensure effective risks management. Here RACI stands for responsible, accountable, consulted and informed. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Responsibility Matrix To Ensure Effective Risk Management Mockup PDF bundle. Topics like Program Design, Cybersecurity Strategy, Performance Evaluation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
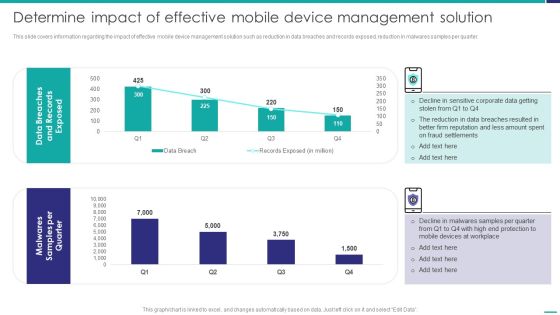
Determine Impact Of Effective Mobile Device Management Solution Mobile Device Security Management Graphics PDF
This slide covers information regarding the impact of effective mobile device management solution such as reduction in data breaches and records exposed, reduction in malwares samples per quarter. Deliver an awe inspiring pitch with this creative Determine Impact Of Effective Mobile Device Management Solution Mobile Device Security Management Graphics PDF bundle. Topics like Fraud Settlements, Devices Workplace, Malwares Samples can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Timeframe For Incident Management Ppt Slides Template PDF
This slide provides information regarding entire duration of incident handling process which occur in various phases. This is a security functioning centre timeframe for incident management ppt slides template pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like timeframe for incident management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. This modern and well-arranged Challenges And Solutions In Information Security Risk Management Cybersecurity Risk Assessment Demonstration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
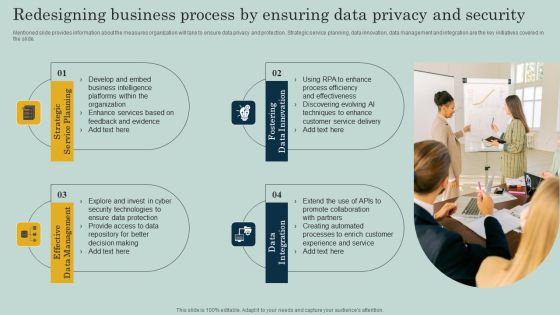
Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF
Mentioned slide provides information about the measures organization will take to ensure data privacy and protection. Strategic service planning, data innovation, data management and integration are the key initiatives covered in the slide. Create an editable Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. Redesigning Business Process By Ensuring Data Privacy And Security Ppt Infographics Objects PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF
Persuade your audience using this Steps Involved In Security Problem Management Ppt Inspiration Graphics Example PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Report, Declare, Remediate, Close, Respond, Identify. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF
This slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. This Best Practices To Implement Cloud Access Security Broker Ppt PowerPoint Presentation File Gallery PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF
This slide describes the first 30 days of managing cyber security in the manufacturing operations plan. It includes metric names, items to be measured, measurement method, time, and teams who are responsible and details. Slidegeeks is here to make your presentations a breeze with Deploying AI To Enhance Managing Cyber Security In Manufacturing 30 Days Plan Formats PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, youre sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Identification Lifecycle And Access Management Lifecycle In Cloud Security Guidelines PDF
This slide depicts access and identification management lifecycle in cloud computing systems. It provides information about user request, revoke access, approval, deletions, validations, etc.Presenting identification lifecycle and access management lifecycle in cloud security guidelines pdf to dispense important information. This template comprises one stage. It also presents valuable insights into the topics including identity deletion, revoke its access, identity or access This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
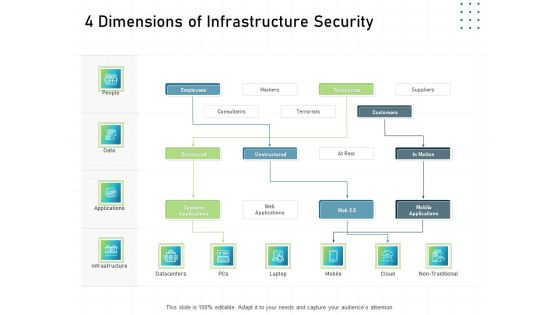
IT Infrastructure Administration 4 Dimensions Of Infrastructure Security Ppt Model Example Topics PDF
This is a it infrastructure administration 4 dimensions of infrastructure security ppt model example topics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Infrastructure Designing And Administration 4 Dimensions Of Infrastructure Security Pictures PDF
This is a infrastructure designing and administration 4 dimensions of infrastructure security pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Project Security Administration IT 30 60 90 Days Plan Ideas PDF
This is a project security administration it 30 60 90 days plan ideas pdf template with various stages. Focus and dispense information on threestages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like 30 60 90 days plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF
Want to ace your presentation in front of a live audience Our Development And Integration Of Cyber Security Incident Administration Table Of Contents Diagrams PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF
This slide covers CISSP certification details such as what is the CISSP, how to become certified, how to prepare for CISSP and why to get CISSP certifications. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF can be your best option for delivering a presentation. Represent everything in detail using Certified Information Systems Security Professional CISSP Details IT Certifications To Enhance Rules PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.
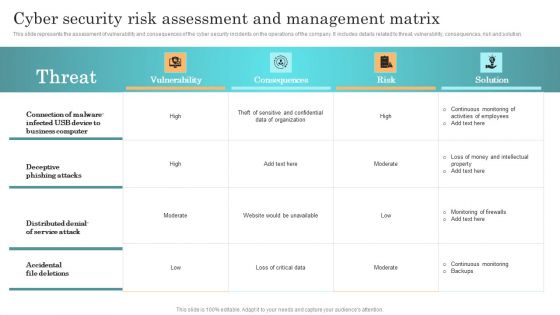
Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF
This slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Cyber Security Risk Assessment And Management Matrix Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF
This slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Present like a pro with Role Of Management In Security Governance Across Firm Ppt PowerPoint Presentation File Icon PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF
From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Organizing Security Awareness Understanding The Frequency And Weightage Of Cyber Attacks Topics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF
This slide portrays information regarding the management role in effective corporate security governance by highlight management level, strategic alignment, risk management, etc. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download How Management Enables Effective Corporate Security Governance Ppt PowerPoint Presentation File Pictures PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Grid Computing For High Performance Solutions Key Components Of Grid Computing Security Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF
This slide describes how SDN can help with intent based networking, which comprises many components, and it gives network managers the freedom to explain their expectations from the network. IBN SDN aims to attain even higher levels of functional clarity, computerized intelligence, and closed loop functionality. Explore a selection of the finest SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our SDN Security Architecture How SDN Can Help With Intent Based Networking IBN Themes PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF
This slide highlights the slide Managed Detection Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response.Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Security Automation To Analyze And Mitigate Cyberthreats Managed Detection And Response Layer Background PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF
This slide represents the timeline of effective management and minimization of impact of cyber security incidents on the business of the company. It includes details related to incident response, business continuity and review and recovery. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Incident Response Techniques Deployement Cyber Security Crisis Management Action Plan Timeline Rules PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF
The purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Prevention Of Information Impact Of Cyber Security Breach General Consequences Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

 Home
Home