Safety Plan
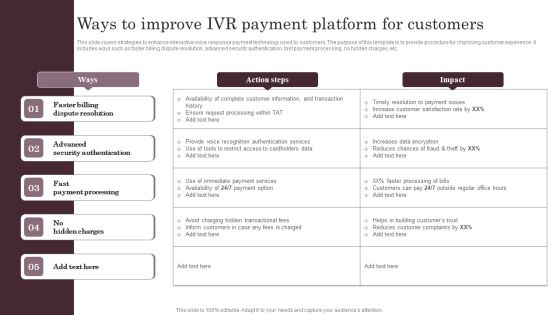
Omnichannel Services Solution In Financial Sector Ways To Improve IVR Payment Platform Infographics PDF
This slide covers strategies to enhance interactive voice response payment technology used by customers. The purpose of this template is to provide procedure for improving customer experience. It includes ways such as faster billing dispute resolution, advanced security authentication, fast payment processing, no hidden charges, etc. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Omnichannel Services Solution In Financial Sector Ways To Improve IVR Payment Platform Infographics PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Steps To Create Virtual Communication And Engagement Policy Themes PDF
This slide mentions the steps to create digital communication policy for organizations. It includes establishing governance, dictating security protocol, defining channels and setting standards for responsiveness. Persuade your audience using this Steps To Create Virtual Communication And Engagement Policy Themes PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Dictate Security Protocol, Establish Governance, Define Channels. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Data Lake Architecture Main Features Of Data Lake For Customer Pictures PDF
This slide represents the main features of data lakes, such as the ability to store structured and unstructured data, infinite scale to store and secure information, link of data to analytics and ML, etc. Deliver an awe inspiring pitch with this creative Data Lake Architecture Main Features Of Data Lake For Customer Pictures PDF bundle. Topics like Organized And Unstructured, Data Analysis, Data Migration, Analytics And Machine Learning Techniques can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF
Deliver and pitch your topic in the best possible manner with this IT Security Risk Management Approach Introduction Key Security Controls To Be Addressed In The Program Formats PDF. Use them to share invaluable insights on Application Whitelisting, Patch Applications, User Application Hardening and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Business Information Protection Program Implementation With Review Information PDF
This slide covers business security program implementation with review which includes organizational facility security risk assessment with service vendors.Persuade your audience using this Business Information Protection Program Implementation With Review Information PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Program Review, Assessment Results, Business Requirement. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
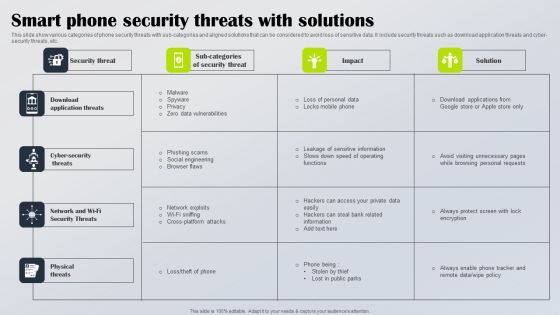
Smart Phone Security Threats With Solutions Diagrams PDF
This slide show various categories of phone security threats with sub categories and aligned solutions that can be considered to avoid loss of sensitive data. It include security threats such as download application threats and cyber security threats, etc. Showcasing this set of slides titled Smart Phone Security Threats With Solutions Diagrams PDF. The topics addressed in these templates are Download Application Threats, Cyber Security Threats, Network Wi Fi Security Threats. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Security Management Four Phase Process Topics PDF
The purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat. Presenting Business Security Management Four Phase Process Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Identify, Evaluate, Treat, Monitor. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF
This slide talks about the outliers model used for predictive analytics, including its use cases, impact and algorithm used in it, such as the generalized linear model for two values. This model helps banking, finance, and cyber security organizations to detect fraud and cyber crimes. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Predictive Analytics Methods Outliers Model For Predictive Analytics Designs PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Best Practices To Create Data Retention Security Mechanism Topics PDF
This slide showcases best practices of data retention policy. The practices covered are data classification, determine business needs, understand legal aspects and regular data backup.Presenting Best Practices To Create Data Retention Security Mechanism Topics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Understand Legal Aspect, Determine Business Needs, Regular Data Backup . This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
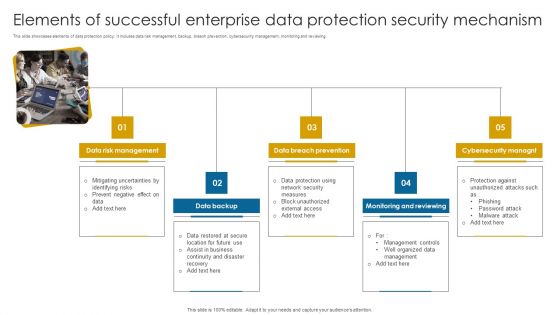
Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF
This slide showcases elements of data protection policy. It includes data risk management, backup, breach prevention, cybersecurity management, monitoring and reviewing.Persuade your audience using this Elements Of Successful Enterprise Data Protection Security Mechanism Information PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Management, Breach Prevention, Monitoring Reviewing. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Integrated Security Risk Management Model Diagram Ppt Idea
This is a integrated security risk management model diagram ppt idea. This is a six stage process. The stages in this process are scope, quality, time, information, assets, sub activities.

Security Management Audits Sample Diagram Ppt Sample Presentations
This is a security management audits sample diagram ppt sample presentations. This is a six stage process. The stages in this process are assets, development, scope, analysis, deploy, replace.

Data Center Infrastructure Management IT Data Center Security Standards We Used Professional PDF
This slide shows the data center security standards that we used to prevent data, and it includes layered security measures, access lists, video surveillance, source access points, and 24 7 security. Deliver and pitch your topic in the best possible manner with this data center infrastructure management it data center security standards we used professional pdf. Use them to share invaluable insights on layered security measures, access lists, video surveillance, secure access points, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF
This slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them.This Challenges And Solutions In Information Security Risk Management Information Security Risk Administration Template PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.

Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
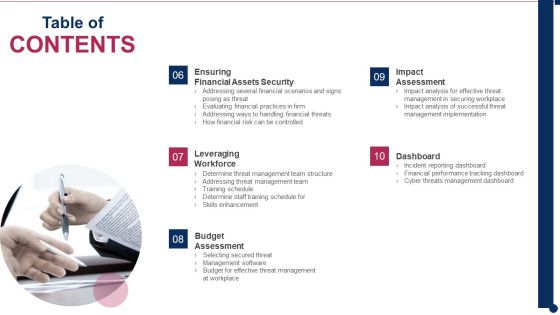
Threat Management At Workplace Contents Brochure Pdf
Presenting threat management at workplace contents brochure pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like training schedule, determine staff training schedule, skills enhancement, selecting secured threat, management software. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Diagram Business Process 3d Man Piggy Bank PowerPoint Templates
We present our diagram business process 3d man piggy bank PowerPoint templates.Present our Future PowerPoint Templates because Our PowerPoint Templates and Slides are like the strings of a tennis racquet. Well strung to help you serve aces. Download our Symbol PowerPoint Templates because you should once Tap the ingenuity of our PowerPoint Templates and Slides. They are programmed to succeed. Present our Security PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Use our Finance PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit.Use these PowerPoint slides for presentations relating to 3d, analyzing, bank, banking, box, business, buying, cartoon, coin, concept, currency, debt, dividend, dollar, exchange, finance, forecasting, fortune, green, growth, human, investment, loan, luck, making, man, market, marketing, money, moving, occupation, omit, paying, pension, people, person, pig, piggy, pleasure, postpone, puppet, rate, savings, stock, success, symbol, tax, wages, wealth. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Professionals tell us our diagram business process 3d man piggy bank PowerPoint templates will make the presenter successul in his career/life. Use our coin PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Use our diagram business process 3d man piggy bank PowerPoint templates are visually appealing. Customers tell us our coin PowerPoint templates and PPT Slides will get their audience's attention. Presenters tell us our diagram business process 3d man piggy bank PowerPoint templates will make the presenter look like a pro even if they are not computer savvy. People tell us our bank PowerPoint templates and PPT Slides effectively help you save your valuable time.

Cyber Crime And War Security Strategic Vision Designs PDF
This slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team.Persuade your audience using this Cyber Crime And War Security Strategic Vision Designs PDF This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Strategy, Protection Promotion, Secured Cyberspace Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF
This slide covers key strategies for enhancing enterprise security operations. It involves strategies such as detect endpoint threats, leverage advanced analytics and automate incident response. Presenting Key Strategies For Enhancing ESO System Ppt PowerPoint Presentation Icon Outline PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Checklist For Selecting Functional Technology Security Vendor Mockup PDF
Showcasing this set of slides titled checklist for selecting functional technology security vendor mockup pdf. The topics addressed in these templates are security, environments, technologies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
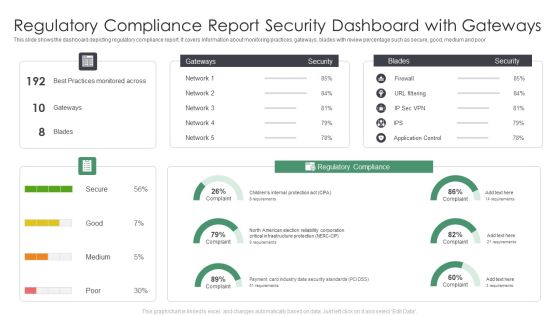
Regulatory Compliance Report Security Dashboard With Gateways Information PDF
This slide shows the dashboard depicting regulatory compliance report. It covers information about monitoring practices, gateways, blades with review percentage such as secure, good, medium and poor. Showcasing this set of slides titled Regulatory Compliance Report Security Dashboard With Gateways Information PDF. The topics addressed in these templates are Regulatory Compliance Report Security, Dashboard With Gateways. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF
This slide covers the roadmap for various courses in security awareness programs. It includes cyber system management, password security program, insider threats program, e mail security program.Presenting Quarterly Cybersecurity Training Program And Schedule Timeline Rules PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Risk Assessment, Security Program, Threats Program. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF
This slide talks about the password guidelines under the internet usage policy. It is further divided into three categories such as selection of a strong password, keeping the password safe, and other security measures. This Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Information Technology Policy And Processes Internet Usage Policy Password Guidelines Mockup PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cyber Security Threat Dashboard With KPI Metrics Icons PDF
This slide shows dashboard of cyber threats to organization and metrics and performance indicators for security officer. It covers operational health, audit and compliance, controls health and project status. Showcasing this set of slides titled Cyber Security Threat Dashboard With KPI Metrics Icons PDF. The topics addressed in these templates are Cyber Security Threat Dashboard, Kpi Metrics. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Dashboard For Insider Threat In Cyber Security Cases Management Background PDF
This slide shows insider threat dashboard for managing multiple cases. It provides information such as active and closed, high and low risk cases, status, user, case time, policy alerts, content update, etc. Showcasing this set of slides titled Dashboard For Insider Threat In Cyber Security Cases Management Background PDF. The topics addressed in these templates are Total Policy Alerts, High, Low, Time Case Opened. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Agency Business Profile Mission Vision And Core Values Microsoft PDF
Presenting Security Agency Business Profile Mission Vision And Core Values Microsoft PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Mission Vision, Core Values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe Slides PDF
This slide represents the overview of fully homomorphic encryption used in confidential computing. This slides purpose is to show its importance, working and multiple benefits. The main benefits include improved security, strict regulatory compliance and enhanced cloud security. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Confidential Computing System Technology What Is Fully Homomorphic Encryption Fhe Slides PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

General Corporate Matters Ppt PowerPoint Presentation Slides Graphics Download
This is a general corporate matters ppt powerpoint presentation slides graphics download. This is a four stage process. The stages in this process are business, list of current officers and directors, lists of all security holders, list of subsidiaries and their respective charter documents, list of no shop or exclusivity obligations.
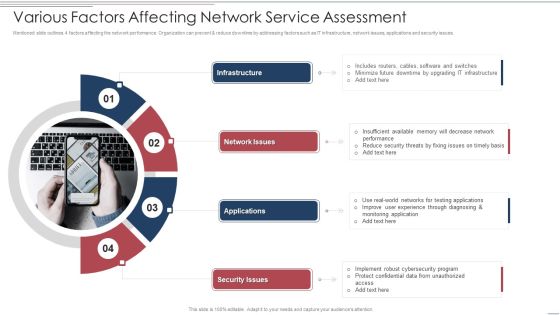
Various Factors Affecting Network Service Assessment Brochure PDF
Mentioned slide outlines 4 factors affecting the network performance. Organization can prevent and reduce downtime by addressing factors such as IT infrastructure, network issues, applications and security issues. Persuade your audience using this Various Factors Affecting Network Service Assessment Brochure PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Infrastructure, Network Issues, Applications. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. It includes benefits of order management system such as fast delivery, less mistakes etc. It includes benefits of order management system such as fast delivery, less mistakes etc. This Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing An Effective Ecommerce Management Framework Importance Of Secure Ecommerce Payment Systems Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today

Four Month Project Timeline Swimlane Timeline Guidelines PDF
This slide represents four month project scheduling swimlane timeline illustrating departments and there tasks such as team members, technology , security, resource allocation, employee staffing etc. Showcasing this set of slides titled four month project timeline swimlane timeline guidelines pdf. The topics addressed in these templates are security, technology, team members. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Types Of Web Application Firewall Security Models WAF Platform Themes PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Presenting Types Of Web Application Firewall Security Models WAF Platform Themes PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like White List Access Control, Black List Access Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Unconventional Monetary Policy How Did It Spread Professional PDF
This is a unconventional monetary policy how did it spread professional pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like investment, securities, agencies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Unconventional Monetary Policy Quantitative Easing Ppt File Inspiration PDF
Presenting unconventional monetary policy quantitative easing ppt file inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like quantitative, interest, market, securities, government. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Addressing Mission Vision And Core Values Associated To Firm Food Security Excellence Ppt Ideas Demonstration PDF
This slide provides information regarding the mission, vision and core values associated to firm. Presenting addressing mission vision and core values associated to firm food security excellence ppt ideas demonstration pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like mission, vision, core values. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

AIOPS Implementation Artificial Intelligence For IT Operations In Retail Industry Background PDF
This slide describes the application of AIOps in the retail industry for IT operations, including data synchronization, secure client information, flexible infrastructure, and maintaining effective operations. Deliver an awe inspiring pitch with this creative AIOPS Implementation Artificial Intelligence For IT Operations In Retail Industry Background PDF bundle. Topics like Customer Experience, Retail Business, New Technology can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF
This slide depicts the real-world applications of the metaverse, including in-game assets, self-identity authentication, an incentive for creators, and control over real estate assets by blockchain. Deliver an awe inspiring pitch with this creative Metaverse Technology IT Real World Applications Of The Metaverse Ppt Show Layout Ideas PDF bundle. Topics like Avoiding Fraud, Avatars Identities, Securely Retain can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
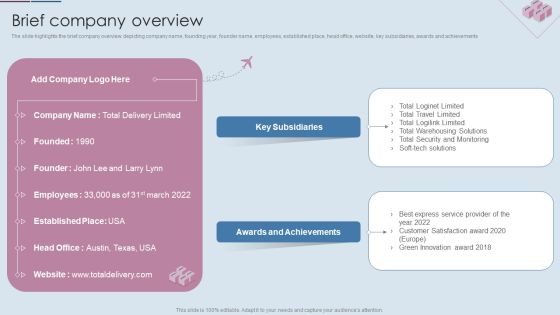
Logistics Shipment Company Profile Brief Company Overview Ppt Backgrounds PDF
The slide highlights the brief company overview depicting company name, founding year, founder name, employees, established place, head office, website, key subsidiaries, awards and achievements. Deliver an awe inspiring pitch with this creative Logistics Shipment Company Profile Brief Company Overview Ppt Backgrounds PDF bundle. Topics like Key Subsidiaries, Awards and Achievements, Total Security, Monitoring can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
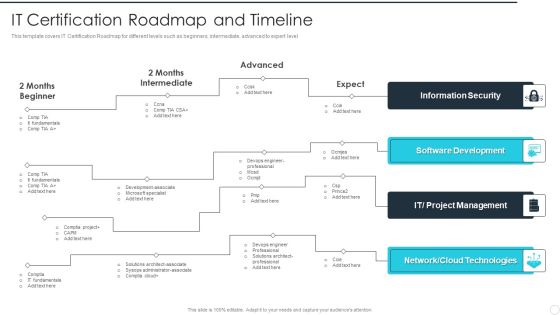
IT Career Certifications IT Certification Roadmap And Timeline Inspiration PDF
This template covers IT Certification Roadmap for different levels such as beginners, intermediate, advanced to expert level . Deliver an awe inspiring pitch with this creative IT Career Certifications IT Certification Roadmap And Timeline Inspiration PDF bundle. Topics like Information Security, Software Development, Project Management, Cloud Technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Certifications Advantages IT Certification Roadmap Microsoft PDF
This template covers IT certification roadmap for different levels such as beginners, intermediate, advanced to expert level. Deliver an awe inspiring pitch with this creative Information Technology Certifications Advantages IT Certification Roadmap Microsoft PDF bundle. Topics like Information Security, Software Development, Project Management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF
Purpose of this slide is to provide information about the cyber security awareness training program to be conducted for in-house team. It also provides the details about training types, content types and audience. If your project calls for a presentation, then Slidegeeks is your go-to partner because we have professionally designed, easy-to-edit templates that are perfect for any presentation. After downloading, you can easily edit Cyber Risks And Incident Response Playbook Cyber Security Awareness Training Program Inspiration PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates

Cybersecurity Guidelines IT Password Creation And Management Policy Sample PDF
This slide depicts the password creation and management policy that explains how to create, implement, and review a defined procedure for establishing, updating, and maintaining strong and secure passwords. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cybersecurity Guidelines IT Password Creation And Management Policy Sample PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Cloud Based Marketing Cloud Services Competitive Landscape Ppt PowerPoint Presentation Summary PDF
This slide provides the chart comparing features of cloud services offered by our company and other vendors available in the market. Deliver an awe-inspiring pitch with this creative cloud based marketing cloud services competitive landscape ppt powerpoint presentation summary pdf bundle. Topics like security framework, pricing transparency, hybrid cloud expertise, overall scores can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF
The following slide highlights the preventive information technical controls which includes authentication, authorization, enable control enforcement, nonrepudiation, secured communications and secured transactions. Presenting Information Technology Threat Mitigation Methods Preventive IT Technical Control Measures Information PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Authorization, Secured Communications, Authentication. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

5G Network Operations Security In 5G Technology Architecture Template PDF
This slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download 5G Network Operations Security In 5G Technology Architecture Template PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the 5G Network Operations Security In 5G Technology Architecture Template PDF.

IT Data Services Certification Programs Career With Cisco Certified Network Associate CCNA Brochure PDF
This slide covers details about Cisco Certified Network Associate CCNA certification including career with CCNA, salary expectations, job responsibilities etc. This is a IT Data Services Certification Programs Career With Cisco Certified Network Associate CCNA Brochure PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Network Fundamentals, Automation And Programmability, Security Fundamentals. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Consultancy Services Company Profile Our Management Team Topics PDF
This slide shows the key people involved in management team which includes chief executive officer, executive assistant, chief financial officer, senior developer, security risk manager and chief technology officer.Presenting IT Consultancy Services Company Profile Our Management Team Topics PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Operational Leadership, Corporate Decisions, Organize Meetings. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Internet Security Threat Analysis With Customer Centric Approach Mockup PDF
Data security breach steps with customer centric approach. It includes 5 steps such as- proactive and preventive analysis, data protection as the default and so on. Showcasing this set of slides titled internet security threat analysis with customer centric approach mockup pdf. The topics addressed in these templates are data minimization, data protection, proactive and preventive. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Risk Security Company Users And Protection Introduction PDF
The following slide highlights the cyber threat security companies with its users retailers, BFSI, large scale enterprises, protection and pricing. Showcasing this set of slides titled cyber risk security company users and protection introduction pdf. The topics addressed in these templates are company, users, protection. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF
This slide provides glimpse about different risks compromising security that are associated with Electronic Data Interchange technology. It includes risks such as disclosure, message modification, sequence modification, etc.Showcasing this set of slides titled Security Risks Associated With Electronic Data Interchange Technology Guidelines PDF. The topics addressed in these templates are Private Multilateral, Multilateral Common, Carrier Dependent. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Network Security Tools And Package Graphics PDF
The slide represents tools encapsulated in cloud computing security software. The elements include computing tools, software such as SaaS, PaaS, IaaS and pricing package. Showcasing this set of slides titled Cloud Network Security Tools And Package Graphics PDF. The topics addressed in these templates are Saas, Paas, Iaas. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Roles And Responsibilities Of Cyber Security Team Ppt Portfolio
The purpose of this slide is to outline various roles and responsibilities of key stakeholders involve in the security awareness team. Chief information security officer CISO, cyber risk committee, cyber risk manager and security operations manager are some of the major stakeholders which are highlighted in the slide. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Roles And Responsibilities Of Cyber Security Team Ppt Portfolio can be your best option for delivering a presentation. Represent everything in detail using Roles And Responsibilities Of Cyber Security Team Ppt Portfolio and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cyber Security Risk Dashboard With KPI Metrics Elements PDF
This slide depicts global cyber security and risk trends providing information about every aspect of threat. It includes overall progression, critical risk identified, initiatives, incident and vulnerabilities management, compliance and patches. Showcasing this set of slides titled Cyber Security Risk Dashboard With KPI Metrics Elements PDF. The topics addressed in these templates are Vulnerability Management Program, Reports And Metrics Elaboration, Critical Risk Identified. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Event And Incident Flow Diagram Icons PDF
This slide represents the flow diagram showing the procedure of managing cyber security incidents in order to minimize its impact on business operations. It starts with detection of cyber security incident and ends with response to crisis situation. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created Cyber Security Event And Incident Flow Diagram Icons PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

Corporate System Security Quality Assurance Matrix Demonstration PDF
This slide covers quality assurance for corporate system security. It includes a matrix based on functional and customer requirements for security system such as no access to restricted sites, email tracking, confidential data protection, etc. Showcasing this set of slides titled Corporate System Security Quality Assurance Matrix Demonstration PDF. The topics addressed in these templates are Customer Requirements, Functional Requirements, Centralised Network. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Impact And Probability Assessment Inspiration PDF
This slide defines the risk impact and likelihood assessment in cyber security. It includes information related to creating awareness in top management regarding technical, commercial, and branding damages deriving from suffering a cyber-attack. Showcasing this set of slides titled Cyber Security Risk Impact And Probability Assessment Inspiration PDF. The topics addressed in these templates are Business Continuity, Restoring Cost, Information Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Different Categories Of Data Centers Types Of Data Centers Colocation Data Centers Topics PDF
This slide shows the one from different types of data centers that is colocation data centers that provide services to organizations, including cooling, bandwidth, and security. Take your projects to the next level with our ultimate collection of Different Categories Of Data Centers Types Of Data Centers Colocation Data Centers Topics PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors theyll make your projects stand out from the rest.

IT Risk Control Strategies Risk Management With Human Capital Ppt Outline Format PDF
This slide covers the model for information technology risk management which focuses on risk strategy, governance risk and compliance, security operations and human capital that helps in considering the IT components for risk and threat management. Persuade your audience using this IT Risk Control Strategies Risk Management With Human Capital Ppt Outline Format PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Risk Strategy, Security Operations, Human Capital. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cyber Security Risk Assessment Control Measures Slides PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain likely possible unlikely and rare. Showcasing this set of slides titled Cyber Security Risk Assessment Control Measures Slides PDF. The topics addressed in these templates are Cyber Security Risk, Assessment Control Measures. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Risk Identification And Remediation Matrix Background PDF
The purpose of this slide is to define the level of hazards and their severity in cybersecurity management along with priority levels 1 to 5 to manage risks. This is categorized as certain, likely, possible, unlikel, and rare. Showcasing this set of slides titled Cyber Security Risk Identification And Remediation Matrix Background PDF. The topics addressed in these templates are Cyber Security Risk Identification, Remediation Matrix. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
 Home
Home