Safety Management

CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF
This slide represents dashboard showing the key metrics of cyber security incident response. It includes key performance indicators such as risk score, compliance status, threat level etc. Crafting an eye catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal CYBER Security Breache Response Strategy Cyber Security Incident Response Kpi Dashboard Rules PDF that effortlessly grabs the attention of your audience. Begin now and be certain to wow your customers.

Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF
This slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets.This is a Information Security Risk Evaluation Process For Information Security Risk Assessment Template PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Identifying Internal, Allocating Vulnerability, Assessing Level. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
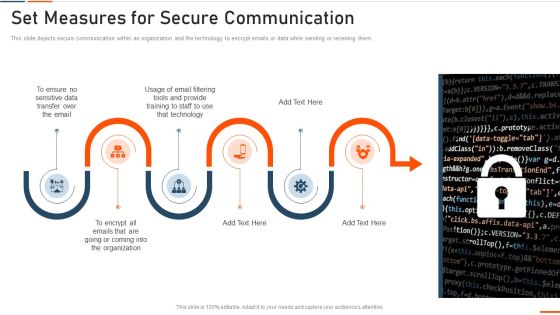
Information Technology Security Set Measures For Secure Communication Ppt Professional Portrait PDF
This is a information technology security set measures for secure communication ppt professional portrait pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, transfer, technology, training, organization. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
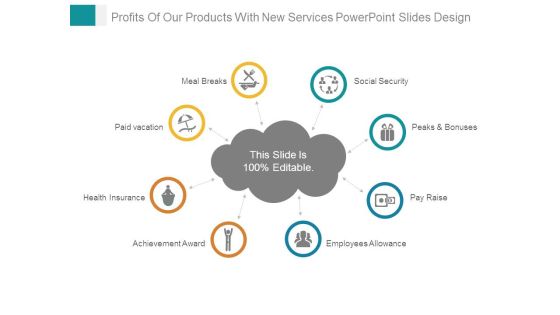
Profits Of Our Products With New Services Powerpoint Slides Design
This is a profits of our products with new services powerpoint slides design. This is a eight stage process. The stages in this process are social security, peaks and bonuses, pay raise, employees allowance, meal breaks, paid vacation, health insurance, achievement award.
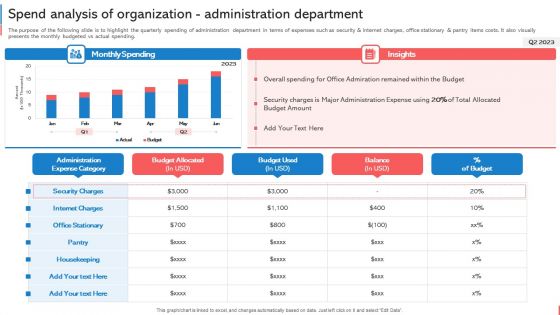
Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF
The purpose of the following slide is to highlight the quarterly spending of administration department in terms of expenses such as security and internet charges, office stationary and pantry items costs. It also visually presents the monthly budgeted vs actual spending. This Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Company Budget Analysis Spend Analysis Of Organization Administration Department Download PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF
This slide represents the overview of the software development life cycle, including its goal, international standard, way of creating, designing, and developing software.Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Overview And Importance Of Secure SDLC Phases Of Software Development Procedure Structure PDF.

Regulatory Compliance Traceability Matrix For Cloud Environment Microsoft PDF
This slide outlines the regulatory compliance matrix for the cloud environment. The purpose of this slide is to share the standards cloud service providers need to include for maintaining information security. The organizations include COBIT, FedRAMP, NESA, NIST, and SOX. Showcasing this set of slides titled Regulatory Compliance Traceability Matrix For Cloud Environment Microsoft PDF. The topics addressed in these templates are Organization Standards, Status, Comments. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
This slide describes the overview of the command security operations center, including its advantages and disadvantages. The purpose of this slide is to demonstrate the pros, cons and main responsibilities of command SOC. The main tasks include monitoring and analyzing security events, coordinating incident response, etc. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cybersecurity Operations Cybersecops Command SOC Overview Advantages Mockup PDF
Information Security Complete Data Security Implementation Checklist Ppt Icon Clipart PDF
This slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. This is a information security complete data security implementation checklist ppt icon clipart pdf template with various stages. Focus and dispense information on eleven stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like strong passwords, antivirus software, frequent staff training, recovery planning, device security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cyber Security Systems Monitoring Report Formats PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Boost your pitch with our creative Cyber Security Systems Monitoring Report Formats PDF. Deliver an awe-inspiring pitch that will mesmerize everyone. Using these presentation templates you will surely catch everyones attention. You can browse the ppts collection on our website. We have researchers who are experts at creating the right content for the templates. So you do not have to invest time in any additional work. Just grab the template now and use them.

Golden Keys On Coins Security PowerPoint Templates Ppt Backgrounds For Slides 0213
We present our Golden Keys On Coins Security PowerPoint Templates PPT Backgrounds For Slides 0213.Use our Money PowerPoint Templates because You can Create a matrix with our PowerPoint Templates and Slides. Feel the strength of your ideas click into place. Present our Security PowerPoint Templates because Our PowerPoint Templates and Slides are conceived by a dedicated team. Use them and give form to your wondrous ideas. Use our Business PowerPoint Templates because They will bring a lot to the table. Their alluring flavours will make your audience salivate. Present our Process and Flows PowerPoint Templates because Our PowerPoint Templates and Slides will let you Hit the right notes. Watch your audience start singing to your tune. Present our Shapes PowerPoint Templates because Your audience will believe you are the cats whiskers.Use these PowerPoint slides for presentations relating to Golden keys on coins, Money, Finance, Business, Success, Security. The prominent colors used in the PowerPoint template are Yellow, Gray, Black.
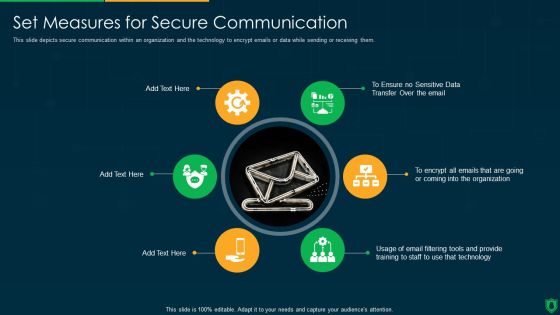
Info Security Set Measures For Secure Communication Ppt PowerPoint Presentation Gallery Graphics Design PDF
This slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. This is a info security set measures for secure communication ppt powerpoint presentation gallery graphics design pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like sensitive data, organization, email filtering tools, technology. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security And Process Integration Security And Operational Tasks Maintenance Checklist Diagrams PDF
This slide provides information regarding security and operational task maintenance checklist with activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver and pitch your topic in the best possible manner with this security and process integration security and operational tasks maintenance checklist diagrams pdf. Use them to share invaluable insights on system monitoring, executive reporting, planning meeting, preventive maintenance and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
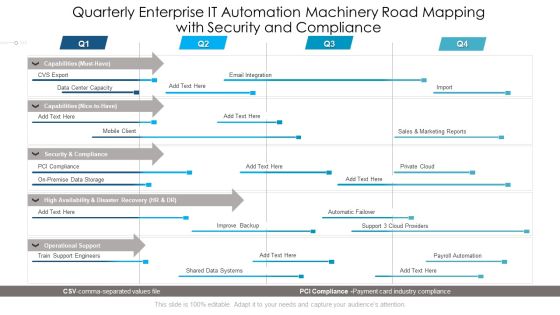
Quarterly Enterprise IT Automation Machinery Road Mapping With Security And Compliance Diagrams
Presenting our innovatively structured quarterly enterprise it automation machinery road mapping with security and compliance diagrams Template. Showcase your roadmap process in different formats like PDF, PNG, and JPG by clicking the download button below. This PPT design is available in both Standard Screen and Widescreen aspect ratios. It can also be easily personalized and presented with modified font size, font type, color, and shapes to measure your progress in a clear way.

Data Breach Prevention Recognition Security Training Program Frameworks Mockup PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver and pitch your topic in the best possible manner with this data breach prevention recognition security training program frameworks mockup pdf. Use them to share invaluable insights on target audience, training success, instruction information sources and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
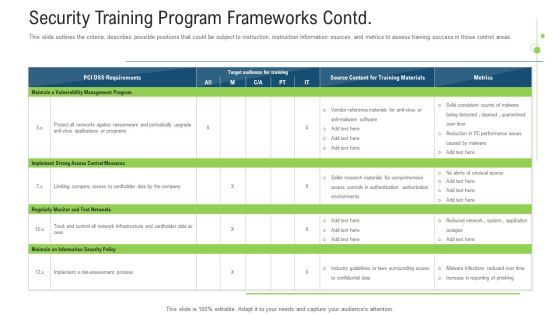
Security Training Program Frameworks Contd Ppt Pictures Layout Ideas PDF
This slide outlines the criteria, describes possible positions that could be subject to instruction, instruction information sources, and metrics to assess training success in those control areas. Deliver an awe inspiring pitch with this creative Security Training Program Frameworks Contd Ppt Pictures Layout Ideas Pdf bundle. Topics like measures, implement, programs, risk can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Service Architecture And Delivery Process For Business Transformation Topics PDF
This slide includes the service architecture process enabling the development of applications that are easier to handle and more secure. These steps help to make software components reusable and efficient. Presenting Service Architecture And Delivery Process For Business Transformation Topics PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Govern Plan Service Products, Direct Plan Resources, Supply Service. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF
This slide highlights the detection and prevention of operational control with physical security control measures and safe environment it also includes detailed preventive measures for operational controls. This is a Information Technology Threat Mitigation Methods Detection And Prevention Of Operational Controls Download PDF template with various stages. Focus and dispense information on two stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Detection Operation Controls, Preventive Operation Controls. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Where Is The Gap In Security Programs Hacking Prevention Awareness Training For IT Security Diagrams PDF
This slide covers the problems in the organization regarding security awareness training along with the gap and solution to overcome those gaps. This is a where is the gap in security programs hacking prevention awareness training for it security diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like problems, gap, solutions. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Checklist Logging And Monitoring Cloud Computing Security IT Ppt Show Example PDF
This slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. This is a cloud security checklist logging and monitoring cloud computing security it ppt show example pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like evaluation, organization, policies, potential, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
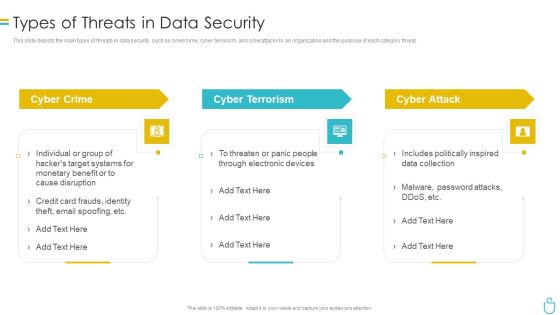
Information Security Types Of Threats In Data Security Ppt Layouts File Formats PDF
This slide depicts the main types of threats in data security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. This is a information security types of threats in data security ppt layouts file formats pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like cyber crime, cyber terrorism, cyber attack. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF
This slide represents the lifecycle of incident response which enables organizations to quickly detect and halt attacks, minimize damage and prevent future attacks of same type. It includes four phases of cyber security incident response such as preparation, detection and analysis etc. There are so many reasons you need a Implementing Cyber Security Incident Cyber Security Incident Response Lifecycle Brochure PDF. The first reason is you cannot spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF
Make sure to capture your audiences attention in your business displays with our gratis customizable Key Stakeholders Of Cyber Security Awareness Training Ppt Ideas Good PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes KPIs such as total intrusion attempts, mean detect team, mean resolve time etc. Present like a pro with Implementing Cyber Security Incident Cyber Security Systems Monitoring Report Icons PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

IT Security Automation Systems Guide Security Automation Integrates Tools Systems And Processes Graphics PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Slidegeeks is here to make your presentations a breeze with IT Security Automation Systems Guide Security Automation Integrates Tools Systems And Processes Graphics PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF
This slide consists of the major pros and cons of using everything as a service XaaS in business organizations. Elements covered include cost savings, scalability, security, downtime, etc. Presenting Pros And Cons Of Using Cloud Service Xaas In Business Formats PDF to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including Cost Savings, Scalability, Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Big Data Security Model Ppt Presentations
This is a big data security model ppt presentations. This is a three stage process. The stages in this process are security model, confidentiality, availability, integrity.

Cyber Security Ppt PowerPoint Presentation Slides Cpb
This is a cyber security ppt powerpoint presentation slides cpb. This is a three stage process. The stages in this process are cyber security.

Software Testing Service Delivery Excellence Model Mockup PDF
This slide showcases delivery excellence framework for software testing services which helps integrate business processes across diverse technologies. It provides information regarding end to end testing, test automation, data testing and security testing. Showcasing this set of slides titled Software Testing Service Delivery Excellence Model Mockup PDF. The topics addressed in these templates are Performance Testing, Digital Test Assurance, Security Testing. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Workforce Security Realization Coaching Plan Highest Number Of Malware Attacks On Departments Professional PDF
This slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an awe-inspiring pitch with this creative workforce security realization coaching plan highest number of malware attacks on departments professional pdf bundle. Topics like sales department, accounts department, it department can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF
This slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Present like a pro with Open Radio Access Network IT Role Of Security In Open RAN Standards Inspiration PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Business Data Protection Security Mechanism Portrait PDF
This slide exhibits broad categories in data protection which are traditional data protection, data security and privacy. It further includes data retention, backup, preventing data loss, risk monitoring, data governance, third party contracts, etc.Showcasing this set of slides titled Business Data Protection Security Mechanism Portrait PDF. The topics addressed in these templates are Data Retention, Physical Infrastructure, Date Security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Picture Of Cyber Security Background Ppt PowerPoint Presentation Layouts Layout
Presenting this set of slides with name picture of cyber security background ppt powerpoint presentation layouts layout. This is a one stage process. The stage in this process is picture of cyber security background. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
System Security Vector Icon Ppt PowerPoint Presentation Model Templates
Presenting this set of slides with name system security vector icon ppt powerpoint presentation model templates. This is a four stage process. The stages in this process are system security vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Cyber Security System Image Ppt PowerPoint Presentation Styles Microsoft PDF
Presenting this set of slides with name cyber security system image ppt powerpoint presentation styles microsoft pdf. This is a three stage process. The stages in this process are cyber security system image. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF
This slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Get a simple yet stunning designed IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit IT Security Automation Systems Guide Impacts Of Ineffective Information Technology Security Infographics PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF
This slide talks about the data security pillar of the cloud access security broker pillar. This slide highlights how CASB data security can help organizations improve their IT requirements and business operations and detect security breaches before they happen. Slidegeeks is here to make your presentations a breeze with Cloud Access Security Broker Pillar Data Security Ppt PowerPoint Presentation File Model PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
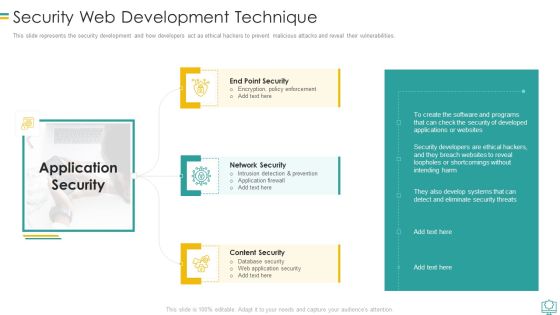
Security Web Development Technique Mockup PDF
This slide represents the security development and how developers act as ethical hackers to prevent malicious attacks and reveal their vulnerabilities.This is a Security Web Development Technique Mockup PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection And Prevention, Encryption Policy Enforcement, Database Security You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF
This slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Deliver and pitch your topic in the best possible manner with this Cybersecurity Risk Administration Plan System Categorization Worksheet Download PDF Use them to share invaluable insights on Accessible Within Organization, Individual System, Accessible To Key Shareholders and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF
This slide represents the data loss threat of cloud security, it is essential to secure organization data and create backups. Presenting Cloud Information Security Cloud Security Threats Loss Of Data Ppt Layouts Example PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Provider Wisely, Procedures Strategies, Storage Locations. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Security How Is Automation Used In Data Security Ppt Model Graphics Template PDF
This slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting information security how is automation used in data security ppt model graphics template pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human augmentation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Make sure to capture your audiences attention in your business displays with our gratis customizable Cyber Security Automation Framework Different Security Automation Tools With Pros And Cons Clipart PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.
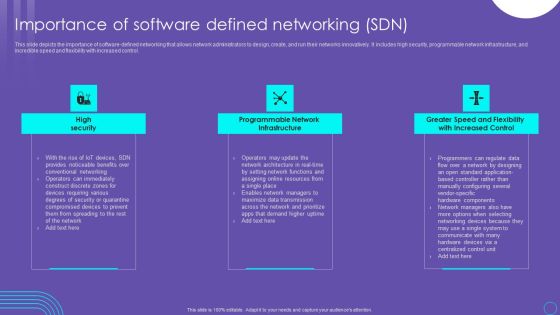
SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF
This slide depicts the importance of software defined networking that allows network administrators to design, create, and run their networks innovatively. It includes high security, programmable network infrastructure, and incredible speed and flexibility with increased control. Are you searching for a SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download SDN Security Architecture Importance Of Software Defined Networking SDN Graphics PDF from Slidegeeks today.
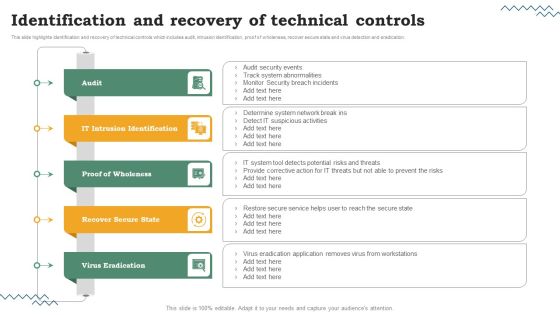
Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF
This slide highlights identification and recovery of technical controls which includes audit, intrusion identification, proof of wholeness, recover secure state and virus detection and eradication. Slidegeeks is here to make your presentations a breeze with Risk Evaluation Of Information Technology Systems Identification And Recovery Of Technical Controls Designs PDF With our easy-to-use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether youre giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF
This slide showcases the merits and demerits of bring your own device to understand its working before implementation. It also includes advantages such as economical for smart up, new tools and features, etc. Presenting Pros And Cons Of Bring Your Own Device Security Policy Within An Organization Sample PDF to dispense important information. This template comprises two stages. It also presents valuable insights into the topics including Data Protection, Organization, Company Information. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF
This slide outlines the driving trends for security operations modernization. The purpose of this slide is to highlight the leading trends that drive the modernization of security operations centers. The main drivers include cloud platform coverage, a shift to identify-centric security, IoT and OT coverage, etc. Present like a pro with Cybersecurity Operations Cybersecops Security Operations Modernization Driving Slides PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart
With Our Stock Photo Business Strategy Examples Piggy Bank Security Lock Clipart Powerpoint Templates You Will Be Doubly Sure. They Possess That Stamp Of Authority. Our Security Powerpoint Templates Do It In Double Quick Time. Speed Up The Process In A Tangible Way.
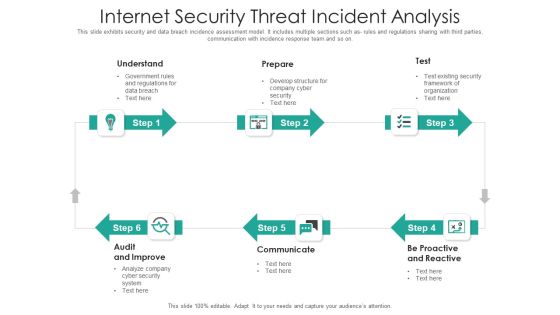
Internet Security Threat Incident Analysis Mockup PDF
This slide exhibits security and data breach incidence assessment model. It includes multiple sections such as- rules and regulations sharing with third parties, communication with incidence response team and so on. Presenting internet security threat incident analysis mockup pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including proactive and reactive, communicate, audit and improve. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
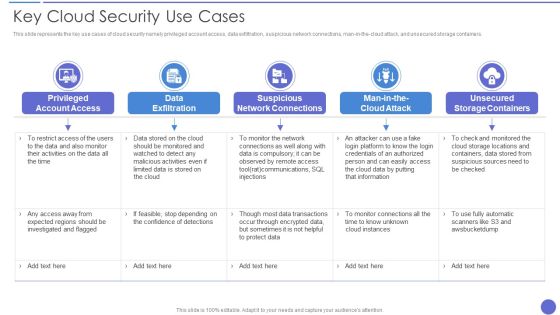
Key Cloud Security Use Cases Elements PDF
This slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers. Presenting Key Cloud Security Use Cases Elements PDF to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like Data Exfiltration, Suspicious Network Connections, Privileged Account Access. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF
This slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. This is a IT Security Automation Tools Integration Security Automation Integrates Tools Systems Summary PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intrusion Detection System, Firewalls, Secure Email Gateways. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF
This slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Make sure to capture your audiences attention in your business displays with our gratis customizable IT Security Automation Systems Guide Security Automation Architecture With Key Elements Inspiration PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Architecture Of Google Cloud Service Platform Professional PDF
This slide showcases google cloud platform service architecture. This further includes operational excellence, security, privacy, and compliance, reliability, cost optimization and performance optimization. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Architecture Of Google Cloud Service Platform Professional PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Three Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Sample
Presenting our jaw dropping three months enterprise it automation machinery road mapping with security and compliance sample. You can alternate the color, font size, font type, and shapes of this PPT layout according to your strategic process. This PPT presentation is compatible with Google Slides and is available in both standard screen and widescreen aspect ratios. You can also download this well researched PowerPoint template design in different formats like PDF, JPG, and PNG. So utilize this visually appealing design by clicking the download button given below.
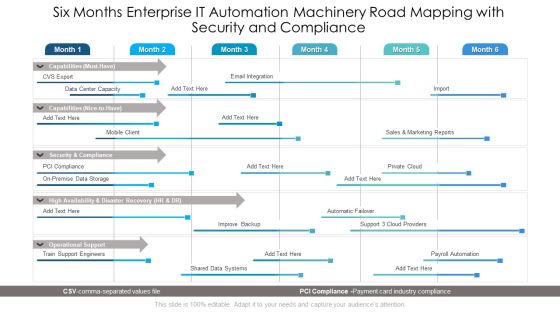
Six Months Enterprise IT Automation Machinery Road Mapping With Security And Compliance Professional
We present our six months enterprise it automation machinery road mapping with security and compliance professional. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched six months enterprise it automation machinery road mapping with security and compliance professional in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Information Technology IT Security Analysis For Small Business Information PDF
This slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Showcasing this set of slides titled Information Technology IT Security Analysis For Small Business Information PDF. The topics addressed in these templates are Security Risk, Security Threat, Impact Of Risk. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Cyber Security Vector Icon Ppt PowerPoint Presentation Inspiration
Presenting this set of slides with name cyber security vector icon ppt powerpoint presentation inspiration. This is a one stage process. The stages in this process are technology, social network, social engineering. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
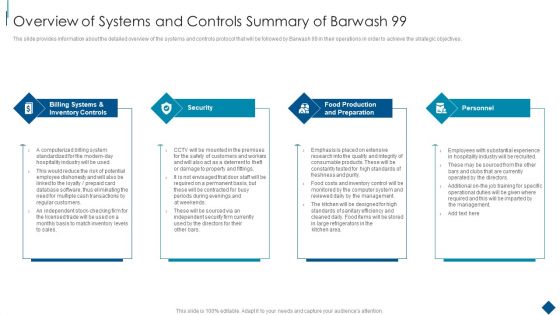
Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF
The slide provides information about the detailed overview of the systems and controls protocol that will be followed by Barwash 99 in their operations in order to achieve the strategic objectives. Presenting Confidential Information Memorandum Overview Of Systems And Controls Summary Guidelines PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Billing Systems Inventory, Controls Security Personnel, Food Production Preparation. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Developing Firm Security Strategy Plan Facilities Offered By Implementation Of Security Centre Formats PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a developing firm security strategy plan facilities offered by implementation of security centre formats pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
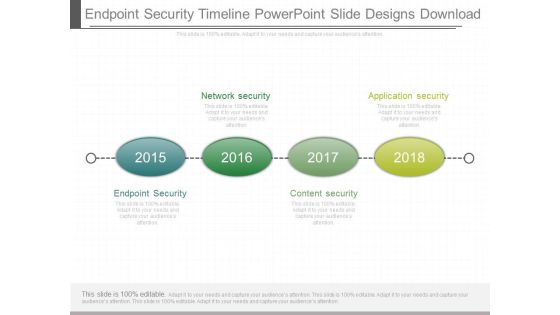
Endpoint Security Timeline Powerpoint Slide Designs Download
This is a endpoint security timeline powerpoint slide designs download. This is a four stage process. The stages in this process are network security, application security, endpoint security, content security.

 Home
Home