Security Controls

IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF
This slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Presenting IT Risk Control Strategies Security And Risk Management With Capabilities Ppt Professional Graphics Example PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Enterprise Security Strategy, Compliance, Security Policy Compliance. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Slidegeeks is here to make your presentations a breeze with Organizations Risk Management And IT Security Preventive IT Technical Control Measures Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Model For IT Risk Control Strategies Security Risk Management Ppt Ideas Portrait PDF
This slide shows the model that depicts IT security risk management which focuses on identification, protection, detection, response and recovery planning with security asset management, governance, data security, detection processes, risk analysis and planning, etc. Persuade your audience using this Model For IT Risk Control Strategies Security Risk Management Ppt Ideas Portrait PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Identifying, Protecting, Detecting. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF
The following slide provides an annual roadmap to prevent cyber threats which is further divided into four quarters. It includes controlling inventory, hardware and software assets, regularly vulnerability management etc. Presenting Quarterly Roadmap To Control Cyber Security Incident Ppt Outline Layout PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Assessment And Testing, CUI Inventory Update, App Penetration Test. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Desktop Security Management Define Access Control Measures For Employees Icons PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a desktop security management define access control measures for employees icons pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Organizations Risk Management And IT Security Detection And Prevention Of Operational Controls Summary PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. Get a simple yet stunning designed Organizations Risk Management And IT Security Detection And Prevention Of Operational Controls Summary PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizations Risk Management And IT Security Detection And Prevention Of Operational Controls Summary PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Developing Firm Security Strategy Plan Determine User Access Controls Levels Guidelines PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Deliver an awe inspiring pitch with this creative developing firm security strategy plan determine user access controls levels guidelines pdf bundle. Topics like administrator, maintainer, guest or disabled can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF
This slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Get a simple yet stunning designed Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Organizational Assets Security Management Strategy Determine User Access Controls Levels Diagrams PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Organizations Risk Management And IT Security Identification And Recovery Of Technical Controls Introduction PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF
This slide represents the block diagram representing the access control in secured database management system. It includes details related to database and security administrator, authorization system, database schemas, application programs etc. Presenting Access Control In Secured DBMS Software Ppt PowerPoint Presentation Gallery Portrait PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including Database Administrator, Security Administrator, Database, Application Programs. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

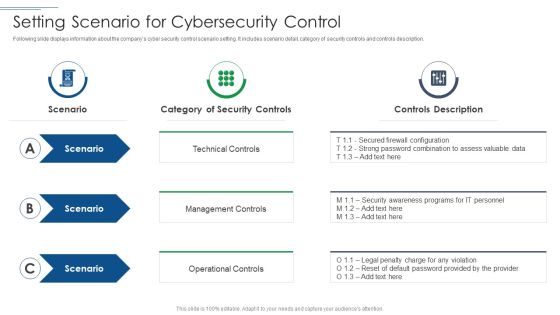
Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Access Control System Key Security Lock Ppt PowerPoint Presentation Pictures Summary
This is a access control system key security lock ppt powerpoint presentation pictures summary. This is a three stage process. The stages in this process are access rights, access management, business.

Access Control Application Account Security Lock Ppt PowerPoint Presentation File Slide Portrait
This is a access control application account security lock ppt powerpoint presentation file slide portrait. This is a two stage process. The stages in this process are access rights, access management, business.

Control Tower For Security Vector Icon Ppt PowerPoint Presentation Infographic Template Clipart PDF
Presenting this set of slides with name control tower for security vector icon ppt powerpoint presentation infographic template clipart pdf. The topics discussed in these slide is control tower for security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
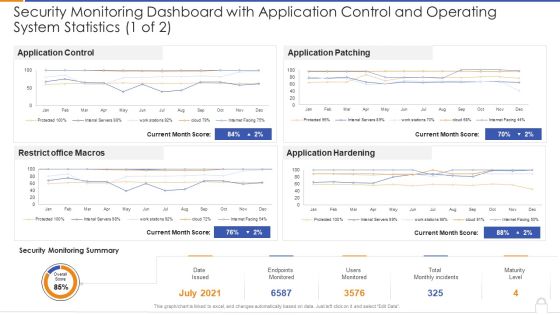
Security Monitoring Dashboard With Application Control And Operating System Statistics 1 Of 2 Ideas PDF
Deliver and pitch your topic in the best possible manner with thissecurity monitoring dashboard with application control and operating system statistics 1 of 2 ideas pdf Use them to share invaluable insights on security monitoring dashboard with application control and operating system statistics and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Online Security System For Business Quality Control Ppt PowerPoint Presentation Gallery Templates PDF
Presenting this set of slides with name online security system for business quality control ppt powerpoint presentation gallery templates pdf. This is a six stage process. The stages in this process are network engineering program, information security management, social engineering program, ethical hacking program, crime investigation program, internet security program. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF
This slide highlights the implementation control with residual risk which includes information technology risks and threats are controlled and minimized by system control measures. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Organizations Risk Management And IT Security Residual Risk From IT Control Measures Slides PDF today and make your presentation stand out from the rest.

Final Food Product Quality Control Checklist Food Security Excellence Ppt Portfolio Layout Ideas PDF
This slide provides information regarding the food quality control checklist which will be filled by project supervisor for quality controllable assessment. Deliver an awe inspiring pitch with this creative final food product quality control checklist food security excellence ppt portfolio layout ideas pdf bundle. Topics like improvement, malfunctioning, sanitation, quality indicators can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Monitoring Dashboard With Application Control And Operating System Statistics Template PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver and pitch your topic in the best possible manner with this security monitoring dashboard with application control and operating system statistics template pdf. Use them to share invaluable insights on application control, restrict office macros, application patching, application hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Addressing Processed Food Quality Control Tools Food Security Excellence Ppt Infographics Show PDF
This slide provides information regarding the quality control tools such as ingredient specification and product standards. Deliver an awe inspiring pitch with this creative addressing processed food quality control tools food security excellence ppt infographics show pdf bundle. Topics like microbiological standards, chemical characteristics, physical characteristics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Food Process Tracking With Control Chart Food Security Excellence Ppt Inspiration Graphics Example PDF
The quality team will use control chart as food quality management tool. It will help in determining the food processes are stable and capable under provided conditions. Deliver an awe inspiring pitch with this creative food process tracking with control chart food security excellence ppt inspiration graphics example pdf bundle. Topics like action plan, resources, chart analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Download PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls download pdf bundle. Topics like logical access controls, control implementation costs, physical access controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Microsoft PDF
This slide provides information about the fifth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Adopting Access Controls. Deliver an awe inspiring pitch with this creative security management plan steps in detail adopting access controls microsoft pdf bundle. Topics like implementation costs, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Adopting Access Controls Clipart PDF
Deliver and pitch your topic in the best possible manner with this Security management plan steps in detail adopting access controls clipart pdf. Use them to share invaluable insights on logical access controls, physical access controls, control implementation costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Adopting Access Controls Demonstration PDF
Presenting security management plan steps in detail adopting access controls demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like logical access controls, control implementation, physical access controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Online Security Learning System For Malware Threat Control Ppt PowerPoint Presentation Layouts Portfolio PDF
Presenting this set of slides with name online security learning system for malware threat control ppt powerpoint presentation layouts portfolio pdf. This is a three stage process. The stages in this process are network protection and control, access control protection, email and web browser protections, virus penetration testing and control fundamentals, password protection, wireless protection, cyber incitement management, ethical hacking. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Define Access Control Measures For Employees IT Security IT Ppt Professional Icon PDF
This slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. This is a define access control measures for employees it security it ppt professional icon pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, access data, networks, responsibilities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Remote Access Control Diagrams PDF
This is a security management plan steps in detail remote access control diagrams pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like control security status, requirement for additional software installation, remote access control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Plan Steps In Detail Remote Access Control Mockup PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e. Remote Access Control. Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control mockup pdf bundle. Topics like security management plan steps in detail remote access control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Topics PDF
This slide provides information about the sixth step in security management plan that must be implemented by the company and IT security manager in order to solve potential insider threats, external security breaches and reduce the risk of CaaS i.e., Remote Access Control. Deliver and pitch your topic in the best possible manner with this security management plan steps in detail remote access control topics pdf. Use them to share invaluable insights on requirement, security, implementation cost and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Management Plan Steps In Detail Remote Access Control Inspiration PDF
Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control inspiration pdf bundle. Topics like deploying remote access, provides a secure connection, requirement for additional can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF
This is a IT Security Risk Management Approach Introduction Setting Scenario For Cybersecurity Control Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Technical Control, Management Controls, Operational Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Personnel Standing In Middle Of Road For Traffic Controlling Ppt PowerPoint Presentation Designs PDF
Showcasing this set of slides titled security personnel standing in middle of road for traffic controlling ppt powerpoint presentation designs pdf. The topics addressed in these templates are security personnel standing in middle of road for traffic controlling. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

cyber security administration in organization how financial risk can be controlled inspiration pdf
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. This is a cyber security administration in organization how financial risk can be controlled inspiration pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like handling, liquidity, financial, flexibility, structure . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
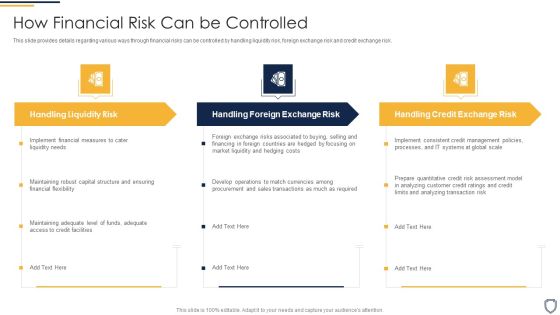
Corporate Security And Risk Management How Financial Risk Can Be Controlled Infographics PDF
This slide provides details regarding various ways through financial risks can be controlled by handling liquidity risk, foreign exchange risk and credit exchange risk. Presenting corporate security and risk management how financial risk can be controlled infographics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like handling liquidity risk, handling foreign exchange risk, handling credit exchange risk . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF
This slide covers business strategy and attributes mapping for security controls which includes mapping business requirements, evaluating risk and product with service mapping. Showcasing this set of slides titled Business Information Strategy And Attributes Mapping For Protection Controls Portrait PDF. The topics addressed in these templates are Major Identification, Service Mapping, Recommendation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. This is a Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Detection Operation Controls, Preventive Operation Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Hierarchy Of Controls For Eliminating Covid At Workplace Demonstration PDF
This template covers hierarchy of controls to eliminate the spread of COVID 19 in the workplace. It also depicts that based on risk levels identified for the workplace this control program is prepared to protect the general workforce from spreading infection. Deliver an awe inspiring pitch with this creative Hierarchy Of Controls For Eliminating Covid At Workplace Demonstration PDF bundle. Topics like Require, Execute, Team Member can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT System Risk Management Guide Detection And Prevention Of Operational Controls Structure PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. Get a simple yet stunning designed IT System Risk Management Guide Detection And Prevention Of Operational Controls Structure PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT System Risk Management Guide Detection And Prevention Of Operational Controls Structure PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
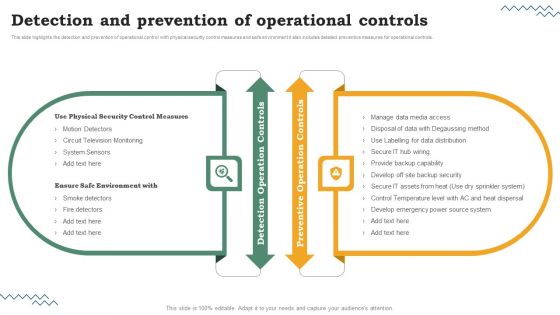
Risk Evaluation Of Information Technology Systems Detection And Prevention Of Operational Controls Portrait PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. Get a simple yet stunning designed Risk Evaluation Of Information Technology Systems Detection And Prevention Of Operational Controls Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Risk Evaluation Of Information Technology Systems Detection And Prevention Of Operational Controls Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for. Grab this template today.

Controls Internal Audit And Tax Management Financial Regulatory Compliance Designs PDF
This slide showcases internal audit and tax management for evaluating firms controls, corporate governance and accounting process and securing compliance with policies of company.Presenting Controls Internal Audit And Tax Management Financial Regulatory Compliance Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Internal Audit, Tax Management, Reporting Processes This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
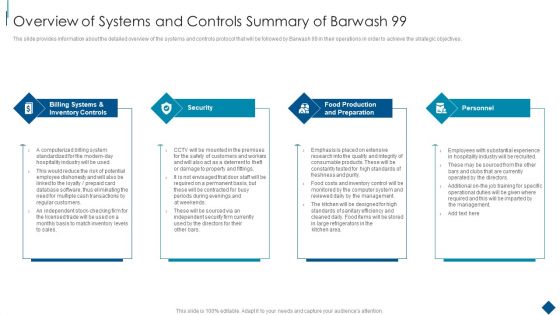
Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Billing Systems Inventory, Controls Security Personnel, Food Production Preparation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
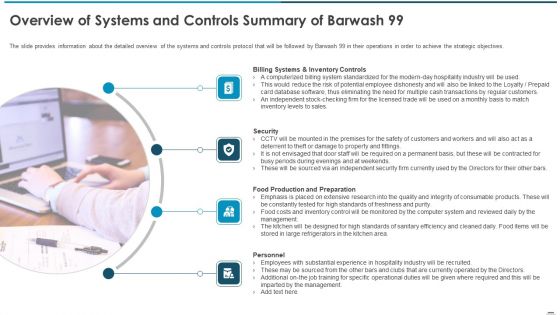
Sell Side Confidential Information Memorandum CIM Pitch Book Overview Of Systems And Controls Summary Brochure PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. This is a sell side confidential information memorandum cim pitch book overview of systems and controls summary brochure pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like billing systems and inventory controls, security, food production and preparation, personnel. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Management Consulting Sample Diagram Powerpoint Images
This is a security management consulting sample diagram powerpoint images. This is a four stage process. The stages in this process are information risk assessment, risk mitigation, security controls, business strategy.

Classified Data Memo Record With Strategic Goals Overview Of Systems And Controls Summary Of Barwash 99 Rules PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting classified data memo record with strategic goals overview of systems and controls summary of barwash 99 rules pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like billing systems and inventory controls, security, food production and preparation, personnel. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Management Good Ppt Example
This is a security management good ppt example. This is a thirteen stage process. The stages in this process are logical security, access control, digital video , asset management, alarm, management, multi tenant property management, fire alarm integration.

Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Presenting Information Technology Threat Mitigation Methods Identification And Recovery Of Technical Controls Demonstration PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Recover Secure State, Virus Eradication, Audit. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT System Risk Management Guide Identification And Recovery Of Technical Controls Microsoft PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Slidegeeks is here to make your presentations a breeze with IT System Risk Management Guide Identification And Recovery Of Technical Controls Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
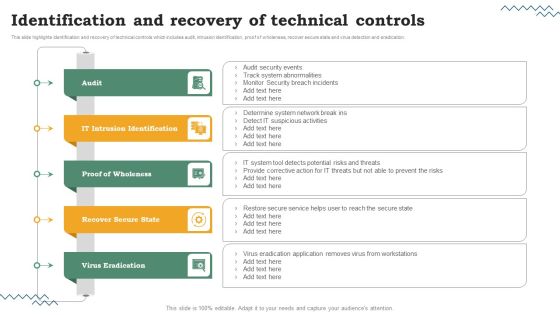
Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Slidegeeks is here to make your presentations a breeze with Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Steps Of Risk Management With Administrative Controls Ppt PowerPoint Presentation Ideas Example Introduction PDF
This Slide covers four risk assessment control measures which helps the project managers in preventing the harm and reducing the risk. It also includes elimination, substitution, engineering control, administration control and personal protective clothes and equipment. Persuade your audience using this steps of risk management with administrative controls ppt powerpoint presentation ideas example introduction pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including personal protective clothing equipment, administrative controls, engineering controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Financial Planning Pyramid With Administrative Controls Ppt PowerPoint Presentation Summary Tips PDF
Presenting this set of slides with name financial planning pyramid with administrative controls ppt powerpoint presentation summary tips pdf. This is a five stage process. The stages in this process are elimination, substitution, engineering controls, administrative controls, personal protective equipment. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

CIM With Operation And Account Statements Overview Of Systems And Controls Summary Demonstration PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting cim with operation and account statements overview of systems and controls summary demonstration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like billing systems, security, food production and preparation, personnel . In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
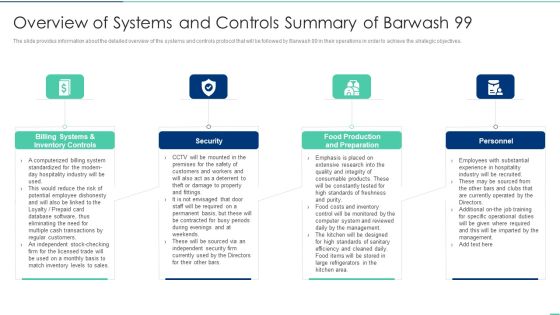
Overview Of Systems And Controls Summary Of Barwash 99 Ppt Professional PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. This is a overview of systems and controls summary of barwash 99 ppt professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sales, systems, inventory, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategic Playbook Sustaining Business During Pandemic Hierarchy Of Controls For Eliminating Topics PDF
This template covers hierarchy of controls to eliminate the spread of COVID 19 in the workplace. It also depicts that based on risk levels identified for the workplace this control program is prepared to protect the general workforce from spreading infection. Deliver an awe inspiring pitch with this creative Strategic Playbook Sustaining Business During Pandemic Hierarchy Of Controls For Eliminating Topics PDF bundle. Topics like Require, Employees, Administrative can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Hierarchy Of Controls For Eliminating Covid At Workplace Pandemic Company Playbook Infographics PDF
This template covers hierarchy of controls to eliminate the spread of COVID-19 in the workplace. It also depicts that based on risk levels identified for the workplace this control program is prepared to protect the general workforce from spreading infection.From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy-to-edit and customizable templates. Hierarchy Of Controls For Eliminating Covid At Workplace Pandemic Company Playbook Infographics PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Post COVID Organizational Planning Model Hierarchy Of Controls For Eliminating Covid At Workplace Download PDF
This template covers hierarchy of controls to eliminate the spread of COVID 19 in the workplace. It also depicts that based on risk levels identified for the workplace this control program is prepared to protect the general workforce from spreading infection. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Post COVID Organizational Planning Model Hierarchy Of Controls For Eliminating Covid At Workplace Download PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Post COVID Organizational Planning Model Hierarchy Of Controls For Eliminating Covid At Workplace Download PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Types Data Protection Controls Ppt PowerPoint Presentation Ideas Summary Cpb Pdf
Presenting this set of slides with name types data protection controls ppt powerpoint presentation ideas summary cpb pdf. This is an editable Powerpoint five stages graphic that deals with topics like types data protection controls to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
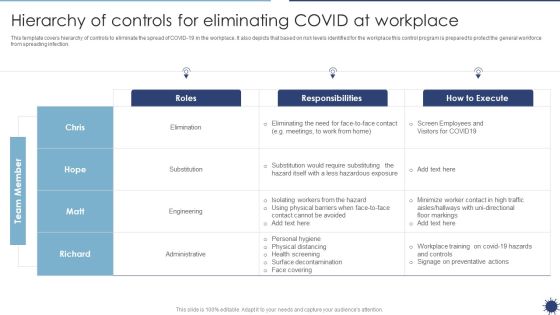
Hierarchy Of Controls For Eliminating COVID At Workplace Organization Transformation Instructions Guidelines PDF
This template covers hierarchy of controls to eliminate the spread of COVID-19 in the workplace. It also depicts that based on risk levels identified for the workplace this control program is prepared to protect the general workforce from spreading infection.This Hierarchy Of Controls For Eliminating COVID At Workplace Organization Transformation Instructions Guidelines PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Post Pandemic Business Hierarchy Of Controls For Eliminating Covid At Workplace Pictures PDF
This template covers hierarchy of controls to eliminate the spread of COVID-19 in the workplace. It also depicts that based on risk levels identified for the workplace this control program is prepared to protect the general workforce from spreading infection. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Post Pandemic Business Hierarchy Of Controls For Eliminating Covid At Workplace Pictures PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
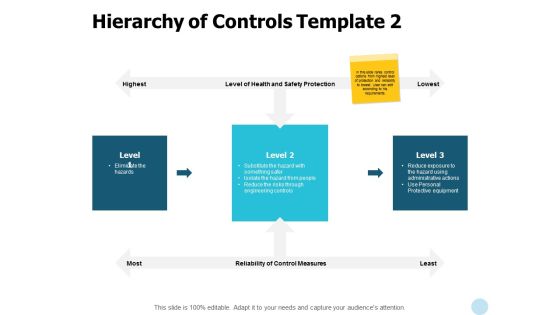
Hierarchy Of Controls Protective Equipment Ppt PowerPoint Presentation Infographic Template Smartart
Presenting this set of slides with name hierarchy of controls protective equipment ppt powerpoint presentation infographic template smartart. This is a three stage process. The stages in this process are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security System Ppt Powerpoint Topics
This is a information security system ppt powerpoint topics. This is a seven stage process. The stages in this process are network security, access control, security management, physical security, business continuity and dr planning, operations security, application system security, information.

Cyber Security Risk Mitigation Framework Demonstration PDF
The following slide showcases the risk mitigation framework to plan preventive and reactive actions. It includes elements such as categorize, select, implement, assess, authorize and monitor etc. Persuade your audience using this Cyber Security Risk Mitigation Framework Demonstration PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Categorize System, Select Security Controls, Implement Security Controls. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Security Operations Management Sample Presentation Images
This is a security operations management sample presentation images. This is a five stage process. The stages in this process are compliance and validation, security organization, device control, security operations, patch management.

Data Safety Initiatives Setting Scenario For Cybersecurity Control Inspiration PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative data safety initiatives setting scenario for cybersecurity control inspiration pdf bundle. Topics like scenario, technical controls, management controls, operational controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
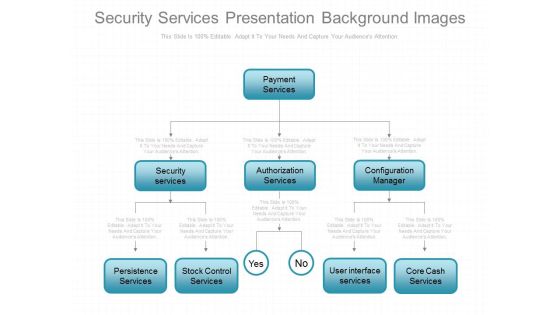
Security Services Presentation Background Images
This is a security services presentation background images. This is an eight stage process. The stages in this process are payment services, security services, authorization services, configuration manager, persistence services, stock control services, user interface services, core cash services.

Data Safety Initiatives For Effective IT Security Threats Administration Security Lifecycle Template PDF
This is a data safety initiatives for effective it security threats administration security lifecycle template pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information system, security controls, monitor, assess, implement, authorize. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
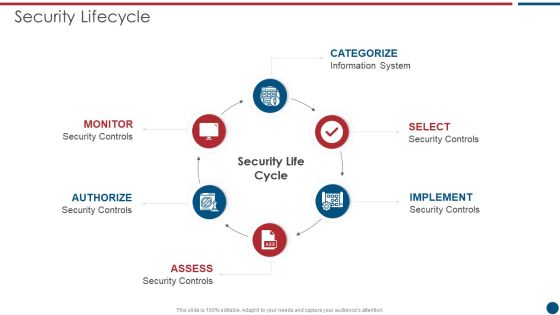
Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF
This is a Risk Based Procedures To IT Security Security Lifecycle Ppt PowerPoint Presentation File Rules PDF template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information System, Security Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Implementation Process Brochure PDF
The following slide explains implementation method for cybersecurity risk management for the organization to ensure protection of key business data. It includes steps such as categorize, security controls, implementation, assess, etc. Persuade your audience using this IT Security Risk Management Implementation Process Brochure PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Monitor, Authorize, Assess, Implementation, Security Controls, Categorize System. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF
This slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs.Presenting Cloud Security Assessment Key Challenges In Cloud Security Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Compliance Violations, Access Control, Daniel Of Service In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

SDN Security Architecture Software Defined Networking And Security Guidelines PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate SDN Security Architecture Software Defined Networking And Security Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Setting Scenario For Cybersecurity Control Ppt Pictures Graphics Tutorials PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting setting scenario for cybersecurity control ppt pictures graphics tutorials pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like management controls, technical controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Administration Powerpoint Shapes
This is a security administration powerpoint shapes. This is a three stage process. The stages in this process are storage management, directory service administration, security administration.

Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment SMB Cloud Security Solutions Diagrams PDF. Use them to share invaluable insights on Cloud Frameworks, Information Division, Cautious Scaling and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Solutions Powerpoint Templates
This is a security solutions powerpoint templates. This is a four stage process. The stages in this process are site preparation, networking solutions, security solutions, it system integration.

Cloud Security Assessment Why Cloud Security Is Important Pictures PDF
This slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Why Cloud Security Is Important Pictures PDF bundle. Topics like Centralized Security, Cost Effective, Diminished Administration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enterprise Information Security Process Ppt Sample Ppt Files
This is a enterprise information security process ppt sample ppt files. This is a six stage process. The stages in this process are security policy, access control, compliance, physical security, operations security, business continuity.

Desktop Security Management Best Practices For Cloud Security Topics PDF
This slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. This is a desktop security management best practices for cloud security topics pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like security, management, measures, planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance.This is a Cloud Security Assessment Topics That Fall Under The Umbrella Of Cloud Security Microsoft PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Threat Prevention, Access Control, Centre Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Computing Application Security Architecture Checklist Template PDF
The slide shows course of action for application security control and management. It includes understanding responsibility model, focusing on design andarchitect, testing, managing control, regulating and compliance needs, user training and monitoring and optimizing. Showcasing this set of slides titled Cloud Computing Application Security Architecture Checklist Template PDF. The topics addressed in these templates are Data Classification Accountability, Client Point Protection, Penetration Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Information Integrated Protection Control For Threat Prevention Graphics PDF
This slide covers business integrated security control for threat prevention which includes Business process and security system.Pitch your topic with ease and precision using this Business Information Integrated Protection Control For Threat Prevention Graphics PDF. This layout presents information on Incident Response, Security Policy Distribution, Threat Information. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Computer Security Incident Handling Optimizing Cybersecurity Framework Roadmap Designs PDF
Presenting this set of slides with name computer security incident handling optimizing cybersecurity framework roadmap designs pdf. The topics discussed in these slides are implement enterprise security program, implement control environment, implement security processes. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Complete IT Security Implementation Checklist Ppt Layouts Graphics PDF
This slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Presenting complete information technology security implementation checklist ppt file introduction pdf to provide visual cues and insights. Share and navigate important information on twelve stages that need your due attention. This template can be used to pitch topics like secure communications, device security, access control measures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Overview Of Security Operations Centre Sample PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system.Deliver and pitch your topic in the best possible manner with this overview of security operations centre sample pdf. Use them to share invaluable insights on command and control, network security monitoring, threat intelligence and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF
This slide portrays information regarding optimization of current mobile device security framework. The IT department will require to fulfill crucial activities in specific timeframe. Deliver and pitch your topic in the best possible manner with this Implementing Mobile Device Security Framework Roadmap Mobile Device Security Management Infographics PDF. Use them to share invaluable insights on Implement Enterprise, Security Program, Implement Control and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF
This slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance. This is a Cloud Information Security Topics That Fall Under The Umbrella Of Cloud Security Ppt Layouts Inspiration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Access Control, Threat Prevention, Threat Detection. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Security Company Strategic Partnerships Summary PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation.Deliver and pitch your topic in the best possible manner with this Security Camera System Company Profile Security Company Strategic Partnerships Summary PDF. Use them to share invaluable insights on Security Application, Technology Partner, Google Assistant and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Handling Cyber Threats Digital Era Setting Scenario For Cybersecurity Control Ppt Infographics Brochure PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Presenting handling cyber threats digital era setting scenario for cybersecurity control ppt infographics brochure pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like technical controls, management controls, operational controls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Security Company Strategic Partnerships Graphics PDF. Use them to share invaluable insights on Technology Partner, Installation Centres, Partnership Type and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

How Does Cloud Security Work Cloud Computing Security IT Ppt Show Graphics Design PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting how does cloud security work cloud computing security it ppt show graphics design pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like data security, access management, governance, business continuity planning, legal compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. This is a Cloud Information Security How Does Cloud Security Work Ppt Inspiration Graphics PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Legal Compliance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.This is a Cloud Security Assessment How Does Cloud Security Work Data Retention And Business Continuity Planning Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Data Security, Access Management, Business Continuity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Security Brochure PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard security brochure pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Security Monitoring Dashboard Sample PDF
Deliver an awe inspiring pitch with this creative modern security observation plan to eradicate cybersecurity risk and data breach security monitoring dashboard sample pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
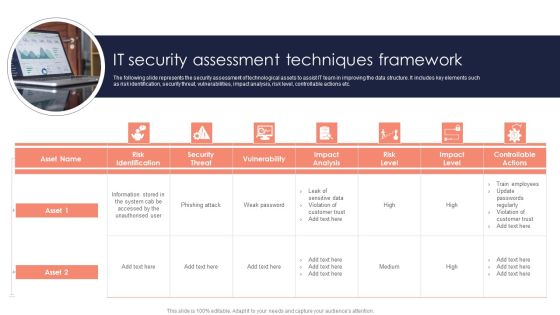
It Security Assessment Techniques Framework Introduction PDF
The following slide represents the security assessment of technological assets to assist IT team in improving the data structure. It includes key elements such as risk identification, security threat, vulnerabilities, impact analysis, risk level, controllable actions etc. Persuade your audience using this It Security Assessment Techniques Framework Introduction PDF. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including Impact Analysis, Risk Level, Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Network Security Ppt PowerPoint Presentation Show Rules
This is a cyber security network security ppt powerpoint presentation show rules. This is a nine stage process. The stages in this process are business, lock, planning, strategy, marketing, security.
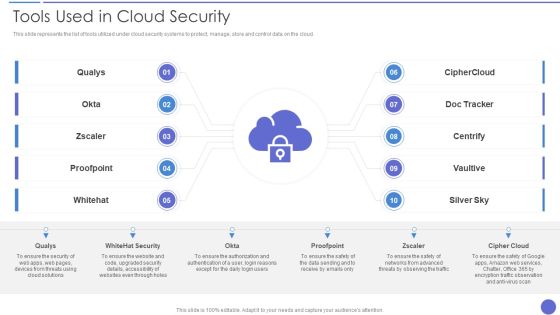
Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
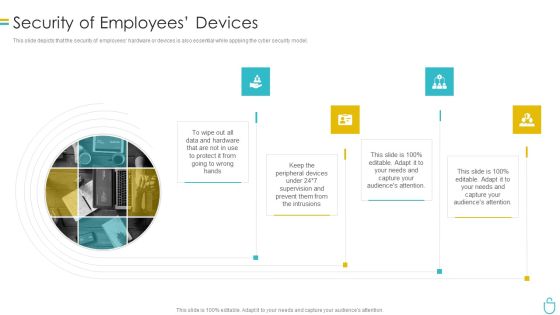
Information Security Security Of Employees Devices Ppt Model Infographics PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Presenting information security security of employees devices ppt model infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security of employees devices. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Features Of Zero Trust Network Access Security Model Sample PDF
This slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Explore a selection of the finest Features Of Zero Trust Network Access Security Model Sample PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Features Of Zero Trust Network Access Security Model Sample PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF
Following slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Deliver and pitch your topic in the best possible manner with this Info Safety And ISO 27001 Performance Indicators To Measure Information Security Sample PDF. Use them to share invaluable insights on Information Security Policy, Information Security Training, Asset Inventory and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Complete IT Security IT Implementation Checklist Ppt Diagrams PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Deliver an awe inspiring pitch with this creative complete it security it implementation checklist ppt diagrams pdf bundle. Topics like training, antivirus software, secure communications, access control measures, device security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Key Elements Of Computer Security Download PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a desktop security management key elements of computer security download pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like planning, information security, application security, network security, cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
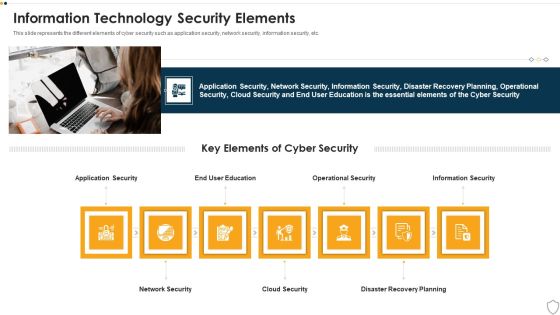
IT Security Information Technology Security Elements Ppt Images PDF
This slide represents the different elements of cyber security such as application security, network security, information security, etc. This is a it security information technology security elements ppt images pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application security, network security, cloud security, disaster recovery planning, operational security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Desktop Security Management Compliance Dashboard Of Computer Security Graphics PDF
This slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Deliver an awe inspiring pitch with this creative desktop security management compliance dashboard of computer security graphics pdf bundle. Topics like compliance dashboard of computer security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions.Presenting Cloud Security Assessment Types Of Cloud Security Solutions Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Categorization Of Services, Access Control, Data Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
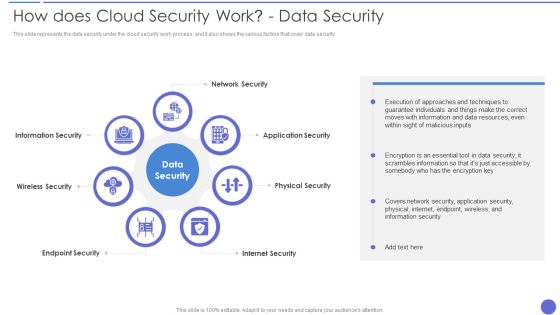
How Does Cloud Security Work Data Security Infographics PDF
This slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. This is a How Does Cloud Security Work Data Security Infographics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Application Security, Physical Security, Internet Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Presenting Cloud Security Assessment Essential Pillars Of Cloud Security Clipart PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Visibility And Consistency, Network Security, Identity Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Desktop Security Management Security Of Employees Devices Microsoft PDF
This slide depicts that the security of employees hardware or devices is also essential while applying the cyber security model. Deliver an awe inspiring pitch with this creative desktop security management security of employees devices microsoft pdf bundle. Topics like security of employees devices can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Security And Protection Security Mechanism Framework Background PDF
This slide showcases policies covered in data protection and information security. The policies includes are BYOD, system security, information rights, PCI DSS, network security, etc.Pitch your topic with ease and precision using this Data Security And Protection Security Mechanism Framework Background PDF. This layout presents information on Information Rights, Retention Policy, Details Processing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Agency Business Profile Additional Security Services Download PDF
This slide highlights the security company additional security services which includes safety escort service, executive protection and special event security. This is a Security Agency Business Profile Additional Security Services Download PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Safety Escort Service, Executive Protection, Special Event Security . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Pillars Of Cloud Security Network Security Rules PDF
This slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks. This is a Pillars Of Cloud Security Network Security Rules PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Secure, Network, Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF
This slide represents the architecture of the cloud security system and how data is organized and secured under a cloud system.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Architecture Of Cloud Security Cont Diagrams PDF bundle. Topics like Security And Monitoring, Recognize Services, Supporting Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Desktop Security Management Roadmap For Computer Security Training Graphics PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Presenting desktop security management roadmap for computer security training graphics pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like information, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizational Security Solutions Impact Of Effective Security Management Information PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative organizational security solutions impact of effective security management information pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
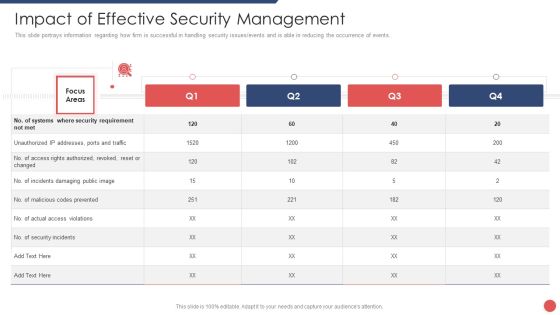
Security Functioning Centre Impact Of Effective Security Management Brochure PDF
This slide portrays information regarding how firm is successful in handling security issues events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative security functioning centre impact of effective security management brochure pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
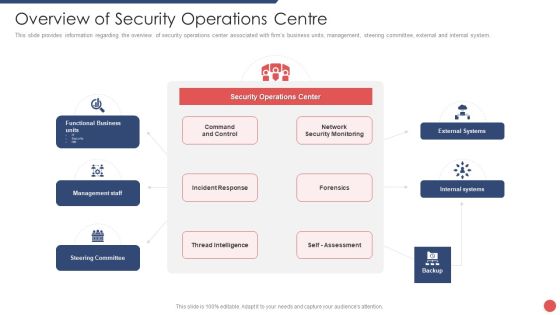
Security Functioning Centre Overview Of Security Operations Centre Summary PDF
This slide provides information regarding the overview of security operations center associated with firms business units, management, steering committee, external and internal system. Deliver and pitch your topic in the best possible manner with this security functioning centre overview of security operations centre summary pdf. Use them to share invaluable insights on management, thread intelligence, network security monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Pillars Of Cloud Security Process Based Security Information PDF
This slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take. This is a Pillars Of Cloud Security Process Based Security Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Vulnerability Management, Application, Security Requires. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Security Patches And Updates Summary PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting Cloud Security Checklist Security Patches And Updates Summary PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Security Patches, Measures, Organization. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

 Home
Home