Safety Management System

Implementation Process Automation And Integrate Lead Generation Demonstration PDF
This slide highlights the setting roles of new users and assigning roles, also highlights the enable security with field level and integration of lead generation with emails for contact management.Deliver an awe inspiring pitch with this creative Implementation Process Automation And Integrate Lead Generation Demonstration PDF bundle. Topics like Schedule Appointments, Contact Management, Lead Generation can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Wan Optimization Template Powerpoint Slides Rules
This is a wan optimization template powerpoint slides rules. This is a five stage process. The stages in this process are data center, remote office, application visibility, wan security, central management.

Three Lines Of Defense Border Model For Cyber Security Designs PDF
This slide represents the model of lines of defense for products and services quality assurance. It includes activities performed in first, second and third line of defense for quality assurance such as risk management, monitor and support in risk related matters, internal quality audits etc. Presenting Three Lines Of Defense Border Model For Cyber Security Designs PDF to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including Cyber Security, Three Lines, Border Model. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Current Trends In Information Technology Template Powerpoint Slide
This is a current trends in information technology template powerpoint slide. This is a eight stage process. The stages in this process are network management, programming, scalable architecture, cloud computing, data governance, data analytics, data quality, security.

AI Based Automation Of Cyber Risk Security Controls Summary PDF
The following slide highlights the threat security controls which are integrated with artificial intelligence which includes RPA and ML. Showcasing this set of slides titled ai based automation of cyber risk security controls summary pdf. The topics addressed in these templates are controls management, cyber threat security controls, ai based cyber threat security. All the content presented in this PPT design is completely editable. Download it and make adjustments in color, background, font etc. as per your unique business setting.

Optimizing Educational Technology Powerpoint Templates Microsoft
This is a optimizing educational technology powerpoint templates microsoft. This is a six stage process. The stages in this process are information security, technology and analytics, institutional data management, optimizing educational technology, it workforce hiring and retention, it funding models.

Methods Of Software Risk Assessment Ppt Powerpoint Guide
This is a methods of software risk assessment ppt powerpoint guide. This is a seven stage process. The stages in this process are risk management, risk assessment, risk identification, risk periodization, security requirements, external review, penetration testing.

Components Of Enterprise Architecture Diagram Presentation Diagrams
This is a components of enterprise architecture diagram presentation diagrams. This is a four stage process. The stages in this process are risk and security, program management, technology driven, business driven.
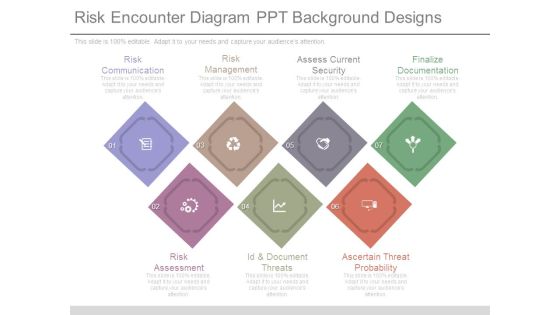
Risk Encounter Diagram Ppt Background Designs
This is a risk encounter diagram ppt background designs. This is a seven stage process. The stages in this process are risk communication, risk management, assess current security, finalize documentation, risk assessment, id and document threats, ascertain threat probability.
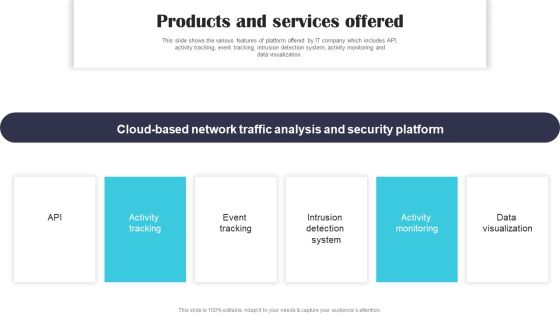
Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF
This slide shows the various features of platform offered by IT company which includes API, activity tracking, event tracking, intrusion detection system, activity monitoring and data visualization. This modern and well arranged Security Software Company Investor Funding Pitch Deck Products And Services Offered Clipart PDF provides lots of creative possibilities. It is very simple to customize and edit with the Powerpoint Software. Just drag and drop your pictures into the shapes. All facets of this template can be edited with Powerpoint no extra software is necessary. Add your own material, put your images in the places assigned for them, adjust the colors, and then you can show your slides to the world, with an animated slide included.

Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF
This slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.This is a Cloud Security Assessment Cloud Security Checklist Access Control Sample PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Administrative Rights, Privileged Credentials, Legitimate Users You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
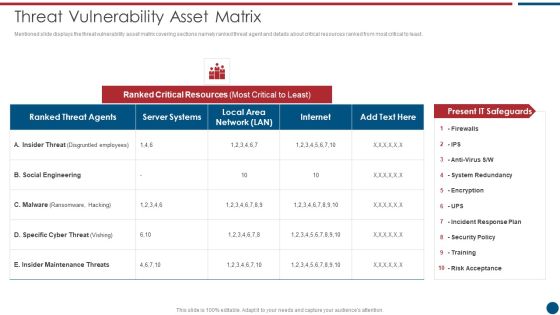
Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF
Mentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an awe inspiring pitch with this creative Risk Based Procedures To IT Security Threat Vulnerability Asset Matrix Ppt PowerPoint Presentation Gallery Ideas PDF bundle. Topics like Ranked Critical, Server Systems, Social Engineering can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
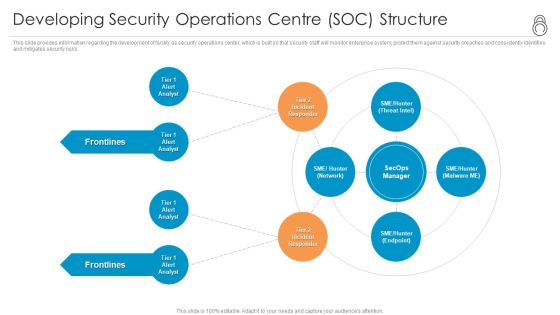
Enhanced Protection Corporate Event Administration Developing Security Operations Centre SOC Structure Formats PDF
This slide provides information regarding the development of facility as security operations center, which is built so that security staff will monitor enterprise system, protect them against security breaches and consistently identifies and mitigates security risks. Presenting enhanced protection corporate event administration developing security operations centre soc structure formats pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like developing security operations centre soc structure. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Ecommerce Challenges Online Security Ppt PowerPoint Presentation Styles Gridlines
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation styles gridlines. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Ecommerce Challenges Online Security Ppt PowerPoint Presentation Icon Show
Presenting this set of slides with name ecommerce challenges online security ppt powerpoint presentation icon show. This is a eight stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Convertible Fixed Income Securities Ppt PowerPoint Presentation Pictures Inspiration
Presenting this set of slides with name convertible fixed income securities ppt powerpoint presentation pictures inspiration. This is a six stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Marketable Securities Overview Investment Ppt PowerPoint Presentation Styles Graphic Images
Presenting this set of slides with name marketable securities overview investment ppt powerpoint presentation styles graphic images. This is a two stage process. The stages in this process are process, business, management, planning, strategy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
Internet Of Things Advantages In Business Ppt PowerPoint Presentation Gallery Icon PDF
Presenting internet of things advantages in business ppt powerpoint presentation gallery icon pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including security system, operational expenditure, rich data. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
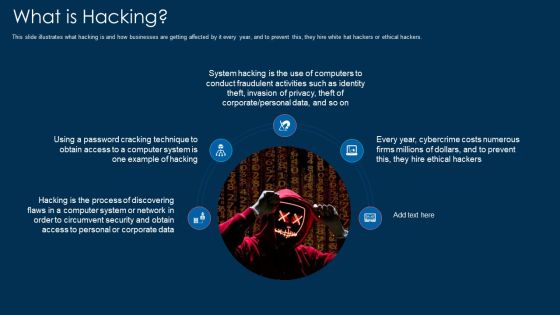
What Is Hacking Ppt Gallery Layouts PDF
Presenting what is hacking ppt gallery layouts pdf to provide visual cues and insights. Share and navigate important information on five stages that need your due attention. This template can be used to pitch topics like system, technique, security. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF
This slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve, such as hiring professionals, identifying weakest points in systems, assessing employees knowledge of cyber security and so on. Find a pre designed and impeccable Cyber Security Components To Enhance Processes End User Security Element Of Cyber Security Formats PDF. The templates can ace your presentation without additional effort. You can download these easy to edit presentation templates to make your presentation stand out from others. So, what are you waiting for Download the template from Slidegeeks today and give a unique touch to your presentation.
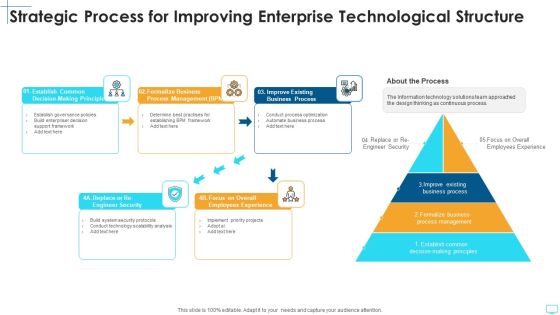
Strategic Process For Improving Enterprise Technological Structure Elements PDF
Presenting strategic process for improving enterprise technological structure elements pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including establish common decision making principles, formalize business process management, improve existing business process, replace or re engineer security, focus on overall employees experience. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Uniformed Security Proposal For Security Guard Services Table Of Content Inspiration PDF
This is a uniformed security proposal for security guard services table of content inspiration pdf template with various stages. Focus and dispense information on ten stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like plan, testimonials, investment, services, equipment. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
Information Technology Facilities Governance Client Standards Checklist Contd Icons PDF
In order to maximise service delivery efficiencies, customer satisfaction, the firm standardised certain environmental qualifications for type of hardwares, softwares, operating systems. This is a information technology facilities governance client standards checklist contd icons pdf template with various stages. Focus and dispense information on eight stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like protect servers, high speed internet access, secured encryption, wireless data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

White Hat Or Ethical Hackers Ppt Show Diagrams PDF
Deliver an awe inspiring pitch with this creative white hat or ethical hackers ppt show diagrams pdf bundle. Topics like organization, security, system, information can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF
This slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.This is a Cloud Security Assessment Cloud Security Threats Shared Vulnerabilities Icons PDF template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Security Standards, Authorization Restrictions, Providers Already. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.
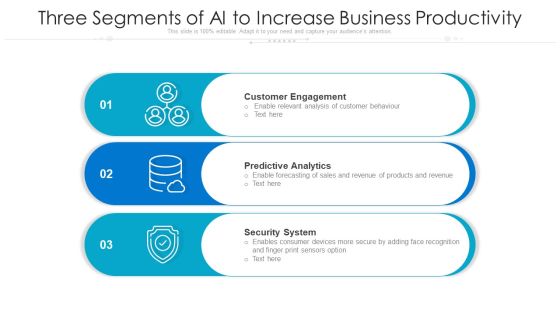
Three Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation Gallery Microsoft PDF
Presenting three segments of ai to increase business productivity ppt powerpoint presentation gallery microsoft pdf to dispense important information. This template comprises three stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
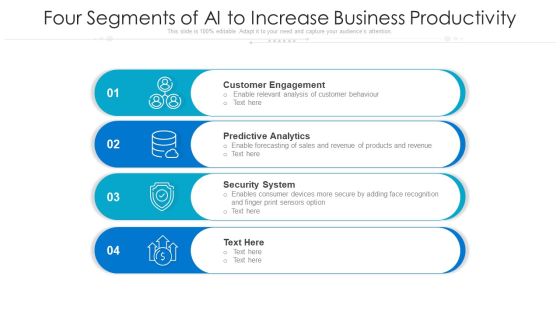
Four Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation Gallery Show PDF
Presenting four segments of ai to increase business productivity ppt powerpoint presentation gallery show pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Five Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation Gallery Visuals PDF
Presenting five segments of ai to increase business productivity ppt powerpoint presentation gallery visuals pdf to dispense important information. This template comprises five stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Six Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation File Styles PDF
Presenting six segments of ai to increase business productivity ppt powerpoint presentation file styles pdf to dispense important information. This template comprises six stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Seven Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation File Themes PDF
Presenting seven segments of ai to increase business productivity ppt powerpoint presentation file themes pdf to dispense important information. This template comprises seven stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.
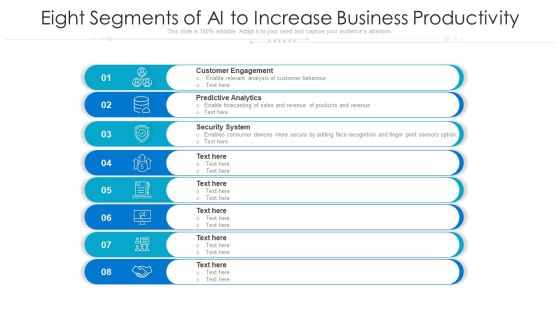
Eight Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation File Background Designs PDF
Presenting eight segments of ai to increase business productivity ppt powerpoint presentation file background designs pdf to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Nine Segments Of AI To Increase Business Productivity Ppt PowerPoint Presentation Gallery Format Ideas PDF
Presenting nine segments of ai to increase business productivity ppt powerpoint presentation gallery format ideas pdf to dispense important information. This template comprises nine stages. It also presents valuable insights into the topics including customer engagement, predictive analytics, security system. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Security And Process Integration Table Of Contents Designs PDF
Deliver an awe inspiring pitch with this creative security and process integration table of contents designs pdf bundle. Topics like management, implementation, analysis, technologies can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
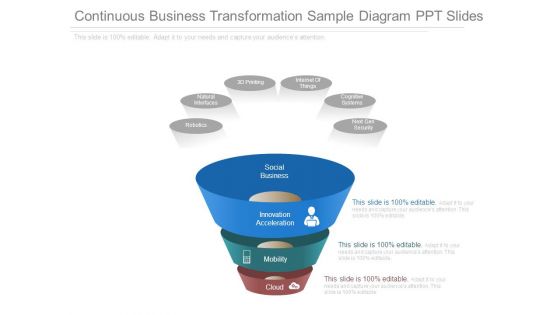
Continuous Business Transformation Sample Diagram Ppt Slides
This is a continuous business transformation sample diagram ppt slides. This is a three stage process. The stages in this process are robotics, natural, 3d printing, internet of things, cognitive systems, next gen security, social business, interfaces, innovation acceleration, mobility, cloud.

What Are The Downsides Of A Cloud Security Cloud Computing Security IT Ppt Summary Structure PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Deliver and pitch your topic in the best possible manner with this what are the downsides of a cloud security cloud computing security it ppt summary structure pdf. Use them to share invaluable insights on loss of control, data loss, insider theft, data breaches and impress your audience. This template can be altered and modified as per your expectations. So, grab it now.

Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF
This slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches. Presenting Cloud Information Security What Are The Downsides Of A Cloud Security Ppt Infographics Files PDF to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like Data Loss, Loss Control, Insider Theft, Data Breaches. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Computer Data Applications In E Commerce Sector Information PDF
The following slide highlights applications of big data in ecommerce to enhance online shopping experience. It covers use cases such as supply chain management, product recommendation, customer service, secure payments, target advertising, and demand forecasting. Presenting Computer Data Applications In E Commerce Sector Information PDF to dispense important information. This template comprises eight stages. It also presents valuable insights into the topics including Logistics Management, Customer Service, Pricing Optimization. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Facilities Rendered By Security Centre Implementation Ppt Pictures Design Templates PDF
This slide provides information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an awe inspiring pitch with this creative facilities rendered by security centre implementation ppt pictures design templates pdf bundle. Topics like Determine, organization, Security, Systems, data can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.
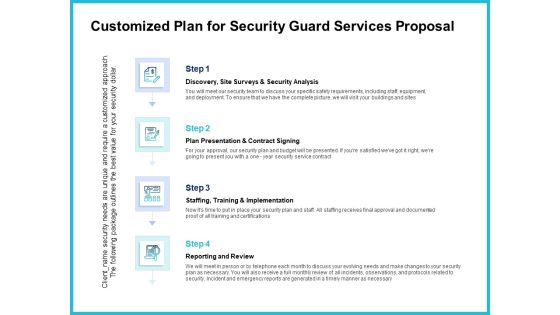
Uniformed Security Customized Plan For Security Guard Services Proposal Portrait PDF
Presenting uniformed security customized plan for security guard services proposal portrait pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like security analysis, plan presentation, training and implementation, reporting and review. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Way To Overcome Security Monitoring Challenges Setting Up An Advanced Cybersecurity Monitoring Plan Professional PDF
Presenting way to overcome security monitoring challenges setting up an advanced cybersecurity monitoring plan professional pdf to provide visual cues and insights. Share and navigate important information on nine stages that need your due attention. This template can be used to pitch topics like monitoring all systems, monitoring network traffic, monitoring user activity. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Security And Process Integration Contingency Plan For Threat Handling Template PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative security and process integration contingency plan for threat handling template pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Google Cloud Services Identity And Security Graphics PDF
This slide describes the identity and security service of google cloud, and it includes cloud resource manager, cloud IAM, cloud security scanner, and cloud platform security. This is a Google Cloud Services Identity And Security Graphics PDF template with various stages. Focus and dispense information on four stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like Cloud Resource Manager, Cloud Security Scanner, Cloud Platform Security. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF
This slide shows insider threat detection process flow. It contains information such as administrator, personal devices, behavior, detection system, behavior analysis, security auditing, terminating user access, etc. Presenting Process Flow For Detecting Insider Threat In Cyber Security Mockup PDF to dispense important information. This template comprises one stages. It also presents valuable insights into the topics including User Authentication, Insider Attacker, Administrator, Controlled Access. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Execution Of ICT Strategic Plan Implementation Of ICT Technologies For Operational Efficiency Background PDF
This slide represents information and communications technology ICT to enhance organization efficiency. It includes workforce management, service management, and security. Create an editable Execution Of ICT Strategic Plan Implementation Of ICT Technologies For Operational Efficiency Background PDF that communicates your idea and engages your audience. Whether you are presenting a business or an educational presentation, pre designed presentation templates help save time. Execution Of ICT Strategic Plan Implementation Of ICT Technologies For Operational Efficiency Background PDF is highly customizable and very easy to edit, covering many different styles from creative to business presentations. Slidegeeks has creative team members who have crafted amazing templates. So, go and get them without any delay.
Enhanced Protection Corporate Event Administration Contingency Plan For Threat Handling Icons PDF
This slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an awe inspiring pitch with this creative enhanced protection corporate event administration contingency plan for threat handling icons pdf bundle. Topics like contingency considerations, mainframe systems, security, implementation, technologies integration can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

Product Inauguration Event Planning And Administration Factors Considered For Event Diagrams PDF
This slide showcases factors to be considered for selecting event venue. Major factors considered are number of guests, parking facility, security, sound system, projector, podiums, stage, generators, etc. There are so many reasons you need a Product Inauguration Event Planning And Administration Factors Considered For Event Diagrams PDF. The first reason is you can not spend time making everything from scratch, Thus, Slidegeeks has made presentation templates for you too. You can easily download these templates from our website easily.
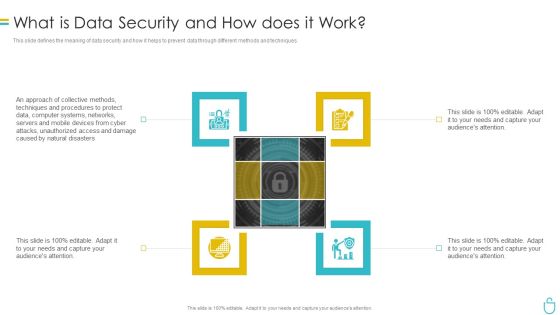
Information Security What Is Data Security And How Does It Work Ppt Professional Infographics PDF
This slide defines the meaning of data security and how it helps to prevent data through different methods and techniques. Presenting information security what is data security and how does it work ppt professional infographics pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like techniques, computer systems, protect. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Cloud Security Checklist Security Patches And Updates Cloud Computing Security IT Ppt File Icon PDF
This slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Presenting cloud security checklist security patches and updates cloud computing security it ppt file icon pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like organization, measures, technologies, developed. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Us Dollars Locked And Chained Security PowerPoint Templates Ppt Backgrounds For Slides 0113
We present our US Dollars Locked And Chained Security PowerPoint Templates PPT Backgrounds For Slides 0113.Present our Money PowerPoint Templates because You can Hit the nail on the head with our PowerPoint Templates and Slides. Embed your ideas in the minds of your audience. Download and present our Security PowerPoint Templates because you can Add colour to your speech with our PowerPoint Templates and Slides. Your presentation will leave your audience speechless. Download our Business PowerPoint Templates because It can be used to Set your controls for the heart of the sun. Our PowerPoint Templates and Slides will be the propellant to get you there. Download our Chains PowerPoint Templates because Our PowerPoint Templates and Slides will bullet point your ideas. See them fall into place one by one. Download and present our Services PowerPoint Templates because Our PowerPoint Templates and Slides will let you meet your Deadlines.Use these PowerPoint slides for presentations relating to
Wearable Electronics And The Internet Of Things Diagram Ppt Slides
This is a wearable electronics and the internet of things diagram ppt slides. This is a five stage process. The stages in this process are remote health monitoring, smart traffic control, energy management, building automation and security, machine to machine communication, internet of things.

Why Organizations Recruit Ethical Hackers Ppt Slides Smartart PDF
This is a why organizations recruit ethical hackers ppt slides smartart pdf template with various stages. Focus and dispense information on six stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like information systems, security, measures, data. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Consumer Service Strategy Project Deliverables And People Displayed In RACI Matrix Topics PDF
This slide provides information regarding the RACI matrix that is used during customer relationship transformation process with important project deliverables involved and key people involved. Deliver an awe inspiring pitch with this creative Consumer Service Strategy Project Deliverables And People Displayed In RACI Matrix Topics PDF bundle. Topics like Crm Goals Prioritizing, Risk And Security Management, Crm Team Building can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF
This slide depicts the reasons to describe the need for ethical hacking, including identification and correction of security flaws, aid in development quality control, and evaluation of the companys security regulatory compliance.Presenting IT Security Hacker Ethical Hacker And Why We Need Ethical Hacker Guidelines PDF to provide visual cues and insights. Share and navigate important information on three stages that need your due attention. This template can be used to pitch topics like Systems, Applications, Correcting Security, Regulatory Compliance. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

Introduction To Secure Access Service Edge SASE Ppt Infographics Demonstration PDF
This slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Want to ace your presentation in front of a live audience Our Introduction To Secure Access Service Edge SASE Ppt Infographics Demonstration PDF can help you do that by engaging all the users towards you. Slidegeeks experts have put their efforts and expertise into creating these impeccable powerpoint presentations so that you can communicate your ideas clearly. Moreover, all the templates are customizable, and easy to edit and downloadable. Use these for both personal and commercial use.

Smart Phone Device Security Best Practices Structure PDF
This slide shows key practices for protecting business data of mobile. The purpose of this slide is to highlight latest practices that can be used for securing mobile data. It include practices such as enable user authentication, update OS system, etc. Presenting Smart Phone Device Security Best Practices Structure PDF to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including Enable User Authentication, Avoid Using Public Wi Fi, Follow BYOD Policy. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Formation Of Acquired Entities Security Ppt PowerPoint Presentation Portfolio Images
Presenting this set of slides with name formation of acquired entities security ppt powerpoint presentation portfolio images. This is a four stage process. The stages in this process are formation, entities, business, development, management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.

Benefits For Successful Human Resource Service Delivery Ppt PowerPoint Presentation Gallery Graphics PDF
This slide covers the importance of effective human resource service delivery such as user experience, tasks and processes, rights and security, employee focus, etc. which are helpful in satisfying the user requirements, human resource system, secure documents, etc. Presenting benefits for successful human resource service delivery ppt powerpoint presentation gallery graphics pdf to dispense important information. This template comprises four stages. It also presents valuable insights into the topics including user experience, tasks and processes, rights and security. This is a completely customizable PowerPoint theme that can be put to use immediately. So, download it and address the topic impactfully.

Agenda Of Food Security Excellence Ppt Model Visuals PDF
Presenting agenda of food security excellence ppt model visuals pdf to provide visual cues and insights. Share and navigate important information on four stages that need your due attention. This template can be used to pitch topics like maintaining, process, management, raising quality. In addtion, this PPT design contains high resolution images, graphics, etc, that are easily editable and available for immediate download.

IT Security Common Methods Used To Threaten IT Security Ppt Portfolio Slides
This slide depicts the standard methods used to threaten network-security by cybercriminals attackers. It also shows the reasons for these threats and preventions from these threats. This is a common methods used to threaten information technology security ppt infographics master slide pdf template with various stages. Focus and dispense information on five stages using this creative set, that comes with editable features. It contains large content boxes to add your information on topics like politically, monetary, profit, system, malicious. You can also showcase facts, figures, and other relevant content using this PPT layout. Grab it now.

Security Architecture In 5G Technology 5G Functional Architecture Topics PDF
This slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration.Deliver an awe inspiring pitch with this creative Security Architecture In 5G Technology 5G Functional Architecture Topics PDF bundle. Topics like Standardization Segment, Concentrated Security, Components Interfaces can be discussed with this completely editable template. It is available for immediate download depending on the needs and requirements of the user.

 Home
Home