AI PPT Maker
Templates
PPT Bundles
Design Services
Business PPTs
Business Plan
Management
Strategy
Introduction PPT
Roadmap
Self Introduction
Timelines
Process
Marketing
Agenda
Technology
Medical
Startup Business Plan
Cyber Security
Dashboards
SWOT
Proposals
Education
Pitch Deck
Digital Marketing
KPIs
Project Management
Product Management
Artificial Intelligence
Target Market
Communication
Supply Chain
Google Slides
Research Services
 One Pagers
One PagersAll Categories
-
Home
- Customer Favorites
- Safety Management
Safety Management

Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Formulating a presentation can take up a lot of effort and time, so the content and message should always be the primary focus. The visuals of the PowerPoint can enhance the presenters message, so our Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF was created to help save time. Instead of worrying about the design, the presenter can concentrate on the message while our designers work on creating the ideal templates for whatever situation is needed. Slidegeeks has experts for everything from amazing designs to valuable content, we have put everything into Cyber Security Automation Framework Domain Security Controls That Can Be Automated Clipart PDF.

Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF
This slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain.Find highly impressive Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Security Automation To Analyze And Mitigate Cyberthreats Domain Security Controls That Microsoft PDF for your upcoming presentation. All the presentation templates are 100 precent editable and you can change the color and personalize the content accordingly. Download now.
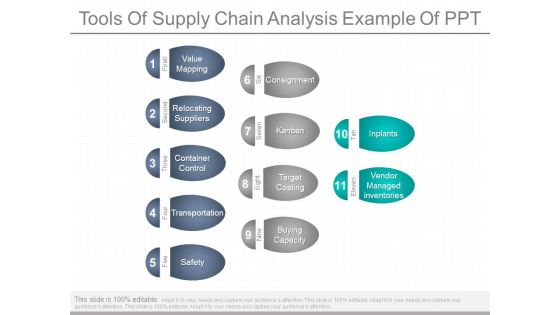
Tools Of Supply Chain Analysis Example Of Ppt
This is a tools of supply chain analysis example of ppt. This is a eleven stage process. The stages in this process are first, value mapping, second, relocating suppliers, three, container control, four, transportation, five, safety, six, consignment, seven, kanban, eight, target costing, nine, buying capacity, ten, inplants, eleven, vendor managed inventories.

CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Want to ace your presentation in front of a live audience Our CYBER Security Breache Response Strategy Comparative Analysis Of Cyber Security Incident Mitigation Guidelines PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF
The following slide showcases comparison of different cloud infrastructure securities which provides continuous monitoring and support for improvement and better management of security. It presents information related to Microsoft defender, identity manager, etc. Showcasing this set of slides titled Comparative Assessment Of Cloud Infra Cyber Security Solution Professional PDF. The topics addressed in these templates are Software, Services, Security Layer. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

The Big Idea Ppt PowerPoint Presentation Show
This is a the big idea ppt powerpoint presentation show. This is a one stage process. The stages in this process are safety, key, business, marketing.

Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Presenting this PowerPoint presentation, titled Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF, with topics curated by our researchers after extensive research. This editable presentation is available for immediate download and provides attractive features when used. Download now and captivate your audience. Presenting this Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF. Our researchers have carefully researched and created these slides with all aspects taken into consideration. This is a completely customizable Comparative Analysis Of Cyber Security Incident Mitigation Software Diagrams PDF that is available for immediate downloading. Download now and make an impact on your audience. Highlight the attractive features available with our PPTs.

Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. If you are looking for a format to display your unique thoughts, then the professionally designed Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Comparative Analysis Of Cyber Security Incident Mitigation Software Rules PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF
This slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Deliver an awe inspiring pitch with this creative Cloud Security Assessment How Does Cloud Security Work Legal Compliance Microsoft PDF bundle. Topics like Provide Limited, Personnel To Protect, Authentication Processes can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Tools For Risk Evaluation Chart Ppt Files
This is a tools for risk evaluation chart ppt files. This is a six stage process. The stages in this process are quality, safety, schedule, legal, security, cost.
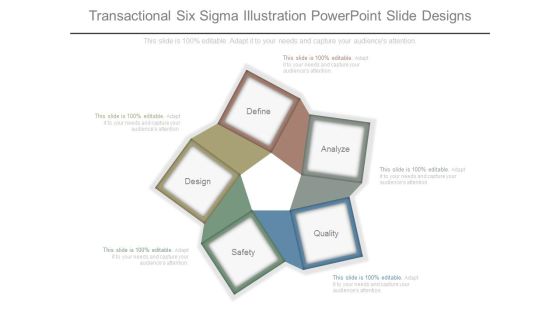
Transactional Six Sigma Illustration Powerpoint Slide Designs
This is a transactional six sigma illustration powerpoint slide designs. This is a five stage process. The stages in this process are define, design, safety, quality, analyze.
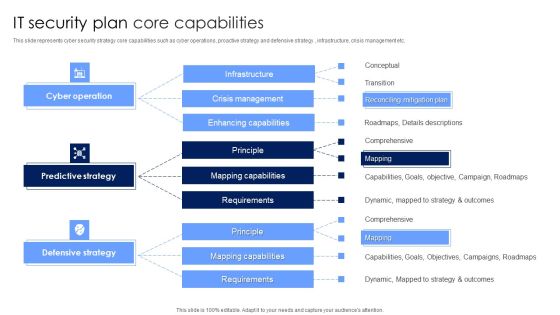
IT Security Plan Core Capabilities Rules PDF
This slide represents cyber security strategy core capabilities such as cyber operations, proactive strategy and defensive strategy , infrastructure, crisis management etc. Showcasing this set of slides titled IT Security Plan Core Capabilities Rules PDF. The topics addressed in these templates are Defensive Strategy, Predictive Strategy, Cyber Operation. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.
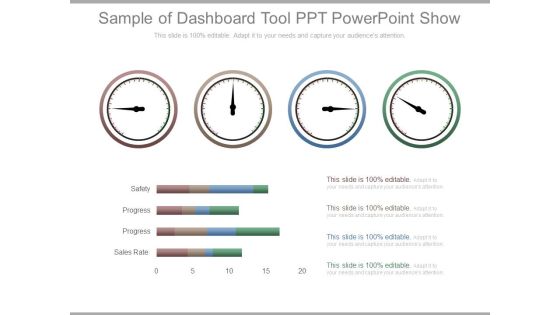
Sample Of Dashboard Tool Ppt Powerpoint Show
This is a sample of dashboard tool ppt powerpoint show. This is a four stage process. The stages in this process are safety, progress, sales rate.

Business Departments Performance Metrics Ppt Slides
This is a business departments performance metrics ppt slides. This is a seven stage process. The stages in this process are engineering, construction, maintenance, operations, safety, finance, environment.

Digital Dashboard Resource Kit Ppt Powerpoint Slides Design
This is a digital dashboard resource kit ppt powerpoint slides design. This is a four stage process. The stages in this process are sales rate, progress, profits, safety.

Building Positive Relationships Example Ppt Design
This is a building positive relationships example ppt design. This is a seven stage process. The stages in this process are safety, trust, respect, connect, identify, close, plan.
Life Insurance Marketing Plan Template Ppt Summary
This is a life insurance marketing plan template ppt summary. This is a five stage process. The stages in this process are safety, help, confidence, protection, coverage.

Agency Performance Ppt PowerPoint Presentation Background Designs
This is a agency performance ppt powerpoint presentation background designs. This is a four stage process. The stages in this process are transcore, viewability, brand safety, ad fraud.

Dashboard Ppt PowerPoint Presentation Files
This is a dashboard ppt powerpoint presentation files. This is a four stage process. The stages in this process are sales rate, progress, profits, safety.

Workforce Security Realization Coaching Plan The ROI Of Security Awareness Training Pictures PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this workforce security realization coaching plan the roi of security awareness training pictures pdf. Use them to share invaluable insights on security awareness training and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
The Roi Of Security Awareness Training Hacking Prevention Awareness Training For IT Security Icons PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this the roi of security awareness training hacking prevention awareness training for it security icons pdf. Use them to share invaluable insights on organizations, training, security, costs and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Some Data Security Measures To Overcome Cybersecurity Threats By ABS Healthcare Company Introduction PDF
The slide shows some measures that can be adopted by the company in order to ensure data protection and restrict access such Get Customized security programs, Inculcate organizations with healthcare threat intelligence softwares, get updated with latest security management softwares, ensure insider Threat protection etc. This is a some data security measures to overcome cybersecurity threats by ABS healthcare company introduction pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like restrict data accessibility, programs and firewall softwares, security management, techniques and provide. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF
This slide shows the dashboard representing details related to management of supply chain risks by the incident management team. It includes details related to KPIs such as policy and compliance, resource security hygiene etc. Slidegeeks is here to make your presentations a breeze with Implementing Cyber Security Incident Cyber Supply Chain Risk Dashboard Download PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.

Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF
This slide provides information regarding ITIL process areas in terms of service strategy and service design and associated sequential activities. Deliver an awe inspiring pitch with this creative Adopting Information Technology Infrastructure Addressing ITIL Process Areas Service Transition Sample PDF bundle. Topics like Sequential Activities Processes, Strategy Management Execution, Sequential Activities Security can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF
This slide represents the comparison between various cyber security incident management softwares based on multiple parameters to help organization select the best incident management software for their organization. It includes comparison between softwares based on user rating, price, mobile support etc. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Incident Response Techniques Deployement Comparative Analysis Of Cyber Security Incident Mitigation Software Summary PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

SIEM Services Traditional SIEM Deployment Model Ppt Gallery Layout Ideas PDF
This slide covers the traditional in-house SIEM model wherein the client take care of all the security incident and event management process on its own. Deliver an awe inspiring pitch with this creative siem services traditional siem deployment model ppt gallery layout ideas pdf bundle. Topics like alerting, analytics, reporting, retention can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
The Roi Of Security Awareness Training Ppt Infographics Icon PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber conscious workforce. Deliver an awe inspiring pitch with this creative the roi of security awareness training ppt infographics icon pdf bundle. Topics like the roi of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Certified Information Systems Security Professional Cissp Examination Details Elements PDF
This slide covers information about CISSP Examination such as weight of each domain in exams, prep courses details, qualification details etc. Deliver an awe inspiring pitch with this creative certified information systems security professional cissp examination details elements pdf bundle. Topics like requirements, network security, security engineering, management can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Securities Allocation Dashboard For Project Metrics Information PDF
This slide shows the securities allocation dashboard for project management which focuses on expenses incurred on project which includes cash, commends, revenues and inventory with total allocation of securities with the percentage. Showcasing this set of slides titled Securities Allocation Dashboard For Project Metrics Information PDF. The topics addressed in these templates are Inventory, Project, Revenues. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Employee Security Awareness Training Budget Ppt Infographics Shapes PDF
This slide covers the training budget along with topics, provider, training date, duration, qualification, capability level and refresh or renewal status. Deliver an awe inspiring pitch with this creative employee security awareness training budget ppt infographics shapes pdf bundle. Topics like management program, secure network, budget can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Comparative Analysis Between Public And Private Cloud Administration System Sample PDF
This slide showcases distinguish between public and private cloud management platforms based on various basis. It also includes development testing, training services, environment security, flexibility, etc. Showcasing this set of slides titled Comparative Analysis Between Public And Private Cloud Administration System Sample PDF. The topics addressed in these templates are Storage Location, Security, Flexibility. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF
Following slide displays information about the companys cyber security control scenario setting. It includes scenario detail, category of security controls and controls description. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Setting Scenario For Cybersecurity Control Professional PDF bundle. Topics like Technical Controls, Management Controls, Operational Controls can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
Food Process Tracking With Control Chart Food Security Excellence Ppt Inspiration Graphics Example PDF
The quality team will use control chart as food quality management tool. It will help in determining the food processes are stable and capable under provided conditions. Deliver an awe inspiring pitch with this creative food process tracking with control chart food security excellence ppt inspiration graphics example pdf bundle. Topics like action plan, resources, chart analysis can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cyber Security Administration In Organization Addressing Natural Calamities Posing Threat Sample PDF
This slide provides details regarding natural calamities posing as threat to organization and threat management checklist during nature crisis. Deliver an awe inspiring pitch with this creative cyber security administration in organization addressing natural calamities posing threat sample pdf bundle. Topics like sources, evacuation, environmental, contamination can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF
Presenting Table Of Contents Information Security Risk Evaluation And Administration Plan Slide Slides PDF to provide visual cues and insights. Share and navigate important information on one stage that need your due attention. This template can be used to pitch topics like Process Formulate, Management Plan, Mitigating Information. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF
This slide represents the budget prepared to predict cash flows and allocate required resources for incident management training. It includes training budget of IT, HR, operations, and finance department etc. There are so many reasons you need a Deploying Cyber Security Incident Response Administration Budget Allocation For Cyber Incident Microsoft PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Competitive Advantage Real Time Assessment Of Security Threats SIEM Pictures PDF
This slide covers the competitive advantage scoring for security information and event management based on different factors such as value, deployment, ease of use, support, etc. Deliver an awe inspiring pitch with this creative competitive advantage real time assessment of security threats siem pictures pdf bundle. Topics like siem competitive advantage can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Data Breach Prevention Recognition The ROI Of Security Awareness Training Brochure PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver an awe-inspiring pitch with this creative data breach prevention recognition the roi of security awareness training brochure pdf bundle. Topics like the roi of security awareness training can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Organizational Network Staff Learning The ROI Of Security Awareness Training Designs PDF
This slide covers the security awareness rate of interest calculations including typical cyber risk management factor for a trained, cyber-conscious workforce. Deliver and pitch your topic in the best possible manner with this organizational network staff learning the roi of security awareness training designs pdf. Use them to share invaluable insights on employee training program, security awareness training platform, productivity loss and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
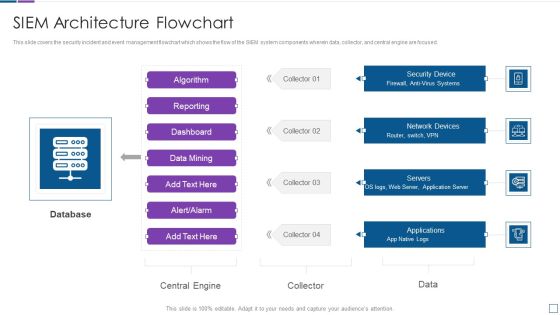
Real Time Assessment Of Security Threats SIEM Architecture Flowchart Sample PDF
This slide covers the security incident and event management flowchart which shows the flow of the SIEM system components wherein data, collector, and central engine are focused. Deliver an awe inspiring pitch with this creative real time assessment of security threats siem architecture flowchart sample pdf bundle. Topics like database, network devices, security device, servers, applications can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cybersecurity Monitoring Plan Steps In Detail Establish A Security Monitoring Strategy And Supporting Policies Microsoft PDF
Presenting cybersecurity monitoring plan steps in detail establish a security monitoring strategy and supporting policies microsoft pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like transactional monitoring, develop and execute, incident management plan. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF
Persuade your audience using this 8 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Rules PDF. This PPT design covers eight stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Security Plan, Management Program. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
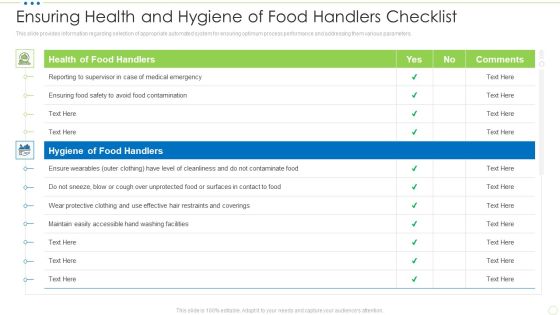
Ensuring Health And Hygiene Of Food Handlers Checklist Food Security Excellence Ppt Slides Graphics PDF
This slide provides information regarding checklist for health and hygiene of food handler to ensure maximum sanitation during food management process. TDeliver and pitch your topic in the best possible manner with this ensuring health and hygiene of food handlers checklist food security excellence ppt slides graphics pdf. Use them to share invaluable insights on health of food handlers, hygiene of food handlers and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Security Functioning Centre Essential Roles And Responsibilities Involved In Secops Diagrams PDF
This slide portrays information regarding the roles and responsibilities, qualification associated to staff available at Tier1, 2, 3, and 4 level at SOC structure. Deliver an awe inspiring pitch with this creative security functioning centre essential roles and responsibilities involved in secops diagrams pdf bundle. Topics like project management skills, communication skills, prioritization can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

4 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Graphics PDF
Persuade your audience using this 4 Stages To Developing Cloud Security Plan With Jigsaw Puzzle Graphics PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Business Goals, Management Program, Continuously Improve. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Efficiency Administration Software Investor Financing Different Phases Depicting Progressive Professional PDF
This slide caters details about progressive evolution of business productivity management platform through different phases. This is a efficiency administration software investor financing different phases depicting progressive professional pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like application, networking, services, secured digital. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
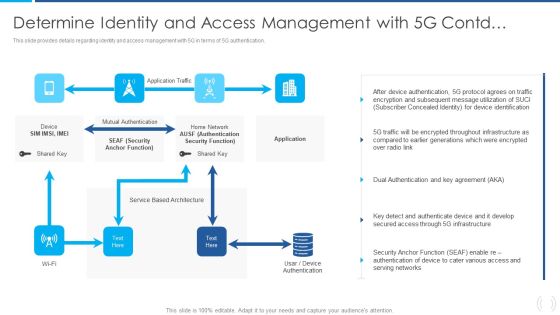
Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF
This slide provides details regarding identity and access management with 5G in terms of 5G authentication. Deliver and pitch your topic in the best possible manner with this Proactive Method For 5G Deployment By Telecom Companies Determine Identity And Acces Microsoft PDF Structure PDF Use them to share invaluable insights on Mutual Authentication, Authentication Security, Service Based and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Incident Response Techniques Deployement Impact Of Cybersecurity Incidents On Organization Clipart PDF
This slide represents the impact of events which indicates that organizations data has been compromised for unlawful activities. It includes impact of cyber security events such as increased costs, operational disruption, reputational damage etc. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Incident Response Techniques Deployement Cyber Security Incident Management Team Structure Diagrams PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Execute Operational Procedure Plan Steps In Detail Developing An Implementation Plan And Timeline Pictures PDF
This slide provides information about the Fifth and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline.This is a execute operational procedure plan steps in detail developing an implementation plan and timeline pictures pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like implementation plan, stakeholders to define, identify problem to be solved. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Operational Process Improvement Plan Steps In Detail Process Analysis Microsoft PDF
This slide provides information about the second and the foremost step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Process Analysis. This is a operational process improvement plan steps in detail process analysis microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like analysis process, resources, deploying, implementation. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
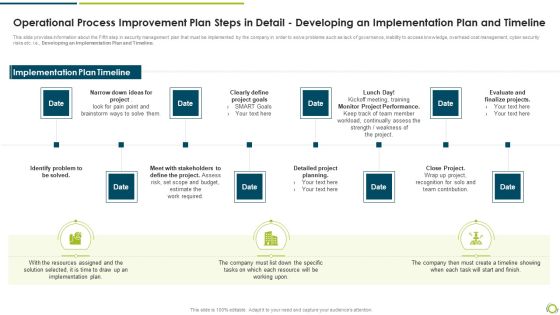
Operational Process Improvement Plan Steps In Detail Developing An Implementation Plan And Timeline Demonstration PDF
This slide provides information about the Fifth step in security management plan that must be implemented by the company in order to solve problems such as lack of governance, inability to access knowledge, overhead cost management, cyber security risks etc. i.e., Developing an Implementation Plan and Timeline.This is a operational process improvement plan steps in detail developing an implementation plan and timeline demonstration pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like identify problem to be solved, clearly define project goals, monitor project performance. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF
This slide signifies the business governance operating model to improve decision making. It includes steps like security management plan, executive security board, strategic direction and operations.Pitch your topic with ease and precision using this Corporate Governance Operating Framework To Improve Decision Making Diagrams PDF. This layout presents information on Executive Security, Direction Governance, Communications Technology. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

ATS Administration To Improve Bluetooth Low Energy BLE Asset Tracking Technique Ideas PDF
This slide covers key features and components of Bluetooth low energy technique for effective asset tracking. It involves real time tracking, cloud based security, email and messages notifications. Whether you have daily or monthly meetings, a brilliant presentation is necessary. ATS Administration To Improve Best Practices For Effective Inventory Management Inspiration PDF can be your best option for delivering a presentation. Represent everything in detail using ATS Administration To Improve Best Practices For Effective Inventory Management Inspiration PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Cloud Computing Scalability Impact On The Organization After Removing Multi Cloud Diagrams PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. Are you in need of a template that can accommodate all of your creative concepts This one is crafted professionally and can be altered to fit any style. Use it with Google Slides or PowerPoint. Include striking photographs, symbols, depictions, and other visuals. Fill, move around, or remove text boxes as desired. Test out color palettes and font mixtures. Edit and save your work, or work with colleagues. Download Cloud Computing Scalability Impact On The Organization After Removing Multi Cloud Diagrams PDF and observe how to make your presentation outstanding. Give an impeccable presentation to your group and make your presentation unforgettable.

Cloud Based Computing Analysis Impact On The Organization After Removing Multi Graphics PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies. If you are looking for a format to display your unique thoughts, then the professionally designed Cloud Based Computing Analysis Impact On The Organization After Removing Multi Graphics PDF is the one for you. You can use it as a Google Slides template or a PowerPoint template. Incorporate impressive visuals, symbols, images, and other charts. Modify or reorganize the text boxes as you desire. Experiment with shade schemes and font pairings. Alter, share or cooperate with other people on your work. Download Cloud Based Computing Analysis Impact On The Organization After Removing Multi Graphics PDF and find out how to give a successful presentation. Present a perfect display to your team and make your presentation unforgettable.

Impact On The Organization After Removing Multicloud Complexity Cloud Computing Complexities And Solutions Sample PDF
This slide covers the impact on organization such as consistent policy and control, simplified management, enhance visibility, improved reliability and increased security after implementing multi cloud management strategies.Do you know about Slidesgeeks Impact On The Organization After Removing Multicloud Complexity Cloud Computing Complexities And Solutions Sample PDF These are perfect for delivering any kind od presentation. Using it, create PowerPoint presentations that communicate your ideas and engage audiences. Save time and effort by using our pre-designed presentation templates that are perfect for a wide range of topic. Our vast selection of designs covers a range of styles, from creative to business, and are all highly customizable and easy to edit. Download as a PowerPoint template or use them as Google Slides themes.
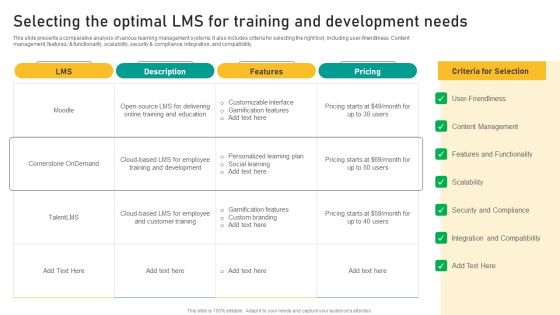
Talent Retention Initiatives For New Hire Onboarding Selecting The Optimal LMS For Training Designs PDF
This slide presents a comparative analysis of various learning management systems. It also includes criteria for selecting the right tool, including user-friendliness. Content management, features, and functionality, scalability, security and compliance, integration, and compatibility. Slidegeeks has constructed Talent Retention Initiatives For New Hire Onboarding Selecting The Optimal LMS For Training Designs PDF after conducting extensive research and examination. These presentation templates are constantly being generated and modified based on user preferences and critiques from editors. Here, you will find the most attractive templates for a range of purposes while taking into account ratings and remarks from users regarding the content. This is an excellent jumping off point to explore our content and will give new users an insight into our top notch PowerPoint Templates.

Big Data Analytics Service Framework Graphics PDF
Mentioned slide illustrates big data managed services which can be used by business to gather real time company analytics. It includes services such as data acquisition, storage, testing, monitoring, data security, analysis, architecture, development, migration and optimization. Persuade your audience using this Big Data Analytics Service Framework Graphics PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Data Analysis, Assessment Of Business, Management Infrastructure. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Monitoring Computer Software Application Introduction To Continuous Monitoring Ppt PowerPoint Presentation Model Files PDF
Presenting this set of slides with name monitoring computer software application introduction to continuous monitoring ppt powerpoint presentation model files pdf. This is a five stage process. The stages in this process are introduction, data security continuous monitoring, maintaining current awareness, knowledge security, vulnerabilities, and threats, support structure, risk management selections. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

All About Nagios Core Introduction To Continuous Monitoring Ppt PowerPoint Presentation Styles Infographics PDF
Presenting this set of slides with name all about nagios core introduction to continuous monitoring ppt powerpoint presentation styles infographics pdf. This is a five stage process. The stages in this process are introduction, data security continuous monitoring, maintaining current awareness, knowledge security, vulnerabilities, and threats, support structure, risk management selections. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
