Safety Management System

Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF
This slide showcases the steps for digital certificate creating procedure with secure communication. It includes elements such as request generation, verification, obtaining public key and sending digital certificate. Showcasing this set of slides titled Online Certificate Creation Process With Secure Communication Ppt Layouts Inspiration PDF. The topics addressed in these templates are Certifying Authority, Key Communication, Digital Certificate. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Quarterly IT Innovation Approach Roadmap For Value And Security Benefit Elements
We present our quarterly it innovation approach roadmap for value and security benefit elements. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched quarterly it innovation approach roadmap for value and security benefit elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Cloud Computing Security Plan Three Months Roadmap With Key Enablers Elements
We present our cloud computing security plan three months roadmap with key enablers elements. This PowerPoint layout is easy to edit so you can change the font size, font type, color, and shape conveniently. In addition to this, the PowerPoint layout is Google Slides compatible, so you can share it with your audience and give them access to edit it. Therefore, download and save this well researched cloud computing security plan three months roadmap with key enablers elements in different formats like PDF, PNG, and JPG to smoothly execute your business plan.

Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF
This slide covers framework depicting top risks and threats for IIOT disrupting the operations and processes. It also includes integration of different technologies used to increase the security for IIOT operations such as virtual patching, behaviour analysis, anti malware, risk detection, anti spear phishing, spam protection, etc. Pitch your topic with ease and precision using this Integrating Iiot To Improve Operational Efficiency Security Reference Architecture Themes PDF. This layout presents information on Operational Technology, IT Business Process, Iot Platform Middleware . It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

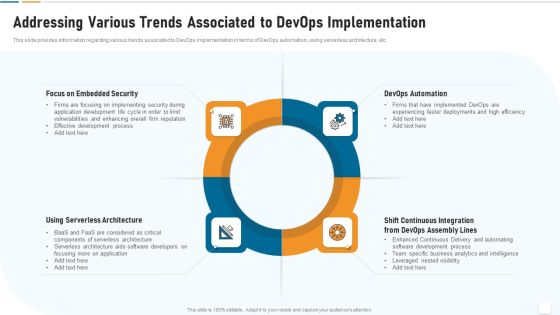
Addressing Various Trends Associated To Devops Implementation IT Infrastructure By Executing Devops Approach Mockup PDF
This slide provides information regarding various trends associated to DevOps implementation in terms of DevOps automation, using serverless architecture, etc. This is a addressing various trends associated to devops implementation it infrastructure by executing devops approach mockup pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like devops automation, continuous integration, devops assembly, serverless architecture, security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Strategic Development And Operations Execution IT Addressing Various Trends Associated Themes PDF
This slide provides information regarding various trends associated to DevOps implementation in terms of DevOps automation, using serverless architecture, etc. This is a strategic development and operations execution it addressing various trends associated themes pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like focus on embedded security, using serverless architecture, devops automation, shift continuous integration from devops assembly lines. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
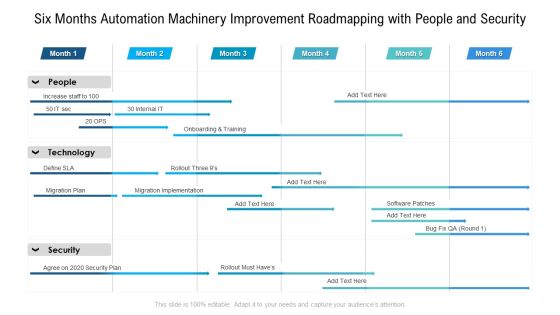
Six Months Automation Machinery Improvement Roadmapping With People And Security Brochure
Presenting the six months automation machinery improvement roadmapping with people and security brochure. The template includes a roadmap that can be used to initiate a strategic plan. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your needs. This PPT slide can be easily reached in standard screen and widescreen aspect ratios. The set is also available in various formats like PDF, PNG, and JPG. So download and use it multiple times as per your knowledge.

Information And Technology Security Operations Facilities Offered By Successful Implementation Guidelines PDF
This slide portrays information regarding the various facilities that are offered by successful implementation of SecOps in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. This is a information and technology security operations facilities offered by successful implementation guidelines pdf template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like malware detection and investigation, phishing detection and prevention, investigations by hr, risk mitigation of left employees. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Dispose Data And Equipment Properly IT Security IT Ppt Icon Clipart Images PDF
This slide depicts the importance of disposal of the data and equipment that is not in use anymore and restricts the employees who already left the organization. Presenting dispose data and equipment properly it security it ppt icon clipart images pdf to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like dispose data and equipment properly. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
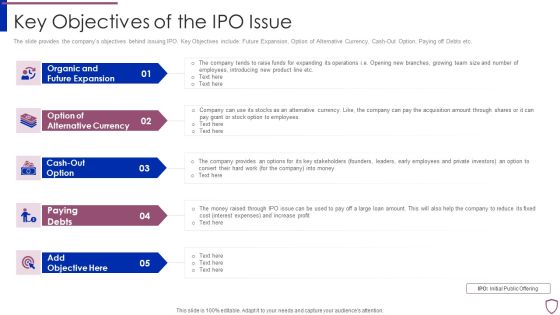
Financing Catalogue For Security Underwriting Agreement Key Objectives Of The IPO Issue Mockup PDF
The slide provides the companys objectives behind issuing IPO. Key Objectives include Future Expansion, Option of Alternative Currency, Cash-Out Option, Paying off Debts etc. Presenting financing catalogue for security underwriting agreement key objectives of the ipo issue mockup pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like organic and future expansion, option of alternative currency, cash out option, paying debts. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Digital Trends In Customer Finance Market Template PDF
The slide highlights various digital and tech based trends in consumer financing and lending market. It includes key components like better customer experience, enhanced security, greater Omni channel capabilities, Non banking institutions market entry and AI tools. Persuade your audience using this Digital Trends In Customer Finance Market Template PDF. This PPT design covers five stages, thus making it a great tool to use. It also caters to a variety of topics including Evaluate Data, Ensure Security, Lending Services. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Information Technology Policy And Processes Information Security Policy For Employees Structure PDF
This slide depicts the information security policy that critical topics covered in this policy. It also covers the reasons for frequent changes in the policy. Make sure to capture your audiences attention in your business displays with our gratis customizable Information Technology Policy And Processes Information Security Policy For Employees Structure PDF. These are great for business strategies, office conferences, capital raising or task suggestions. If you desire to acquire more customers for your tech business and ensure they stay satisfied, create your own sales presentation with these plain slides.

Best Data Security Software Client Testimonials For Company Online Database Security Guidelines PDF
Presenting this set of slides with name best data security software client testimonials for company online database security guidelines pdf. This is a three stage process. The stages in this process are client testimonials, company, online database security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Roadmap For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software roadmap for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are roadmap, company, online database security, 2016 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Timeline For Company Online Database Security Proposal Graphics PDF
Presenting this set of slides with name best data security software timeline for company online database security proposal graphics pdf. This is a five stage process. The stages in this process are timeline, company, online database security, 2017 to 2020. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF
This slide represents the conspicuous russian cyber attacks on ukraine, including the attacks on government and banking websites, hacking of the countrys railway computer networks, etc. There are so many reasons you need a Series Of Cyber Security Attacks Against Ukraine 2022 Cyber Attacks On Ukraine Are Conspicuous By Their Absence Summary PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.

Essential Pillars Of Cloud Security Cloud Computing Security IT Ppt Design Ideas PDF
This slide shows the four essential pillars of cloud security, namely visibility and consistency, process-based security, network security, and identity security. Presenting essential pillars of cloud security cloud computing security it ppt design ideas pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like visibility and consistency, process based security, network security, identity security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.
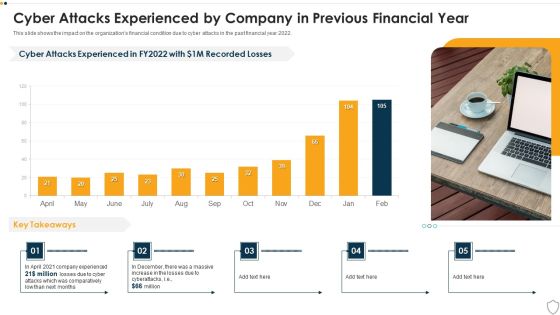
IT Security Cyber Attacks Experienced By Company In Previous Financial Year Ppt Outline Gallery PDF
This slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Deliver and pitch your topic in the best possible manner with this it security cyber attacks experienced by company in previous financial year ppt outline gallery pdf. Use them to share invaluable insights on cyber attacks experienced by company in previous financial year and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.
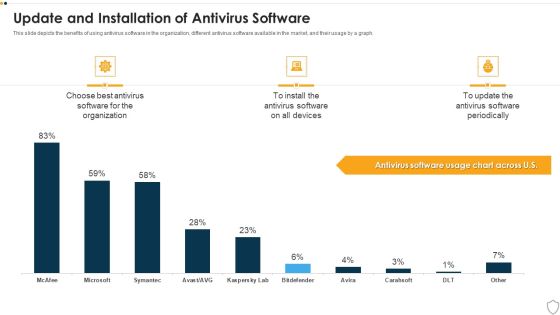
IT Security Update And Installation Of Antivirus Software Ppt Outline Sample PDF
This slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver and pitch your topic in the best possible manner with this it security update and installation of antivirus software ppt outline sample pdf. Use them to share invaluable insights on update and installation of antivirus software and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF
This slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Deliver and pitch your topic in the best possible manner with this IT Security Automation Tools Integration Different Security Automation Tools With Pros And Cons Summary PDF. Use them to share invaluable insights on Robotic Process Automation, Security Orchestration, Price and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF
This slide represents the techniques to protect our website from hacking and cyber attacks, including enhanced access controls, increased network security, installation of security software, etc.This is a IT Security Hacker Techniques To Keep Our Website Protected Guidelines PDF template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Software, Enhance Access, Update Everything. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF
This slide depicts software defined networking architecture features that include straight configurable, agile, vendor neutral, and open standards based. It also includes various components of SDN architecture such as application tier, control tier and infrastructure tier. Find highly impressive Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Features Of SDN Security Architecture Ppt PowerPoint Presentation File Ideas PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now

Channel Limitations Ppt Slide Design
This is a channel limitations ppt slide design. This is a three stage process. The stages in this process are direct, manufacturer, 1 tier partner, distributor, channels, 2 tier partner, end customers.

Our Keys To Success Template 1 Ppt PowerPoint Presentation Ideas Infographic Template
This is a our keys to success template 1 ppt powerpoint presentation ideas infographic template. This is a one stage process. The stages in this process are success, business, marketing, technology.
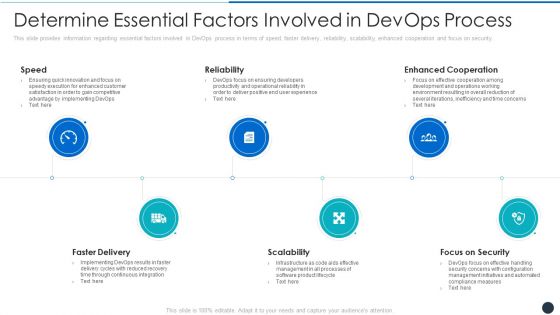
Determine Essential Factors Involved In Devops Process Elements PDF
This slide provides information regarding essential factors involved in DevOps process in terms of speed, faster delivery, reliability, scalability, enhanced cooperation and focus on security. This is a determine essential factors involved in devops process elements pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like reliability, enhanced, operationalq. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Strategies For Data Protection And Privacy Rules PDF
The following slide showcases some techniques to ensure data security and privacy. It includes elements such as authentication, data encryption, network security, access controls etc. Persuade your audience using this Key Strategies For Data Protection And Privacy Rules PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Authentication, Data Encryption, Network Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF
This slide signifies the enterprise resource planning skill evaluation to increase employee productivity. It covers information about grouping, technology ,process and functional related. Showcasing this set of slides titled Enterprise Resource Planning Assessment Model To Improve Cyber Security Performance Guidelines PDF. The topics addressed in these templates are Regular Major Releases, Application Scanner, Implement Assessment. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Table Of Contents For Amazon Strategic Growth Initiative On Global Scale Securing Elements PDF
Find highly impressive Table Of Contents For Amazon Strategic Growth Initiative On Global Scale Securing Elements PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Table Of Contents For Amazon Strategic Growth Initiative On Global Scale Securing Elements PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now.

Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF
Find highly impressive Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF on Slidegeeks to deliver a meaningful presentation. You can save an ample amount of time using these presentation templates. No need to worry to prepare everything from scratch because Slidegeeks experts have already done a huge research and work for you. You need to download Agenda For Developing Information Technology Security Awareness Training Program For Employees Elements PDF for your upcoming presentation. All the presentation templates are 100 percent editable and you can change the color and personalize the content accordingly. Download now
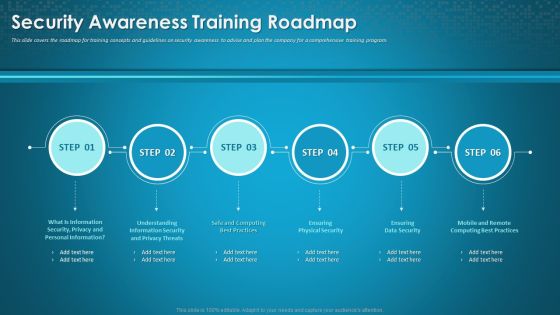
Organizational Network Staff Learning Security Awareness Training Roadmap Sample PDF
This slide covers the roadmap for training concepts and guidelines on security awareness to advise and plan the company for a comprehensive training program. Presenting organizational network staff learning security awareness training roadmap sample pdf to provide visual cues and insights. Share and navigate important information on six stages that need your due attention. This template can be used to pitch topics like ensuring data security, information security and privacy threats, ensuring physical security. In addition, this PPT design contains high-resolution images, graphics, etc, that are easily editable and available for immediate download.

Pre And Post Process Results Of Cyber Security Process Changes Sample PDF
This slide shows reduction in threats percentage after adopting cyber security. It includes computer virus, data breach, DOS and phishing. Pitch your topic with ease and precision using this Pre And Post Process Results Of Cyber Security Process Changes Sample PDF. This layout presents information on Process Results, Process Changes, Key Insights. It is also available for immediate download and adjustment. So, changes can be made in the color, design, graphics or any other component to create a unique layout.

Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF
This slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development.This is a Steps To Ensure Robotic Process Automation Security Robotic Process Automation Technology Icons PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Guarantee Accountability, Empower Secure, Log Respectability. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Best Data Security Software Timeframe For Company Online Database Security Proposal Topics PDF
Presenting this set of slides with name best data security software timeframe for company online database security proposal topics pdf. This is a four stage process. The stages in this process are project kickoff, planning, development and implementation, result. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
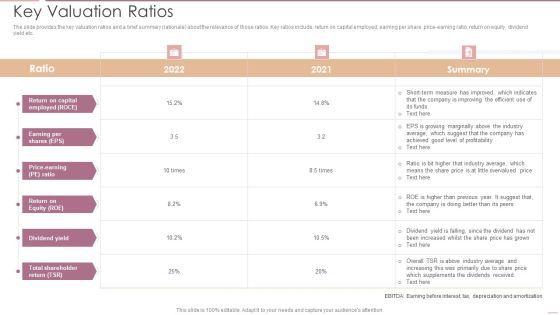
Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF
The slide provides the key valuation ratios and a brief summary rationale about the relevance of those ratios. Key ratios include return on capital employed, earning per share, price-earning ratio, return on equity, dividend yield etc.Deliver and pitch your topic in the best possible manner with this Investment Banking Security Underwriting Pitchbook Key Valuation Ratios Infographics PDF Use them to share invaluable insights on Measure Improved, Dividends Received, Total Shareholder and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Solutions To Overcome Security Operations Challenges Template PDF
This slide outlines solutions to overcome challenges faced by security operations teams in order to deal with an increasing number of cyber attacks. It includes challenges such as skill shortage, lack of automation, large volume of data, and work processes integration. Persuade your audience using this Solutions To Overcome Security Operations Challenges Template PDF. This PPT design covers one stages, thus making it a great tool to use. It also caters to a variety of topics including Lack Of Automation, Work Processes Integration, Data Security. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF
This slide consists of applicability of artificial intelligence and various dimensions in banking industry. The key areas are trend forecasting, customer support, transaction security and operation process. Persuade your audience using this Applications Of Artificial Intelligence In Commercial Banking Industry Elements PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Trend Forecasting, Transaction Security, Operation Process. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.
Global Cloud Based Email Security Market Our Team Ppt Portfolio Outline PDF
Presenting this set of slides with name global cloud based email security market our team ppt portfolio outline pdf. This is a three stage process. The stages in this process are our team. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Best Data Security Software Why Us For Company Online Database Security Proposal Themes PDF
Presenting this set of slides with name best data security software why us for company online database security proposal themes pdf. This is a four stage process. The stages in this process are our team includes elite software engineers and cyber security experts to keep our culture fresh, innovative and energetic. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Email Security Market Research Report Industry Drivers Ppt Outline Maker PDF
Presenting this set of slides with name email security market research report industry drivers ppt outline maker pdf. This is a five stage process. The stages in this process are increase in supply chain security, asia pacific area to show most growth, ai taking over the international market. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Security And Surveillance Company Profile Existing Channel Development Strategy Formats PDF
This slide highlights the security company channel development strategy which covers direct to home strategy including new incentive scheme and extra margin to channel hubs. It also includes inside sales strategy which focus on lead referral partners. Presenting Security And Surveillance Company Profile Existing Channel Development Strategy Formats PDF to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like Motion Awareness, Flood Protection, Thermostat Control. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF
This slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms.This is a Strategies To Enhance Retail Store Security Retail Outlet Operations Performance Evaluation Clipart PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Utilizes Electronic, Integrate Access, Monitored Alarms. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
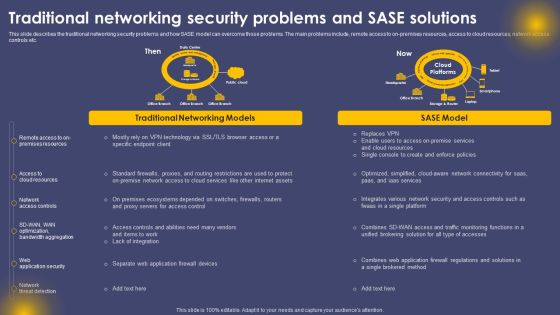
Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF
This slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. The best PPT templates are a great way to save time, energy, and resources. Slidegeeks have 100 percent editable powerpoint slides making them incredibly versatile. With these quality presentation templates, you can create a captivating and memorable presentation by combining visually appealing slides and effectively communicating your message. Download Traditional Networking Security Problems And SASE Solutions Ppt Infographic Template Slides PDF from Slidegeeks and deliver a wonderful presentation.
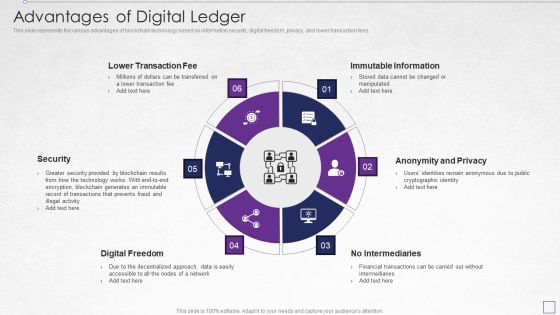
Digitized Record Book Technology Advantages Of Digital Ledger Elements PDF
This slide represents the various advantages of blockchain technology based on information security, digital freedom, privacy, and lower transaction fees. This is a digitized record book technology advantages of digital ledger elements pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like lower transaction fee, immutable information, anonymity and privacy, security, digital freedom. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Key Components Critical To Devops Viability IT Addressing Vital Success Factors Microsoft PDF
This slide provides information regarding the critical success factors associated to DevOps in terms of service and product ownership, cross functional teams and implementing security in DevOps. This is a key components critical to devops viability it addressing vital success factors microsoft pdf template with various stages. Focus and dispense information on three stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like service and product ownership, cross functional teams, implementing security in devops. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

3d Arrows Depicting 8 Concepts Flow Charts Office PowerPoint Templates
We present our 3d arrows depicting 8 concepts flow charts office PowerPoint templates.Use our Arrows PowerPoint Templates because, Knowledge is power goes the popular saying. Use our Shapes PowerPoint Templates because,your group can behave steady in the top bracket. Use our Signs PowerPoint Templates because,It helps you to Inform your team of your innovative ideas. Use our Business PowerPoint Templates because,You have secured a name for yourself in the domestic market. Now the time is right to spread your reach to other countries Use our Process and Flows PowerPoint Templates because,This template helps you to illustrate your method, piece by piece, and interlock the whole process in the minds of your audience.Use these PowerPoint slides for presentations relating to background, cheat, concept, conceptual, confession, deception, delusion, despair, direction, dishonesty, doubt, false, finance, fraud, hide, illustration, inaccuracy, insincerity, lie, mislead, psychology, road, sadness, sham, sign, trick, trickery, trust, truth, untruth, wrong. The prominent colors used in the PowerPoint template are Green, Green dark , Black. People tell us our 3d arrows depicting 8 concepts flow charts office PowerPoint templates are Vintage. The feedback we get is that our direction PowerPoint templates and PPT Slides have awesome images to get your point across. People tell us our 3d arrows depicting 8 concepts flow charts office PowerPoint templates are Second to none. Presenters tell us our conceptual PowerPoint templates and PPT Slides are readymade to fit into any presentation structure. The feedback we get is that our 3d arrows depicting 8 concepts flow charts office PowerPoint templates are Radiant. Professionals tell us our confession PowerPoint templates and PPT Slides are Handsome.
Employee Benefits Achievement Award Ppt PowerPoint Presentation Layouts Maker
This is a employee benefits achievement award ppt powerpoint presentation layouts maker. This is a eight stage process. The stages in this process are achievement award, employees allowance, pay raise, perks and bonuses, social security.

Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF
This slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. This Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Software Development Life Cycle Planning IT Security Residual Risk Matrix With Response Actions Graphics PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, dont wait, grab the presentation templates today.
Differentiating 2 Items Illustration For Free Internet Security Clipart PDF
Presenting differentiating 2 items illustration for free internet security clipart pdf to provide visual cues and insights. Share and navigate important information on two stages that need your due attention. This template can be used to pitch topics like differentiating 2 items illustration for free internet security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Blockchain Business Methodology For Business Security Icon Clipart PDF
Persuade your audience using this Blockchain Business Methodology For Business Security Icon Clipart PDF. This PPT design covers four stages, thus making it a great tool to use. It also caters to a variety of topics including Blockchain Business Methodology, Business Security Icon. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

Classification Of Business Data With Restricted Sensitive And Public Ppt PowerPoint Presentation Infographics Icon PDF
Presenting this set of slides with name classification of business data with restricted sensitive and public ppt powerpoint presentation infographics icon pdf. This is a three stage process. The stages in this process are public, sensitive, restricted, levels. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Key With Lock Vector Icon Ppt PowerPoint Presentation Portfolio Graphics Download PDF
Presenting this set of slides with name key with lock vector icon ppt powerpoint presentation portfolio graphics download pdf. This is a three stage process. The stages in this process are key with lock vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Open Lock Icon With Text Holders Ppt PowerPoint Presentation Ideas Templates PDF
Presenting this set of slides with name open lock icon with text holders ppt powerpoint presentation ideas templates pdf. This is a one stage process. The stage in this process is open lock icon with text holders. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Open Lock On Hand Vector Icon Ppt PowerPoint Presentation Styles Deck PDF
Presenting this set of slides with name open lock on hand vector icon ppt powerpoint presentation styles deck pdf. This is a three stage process. The stages in this process are open lock on hand vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Open Tablet With Password Vector Icon Ppt PowerPoint Presentation Pictures Slide Portrait PDF
Presenting this set of slides with name open tablet with password vector icon ppt powerpoint presentation pictures slide portrait pdf. This is a three stage process. The stages in this process are open tablet with password vector icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Padlock Icon On Laptop Screen Vector Illustration Ppt PowerPoint Presentation Portfolio
Presenting this set of slides with name padlock icon on laptop screen vector illustration ppt powerpoint presentation portfolio. This is a three stage process. The stages in this process are padlock icon on laptop screen vector illustration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Lock Icon On Computer Showing User Privacy Ppt PowerPoint Presentation Icon Inspiration PDF
Presenting this set of slides with name lock icon on computer showing user privacy ppt powerpoint presentation icon inspiration pdf. This is a one stage process. The stage in this process is lock icon on computer showing user privacy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Lock With Key With Facebook Sign Vector Illustration Ppt PowerPoint Presentation Show Model PDF
Presenting this set of slides with name lock with key with facebook sign vector illustration ppt powerpoint presentation show model pdf. This is a one stage process. The stage in this process is lock with key with facebook sign vector illustration. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF
This slide represents the cybersecurity risks associated with russia and ukraine conflict that are the most serious cyber threat, and many organizations are advised to take precautions. Do you have to make sure that everyone on your team knows about any specific topic I yes, then you should give Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF a try. Our experts have put a lot of knowledge and effort into creating this impeccable Series Of Cyber Security Attacks Against Ukraine 2022 Cybersecurity Risks Of An Escalating Russia Ukraine Conflict Infographics PDF. You can use this template for your upcoming presentations, as the slides are perfect to represent even the tiniest detail. You can download these templates from the Slidegeeks website and these are easy to edit. So grab these today.

Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF
This slide represents the ukraine and russia cyber warfare impact on western countries such as the united states, united kingdom, and estonia. This Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF is perfect for any presentation, be it in front of clients or colleagues. It is a versatile and stylish solution for organizing your meetings. The Series Of Cyber Security Attacks Against Ukraine 2022 Ukraine And Russia Cyber Warfare Impact On Western Countries Designs PDF features a modern design for your presentation meetings. The adjustable and customizable slides provide unlimited possibilities for acing up your presentation. Slidegeeks has done all the homework before launching the product for you. So, don not wait, grab the presentation templates today.

Integrated IOT Blockchain Platform Security Through Technology Background PDF
This slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Persuade your audience using this Integrated IOT Blockchain Platform Security Through Technology Background PDF. This PPT design covers six stages, thus making it a great tool to use. It also caters to a variety of topics including Transaction Requested Party, Requested Transaction, Crypto Currency. Download this PPT design now to present a convincing pitch that not only emphasizes the topic but also showcases your presentation skills.

 Home
Home