Safety
Info Security Dashboard For Threat Tracking In Information Security Ppt PowerPoint Presentation File Example Introduction PDF
This slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Deliver an awe inspiring pitch with this creative info security dashboard for threat tracking in information security ppt powerpoint presentation file example introduction pdf bundle. Topics like threats by owners, risk by threats, threat report, monthly threat status, current risk status, threats based on role can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
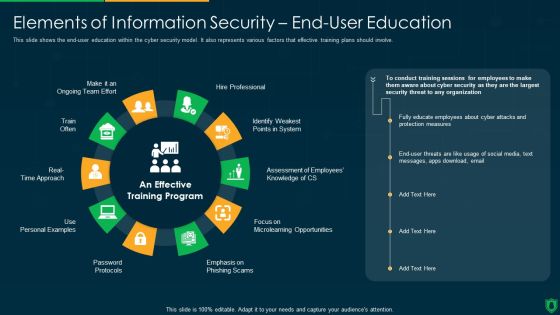
Info Security Elements Of Information Security End User Education Ppt PowerPoint Presentation File Example File PDF
This slide shows the end-user education within the cyber security model. It also represents various factors that effective training plans should involve. Presenting info security elements of information security end user education ppt powerpoint presentation file example file pdf to provide visual cues and insights. Share and navigate important information on ten stages that need your due attention. This template can be used to pitch topics like hire professional, emphasis on phishing scam, password protocols, train often. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
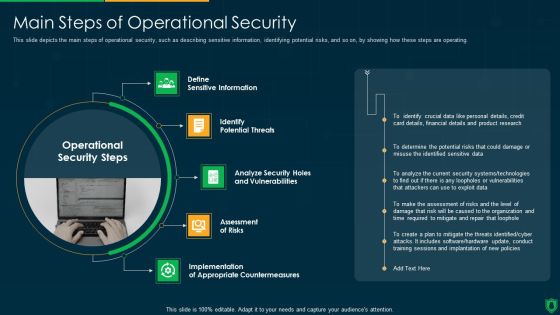
Info Security Main Steps Of Operational Security Ppt PowerPoint Presentation File Summary PDF
This slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. This is a info security main steps of operational security ppt powerpoint presentation file summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like define sensitive information, identify potential threats, assessment risks, implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Requirement Of Information Security In Different Sectors Ppt PowerPoint Presentation File Grid PDF
This slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an awe inspiring pitch with this creative info security requirement of information security in different sectors ppt powerpoint presentation file grid pdf bundle. Topics like cyber attacks, past 12 months, organizations transfer, sensitive data over internet can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
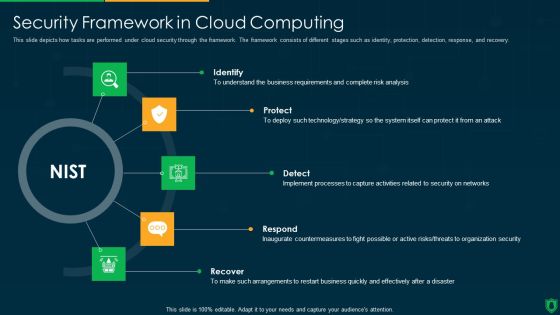
Info Security Security Framework In Cloud Computing Ppt PowerPoint Presentation Gallery Images PDF
This slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. This is a info security security framework in cloud computing ppt powerpoint presentation gallery images pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identify, protect, detect, respond, recover. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
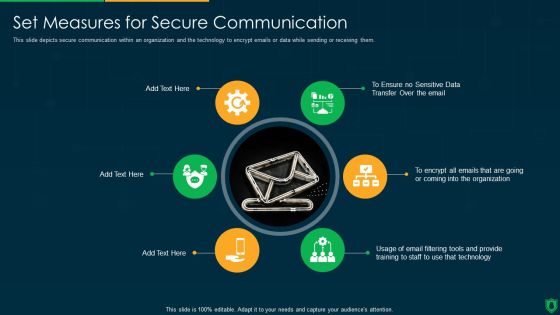
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Info Security Types Of Threats In Information Security Ppt PowerPoint Presentation Gallery Layout Ideas PDF
This slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Presenting info security types of threats in information security ppt powerpoint presentation gallery layout ideas pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like cyber crime, cyber terrorism, cyber attack. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
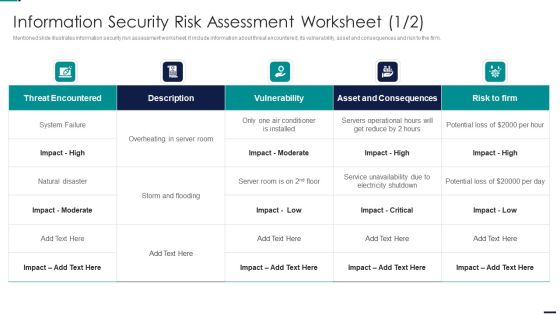
Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Deliver and pitch your topic in the best possible manner with this Information Security Risk Assessment Worksheet Risk Management Model For Data Security Designs PDF. Use them to share invaluable insights on Threat Encountered, Vulnerability, Asset And Consequences, Risk To Firm and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Model For Data Security Budget For Information Security Management Sample PDF
Mentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Budget For Information Security Management Sample PDF bundle. Topics like Functional Area, Training Duration, Risk Management, Incident Management, Asset Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF
This slide shows the categorization of information security threats. Categories covered are human error, natural disaster, software attacks and environmental control failures. Presenting Risk Management Model For Data Security Defining Categories Of Information Security Threats Graphics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Human Error, Natural Disaster, Deliberate Software Attacks, Environmental Control Failures. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
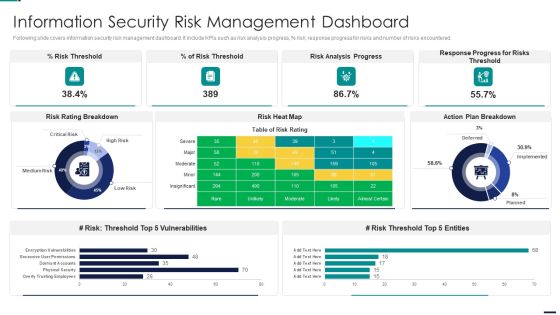
Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF
Following slide covers information security risk management dashboard. It include KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Information Security Risk Management Dashboard Pictures PDF bundle. Topics like Risk Threshold, Risk Analysis Progress, Response Progress For Risks Threshold, Action Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF
Following slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver and pitch your topic in the best possible manner with this Risk Management Model For Data Security Present Security Management Capabilities Of The Firm Elements PDF. Use them to share invaluable insights on Core Functions, Key Enablers, Required Standard Rating, Actual Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
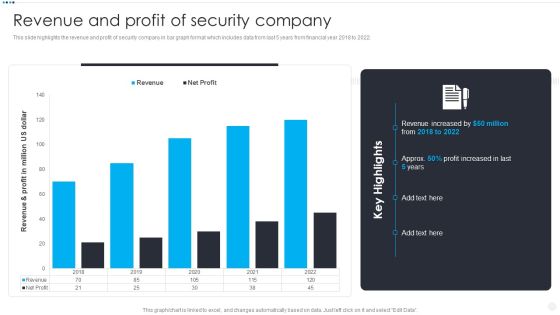
Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022. Deliver and pitch your topic in the best possible manner with this Smart Home Security Solutions Company Profile Revenue And Profit Of Security Company Elements PDF. Use them to share invaluable insights on Revenue And Profit, Million US Dollar, Revenue Increased Profit and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Smart Home Security Solutions Company Profile Security Company Business Model Infographics PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Security Company Business Model Infographics PDF bundle. Topics like Target Market Revenue, Stream Cost Structure, Customer Relationship Products, Customer Segments Key can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
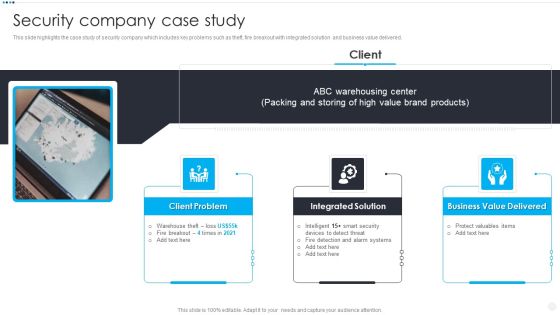
Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Presenting Smart Home Security Solutions Company Profile Security Company Case Study Brochure PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like High Value Brand, Client Problem Storing, Integrated Solution Warehousing, Business Value Delivered. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
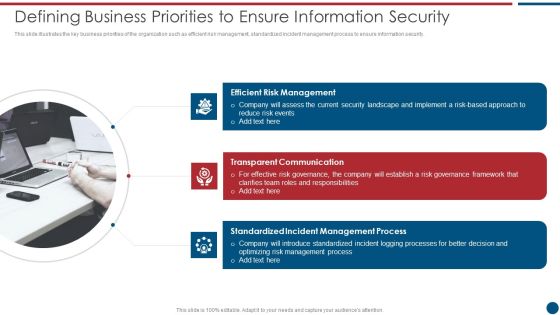
Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting Risk Based Procedures To IT Security Defining Business Priorities To Ensure Information Security Diagrams PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Risk Management, Transparent Communication, Standardized Incident. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
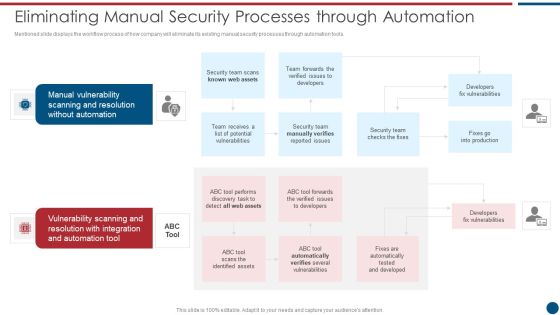
Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF
Mentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. This is a Risk Based Procedures To IT Security Eliminating Manual Security Processes Through Automation Information PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Manual Vulnerability, Vulnerability Scanning, Automation Tool. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF
Mentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. This is a Risk Based Procedures To IT Security Information Security Program Framework Key Components Themes PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Context Leadership, Evaluation Direction, Change Support. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF
Following slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Presenting Risk Based Procedures To IT Security Information Security Program Values To Business Infographics PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Detection Response, Attack Surface, Current Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a Cloud Information Security Cloud Security Checklist Data Encryption Ppt Summary Shapes PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Sensitive Data, Protect Keys, Data Servers. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Risks Or Threats Ppt Model Clipart PDF
This slide represents the list of threats or risks that can impact the security of a cloud, these risks include loss of intellectual property, compliance violations, malware attacks, and so on. Presenting Cloud Information Security Cloud Security Risks Or Threats Ppt Model Clipart PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Shared Vulnerabilities, Malware Attacks, Compliance Violations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF
This slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non-compliance state. This is a Cloud Information Security Cloud Security Threats Compliance Violations Ppt Slides Aids PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Risks Organizations, Data Business, Serious Repercussions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF
This slide represents the end-user threat in cloud security and how an organization needs to control user access and be aware of potential threats. This is a Cloud Information Security Cloud Security Threats End User Control Ppt Summary Ideas PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Customer List, Rival Organizations, Could Upload. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF
This slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss. This is a Cloud Information Security Cloud Security Threats Malware Attacks Ppt File Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Administrations, Cyber Criminals, Deploy Malware. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF
This slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan. Presenting Cloud Information Security Cloud Security Threats Revenue Losses Ppt Model Themes PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Cyber Threats, Organizations Could, Drastic Decrease. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. This is a Cloud Information Security How Does Cloud Security Work Governance Ppt Show Slide Portrait PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Owner Ship, Accessibility Knowledge, Data Governance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF
This slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Presenting Cloud Information Security How Does Cloud Security Work Legal Compliance Ppt Layouts Templates PDF to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like Regulations Transparency, Standards Policies, Requirements Governance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery. Presenting Cloud Information Security How To Manage Security In Cloud Ppt Ideas Example Topics PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Access Controls, Data Recovery, Data Masking. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Industries That Can Benefit From Cloud Security Ppt Summary Graphics PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds. This is a Cloud Information Security Industries That Can Benefit From Cloud Security Ppt Summary Graphics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automotive Education, Financial Healthcare, Insurance Production. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls. This is a Cloud Information Security Measures And Controls In Cloud Security Ppt Slides Graphic Images PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF
This slide shows the small and midsized business cloud security solutions, including multi-tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks. Presenting Cloud Information Security SMB Cloud Security Solutions Ppt Show Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Multi Tenant, Access Control, Information Division. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. This is a Cloud Information Security Tools Used In Cloud Security Ppt Diagram Lists PDF template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Solutions, Advanced Threats, Cipher Cloud. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Presenting Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Expanded Attack, Access Management, Complex Frameworks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Loss Control, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Information Security How Does Cloud Security Work Data Retention And Business Summary PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a Cloud Information Security How Does Cloud Security Work Data Retention And Business Summary PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Business Continuity, Recovery Strategies, Plan Development. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Presenting Cloud Information Security How Does Cloud Security Work Identity And Access Management IAM Formats PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Central Repository, Access Management, Authorization Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Risk Management Approach Introduction Defining Business Priorities To Ensure Information Security Microsoft PDF
This slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Presenting IT Security Risk Management Approach Introduction Defining Business Priorities To Ensure Information Security Microsoft PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Transparent Communication, Efficient Risk Management, Standardized Incident Management. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
IT Security Risk Management Approach Introduction Kpi Dashboard To Track Security Risk Events Icons PDF
This slide displays KPI dashboard that company will use to track multiple risk events. Metrics covered in the dashboard are residual risks by period and risk category by total risk rating. Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Kpi Dashboard To Track Security Risk Events Icons PDF. Use them to share invaluable insights on System Technology Risk, Governance Risk, Security Risk Events and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Presenting Cloud Security Assessment Cloud Security Checklist Logging And Monitoring Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Security Breaches, Access Sensitive, System Activities In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF
This slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.This is a Cloud Security Assessment Cloud Security Threats End User Control Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Rival Organizations, Cybercriminals, Contact Information. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Difference Between Cloud Security Solutions And Traditional IT Solutions Portrait PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses.Presenting Cloud Security Assessment Difference Between Cloud Security Solutions And Traditional IT Solutions Portrait PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Reduced Infrastructure, Resource Utilization, Diminished Opportunity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF
This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Presenting Cloud Security Assessment How Does Cloud Security Work Identity And Access Management IAM Background PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Accessibility, Knowledge, Technology. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF
This slide defines the process of data security management in the cloud system that includes firewalls, access controls, data masking, and data recovery.This is a Cloud Security Assessment How To Manage Security In Cloud Cont Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Firewalls, Access Controls, Data Masking You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Industries That Can Benefit From Cloud Security Topics PDF
This slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds.This is a Cloud Security Assessment Industries That Can Benefit From Cloud Security Topics PDF template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Automotive, Healthcare, Production You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF
This slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls.This is a Cloud Security Assessment Measures And Controls In Cloud Security Demonstration PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Preventive Control, Deterrent Control, Detective Control You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF
This slide highlights the revenue and profit of security company in bar graph format which includes data from last 5 years from financial year 2018 to 2022.Deliver and pitch your topic in the best possible manner with this Security And Surveillance Company Profile Revenue And Profit Of Security Company Microsoft PDF. Use them to share invaluable insights on Revenue Increased, Increased In Last, Key Highlights and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Surveillance Company Profile Security Company Case Study Demonstration PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. Presenting Security And Surveillance Company Profile Security Company Case Study Demonstration PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Client Problem, Integrated Solution, Business Value. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
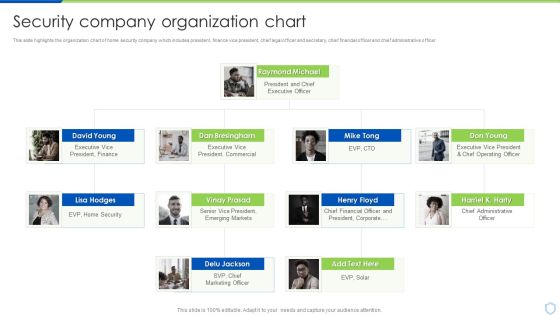
Security And Surveillance Company Profile Security Company Organization Chart Portrait PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. This is a Security And Surveillance Company Profile Security Company Organization Chart Portrait PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Raymond Michael, Executive President, Emerging Markets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Security Company Case Study Clipart PDF
This slide highlights the case study of security company which includes key problems such as theft, fire breakout with integrated solution and business value delivered. This is a Security Camera System Company Profile Security Company Case Study Clipart PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Integrated Solution, Value Delivered, Client Problem. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Camera System Company Profile Security Company Organization Chart Ideas PDF
This slide highlights the organization chart of home security company which includes president, finance vice president, chief legal officer and secretary, chief financial officer and chief administrative officer. Presenting Security Camera System Company Profile Security Company Organization Chart Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like President Finance, President And Chief, Executive Officer. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Current Information And Data Security Capabilities Of Firm Introduction PDF. Use them to share invaluable insights on Required Standard Rating Actual, Standard Rating and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF
This slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating,This is a Information Security Risk Evaluation Current Information Security Issues Faced By Organization Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Untrained Employees, Complex Risk, Management Policy . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF
This slide showcases capabilities of organization regarding information and data security after risk management plan. Its key components are risk management functions, required standard rating and actual standard rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Estimated Impact Of Information Security Risk Management Plan Microsoft PDF. Use them to share invaluable insights on Identification Assess, Protecting Safeguarding, Detect Threat and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF
This slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyze risks, evaluate and treat risks.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Framework For Information Security Risk Management Icons PDF. Use them to share invaluable insights on Establish The Context, Identify Risks, Analyze Risks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Identifying Employees For Information Security Training Programme Background PDF
This slide showcases plan that can help organization to conduct training for employees for information security risk management. It will enable employees to monitor risks and resolve them in timely manner.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Identifying Employees For Information Security Training Programme Background PDF. Use them to share invaluable insights on Threat Scanning, Malware Detection, Report Formulation and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF
This slide showcases dashboard that can help organization to track the major information security risks and resolve them in timely manner. Its key components are risk rating breakdown, heat map, action plan and top 5 vulnerabilities.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Risk Management Dashboard For Information Security Summary PDF. Use them to share invaluable insights on Rating Breakdown, Vulnerabilities, Response Progress and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Presenting IT Security Automation Tools Integration Security Processes That Cant Be Automated Background PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Threat Modeling, Penetration Testing, Bug Bounty. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF
This slide highlights the time to fix the security threat and error with manual testing in bar graph format. It covers key takeaways which explains how much percent of error are fixed in 1 to 3 hour, 3 to 6 hour and working day etc. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Time To Fix Security Threat With Manual Testing Template PDF. Use them to share invaluable insights on Manual Testing, Fix Error, 3 Working Days and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF
This slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. This is a IT Security Automation Tools Integration Why To Automate The IT Security Process Pictures PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Better Threat Detection, Faster Containment, Improve Productivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
 Home
Home