Safety Plan
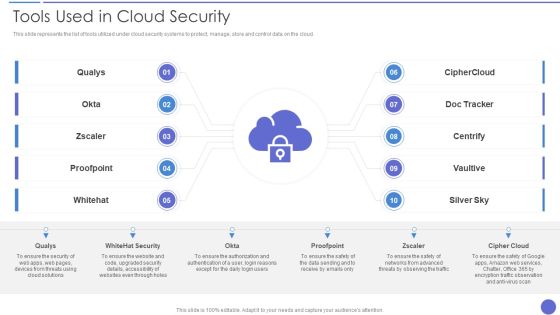
Tools Used In Cloud Security Template PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Presenting Tools Used In Cloud Security Template PDF to provide visual cues and insights. Share and navigate important information on one stages that need your due attention. This template can be used to pitch topics like Qualys, Whitehat Security, Cipher Cloud. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Corporate Security And Risk Management Table Of Contents Corporate Security And Risk Download PDF
Presenting corporate security and risk management table of contents corporate security and risk download pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like current scenario assessment, ensuring physical security, securing firm from natural calamity threats, handling cyber threats to secure digital assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

What Makes Cloud Security Different Diagrams PDF
This slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system. This is a What Makes Cloud Security Different Diagrams PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Developing, Essential Strategy, Cloud Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF
This slide represents the activities through which cyber incident management team can effectively and efficiently detect cyber security incidents. It includes various ways of detecting cyber security incidents such as unusual behavior from privileged user accounts etc. Create an editable CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF that communicates your idea and engages your audience. Whether youre presenting a business or an educational presentation, pre designed presentation templates help save time. CYBER Security Breache Response Strategy Ways To Detect Cyber Security Incidents Sample PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Checklist To Implement Cloud Security In Business Cloud Computing Security IT Ppt Infographic Template Example File
This slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Deliver an awe inspiring pitch with this creative checklist to implement cloud security in business cloud computing security it ppt infographic template example file bundle. Topics like networking, policies and procedures, logging and monitoring, data encryption, security patches and updates can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Credit Card Payment Processing Security Rules PDF
This slide outline the basics of payment processing security to protect business operations and sensitive consumer data. It includes secure data storage, payment data encryption and payment data tokenization. Presenting Credit Card Payment Processing Security Rules PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Secure Data Storage Vault, Payment Data Encryption, Payment Data Tokenization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Corporate Security And Risk Management Table Of Contents Corporate Security Summary PDF
This is a corporate security and risk management table of contents corporate security summary pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring financial assets security, leveraging workforce, budget assessment, dashboard, impact assessment . You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Deploying Cyber Security Incident Response Administration Strategies To Analyze Cyber Security Incidents Template PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Present like a pro with Deploying Cyber Security Incident Response Administration Strategies To Analyze Cyber Security Incidents Template PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Security Patch Management Template Presentation Images
This is a security patch management template presentation images. This is a six stage process. The stages in this process are testing, architecture, quality assurance, analysis, design, synthesis.

Information Security Management Best Practices Themes PDF
This slide presents various best practices for information security governance to effectively manage and mitigate IT risks. It includes key practices such as reflect business objectives, develop and enforce security program, embrace organizations culture, etc. Presenting Information Security Management Best Practices Themes PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Reflect Business Objectives, Spend Resources Effectively, Embrace Organizations Culture. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
Payment Card Security Processing Icon Portrait PDF
Presenting Payment Card Security Processing Icon Portrait PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Payment Card Security, Processing Icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Service Provider Contract Review Agreement Checklist Information PDF
Purpose of this slide is to showcase contract checklist for service provider. It includes involvement of IT team, security specific language, setting benchmarks and auditing vendors. Showcasing this set of slides titled service provider contract review agreement checklist information pdf. The topics addressed in these templates are service provider contract review agreement checklist. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF
This slide represents the key takeaways for the cyber security incident management team after they effectively respond to and manage the cyber attacks experienced by the organization. It includes key lessons learned by organization such as ransomware is here to stay etc. This CYBER Security Breache Response Strategy Key Lessons Learned By Organization From Cyber Security Incident Graphics PDF from Slidegeeks makes it easy to present information on your topic with precision. It provides customization options, so you can make changes to the colors, design, graphics, or any other component to create a unique layout. It is also available for immediate download, so you can begin using it right away. Slidegeeks has done good research to ensure that you have everything you need to make your presentation stand out. Make a name out there for a brilliant performance.
Elements Of Information Technology Security Information Technology Security Ppt Inspiration Icons PDF
This slide represents the network security element of network security and different network security methods such as firewalls, email security, web security, and antivirus software. Presenting elements of information technology security information technology security ppt inspiration icons pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like network security methods, tools, techniques, respond. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Real Time Assessment Of Security Threats Agenda Of Real Time Assessment Of Security Threats Designs PDF
This is a real time assessment of security threats agenda of real time assessment of security threats designs pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like agenda of real time assessment of security threats. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Service Models Disadvantages Of Saas Cloud Computing Layer Designs PDF
This slide depicts the factors such as cloud security, cloud compliance, service levels, architecture, manageability, costs, and support to choose the right cloud service provider.Presenting Cloud Based Service Models Disadvantages Of Saas Cloud Computing Layer Designs PDF to provide visual cues and insights. Share and navigate important information on seven stages that need your due attention. This template can be used to pitch topics like Cloud Security, Manageability, Architecture. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Our Services Maintenance Company Profile Ppt Summary Graphics PDF
This is a our services maintenance company profile ppt summary graphics pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like digital advertising, marketing and analytics, digital care package, security and maintenance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Hard And Soft Facility Management Services Developing Tactical Fm Services Microsoft PDF
This slide highlights hard and soft facility management services which are offered by the company which includes cleaning services, support services, security services, catering services and technical services.The Hard And Soft Facility Management Services Developing Tactical Fm Services Microsoft PDF is a compilation of the most recent design trends as a series of slides. It is suitable for any subject or industry presentation, containing attractive visuals and photo spots for businesses to clearly express their messages. This template contains a variety of slides for the user to input data, such as structures to contrast two elements, bullet points, and slides for written information. Slidegeeks is prepared to create an impression.
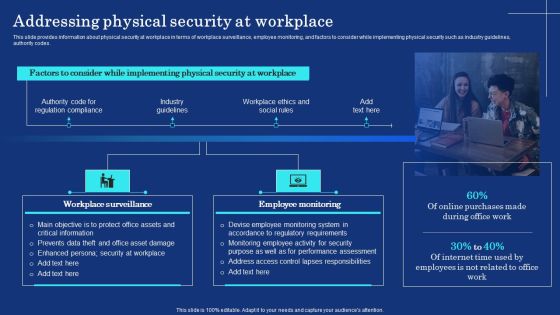
Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF
This slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Create an editable Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Organizational Assets Security Management Strategy Addressing Physical Security At Workplace Mockup PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
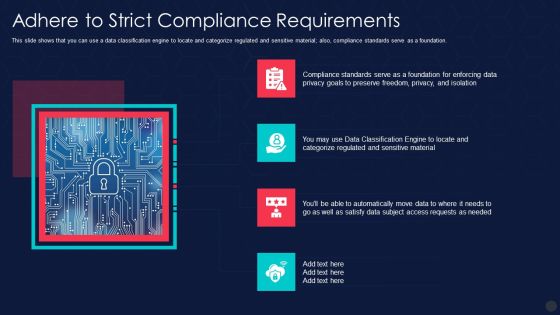
Information Privacy IT Adhere To Strict Compliance Requirements Slides PDF
This slide shows that you can use a data classification engine to locate and categorize regulated and sensitive material also, compliance standards serve as a foundation. Presenting information privacy it adhere to strict compliance requirements slides pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like adhere to strict compliance requirements. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Networking Cloud Computing Security IT Ppt Show Samples PDF
This slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Presenting cloud security checklist networking cloud computing security it ppt show samples pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like security, mechanisms, security, critical data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Table Of Contents Cyber Security Administration In Organization Security Sample PDF
This is a table of contents cyber security administration in organization security sample pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring, financial, assets, security, workforce. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. There are so many reasons you need a IT Security Automation Systems Guide Domain Security Controls That Can Be Automated Sample PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks has constructed Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF
This slide illustrates the roles and responsibilities of the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Explore a selection of the finest Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Cybersecurity Operations Cybersecops Roles And Responsibilities Of Socas A Service Ideas PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Information Technology Solutions Business Profile Major Competitors By Service Ideas PDF
This slide showcases the major competitors by services such as software development services, consulting services and security services.This is a Information Technology Solutions Business Profile Major Competitors By Service Ideas PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Software Development, Consulting Services, Security Services. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF
This slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Boost your pitch with our creative CYBER Security Breache Response Strategy Various Cyber Security Incidents Detected By It Department Demonstration PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Eight Key Steps Of Successful Testing Process Ppt PowerPoint Presentation Model Visuals PDF
Persuade your audience using this eight key steps of successful testing process ppt powerpoint presentation model visuals pdf. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including keyword testing, object driven testing, manual tests. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Privacy IT Accuracy Principle Of Gdpr Law Clipart PDF
This slide depicts the accuracy principle, which emphasizes that you are responsible for all efforts taken to ensure the datas privacy it must be correct and up to date. This is a information privacy it accuracy principle of gdpr law clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like accuracy principle of gdpr law. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
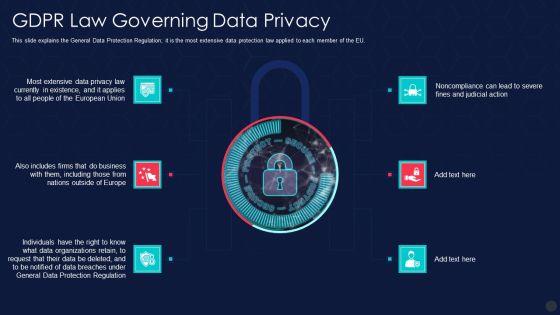
Information Privacy IT Gdpr Law Governing Data Privacy Ideas PDF
This slide explains the General Data Protection Regulation it is the most extensive data protection law applied to each member of the EU. Presenting information privacy it gdpr law governing data privacy ideas pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like gdpr law governing data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Importance Of Data Privacy Professional PDF
This slide illustrates the importance of data privacy in terms of developing trust with customers that value privacy and assisting with data management. Presenting information privacy it importance of data privacy professional pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like importance of data privacy. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Monitor And Detect Abnormal Activity On Sensitive Data Structure PDF
This slide highlights that you will have continuous monitoring and detection of abnormal activities of all the organizations data. Presenting information privacy it monitor and detect abnormal activity on sensitive data structure pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like monitor and detect abnormal activity on sensitive data. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Privacy IT Purpose Limitation Principle Of Gdpr Law Topics PDF
This slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Presenting information privacy it purpose limitation principle of gdpr law topics pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like rpose limitation principle of gdpr law. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
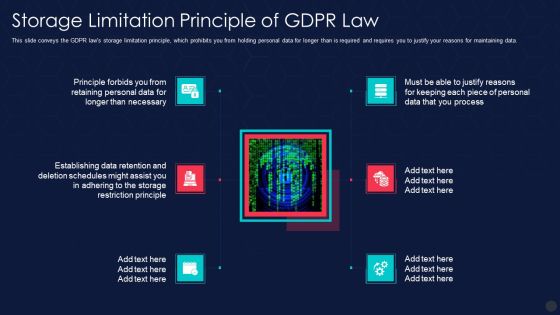
Information Privacy IT Storage Limitation Principle Of Gdpr Law Professional PDF
This slide conveys the GDPR laws storage limitation principle, which prohibits you from holding personal data for longer than is required and requires you to justify your reasons for maintaining data. This is a information privacy it storage limitation principle of gdpr law professional pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like storage limitation principle of gdpr law. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
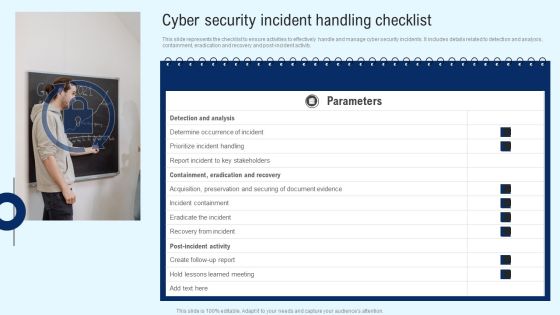
Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF
This slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post-incident activity. This Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cyber Security Incident Cyber Security Incident Handling Checklist Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Implementing Security Management Strategy To Mitigate Risk Table Of Contents Portrait PDF
This is a implementing security management strategy to mitigate risk table of contents portrait pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like suggested coverage for security management plan, essential elements to be included in a security management plan. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Data Encryption Cloud Computing Security IT Ppt Summary Tips PDF
This slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. This is a cloud security checklist data encryption cloud computing security it ppt summary tips pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like safeguard, data servers, network, encryption. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Determine Ideal Tasks For Security Automation Designs PDF
This slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Want to ace your presentation in front of a live audience Our IT Security Automation Systems Guide Determine Ideal Tasks For Security Automation Designs PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Information Security Set Measures For Secure Communication Ppt Outline Slide Download PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a information security set measures for secure communication ppt outline slide download pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like organization, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Introduction To Branchless Banking In Next Generation Payments Ppt Icon Background Designs PDF
This slide covers introduction to branchless banking services offered by banking sector. The purpose of this template is to provide an overview on benefits of using branchless banking services. It includes advantages such as supporting multiple transactions, advanced payment security, contactless payment solutions along with categories covering digital wallets, IVR bill payments, API bill payments and credit card bills. Welcome to our selection of the Introduction To Branchless Banking In Next Generation Payments Ppt Icon Background Designs PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
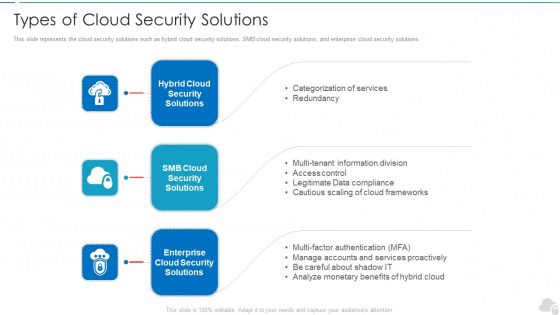
Types Of Cloud Security Solutions Cloud Computing Security IT Ppt Layouts Example PDF
This slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions. This is a types of cloud security solutions cloud computing security it ppt layouts example pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like hybrid cloud security solutions, smb cloud security solutions, enterprise cloud security solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Policies And Procedures Rules PDF
This slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. This is a Cloud Security Checklist Policies And Procedures Rules PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Security, Organization, Security Procedures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it nowC

Evaluation Of HR Security Policy And Procedure Diagrams PDF
Persuade your audience using this Evaluation Of HR Security Policy And Procedure Diagrams PDF. This PPT design covers three stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluation HR Security, Policy Procedure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

SIEM Logging Sources SIEM Services Ppt Inspiration Format PDF
This slide covers the logging sources for SIEM which uses different devices such as security, network, servers, and applications. Presenting siem logging sources siem services ppt inspiration format pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like siem logging sources. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Burp Suite Ethical Hacking Tool Ppt Portfolio Skills PDF
This slide depicts the burp suite ethical hacking tool, including its features such as open source and custom built software, easy to use login sequence recorder, crawl, and scan automation, etc. Presenting burp suite ethical hacking tool ppt portfolio skills pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like security, application, information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Threats Contract Breaches With Clients Cloud Computing Security IT Ppt Ideas Introduction PDF
This slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data. Presenting cloud security threats contract breaches with clients cloud computing security it ppt ideas introduction pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like business, organization, sensitive data stored. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Elements Of IT Security IT Information Security Ppt Background Image PDF
This slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Presenting elements of it security it information security ppt background image pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like integrity, confidentiality, availability. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
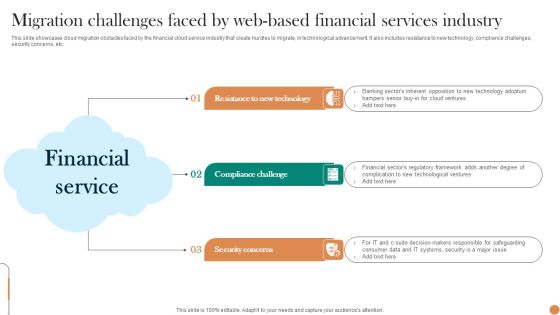
Migration Challenges Faced By Web Based Financial Services Industry Professional PDF
This slide showcases cloud migration obstacles faced by the financial cloud service industry that create hurdles to migrate, in technological advancement. It also includes resistance to new technology, compliance challenges, security concerns, etc. Presenting Migration Challenges Faced By Web Based Financial Services Industry Professional PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Resistance To New Technology, Compliance Challenge, Security Concerns. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF
This slide consists of the major pros and cons of using everything as a service XaaS in business organizations. Elements covered include cost savings, scalability, security, downtime, etc. Presenting Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Cost Savings, Scalability, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Saving Is Depend On Time PowerPoint Templates Ppt Backgrounds For Slides 0513
Activate the drive in your team. Arouse them with our Saving Is Dependent On Time PowerPoint Templates PPT Backgrounds For Slides. Pop the cork with our Money PowerPoint Templates. Let your audience take in the aroma of your thoughts. Drive your team along the road to success. Take the wheel with our Security PowerPoint Templates.
Elements Of Information Technology Security Cloud Security Ppt Icon Gridlines PDF
This slide defines the cloud security element of network security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. This is a elements of information technology security cloud security ppt icon gridlines pdf show pdf template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like elements of information technology security cloud security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
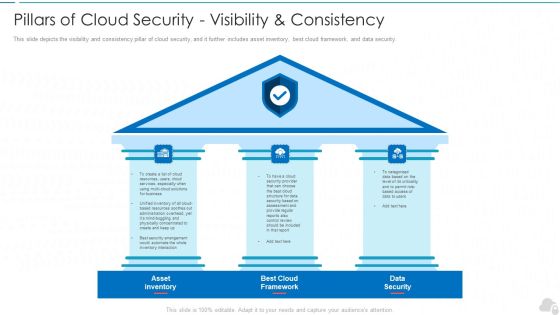
Pillars Of Cloud Security Visibility And Consistency Cloud Computing Security IT Ppt Slide PDF
This slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security. Presenting pillars of cloud security visibility and consistency cloud computing security it ppt slide pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like asset inventory, best cloud framework, data security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Does Cloud Security Work Governance Professional PDF
This slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Presenting How Does Cloud Security Work Governance Professional PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Access Management, Business Continuity Planning, Data Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF
This slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. If your project calls for a presentation, then Slidegeeks is your go to partner because we have professionally designed, easy to edit templates that are perfect for any presentation. After downloading, you can easily edit IT Security Automation Systems Guide Unified Platform Integration For Security Automation Background PDF and make the changes accordingly. You can rearrange slides or fill them with different images. Check out all the handy templates.

SIEM Services Key Features Of SIEM Software Ppt Pictures Background Image PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. This is a siem services key features of siem software ppt pictures background image pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, internal auditing, scalability, security, enrichment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Distribution Service Models Disadvantages Of Iaas Cloud Computing Layer Icons PDF
This slide shows the disadvantages of the IaaS cloud computing layer based on security, maintenance and upgrade, and interoperability issues. This is a Cloud Distribution Service Models Disadvantages Of Iaas Cloud Computing Layer Icons PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security, Interoperability Issues, Maintenance And Upgrade. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Distribution Service Models Disadvantages Of Saas Cloud Computing Layer Sample PDF
This slide represents the disadvantages of the SaaS cloud computing layer, including security, latency issues, dependency on the internet and difficulty between SaaS vendors switching. This is a Cloud Distribution Service Models Disadvantages Of Saas Cloud Computing Layer Sample PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Totally Internet Dependent, Latency Issue, Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF
The slide highlights various challenges faced business while outsourcing workforce to hire top industry talent. It includes key challenges such as devoid of connection, delay in response, security of employee data and loss of experienced HR personnel. Presenting Challenges And Solutions For Workforce Outsourcing For Staffing Services Diagrams PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Lack Collaboration, Slow Response Time, Security Staff Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
 Home
Home