Safety Plan
List Cyber Security Risks Ppt PowerPoint Presentation File Example File Cpb
Presenting this set of slides with name list cyber security risks ppt powerpoint presentation file example file cpb. This is an editable Powerpoint seven stages graphic that deals with topics like list cyber security risks to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

List E Commerce Cyber Security Threats Ppt PowerPoint Presentation Slides Introduction Cpb
Presenting this set of slides with name list e commerce cyber security threats ppt powerpoint presentation slides introduction cpb. This is an editable Powerpoint four stages graphic that deals with topics like list e commerce cyber security threats to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Temporary Employment Firm Contract Agreement Policies Ppt PowerPoint Presentation Inspiration Clipart PDF
Presenting temporary employment firm contract agreement policies ppt powerpoint presentation inspiration clipart pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including temporary employment firm contract agreement policies. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF
Following slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. This is a Risk Based Procedures To IT Security Checklist For Effectively Managing Asset Security Portrait PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like System Monitoring, Data Backup, Security Patches. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Ways To Avoid Software As A Service Implementation Risks Microsoft PDF
The following slide showcases ways to avoid SaaS implementation risk. It includes skills gap, unintended integration and data security. Presenting Ways To Avoid Software As A Service Implementation Risks Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Skills Gap, Unintended Integration, Data Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Marketing Concepts Many To 5 Stages Process Diagram Business Strategy Consultant
We present our marketing concepts many to 5 stages process diagram business strategy consultant.Download our Marketing PowerPoint Templates because They will Put the wind in your sails. Skim smoothly over the choppy waters of the market. Use our Business PowerPoint Templates because Our PowerPoint Templates and Slides will let you Clearly mark the path for others to follow. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Present our Process and Flows PowerPoint Templates because You should Throw the gauntlet with our PowerPoint Templates and Slides. They are created to take up any challenge. Use our Curves and Lines PowerPoint Templates because You can Inspire your team with our PowerPoint Templates and Slides. Let the force of your ideas flow into their minds.Use these PowerPoint slides for presentations relating to Development, Web, Design, Building, Plan, Hand, Success, Successful, Internet, Visitor, Site, Website, Network, White, Innovation, Formula, Media, Business, Server, Concept, Characteristic, Organizing, Diagram, Drawing, Marketing, Word, Starting, Technology, Security, Blogging, Strategy, Technique, Young, Writing, Domain, Text, Quality, Organization, Brainstorming, Information, Background, Hosting, Blog, Database, Software, Component, White Board, Entrepreneur, Communication. The prominent colors used in the PowerPoint template are Blue, Gray, Black.

Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Presenting Cloud Security Assessment Pillars Of Cloud Security Visibility And Consistency Portrait PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Asset Inventory, Cloud Framework, Data Security In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Tech Support Services Cost And Pricing Agenda For Pricing IT Services Ppt PowerPoint Presentation Summary Diagrams
Presenting this set of slides with name tech support services cost and pricing agenda for pricing it services ppt powerpoint presentation summary diagrams. The topics discussed in these slides are infrastructure, analyzing, cyber security, monitoring, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Support And Monitoring Services Pricing Agenda For IT Support And Monitoring Services Pricing Elements PDF
Presenting this set of slides with name it support and monitoring services pricing agenda for it support and monitoring services pricing elements pdf. This is a six stage process. The stages in this process are infrastructure, analyzing, monitoring, cyber security, implementing. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security For Your Organization Agenda For Cyber Security Management Ppt Tips PDF
Presenting this set of slides with name cyber security for your organization agenda for cyber security management ppt tips pdf. This is a one stage process. The stages in this process are roles and responsibilities, management, executives responsible, risk management, optimize cybersecurity risk framework, executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Six Practices For IT Security Management Program Microsoft PDF
This slide shows the best practices for security management program which includes essential tasks such as risk analysis and identification, manage risk, threat and issues, security consolidation procedure, etc. With assigned owner and frequency.Presenting Six Practices For IT Security Management Program Microsoft PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Analysis Prioritization, Consolidation Procedure, Strategic Initiatives This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security For Your Organization Recovery Task List Maintenance Ppt Layouts Designs Download PDF
Presenting this set of slides with name cyber security for your organization recovery task list maintenance ppt layouts designs download pdf. This is a one stage process. The stages in this process are estimated time, actual time, assigned, comments. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart
With Our Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart Powerpoint Templates You Will Be Doubly Sure. They Possess That Stamp Of Authority. Our Security Powerpoint Templates Do It In Double Quick Time. Speed Up The Process In A Tangible Way.
Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF
This slide portrays information regarding the dashboard that firm will track various incidents detected. These incidents will be managed in order to avoid security risks. Find highly impressive Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Incidents Tracking Dashboard Workplace Security Management Program Summary PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Cloud Computing Services Overview Of Cloud Service Provider Company Rules PDF
This slide depicts the overview of the cloud service provider company, including its functionality, number of customers and partners, security, and operational expertise. This is a Cloud Computing Services Overview Of Cloud Service Provider Company Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Most Functionality, Most Secure, Largest Community, Customers And Partners. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF
This template depicts that by uploading existing email lists to Google, Facebook, and LinkedIn, user may target those customers with display advertising or create fresh unique lookalike audiences. This is a Security And Performance Digital Marketing Use Existing Email Lists To Launch Retargeting Campaigns Clipart PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Lookalike Audience, Retargeted Advertising, Lookalike Retargeting. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Program Hazards Management Strategy Topics PDF
This slide provides a strategy for cyber security risk management which helps business and organizations to secure the data and information. Key elements are understand, assess, determine and document.Persuade your audience using this Cyber Security Program Hazards Management Strategy Topics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Understand, Determine. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF
This slide highlights the top IT risks reported at workplace which includes cyber threats, data loss, social engineering attacks, regulatory incidents, domain based threats and denial of service. Slidegeeks has constructed Organizations Risk Management And IT Security Top IT Risks Reported At The Workplace Brochure PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Stock Photo Business Strategy Execution Umbrella With Flag Design Stock Photo Pictures Images
Our stock photo business strategy execution umbrella with flag design stock photo pictures images Let You Put Your Feet Up. Enjoy The Comforts They Will Bring. Get Your Team To Follow In Your Footsteps. Our Americana Will Blaze The Trail.

Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF
The purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Get a simple yet stunning designed Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy-to-edit Prevention Of Information Cyber Security Awareness Checklist To Ensure IT Asset Portrait PDF can be your go-to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF
This slide outlines the popular cloud access security broker vendors. The purpose of this slide is to showcase the multiple leading service providers for CASB, including Forcepoint, McAfee, Cisco Systems, Microsoft, Bitglass, and Net Spoke. It also includes the features and technology used by these vendors. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Popular Cloud Access Security Broker Vendors Ppt PowerPoint Presentation File Example PDF today and make your presentation stand out from the rest.

Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Developing IT Security Strategy Mitigation Strategies To Tackle Information Security Sample PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers
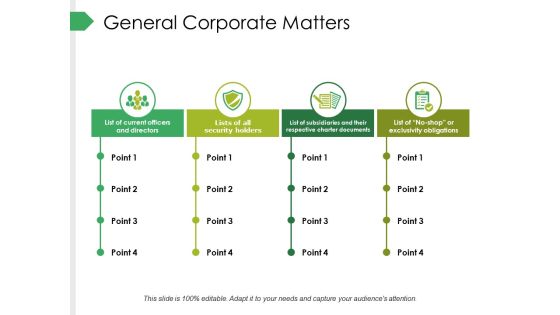
General Corporate Matters Ppt PowerPoint Presentation Summary Clipart Images
This is a general corporate matters ppt powerpoint presentation summary clipart images. This is a four stage process. The stages in this process are business, list of current officers and directors, lists of all security holders, list of subsidiaries and their respective charter documents, list of no shop or exclusivity obligations.
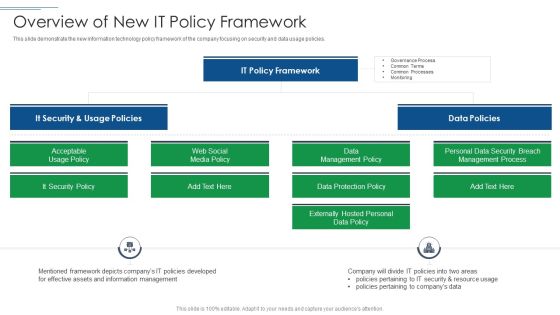
IT Security Risk Management Approach Introduction Overview Of New It Policy Framework Ideas PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting IT Security Risk Management Approach Introduction Overview Of New It Policy Framework Ideas PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like It Security, It Policy Framework, Data Policies. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Yellow Computer Folder With-key Internet PowerPoint Templates And PowerPoint Themes 1112
We present our Yellow Computer Folder With-Key Internet PowerPoint Templates And PowerPoint Themes 1112.Use our Computer PowerPoint Templates because, Different people with differing ideas and priorities perform together to score. Use our Internet PowerPoint Templates because, Our template will help pinpoint their viability. Use our Communication PowerPoint Templates because, Use our creative template to lay down your views. Use our Security PowerPoint Templates because, Gears Interconnected:- The Gear Train is a basic element of living and daily business. Use our Symbol PowerPoint Templates because,Use our templates for your colleagues knowledge to feed.Use these PowerPoint slides for presentations relating to Yellow computer folder with key Internet Security Computer Symbol Communication. The prominent colors used in the PowerPoint template are Yellow, White, Brown

CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Do you know about Slidesgeeks CYBER Security Breache Response Strategy Strategies To Analyze Cyber Security Incidents Inspiration PDF. These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.

CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF
This slide represents the various parameters to look for before choosing an effective and efficient cyber security containment strategy. It includes key parameters such as higher potential damages and theft of organizational resources etc. Take your projects to the next level with our ultimate collection of CYBER Security Breache Response Strategy Key Parameters To Select Cyber Security Containment Strategy Information PDF. Slidegeeks has designed a range of layouts that are perfect for representing task or activity duration, keeping track of all your deadlines at a glance. Tailor these designs to your exact needs and give them a truly corporate look with your own brand colors they will make your projects stand out from the rest.

Golden Key With Coins Secure Investment PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Golden Key With Coins Secure Investment PowerPoint Templates PPT Backgrounds For Slides 0213.Present our Money PowerPoint Templates because Our PowerPoint Templates and Slides offer you the needful to organise your thoughts. Use them to list out your views in a logical sequence. Present our security PowerPoint Templates because Our PowerPoint Templates and Slides will give you great value for your money. Be assured of finding the best projection to highlight your words. Download and present our Business PowerPoint Templates because Your audience will believe you are the cats whiskers. Present our Signs PowerPoint Templates because You can Double your output with our PowerPoint Templates and Slides. They make beating deadlines a piece of cake. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience.Use these PowerPoint slides for presentations relating to Gold yen coin key, money, security, business, sign, shapes. The prominent colors used in the PowerPoint template are Black, Orange, Gray.
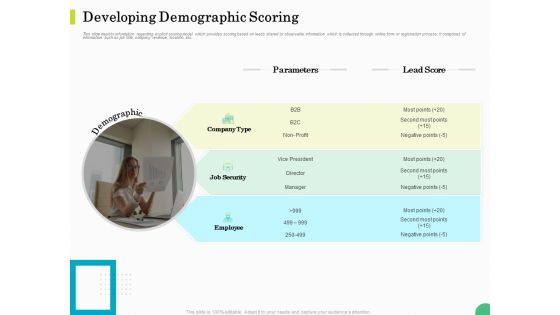
Evaluating Rank Prospects Developing Demographic Scoring Ppt Layouts Objects PDF
This slide depicts information regarding explicit scoring model which provides scoring based on leads shared or observable information which is collected through online form or registration process. It comprises of information such as job title, company revenue, location, etc. Presenting evaluating rank prospects developing demographic scoring ppt layouts objects pdf to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like parameters, lead score, job security, employee, demographic. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Three Types Of Computer Security Designs PDF
This slide shows the various types of information technology security. It includes network, end point and internet security. Presenting Three Types Of Computer Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Network Security, Point Security, Internet Security This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Schedule Grid To Increase Data Security Structure PDF
This slide signifies the IT schedule table to enhance data protection. It covers information about weekly schedule of activities to be conducted like configure technical security, conduct penetration test, install firewalls, conduct formal training. Pitch your topic with ease and precision using this Cyber Security Schedule Grid To Increase Data Security Structure PDF. This layout presents information on Recovery System, Vendor Risk Assessment, Configuring Security Software. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF
This slide represents the comparison between current and past scenario to analyze the impact of cyber security incident management on business operations. It includes analysis of KPIs such engagement, satisfaction, turnover rate etc. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye catching visual experience. Download CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high quality content for you. Later on, you can personalize the content by editing the CYBER Security Breache Response Strategy Impact Of Implementing Cyber Security Incident Management Inspiration PDF.

Information IT Security Swot Analysis Matrix Clipart PDF
This slide covers the strengths, weaknesses, opportunities and threats analysis of the company. IT showcases how the company is providing security to its client and on which areas they need to work upon. Persuade your audience using this Information IT Security Swot Analysis Matrix Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Strengths, Opportunities, Weaknesses, Threats. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
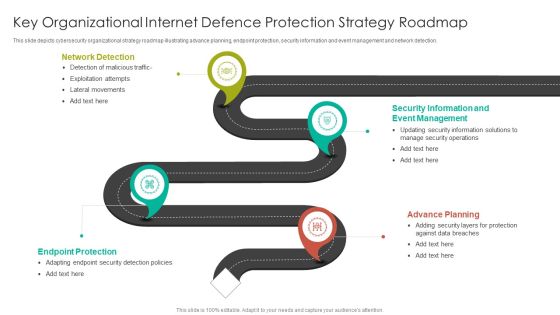
Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF
This slide depicts cybersecurity organizational strategy roadmap illustrating advance planning, endpoint protection, security information and event management and network detection.Persuade your audience using this Key Organizational Internet Defence Protection Strategy Roadmap Summary PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Network Detection, Event Management, Security Information. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
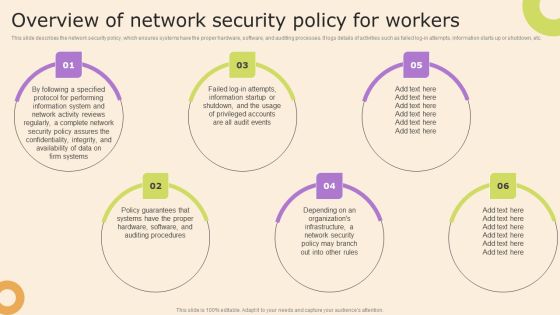
Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF
This slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Information Technology Policy And Processes Overview Of Network Security Policy For Workers Pictures PDF from Slidegeeks and deliver a wonderful presentation.
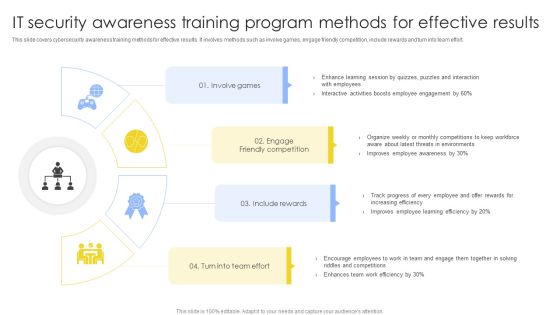
IT Security Awareness Training Program Methods For Effective Results Summary PDF
This slide covers cybersecurity awareness training methods for effective results. It involves methods such as involve games, engage friendly competition, include rewards and turn into team effort. Presenting IT Security Awareness Training Program Methods For Effective Results Summary PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Involve Games, Engage Friendly Competition, Include Rewards. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Internet Security Threat Analysis Strategy For Corporates Ppt PowerPoint Presentation File Picture PDF
Pitch your topic with ease and precision using this internet security threat analysis strategy for corporates ppt powerpoint presentation file picture pdf. This layout presents information on advanced cyber defence, operational security, platform security. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Process Diagram Powerpoint Presentation
This is a security process diagram powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.
Security Process Sample Powerpoint Presentation
This is a security process sample powerpoint presentation. This is a four stage process. The stages in this process are data, policy, assess, identify risk.

Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF
This slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always-changing tracking, access management, complex frameworks, and cloud compliance and governance. Presenting Cloud Information Security Top Advanced Cloud Security Challenges Ppt Show Maker PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Expanded Attack, Access Management, Complex Frameworks. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Strategy Framework Ppt PowerPoint Presentation Model Skills Cpb
Presenting this set of slides with name information security strategy framework ppt powerpoint presentation model skills cpb. This is an editable Powerpoint four stages graphic that deals with topics like information security strategy framework to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.

Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF
This slide showcases the steps for digital certificate creating procedure with secure communication. It includes elements such as request generation, verification, obtaining public key and sending digital certificate. Showcasing this set of slides titled Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF. The topics addressed in these templates are Certifying Authority, Key Communication, Digital Certificate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
Implementing Security Management Strategy To Mitigate Risk Icons Slide Icons PDF
Help your business to create an attention-grabbing presentation using our implementing security management strategy to mitigate risk icons slide icons pdf set of slides. The slide contains innovative icons that can be flexibly edited. Choose this implementing security management strategy to mitigate risk icons slide icons pdf template to create a satisfactory experience for your customers. Go ahead and click the download button.

Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF
Showcasing this set of slides titled Cyber Security Risk Management Icon In IT Risk Control Strategies Sample PDF. The topics addressed in these templates are Cyber Security, Risk Management, Icon, IT Risk, Control Strategies. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF
This slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Explore a selection of the finest Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Developing IT Security Strategy Checklist For Information Security Risk Management Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Boost your pitch with our creative Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Techniques And Strategies To Reduce Security Management Risks Current Security Management Professional PDF
This slide shows some of the current Security Management challenges and issues that are faced by the company and IT security managers.Deliver and pitch your topic in the best possible manner with this techniques and strategies to reduce security management risks current security management professional pdf Use them to share invaluable insights on potential insider threats, external security breaches, centric breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Protecting Profit Business PowerPoint Backgrounds And Templates 0111
Microsoft PowerPoint Template and Background with 3d illustration of two thick chrome chain links lying over top of a bright green stock chart

Cloud Based Marketing Key Challenges Of Cloud Services Ppt PowerPoint Presentation Styles Graphics Template PDF
Deliver an awe-inspiring pitch with this creative cloud based marketing key challenges of cloud services ppt powerpoint presentation styles graphics template pdf bundle. Topics like building private cloud, performance, managing multiple clouds, compliance, governance, control, lack resources, expertise, security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Presenting Cloud Information Security Cloud Security Checklist Logging And Monitoring Ppt Show Information PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Future Evaluation, New Policies, Potential Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Attack Ppt PowerPoint Presentation Complete Deck With Slides
Improve your presentation delivery using this Cyber Security Attack Ppt PowerPoint Presentation Complete Deck With Slides. Support your business vision and objectives using this well-structured PPT deck. This template offers a great starting point for delivering beautifully designed presentations on the topic of your choice. Comprising twelve slides this professionally designed template is all you need to host discussion and meetings with collaborators. Each slide is self-explanatory and equipped with high-quality graphics that can be adjusted to your needs. Therefore, you will face no difficulty in portraying your desired content using this PPT slideshow. This PowerPoint slideshow contains every important element that you need for a great pitch. It is not only editable but also available for immediate download and utilization. The color, font size, background, shapes everything can be modified to create your unique presentation layout. Therefore, download it now.

Quarterly IT Security Recognition Program Roadmap Infographics
Presenting our innovatively-structured quarterly it security recognition program roadmap infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Computer Server With Cloud Shape Structure PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Computer Server With Cloud Shape Structure PowerPoint Templates PPT Backgrounds For Slides 0213.Download and present our Business PowerPoint Templates because It will Raise the bar of your Thoughts. They are programmed to take you to the next level. Download and present our Communication PowerPoint Templates because Our PowerPoint Templates and Slides help you pinpoint your timelines. Highlight the reasons for your deadlines with their use. Download our Security PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the target. Go the full distance with ease and elan. Present our Technology PowerPoint Templates because It will get your audience in sync. Download our Success PowerPoint Templates because you can Break through with our PowerPoint Templates and Slides. Bring down the mental barriers of your audience.Use these PowerPoint slides for presentations relating to One computer server with a cloud shape, business, communication, security, technology, success. The prominent colors used in the PowerPoint template are Blue, White, Black.

Computer Cyber Security Icon Infographics PDF
Presenting Computer Cyber Security Icon Infographics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Computer Cyber, Security Icon This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Computer Security Incident Handling Agenda For Cybersecurity Management Slides PDF
Presenting this set of slides with name computer security incident handling agenda for cybersecurity management slides pdf. The topics discussed in these slides are determining roles and responsibilities of senior management and executives who are responsible in risk management, presenting optimize cybersecurity risk framework to senior management and executives. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Agile Delivery Methodology For IT Project Agile Delivery Metrics Performance Ppt Infographics Structure PDF
Listed Here are the metrics used by the organization to measure agile capability on the basis of product performance, security level and user satisfaction. Deliver and pitch your topic in the best possible manner with this agile delivery methodology for IT project agile delivery metrics performance ppt infographics structure pdf. Use them to share invaluable insights on performance, accuracy of planning, resourse consumption, functional coverage, security and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF
This slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Showcasing this set of slides titled Risk Management Methodology In IT Risk Control Strategies Security Ppt Inspiration Background PDF. The topics addressed in these templates are Assessment, Mitigation, Continual Evaluation Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF
This slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Cyber Security Automation Framework Security Automation Stages With Maturity Level Clipart PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Techniques And Strategies To Reduce Security Management Risks Major Reasons For Poor Security Guidelines PDF
This slide shows some of the major reasons for poor security management in the company along with tips in order to resolve the issue.Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks major reasons for poor security guidelines pdf bundle. Topics like outdated software, lack of proper protection, another dangerous aspect can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
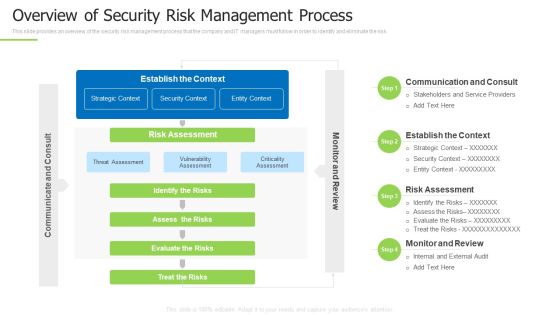
Techniques And Strategies To Reduce Security Management Risks Overview Of Security Risk Background PDF
This slide provides an overview of the security risk management process that the company and IT managers must follow in order to identify and eliminate the risk. Deliver an awe inspiring pitch with this creative techniques and strategies to reduce security management risks overview of security risk background pdf bundle. Topics like identify the risks, strategic context, vulnerability assessment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
 Home
Home