Safety Management

Six Months Cyber Security Recognition Training Program Roadmap Introduction
We present our six months cyber security recognition training program roadmap introduction. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched six months cyber security recognition training program roadmap introduction in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
Three Months Cyber Security Recognition Training Program Roadmap Icons
We present our three months cyber security recognition training program roadmap icons. This PowerPoint layout is easy-to-edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well-researched three months cyber security recognition training program roadmap icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
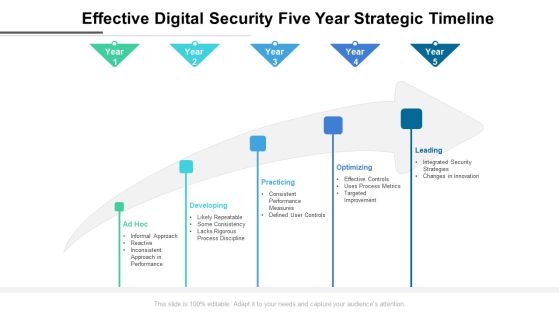
Effective Digital Security Five Year Strategic Timeline Formats
We present our effective digital security five year strategic timeline formats. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched effective digital security five year strategic timeline formats in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

3 Months Action Plan Advantage Roadmap For Cyber Security Inspiration
We present our 3 months action plan advantage roadmap for cyber security inspiration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 3 months action plan advantage roadmap for cyber security inspiration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

6 Months Action Plan Advantage Roadmap For Cyber Security Diagrams
We present our 6 months action plan advantage roadmap for cyber security diagrams. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched 6 months action plan advantage roadmap for cyber security diagrams in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Half Yearly Action Plan Advantage Roadmap For Cyber Security Themes
We present our half yearly action plan advantage roadmap for cyber security themes. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched half yearly action plan advantage roadmap for cyber security themes in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
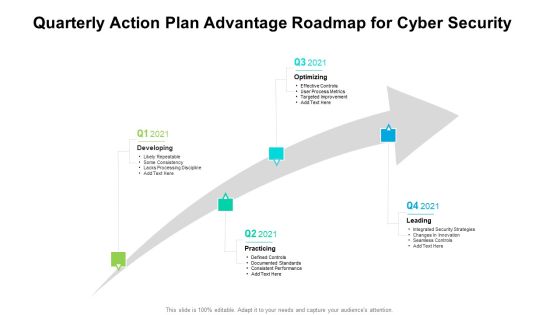
Quarterly Action Plan Advantage Roadmap For Cyber Security Sample
We present our quarterly action plan advantage roadmap for cyber security sample. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly action plan advantage roadmap for cyber security sample in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
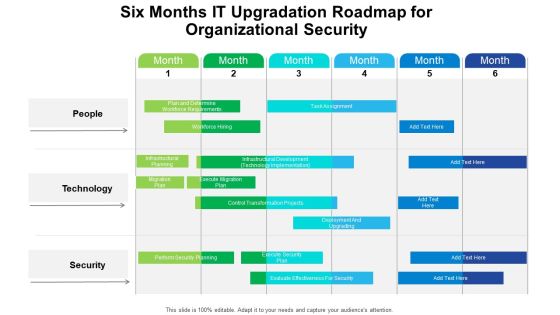
Six Months IT Upgradation Roadmap For Organizational Security Structure
We present our six months it upgradation roadmap for organizational security structure. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months it upgradation roadmap for organizational security structure in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cyber Security Awareness Trends In 2022 Diagrams PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Presenting Cyber Security Awareness Trends In 2022 Diagrams PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Malware Ransomware, Advanced Challenging, Malware Ransomware. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security Roadmap For Data Privacy Implementation Information PDF
This slide depicts the roadmap for data privacy implementation that includes hiring DPO as per GDPR requirement, also checking privacy threats within and outside the organization. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Information Security Roadmap For Data Privacy Implementation Information PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Information Security Roadmap For Data Privacy Implementation Information PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Cyber Security Awareness Trends In 2023 Ppt Graphics PDF
The purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Cyber Security Awareness Trends In 2023 Ppt Graphics PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.
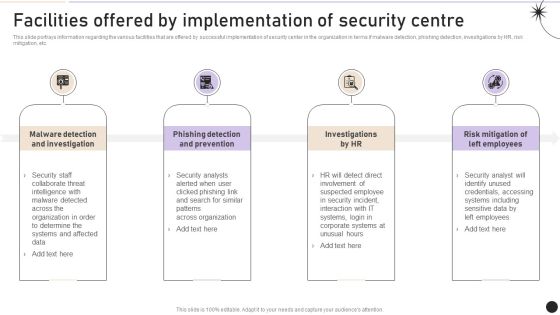
Facilities Offered By Implementation Of Security Centre Topics PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Slidegeeks is here to make your presentations a breeze with Facilities Offered By Implementation Of Security Centre Topics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Substructure Segment Analysis 4 Dimensions Of Infrastructure Security Ppt Portfolio
This is a substructure segment analysis 4 dimensions of infrastructure security ppt portfolio template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like people, data, applications, infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Framework Of IT Security Awareness Training Program Information PDF
This slide covers framework of cybersecurity awareness training program. It involves five steps such as analyse, plan, deploy, measure and optimize. Presenting Framework Of IT Security Awareness Training Program Information PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Analyze, Plan, Deploy, Measure, Optimize. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF
This slide defines the web attack target and defense measures. It includes information related to the attacks target, attacks description and defense measures. Showcasing this set of slides titled Cyber Security Attack Target And Defense Measures Ppt Infographic Template Background Image PDF. The topics addressed in these templates are Attack Target, Defense Measures, End System, Control Plane. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Omnichannel Banking Services Platform Techniques To Optimize API Bill Payment Option For Customers Demonstration PDF
This slide covers strategies to improve performance of application programming interface technology. It includes strategies such as reducing payloads, use of faster networks, API caching, advanced security applications along with action steps to be taken and impact of these practices. Present like a pro with Omnichannel Banking Services Platform Techniques To Optimize API Bill Payment Option For Customers Demonstration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF
Mentioned slide displays a five-day employee upskilling training program that company will use to provide an in-dept details about information security program activities and deliverables. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Employee Upskilling Training Program Microsoft PDF bundle. Topics like Assess Security, Gap Analysis, Gap Initiatives can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Current State Of Security Automation With Projected Development Slides PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download IT Security Automation Systems Guide Different Security Automation Tools With Pros And Cons Summary PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

5 Kpis To Monitor And Track Network Service Assessment Information PDF
Mentioned slide outlines various kpis which can be used by IT reps to monitor network performance. The kpis mentioned in the template are latency, network jitter, packet loss, throughput and mean opinion score. It also covers information about objective, strategies implemented and actual performance of each kpis. Showcasing this set of slides titled 5 Kpis To Monitor And Track Network Service Assessment Information PDF. The topics addressed in these templates are Strategies Implemented, Network Security, Quality. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. There are so many reasons you need a Prevention Of Information Comparison Of Various Security Awareness Training Software Template PDF. The first reason is you cant spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
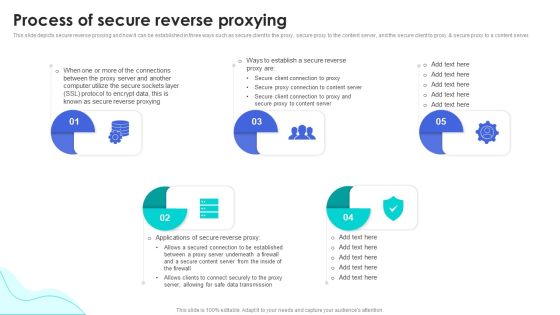
Reverse Proxy Web Server Process Of Secure Reverse Proxying Ppt Gallery Themes PDF
This slide depicts secure reverse proxying and how it can be established in three ways such as secure client to the proxy, secure proxy to the content server, and the secure client to proxy and secure proxy to a content server. Make sure to capture your audiences attention in your business displays with our gratis customizable Reverse Proxy Web Server Process Of Secure Reverse Proxying Ppt Gallery Themes PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

IT Services And Consulting Company Profile Case Study Approach Demonstration PDF
This slide shows the case study which includes challenge faced by client in establishing cloud platform to access applications on demand that our company considered and offered high tech service to reduce cost incurred by client.This is a IT Services And Consulting Company Profile Case Study Approach Demonstration PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Deliver Infrastructure, Secure Information, Applications On Demand You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF
This slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely.Deliver and pitch your topic in the best possible manner with this Secure Client Connection To Proxy And Secure Proxy Connection To Content Server Reverse Proxy For Load Balancing Rules PDF. Use them to share invaluable insights on Server Outside, Between Server, Situation Works and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cyber Security Attack On Web Applications Ppt Outline Files PDF
This slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Presenting Cyber Security Attack On Web Applications Ppt Outline Files PDF to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including Password Attack, Session Hijacking Attacks, Eavesdropping Attack. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Key Components Of Grid Computing Security Structure PDF
This slide talks about the security component of a grid computing network and how it protects the system by offering authentication and authorization processes. It also contains the OpenSSL deployment that permit users to execute operations within the grid. Welcome to our selection of the Key Components Of Grid Computing Security Structure PDF. These are designed to help you showcase your creativity and bring your sphere to life. Planning and Innovation are essential for any business that is just starting out. This collection contains the designs that you need for your everyday presentations. All of our PowerPoints are 100 percent editable, so you can customize them to suit your needs. This multi purpose template can be used in various situations. Grab these presentation templates today.

Incident Response Techniques Deployement Strategies To Analyze Cyber Security Incidents Sample PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks is here to make your presentations a breeze with Incident Response Techniques Deployement Key Parameters To Select Cyber Security Containment Strategy Information PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Amrs In Autonomous Security Robots Asrs Inspiration PDF
This slide describes the application of autonomous security robots to help security personnel. AMRs are also beneficial for cutting the high personnel costs and a thorough inspection of the incidents if anything suspicious is found. Boost your pitch with our creative Amrs In Autonomous Security Robots Asrs Inspiration PDF. Deliver an awe inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Access Regulations Technology Half Yearly Roadmap With Security Solution Guidelines
Presenting the access regulations technology half yearly roadmap with security solution guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
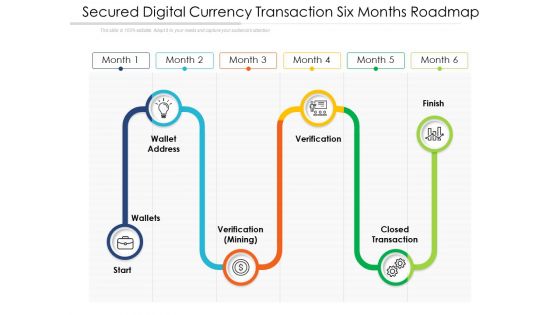
Secured Digital Currency Transaction Six Months Roadmap Guidelines
Presenting the secured digital currency transaction six months roadmap guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Five Year Individual Data Security Career Roadmap Guidelines
Presenting the five year individual data security career roadmap guidelines. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
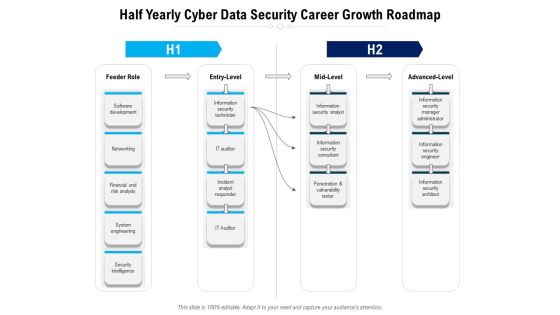
Half Yearly Cyber Data Security Career Growth Roadmap Topics
Presenting the half yearly cyber data security career growth roadmap topics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
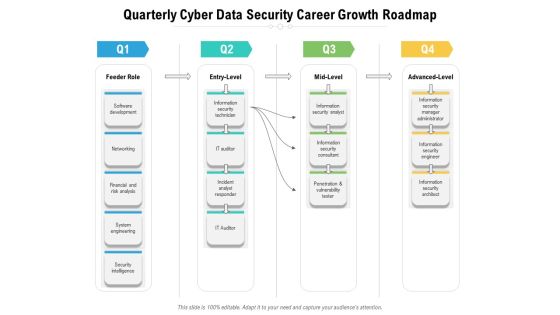
Quarterly Cyber Data Security Career Growth Roadmap Infographics
Presenting the quarterly cyber data security career growth roadmap infographics. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Individual Data Security Career Roadmap Slides
Presenting the six months individual data security career roadmap slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Individual Data Security Career Roadmap Inspiration
Presenting the three months individual data security career roadmap inspiration. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Plan Quarterly Roadmap With Multiple Phases Download
Presenting the cloud computing security plan quarterly roadmap with multiple phases download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Cloud Computing Security Six Months Roadmap With Deployment Plan Themes
Presenting the cloud computing security six months roadmap with deployment plan themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
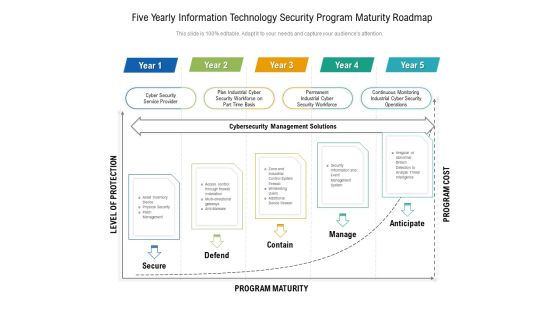
Five Yearly Information Technology Security Program Maturity Roadmap Information
Presenting the five yearly information technology security program maturity roadmap information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Quarterly Information Technology Security Roadmap For Continuous Threat Analysis Download
Presenting the quarterly information technology security roadmap for continuous threat analysis download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
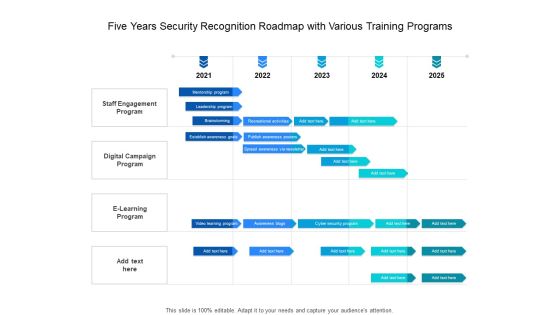
Five Years Security Recognition Roadmap With Various Training Programs Slides
Presenting the five years security recognition roadmap with various training programs slides. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
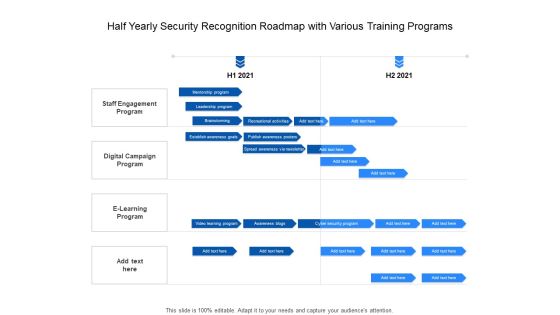
Half Yearly Security Recognition Roadmap With Various Training Programs Themes
Presenting the half yearly security recognition roadmap with various training programs themes. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
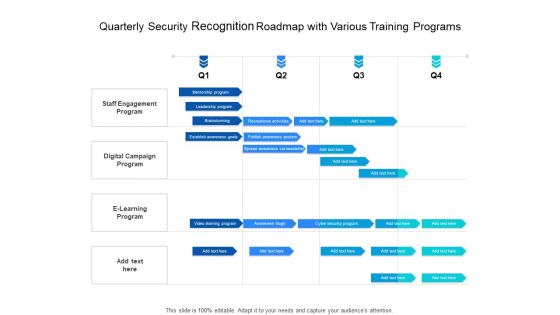
Quarterly Security Recognition Roadmap With Various Training Programs Download
Presenting the quarterly security recognition roadmap with various training programs download. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Six Months Security Recognition Roadmap With Various Training Programs Summary
Presenting the six months security recognition roadmap with various training programs summary. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Three Months Security Recognition Roadmap With Various Training Programs Elements
Presenting the three months security recognition roadmap with various training programs elements. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Effective Digital Security Six Months Strategic Timeline Information
Presenting the effective digital security six months strategic timeline information. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Five Year IT Upgradation Roadmap For Organizational Security Rules
Presenting the five year it upgradation roadmap for organizational security rules. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Core Pillars Of Effective Smart Phone Security Policy Slides PDF
This slide shows essential components of phone security policy. The purpose of this strategy is to highlight main elements that should be considered for framing security policy. It include pillars such as security policy, IT security process and people training, etc. Persuade your audience using this Core Pillars Of Effective Smart Phone Security Policy Slides PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Security Policy, IT Security Process, New Security Products. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Sample Network Security Diagram Ppt Example Of Ppt
This is a sample network security diagram ppt example of ppt. This is a six stage process. The stages in this process are network security, analyse, plan, design, implement, operate, optimize.

Architect Trade Cyber Security Data Ppt PowerPoint Presentation Gallery Layouts
This is a architect trade cyber security data ppt powerpoint presentation gallery layouts. This is a four stage process. The stages in this process are architect trade, cyber security data.

Computer Security Ppt PowerPoint Presentation Complete Deck With Slides
This is a computer security ppt powerpoint presentation complete deck with slides. This is a one stage process. The stages in this process are computer security, business, planning, strategy, marketing.

Technology Transformation Seven Basic Goals Ppt PowerPoint Presentation Ideas Images PDF
Persuade your audience using this technology transformation seven basic goals ppt powerpoint presentation ideas images pdf. This PPT design covers seven stages, thus making it a great tool to use. It also caters to a variety of topics including safeguarding digital resources cyber threats, technology optimization to push faster and respond to changes, technology optimization more productive, secure, track and react to conditions real time, optimizing investment protection to reduce resources and administration, ensuring threats handled and fully complied security, build modern business plan grabbing new opportunities. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
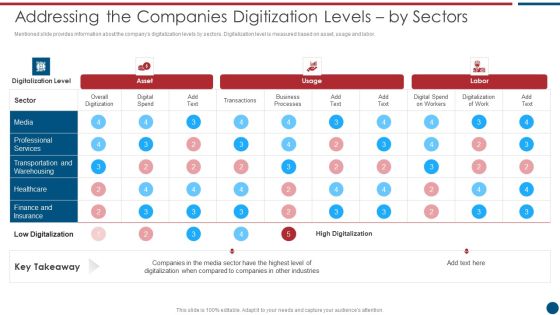
Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF
Mentioned slide provides information about the companys digitalization levels by sectors. Digitalization level is measured based on asset, usage and labor. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Addressing The Companies Digitization Levels By Sectors Infographics PDF bundle. Topics like Digital Spend, Digitalization Level, Business Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Security Analysis Ppt PowerPoint Presentation Infographic Template Shapes
This is a security analysis ppt powerpoint presentation infographic template shapes. This is a one stage process. The stages in this process are open, high, low, sales, ebidta.

Thank You Computer Security Ppt PowerPoint Presentation Outline Guidelines
This is a thank you computer security ppt powerpoint presentation outline guidelines. This is a one stage process. The stages in this process are thank you.
Thank You It Security Ppt PowerPoint Presentation Outline Infographics
This is a thank you it security ppt powerpoint presentation outline infographics. This is a one stage process. The stages in this process are thank you.
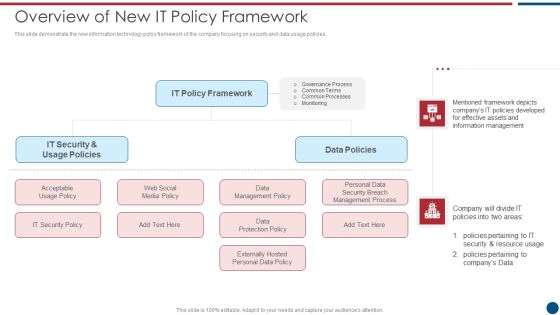
Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF
This slide demonstrate the new information technology policy framework of the company focusing on security and data usage policies. Presenting Risk Based Procedures To IT Security Overview Of New IT Policy Framework Guidelines PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like IT Policy, Data Policies, IT Security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
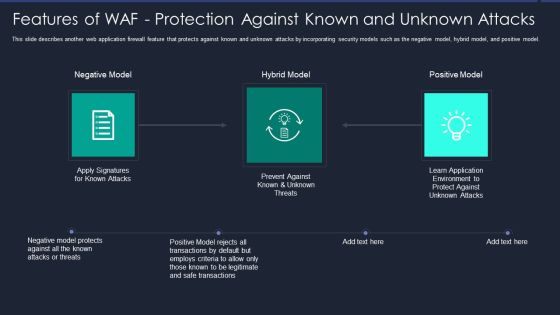
Web App Firewall Services IT Features Of WAF Protection Against Known Clipart PDF
This slide describes another web application firewall feature that protects against known and unknown attacks by incorporating security models such as the negative model, hybrid model, and positive model. Presenting web app firewall services it features of waf protection against known clipart pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like negative model, hybrid model, positive model. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
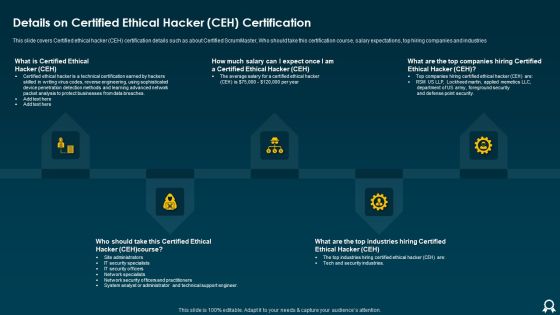
IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF
This slide covers Certified ethical hacker CEH certification details such as about Certified ScrumMaster, Who should take this certification course, salary expectations, top hiring companies and industries. This is a IT Data Services Certification Programs Details On Certified Ethical Hacker CEH Certification Brochure PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Average Salary, Point Security, Methods. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Based Service Models Cloud Computing In Manufacturing Industry Ideas PDF
This slide describes the usages of cloud computing in the manufacturing industry, including cyber security, cloud computing, big data, autonomous robots, augmented reality, simulation, etc.Presenting Cloud Based Service Models Cloud Computing In Manufacturing Industry Ideas PDF to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like Cloud Computing, Augmented Reality, Additive Manufacturing. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

General Corporate Matters Ppt PowerPoint Presentation Infographics Slideshow
This is a general corporate matters ppt powerpoint presentation infographics slideshow. This is a four stage process. The stages in this process are point, lists of all security holders, list of current officers and directors.

Current State Of Security Automation With Projected Development Rules PDF
This slide highlights the current state of security automation in the pie chart format. It includes projected development of security automation and state of security automation. If you are looking for a format to display your unique thoughts, then the professionally designed Current State Of Security Automation With Projected Development Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Current State Of Security Automation With Projected Development Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

 Home
Home