Security Controls

CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Do you know about Slidesgeeks CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Risk Based Procedures To IT Security KPI Dashboard To Track Security Risk Events Designs PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this Risk Based Procedures To IT Security KPI Dashboard To Track Security Risk Events Designs PDF. Use them to share invaluable insights on Governance Risk, People Risk, Financial Risk and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
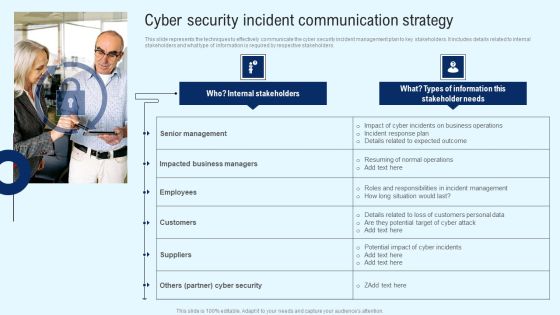
Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF
This slide represents the techniques to effectively communicate the cyber security incident management plan to key stakeholders. It includes details related to internal stakeholders and what type of information is required by respective stakeholders. This modern and well arranged Implementing Cyber Security Incident Cyber Security Incident Communication Strategy Diagrams PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

IT Security Information Technology Security Awareness Training For Staff Ppt Slide PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Presenting it security information technology security awareness training for staff ppt slide pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like senior executives, developers, front line staff, it teams, project managers. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
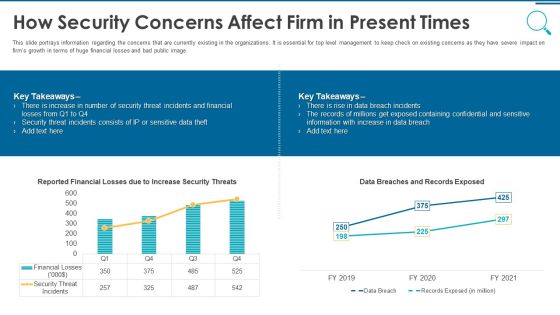
Information And Technology Security Operations How Security Concerns Affect Firm In Present Times Rules PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative information and technology security operations how security concerns affect firm in present times rules pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions How Security Concerns Affect Firm In Present Times Structure PDF
This slide portrays information regarding the concerns that are currently existing in the organizations. It is essential for top level management to keep check on existing concerns as they have severe impact on firms growth in terms of huge financial losses and bad public image. Deliver an awe inspiring pitch with this creative organizational security solutions how security concerns affect firm in present times structure pdf bundle. Topics like financial, containing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Identifying Information Security Threats And Impact On Organization Sample PDF bundle. Topics like Errors And Omissions, Fraud And Theft, Employee Sabotage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
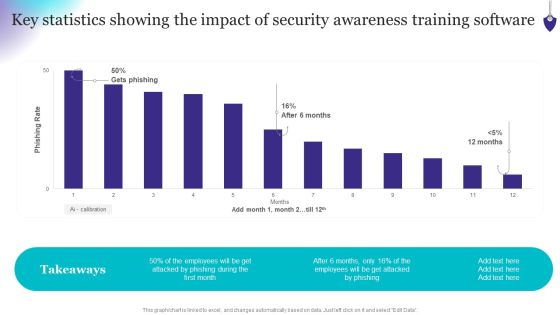
Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF
Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Organizing Security Awareness Key Statistics Showing The Impact Of Security Awareness Clipart PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
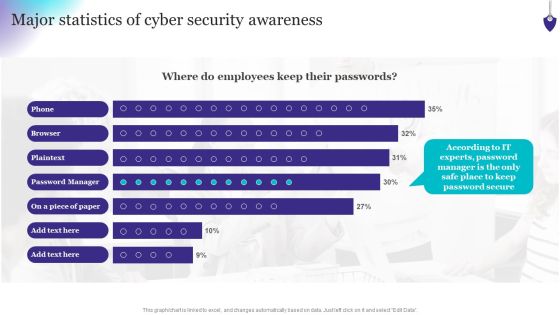
Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF
This graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Welcome to our selection of the Organizing Security Awareness Major Statistics Of Cyber Security Awareness Formats PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF
This slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Automation Framework Measure Security Automation Metrics For Operations Efficiency Formats PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Case Study On Security Improvement Through Security Operations Implementation Mockup PDF
This slide exhibits a case study of the SecOps application in a pharmaceutical company. It includes information about the firm, challenges, solutions, and benefits to a business. Persuade your audience using this Case Study On Security Improvement Through Security Operations Implementation Mockup PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Benefit To Business, Organisation Productivity, Average. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Welcome to our selection of the Implementing Cyber Security Incident Cyber Security Incident Response Plan Timeline Download PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
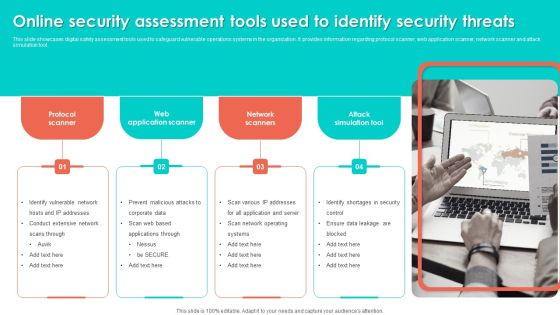
Online Security Assessment Tools Used To Identify Security Threats Slides PDF
This slide showcases digital safety assessment tools used to safeguard vulnerable operations systems in the organization. It provides information regarding protocol scanner, web application scanner, network scanner and attack simulation tool. Persuade your audience using this Online Security Assessment Tools Used To Identify Security Threats Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Scanners, Attack Simulation Tool, Web Application Scanner. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. This is a Cloud Information Security Cloud Security Threats Contract Breaches With Clients Background PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Information Could, Business Partners, Data Stored. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF
This slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download CYBER Security Breache Response Strategy Cyber Security Threats Detection Techniques Diagrams PDF from Slidegeeks and deliver a wonderful presentation.

Info Security Information security Awareness Training For Staff Ppt PowerPoint Presentation Gallery Template PDF
This slide represents the cybersecurity awareness training program for staff, including the name of the participants and what modules would be covered under training daily. Deliver and pitch your topic in the best possible manner with this info security information security awareness training for staff ppt powerpoint presentation gallery template pdf. Use them to share invaluable insights on senior executives, project managers, it teams, developers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Info Security How Is Automation Used In Information security Ppt PowerPoint Presentation Gallery Samples PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting info security how is automation used in information security ppt powerpoint presentation gallery samples pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Contract Breaches With Clients Cloud Computing Security IT Ppt Ideas Introduction PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting cloud security threats contract breaches with clients cloud computing security it ppt ideas introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, organization, sensitive data stored. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Presenting Cloud Security Assessment Cloud Security Threats Contract Breaches With Clients Professional PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Business Partners, Contract Breaches, Against The Organization In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing IT Security Strategy Rising Number Of Information Security Attacks Graphics PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes - malware, DoS attack, phishing and SQL injection. This modern and well-arranged Developing IT Security Strategy Rising Number Of Information Security Attacks Graphics PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.
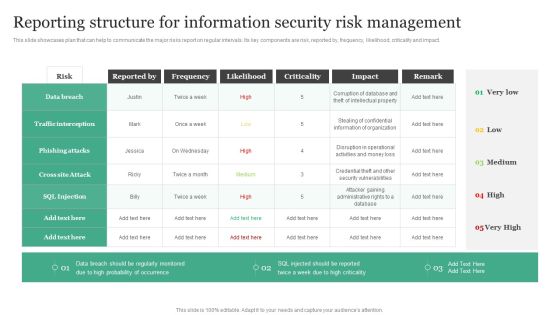
Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF
This slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact.Do you know about Slidesgeeks Reporting Structure For Information Security Risk Management Information Security Risk Administration Elements PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF
This slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan.This modern and well-arranged Kpis To Measure Information Security Risk Management Information Security Risk Administration Mockup PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Slidegeeks has constructed Asset Identification For Information Security Risk Management Information Security Risk Administration Information PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping-off point to explore our content and will give new users an insight into our top-notch PowerPoint Templates.

Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Slidegeeks is here to make your presentations a breeze with Deploying Cyber Security Incident Response Administration Cyber Security Systems Monitoring Report Microsoft PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help form to monitor the asset in real time for any data breach or cyber attack. Take your projects to the next level with our ultimate collection of Information Systems Security And Risk Management Plan Asset Identification For Information Security Risk Management Background PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Information Systems Security And Risk Management Plan Rising Number Of Information Security Attacks Information PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes - malware, DoS attack, phishing and SQL injection. Welcome to our selection of the Information Systems Security And Risk Management Plan Rising Number Of Information Security Attacks Information PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Developing IT Security Strategy Information Security Attacks Faced By Organization Rules PDF
This slide showcases most common information attacks faced by organization. It includes - malware, phishing, man in the middle attack, SQL injection, zero day exploit and DNS attack. Slidegeeks is here to make your presentations a breeze with Developing IT Security Strategy Information Security Attacks Faced By Organization Rules PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF
This slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Developing IT Security Strategy Asset Identification For Information Security Risk Professional PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Security Administration Strategy Security Ppt PowerPoint Presentation Complete Deck With Slides
Share a great deal of information on the topic by deploying this security administration strategy security ppt powerpoint presentation complete deck with slides. Support your ideas and thought process with this prefabricated set. It includes a set of twelve slides, all fully modifiable and editable. Each slide can be restructured and induced with the information and content of your choice. You can add or remove large content boxes as well, to make this PPT slideshow more personalized. Its high-quality graphics and visuals help in presenting a well-coordinated pitch. This PPT template is also a resourceful tool to take visual cues from and implement the best ideas to help your business grow and expand. The main attraction of this well-formulated deck is that everything is editable, giving you the freedom to adjust it to your liking and choice. Changes can be made in the background and theme as well to deliver an outstanding pitch. Therefore, click on the download button now to gain full access to this multifunctional set.
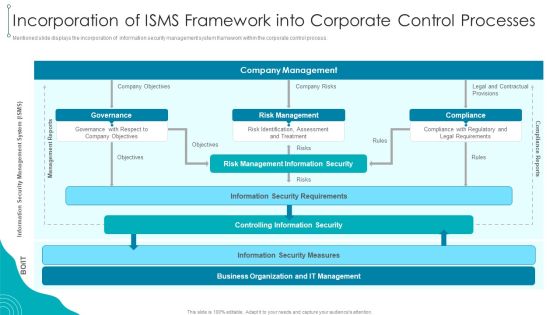
Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Download PDF. Use them to share invaluable insights on Management Information, Security Requirements, Information Security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Portable Home Safety Systems Company Profile Security Company Strategic Partnerships Structure PDF
This slide highlights the strategic partnership of the security company. It covers the major services such as voice control, mobile security application, and CCTV installation. Deliver and pitch your topic in the best possible manner with this Portable Home Safety Systems Company Profile Security Company Strategic Partnerships Structure PDF. Use them to share invaluable insights on Services, Partnership Type, Year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cybersecurity Risk Administration Plan Framework Ideas PDF
This slide showcases a cyber security risk management framework to increase system capability to protect, detect and react under uncertain security threats. It includes steps such as categorize system, select security control, apply security controls, evaluate security controls, etc. Presenting Cybersecurity Risk Administration Plan Framework Ideas PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Categorise System, Select Security Controls, Apply Security Controls. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Advantages Of Cloud Computing With Flexibility And Security Ppt PowerPoint Presentation Portfolio Format PDF
Presenting this set of slides with name advantages of cloud computing with flexibility and security ppt powerpoint presentation portfolio format pdf. This is a eight stage process. The stages in this process are flexibility, disaster recovery, automatic software updates, pay as you go, increased collaboration, document control, security, location independent. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
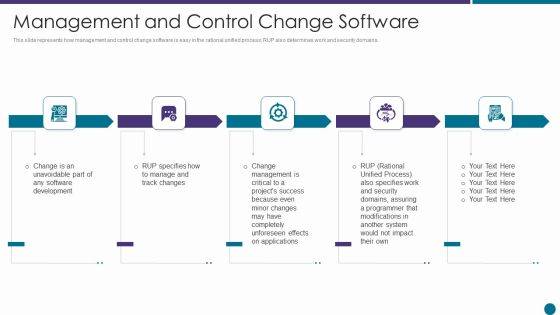
Management And Control Change Software Ppt Show Designs PDF
This slide represents how management and control change software is easy in the rational unified process RUP also determines work and security domains. Presenting management and control change software ppt show designs pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like management, applications, development, security, system. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
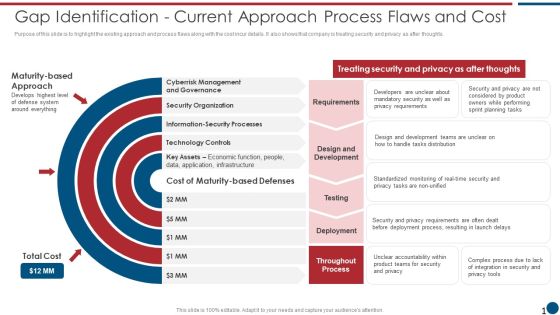
Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF
Purpose of this slide is to highlight the existing approach and process flaws along with the cost incur details. It also shows that company is treating security and privacy as after thoughts. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Gap Identification Current Approach Process Flaws And Cost Elements PDF bundle. Topics like Cyberrisk Management, Security Organization, Technology Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Incorporation Of ISMS Framework Into Corporate Control Processes Inspiration PDF
Mentioned slide displays the incorporation of information security management system framework within the corporate control process.Deliver and pitch your topic in the best possible manner with this Incorporation Of ISMS Framework Into Corporate Control Processes Inspiration PDF. Use them to share invaluable insights on Risk Management, Management Information, Controlling Information and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Operating Designs PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Center Infrastructure Management IT Checklist We Follow For Data Center Security Formats PDF
This slide depicts the best practices for data center security based including identity and control data, classify sensitive data, map data flows, define groups, periodic audits, and reviews and integrate devsecops. Deliver an awe inspiring pitch with this creative data center infrastructure management it checklist we follow for data center security formats pdf bundle. Topics like identity and control data, classify sensitive data, map data flows, define groups, periodic audits and reviews, integrate devsecops can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Advantages Of Cloud Computing With Better Operational Control Ppt PowerPoint Presentation Styles Samples PDF
Presenting this set of slides with name advantages of cloud computing with better operational control ppt powerpoint presentation styles samples pdf. This is a eight stage process. The stages in this process are agility to meet volatile business cycles, reorganizes it cost structure, agile application release cycles through devops, better operational control of the platform, elasticity to support demand consumption, cost reduction and improved cost predictability, facilitate access to enhanced capabilities, increased security and controls through automation. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
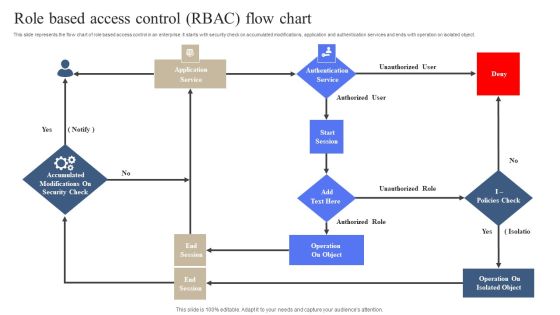
Role Based Access Control RBAC Flow Chart Slides PDF
This slide represents the flow chart of role based access control in an enterprise. It starts with security check on accumulated modifications, application and authentication services and ends with operation on isolated object. Persuade your audience using this Role Based Access Control RBAC Flow Chart Slides PDF. This PPT design covers One stage, thus making it a great tool to use. It also caters to a variety of topics including Operation On Object, Operation On Isolated Object. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Risk Dashboard With Current Risks And Security Service Formats PDF
The following slide focuses on the cyber threat dashboard which highlights current threats, current risks, regulation and policy coverage, security service and asset control issues. Pitch your topic with ease and precision using this cyber risk dashboard with current risks and security service formats pdf. This layout presents information on current threats, current risks, regulation and policy coverage. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
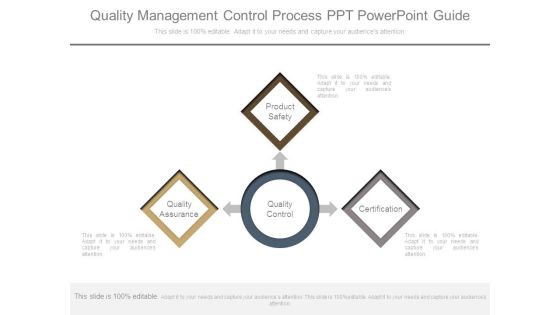
Quality Management Control Process Ppt Powerpoint Guide
This is a quality management control process ppt powerpoint guide. This is a three stage process. The stages in this process are quality control, product safety, certification, quality assurance, quality control.
Key Reasons For Significance Of Transformation Control Icons PDF
The following slide highlights reasons for signifying change control in IT systems aiming to ensure systematic approach for making configuration changes. It covers preventing unexpected downtime, security and documented systems. Presenting Key Reasons For Significance Of Transformation Control Icons PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Unexpected Downtime, Security, Documented Systems. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Information Management Process Control Ppt Slides
This is a information management process control ppt slide. This is a four stage process. The stages in this process are process improvement, facilities and safety, customer service, documents and records.

Key Elements Of Enterprise Control Structure PDF
This is a key elements of enterprise control structure pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like enterprise resource planning, environment and safety systems, asset management. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF
Purpose of this slide is to highlight the risk based approach and process efficiency along with the cost incur details. It also shows that company will develop agile security and privacy models. Deliver an awe inspiring pitch with this creative IT Security Risk Management Approach Introduction Embedding Risk Based Approach Into Product Information PDF bundle. Topics like Technology Controls, Information Security Processes, Security Organization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

National Security France PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Download our Success PowerPoint Templates because Our PowerPoint Templates and Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. Download and present our Business PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Use our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides help you meet the demand of the Market. Just browse and pick the slides that appeal to your intuitive senses. Present our Signs PowerPoint Templates because They will Put your wonderful verbal artistry on display. Our PowerPoint Templates and Slides will provide you the necessary glam and glitter.Use these PowerPoint slides for presentations relating to Key with french flag, security, success, business, shapes, signs. The prominent colors used in the PowerPoint template are Blue navy, White, Red. We assure you our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 will make the presenter successul in his career/life. Professionals tell us our security PowerPoint templates and PPT Slides will save the presenter time. We assure you our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 look good visually. The feedback we get is that our security PowerPoint templates and PPT Slides are incredible easy to use. Customers tell us our National Security France PowerPoint Templates PPT Backgrounds For Slides 0113 are designed to make your presentations professional. Customers tell us our french PowerPoint templates and PPT Slides provide great value for your money. Be assured of finding the best projection to highlight your words.

Image Of Internet Security PowerPoint Templates Ppt Backgrounds For Slides 0713
Highlight your drive with our Image Of Internet Security PowerPoint Templates PPT Backgrounds For Slides. Prove the fact that you have control. Go the distance with our Security PowerPoint Templates. Maintain the pace till the end. Draw on the energy of our Technology PowerPoint Templates. Your thoughts will perk up.

Upgrading Total Project Safety IT Determine Established Security Centre Overview Sample PDF
This slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. This is a upgrading total project safety it determine established security centre overview sample pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like incident response, forensics, threat intelligence, command and control, network security monitoring. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manufacturing Planning And Control For Business Template Presentation Slides
This is a Manufacturing Planning And Control For Business Template Presentation Slides. This is a six stage process. The stages in this process are master production schedule, aggregate production planning, strategic planning, material requirement planning, assembly, dispatch.

Security Training Program Frameworks Cont Ppt File Slideshow PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas.Deliver and pitch your topic in the best possible manner with this security training program frameworks cont ppt file slideshow pdf. Use them to share invaluable insights on implement strong access control measures, regularly monitor and test networks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver and pitch your topic in the best possible manner with this Information Technology Threat Mitigation Methods IT Security Residual Risk Matrix With Response Actions Mockup PDF. Use them to share invaluable insights on Database, Network, Application and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. The Retail Store Operations Strategies To Enhance Retail Store Security Pictures PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.

Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. This is a Retail Outlet Operational Efficiency Analytics Strategies To Enhance Retail Store Security Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Article Surveillance, Install Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF
This slide depicts the forwarding and control element separation methodology of SDN development and caters to the overview and deployment methods. It also includes the FORCES architecture, consisting of control and forwarding elements. Take your projects to the next level with our ultimate collection of SDN Security Architecture Methodologies For Developing SDN Forces Structure PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest

Multipoint Checklist To Improve Computer Security Guidelines PDF
This slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Showcasing this set of slides titled Multipoint Checklist To Improve Computer Security Guidelines PDF The topics addressed in these templates are Frequent System, Control Administrative, System Password All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Agency Business Profile Team Communication Layout Topics PDF
This slide highlights the security guard service company team communication layout which includes guard, supervisor, mobile response team ,customer relation officer and control room. Deliver and pitch your topic in the best possible manner with this Security Agency Business Profile Team Communication Layout Topics PDF. Use them to share invaluable insights on Customer Relationship Officer, Mobile Response Team, Supervisor and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Manpower Corporate Security Business Profile Team Communication Layout Icons PDF
This slide highlights the security guard service company team communication layout which includes guard, supervisor, mobile response team , customer relation officer and control room. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Team Communication Layout Icons PDF bundle. Topics like Customer Relationship Officer, Supervisor, Mobile Response Team can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Training Program Frameworks Ppt Outline Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this security training program frameworks ppt outline layout ideas pdf. Use them to share invaluable insights on requirements, metrics, systems security, materials and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
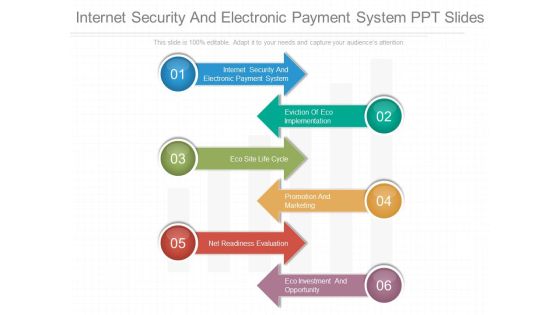
Internet Security And Electronic Payment System Ppt Slides
This is a internet security and electronic payment system ppt slides. This is a six stage process. The stages in this process are internet security and electronic payment system, eviction of eco implementation, eco site life cycle, promotion and marketing, net readiness evaluation, eco investment and opportunity.

Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF
This slide showcases startegies that can help organization to avoid information breach. Key strategies include impelment antivirus software, monitor network traffic, incident reponse plan, patch management schedule and establish network access controls .This is a Information Security Risk Evaluation Mitigation Strategies To Avoid Information Breach Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Management Schedule, Incident Response, Implement Antivirus . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF
This slide depicts the risk evaluation dashboard for data privacy based on audits with open findings, GDPR processing per region, control and measure trends, average response time. There are so many reasons you need a Information Security Risk Evaluation Dashboard For Data Privacy Introduction PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
Companys Data Safety Recognition Security Training Program Frameworks Icons PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative companys data safety recognition security training program frameworks icons pdf bundle. Topics like requirements, target audience, metrics, training materials can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Security Training Program Frameworks Mockup PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
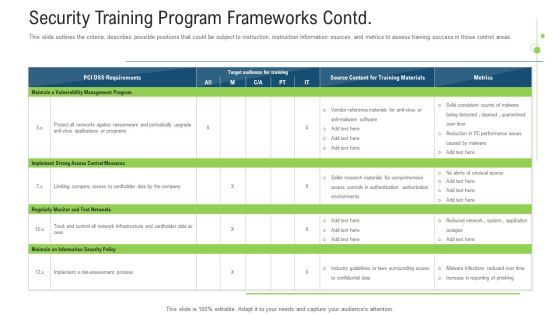
Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Machine To Machine Communication What Is Iot Security Portrait PDF
The slide highlights IoT session layer protocol.This is a machine to machine communication what is iot security portrait pdf. template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like database, command and control center. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
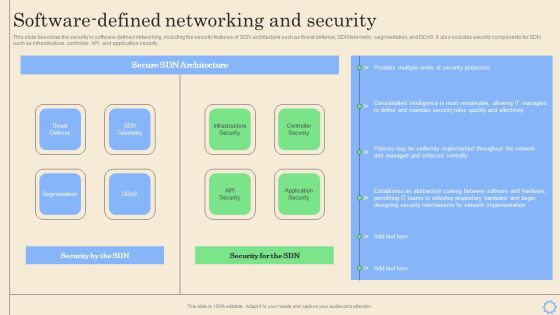
Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF
This slide describes the security in software-defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Want to ace your presentation in front of a live audience Our Software Defined Networking Development Strategies Software Defined Networking And Security Pictures PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Computer Security PowerPoint Templates And PowerPoint Themes 1012
Computer Security PowerPoint Templates And PowerPoint Themes 1012-With the move to high speed internet connection comes the greater possibility of your business being the target of an attack. One use of the term computer security refers to technology to implement a secure operating system. The Above Template will help you and your partners to understand the importance of Computer Security. Deliver amazing presentations to mesmerize your audience with our Security Template.-Computer Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Protect your computer, security, communication, computer, technology, background

Cyber Security Risk Management Framework For Threat Protection Demonstration PDF
This slide highlights the cyber security risk management framework which include third party risk management, IT risk assessment and security center operations. Presenting cyber security risk management framework for threat protection demonstration pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including cyber security governance, security assessment, independent audit. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Process Business PowerPoint Templates And PowerPoint Themes 0512
Microsoft Powerpoint Templates and Background with security process-Security Process Business PowerPoint Templates And PowerPoint Themes 0512-These PowerPoint designs and slide layouts can be used for themes relating to -Security process business, background, success, symbol, security, business

Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF
The following slide shows dashboard of CPM cyber security program management which helps to access high value assets and check threats , risks and policies on one platform. It includes current threat postures, risks, policy, service breakdown, assets by category and their control issues. Pitch your topic with ease and precision using this Cyber Security Program Management Dashboard With KPI Metrics Ideas PDF. This layout presents information on Cyber Security, Program Management Dashboard, Kpi Metrics. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Chain Security PowerPoint Templates And PowerPoint Themes 1012
Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template consists of an image of many linked chains connected to one circular green chain. This image represents the concept of security or steps of business strategies. This template also emphasize strong group between family, business etc. Present your views using our innovative slides and be assured of leaving a lasting impression. -Chain Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chains of design, communication, security, business, teamwork, industrial

Cyber Security Cloud Data Ppt PowerPoint Presentation Summary Graphics Download
This is a cyber security cloud data ppt powerpoint presentation summary graphics download. This is a five stage process. The stages in this process are business, lock, planning, strategy, marketing, security.

Home Security Systems PowerPoint Templates And PowerPoint Themes 1012
Home Security Systems PowerPoint Templates And PowerPoint Themes 1012-With these pre-designed chains you can visualize almost any type of concept, chronological process or steps of your strategies. This Targets the Security of Home, Business as illustrated by image. This Template points to the Chain Security which can be showed by alarm clock, dollars and house.-Home Security Systems PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Great For Home Security, Security, Business, Shapes, Symbol, Background
Icon For Information And Cyber Security Risk Management Themes PDF
Presenting icon for information and cyber security risk management themes pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including icon for information and cyber security risk management. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security Process Business PowerPoint Templates And PowerPoint Themes 0312
Microsoft Powerpoint Templates and Background with security process concept in business and technology

Chain Cross Security PowerPoint Templates And PowerPoint Themes 1012
Chain Cross Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint Template Targets the Security in Life, Business as shown above. This Template points to the Chain Security which signifies Team Work. It shows the number of chains crossed together to secure the family ,Business etc.-Chain Cross Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chain cross, security, business, chains, success, leadership

Encrypted Business Data Cyber Security Assessment Icon Professional PDF
Presenting Encrypted Business Data Cyber Security Assessment Icon Professional PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Manage Handy Backups, Incorporate Multi Layer Security, Train Employees, Invest In Protective Software. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Email Security Vector Icon Ppt PowerPoint Presentation Model Example Topics
Presenting this set of slides with name email security vector icon ppt powerpoint presentation model example topics. This is a four stage process. The stages in this process are email security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
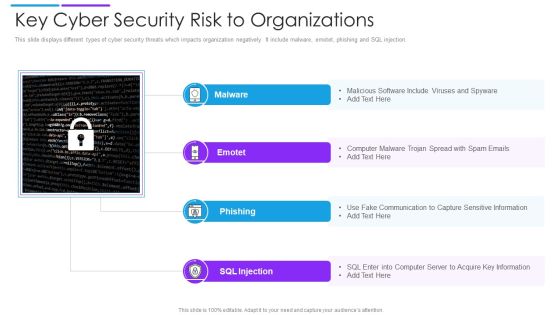
Key Cyber Security Risk To Organizations Structure PDF
This slide displays different types of cyber security threats which impacts organization negatively. It include malware, emotet, phishing and SQL injection. Presenting key cyber security risk to organizations structure pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including malware, phishing, sql injection. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Security Of Cloud Computing Ppt PowerPoint Presentation Inspiration Microsoft
This is a security of cloud computing ppt powerpoint presentation inspiration microsoft. This is a four stage process. The stages in this process are computer software, operating system, open source.

Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012
Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012-With these pre-designed chains you can visualize almost any type of concept, chronological process or steps of your strategies. This Targets the Security in Life, Business as shown above. This Template points to the Chain Security which signifies Team Work. It shows the number of chains crossed together to secure the family ,Business etc.-Chain Cross Business Security PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chain cross, security, business, chains, success, leadership

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
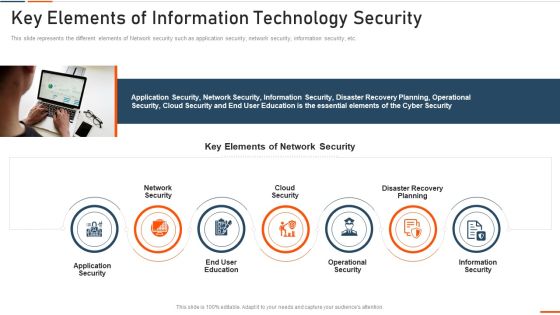
Key Elements Of Information Technology Security Ppt Styles Example PDF
This slide defines the meaning of network security and how it helps to prevent data through different methods and techniques. Presenting key elements of information technology security ppt styles example pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like approach, collective, methods, techniques, procedures, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security Process In Business PowerPoint Templates And PowerPoint Themes 0512
Security Process In Business PowerPoint Templates And PowerPoint Themes PPT designs-Microsoft Powerpoint Templates and Background with security process

Security Process Success PowerPoint Templates And PowerPoint Themes 0512
Security Process Success PowerPoint Templates And PowerPoint Themes PPT designs-Microsoft Powerpoint Templates and Background with security process

Privacy Security Ppt PowerPoint Presentation File Background Image
Presenting this set of slides with name privacy security ppt powerpoint presentation file background image. This is a four stage process. The stages in this process are business, management, planning, strategy, marketing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Email Security Market Research Report Industry Challenges Ppt Ideas PDF
Presenting this set of slides with name email security market research report industry challenges ppt ideas pdf. This is a five stage process. The stages in this process are threat of ransomware, threat of serverless apps, iot threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Chain Cross Security Leadreship PowerPoint Templates And PowerPoint Themes 1012
Chain Cross Security Leadership PowerPoint Templates And PowerPoint Themes 1012-Create stunning Microsoft office PPT Presentations with our professional templates containing a graphic of red ring connected with chains. This image has been professionally designed to emphasize the concept of strong group. It also depicts the concept of security. Our stunning image makes your presentations friendly and simpler showing that you care about even the smallest details.-Chain Cross Security Leadreship PowerPoint Templates And PowerPoint Themes 1012-This PowerPoint template can be used for presentations relating to-Chain cross, security, business, chains, success, leadership

National Security America PowerPoint Templates Ppt Backgrounds For Slides 1212
We present our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212.Use our Americana PowerPoint Templates because you have the plans ready for them to absorb and understand. Use our Security PowerPoint Templates because you can gain the success to desired levels in one go. Download our Success PowerPoint Templates because iT outlines the entire thought process for the benefit of others. Tell it to the world with your characteristic aplomb. Use our Business PowerPoint Templates because you have churned your mind and come upwith solutions. Present our Stars PowerPoint Templates because the Venn graphic comprising interlinking circles geometrically demonstate how various functions operating independantly, to a large extent, are essentially interdependant.Use these PowerPoint slides for presentations relating to National security america, business, security, success, americana, stars. The prominent colors used in the PowerPoint template are Red, White, Blue navy. Customers tell us our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 are Ultra. Presenters tell us our security PowerPoint templates and PPT Slides are Exuberant. Use our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 will get their audience's attention. PowerPoint presentation experts tell us our america PowerPoint templates and PPT Slides are Ultra. Customers tell us our National Security America PowerPoint Templates PPT Backgrounds For Slides 1212 will save the presenter time. Presenters tell us our stars PowerPoint templates and PPT Slides are Perfect.

Information Technology Security Prepare Data Backup Ppt Layouts Slides PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a information technology security prepare data backup ppt layouts slides pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect, information, manipulation, deletion, prevent . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Computer Enhanced Security System Ppt PowerPoint Presentation Show Structure
This is a computer enhanced security system ppt powerpoint presentation show structure. This is a three stage process. The stages in this process are access rights, access management, business.

Finance Saving Business Security PowerPoint Templates And PowerPoint Themes 1112
We present our Finance Saving Business Security PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because, This template with an image of helps you chart the course of your presentation. Use our Success PowerPoint Templates because,Break it all down to Key Result Areas. Use our Future PowerPoint Templates because, You have some exciting plans to spread goodwill among the underprivileged, Expound on your ideas and show to your colleagues how they can help others and in the process increase your Brand value. Use our Business PowerPoint Templates because, Expound on how you plan to gain their confidence and assure them of continued and consistent excellence in quality of service. Use our Finance PowerPoint Templates because, Watch their mental juices begin to flow.Use these PowerPoint slides for presentations relating to Piggy bank secured with padlock, success, future, security, business, finance. The prominent colors used in the PowerPoint template are Blue, Yellow, Black

Information Security Challenges Users Face In Data Privacy Sample PDF
This slide outlines the challenges users face in data privacy, including online tracking, losing control of data, lack of transparency, social media, and cybercrime. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Security Challenges Users Face In Data Privacy Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Security Challenges Users Face In Data Privacy Sample PDF.

Business Finance Security PowerPoint Templates And PowerPoint Themes 1112
We present our Business Finance Security PowerPoint Templates And PowerPoint Themes 1112.Use our Security PowerPoint Templates because,Explain the process by which you intend to right it. Use our Chains PowerPoint Templates because, Enlighten them with your brilliant understanding of mental health. Use our Money PowerPoint Templates because, Business Process Design:- The template offers an excellent background to build up the various stages of your business process. Use our Finance PowerPoint Templates because, They are logical, accurate and to the point. Use our Business PowerPoint Templates because, Brilliant ideas popping up all over the place.Use these PowerPoint slides for presentations relating to Dollars chained and locked, money, finance, business, security, chains . The prominent colors used in the PowerPoint template are Yellow, Black, White

Locked House Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113.Use our Secuity PowerPoint Templates because You should Ascend the ladder of success with ease. Our PowerPoint Templates and Slides will provide strong and sturdy steps. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will Activate the energies of your audience. Get their creative juices flowing with your words. Download and present our Real estate PowerPoint Templates because Your audience will believe you are the cats whiskers. Present our Business PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds. Present our Construction PowerPoint Templates because you should Whip up a frenzy with our PowerPoint Templates and Slides. They will fuel the excitement of your team.Use these PowerPoint slides for presentations relating to Key with house, security, success, real estate, business, construction. The prominent colors used in the PowerPoint template are Blue, White, Gray. We assure you our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our real PowerPoint templates and PPT Slides are second to none. Presenters tell us our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 effectively help you save your valuable time. Professionals tell us our real PowerPoint templates and PPT Slides are specially created by a professional team with vast experience. They diligently strive to come up with the right vehicle for your brilliant Ideas. The feedback we get is that our Locked House Security PowerPoint Templates PPT Backgrounds For Slides 0113 provide you with a vast range of viable options. Select the appropriate ones and just fill in your text. PowerPoint presentation experts tell us our success PowerPoint templates and PPT Slides will help them to explain complicated concepts.
Information Security Outsourcing Ppt PowerPoint Presentation Styles Outfit Cpb
This is a information security outsourcing ppt powerpoint presentation styles outfit cpb. This is a four stage process. The stages in this process are information security outsourcing, planning, business, management, marketing.

House Locked Security PowerPoint Templates Ppt Backgrounds For Slides 0313
We present our House Locked Security PowerPoint Templates PPT Backgrounds For Slides 0313.Present our Future PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Illuminate the road ahead to Pinpoint the important landmarks along the way. Download and present our Finance PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place. Download and present our Security PowerPoint Templates because You can Score a slam dunk with our PowerPoint Templates and Slides. Watch your audience hang onto your every word. Present our Money PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence.Use these PowerPoint slides for presentations relating to A key in a lock with house, security, future, business, finance, money. The prominent colors used in the PowerPoint template are Yellow, Brown, Green.

Winning Strategies To Improve Organization Data Security Pictures PDF
The following slide highlights a winning strategy to avoid data security breach in the organization. Businesses can protect the confidential data by following strategies such as security audit, establishing strong password, back up sensitive data, and improve cyber-security. Presenting Winning Strategies To Improve Organization Data Security Pictures PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Audit, Establish Strong, Sensitive Data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF
This slide outlines the overview of 51 percent attack in blockchain technology. The purpose of this slide is to showcase how malicious miners possess control over 51 percent of blockchain blocks, including a before and after use case. Retrieve professionally designed Blockchain Security Solutions Deployment Understanding 51 Percent Attack Sample PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You do not have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Computer Security Vector Icon Ppt PowerPoint Presentation File Outline PDF
Presenting this set of slides with name computer security vector icon ppt powerpoint presentation file outline pdf. This is a three stage process. The stages in this process are computer security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
System Security Vector Icon Ppt PowerPoint Presentation Model Templates
Presenting this set of slides with name system security vector icon ppt powerpoint presentation model templates. This is a four stage process. The stages in this process are system security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security System Image Ppt PowerPoint Presentation Styles Microsoft PDF
Presenting this set of slides with name cyber security system image ppt powerpoint presentation styles microsoft pdf. This is a three stage process. The stages in this process are cyber security system image. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart
With Our Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart Powerpoint Templates You Will Be Doubly Sure. They Possess That Stamp Of Authority. Our Security Powerpoint Templates Do It In Double Quick Time. Speed Up The Process In A Tangible Way.

Picture Of Cyber Security Background Ppt PowerPoint Presentation Layouts Layout
Presenting this set of slides with name picture of cyber security background ppt powerpoint presentation layouts layout. This is a one stage process. The stage in this process is picture of cyber security background. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Stock Photo Atm Card With Lock For Security PowerPoint Slide
This image slide contains graphics of ATM card with lock. You may use this image to depict safe, secure and easy way to manage your money. Accelerate the impact of your ideas with this image slide.

Security Real Estate Finance PowerPoint Templates And PowerPoint Themes 1112
Security Real Estate Finance PowerPoint Templates And PowerPoint Themes 1112-The above PowerPoint template displays a diagram of us money locked in a padlock with keys. Use this template for Business and Financial purposes. It signifies the concept of finance, profit, loss, money, economics, real estate, business, investment, funding etc. Present your views using our innovative slides and be assured of leaving a lasting impression.-Security Real Estate Finance PowerPoint Templates And PowerPoint Themes 1112-This PowerPoint template can be used for presentations relating to-House attached to key, Security, Money, Finance, Real estate, Marketing

Corporate Data Management And Privacy Security Mechanism Icon Slides PDF
Persuade your audience using this Corporate Data Management And Privacy Security Mechanism Icon Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Corporate Data, Management Privacy, Security Mechanism Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF
This slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcomethose challenges. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Traditional Perimeter Based Network Security Overview And Limitations Inspiration PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.
Emergency Procedures Security Ppt PowerPoint Presentation Icon Styles
Presenting this set of slides with name emergency procedures security ppt powerpoint presentation icon styles. This is a three stage process. The stages in this process are technology, marketing, planning, business, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Business Context Diagram 3d Man With Chain Security PowerPoint Slides
We present our business context diagram 3d man with chain security PowerPoint Slides.Download our Security PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will effectively help you save your valuable time. They are readymade to fit into any presentation structure. Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides are aesthetically designed to attract attention. We gaurantee that they will grab all the eyeballs you need. Use our Process and Flows PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will give good value for money. They also have respect for the value of your time.Use these PowerPoint slides for presentations relating to 3d, Business, Chain, Connect, Connection, Heavy, Industrial, Industry, Isolated, Link, Linked, Man, Metal, Power, Powerful, Protection, Secure, Steel, Strength, Support, Symbol, Teamwork, Weak, White. The prominent colors used in the PowerPoint template are Blue, Gray, Black. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. The feedback we get is that our Industry PowerPoint templates and PPT Slides are designed to make your presentations professional. Professionals tell us our business context diagram 3d man with chain security PowerPoint Slides are effectively colour coded to prioritise your plans They automatically highlight the sequence of events you desire. People tell us our Connection PowerPoint templates and PPT Slides are designed by professionals PowerPoint presentation experts tell us our business context diagram 3d man with chain security PowerPoint Slides look good visually. You can be sure our Industry PowerPoint templates and PPT Slides will make you look like a winner.

Cyber Security Vector Icon Ppt PowerPoint Presentation Inspiration
Presenting this set of slides with name cyber security vector icon ppt powerpoint presentation inspiration. This is a one stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Checking Security PowerPoint Templates And PowerPoint Backgrounds 0211
Microsoft PowerPoint Template and Background with the phone and cursor

Checking Security PowerPoint Themes And PowerPoint Slides 0211
Microsoft PowerPoint Theme and Slides with the phone and cursor

 Home
Home