Safety Plan

Real Time Assessment Of Security Threats Fully Managed Service Model Demonstration PDF
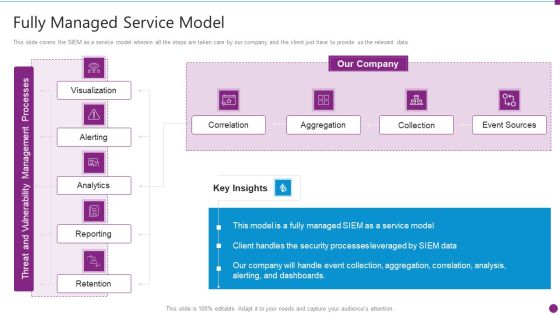
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver an awe inspiring pitch with this creative real time assessment of security threats fully managed service model demonstration pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
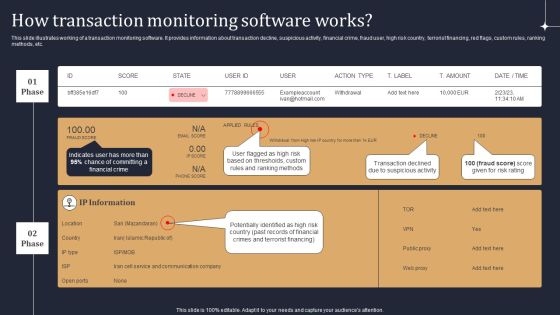
KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF
This slide illustrates working of a transaction monitoring software. It provides information about transaction decline, suspicious activity, financial crime, fraud user, high risk country, terrorist financing, red flags, custom rules, ranking methods, etc. Are you searching for a KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download KYC Transaction Monitoring System Business Security How Transaction Monitoring Software Works Themes PDF from Slidegeeks today.

WAF Introduction Types Of Web Application Firewall Security Models Information PDF
This slide represents the various types of WAF security models, including the whitelist or negative security model, blacklist or positive security model, and hybrid security model. Are you searching for a WAF Introduction Types Of Web Application Firewall Security Models Information PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download WAF Introduction Types Of Web Application Firewall Security Models Information PDF from Slidegeeks today.

Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF
Mentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom.Are you searching for a Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Security Controls To Reduce The Risk Improving Cybersecurity With Incident Pictures PDF from Slidegeeks today.

Two Stage Information Security Management Framework Ppt PowerPoint Presentation File Background Image PDF
Showcasing this set of slides titled two stage information security management framework ppt powerpoint presentation file background image pdf. The topics addressed in these templates are analyze, proposals, security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

ISO 27001 Information Security Management Standard Microsoft PDF
Deliver and pitch your topic in the best possible manner with this ISO 27001 Information Security Management Standard Microsoft PDF. Use them to share invaluable insights on Contextual Requirements, Leadership Requirements, Planning Requirements and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF
This slide depicts the overview of security as a service that helps organizations to outsource cybersecurity services from cloud providers, including its main components such as remote users, web data, internet, and web security as a service.Deliver and pitch your topic in the best possible manner with this Security As A Service Secaas Overview Xaas Cloud Computing Models Ppt PowerPoint Presentation Outline Slide Download PDF. Use them to share invaluable insights on Outsourcing Cybersecurity, Software Solution, Expenses Upkeep and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
Security Information And Event Management Strategies For Financial Audit And Compliance Fully Managed Service Model Portrait PDF
This slide covers the SIEM as a service model wherein all the steps are taken care by our company and the client just have to provide us the relevant data. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance fully managed service model portrait pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF
This template covers working of Facebooks machine learning or algorithms to filter through a massive amount of data and generate a list of qualified, cold prospects.Deliver an awe inspiring pitch with this creative Security And Performance Digital Marketing Targeting Lookalike Audiences For Social Media Prospecting Themes PDF bundle. Topics like Interests Activity, Common Builds, Target Customer can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF
This slide shows best practices on individual and organizational level for preventing cyber terrorism attacks. It include practices such as Choose complicated password, Invest in cyber security plan etc. Pitch your topic with ease and precision using this Individual And Organizational Practices For Digital Terrorism Attacks Microsoft PDF. This layout presents information on Organization, Promote Security, Security Insurance. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Camera System Company Profile Mission Vision And Core Values Demonstration PDF
This slide highlights the security company mission, vision and core values which includes trust, collaboration, service, and innovation as base of core values.Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Mission Vision And Core Values Demonstration PDF bundle. Topics like Peace Of Mind, Collaboration, Innovation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF
This slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Market Positioning With Technology Mockup PDF bundle. Topics like Monitoring, Bluestone Security, Launched Integrated can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Prepare Data Backup For Sensitive Information IT Security IT Ppt Infographics Clipart PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. Deliver an awe inspiring pitch with this creative prepare data backup for sensitive information it security it ppt infographics clipart pdf bundle. Topics like manipulation, secure, disasters, cloud services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF
Deliver an awe inspiring pitch with this creative ISO 27001 Organizational Qualifying Procedure ISO 27001 Information Security Management Standard Mockup PDF bundle. Topics like Leadership Requirements, Contextual Requirements, Planning Requirements can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Real Time Assessment Of Security Threats Estimating Total Cost Of Ownership Of SIEM Icons PDF
This slide covers the total cost of ownership incurred by SIEM services which focuses on the costs of hardware, software, infrastructure, and support.Deliver an awe inspiring pitch with this creative real time assessment of security threats estimating total cost of ownership of siem icons pdf bundle. Topics like hardware, infrastructure, software, support can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF
This slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver and pitch your topic in the best possible manner with this 5G Evolution Architectural Technology Key Security Considerations For 5G For Threat Handling Sample PDF Use them to share invaluable insights on Concerns To Catered, Handling Initiatives, Implementing Middleware and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
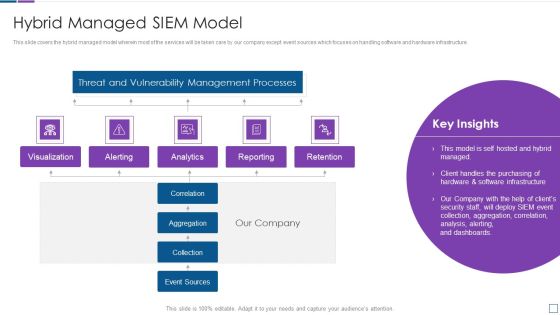
Real Time Assessment Of Security Threats Hybrid Managed SIEM Model Brochure PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver an awe inspiring pitch with this creative real time assessment of security threats hybrid managed siem model brochure pdf bundle. Topics like threat and vulnerability management processes, reporting, retention, correlation, collection can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Intelligence Framework For Application Consumption Case Study 4 Improving Patient Security And Reducing Risk Of Violence Guidelines PDF
The slide provides the case study of a healthcare company that faced the issue of growing risks of patient security and violence in the hospital. The slide provides the solutions offered by the technology company related to risk protection and security effectiveness. Deliver an awe inspiring pitch with this creative cloud intelligence framework for application consumption case study 4 improving patient security and reducing risk of violence guidelines pdf bundle. Topics like power management, building management, security management, security effectiveness, global supervision can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
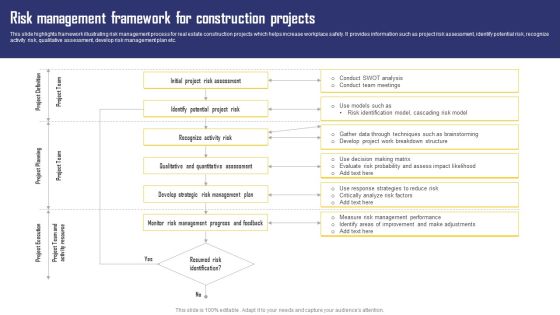
Risk Management Framework For Construction Projects Ideas PDF
This slide highlights framework illustrating risk management process for real estate construction projects which helps increase workplace safety. It provides information such as project risk assessment, identify potential risk, recognize activity risk, qualitative assessment, develop risk management plan etc. Showcasing this set of slides titled Risk Management Framework For Construction Projects Ideas PDF. The topics addressed in these templates are Project Definition, Project Planning, Project Execution. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
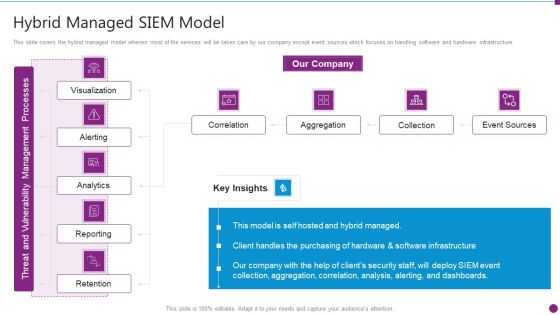
Security Information And Event Management Strategies For Financial Audit And Compliance Hybrid Managed Siem Model Topics PDF
This slide covers the hybrid managed model wherein most of the services will be taken care by our company except event sources which focuses on handling software and hardware infrastructure. Deliver and pitch your topic in the best possible manner with this security information and event management strategies for financial audit and compliance hybrid managed siem model topics pdf. Use them to share invaluable insights on correlation, aggregation, collection, event sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
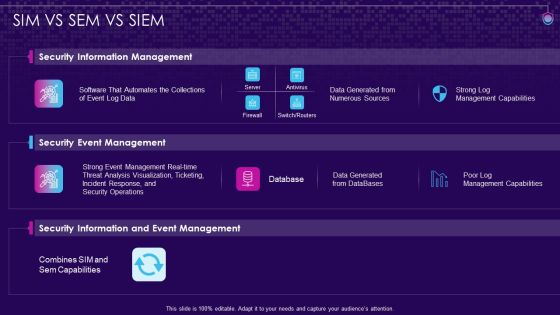
SIM VS SEM VS SIEM SIEM Services Ppt Show Slides PDF
Deliver and pitch your topic in the best possible manner with this sim vs sem vs siem siem services ppt show slides pdf. Use them to share invaluable insights on security information management, security event management, security information and event management and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Security And Protection Security Mechanism Framework Background PDF
This slide showcases policies covered in data protection and information security. The policies includes are BYOD, system security, information rights, PCI DSS, network security, etc.Pitch your topic with ease and precision using this Data Security And Protection Security Mechanism Framework Background PDF. This layout presents information on Information Rights, Retention Policy, Details Processing. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Security Operations Framework To Monitor Security Threats Demonstration PDF
This slide display security operations threat detection and eradication process in order to increase security at all stages of development. It includes new security incident, response to threat, root cause analysis, etc. Pitch your topic with ease and precision using this Security Operations Framework To Monitor Security Threats Demonstration PDF. This layout presents information on Execute Mitigation, Develop, Strategy. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
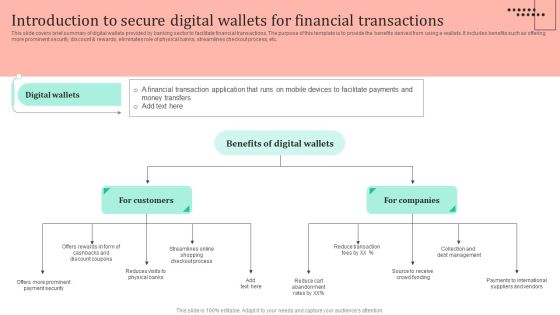
Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF
This slide covers brief summary of digital wallets provided by banking sector to facilitate financial transactions. The purpose of this template is to provide the benefits derived from using e wallets. It includes benefits such as offering more prominent security, discount and rewards, eliminates role of physical banks, streamlines checkout process, etc. Welcome to our selection of the Omnichannel Strategy Implementation For Banking Solutions Introduction To Secure Digital Wallets For Financial Pictures PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cloud Security Assessment Tools Used In Cloud Security Designs PDF
This slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Deliver an awe inspiring pitch with this creative Cloud Security Assessment Tools Used In Cloud Security Designs PDF bundle. Topics like Advanced Threats, Traffic Observation, Details Accessibility can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
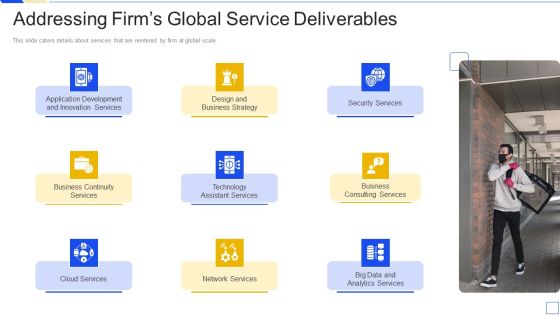
Service Marketing Fundraising Addressing Firms Global Service Deliverables Portrait PDF
This slide caters details about services that are rendered by firm at global scale. Deliver an awe inspiring pitch with this creative service marketing fundraising addressing firms global service deliverables portrait pdf bundle. Topics like business continuity services, technology assistant services, business consulting services, security services, network services can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Control Techniques For Real Estate Project Control Measures To Avoid Excavation And Trenching Injuries Diagrams PDF
Welcome to our selection of the Security Control Techniques For Real Estate Project Control Measures To Avoid Excavation And Trenching Injuries Diagrams PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi-purpose template can be used in various situations. Grab these presentation templates today.

Business Information And Protection Expert For Service Architecture Demonstration PDF
This slide covers business process and security exert for service architecture which includes policy generation framework, process security workbench and transformation unit.Showcasing this set of slides titled Business Information And Protection Expert For Service Architecture Demonstration PDF. The topics addressed in these templates are Business Process, Computer Integrated, Product Information. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SDN Security Architecture Software Defined Networking And Security Guidelines PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and DDoS. It also includes security components for SDN such as infrastructure, controller, API, and application security. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate SDN Security Architecture Software Defined Networking And Security Guidelines PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. Welcome to our selection of the Incident Response Techniques Deployement Cyber Security Incident Response Lifecycle Template PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Cloud Security Assessment Cloud Security Best Practices Infographics PDF
This slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues.Deliver and pitch your topic in the best possible manner with this Cloud Security Assessment Cloud Security Best Practices Infographics PDF Use them to share invaluable insights on Understand Cloud, Review Specifications, Discover Malicious and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF
This slide describes the security in software defined networking, including the security features of SDN architecture such as threat defense, SDN telemetry, segmentation, and ddos. It also includes security components for SDN such as infrastructure, controller, API, and application security. Welcome to our selection of the Empowering Network Agility Through SDN Software Defined Networking And Security Rules PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.
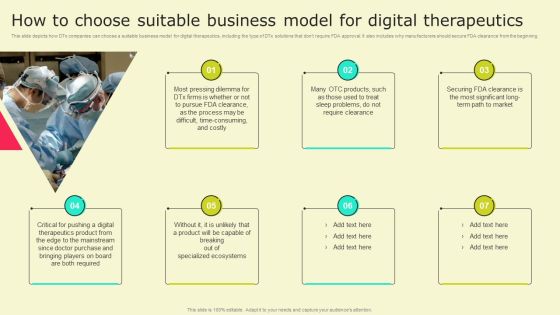
Digital Health Interventions How To Choose Suitable Business Model Digital Therapeutics Template PDF
This slide depicts how DTx companies can choose a suitable business model for digital therapeutics, including the type of DTx solutions that donot require FDA approval. It also includes why manufacturers should secure FDA clearance from the beginning. Are you searching for a Digital Health Interventions How To Choose Suitable Business Model Digital Therapeutics Template PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Digital Health Interventions How To Choose Suitable Business Model Digital Therapeutics Template PDF from Slidegeeks today.

Checklist To Implement Digital Twin Technology Ppt PowerPoint Presentation File Infographics PDF
This slide represents the checklist to implement digital twin technology in the company, including updating data security protocols, managing data quality, and training the team. Are you searching for a Checklist To Implement Digital Twin Technology Ppt PowerPoint Presentation File Infographics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Checklist To Implement Digital Twin Technology Ppt PowerPoint Presentation File Infographics PDF from Slidegeeks today.

Challenges Faced By Shipment Services Companies Diagrams PDF
This slide shows the challenges faced by transportation industry. It includes supply chain integration, digital transformation, proactive cyber security, parking issues and traffic. Pitch your topic with ease and precision using this Challenges Faced By Shipment Services Companies Diagrams PDF. This layout presents information on Online Sales, Proactive Cyber Security, Workforce. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
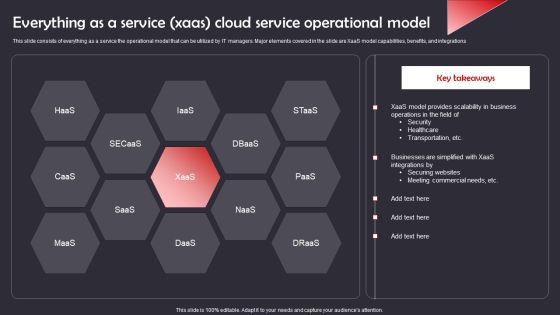
Everything As A Service Xaas Cloud Service Operational Model Mockup PDF
This slide consists of everything as a service the operational model that can be utilized by IT managers. Major elements covered in the slide are XaaS model capabilities, benefits, and integrations. Showcasing this set of slides titled Everything As A Service Xaas Cloud Service Operational Model Mockup PDF. The topics addressed in these templates are Securing Websites, Meeting Commercial Needs, Security, Healthcare . All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Data Processing Cloud Services Icon Infographics PDF
Pitch your topic with ease and precision using this Data Processing Cloud Services Icon Infographics PDF. This layout presents information on Security Compliance, Monitor Visibility, Authentication. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Cios Methodologies To Improve IT Spending Addressing Critical It Budgeting Measures Checklist Introduction PDF
This slide provides information regarding critical IT budgeting measures checklist comprising of categorizing IT expenses, focus on IT security and disaster recovery risks, budget planning for work from home scenario, tax calculation, etc. Deliver an awe inspiring pitch with this creative Cios Methodologies To Improve IT Spending Addressing Critical It Budgeting Measures Checklist Introduction PDF bundle. Topics like Security Disaster, Costs Monitoring, Budget Planning can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Services Model With Service Provider And Consumer Ppt PowerPoint Presentation Gallery Mockup PDF
Pitch your topic with ease and precision using this cloud computing services model with service provider and consumer ppt powerpoint presentation gallery mockup pdf. This layout presents information on security audit, management, service aggregation. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Platform As A Service Model For Service Applications Ppt PowerPoint Presentation Icon Deck PDF
Showcasing this set of slides titled platform as a service model for service applications ppt powerpoint presentation icon deck pdf. The topics addressed in these templates are organizational security, social graphs, service applications. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security And Surveillance Company Profile Security Company Business Model Designs PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security And Surveillance Company Profile Security Company Business Model Designs PDF bundle. Topics like Target Market, Revenue Stream, Cost Structure can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Camera System Company Profile Security Company Business Model Mockup PDF
This slide highlights the business model of home security company which includes target market, revenue stream, cost structure, future plans, products, customer segments, key activities and channels. Deliver an awe inspiring pitch with this creative Security Camera System Company Profile Security Company Business Model Mockup PDF bundle. Topics like Revenue Stream, Customer Relationship, Customer Segments can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Software Testing Service Delivery Excellence Model Mockup PDF
This slide showcases delivery excellence framework for software testing services which helps integrate business processes across diverse technologies. It provides information regarding end to end testing, test automation, data testing and security testing. Showcasing this set of slides titled Software Testing Service Delivery Excellence Model Mockup PDF. The topics addressed in these templates are Performance Testing, Digital Test Assurance, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Business Term Sheet Term Sheet Proposed Investment In Company Name Ltd Ppt File Good PDF
Deliver and pitch your topic in the best possible manner with this business term sheet term sheet proposed investment in company name ltd ppt file good pdf. Use them to share invaluable insights on business, investment, potential, securities, value and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Housing Mortgage Additional Benefits For Home Loan Proposal Ppt Slides Background PDF
Deliver an awe inspiring pitch with this creative housing mortgage additional benefits for home loan proposal ppt slides background pdf bundle. Topics like credit cards, easy security investment can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Improved Digital Expenditure Addressing Critical IT Budgeting Measures Checklist Diagrams PDF
This slide provides information regarding critical IT budgeting measures checklist comprising of categorizing IT expenses, focus on IT security and disaster recovery risks, budget planning for work from home scenario, tax calculation, etc. Deliver and pitch your topic in the best possible manner with this Improved Digital Expenditure Addressing Critical IT Budgeting Measures Checklist Diagrams PDF. Use them to share invaluable insights on Infrastructure Comprises, Budget Planning, Costs Monitoring and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF
This slide covers the grid specifying data risk faced and its mitigation plan. The purpose of this template is to analyze the risk incurred and plans implemented to overcome the same. It also includes elements such as impact, likelihood, metric, threshold, etc.Showcasing this set of slides titled Data Constraints Information Limitation And Risk Management Matrix For Analyzing Data Loss Brochure PDF. The topics addressed in these templates are Data Distribution, Secure Computation, Verifiable Computation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

SIEM Services How SIEM Works Ppt Microsoft PDF
Deliver an awe inspiring pitch with this creative siem services how siem works ppt microsoft pdf bundle. Topics like network device, operating systems, security device, vulnerability and threats can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Framework Of Information IT Security Action Program Slides PDF
This slide focuses on information security action program framework which covers governance plan, security standards, stakeholder engagement and operational management to manage risks, handling threat, data security management, etc.Showcasing this set of slides titled Framework Of Information IT Security Action Program Slides PDF The topics addressed in these templates are Security Standards, Data Protection, Response Structure All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Security Risk Management Assessment Checklist Brochure PDF
This slide shows a security risk management assessment checklist with multiple categories. Deliver and pitch your topic in the best possible manner with this security risk management assessment checklist brochure pdf. Use them to share invaluable insights on security, management, requirements, organizations and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Resilience Assurance Model Slides PDF
The following slide illustrates cybersecurity assurance framework aimed at propagating principles, objectives to be achieved by regulated agencies. It covers four domains leadership and governance, risk management and compliance, operations and technology with third party considerations. Pitch your topic with ease and precision using this Cyber Security Resilience Assurance Model Slides PDF. This layout presents information on Awareness, Training Programs, Project Management. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
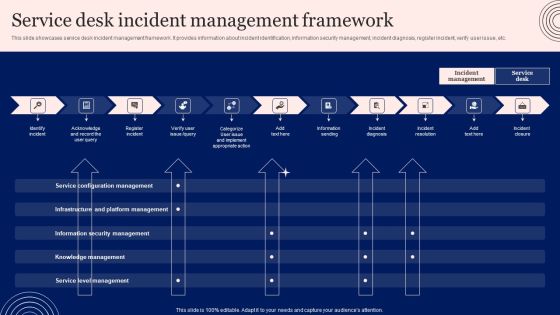
Implementing Advanced Service Help Desk Administration Program Service Desk Incident Management Framework Pictures PDF
This slide showcases service desk incident management framework. It provides information about incident identification, information security management, incident diagnosis, register incident, verify user issue, etc. Find a pre-designed and impeccableImplementing Advanced Service Help Desk Administration Program Service Desk Incident Management Framework Pictures PDF. The templates can ace your presentation without additional effort. You can download these easy-to-edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.

Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF
This slide outlines the practice of protecting organizations crucial data in accordance with the companys law and industry standards. the respective policies include internet access, VPN, firewall rules, wireless LAN, and remote connection. Showcasing this set of slides titled Network Cyber Security Assessment Policy To Secure Business Data Microsoft PDF. The topics addressed in these templates are Internet Access Policy, Firewall Rules Policy, Wireless LAN Policy, Remote Connection Policy. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
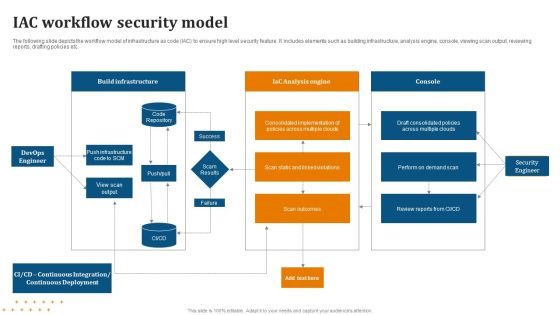
IAC Workflow Security Model Diagrams PDF
Showcasing this set of slides titled IAC Workflow Security Model Diagrams PDF. The topics addressed in these templates are Workflow, Security Model. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
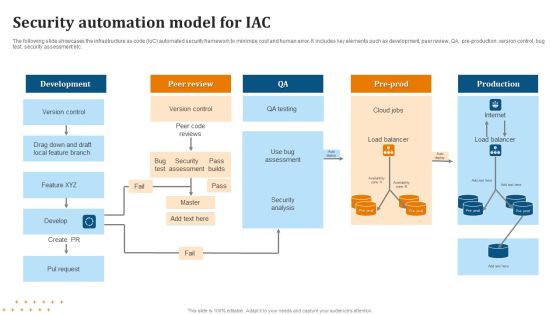
Security Automation Model For IAC Summary PDF
Pitch your topic with ease and precision using this Security Automation Model For IAC Summary PDF. This layout presents information on Security Automation, Model For IAC . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Business Data Protection Security Mechanism Portrait PDF
This slide exhibits broad categories in data protection which are traditional data protection, data security and privacy. It further includes data retention, backup, preventing data loss, risk monitoring, data governance, third party contracts, etc.Showcasing this set of slides titled Business Data Protection Security Mechanism Portrait PDF. The topics addressed in these templates are Data Retention, Physical Infrastructure, Date Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
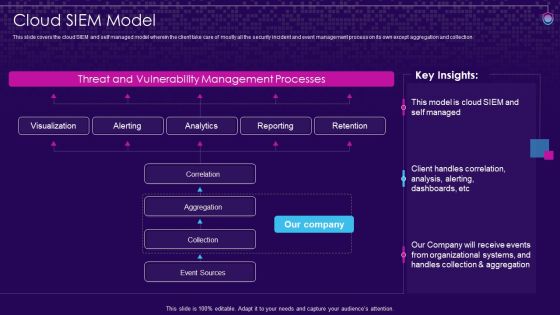
SIEM Services Cloud SIEM Model Ppt Outline Aids PDF
This slide covers the cloud SIEM and self managed model wherein the client take care of mostly all the security incident and event management process on its own except aggregation and collection. Deliver an awe inspiring pitch with this creative siem services cloud siem model ppt outline aids pdf bundle. Topics like aggregation, correlation, collection, event sources can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Four Computer Security Threats Rules PDF
This slide shows the 4 threats to cyber security. It includes phishing attacks, cloud jacking, IoT devices and insider threats.Pitch your topic with ease and precision using this Four Computer Security Threats Rules PDF This layout presents information on Data Manipulation, Attacker Attempts, Sensitive Information It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF
This slide represents the flow chart representing the detection and reaction to cyber security incidents, determination of their scope and risk and reduction of likelihood of incident from reoccurring. It starts with incident declaration and ends with system recovery. Coming up with a presentation necessitates that the majority of the effort goes into the content and the message you intend to convey. The visuals of a PowerPoint presentation can only be effective if it supplements and supports the story that is being told. Keeping this in mind our experts created CYBER Security Breache Response Strategy Cyber Security Incident Response Process Flow Chart Background PDF to reduce the time that goes into designing the presentation. This way, you can concentrate on the message while our designers take care of providing you with the right template for the situation.

 Home
Home