AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Safety Management
Safety Management

CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets.This is a Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identifying Internal, Allocating Vulnerability, Assessing Level. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
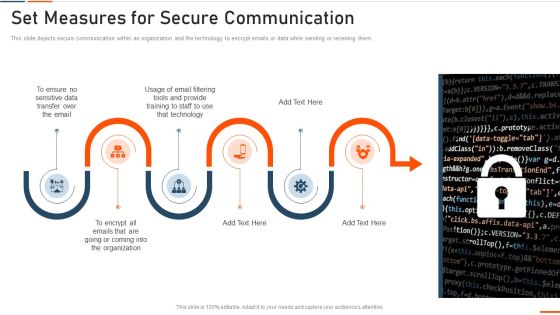
Information Technology Security Set Measures For Secure Communication Ppt Professional Portrait PDF
This is a information technology security set measures for secure communication ppt professional portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, transfer, technology, training, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Profits Of Our Products With New Services Powerpoint Slides Design
This is a profits of our products with new services powerpoint slides design. This is a eight stage process. The stages in this process are social security, peaks and bonuses, pay raise, employees allowance, meal breaks, paid vacation, health insurance, achievement award.
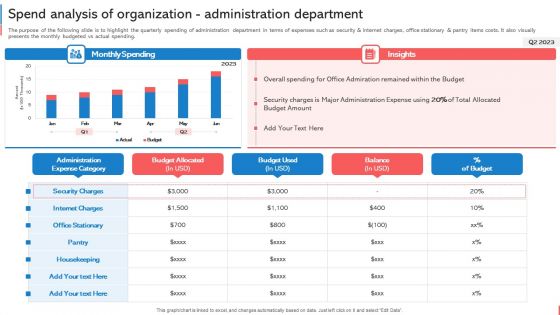
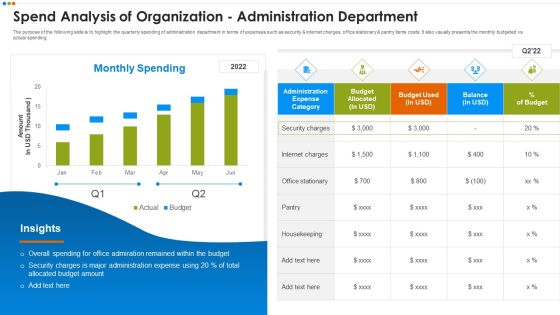
Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending. This Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF
This slide represents the overview of the software development life cycle, including its goal, international standard, way of creating, designing, and developing software.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF.

Regulatory Compliance Traceability Matrix For Cloud Environment Microsoft PDF
This slide outlines the regulatory compliance matrix for the cloud environment. The purpose of this slide is to share the standards cloud service providers need to include for maintaining information security. The organizations include COBIT, FedRAMP, NESA, NIST, and SOX. Showcasing this set of slides titled Regulatory Compliance Traceability Matrix For Cloud Environment Microsoft PDF. The topics addressed in these templates are Organization Standards, Status, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Golden Keys On Coins Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Golden Keys On Coins Security PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Money PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Use our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Present our Shapes PowerPoint Templates because Your audience will believe you are the cats whiskers.Use these PowerPoint slides for presentations relating to Golden keys on coins, Money, Finance, Business, Success, Security. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
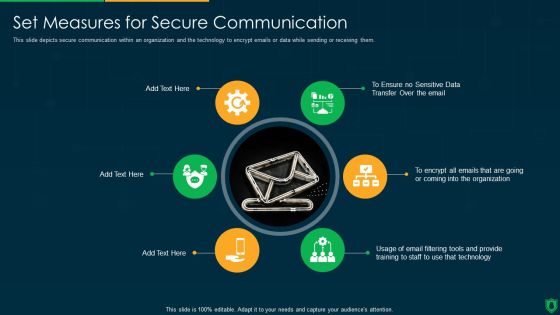
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration Security And Operational Tasks Maintenance Checklist Diagrams PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security and process integration security and operational tasks maintenance checklist diagrams pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
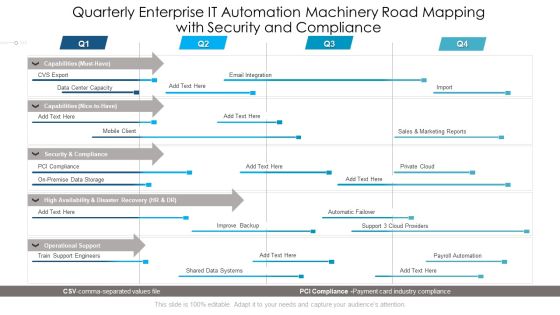
Quarterly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Diagrams
Presenting our innovatively structured quarterly enterprise it automation machinery road mapping with security and compliance diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Data Breach Prevention Recognition Security Training Program Frameworks Mockup PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
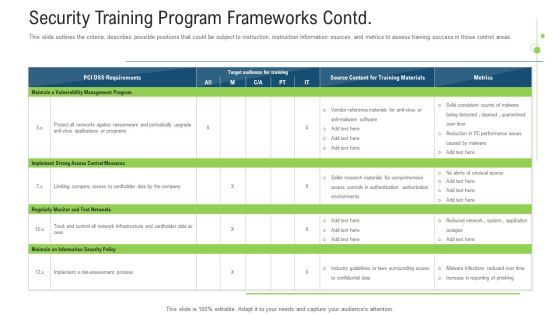
Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Service Architecture And Delivery Process For Business Transformation Topics PDF
This slide includes the service architecture process enabling the development of applications that are easier to handle and more secure. These steps help to make software components reusable and efficient. Presenting Service Architecture And Delivery Process For Business Transformation Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Govern Plan Service Products, Direct Plan Resources, Supply Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. This is a Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Detection Operation Controls, Preventive Operation Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Where Is The Gap In Security Programs Hacking Prevention Awareness Training For IT Security Diagrams PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a where is the gap in security programs hacking prevention awareness training for it security diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
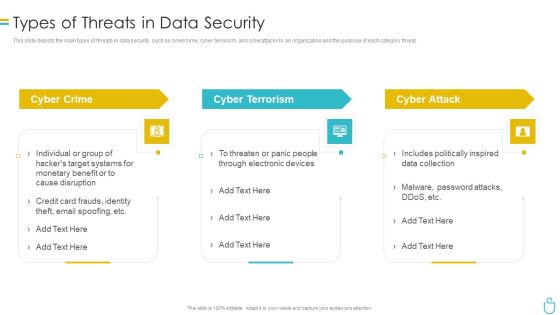
Information Security Types Of Threats In Data Security Ppt Layouts File Formats PDF
This slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a information security types of threats in data security ppt layouts file formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

IT Security Automation Systems Guide Security Automation Integrates Tools Systems And Processes Graphics PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Slidegeeks is here to make your presentations a breeze with IT Security Automation Systems Guide Security Automation Integrates Tools Systems And Processes Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF
This slide consists of the major pros and cons of using everything as a service XaaS in business organizations. Elements covered include cost savings, scalability, security, downtime, etc. Presenting Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Cost Savings, Scalability, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Big Data Security Model Ppt Presentations
This is a big data security model ppt presentations. This is a three stage process. The stages in this process are security model, confidentiality, availability, integrity.

Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.

Software Testing Service Delivery Excellence Model Mockup PDF
This slide showcases delivery excellence framework for software testing services which helps integrate business processes across diverse technologies. It provides information regarding end to end testing, test automation, data testing and security testing. Showcasing this set of slides titled Software Testing Service Delivery Excellence Model Mockup PDF. The topics addressed in these templates are Performance Testing, Digital Test Assurance, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Present like a pro with Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Business Data Protection Security Mechanism Portrait PDF
This slide exhibits broad categories in data protection which are traditional data protection, data security and privacy. It further includes data retention, backup, preventing data loss, risk monitoring, data governance, third party contracts, etc.Showcasing this set of slides titled Business Data Protection Security Mechanism Portrait PDF. The topics addressed in these templates are Data Retention, Physical Infrastructure, Date Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Picture Of Cyber Security Background Ppt PowerPoint Presentation Layouts Layout
Presenting this set of slides with name picture of cyber security background ppt powerpoint presentation layouts layout. This is a one stage process. The stage in this process is picture of cyber security background. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
System Security Vector Icon Ppt PowerPoint Presentation Model Templates
Presenting this set of slides with name system security vector icon ppt powerpoint presentation model templates. This is a four stage process. The stages in this process are system security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security System Image Ppt PowerPoint Presentation Styles Microsoft PDF
Presenting this set of slides with name cyber security system image ppt powerpoint presentation styles microsoft pdf. This is a three stage process. The stages in this process are cyber security system image. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Get a simple yet stunning designed IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
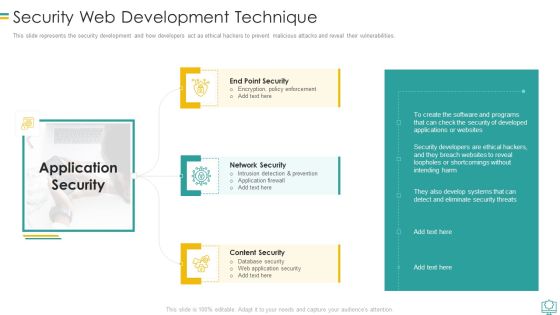
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF Use them to share invaluable insights on Accessible Within Organization, Individual System, Accessible To Key Shareholders and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security How Is Automation Used In Data Security Ppt Model Graphics Template PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting information security how is automation used in data security ppt model graphics template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
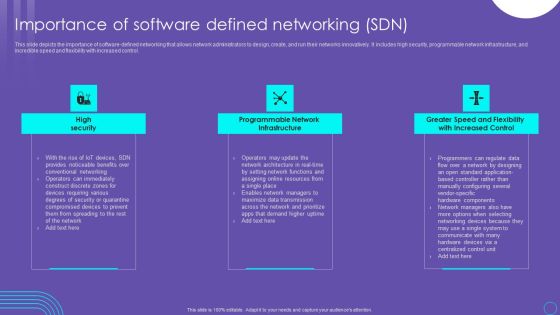
SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF
This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Are you searching for a SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF from Slidegeeks today.
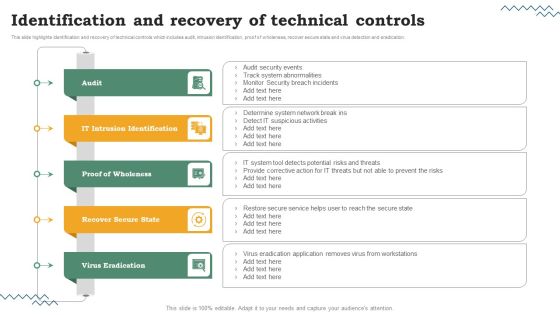
Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Slidegeeks is here to make your presentations a breeze with Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF
This slide outlines the driving trends for security operations modernization. The purpose of this slide is to highlight the leading trends that drive the modernization of security operations centers. The main drivers include cloud platform coverage, a shift to identify-centric security, IoT and OT coverage, etc. Present like a pro with Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart
With Our Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart Powerpoint Templates You Will Be Doubly Sure. They Possess That Stamp Of Authority. Our Security Powerpoint Templates Do It In Double Quick Time. Speed Up The Process In A Tangible Way.
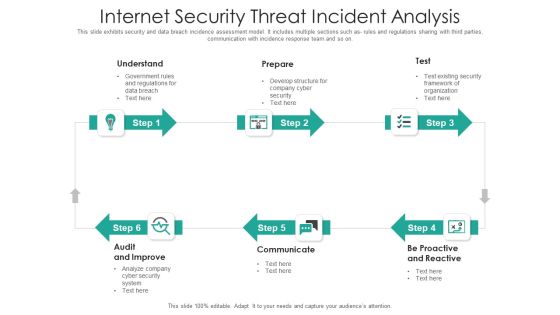
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
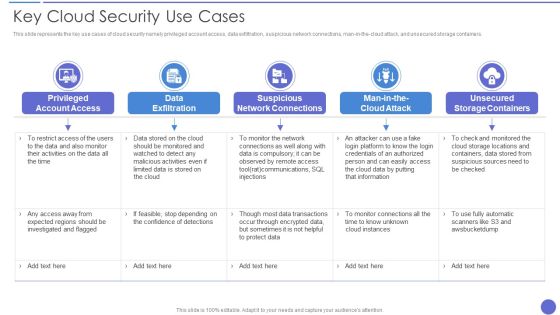
Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Architecture Of Google Cloud Service Platform Professional PDF
This slide showcases google cloud platform service architecture. This further includes operational excellence, security, privacy, and compliance, reliability, cost optimization and performance optimization. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Architecture Of Google Cloud Service Platform Professional PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Three Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Sample
Presenting our jaw dropping three months enterprise it automation machinery road mapping with security and compliance sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
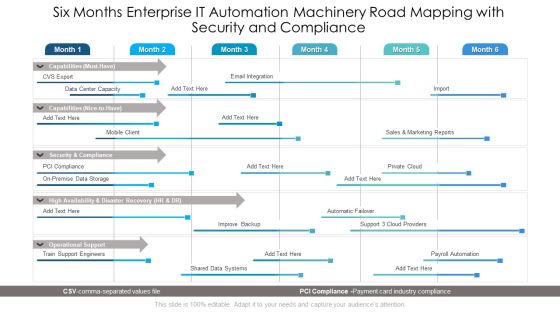
Six Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Professional
We present our six months enterprise it automation machinery road mapping with security and compliance professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise it automation machinery road mapping with security and compliance professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Vector Icon Ppt PowerPoint Presentation Inspiration
Presenting this set of slides with name cyber security vector icon ppt powerpoint presentation inspiration. This is a one stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
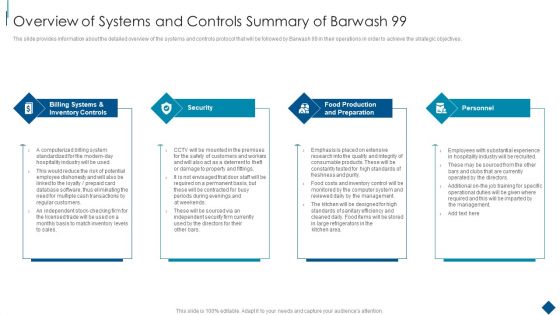
Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Billing Systems Inventory, Controls Security Personnel, Food Production Preparation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a developing firm security strategy plan facilities offered by implementation of security centre formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
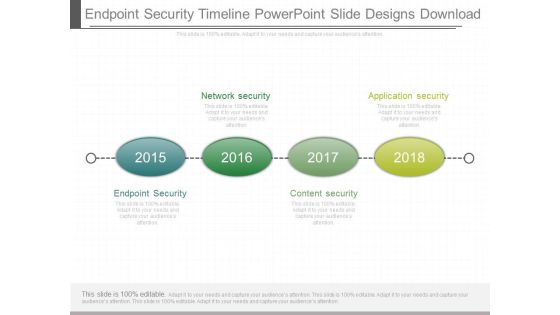
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.

Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF
This slide exhibits tactics to implement SecOps in order to effectively automate organization processes and improve business reputation. It includes define SecOps scope, develop repeatable workflows, execute red-team exercises, and automate processes. Presenting Best Practices For Implementing Security Operations To Increase Productivity Clipart PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Develop Repeatable Workflows, Automate Right Processes, Define Secops Scope. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
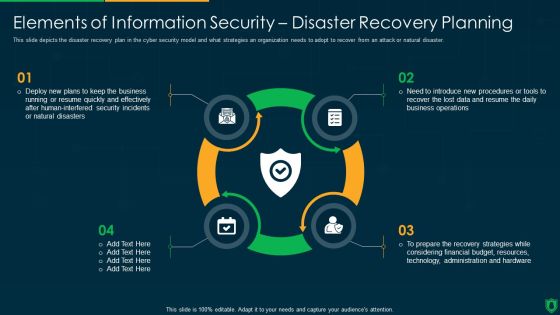
Info Security Elements Of Information Security Disaster Recovery Planning Ppt PowerPoint Presentation Gallery Designs PDF
This slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. This is a info security elements of information security disaster recovery planning ppt powerpoint presentation gallery designs pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like deploy new plans, quickly and effectively, security incidents, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Practices For Effective IT Security Awareness Training Program Background PDF
This slide covers best practices for effective cybersecurity awareness training program. It involves best practices such as getting into compliance, including everyone, establishing basics and making training engaging and entertaining. Presenting Best Practices For Effective IT Security Awareness Training Program Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Getting Into Compliance, Including Everyone, Establishing Basics. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cyber Security Businesses Diagram Ppt Slide Design
This is a cyber security businesses diagram ppt slide design. This is a four stage process. The stages in this process are application security, cloud security, respond, monitor.
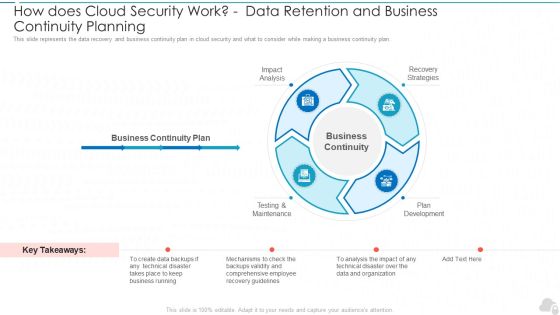
How Does Cloud Security Work Data Retention And Business Continuity Planning Cloud Computing Security IT Ppt Slides Demonstration PDF
This slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. This is a how does cloud security work data retention and business continuity planning cloud computing security it ppt slides demonstration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like impact analysis, testing and maintenance, plan development, recovery strategies. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Small Savings For Big Income PowerPoint Templates Ppt Backgrounds For Slides 0613
Document the process on our Small Savings For Big Income PowerPoint Templates PPT Backgrounds For Slides . Make a record of every detail. Satiate desires with our Umbrellas PowerPoint Templates. Give them all they want and more. Be the doer with our Security PowerPoint Templates. Put your thoughts into practice.

IT Security Common Methods Used To Threaten IT Security Ppt Portfolio Slides
This slide depicts the standard methods used to threaten network-security by cybercriminals attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten information technology security ppt infographics master slide pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like politically, monetary, profit, system, malicious. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF
The following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Find highly impressive IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download IT Security Automation Systems Guide Security Processes That Cant Be Automated Portrait PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Security Camera System Company Profile Our Expertise Pictures PDF
This slide highlights the security company expertise which includes integrated control of devices, internet protocol, RFID based security, wireless based communication and locality surveillance. This is a Security Camera System Company Profile Our Expertise Pictures PDF template with various stages. Focus and dispense information on Eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Internet Protocol, Physical Security, Communication Infrastructure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF
This slide showcases the features do digital security have for security. It includes features such as authentication, confidentiality, integrity, non-repudiation and access control. Persuade your audience using this Online Certificate Security And Privacy Measures Ppt Ideas Gallery PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Security Measures, Functions, Authentication, Confidentiality. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Cloud Computing Data Protection Security Architecture Solution Professional PDF
The slide shows a overall architecture of cloud data security system to provide data protection solution in controllable cloud security environment. It includes web application firewall, risk detection, physical and hardware security, digitalization and data encryption and back up. Showcasing this set of slides titled Cloud Computing Data Protection Security Architecture Solution Professional PDF. The topics addressed in these templates are Web Application Firewall, Data Detection, Data Awareness. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF
This slide depicts cyber security principles, including work factor, compromising recording, the economy of mechanism, fail-safe defaults, complete mediation, open design, separation of privilege, least privilege, least common mechanism, and so on. Get a simple yet stunning designed Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Cyber Security Components To Enhance Processes Principles Of Cyber Security Inspiration PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.
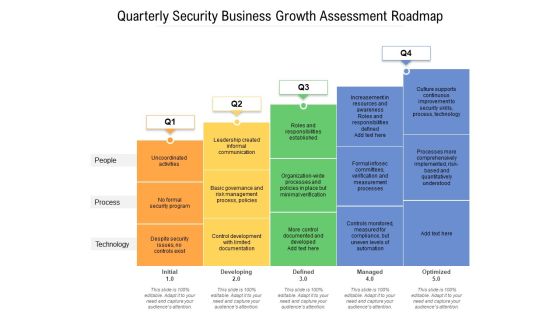
Quarterly Security Business Growth Assessment Roadmap Infographics
Presenting our jaw-dropping quarterly security business growth assessment roadmap infographics. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well-researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually-appealing design by clicking the download button given below.

Quarterly IT Security Recognition Program Roadmap Infographics
Presenting our innovatively-structured quarterly it security recognition program roadmap infographics Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Half Yearly Strategic Timeline Icons
Presenting our innovatively structured cyber security half yearly strategic timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Cyber Security Three Months Strategic Timeline Sample
Presenting our jaw dropping cyber security three months strategic timeline sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
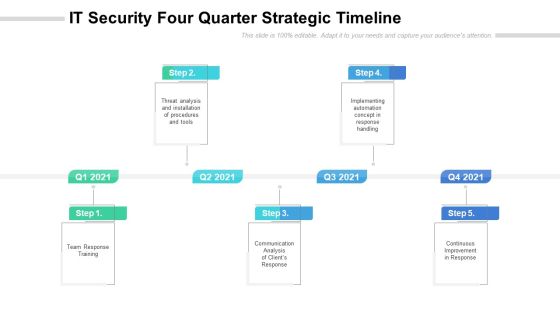
IT Security Four Quarter Strategic Timeline Slides
Presenting our innovatively structured it security four quarter strategic timeline slides Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

IT Security Three Months Strategic Timeline Portrait
Presenting our jaw dropping it security three months strategic timeline portrait. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
Security Strategic Four Quarter Functional Timeline Icons
Presenting our innovatively structured security strategic four quarter functional timeline icons Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Security Strategic Three Months Functional Timeline Introduction
Presenting our jaw dropping security strategic three months functional timeline introduction. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.

Security Agency Business Profile Government And Private Sector Clients Sample PDF
This slide highlights the security company clients from government and private sector which includes offices with location and industries with company name. Deliver an awe inspiring pitch with this creative Security Agency Business Profile Government And Private Sector Clients Sample PDF bundle. Topics like Location, Industry can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Our Service Maintenance Ppt PowerPoint Presentation Professional Visual Aids
Presenting this set of slides with name our service maintenance ppt powerpoint presentation professional visual aids. This is a four stage process. The stages in this process are our service, marketing, analytics, security, maintenance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vector Showing Multi Channel For Secured Experience Ppt PowerPoint Presentation Professional Skills PDF
Presenting this set of slides with name vector showing multi channel for secured experience ppt powerpoint presentation professional skills pdf. This is a two stage process. The stages in this process are vector showing multi channel for secured experience. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Computer Server Security Symbol With Lock Icon Ppt PowerPoint Presentation Summary Graphics Example PDF
Presenting this set of slides with name computer server security symbol with lock icon ppt powerpoint presentation summary graphics example pdf. This is a three stage process. The stages in this process are computer server security symbol with lock icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Picture Showing Software Security System Ppt PowerPoint Presentation Model Slides PDF
Presenting this set of slides with name picture showing software security system ppt powerpoint presentation model slides pdf. This is a three stage process. The stages in this process are picture showing software security system. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Shield Icon With Bitcoin Crypto Currency Symbol Ppt PowerPoint Presentation Pictures Skills PDF
Presenting this set of slides with name picture showing software security system ppt powerpoint presentation model slides pdf. This is a three stage process. The stages in this process are security shield icon with bitcoin crypto currency symbol. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Shield Vector With Star Icon Ppt PowerPoint Presentation Inspiration Elements PDF
Presenting this set of slides with name security shield vector with star icon ppt powerpoint presentation inspiration elements pdf. This is a three stage process. The stages in this process are security shield vector with star icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Shield With Dollar Symbol Vector Icon Ppt PowerPoint Presentation Pictures Model PDF
Presenting this set of slides with name security shield with dollar symbol vector icon ppt powerpoint presentation pictures model pdf. This is a three stage process. The stages in this process are security shield with dollar symbol vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Shield With Gear Symbol Vector Icon Ppt PowerPoint Presentation Slides Layout PDF
Presenting this set of slides with name security shield with gear symbol vector icon ppt powerpoint presentation slides layout pdf. This is a three stage process. The stages in this process are security shield with gear symbol vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Vector Showing Wide Area Network Security Analysis Ppt PowerPoint Presentation Summary Templates PDF
Presenting this set of slides with name vector showing wide area network security analysis ppt powerpoint presentation summary templates pdf. This is a three stage process. The stages in this process are vector showing wide area network security analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Number Lock With Security Key Vector Icon Ppt PowerPoint Presentation Professional Demonstration PDF
Presenting this set of slides with name number lock with security key vector icon ppt powerpoint presentation professional demonstration pdf. This is a three stage process. The stages in this process are number lock with security key vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Secure File Locked Document Vector Icon Ppt PowerPoint Presentation Infographics Clipart PDF
Presenting this set of slides with name secure file locked document vector icon ppt powerpoint presentation infographics clipart pdf. This is a two stage process. The stages in this process are secure file locked document vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Combination Number Lock Icon For Security Ppt PowerPoint Presentation Professional Slides PDF
Presenting this set of slides with name combination number lock icon for security ppt powerpoint presentation professional slides pdf. This is a one stage process. The stage in this process is combination number lock icon for security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Online Security Lock With Chain On Computer Screen Ppt PowerPoint Presentation Infographic Template Brochure PDF
Presenting this set of slides with name online security lock with chain on computer screen ppt powerpoint presentation infographic template brochure pdf. This is a one stage process. The stage in this process is online security lock with chain on computer screen. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Lock And Key Icon On Computer Screen Ppt PowerPoint Presentation Show Objects PDF
Presenting this set of slides with name security lock and key icon on computer screen ppt powerpoint presentation show objects pdf. This is a three stage process. The stages in this process are security lock and key icon on computer screen. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Security Lock Shield For Virus Threat Ppt PowerPoint Presentation Gallery Outfit PDF
Presenting this set of slides with name security lock shield for virus threat ppt powerpoint presentation gallery outfit pdf. This is a three stage process. The stages in this process are security lock shield for virus threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Yellow Lock Icon For Security And Protection Ppt PowerPoint Presentation Infographics Tips PDF
Presenting this set of slides with name yellow lock icon for security and protection ppt powerpoint presentation infographics tips pdf. This is a three stage process. The stages in this process are yellow lock icon for security and protection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF
This slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Slidegeeks is here to make your presentations a breeze with Secure Web Gateways SWG Setup And Working Ppt Show Tips PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
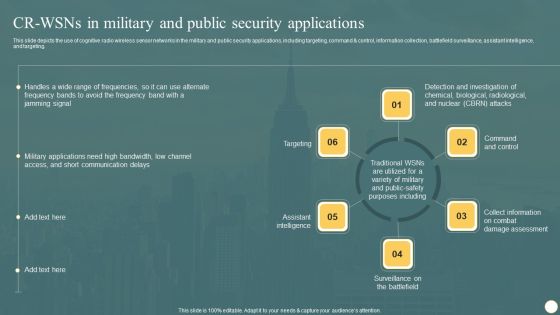
Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Presenting this PowerPoint presentation, titled Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Cognitive Radio Network IT CR WSNS In Military And Public Security Applications Graphics PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.
Info Security Complete Information Security Implementation Checklist Ppt PowerPoint Presentation Icon Portfolio PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a info security complete information security implementation checklist ppt powerpoint presentation icon portfolio pdf template with various stages. Focus and dispense information on twelve stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like frequent, staff training, antivirus software, strong passwords, data backup, recovery planning. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
PowerPoint Slide Teamwork Chains Process Ppt Theme
PowerPoint Slide Teamwork chains process PPT Theme-These Fabulous PowerPoint slides and PowerPoint templates have been delicately designed by our professional team to leave long-lasting impressions on your audiences
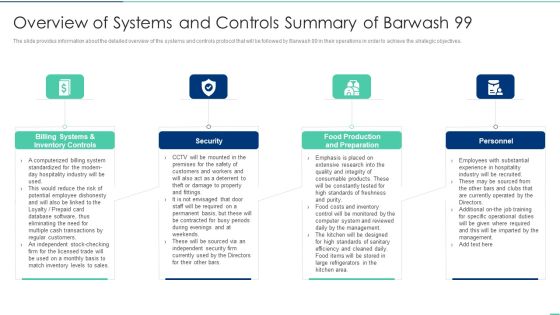
Overview Of Systems And Controls Summary Of Barwash 99 Ppt Professional PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. This is a overview of systems and controls summary of barwash 99 ppt professional pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sales, systems, inventory, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
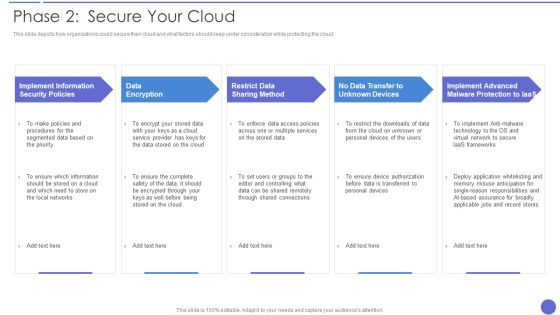
Phase 2 Secure Your Cloud Clipart PDF
This slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud. Presenting Phase 2 Secure Your Cloud Clipart PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Encryption, Restrict Data Sharing Method, Implement Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Five Years Enterprise IT Automation Machinery Road Mapping With Security And Compliance Ideas
Presenting the five years enterprise it automation machinery road mapping with security and compliance ideas. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Half Yearly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Inspiration
Introducing our half yearly enterprise it automation machinery road mapping with security and compliance inspiration. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Model Business PowerPoint Templates Security Plan Slides
We present our model business powerpoint templates security plan Slides.Download our Marketing PowerPoint Templates because you should Experience excellence with our PowerPoint Templates and Slides. They will take your breath away. Download our Circle Charts PowerPoint Templates because It can Leverage your style with our PowerPoint Templates and Slides. Charm your audience with your ability. Download our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides come in all colours, shades and hues. They help highlight every nuance of your views. Download and present our Business PowerPoint Templates because It will get your audience in sync. Download and present our Shapes PowerPoint Templates because You are working at that stage with an air of royalty. Let our PowerPoint Templates and Slides be the jewels in your crown.Use these PowerPoint slides for presentations relating to arrow, blue, chart, chevron, circle, circular, diagram, graphic, green, hub, icon, illustration, isometric, pie, pieces, process, purple, red, round, set, slices, stages, vector, wheel, yellow. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
PowerPoint Presentation Marketing Chains Process Ppt Presentation
PowerPoint Presentation Marketing chains process PPT Presentation-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.
PowerPoint Backgrounds Process Linked Chains Ppt Template
PowerPoint Backgrounds Process linked chains PPT Template-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.
PowerPoint Slide Designs Process Chains Ppt Template
PowerPoint Slide Designs Process Chains PPT Template-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.
PowerPoint Themes Process Chains Ppt Theme
PowerPoint Themes Process Chains PPT Theme-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.
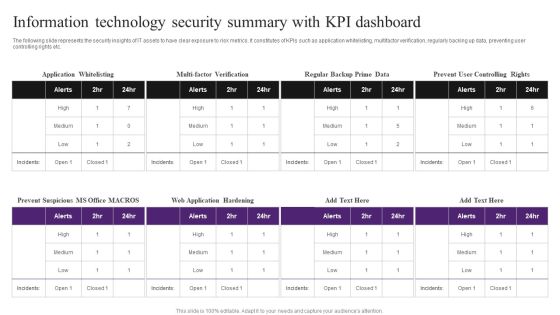
Information Technology Security Summary With KPI Dashboard Inspiration PDF
The following slide represents the security insights of IT assets to have clear exposure to risk metrics. It constitutes of KPIs such as application whitelisting, multifactor verification, regularly backing up data, preventing user controlling rights etc. Pitch your topic with ease and precision using this Information Technology Security Summary With KPI Dashboard Inspiration PDF. This layout presents information on Information Technology Security, Summary With KPI Dashboard. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
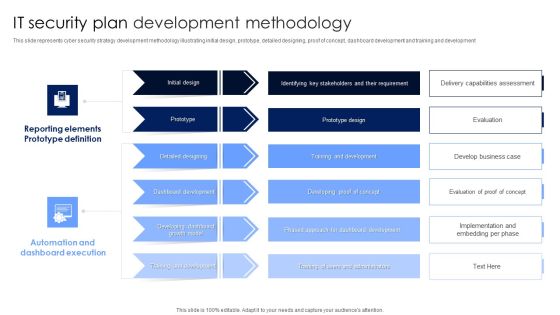
IT Security Plan Development Methodology Microsoft PDF
This slide represents cyber security strategy development methodology illustrating initial design, prototype, detailed designing, proof of concept, dashboard development and training and development. Pitch your topic with ease and precision using this IT Security Plan Development Methodology Microsoft PDF. This layout presents information on Automation And Dashboard Execution, Reporting Elements Prototype Definition, Dashboard Development. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Operational And Business Benefits Presentation Backgrounds
This is a operational and business benefits presentation backgrounds. This is a seven stage process. The stages in this process are vision, plan, design, build, deliver, operate, people change and learning, process and package, business intelligence, information technology, security and controls, tax.

Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Cognitive Sensor Network CR Wsns In Military And Public Security Applications Template PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers.

Computer Security Ppt Diagram Example Ppt Presentation
This is a computer security ppt diagram example ppt presentation. This is a eight stage process. The stages in this process are application guard, antivirus, passwords, firewall, attack detection, system guard, file lock, process quarantine.
Workforce Security Realization Coaching Plan Different Training Formats For Different Organizational Levels Icons PDF
This slide covers the training format at different organization levels including strategy improves the actions of the customers and helps create a cybersafe atmosphere. Presenting workforce security realization coaching plan different training formats for different organizational levels icons pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like interactive protection simulation, cybersecurity for it online, automated security awareness platform. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.
Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending.Deliver an awe inspiring pitch with this creative Quarterly Budget Analysis Of Business Organization Spend Analysis Of Organization Microsoft PDF bundle. Topics like Overall Spending, Admiration Remained, Security Administration Expense can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF
This slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help orgnaization to minimize the financial loss and maintain reputation of business.Presenting Information Security Risk Evaluation Mitigation Strategies To Tackle Information Security Threats Designs PDF to provide visual cues and insights. Share and navigate important information on fivestages that need your due attention. This template can be used to pitch topics like Phishing, Rotate Passwords, Install Firewalls. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Info Security What Is Information Security And How Does It Work Ppt PowerPoint Presentation File Clipart PDF
This slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. This is a info security what is information security and how does it work ppt powerpoint presentation file clipart pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like collective methods, techniques and procedures, protect data, computer systems, networks. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Survey Template Ppt Example
This is a information security survey template ppt example. This is a four stage process. The stages in this process are information, security, personal, secret.

Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF
This slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal.Create an editable Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre-designed presentation templates help save time. Advantages And Working Of Secure SDLC Phases Of Software Development Procedure Professional PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF
This slide depicts the use of cognitive radio wireless sensor networks in the military and public security applications, including targeting, command and control, information collection, battlefield surveillance, assistant intelligence, and targeting. This modern and well-arranged Cognitive Sensing Innovation CR Wsns In Military And Public Security Applications Inspiration PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint, no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

SIEM Services Key Features Of SIEM Software Ppt Pictures Background Image PDF
This slide provides the details about our companys SIEM key features such as automated reports, log collection and classification, high scalability, security automation, etc. This is a siem services key features of siem software ppt pictures background image pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like compliance, internal auditing, scalability, security, enrichment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Presenting this PowerPoint presentation, titled CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable CYBER Security Breache Response Strategy Impact Of Cybersecurity Incidents On Organization Template PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Critical Violations Security Dashboard With KPI Metrics Graphics PDF
This slide shows dashboard of security to mitigate violation by prioritizing KPIs. It includes application control, operating systems, restrict admin privileges, multi factor authentication and backup of important data. Showcasing this set of slides titled Critical Violations Security Dashboard With KPI Metrics Graphics PDF. The topics addressed in these templates are Risk Model, Application Components, Technologies Overview. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cloud Network Security Training Programs Timeline Download PDF
The slide showcases training programs to improve individuals level of awareness about security measures designed to protect cloud based infrastructure and data. The elements are SANS, infosec, ISC, edX with their completion timeline and pricing package . Showcasing this set of slides titled Cloud Network Security Training Programs Timeline Download PDF. The topics addressed in these templates are Training Programs, Models Controls, Offense Defense Operations. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Information Security Key Elements Of Data Security Ppt Pictures Show PDF
This slide represents the different elements of data security such as application security, network security, information security, etc. Presenting information security key elements of data security ppt pictures show pdf to provide visual cues and insights. Share and navigate important information on eight stages that need your due attention. This template can be used to pitch topics like network security, application security, cloud security, operational security, information security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF
The purpose of this slide is to showcase the dos and donts of ransomware prevention attack. The slide covers information about updating the software, installing a firewall software, using reliable website and sources etc. Present like a pro with Organizing Security Awareness Dos And Donts Of Prevention From Ransomware Diagrams PDF Create beautiful presentations together with your team, using our easy-to-use presentation slides. Share your ideas in real-time and make changes on the fly by downloading our templates. So whether youre in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Quarterly Roadmap For Employee Security Recognition Pictures
Introducing our quarterly roadmap for employee security recognition pictures. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cyber Security Six Months Strategic Timeline Designs
Introducing our cyber security six months strategic timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

IT Security Half Yearly Strategic Timeline Diagrams
Introducing our it security half yearly strategic timeline diagrams. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
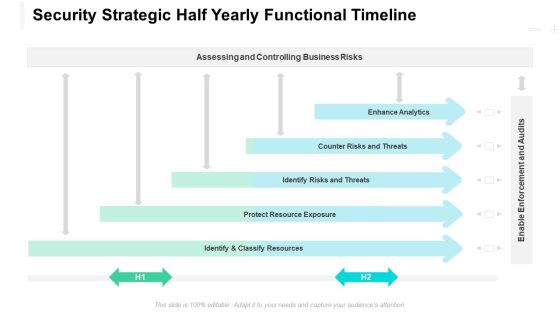
Security Strategic Half Yearly Functional Timeline Designs
Introducing our security strategic half yearly functional timeline designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
IT Services Investor Financing Elevator Pitch Deck Services Offered By Software Company Microsoft PDF
This slide provides the glimpse about the services offered by our software company such as cross platform support, user friendly interface, customization, security, etc.Presenting it services investor financing elevator pitch deck services offered by software company microsoft pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like cross platform support, customization, key enterprise system integration In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Agile Quality Control Framework IT QA Testing Methodologies Nonfunctional Information PDF
This slide shows the non functional methodologies for Quality assurance testing. Methodologies covered in the slide are Vulnerability, usability testing, compatible testing and performance testing. Presenting agile quality control framework it qa testing methodologies functional themes pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security, software, performance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
Kinds Of Fixed Income Securities Powerpoint Slide Images
This is a kinds of fixed income securities powerpoint slide images. This is a four stage process. The stages in this process are government securities, government agency issues, municipal bonds, corporate bonds.

Defense And National Security Powerpoint Slide Background
This is a defense and national security powerpoint slide background. This is a five stage process. The stages in this process are defense and national security, homeland security, intelligence operations, law enforcement, international affairs and commerce.

Security Website Template Powerpoint Slide Background Designs
This is a security website template powerpoint slide background designs. This is a six stage process. The stages in this process are inventory, secure coding, secure testing, remediation plan, define next steps, deep scan.
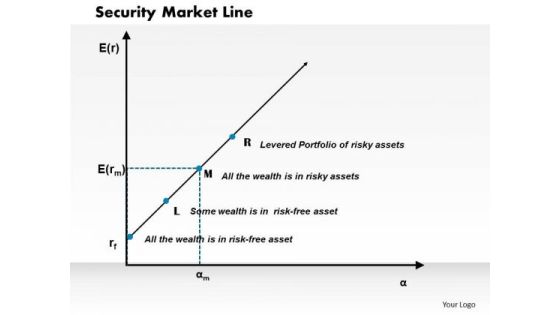
Security Market Line Business PowerPoint Presentation
Document The Process On Our Security Market Line Business Powerpoint Presentation Powerpoint Templates. Make A Record Of Every Detail. Satiate Desires With Our success Powerpoint Templates. Give Them All They Want And More.

Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF
This slide highlights some of the major risks faced by businesses that are engaged in outsourcing the activities to a foreign company. The key risks are security breaches, cost of service, communication issues and overdependence on service providers. Presenting Major Risks Involved In Business Process Outsourcing Service Industry Designs PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Security Breaches, Cost Services, Communicationi Ssues. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
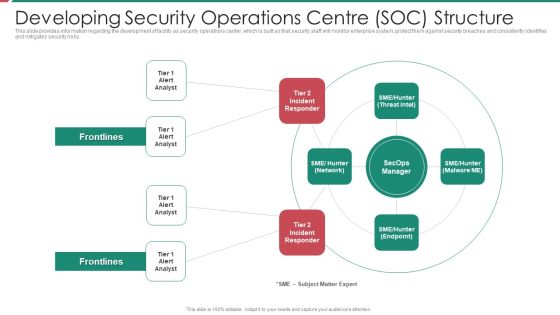
Security And Process Integration Developing Security Operations Centre SOC Structure Inspiration PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting security and process integration developing security operations centre soc structure inspiration pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Roadmap For Information Technology Security Training Ppt Layouts Vector PDF
This slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. This is a it security roadmap for information technology security training ppt layouts vector pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like ensuring physical security, ensuring data security, mobile and remote computing best practices, safe and computing best practices. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
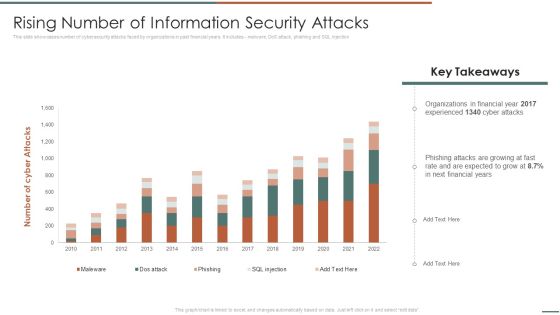
Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF
This slide showcases number of cybersecurity attacks faced by organizations in past financial years. It includes malware, DoS attack, phishing and SQL injection.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Rising Number Of Information Security Attacks Summary PDF. Use them to share invaluable insights on Organizations In Financial, Experienced, Phishing Attacks and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF
This slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. There are so many reasons you need a Developing IT Security Strategy Identifying Information Security Threats And Impact On Download PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Impact On Organization After Implementing Computer Security Strategy And Training Ideas PDF
This slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. This is a impact on organization after implementing computer security strategy and training ideas pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like network intrusion, system misconfiguration. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF
This Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Current Information Security Issues Faced By Organization Cybersecurity Risk Assessment Guidelines PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Comparison Of Various Security Awareness Training Software Elements PDF
The purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver and pitch your topic in the best possible manner with this Comparison Of Various Security Awareness Training Software Elements PDF. Use them to share invaluable insights on Individualized Security, Industry Specific, Deployment and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Diagram Business Process 3d Man Piggy Bank PowerPoint Templates
We present our diagram business process 3d man piggy bank PowerPoint templates.Present our Future PowerPoint Templates because Our PowerPoint Templates and Slides are like the strings of a tennis racquet. Well strung to help you serve aces. Download our Symbol PowerPoint Templates because you should once Tap the ingenuity of our PowerPoint Templates and Slides. They are programmed to succeed. Present our Security PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Use our Finance PowerPoint Templates because Timeline crunches are a fact of life. Meet all deadlines using our PowerPoint Templates and Slides. Download and present our Success PowerPoint Templates because Our PowerPoint Templates and Slides will provide you a launch platform. Give a lift off to your ideas and send them into orbit.Use these PowerPoint slides for presentations relating to 3d, analyzing, bank, banking, box, business, buying, cartoon, coin, concept, currency, debt, dividend, dollar, exchange, finance, forecasting, fortune, green, growth, human, investment, loan, luck, making, man, market, marketing, money, moving, occupation, omit, paying, pension, people, person, pig, piggy, pleasure, postpone, puppet, rate, savings, stock, success, symbol, tax, wages, wealth. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Professionals tell us our diagram business process 3d man piggy bank PowerPoint templates will make the presenter successul in his career/life. Use our coin PowerPoint templates and PPT Slides are topically designed to provide an attractive backdrop to any subject. Use our diagram business process 3d man piggy bank PowerPoint templates are visually appealing. Customers tell us our coin PowerPoint templates and PPT Slides will get their audience's attention. Presenters tell us our diagram business process 3d man piggy bank PowerPoint templates will make the presenter look like a pro even if they are not computer savvy. People tell us our bank PowerPoint templates and PPT Slides effectively help you save your valuable time.
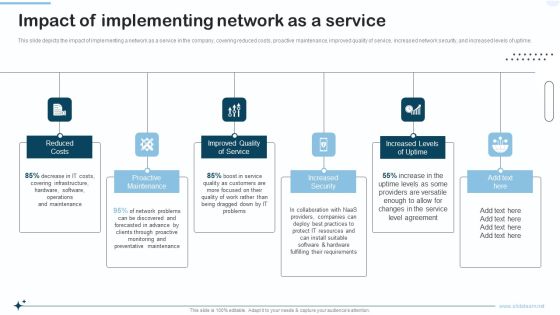
Naas Integrated Solution IT Impact Of Implementing Network As A Service Portrait PDF
This slide depicts the impact of implementing a network as a service in the company, covering reduced costs, proactive maintenance, improved quality of service, increased network security, and increased levels of uptime. Presenting Naas Integrated Solution IT Impact Of Implementing Network As A Service Portrait PDF to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like Improved Quality Of Service, Increased Security, Increased Levels Of Uptime. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
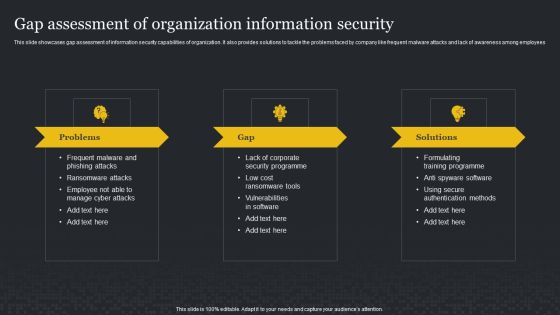
Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF
This slide showcases gap assessment of information security capabilities of organization. It also provides solutions to tackle the problems faced by company like frequent malware attacks and lack of awareness among employees. Here you can discover an assortment of the finest PowerPoint and Google Slides templates. With these templates, you can create presentations for a variety of purposes while simultaneously providing your audience with an eye-catching visual experience. Download Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF to deliver an impeccable presentation. These templates will make your job of preparing presentations much quicker, yet still, maintain a high level of quality. Slidegeeks has experienced researchers who prepare these templates and write high-quality content for you. Later on, you can personalize the content by editing the Gap Assessment Of Organization Information Security Cybersecurity Risk Assessment Ideas PDF.

Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Get a simple yet stunning designed Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Implementing Cyber Security Incident Impact Of Cybersecurity Incidents On Organization Graphics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cyber Security Five Year Strategic Timeline Demonstration
We present our cyber security five year strategic timeline demonstration. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cyber security five year strategic timeline demonstration in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
IT Security Five Years Strategic Timeline Icons
We present our it security five years strategic timeline icons. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched it security five years strategic timeline icons in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Security Strategic Five Year Functional Timeline Graphics
We present our security strategic five year functional timeline graphics. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched security strategic five year functional timeline graphics in different formats like PDF, PNG, and JPG to smoothly execute your business plan.
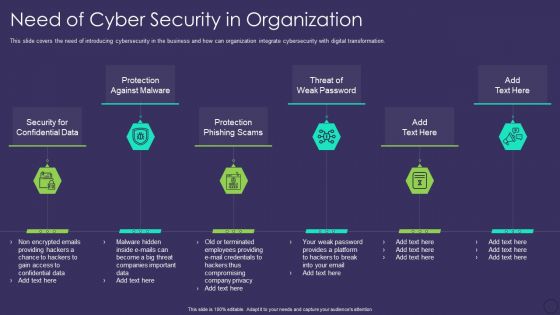
Comprehensive Business Digitization Deck Need Of Cyber Security In Organization Formats PDF
This slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation. Presenting comprehensive business digitization deck need of cyber security in organization formats pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like security for confidential data, protection against malware, protection phishing scams, threat of weak password. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
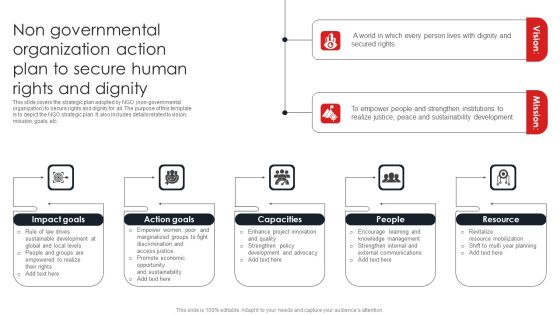
Non Governmental Organization Action Plan To Secure Human Rights And Dignity Mockup PDF
This slide covers the strategic plan adopted by NGO non governmental organization to secure rights and dignity for all. The purpose of this template is to depict the NGO strategic plan. It also includes details related to vision, mission, goals, etc.Persuade your audience using this Non Governmental Organization Action Plan To Secure Human Rights And Dignity Mockup PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Crowdfunding Through, Social Responsibility, Collecting Recycling. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF
Are you searching for a Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF that is uncluttered, straightforward, and original It is easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, it is perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Impact Of Information Security Loss On Organization Cybersecurity Risk Assessment Ideas PDF from Slidegeeks today.

Cybersecurity Elements Of Electronic Information Security Network Security Ppt Ideas Skills PDF
This slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. This is a cybersecurity elements of electronic information security network security ppt ideas skills pdf template with various stages. Focus and dispense information on seven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like email security, web security, virtual private network, antivirus software. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF
This slide showcases financial impact of different cyber security attacks on organizations. Its key elements are business disruption, information loss, revenue loss, equipment damage and total cost by attack type. Boost your pitch with our creative Developing IT Security Strategy Financial Impact Of Information Security Attacks Rules PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF
This slide represents the techniques to be used by the organizations to analyze the impact of cyber security incidents on business operations. It includes strategies for analyzing cyber incidents such as profile network and systems etc. Slidegeeks has constructed Implementing Cyber Security Incident Strategies To Analyze Cyber Security Incidents Background PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Business Process Flow 3d Man With Big Golden Key PowerPoint Templates Backgrounds For Slides
We present our business process flow 3d man with big golden key PowerPoint templates backgrounds for slides.Download and present our Security PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Present our Business PowerPoint Templates because You have gained great respect for your brilliant ideas. Use our PowerPoint Templates and Slides to strengthen and enhance your reputation. Download and present our Magnifier Glasses PowerPoint Templates because Our PowerPoint Templates and Slides are like the strings of a tennis racquet. Well strung to help you serve aces. Download and present our Symbol PowerPoint Templates because Our PowerPoint Templates and Slides will weave a web of your great ideas. They are gauranteed to attract even the most critical of your colleagues. Use our Shapes PowerPoint Templates because It can Conjure up grand ideas with our magical PowerPoint Templates and Slides. Leave everyone awestruck by the end of your presentation.Use these PowerPoint slides for presentations relating to 3d, abstract, analyzing, background, brilliance, business, character, concept, cute, discovery, equipment, examining, glass, gold, golden, graphics, guy, hand, handle, human, humorous, icon, idea, illustration, image, isolated, key, large, lens, little, look, loupe, magnification, magnify, man, people, person, puzzle, render, research, riddle, science, search, single, solution, steel, symbol, white, work. The prominent colors used in the PowerPoint template are Yellow, Gray, Black. Professionals tell us our business process flow 3d man with big golden key PowerPoint templates backgrounds for slides will help them to explain complicated concepts. The feedback we get is that our character PowerPoint templates and PPT Slides look good visually. PowerPoint presentation experts tell us our business process flow 3d man with big golden key PowerPoint templates backgrounds for slides are visually appealing. You can be sure our background PowerPoint templates and PPT Slides are incredible easy to use. People tell us our business process flow 3d man with big golden key PowerPoint templates backgrounds for slides are aesthetically designed to attract attention. We guarantee that they will grab all the eyeballs you need. You can be sure our character PowerPoint templates and PPT Slides will make the presenter look like a pro even if they are not computer savvy.

Competitor Analysis Grid Of Security Software Inspiration PDF
This slide provides an overview of the comparison among various software. The comparison is done on the basis of features that are antivirus, firewall, system cleansing, anti-spyware and parental control. Pitch your topic with ease and precision using this Competitor Analysis Grid Of Security Software Inspiration PDF. This layout presents information on System Cleansing, Everyday Backup Option, Anti Spyware. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
Security Challenges Domains On Web Sample Diagram
This is a security challenges domains on web sample diagram. This is a three stage process. The stages in this process are web, process, people, technology.
Security Awareness Tracking Kpis Ppt Layouts Graphics Template PDF
This slide covers the key performance for security awareness training including compliance, security culture and incident reduction.Deliver an awe-inspiring pitch with this creative security awareness tracking kpis ppt layouts graphics template pdf. bundle. Topics like phishing informants, social engineering, refresher training scores can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

3d Man With Locked Jigsaw Puzzle Security PowerPoint Templates And PowerPoint Themes 1112
We present our 3d Man With Locked Jigsaw Puzzle Security PowerPoint Templates And PowerPoint Themes 1112.Use our Business PowerPoint Templates because,Sales & Marketing funnel:- You have the product you need. Use our People PowerPoint Templates because, This template with an image of helps you chart the course of your presentation. Use our Security PowerPoint Templates because, Use our templates to emphasise your views. Use our Success PowerPoint Templates because, Corporate Ladder:- The graphic is a symbol of growth and sucess. Use our Puzzles or Jigsaws PowerPoint Templates because, Business 3D Circular Puzzle:- Your business and plans for its growth consist of processes that are highly co-related.Use these PowerPoint slides for presentations relating to Man with puzzle, business, people, security, success, puzzles or jigsaws, shapes. The prominent colors used in the PowerPoint template are Green, Black, White

Pricing Plan Of Security Awareness Packages Ppt Ideas Graphic Tips PDF
The purpose of this slide is to showcase the pricing plan of cyber security awareness package. It covers information about the total number of employees along with different packages such as silver, gold, platinum and diamond. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Pricing Plan Of Security Awareness Packages Ppt Ideas Graphic Tips PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Pricing Plan Of Security Awareness Packages Ppt Ideas Graphic Tips PDF today and make your presentation stand out from the rest.
SIEM Integrations SIEM Services Ppt Icon Graphic Tips PDF
Presenting siem integrations siem services ppt icon graphic tips pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security events, network logs, applications and devices, it infrastructure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

How Cloud Computing Accelerates Technology Transformation Services Infographics PDF
The following slide showcases cloud computing technologies to accelerate transformation plans in organization. It presents information related to cost efficiency, scalability, etc. Presenting How Cloud Computing Accelerates Technology Transformation Services Infographics PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Unmatched Accessibility, Enhanced Security, Cost Efficient, High Scalability. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard AND regulation etc. This Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Prevention Of Information KPI Dashboard To Monitor Cyber Security Performance Information PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today
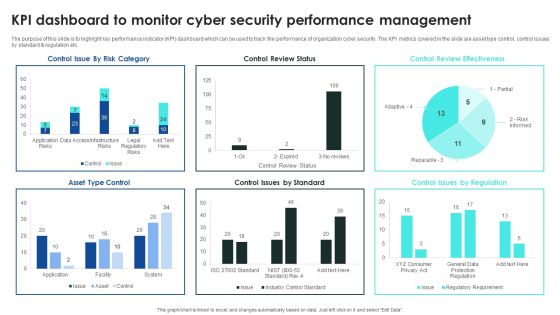
Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF
The purpose of this slide is to highlight key performance indicator KPI dashboard which can be used to track the performance of organization cyber security. The KPI metrics covered in the slide are asset type control, control issues by standard and regulation etc. This Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Cybersecurity Awareness Program To Prevent Attacks KPI Dashboard To Monitor Cyber Security Introduction PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF
This slide represents essential information and communication technology ICT security measures businesses use. It covers strong password authentication, data backup, network access control, etc. Create an editable Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Key ICT Security Measures Used By Businesses Ideas PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.

Deploying Docker Container And Kubernetes Within Organization Best Security Measures In Kubernetes Ppt PowerPoint Presentation PDF
Presenting this set of slides with name deploying docker container and kubernetes within organization best security measures in kubernetes ppt powerpoint presentation pdf. This is a ten stage process. The stages in this process are enables auditing provide limited direct access kubernetes nodes, resources quota, authorized repository, rules resources, implement, network segmentation, log everything production environment, restrict access to etcd. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Information Security Challenges Users Face In Data Privacy Sample PDF
This slide outlines the challenges users face in data privacy, including online tracking, losing control of data, lack of transparency, social media, and cybercrime. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Information Security Challenges Users Face In Data Privacy Sample PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Information Security Challenges Users Face In Data Privacy Sample PDF.
PowerPoint Presentation Designs Marketing Chains Process Ppt Designs
PowerPoint Presentation Designs Marketing chains process PPT Designs-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.
PowerPoint Presentation Designs Marketing Chains Process Ppt Templates
PowerPoint Presentation Designs Marketing chains process PPT Templates-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.

PowerPoint Slide Designs Marketing Chains Process Ppt Presentation
PowerPoint Slide Designs Marketing chains process PPT Presentation-Most events and in every aspect of life are invariably interlinked. Use this chains graphic to outline your thoughts and their inherent interdependance to acheive the final outcome. Highlight the strength and durability of your thoughts, ideas and products.-These amazing PowerPoint pre-designed slides and PowerPoint templates have been carefully created by our team of experts to help you impress your audience. Our stunning collection of Powerpoint slides are 100% editable and can easily fit in any PowerPoint presentations. By using these animations and graphics in PowerPoint and you can easily make professional presentations. Any text can be entered at any point in the PowerPoint template or slide. Just DOWNLOAD our awesome PowerPoint templates and you are ready to go.

Cyber Security Strategic Four Quarter Timeline Formats
Presenting the cyber security strategic four quarter timeline formats. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

IT Security Six Months Strategic Timeline Portrait
Presenting the it security six months strategic timeline portrait. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Security Strategic Six Months Functional Timeline Clipart
Presenting the security strategic six months functional timeline clipart. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.
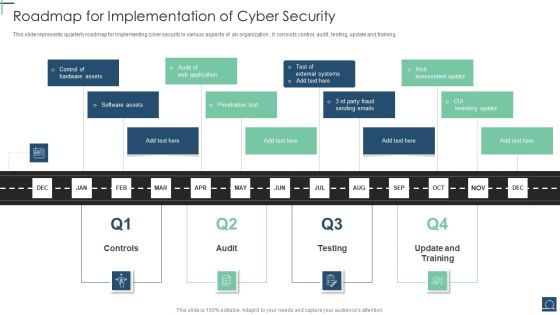
Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF
This slide represents quarterly roadmap for implementing cyber security in various aspects of an organization . It consists control, audit , testing, update and training. Presenting Roadmap For Implementation Of Cyber Security Ppt PowerPoint Presentation Gallery Designs Download PDF to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including Penetration Test, Software Assets, Control Hardware Assets. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Overview Of Everything As A Service Xaas Cloud Computing Models Ppt PowerPoint Presentation Ideas Guide PDF
This slide depicts the overview of the everything as a service provider company, including its functionality, number of customers and partners, security, and operational expertise.This is a Overview Of Everything As A Service Xaas Cloud Computing Models Ppt PowerPoint Presentation Ideas Guide PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Most Functionality, Largest Community, Most Secure. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
