Security Controls

Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF
The following slide exhibits four practices for selecting managed security service provider. Expertise, cost, business requirements and testimonials are some of the practices which will help the organization in selecting trusted security providers. Persuade your audience using this Key Practices For Selecting Managed Cyber Security Solutions Service Provider Ppt Professional Aids PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Expertise, Cost, Business Requirements, Testimonials. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Financial Security Guidelines Document Vector Icon Ppt PowerPoint Presentation Icon Outline PDF
Presenting financial security guidelines document vector icon ppt powerpoint presentation icon outline pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including financial security guidelines document vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Computing Security Operations Vector Icon Ppt PowerPoint Presentation Outline Influencers PDF
Presenting cloud computing security operations vector icon ppt powerpoint presentation outline influencers pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including cloud computing security operations vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enhanced Protection Corporate Event Administration Selecting Suitable Security Incident Management Software Demonstration PDF
This slide will help firm in selecting the suitable automated incident management software which will handle existing security and privacy issues and predict upcoming incidents. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration selecting suitable security incident management software demonstration pdf bundle. Topics like security incident forms, access rights, automated workflows, centralized platform can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Developing Firm Security Strategy Plan Information PDF
Deliver an awe inspiring pitch with this creative table of contents for developing firm security strategy plan information pdf bundle. Topics like implementing, security, management, corporate, governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF
Presenting 9 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Microsoft PDF to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including Security Plan, Business Goals, Management Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Roles And Responsibilities Of Risk Management Team Information Security Risk Administration Designs PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are - information security manager, risk management officer and chief information officer.Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Roles And Responsibilities Of Risk Management Team Information Security Risk Administration Designs PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
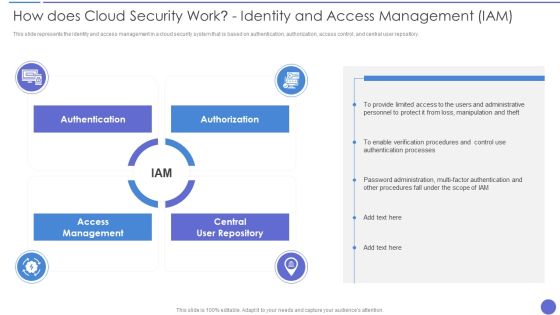
How Does Cloud Security Work Identity And Access Management IAM Professional PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a How Does Cloud Security Work Identity And Access Management IAM Professional PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Accessibility, Security, Quality. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
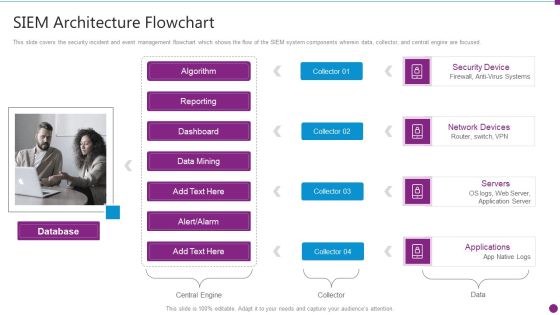
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Architecture Flowchart Microsoft PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. This is a security information and event management strategies for financial audit and compliance siem architecture flowchart microsoft pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, security device, network devices, servers, applications. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
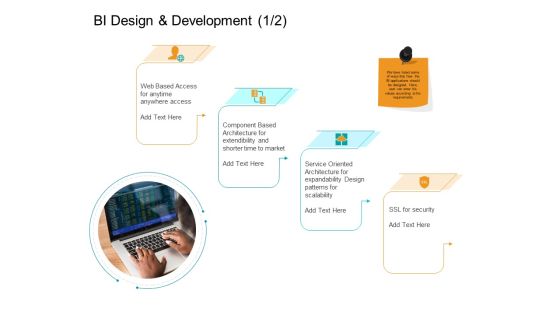
Facts Assessment BI Design And Development Security Ppt PowerPoint Presentation Slides Master Slide PDF
Presenting this set of slides with name facts assessment bi design and development security ppt powerpoint presentation slides master slide pdf. This is a four stage process. The stages in this process are web based access, component based architecture, service oriented architecture, ssl security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Crime Threat To Security Ppt PowerPoint Presentation Visual Aids Files
Presenting this set of slides with name cyber crime threat to security ppt powerpoint presentation visual aids files. This is a one stage process. The stage in this process is cyber crime threat to security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Bug And Cyber Security Vector Illustration Ppt PowerPoint Presentation Portfolio Skills PDF
Presenting this set of slides with name computer bug and cyber security vector illustration ppt powerpoint presentation portfolio skills pdf. This is a three stage process. The stages in this process are computer bug and cyber security vector illustration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Threat Detection Online Security Computer Program Ppt PowerPoint Presentation Professional Icon PDF
Presenting this set of slides with name threat detection online security computer program ppt powerpoint presentation professional icon pdf. This is a three stage process. The stages in this process are threat detection online security computer program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Icon Showing Insurance Of Personal Property Ppt PowerPoint Presentation Model Visuals PDF
Presenting this set of slides with name security icon showing insurance of personal property ppt powerpoint presentation model visuals pdf. This is a three stage process. The stages in this process are security icon showing insurance of personal property. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Client Testimonials For Company Online Database Proposal Topics PDF
Presenting this set of slides with name best data security software client testimonials for company online database proposal topics pdf. This is a two stage process. The stages in this process are client testimonials, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF
This slide depicts the security services on the google cloud platform. The purpose of this slide is to show the various security services available on the google cloud platform. The main components include a cloud resource manager, cloud identity and access management, cloud security scanner, and cloud platform security. Welcome to our selection of the Google Cloud Service Models Identity And Security Services On Google Cloud Platform Clipart PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF
This slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Cloud Access Security Broker Pillar Overview Ppt PowerPoint Presentation File Infographics PDF today and make your presentation stand out from the rest.

Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF
This slide covers quarterly cyber security planning roadmap by management to reduce risk with program maturity and cost .It consist secure , defend, contain, manage and anticipate. Persuade your audience using this Cyber Security Management Roadmap With Program Maturity And Cost Ppt PowerPoint Presentation File Graphic Tips PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Cyber Security Management, Level Risk Reduction. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Logging Sources Mockup PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting security information and event management strategies for financial audit and compliance siem logging sources mockup pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security devices, network devices, applications, servers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Solarwinds Security Event Manager Ethical Hacking Tool Ppt Show Clipart Images PDF
This slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy to use user interface, built-in compliance reports, etc. Presenting solarwinds security event manager ethical hacking tool ppt show clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like network, security program, dashboard, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF
This slide highlights the security company journey which showcases founding year, add armed security services in 2004, acquire GS security on 2015, add cash vans in 2016 and recruit personal protection officers. Get a simple yet stunning designed Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Security And Human Resource Services Business Profile Company Timeline From 1992 To 2022 Pictures PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF
The following slide highlights various managed security services strategies used for effective content management. Clean up plugins, scanning CMS platforms, and using the latest version are some of the key strategies which are highlighted in this template. Persuade your audience using this Managed Cyber Security Solutions Service Strategies For Effective Content Management Ppt Styles Example File PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Managed Cyber Security, Solutions Service Strategies, Effective Content Management. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF
This slide provides information regarding security objectives such as confidentiality, integrity and availability and their role in IoT security compliance. Boost your pitch with our creative Addressing Confidentiality Integrity And Availability In Iot Security Compliance Ppt Portfolio Deck PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Security Officer Service Company Profile Executive Leadership And Management Team Background PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Security Officer Service Company Profile Executive Leadership And Management Team Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Human Resource Management, Business Strategist, Management Consultant, Strategizing Business. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
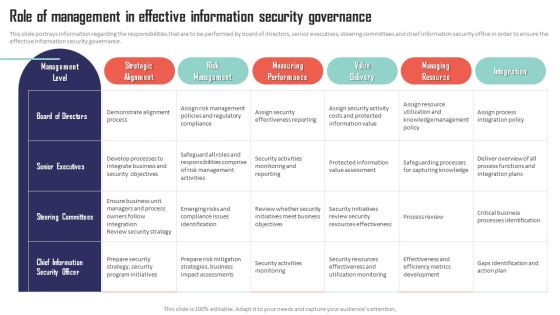
Mobile Device Management Role Of Management In Effective Information Security Microsoft PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Mobile Device Management Role Of Management In Effective Information Security Microsoft PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF
This slide showcases four cyclic stages of cyber security process of creating and maintaining a secure . It includes security assess , detecting , identifying , recording attacks , bringing safety measures , strengthening protection etc. Presenting Four Steps Business Cyclic Process Of Building Cyber Security Ppt PowerPoint Presentation File Model PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Recovery, Remediation, Repair, Site And Strengthen, Protection Through Updates. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF
This slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Presenting this PowerPoint presentation, titled Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cloud Access Security Broker And Encryption Ppt PowerPoint Presentation File Example PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Role Of Management In Effective Governance Mobile Device Security Management Background PDF
This slide portrays information regarding the responsibilities that are to be performed by board of directors, senior executives, steering committees and chief information security office in order to ensure the effective information security governance. Deliver and pitch your topic in the best possible manner with this Role Of Management In Effective Governance Mobile Device Security Management Background PDF. Use them to share invaluable insights on Senior Executives, Steering Committees, Effectiveness Reporting and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are - information security manager, risk management officer and chief information officer. Are you searching for a Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Information Systems Security And Risk Management Plan Roles And Responsibilities Of Risk Management Team Pictures PDF from Slidegeeks today.

Corporate Security And Risk Management Impact Analysis For Effective Threat Management Slides PDF
This slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Deliver an awe inspiring pitch with this creative corporate security and risk management impact analysis for effective threat management slides pdf bundle. Topics like impact analysis for effective threat management in securing workplace can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF
This slide provides information regarding mobile device compliance and policy enforcement with automated device setup, dynamic workflows and policies, etc. This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. There are so many reasons you need a Mobile Device Management Ensuring Checklist For Mobile Security Deployment Elements PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Integrations Ideas PDF
This is a security information and event management strategies for financial audit and compliance siem integrations ideas pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security events, network logs, applications and devices, it infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF
This slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. There are so many reasons you need a Requirements For Appropriate Cloud Security Model Ppt PowerPoint Presentation File Gallery PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Elements Of IT Security Disaster Recovery Planning Ppt Icon Rules PDF
This slide depicts the disaster recovery plan in the network security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a elements of information technology security disaster recovery planning ppt outline background pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like business, security, operations, business. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF
This slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security Categorization Worksheet For Assets Owned By Organization Microsoft PDF. Use them to share invaluable insights on Server Computer, System Location, System Accessibility and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Operations Compliance And Security Testing Ppt PowerPoint Presentation Slides Master Slide
This is a operations compliance and security testing ppt powerpoint presentation slides master slide. This is a three stage process. The stages in this process are quality assurance, quality analysis, qa, testing process, bugs analysis.

Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF
This slide highlights the security company leadership and management team which includes president CEO, executive vice president of finance, EVP home security, chief administration officer. This is a Security And Surveillance Company Profile Executive Leadership And Management Team Demonstration PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Incentive Scheme, Referral Partners, Sales Strategy. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Distributed Computing IT Security Of Data And Networks In Edge Computing Themes PDF
This slide represents the security of data and networks in edge computing. It also shows that data is secure because data is not traveling on any network however, edge devices are vulnerable. Presenting distributed computing it security of data and networks in edge computing themes pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organization, data storage, computing security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Consolidated Cycle With Security Management And Health Ppt PowerPoint Presentation File Show PDF
This slide showcase integrated cycle with security and health management system. It includes major activities such as-quality management for internal and external user satisfaction, minimizing the pollution produced etc. Presenting consolidated cycle with security management and health ppt powerpoint presentation file show pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including security and heath, corporate social responsibility, environment. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Real Time Assessment Of Security Threats Benefits Of Choosing Our Company For SIEM Services Introduction PDF
This slide covers the benefits of SIEM software system such as improved efficiency, cost savings, compliance, prevention of security breaches, etc. This is a real time assessment of security threats benefits of choosing our company for siem services introduction pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cost saving, security events, compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Agency Business Profile Executive Leadership And Management Team Elements PDF
This slide highlights the security guard company management team which includes companys chairman and MD, head of security operations, training, strategic growth and site. Presenting Security Agency Business Profile Executive Leadership And Management Team Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Business Economist, Resource Management, Manufacturing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF
The flowing slide highlights managed security service framework. It provides information about components such as clients issues and key operations to be performed by service provider such as antivirus offerings, data loss prevention etc. Presenting Managed Cyber Security Solutions Service Framework For Operations Management Ppt Styles Themes PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Framework Significance, Business Security Users, Major Bottlenecks. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
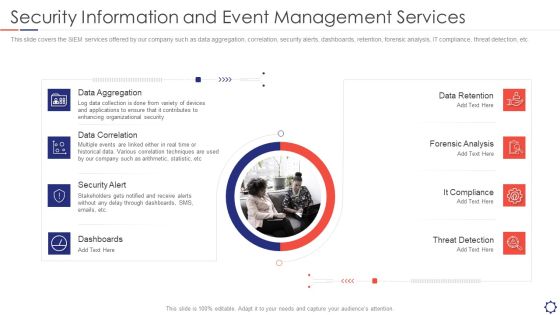
SIEM Security Information And Event Management Services Ppt Ideas Graphics Pictures PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. This is a siem security information and event management services ppt ideas graphics pictures pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Aggregation, Data Correlation, Security Alert, Dashboards, Data Retention. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Human Resource Services Business Profile Commercial And Residential Microsoft PDF
This slide highlights the commercial and residential building security offered by security company which includes visitor management, vehicle and parking management, CCTV operating and monitoring. Want to ace your presentation in front of a live audience Our Security And Human Resource Services Business Profile Commercial And Residential Microsoft PDF can help you do that by engaging all the users towards you.. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy-to-edit and downloadable. Use these for both personal and commercial use.

Elements Of IT Security End User Education Ppt Summary Portrait PDF
This slide shows the end-user education within the network security model. It also represents various factors that effective training plans should involve. Presenting elements of information technology security end user education ppt model graphics pictures pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like elements of information technology security end user education. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF
This slide steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Create an editable Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Steps For Information Security Risk Management Cybersecurity Risk Assessment Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

SIEM Services Security Information And Event Management Services Ppt Ideas Design Ideas PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. This is a siem services security information and event management services ppt ideas design ideas pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data correlation, data aggregation, security alert, dashboards. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
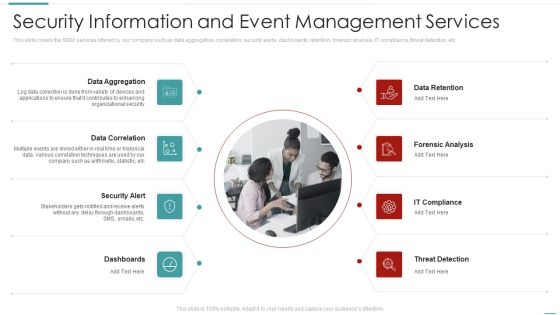
Risk Recognition Automation Security Information And Event Management Services Ppt Slides Demonstration PDF
This slide covers the SIEM services offered by our company such as data aggregation, correlation, security alerts, dashboards, retention, forensic analysis, IT compliance, threat detection, etc. Presenting risk recognition automation security information and event management services ppt slides demonstration pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like data aggregation, data correlation, security alert, dashboards, data retention. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF
This slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Welcome to our selection of the Workplace Portable Device Monitoring And Administration Ensuring Checklist For Mobile Security Deployment Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
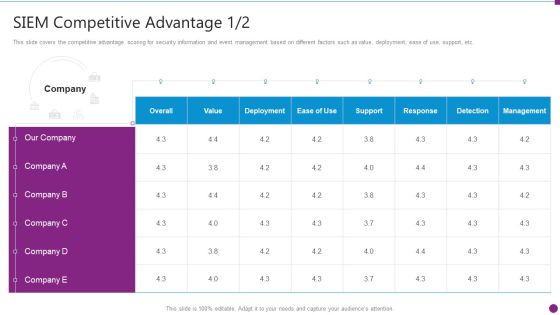
Security Information And Event Management Strategies For Financial Audit And Compliance SIEM Competitive Guidelines PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance siem competitive guidelines pdf. Use them to share invaluable insights on siem competitive advantage and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Officer Service Company Profile Awards And Accolades Ppt PowerPoint Presentation Gallery Example PDF
This slide highlights the awards and allocates received by security company which includes best security company, community member award, great place to work and corporate excellence awards. This is a Security Officer Service Company Profile Awards And Accolades Ppt PowerPoint Presentation Gallery Example PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like SIA Awards, ASIS International, GPTW Institute, ICSI India. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing Firm Security Strategy Plan How Firm Handle Various Insider Threats At Workplace Elements PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a developing firm security strategy plan how firm handle various insider threats at workplace elements pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail System Maintenance And Monitoring Summary PDF
This slide provides information about the ninth and the last step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., System Maintenance and Monitoring. Presenting security management plan steps in detail system maintenance and monitoring summary pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like types of system maintenance, installation costs, types of system monitoring. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Determining Roles And Responsibilities For Risk Handling Mobile Device Security Management Designs PDF
This slide provides information regarding the roles and responsibilities of management in handling mobile device security risks. Key people involved in risk handling are chief risk officer, chief information security officer, senior management and executives and line managers. This is a Determining Roles And Responsibilities For Risk Handling Mobile Device Security Management Designs PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Executive Management, Development Implementation, Management Program. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Steps To Create Role Specific Cyber Security Training Program Structure PDF
This slide highlights various steps to develop role based training program for cyber security risk management. It includes key steps such as assess existing training, identify employee roles, define role-specific security risks, outline process and technology, etc. Persuade your audience using this Key Steps To Create Role Specific Cyber Security Training Program Structure PDF This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Process, Description, Elements. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF
The following slide highlights four step process of cloud digitization of security systems. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Persuade your audience using this Key Statistics Of IT Digitization Of Security Systems Ppt Layouts Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Container Configure Management, Use Infrastructure, Code Automate Asset Tagging. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
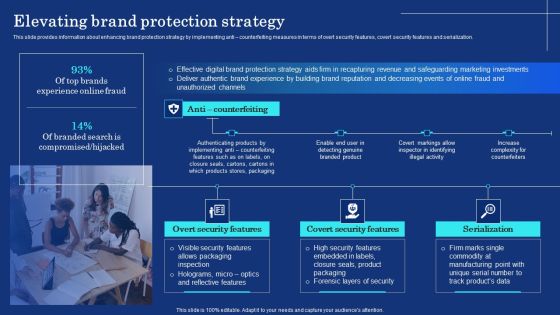
Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF
This slide provides information about enhancing brand protection strategy by implementing anti counterfeiting measures in terms of overt security features, covert security features and serialization. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizational Assets Security Management Strategy Elevating Brand Protection Strategy Guidelines PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF
The following slide outlines a comprehensive training plan for managed security service and awareness for employees. It provides information about the training subject, trainer name, training hours, status and learning outcome. Pitch your topic with ease and precision using this Training Plan For Managed Cyber Security Solutions Service Ppt Summary Guide PDF. This layout presents information on Training Plan, Managed Cyber Security, Solutions Service. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
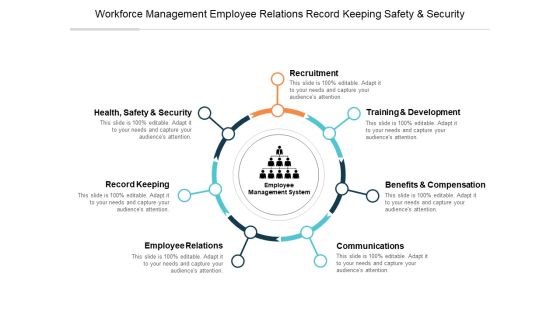
Workforce Management Employee Relations Record Keeping Safety And Security Ppt PowerPoint Presentation Model Outline
This is a workforce management employee relations record keeping safety and security ppt powerpoint presentation model outline. This is a seven stage process. The stages in this process are employee information system, staff management system.

Security Officer Service Company Profile Executive Summary Ppt PowerPoint Presentation Gallery Samples PDF
This slide highlights the executive summary of security company that includes company overview, founder, USP, company shareholding, achievements, key facts and figures This is a Security Officer Service Company Profile Executive Summary Ppt PowerPoint Presentation Gallery Samples PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Company Shareholding, Achievements, Best Security Company. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
 Home
Home