Safety Pyramid

Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF
Mentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Assessment Worksheet Asset Graphics PDF bundle. Topics like Conditioner Is Installed, Asset And Consequences, Electricity Shutdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF
Following slide covers information security risk management dashboard. It include kpis such as risk analysis progress, percent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative Cybersecurity Risk Administration Plan Information Security Risk Management Dashboard Summary PDF bundle. Topics like Risk Rating Breakdown, Action Plan Breakdown, Risk Analysis Progress can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
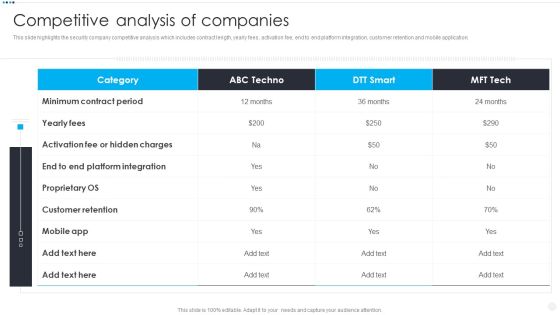
Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF
This slide highlights the security company competitive analysis which includes contract length, yearly fees, activation fee, end to end platform integration, customer retention and mobile application. Deliver an awe inspiring pitch with this creative Smart Home Security Solutions Company Profile Competitive Analysis Of Companies Ideas PDF bundle. Topics like Minimum Contract Period, Activation Fee Hidden, Customer Retention Mobile can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
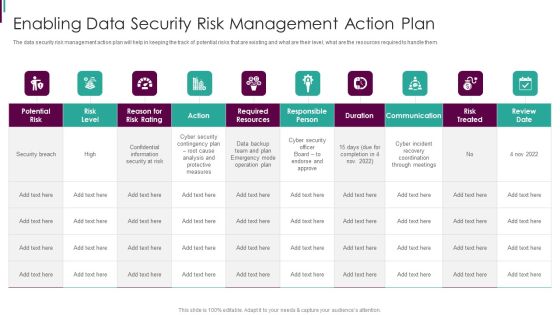
Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF
The data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an awe inspiring pitch with this creative Developing Business Analytics Framework Enabling Data Security Risk Management Elements PDF bundle. Topics like Required Resources, Responsible Person, Communication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Value Optimization Role Of Management In Effective Information Security Governance Ideas PDF bundle. Topics like Management Level, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF
This slide demonstrates the priority requirements of companies while buying IoT products. Strong cybersecurity is the topmost priority of companies followed by reliability and compatibility. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Determining The Priority Requirements For Buying Iot Products Rules PDF bundle. Topics like Cyber Security, Existing Enterprise, IoT products can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, percent risk, response progress for risks and number of risks encountered. Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation Dashboard For Information Security Risk Management Clipart PDF bundle. Topics like Risk Heat, Action Plan, Risk Rating Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Role Of Management In Effective Information Security Microsoft PDF bundle. Topics like Risk Management, Measuring Performance, Managing Resource can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF
This slide shows how an understanding of cloud utilization and risk is mandatory in cloud security and what factors it includes to take care of.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Phase1 Understand Cloud Utilization And Risk Professional PDF bundle. Topics like Shared And Accessed, Risk Assessment, Review Specifications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative CRM Solutions Implementation Strategy Implementation Add Roles And Enable Security Information PDF bundle. Topics like Restrictions By Enabling, Prevent Unauthorized, Double Authentication can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Clipart PDF bundle. Topics like Average, Tracks Networks, Applies Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Competitive Operations And Financials Designs PDF bundle. Topics like Employee Count, Recurring Revenue, Spending can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Paid Subscribers By Channel Background PDF bundle. Topics like Direct Channel, Subscribers In Last, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
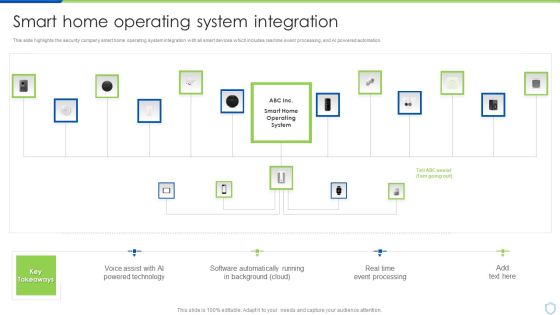
Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Smart Home Operating System Integration Clipart PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
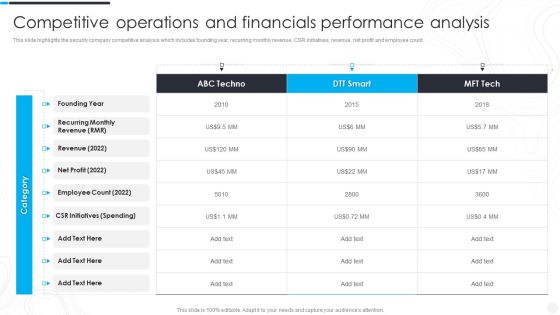
Security Camera System Company Profile Competitive Operations And Financials Slides PDF
This slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Competitive Operations And Financials Slides PDF bundle. Topics like Employee Count, Initiatives Spending, Revenue can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
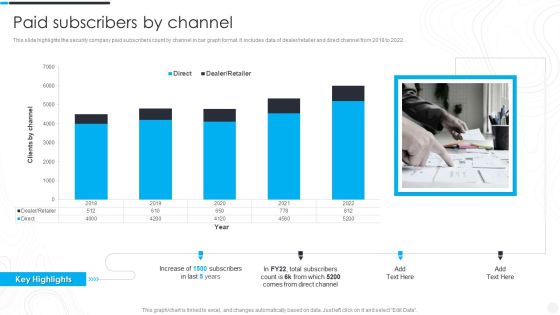
Security Camera System Company Profile Paid Subscribers By Channel Sample PDF
This slide highlights the security company paid subscribers count by channel in bar graph format. It includes data of dealer retailer and direct channel from 2018 to 2022. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Paid Subscribers By Channel Sample PDF bundle. Topics like Total Subscribers, Direct Channel, Key Highlights can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
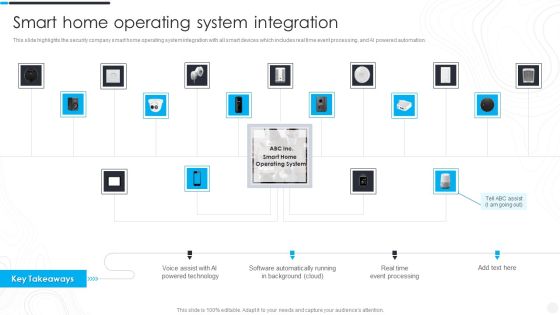
Security Camera System Company Profile Smart Home Operating System Integration Background PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Smart Home Operating System Integration Background PDF bundle. Topics like Powered Technology, Software Automatically, Event Processing can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Altered Business Practices Due To Hacking Structure PDF
This slide represents that hackers forced the company to alter business practices followed by years and shut down online shopping stores in some regions.Deliver an awe inspiring pitch with this creative IT Security Hacker Altered Business Practices Due To Hacking Structure PDF bundle. Topics like Stored Information, Personal Information, Social Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Sales CRM Cloud Solutions Deployment Implementation Add Roles And Enable Security Designs PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative Sales CRM Cloud Solutions Deployment Implementation Add Roles And Enable Security Designs PDF bundle. Topics like Restrictions By Enabling, Double Authentication, Prevent Unauthorized can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF
This slide displays dashboard for information security risk management. It includes KPIs such as risk analysis progress, persent risk, response progress for risks and number of risks encountered.Deliver an awe inspiring pitch with this creative ISO 27001 Certification Procedure Dashboard For Information Security Risk Management Sample PDF bundle. Topics like Vulnerabilities, Rating Breakdown, Plan Breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Cyber Attacks Faced By Different Departments Professional PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Cyber Attacks Faced By Different Departments Professional PDF bundle. Topics like Marketing Department, Operations Department, Accounts Department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF
Mentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases.Deliver an awe inspiring pitch with this creative IT Threats Response Playbook KPI Dashboard To Track Department Wise Security Incidents Brochure PDF bundle. Topics like It Department, Hr Department, Requires Immediate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Improved Digital Expenditure Role Of Management In Effective Information Security Governance Microsoft PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative Improved Digital Expenditure Role Of Management In Effective Information Security Governance Microsoft PDF bundle. Topics like Management Level, Board Directors, Senior Executives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF
This slide provides information regarding role of management in effective information security governance in strategic alignment , risk management, integration, value delivery, etc. Deliver an awe inspiring pitch with this creative IT Spend Management Priorities By Cios Role Of Management In Effective Information Security Governance Graphics PDF bundle. Topics like Senior Executives, Strategic Alignment, Risk Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
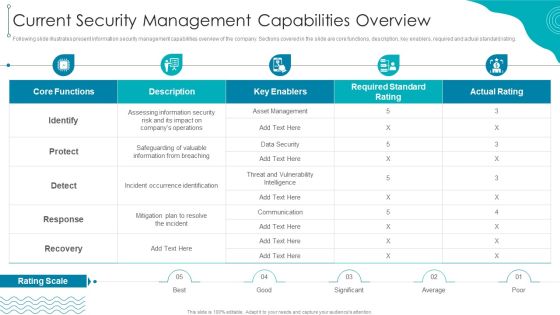
ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF
Following slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating.Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure Current Security Management Capabilities Overview Ideas PDF bundle. Topics like Occurrence Identification, Communication, Required Standard can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Agency Business Profile Government And Private Sector Clients Sample PDF
This slide highlights the security company clients from government and private sector which includes offices with location and industries with company name. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Government And Private Sector Clients Sample PDF bundle. Topics like Location, Industry can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF
This slide highlights the security company weapon and logistics vehicle details which includes repeater, MG16, doble cabin car, bullet proof vehicle, and patrolling vehicle. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Weapon And Logistics Vehicle Details Diagrams PDF bundle. Topics like Weapon, Logistics Vehicle Details can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF
This slide covers CISSP certification information about salary and job responsibilities and CISSP certification salary ranges by job etc. Deliver an awe inspiring pitch with this creative Certified Information Systems Security Professional CISSP Salary And Job Details Sample PDF bundle. Topics like Consumers, Implements Applications, Outlines Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
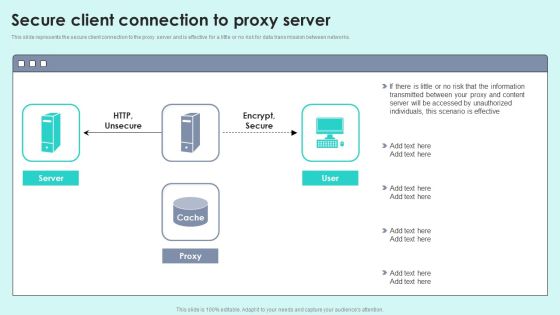
Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF
This slide represents the secure client connection to the proxy server and is effective for a little or no risk for data transmission between networks.Deliver an awe inspiring pitch with this creative Secure Client Connection To Proxy Server Reverse Proxy For Load Balancing Portrait PDF bundle. Topics like Transmitted Between, Accessed Unauthorized, Scenario Effective can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Government And Private Sector Clients Sample PDF
This slide highlights the security company clients from government and private sector which includes offices with location and industries with company name. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Government And Private Sector Clients Sample PDF bundle. Topics like Industry, Location, Treasure Office can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Manpower Corporate Security Business Profile Staff Recruiting Criteria And Training Centre Sample PDF
This slide highlights the security guard company staff recruiting criteria which includes age, medical category, height, records verification with authorized training centre. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Staff Recruiting Criteria And Training Centre Sample PDF bundle. Topics like Selection Criteria, Authorized Training Centre can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
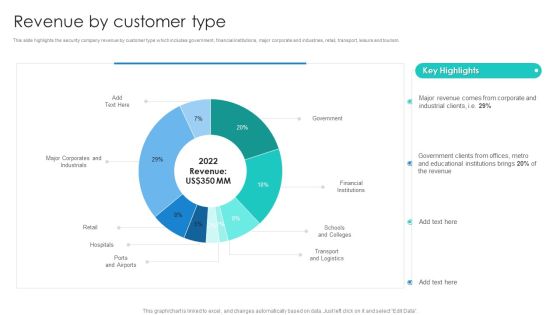
Manpower Corporate Security Business Profile Revenue By Customer Type Download PDF
This slide highlights the security company revenue by customer type which includes government, financial institutions, major corporate and industries, retail, transport, leisure and tourism. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Revenue By Customer Type Download PDF bundle. Topics like Revenue, Financial Institutions, Transport And Logistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Analyzing Budget For Effective Mobile Device Management Mobile Device Security Management Sample PDF
Firm has prepared a budget for managing mobile device security by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an awe inspiring pitch with this creative Analyzing Budget For Effective Mobile Device Management Mobile Device Security Management Sample PDF bundle. Topics like Risk Management, Document Management, Information Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.Deliver an awe inspiring pitch with this creative Strategies To Enhance Retail Store Security Retail Outlet Performance Assessment Professional PDF bundle. Topics like Integrate Access, Control Technology, Prevent Shoplifting can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF
This slide represents the security strategic planning process for CPS, including business strategy, technology roadmap, vision statement environment trends, current state assessment, and so on. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System Security Strategic Planning Process For CPS Icons PDF bundle. Topics like Gap Analysis, Environmental Trends, Business Strategy can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Intelligent Computing System CPS Security And Privacy Life Cycle Slides PDF
This slide depicts the cyber physical systems security and privacy life cycle, including its phases from 1 to 6, along with the tasks performed in each phase. Deliver an awe inspiring pitch with this creative Cyber Intelligent Computing System CPS Security And Privacy Life Cycle Slides PDF bundle. Topics like Management, Analysis, Required can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
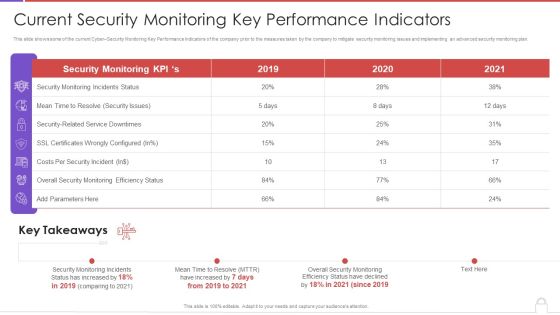
Methods To Develop Advanced Current Security Monitoring Key Performance Indicators Formats PDF
This slide shows some of the current Cyber Security Monitoring Key Performance Indicators of the company prior to the measures taken by the company to mitigate security monitoring issues and implementing an advanced security monitoring plan. Deliver an awe inspiring pitch with this creative methods to develop advanced current security monitoring key performance indicators formats pdf bundle. Topics like monitoring incidents status, security issues, costs per security incident, 2019 to 2020 can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
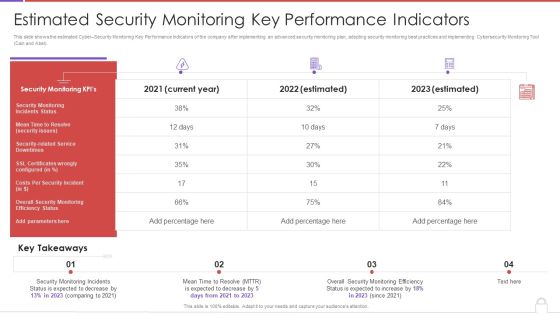
Methods To Develop Advanced Estimated Security Monitoring Key Performance Indicators Structure PDF
This slide shows the estimated Cyber Security Monitoring Key Performance Indicators of the company after implementing an advanced security monitoring plan, adopting security monitoring best practices and implementing Cybersecurity Monitoring Tool Cain and Abel. Deliver an awe inspiring pitch with this creative methods to develop advanced estimated security monitoring key performance indicators structure pdf bundle. Topics like security monitoring kpis, costs per security incident can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Impact Of Security Awareness Training Sample PDF
This slide covers the good impact of security awareness program such as declining in the number of security threats which are phishing, network intrusion, inadvertent disclosure, stolen or lost devices or records and system misconfiguration. Deliver an awe-inspiring pitch with this creative data breach prevention recognition impact of security awareness training sample pdf bundle. Topics like security awareness program, security threats, network intrusion, inadvertent disclosure, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
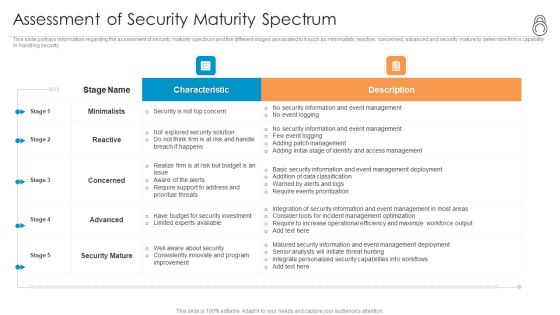
Enhanced Protection Corporate Event Administration Assessment Of Security Maturity Spectrum Background PDF
This slide portrays information regarding the assessment of security maturity spectrum and the different stages associated to it such as minimalists, reactive, concerned, advanced and security mature to determine firms capability in handling security. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration assessment of security maturity spectrum background pdf bundle. Topics like minimalists, reactive, concerned, advanced, security mature can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Electoral Mechanism IT Voting System Standards Security Ppt Professional Sample PDF
This slide represents the security standard of the voting system that ensures the security of voting machines to prevent them from being tempered or manipulated through physical security, auditability, and internet connection. Deliver an awe inspiring pitch with this creative electoral mechanism it voting system standards security ppt professional sample pdf bundle. Topics like physical security of equipment and ballots, auditability, internet connection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Professional PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach professional pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Employee Security Awareness Training Budget Graphics PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe-inspiring pitch with this creative data breach prevention recognition employee security awareness training budget graphics pdf bundle. Topics like budget, capability level, renew, duration, qualification can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition Security Training Program Frameworks Contd Template PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative data breach prevention recognition security training program frameworks contd template pdf bundle. Topics like measures, instruction information sources, target audience can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Information PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach information pdf bundle. Topics like phishing breakdown, network intrusion breakdown, system misconfiguration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Awareness Staff Learning Security Training Program Frameworks Contd Formats PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe-inspiring pitch with this creative organizational network awareness staff learning security training program frameworks contd formats pdf bundle. Topics like target audience for training, source content, metrics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Case Competition Overpower The Obstacle Of Cyber Security In Medicare Table Of Contents Guidelines PDF
Deliver an awe inspiring pitch with this creative case competition overpower the obstacle of cyber security in medicare table of contents guidelines pdf bundle. Topics like swot analysis of abs healthcare company, abs healthcare company competitive analysis, abs healthcare company challenges and their solutions can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Detail Impact Security Awareness Training Can Reduce The Risk Of A Data Breach Icons PDF
This slide covers the impact of data breaching threats such as phishing breakdown, network intrusion breakdown, system misconfiguration, stolen or lost devices or records and inadvertent disclosure. Deliver an awe-inspiring pitch with this creative detail impact security awareness training can reduce the risk of a data breach icons pdf bundle. Topics like phishing breakdown, network intrusion breakdown can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Security Solutions Analysing Various Threats Faced By Firm Professional PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative organizational security solutions analysing various threats faced by firm professional pdf bundle. Topics like threats, negligent, occurrence, compromised, malicious can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Analyzing Various Threats Faced By Firm Introduction PDF
This slide portrays information regarding the various threats that are faced by firm at present times with their cause of threat, risks associated to threats, occurrence of threats, and monetary loss to firm. Deliver an awe inspiring pitch with this creative security functioning centre analyzing various threats faced by firm introduction pdf bundle. Topics like threats, operations, compromised can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Functioning Centre Essential Roles And Responsibilities Involved In Secops Diagrams PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver an awe inspiring pitch with this creative security functioning centre essential roles and responsibilities involved in secops diagrams pdf bundle. Topics like project management skills, communication skills, prioritization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
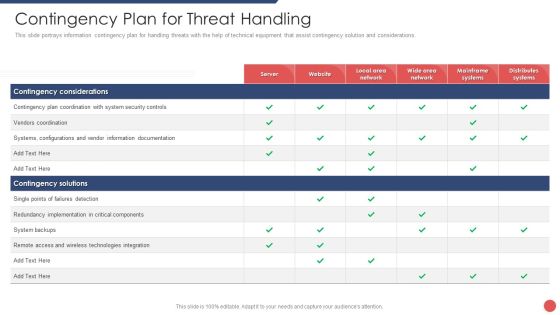
Security Functioning Centre Contingency Plan For Threat Handling Ppt Layouts Outline PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative security functioning centre contingency plan for threat handling ppt layouts outline pdf bundle. Topics like technologies integration, server, distributes systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Case Study 2 Banks Cyber Security Infrastructure Ppt Pictures Example PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges Deliver an awe inspiring pitch with this creative case study 2 banks cyber security infrastructure ppt pictures example pdf bundle. Topics like implemented, integrated, approach can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Auditing Committees For Food Quality Review Food Security Excellence Ppt Summary Example Topics PDF
This slide provides information regarding the different committees such as steering committees, general assembly meet, will review overall quality. Deliver an awe inspiring pitch with this creative auditing committees for food quality review food security excellence ppt summary example topics pdf bundle. Topics like acceptance criteria, quality audit review, corrective actions, quality document control, prepared quality control can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Final Food Product Quality Control Checklist Food Security Excellence Ppt Portfolio Layout Ideas PDF
This slide provides information regarding the food quality control checklist which will be filled by project supervisor for quality controllable assessment. Deliver an awe inspiring pitch with this creative final food product quality control checklist food security excellence ppt portfolio layout ideas pdf bundle. Topics like improvement, malfunctioning, sanitation, quality indicators can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
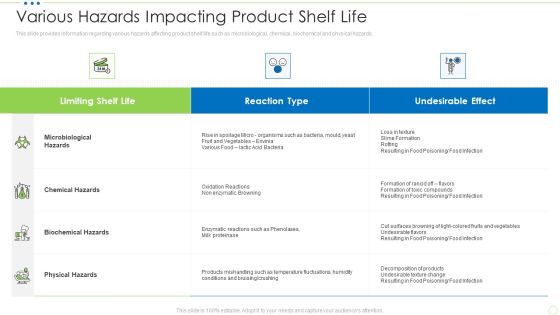
Various Hazards Impacting Product Shelf Life Food Security Excellence Ppt Professional Slide PDF
This slide provides information regarding various hazards affecting product shelf life such as microbiological, chemical, biochemical and physical hazards. Deliver an awe inspiring pitch with this creative various hazards impacting product shelf life food security excellence ppt professional slide pdf bundle. Topics like microbiological hazards, chemical hazards, biochemical hazards, physical hazards can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Addressing Hazard Analysis In Different Focus Areas Food Security Excellence Ppt Infographics Slides PDF
This slide provides information regarding addressing hazard analysis in different focus areas such as ingredients, facility design, equipment design, etc. Deliver an awe inspiring pitch with this creative addressing hazard analysis in different focus areas food security excellence ppt infographics slides pdf bundle. Topics like ingredients, processing procedure, facility design, equipment design and usage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Addressing Processed Food Quality Control Tools Food Security Excellence Ppt Infographics Show PDF
This slide provides information regarding the quality control tools such as ingredient specification and product standards. Deliver an awe inspiring pitch with this creative addressing processed food quality control tools food security excellence ppt infographics show pdf bundle. Topics like microbiological standards, chemical characteristics, physical characteristics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Analyzing Quality Related Concerns Associated To Food Product Food Security Excellence Ppt Infographic Template Picture PDF
This slide provides information regarding the key concerns faced by firm in terms of defects in produced food, decrease in net profit margin, etc. Deliver an awe inspiring pitch with this creative analyzing quality related concerns associated to food product food security excellence ppt infographic template picture pdf bundle. Topics like management, process, net profit margin can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Food Process Tracking With Control Chart Food Security Excellence Ppt Inspiration Graphics Example PDF
The quality team will use control chart as food quality management tool. It will help in determining the food processes are stable and capable under provided conditions. Deliver an awe inspiring pitch with this creative food process tracking with control chart food security excellence ppt inspiration graphics example pdf bundle. Topics like action plan, resources, chart analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home