Safety Management

Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF
This slide showcases table for allocating vulnerability rating to different class of information assets. It shows information about severity, vulnerability score and description. Are you searching for a Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Vulnerability Rating For Risk Identification Topics PDF from Slidegeeks today.
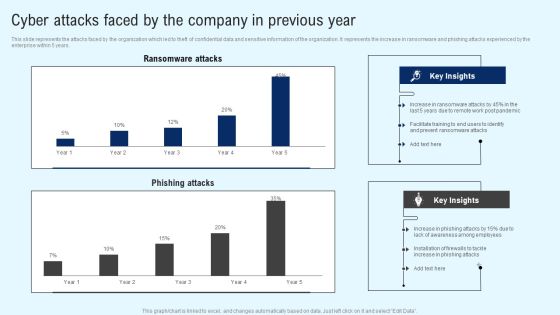
Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF
This slide represents the attacks faced by the organization which led to theft of confidential data and sensitive information of the organization. It represents the increase in ransomware and phishing attacks experienced by the enterprise within 5 years. Slidegeeks is one of the best resources for PowerPoint templates. You can download easily and regulate Implementing Cyber Security Incident Cyber Attacks Faced By The Company In Previous Year Information PDF for your personal presentations from our wonderful collection. A few clicks is all it takes to discover and get the most relevant and appropriate templates. Use our Templates to add a unique zing and appeal to your presentation and meetings. All the slides are easy to edit and you can use them even for advertisement purposes.

Structured Networking Process Diagram 7 Stages Ppt Security Business Plan PowerPoint Slides
We present our structured networking process diagram 7 stages ppt security business plan PowerPoint Slides.Download our Business PowerPoint Templates because It will get your audience in sync. Use our Network Diagrams PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines. Present our Shapes PowerPoint Templates because You can Hit a home run with our PowerPoint Templates and Slides. See your ideas sail into the minds of your audience. Download and present our Circle Charts PowerPoint Templates because Your ideas provide food for thought. Our PowerPoint Templates and Slides will help you create a dish to tickle the most discerning palate. Download our Curves and Lines PowerPoint Templates because Our PowerPoint Templates and Slides are topically designed to provide an attractive backdrop to any subject.Use these PowerPoint slides for presentations relating to art, business, button, chart, clip, communication, design, diagram, element, graph, graphic, green, icon, illustration, isolated, network, process, round, set, shape, shiny, symbol, teamwork, vector, web. The prominent colors used in the PowerPoint template are Gray, White, Black.
Pie Chart Circular 8 Stages Process Ppt Security Business Plan PowerPoint Templates
We present our pie chart circular 8 stages process ppt security business plan PowerPoint templates.Download our Business PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape. Download and present our Circle Charts PowerPoint Templates because You can Be the puppeteer with our PowerPoint Templates and Slides as your strings. Lead your team through the steps of your script. Use our Marketing PowerPoint Templates because Our PowerPoint Templates and Slides are truly out of this world. Even the MIB duo has been keeping tabs on our team. Download and present our Flow Charts PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Present our Shapes PowerPoint Templates because Our PowerPoint Templates and Slides will generate and maintain the level of interest you desire. They will create the impression you want to imprint on your audience.Use these PowerPoint slides for presentations relating to Chart, market, sales, business, concept, success, presentation, symbol, diagram, circle, finance, stock, report, marketing, analyzing, shape, graph, illustration, piece, pie, division, round, growth, progress, account, profit, part, information, background, statistic, financial. The prominent colors used in the PowerPoint template are Blue, Gray, White.

Hexagonal Unidirectional Shape For Process Flow Ppt Security Business Plan PowerPoint Templates
We present our hexagonal unidirectional shape for process flow ppt security business plan PowerPoint templates.Present our Business PowerPoint Templates because Our PowerPoint Templates and Slides will fulfill your every need. Use them and effectively satisfy the desires of your audience. Present our Puzzles or Jigsaws PowerPoint Templates because You canTake a leap off the starting blocks with our PowerPoint Templates and Slides. They will put you ahead of the competition in quick time. Download our Arrows PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Present our Hexagon PowerPoint Templates because Our PowerPoint Templates and Slides team portray an attitude of elegance. Personify this quality by using them regularly. Download our Leadership PowerPoint Templates because our PowerPoint Templates and Slides will give your ideas the shape.Use these PowerPoint slides for presentations relating to hexagon, honeycomb, 3d, abstract, background, vector, shelf, design, decoration, layout, achievement, business, blank, concept, sign, success, presentation, cube, bright, symbol, template, commercial, graphic, clean, element, marketing, technology, development, shape, modern, creative, illustration, decorative, up, frame, science, cover, trendy, banner, art, style, space. The prominent colors used in the PowerPoint template are Blue light, Gray, White.

3Rd Party API Integration To Check Security Ppt PowerPoint Presentation Gallery Example Topics PDF
Presenting 3rd party api integration to check security ppt powerpoint presentation gallery example topics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including check security, implementation, mission. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Business Intranet For Secure Communication Vector Icon Ppt PowerPoint Presentation Infographic Template Design Ideas PDF
Presenting business intranet for secure communication vector icon ppt powerpoint presentation infographic template design ideas pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including business intranet for secure communication vector icon. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Use Of AI In Financial Institution Industry To Improve Security Mockup PDF
Presenting Use Of AI In Financial Institution Industry To Improve Security Mockup PDF to dispense important information. This template comprises Four stages. It also presents valuable insights into the topics including Financial Institution, Industry Improve Security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF
This slide signifies the enterprise resource planning evaluation to increase IT security. It covers information about automated testing tool, check system functionality and quality assurance etc. Pitch your topic with ease and precision using this Enterprise Resource Planning Assessment Checklist To Improve IT Security Brochure PDF. This layout presents information on Checklist, Execution, Functionality. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF
This slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Training Program For Cloud Access Security Broker Ppt PowerPoint Presentation File Show PDF today and make your presentation stand out from the rest.

Cloud Intelligence Framework For Application Consumption Case Study 2 Banks Cyber Security Infrastructure Microsoft PDF
The slide provides the case study of a banking company that covered the details related to cybersecurity challenge faced by the bank, and major approach suggested by the technology company to resolve the challenges. This is a cloud intelligence framework for application consumption case study 2 banks cyber security infrastructure microsoft pdf template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like process workflows, industry standard security metrics, implemented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

5G Network Technology Value Enabler 1 5G Resilient Networks System Ppt Layouts Diagrams PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a 5g network technology value enabler 1 5g resilient networks system ppt layouts diagrams pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service availability, security assurance, secured identities and protocols. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
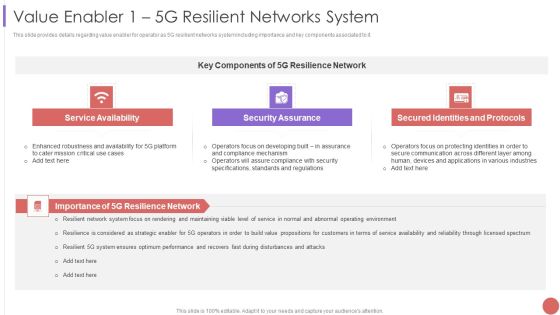
Value Enabler 1 5G Resilient Networks System Professional PDF
This slide provides details regarding value enabler for operator as 5G resilient networks system including importance and key components associated to it. This is a Value Enabler 1 5G Resilient Networks System Professional PDF template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service Availability, Security Assurance, Secured Identities. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Elements PDF
This slide provides information regarding the impact of successful implementation of effective CIOs strategic IT cost optimization in terms alert overall reduction in IT spend, reduction in operational expenses, reduction in security incidents and rise in team productivity, etc. This is a Impact Of Effective Cios Strategic IT Cost Optimization Initiatives Implementation Elements PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Service, Security Incidents, Team Productivity. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Digital Trends In Customer Finance Market Template PDF
The slide highlights various digital and tech based trends in consumer financing and lending market. It includes key components like better customer experience, enhanced security, greater Omni channel capabilities, Non banking institutions market entry and AI tools. Persuade your audience using this Digital Trends In Customer Finance Market Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate Data, Ensure Security, Lending Services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
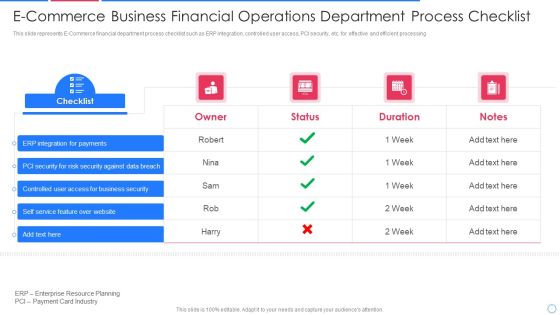
E Commerce Business Financial Operations Department Process Checklist Information PDF
This slide represents E-Commerce financial department process checklist such as ERP integration, controlled user access, PCI security, etc. for effective and efficient processing Pitch your topic with ease and precision using this e commerce business financial operations department process checklist information pdf This layout presents information on integration for payments, security for risk security against, controlled user access It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.
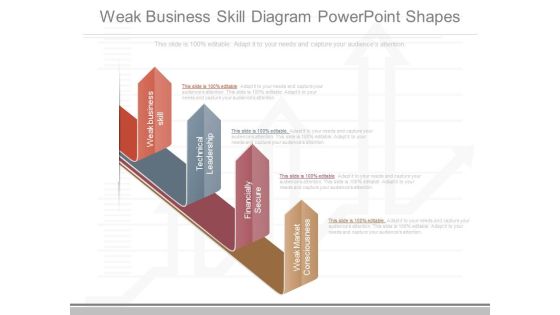
Weak Business Skill Diagram Powerpoint Shapes
This is a weak business skill diagram powerpoint shapes. This is a four stage process. The stages in this process are weak business skill, technical leadership, financially secure, weak market consciousness.

Information And Technology Security Operations How Firm Handle Insider Threats Pictures PDF
This slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. This is a information and technology security operations how firm handle insider threats pictures pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like employee training, it security and hr coordination, develop threat hunting team, implement user behavioral analytics. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Construction Project Plan With Secure Financing Ppt PowerPoint Presentation Gallery Gridlines PDF
Showcasing this set of slides titled construction project plan with secure financing ppt powerpoint presentation gallery gridlines pdf. The topics addressed in these templates are project tasks, contract writing, contract signing, secure financing, obtain permits, site work. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Evolution Of Wireless Technologies What Security Features Does 5G 5Th Generation Portrait PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF
This slide depicts the security features included in 5th generation technology, such as new cryptographic techniques for individual component protection, network slicing, encryption of IMSI to avoid eavesdropping spots, authentication confirmation, and secure network for sensitive data. Explore a selection of the finest Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF here. With a plethora of professionally designed and pre-made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Mobile Phone Generations 1G To 5G What Security Features Does 5G 5Th Generation Designs PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.

Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF
This slide talks about the skills required for security operation teams. The purpose of this slide is to showcase the various skills that can help SecOps to secure an organization completely. The primary skills include no-code automation, communicating modern threats from first principles, peer influence, and so on. Are you searching for a Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal. With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cybersecurity Operations Cybersecops Skills Required For Security Operations Teams Sample PDF from Slidegeeks today.

Cloud Capability Model For Strategy Architecture And Governance Clipart PDF
This slide covers the cloud capability model including strategy, architecture, governance, identity and security with data centre, platform, infrastructure and software as services.Are you searching for a Cloud Capability Model For Strategy Architecture And Governance Clipart PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you ve put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Cloud Capability Model For Strategy Architecture And Governance Clipart PDF from Slidegeeks today.

Business Information And Security Risk Mitigation Strategy Ppt PowerPoint Presentation File Format PDF
Persuade your audience using this business information and security risk mitigation strategy ppt powerpoint presentation file format pdf. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including business information and security risk mitigation strategy. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF
This slide showcases distinguish between bring your own device and choose your own device policies and programs for mobile devices. It also includes differentiation on basis such as benefits , challenges, etc. Pitch your topic with ease and precision using this Comparative Analysis Between Bring Your Own Device Security Policy And CYOD Mobile Device Programs Clipart PDF. This layout presents information on Basis, Benefits, Best Practices. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF
The following slide exhibits complete overview of Five Guys company related to food industry. Information covered in this slide is related to companys mission statement, major stakeholders, products offered, key details and facts and figures. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Securing Market Leadership Through Competitive Excellence Company Overview Five Guys Designs PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.
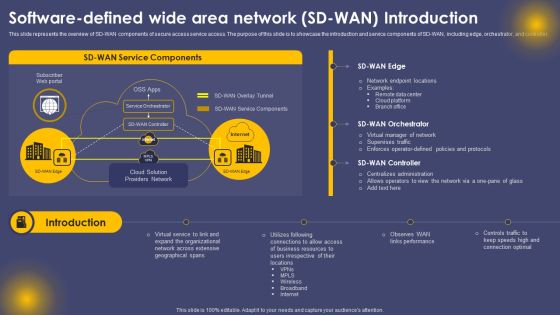
Software Defined Wide Area Network SD WAN Introduction Ppt Slides Objects PDF
This slide represents the overview of SD-WAN components of secure access service access. The purpose of this slide is to showcase the introduction and service components of SD-WAN, including edge, orchestrator, and controller. Present like a pro with Software Defined Wide Area Network SD WAN Introduction Ppt Slides Objects PDF Create beautiful presentations together with your team, using our easy to use presentation slides. Share your ideas in real time and make changes on the fly by downloading our templates. So whether you are in the office, on the go, or in a remote location, you can stay in sync with your team and present your ideas with confidence. With Slidegeeks presentation got a whole lot easier. Grab these presentations today.

Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF
This slide represents the report to effectively monitor the networks and systems of the organization. It includes kpis such as total intrusion attempts, mean detect team, mean resolve time etc. Do you have an important presentation coming up Are you looking for something that will make your presentation stand out from the rest Look no further than Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF. With our professional designs, you can trust that your presentation will pop and make delivering it a smooth process. And with Slidegeeks, you can trust that your presentation will be unique and memorable. So why wait Grab Incident Response Techniques Deployement Cyber Security Systems Monitoring Report Microsoft PDF today and make your presentation stand out from the rest.
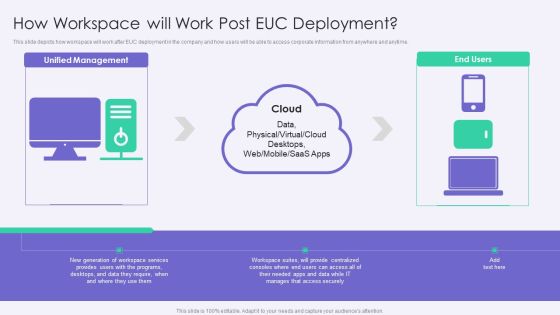
VID How Workspace Will Work Post EUC Deployment Template PDF
This slide depicts how workspace will work after EUC deployment in the company and how users will be able to access corporate information from anywhere and anytime.This is a VID How Workspace Will Work Post EUC Deployment Template PDF template with various stages. Focus and dispense information on one stage using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Workspace Services, Access Securely, Provide Centralized. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Prepare A Disaster Recovery Plan IT Security IT Ppt Ideas Graphics Design PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Presenting prepare a disaster recovery plan it security it ppt ideas graphics design pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like make a report of all assets, risk assessment report, identify the importance of assets. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
How Is Automation Used In Information Technology Security Ppt File Icon PDF
This slide depicts the network protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Presenting how is automation used in information technology security ppt file icon pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like threat detection, threat response, human detection. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Information Technology Security Prepare A Disaster Recovery Plan Ppt Ideas Inspiration PDF
This slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. This is a information technology security prepare a disaster recovery plan ppt ideas inspiration pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like risk assessment report, identify importance assets, report assets. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
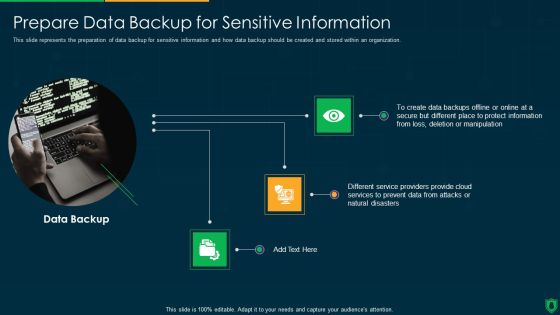
Info Security Prepare Data Backup For Sensitive Information Ppt PowerPoint Presentation File Rules PDF
This slide represents the preparation of data backup for sensitive information and how data backup should be created and stored within an organization. This is a info security prepare data backup for sensitive information ppt powerpoint presentation file rules pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like data backup, provide cloud, prevent data, natural disasters. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF
This slide represents the loss of intellectual property threat and how organizations get affected by these types of risks.This is a Cloud Security Assessment Theft Or Loss Of Intellectual Property Formats PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Intellectual Property, Examination Uncovered, Danger Presented. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF
This slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating.Deliver and pitch your topic in the best possible manner with this Information Security Risk Evaluation Threat Identification And Vulnerability Assessment For Risk Identification Graphics PDF. Use them to share invaluable insights on Vulnerability Severity, Unprotected Storage, Unprotected Communication and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF
This slide covers employee questionnaire to assess cybersecurity training program effectiveness. It involves questions to determine trainer effectiveness in teaching, knowledge and skills of trainer and details about training organization. Showcasing this set of slides titled Employee Questionnaire To Assess IT Security Awareness Training Program Effectiveness Graphics PDF. The topics addressed in these templates are Good Knowledge, Cyberattacks And Methods, Awareness Training. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Why IT Security Awareness Training Program Is Essential For Employees Background PDF
This slide covers need of cybersecurity awareness training withing organization. It involves reasons such as increases employee awareness, assures educated staff, enhances organizational reputation and boosts confidence. Presenting Why IT Security Awareness Training Program Is Essential For Employees Background PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Increases Awareness, Assures Educated Staff, Enhances Organizational Reputation. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF
The following slide showcases various approaches to AI infrastructure which bodes well for future of organizations association. It presents information related to regulatory framework, expert consultations, etc. Presenting Approaches To Improve Infra Cyber Security In AI Infrastructure Diagrams PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Regulatory Framework, Protect AI Related Data, Involve Cybersecurity Experts. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Need For Ethical Hacking Ppt Gallery Portfolio PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development and quality control, and evaluation of the companys security and regulatory compliance. This is a need for ethical hacking ppt gallery portfolio pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like quality control, development, security, system, measures. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF
This slide highlights the security guard company rules and regulations which showcases In and out time, note visitor name, and wear uniform at working hours. Deliver an awe inspiring pitch with this creative Manpower Corporate Security Business Profile Employees Rules And Regulations Formats PDF bundle. Topics like Security, Employees Rules And Regulations can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Computing Security Plan Five Years Roadmap For Data Protection Template
Introducing our cloud computing security plan five years roadmap for data protection template. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Computing Security Plan Half Yearly Roadmap For IT Project Introduction
Introducing our cloud computing security plan half yearly roadmap for it project introduction. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.

Cloud Computing Security Plan Six Months Roadmap With Multiple Phases Themes
Introducing our cloud computing security plan six months roadmap with multiple phases themes. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
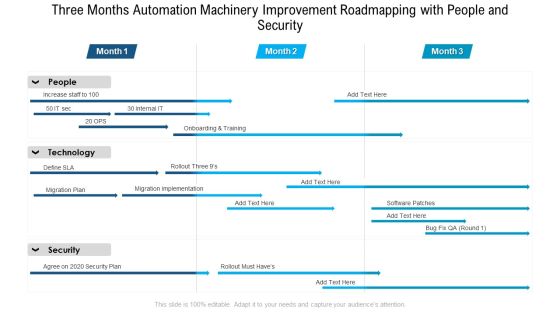
Three Months Automation Machinery Improvement Roadmapping With People And Security Designs
Introducing our three months automation machinery improvement roadmapping with people and security designs. This PPT presentation is Google Slides compatible, therefore, you can share it easily with the collaborators for measuring the progress. Also, the presentation is available in both standard screen and widescreen aspect ratios. So edit the template design by modifying the font size, font type, color, and shapes as per your requirements. As this PPT design is fully editable it can be presented in PDF, JPG and PNG formats.
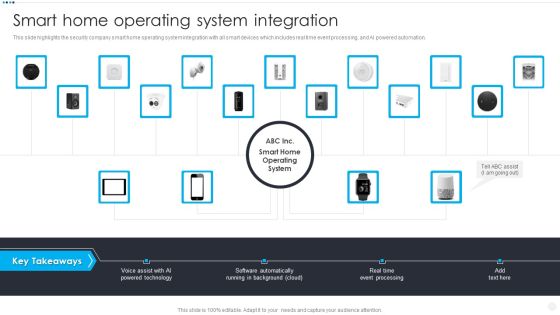
Smart Home Security Solutions Company Profile Smart Home Operating System Integration Elements PDF
This slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. This is a Smart Home Security Solutions Company Profile Smart Home Operating System Integration Elements PDF template with various stages. Focus and dispense information on one stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Voice Assist AI, Powered Technology Software, Automatically Running Background. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF
The purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Crafting an eye-catching presentation has never been more straightforward. Let your presentation shine with this tasteful yet straightforward Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF template. It offers a minimalistic and classy look that is great for making a statement. The colors have been employed intelligently to add a bit of playfulness while still remaining professional. Construct the ideal Key Benefits Of Cyber Security Awareness Training Ppt Model Mockup PDF that effortlessly grabs the attention of your audience Begin now and be certain to wow your customers

Analyzing And Implementing Effective CMS Importance Of Secure Ecommerce Payment Systems Portrait PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. This Analyzing And Implementing Effective CMS Importance Of Secure Ecommerce Payment Systems Portrait PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Analyzing And Implementing Effective CMS Importance Of Secure Ecommerce Payment Systems Portrait PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today.
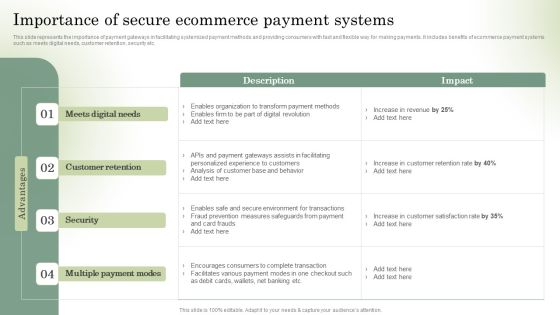
Optimizing Online Stores Importance Of Secure Ecommerce Payment Systems Clipart PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. This Optimizing Online Stores Importance Of Secure Ecommerce Payment Systems Clipart PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Optimizing Online Stores Importance Of Secure Ecommerce Payment Systems Clipart PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF
Mentioned slide provides information about the impact categories which can be used for effectively handling various cyber security incidents. Categories covered are function, information and recoverability impact. This Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Cyber Risks And Incident Response Playbook Impact Categories For Effectively Handling Cyber Security Incidents Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.

Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF
This slide showcase information security attacks faced by different departments of organization. Its key elements are department, number of cyber attacks and type of cyber attacks. Are you searching for a Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF that is uncluttered, straightforward, and original Its easy to edit, and you can change the colors to suit your personal or business branding. For a presentation that expresses how much effort you have put in, this template is ideal With all of its features, including tables, diagrams, statistics, and lists, its perfect for a business plan presentation. Make your ideas more appealing with these professional slides. Download Developing IT Security Strategy Cyber Attacks Faced By Different Departments Download PDF from Slidegeeks today.

Incident Response Techniques Deployement Cyber Security Incident Response Plan Timeline Pictures PDF
This slide represents the timeline representing the action plan to effectively respond to cyber security incidents experienced by the organization. It starts with preparation of cyber incident report and ends with return to normal flow. Explore a selection of the finest Incident Response Techniques Deployement Cyber Security Incident Response Plan Timeline Pictures PDF here. With a plethora of professionally designed and pre made slide templates, you can quickly and easily find the right one for your upcoming presentation. You can use our Incident Response Techniques Deployement Cyber Security Incident Response Plan Timeline Pictures PDF to effectively convey your message to a wider audience. Slidegeeks has done a lot of research before preparing these presentation templates. The content can be personalized and the slides are highly editable. Grab templates today from Slidegeeks.
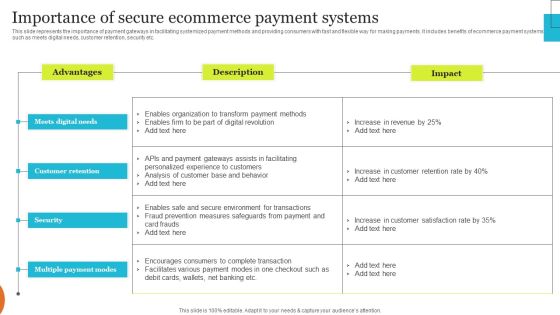
Implementing Effective Ecommerce Managemnet Platform Importance Of Secure Ecommerce Payment Summary PDF
This slide represents the importance of payment gateways in facilitating systemized payment methods and providing consumers with fast and flexible way for making payments. It includes benefits of ecommerce payment systems such as meets digital needs, customer retention, security etc. This Implementing Effective Ecommerce Managemnet Platform Importance Of Secure Ecommerce Payment Summary PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Implementing Effective Ecommerce Managemnet Platform Importance Of Secure Ecommerce Payment Summary PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF
The following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. This Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Determine Cyber Security Risks And Threats Ppt PowerPoint Presentation Diagram Lists PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, do not wait, grab the presentation templates today

Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF
This slide outlines the roadmap for deploying a cloud access security broker in an organization. The purpose of this slide is to showcase the various steps to implement the cloud access security broker model. The steps include starting with the most critical cloud application in the portfolio, looking for suitable CASB, etc. From laying roadmaps to briefing everything in detail, our templates are perfect for you. You can set the stage with your presentation slides. All you have to do is download these easy to edit and customizable templates. Cloud Access Security Broker Implementation Roadmap Ppt PowerPoint Presentation Diagram Lists PDF will help you deliver an outstanding performance that everyone would remember and praise you for. Do download this presentation today.

Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF
This slide describes the threat protection pillar of cloud access security broker. The purpose of this slide is to highlight how CASB can help organizations to detect threats in advance through machine learning algorithms. Whether you have daily or monthly meetings, a brilliant presentation is necessary. Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF can be your best option for delivering a presentation. Represent everything in detail using Cloud Access Security Broker Pillar Threat Protection Ppt PowerPoint Presentation File Pictures PDF and make yourself stand out in meetings. The template is versatile and follows a structure that will cater to your requirements. All the templates prepared by Slidegeeks are easy to download and edit. Our research experts have taken care of the corporate themes as well. So, give it a try and see the results.

Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF
This slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Get a simple yet stunning designed Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF. It is the best one to establish the tone in your meetings. It is an excellent way to make your presentations highly effective. So, download this PPT today from Slidegeeks and see the positive impacts. Our easy to edit Checklist To Adopt A Cloud Access Security Broker Ppt PowerPoint Presentation File Portfolio PDF can be your go to option for all upcoming conferences and meetings. So, what are you waiting for Grab this template today.

Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF
This slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Slidegeeks is here to make your presentations a breeze with Emerging Cloud Security Risks And Threats Ppt PowerPoint Presentation File Diagrams PDF With our easy to use and customizable templates, you can focus on delivering your ideas rather than worrying about formatting. With a variety of designs to choose from, you are sure to find one that suits your needs. And with animations and unique photos, illustrations, and fonts, you can make your presentation pop. So whether you are giving a sales pitch or presenting to the board, make sure to check out Slidegeeks first.
Five Steps Vulnerability Security Testing With Icon Ppt PowerPoint Presentation Inspiration Topics
Presenting this set of slides with name five steps vulnerability security testing with icon ppt powerpoint presentation inspiration topics. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Five Techniques Of Cyber Security Testing Ppt PowerPoint Presentation Layouts Model
Presenting this set of slides with name five techniques of cyber security testing ppt powerpoint presentation layouts model. This is a five stage process. The stages in this process are Penetration Testing, Internal Testing, Gaining access. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

 Home
Home