Safety Pyramid

Environments Best Suited For Efficient And Secure Supply Chains Information PDF
Deliver an awe inspiring pitch with this creative environments best suited for efficient and secure supply chains information pdf bundle. Topics like environments best suited for efficient and secure supply chains can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Dashboard With Downtime Issues And Unsolved Tickets Introduction PDF
Deliver an awe inspiring pitch with this creative Security management dashboard with downtime issues and unsolved tickets introduction pdf bundle. Topics like security management dashboard with downtime issues and unsolved tickets can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Management Plan Steps In Detail Remote Access Control Inspiration PDF
Deliver an awe inspiring pitch with this creative security management plan steps in detail remote access control inspiration pdf bundle. Topics like deploying remote access, provides a secure connection, requirement for additional can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
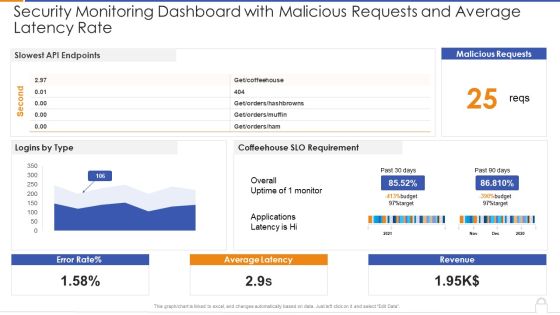
Security Monitoring Dashboard With Malicious Requests And Average Latency Rate Introduction PDF
Deliver an awe inspiring pitch with this creative security monitoring dashboard with malicious requests and average latency rate introduction pdf bundle. Topics like security monitoring dashboard with malicious requests and average latency rate can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Developing Firm Security Strategy Plan Information PDF
Deliver an awe inspiring pitch with this creative table of contents for developing firm security strategy plan information pdf bundle. Topics like implementing, security, management, corporate, governance can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Risk Scorecard Information Security Companies Risk Coverage Scorecard Icons PDF
Deliver an awe inspiring pitch with this creative cybersecurity risk scorecard information security companies risk coverage scorecard icons pdf bundle. Topics like hacker protection, network security, cubit score can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Continuous Development Evaluation Plan Eliminate Cyber Attacks Security Monitoring Dashboard Operating Designs PDF
Deliver an awe inspiring pitch with this creative continuous development evaluation plan eliminate cyber attacks security monitoring dashboard operating designs pdf bundle. Topics like security monitoring dashboard with application control and operating system statistics can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF
Deliver an awe inspiring pitch with this creative Effective Digital Marketing Audit Process IT Security Audit With Risk Level Introduction PDF bundle. Topics like Inactive Computer, Administrative Permissions, Security Groups can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Process Of Seo Based Web Analysis Ppt Powerpoint Shapes
This is a process of seo based web analysis ppt powerpoint shapes. This is a eight stage process. The stages in this process are testing, usability, security, trustability, heading, ranking, navigation, layout, process of seo.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Plan Topics PDF
This slide provides information about the second step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Aligning the Incident Management Policies and Plan. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring plan topics pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail aligning the incident management policies and plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Modern Security Observation Plan To Eradicate Cybersecurity Risk And Data Breach Cybersecurity Monitoring Introduction PDF
This slide provides information about the fifth step in cybersecurity monitoring plan that must be implemented by the company and security monitoring manager in order to solve issues such as malware attacks, pnishing, ransomware, supply chain attacks etc. i.e. Fine Tune Monitoring System. This is a modern security observation plan to eradicate cybersecurity risk and data breach cybersecurity monitoring introduction pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cybersecurity monitoring plan steps in detail fine tune monitoring system. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF
Purpose of this slide is to address and perform various cyber training exercises in order to secure companys assets. Exercises covered are defense in depth, capture the flag etc. Retrieve professionally designed Cyber Risks And Incident Response Playbook Performing Cyber Training Exercises For Securing The Assets Mockup PDF to effectively convey your message and captivate your listeners. Save time by selecting pre-made slideshows that are appropriate for various topics, from business to educational purposes. These themes come in many different styles, from creative to corporate, and all of them are easily adjustable and can be edited quickly. Access them as PowerPoint templates or as Google Slides themes. You dont have to go on a hunt for the perfect presentation because Slidegeeks got you covered from everywhere.

Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Deploying Corporate Aligned IT Strategy Dashboard To Track IT Security Incidents Prevailing Across Firm Designs PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Slidegeeks is here to make your presentations a breeze with Dashboard To Track IT Security Incidents Prevailing Across Firm Ppt PowerPoint Presentation File Outline PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF
This slide highlights the total patents granted to company in 2022 in multiple categories of IT, which includes AL and ML. cloud services, network design, cyber security and others. It also depicts historical patent trend with key insights. Deliver an awe inspiring pitch with this creative Infotech Solutions Research And Development Company Summary Company Patent Grants Icons PDF bundle. Topics like Network Design, Cyber Security, Cloud Services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
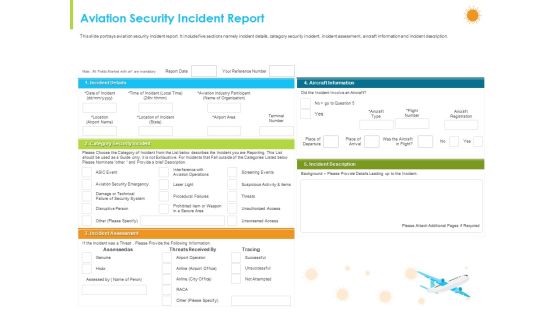
How Aviation Industry Coping With COVID 19 Pandemic Aviation Security Incident Report Template PDF
This slide portrays aviation security incident report. It include five sections namely incident details, category security incident, incident assessment, aircraft information and incident description.Deliver an awe inspiring pitch with this creative how aviation industry coping with COVID 19 pandemic aviation security incident report template pdf. bundle. Topics like suspicious activity and items, aircraft information, category security incident, incident assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Intelligent Architecture Growing Cyber Security Issues Ppt Professional Design Templates PDF
The slide provides the major cyber security issues Unprecedented Attacks, Cyber Espionage, and Data Theft along with the split of total information security incidents by the type of incident Deliver an awe inspiring pitch with this creative intelligent architecture growing cyber security issues ppt professional design templates pdf bundle. Topics like organizations, cyber security, business can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
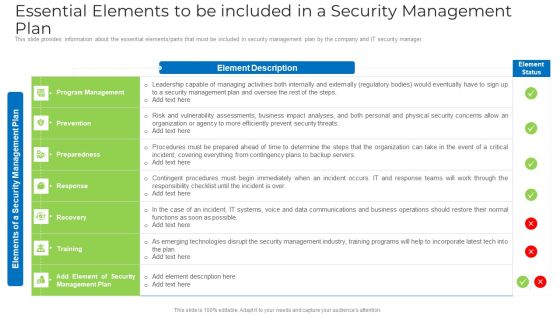
Essential Elements To Be Included In A Security Management Plan Elements PDF
This slide provides information about the essential elements or parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan elements pdf bundle. Topics like risk, organization, security, systems, data communications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Methods To Develop Measures And Ways To Mitigate Security Monitoring Challenges Background PDF
This slide provides information about the ways and measures through which the company and security monitoring managers can overcome the problems and issues related to Security Monitoring. Deliver an awe inspiring pitch with this creative methods to develop measures and ways to mitigate security monitoring challenges background pdf bundle. Topics like security monitoring challenges, employee management, malware attacks can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Securing Our Data With CRM Designing And Deployment Ppt PowerPoint Presentation Icon Example File PDF
This slide highlights the data security using CRM which incorporates IP restriction, two factor authentication, data storage, communication protection and data security. Deliver an awe inspiring pitch with this creative securing our data with crm designing and deployment ppt powerpoint presentation icon example file pdf bundle. Topics like crm data security, ip restriction, data storage and failover, communication protection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF
This slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses. Deliver an awe inspiring pitch with this creative Difference Between Cloud Security Solutions And Traditional It Solutions Pictures PDF bundle. Topics like Traditional It Security, Cloud Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF
This slide showcases responsibilities of major employees involved in information security risk management team. Key roles are information security manager, risk management officer and chief information officer.Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Roles And Responsibilities Of Risk Management Team Structure PDF bundle. Topics like Information Security Manager, Risk Management, Chief Information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Big Data Architect Security Of Information In Big Data Graphics PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Big Data Architect Security Of Information In Big Data Graphics PDF bundle. Topics like Most Challenging, Securing Massive, Data Collections can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Analytics Management Security Of Information In Big Data Summary PDF
This slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on.Deliver an awe inspiring pitch with this creative Data Analytics Management Security Of Information In Big Data Summary PDF bundle. Topics like Securing Massive, Companies Frequently, Comprehending Preserving can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF
This slide covers two ways of enabling data security in CRM systems. It includes options such as IP restrictions and two-factor authentication. Deliver an awe inspiring pitch with this creative Customer Relationship Management Software Implementation Steps Enable Data Security Formats PDF bundle. Topics like Security And Compliance, Factor Authentication, Security Accounts can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
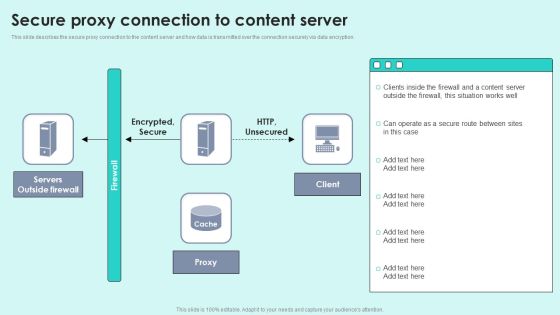
Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF
This slide describes the secure proxy connection to the content server and how data is transmitted over the connection securely via data encryption. Deliver an awe inspiring pitch with this creative Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Designs PDF bundle. Topics like Servers Outside, Encrypted Secure, Outside Firewall can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates Ppt Background For Slides 1112
We present our Golden Key Chain Tied With Puzzle Piece Security PowerPoint Templates PPT Background For Slides 1112.Use our Business PowerPoint Templates because,You too have got the framework of your companys growth in place. Use our Success PowerPoint Templates because, You can Transmit this concern to your staff using our helpful slides. Use our Puzzles or jigsaws PowerPoint Templates because,We all know that alphabetical order is a time honoured concept. Use our Shapes PowerPoint Templates because,you can put it up there for all to see. Use our Marketing PowerPoint Templates because,Networking is an imperative in todays world. You need to access the views of others. Similarly you need to give access to them of your abilitiesUse these PowerPoint slides for presentations relating to Key chain tied with puzzle piece, business, success, puzzles or jigsaws, shapes, marketing. The prominent colors used in the PowerPoint template are Yellow, Black, Red

Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF
The firm can track the financial performance by looking the financial practices it follows in order to avoid any early signs of financial distress. Slidegeeks is here to make your presentations a breeze with Organizational Assets Security Management Strategy Evaluating Financial Practices In Firm Formats PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
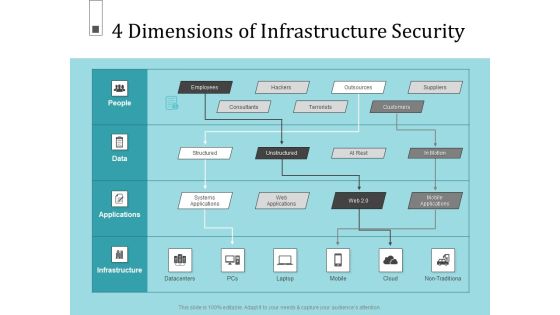
Infrastructure Project Management In Construction 4 Dimensions Of Infrastructure Security Information PDF
Deliver an awe inspiring pitch with this creative infrastructure project management in construction 4 dimensions of infrastructure security information pdf. bundle. Topics like consultants, terrorists, structured, systems applications, suppliers can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Construction Engineering And Industrial Facility Management 4 Dimensions Of Infrastructure Security Graphics PDF
Deliver an awe inspiring pitch with this creative construction engineering and industrial facility management 4 dimensions of infrastructure security graphics pdf bundle. Topics like structured, unstructured, systems applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Weekly Timeline With Task Name Hacking Prevention Awareness Training For IT Security Download PDF
Deliver an awe inspiring pitch with this creative weekly timeline with task name hacking prevention awareness training for it security download pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Agenda For Organizational Network Security Awareness Staff Learning Ppt Styles Master Slide PDF
Deliver an awe-inspiring pitch with this creative agenda for organizational network security awareness staff learning ppt styles master slide pdf bundle. Topics like employees identifying, cybersecurity incidents, information systems can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Icons Slides For Case Competition Overpower The Obstacle Of Cyber Security In Medicare Microsoft PDF
Deliver an awe inspiring pitch with this creative icons slides for case competition overpower the obstacle of cyber security in medicare microsoft pdf bundle. Topics like Icons can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Financial Losses To The Organizations Due To Security Issues Mockup PDF
Deliver an awe inspiring pitch with this creative financial losses to the organizations due to security issues mockup pdf bundle. Topics like physical theft of a data carrying device, malware attacks, insider misuse can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
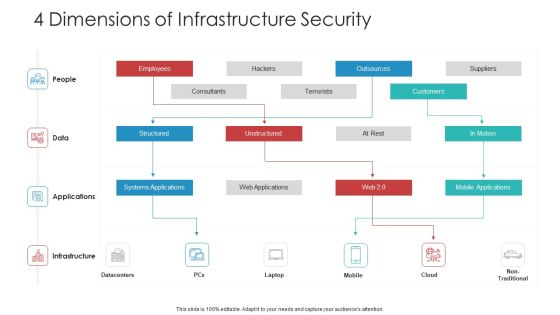
Landscape Architecture Planning And Management 4 Dimensions Of Infrastructure Security Sample PDF
Deliver an awe inspiring pitch with this creative landscape architecture planning and management 4 dimensions of infrastructure security sample pdf bundle. Topics like people, data, applications, infrastructure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Weekly Timeline With Task Name Food Security Excellence Ppt Ideas Professional PDF
Deliver an awe inspiring pitch with this creative weekly timeline with task name food security excellence ppt ideas professional pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Ways Through Which Security Data Can Be Compromised And Measures To Deal With Them Designs PDF
Deliver an awe inspiring pitch with this creative ways through which security data can be compromised and measures to deal with them designs pdf bundle. Topics like attack description, ways to mitigate attack, program and implement can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Developing Firm Security Strategy Plan Weekly Timeline With Task Name Clipart PDF
Deliver an awe inspiring pitch with this creative developing firm security strategy plan weekly timeline with task name clipart pdf bundle. Topics like weekly timeline with task name can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Secured Video Hosting Platform Investor Capital Funding Table Of Content Pictures PDF
Deliver an awe inspiring pitch with this creative secured video hosting platform investor capital funding table of content pictures pdf bundle. Topics like sales and distribution, online video platform, revenue generation, future initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Table Of Content Secured Video Hosting Platform Investor Capital Funding Icons PDF
Deliver an awe inspiring pitch with this creative table of content secured video hosting platform investor capital funding icons pdf bundle. Topics like online video hosting platform overview, growth potential of online video platform market, addressing purpose defining brand and culture can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
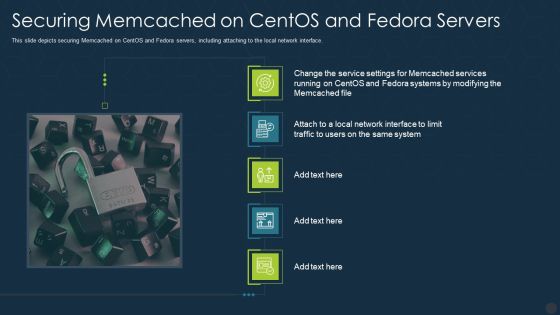
Securing Memcached On Centos And Fedora Servers Ppt Infographics Show PDF
Deliver an awe inspiring pitch with this creative securing memcached on centos and fedora servers ppt infographics show pdf bundle. Topics like system, network can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Information And Event Management Strategies For Financial Audit And Compliance How SIEM Works Clipart PDF
Deliver an awe inspiring pitch with this creative security information and event management strategies for financial audit and compliance how siem works clipart pdf bundle. Topics like behavior analytics, correlation, taxonomy, normalization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
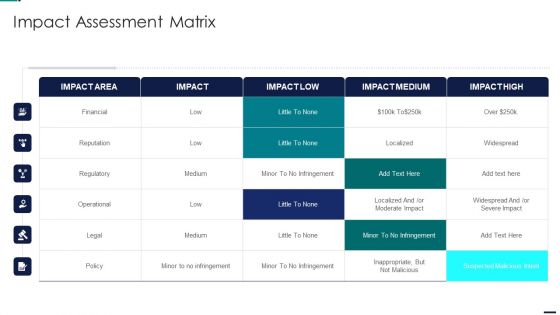
Risk Management Model For Data Security Impact Assessment Matrix Formats PDF
Deliver an awe inspiring pitch with this creative Risk Management Model For Data Security Impact Assessment Matrix Formats PDF bundle. Topics like Financial, Reputation, Regulatory, Operational can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Risk Based Procedures To IT Security Slides PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Risk Based Procedures To IT Security Slides PDF bundle. Topics like Gap Identification, Business Priorities, Digitization Levels can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
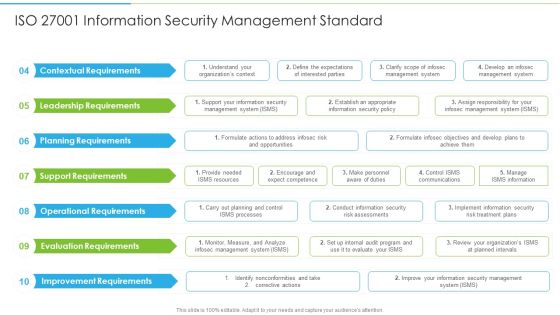
Ways To Accomplish ISO 27001 Accreditation ISO 27001 Information Security Management Infographics PDF
Deliver an awe inspiring pitch with this creative Ways To Accomplish ISO 27001 Accreditation ISO 27001 Information Security Management Infographics PDF bundle. Topics like Contextual Requirements, Leadership Requirements, Planning Requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Data Security Zero Trust Policy And Why You Should Embrace It Microsoft PDF
Deliver an awe inspiring pitch with this creative Cloud Data Security Zero Trust Policy And Why You Should Embrace It Microsoft PDF bundle. Topics like Authentication, Device Validation, Restrict Access can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
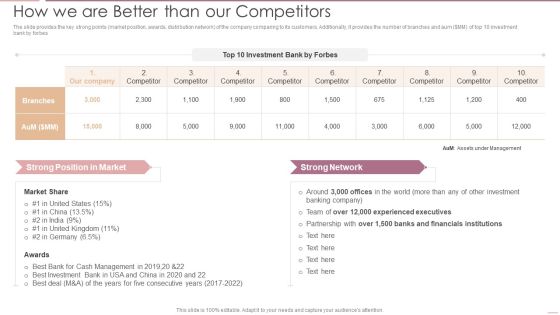
Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF
Deliver an awe inspiring pitch with this creative Investment Banking Security Underwriting Pitchbook How We Are Better Than Our Competitors Introduction PDF bundle. Topics like Experienced Executives, Financials Institutions, Cash Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF
Deliver an awe inspiring pitch with this creative Key Statistics Showing The Impact Of Security Awareness Training Software Information PDF bundle. Topics like Attacked Phishing, Employees Will, Phishing During can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
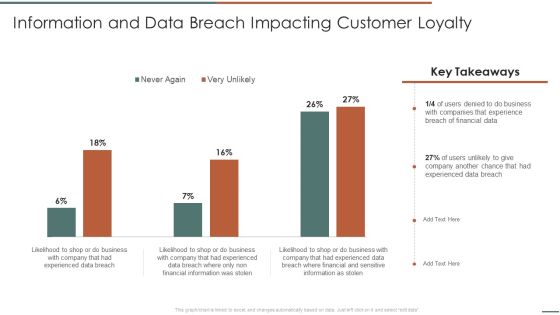
Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF
Deliver an awe inspiring pitch with this creative Information Security Risk Evaluation Information And Data Breach Impacting Customer Loyalty Structure PDF bundle. Topics like Companies Experience, Financial Information, Breach Of Financial can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF
Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF bundle. Topics like Leadership Requirements, Contextual Requirements, Planning Requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents For Mobile Device Security Management In Organization Icons PDF
Deliver an awe inspiring pitch with this creative Table Of Contents For Mobile Device Security Management In Organization Icons PDF bundle. Topics like Analysing Current, Management Workplace, Management Systemcan be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition The ROI Of Security Awareness Training Brochure PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver an awe-inspiring pitch with this creative data breach prevention recognition the roi of security awareness training brochure pdf bundle. Topics like the roi of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Communication Plan General Format Hacking Prevention Awareness Training For IT Security Download PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe inspiring pitch with this creative communication plan general format hacking prevention awareness training for it security download pdf bundle. Topics like security awareness, communication, organizations, frequency can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Security Awareness Staff Learning Communication Plan General Format Infographics PDF
This slide covers the schedule communication plan for security awareness program including brief description, frequency and audience. Deliver an awe-inspiring pitch with this creative organizational network security awareness staff learning communication plan general format infographics pdf bundle. Topics like communication, security awareness, organizations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Staff Learning Automated Security Awareness Platform And Cost Introduction PDF
This slide covers the Automated training programs for security awareness that will help educate workers to act appropriately, even when introduced to entirely new risks. Deliver an awe-inspiring pitch with this creative organizational network staff learning automated security awareness platform and cost introduction pdf bundle. Topics like automated security awareness platform and cost can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Enhanced Protection Corporate Event Administration Impact Of Effective Security Management Brochure PDF
This slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration impact of effective security management brochure pdf bundle. Topics like impact of effective security management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Essential Elements To Be Included In A Security Management Plan Rules PDF
This slide provides information about the essential elements parts that must be included in security management plan by the company and IT security manager. Deliver an awe inspiring pitch with this creative essential elements to be included in a security management plan rules pdf bundle. Topics like program management, prevention, preparedness can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
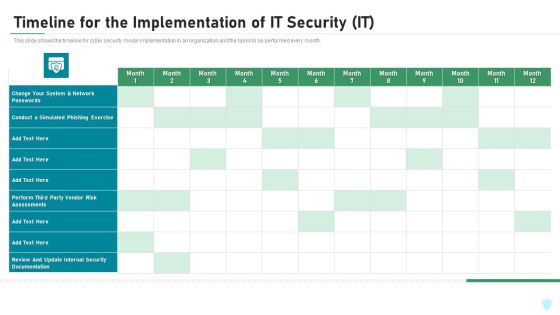
Timeline For The Implementation Of IT Security IT Ppt Inspiration Portrait PDF
This slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an awe inspiring pitch with this creative timeline for the implementation of it security it ppt inspiration portrait pdf bundle. Topics like network, internal security, perform, phishing exercise can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home